| File name: | TempSFX0J90DAFQGZBXSPFL99PNIHBSLJB8Z.EXE |
| Full analysis: | https://app.any.run/tasks/7fcdd9ab-934d-47a3-bb94-2f397ba1b926 |
| Verdict: | Malicious activity |
| Threats: | Amadey is a formidable Windows infostealer threat, characterized by its persistence mechanisms, modular design, and ability to execute various malicious tasks. |
| Analysis date: | June 10, 2025, 17:25:33 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, 5 sections |
| MD5: | 26CC5A6CFD8E8ECC433337413C14CDDB |
| SHA1: | FFC2D03477D5EAF6E111A72B89EC9A4654F96FE9 |
| SHA256: | 2D904D576B46236BAF504DBA21775F6EBBBD0F65272A9C2FCA1C6798184FA4E8 |
| SSDEEP: | 6144:mJEGTYya7Ad20rxuTwKEA2lLlB1HM6TSg6MJYmHWthx:lyyALQkKEAQxB1s6+g6qyx |
MALICIOUS
AMADEY mutex has been found
- TempSFX0J90DAFQGZBXSPFL99PNIHBSLJB8Z.EXE.exe (PID: 3656)
- ramez.exe (PID: 5616)
- ramez.exe (PID: 6224)
AMADEY has been detected (SURICATA)
- ramez.exe (PID: 5616)
Connects to the CnC server
- ramez.exe (PID: 5616)
AMADEY has been detected (YARA)
- ramez.exe (PID: 5616)
Run PowerShell with an invisible window
- powershell.exe (PID: 3148)
- powershell.exe (PID: 5124)
- powershell.exe (PID: 5496)
- powershell.exe (PID: 1200)
Changes Windows Defender settings
- 4GeyKOG.exe (PID: 2864)
- downloaded_app.exe (PID: 3476)
Adds path to the Windows Defender exclusion list
- 4GeyKOG.exe (PID: 2864)
- downloaded_app.exe (PID: 3476)
Bypass execution policy to execute commands
- powershell.exe (PID: 5496)
- powershell.exe (PID: 1200)
Changes powershell execution policy (Bypass)
- downloaded_app.exe (PID: 3476)
Adds process to the Windows Defender exclusion list
- downloaded_app.exe (PID: 3476)
Executing a file with an untrusted certificate
- sGe7ljJ.exe (PID: 6892)
COINMINER has been found (auto)
- ramez.exe (PID: 5616)
SUSPICIOUS
Reads the date of Windows installation
- TempSFX0J90DAFQGZBXSPFL99PNIHBSLJB8Z.EXE.exe (PID: 3656)
- MetaSkins.exe (PID: 1688)
- 4GeyKOG.exe (PID: 6532)
- 4GeyKOG.exe (PID: 2864)
- wKNvchW.exe (PID: 4960)
Starts itself from another location
- TempSFX0J90DAFQGZBXSPFL99PNIHBSLJB8Z.EXE.exe (PID: 3656)
Reads security settings of Internet Explorer
- TempSFX0J90DAFQGZBXSPFL99PNIHBSLJB8Z.EXE.exe (PID: 3656)
- ramez.exe (PID: 5616)
- MetaSkins.exe (PID: 1688)
- 4GeyKOG.exe (PID: 6532)
- 4GeyKOG.exe (PID: 2864)
Executable content was dropped or overwritten
- TempSFX0J90DAFQGZBXSPFL99PNIHBSLJB8Z.EXE.exe (PID: 3656)
- ramez.exe (PID: 5616)
- wKNvchW.exe (PID: 3836)
- wKNvchW.exe (PID: 5720)
- MetaSkins.exe (PID: 1688)
- cmd.exe (PID: 4804)
- MetaSkins.exe (PID: 2292)
- 4GeyKOG.exe (PID: 2864)
- rundll32.exe (PID: 6304)
Contacting a server suspected of hosting an CnC
- ramez.exe (PID: 5616)
Connects to the server without a host name
- ramez.exe (PID: 5616)
- net.exe (PID: 3588)
Application launched itself
- updater.exe (PID: 5432)
- 4GeyKOG.exe (PID: 6532)
- wKNvchW.exe (PID: 5720)
- wKNvchW.exe (PID: 3836)
Potential Corporate Privacy Violation
- ramez.exe (PID: 5616)
- 4GeyKOG.exe (PID: 2864)
- wKNvchW.exe (PID: 4960)
- wKNvchW.exe (PID: 7120)
The process executes via Task Scheduler
- updater.exe (PID: 5432)
- ramez.exe (PID: 6224)
There is functionality for enable RDP (YARA)
- ramez.exe (PID: 5616)
There is functionality for taking screenshot (YARA)
- ramez.exe (PID: 5616)
- wKNvchW.exe (PID: 5720)
- wKNvchW.exe (PID: 3836)
The process drops C-runtime libraries
- wKNvchW.exe (PID: 5720)
- wKNvchW.exe (PID: 3836)
Process requests binary or script from the Internet
- ramez.exe (PID: 5616)
- 4GeyKOG.exe (PID: 2864)
Process drops python dynamic module
- wKNvchW.exe (PID: 5720)
- wKNvchW.exe (PID: 3836)
Process drops legitimate windows executable
- wKNvchW.exe (PID: 5720)
- wKNvchW.exe (PID: 3836)
- MetaSkins.exe (PID: 2292)
- ramez.exe (PID: 5616)
Executing commands from a ".bat" file
- MetaSkins.exe (PID: 1688)
Starts CMD.EXE for commands execution
- MetaSkins.exe (PID: 1688)
- wKNvchW.exe (PID: 4960)
- wKNvchW.exe (PID: 7120)
Uses TIMEOUT.EXE to delay execution
- cmd.exe (PID: 4804)
The executable file from the user directory is run by the CMD process
- MetaSkins.exe (PID: 2292)
Script adds exclusion path to Windows Defender
- 4GeyKOG.exe (PID: 2864)
- downloaded_app.exe (PID: 3476)
Starts POWERSHELL.EXE for commands execution
- 4GeyKOG.exe (PID: 2864)
- downloaded_app.exe (PID: 3476)
Connects to unusual port
- 4GeyKOG.exe (PID: 2864)
Loads Python modules
- wKNvchW.exe (PID: 4960)
The process bypasses the loading of PowerShell profile settings
- downloaded_app.exe (PID: 3476)
Script adds exclusion process to Windows Defender
- downloaded_app.exe (PID: 3476)
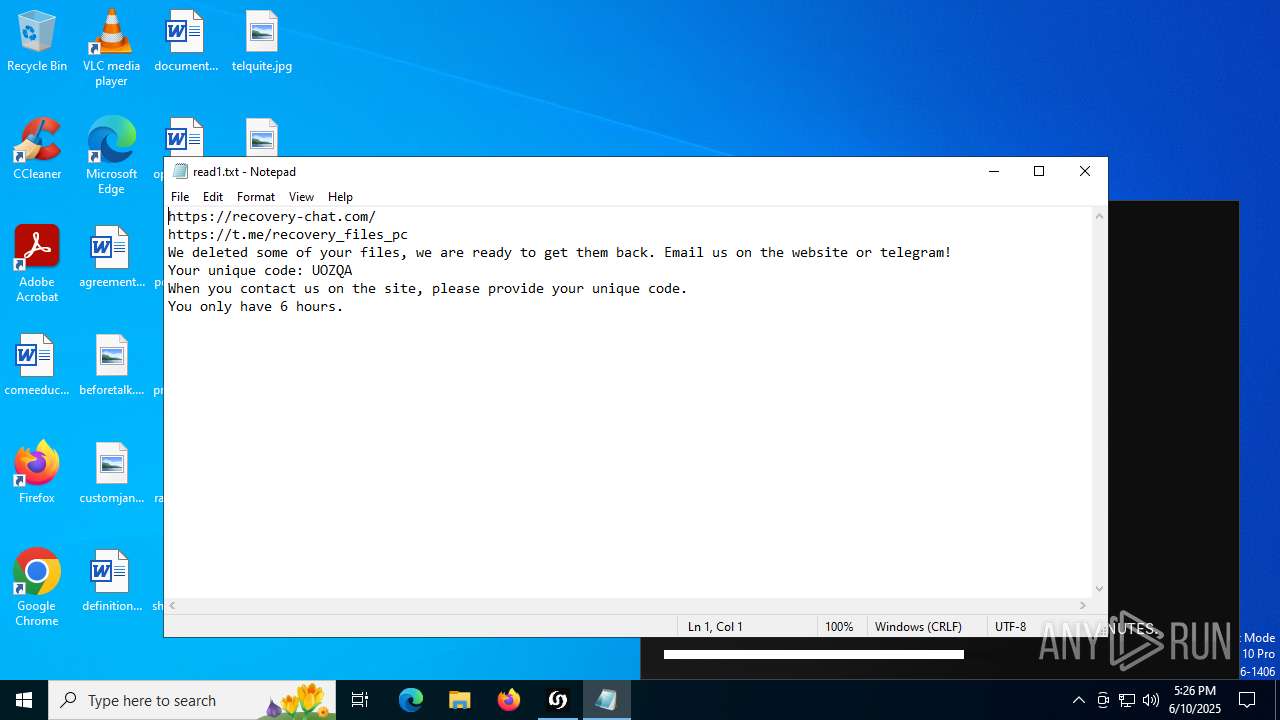
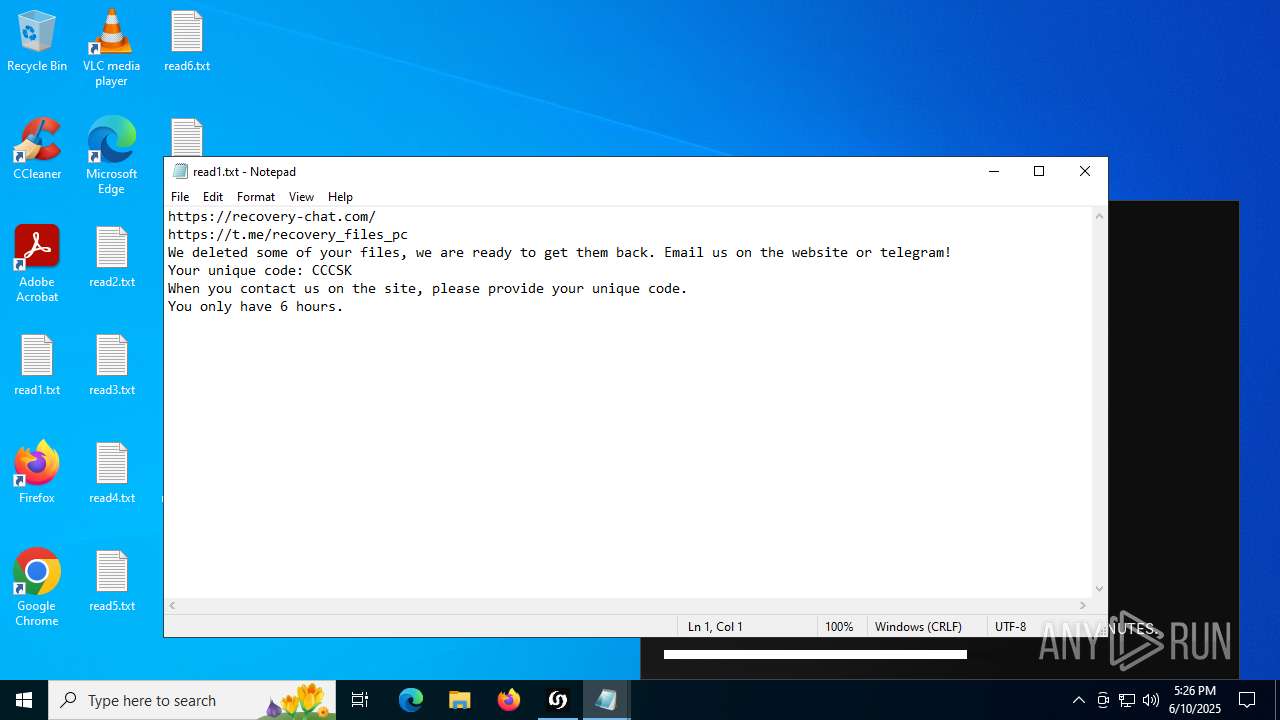
Start notepad (likely ransomware note)
- wKNvchW.exe (PID: 4960)
- wKNvchW.exe (PID: 7120)
Checks for external IP
- svchost.exe (PID: 2200)
- wKNvchW.exe (PID: 4960)
- wKNvchW.exe (PID: 7120)
Process communicates with Telegram (possibly using it as an attacker's C2 server)
- wKNvchW.exe (PID: 4960)
- wKNvchW.exe (PID: 7120)
Starts a Microsoft application from unusual location
- DgO51N6.exe (PID: 5444)
- sGe7ljJ.exe (PID: 6892)
INFO
Reads the computer name
- TempSFX0J90DAFQGZBXSPFL99PNIHBSLJB8Z.EXE.exe (PID: 3656)
- ramez.exe (PID: 5616)
- updater.exe (PID: 5432)
- wKNvchW.exe (PID: 5720)
- wKNvchW.exe (PID: 3836)
- MetaSkins.exe (PID: 1688)
- MetaSkins.exe (PID: 2292)
- 4GeyKOG.exe (PID: 6532)
- 4GeyKOG.exe (PID: 2864)
- msiexec.exe (PID: 2732)
- wKNvchW.exe (PID: 4960)
Reads Environment values
- TempSFX0J90DAFQGZBXSPFL99PNIHBSLJB8Z.EXE.exe (PID: 3656)
- ramez.exe (PID: 5616)
Create files in a temporary directory
- TempSFX0J90DAFQGZBXSPFL99PNIHBSLJB8Z.EXE.exe (PID: 3656)
- ramez.exe (PID: 5616)
- wKNvchW.exe (PID: 3836)
- wKNvchW.exe (PID: 5720)
- MetaSkins.exe (PID: 1688)
- rundll32.exe (PID: 6304)
Checks supported languages
- TempSFX0J90DAFQGZBXSPFL99PNIHBSLJB8Z.EXE.exe (PID: 3656)
- ramez.exe (PID: 5616)
- updater.exe (PID: 5432)
- updater.exe (PID: 6900)
- wKNvchW.exe (PID: 5720)
- wKNvchW.exe (PID: 3836)
- MelonityV2.exe (PID: 1944)
- ramez.exe (PID: 6224)
- MetaSkins.exe (PID: 1688)
- MetaSkins.exe (PID: 2292)
- 4GeyKOG.exe (PID: 6532)
- 4GeyKOG.exe (PID: 2864)
- downloaded_app.exe (PID: 3476)
- msiexec.exe (PID: 2732)
- wKNvchW.exe (PID: 4960)
Process checks computer location settings
- TempSFX0J90DAFQGZBXSPFL99PNIHBSLJB8Z.EXE.exe (PID: 3656)
- ramez.exe (PID: 5616)
- MetaSkins.exe (PID: 1688)
- 4GeyKOG.exe (PID: 6532)
- 4GeyKOG.exe (PID: 2864)
- wKNvchW.exe (PID: 4960)
Checks proxy server information
- ramez.exe (PID: 5616)
- wKNvchW.exe (PID: 4960)
Creates files or folders in the user directory
- ramez.exe (PID: 5616)
- MelonityV2.exe (PID: 1944)
- 4GeyKOG.exe (PID: 2864)
Process checks whether UAC notifications are on
- updater.exe (PID: 5432)
The sample compiled with english language support
- wKNvchW.exe (PID: 5720)
- wKNvchW.exe (PID: 3836)
- ramez.exe (PID: 5616)
- MetaSkins.exe (PID: 2292)
Reads the software policy settings
- ramez.exe (PID: 5616)
Reads the machine GUID from the registry
- ramez.exe (PID: 5616)
PyInstaller has been detected (YARA)
- wKNvchW.exe (PID: 3836)
- wKNvchW.exe (PID: 5720)
Checks if a key exists in the options dictionary (POWERSHELL)
- powershell.exe (PID: 5124)
- powershell.exe (PID: 3148)
Script raised an exception (POWERSHELL)
- powershell.exe (PID: 3148)
- powershell.exe (PID: 5124)
Executable content was dropped or overwritten
- msiexec.exe (PID: 2732)
CONNECTWISE has been detected
- msiexec.exe (PID: 2732)
Checks operating system version
- wKNvchW.exe (PID: 4960)
- wKNvchW.exe (PID: 7120)
Reads Microsoft Office registry keys
- wKNvchW.exe (PID: 4960)
Reads security settings of Internet Explorer
- notepad.exe (PID: 4412)
Attempting to use instant messaging service
- wKNvchW.exe (PID: 7120)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win64 Executable (generic) (64.6) |
|---|---|---|
| .dll | | | Win32 Dynamic Link Library (generic) (15.4) |
| .exe | | | Win32 Executable (generic) (10.5) |
| .exe | | | Generic Win/DOS Executable (4.6) |
| .exe | | | DOS Executable Generic (4.6) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2025:05:01 04:57:19+00:00 |
| ImageFileCharacteristics: | Executable, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 14.29 |
| CodeSize: | 317952 |
| InitializedDataSize: | 123392 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x28c3a |
| OSVersion: | 6 |
| ImageVersion: | - |
| SubsystemVersion: | 6 |
| Subsystem: | Windows GUI |
Total processes
186
Monitored processes
47
Malicious processes
10
Suspicious processes
5
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1080 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1200 | powershell -NoProfile -WindowStyle Hidden -ExecutionPolicy Bypass -Command "Add-MpPreference -ExclusionProcess ''" | C:\Windows\SysWOW64\WindowsPowerShell\v1.0\powershell.exe | — | downloaded_app.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows PowerShell Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1204 | "C:\WINDOWS\system32\NOTEPAD.EXE" C:\Users\admin\Desktop\read1.txt | C:\Windows\System32\notepad.exe | — | wKNvchW.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1688 | "C:\Users\admin\AppData\Local\Temp\10355390101\MetaSkins.exe" | C:\Users\admin\AppData\Local\Temp\10355390101\MetaSkins.exe | ramez.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 4294967295 Modules
| |||||||||||||||
| 1812 | "C:\Users\admin\AppData\Local\Temp\10355390101\MetaSkins.exe" | C:\Users\admin\AppData\Local\Temp\10355390101\MetaSkins.exe | — | ramez.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221226540 Modules
| |||||||||||||||
| 1944 | "C:\Users\admin\AppData\Local\Temp\10355370101\MelonityV2.exe" | C:\Users\admin\AppData\Local\Temp\10355370101\MelonityV2.exe | ramez.exe | ||||||||||||
User: admin Company: Melonity Integrity Level: HIGH Description: Melonity Launcher Version: 1.1.0.0 Modules
| |||||||||||||||
| 2200 | C:\WINDOWS\system32\svchost.exe -k NetworkService -p -s Dnscache | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2276 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2292 | "C:\Users\admin\AppData\Local\Temp\10355390101\MetaSkins.exe" | C:\Users\admin\AppData\Local\Temp\10355390101\MetaSkins.exe | cmd.exe | ||||||||||||
User: admin Integrity Level: HIGH Modules
| |||||||||||||||
| 2552 | C:\Windows\syswow64\MsiExec.exe -Embedding 730CF7B01571F4ADF3CAE2EF416A8CD2 | C:\Windows\SysWOW64\msiexec.exe | — | msiexec.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows® installer Exit code: 0 Version: 5.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
32 734
Read events
32 705
Write events
20
Delete events
9
Modification events
| (PID) Process: | (3656) TempSFX0J90DAFQGZBXSPFL99PNIHBSLJB8Z.EXE.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (3656) TempSFX0J90DAFQGZBXSPFL99PNIHBSLJB8Z.EXE.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (3656) TempSFX0J90DAFQGZBXSPFL99PNIHBSLJB8Z.EXE.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (3656) TempSFX0J90DAFQGZBXSPFL99PNIHBSLJB8Z.EXE.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (5616) ramez.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (5616) ramez.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (5616) ramez.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (5616) ramez.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\FileExts\.msi\OpenWithProgids |
| Operation: | write | Name: | Msi.Package |
Value: | |||
| (PID) Process: | (2732) msiexec.exe | Key: | HKEY_USERS\S-1-5-21-1693682860-607145093-2874071422-1001\SOFTWARE\Microsoft\RestartManager\Session0000 |
| Operation: | write | Name: | Owner |
Value: AC0A0000A8C956CA2CDADB01 | |||
| (PID) Process: | (2732) msiexec.exe | Key: | HKEY_USERS\S-1-5-21-1693682860-607145093-2874071422-1001\SOFTWARE\Microsoft\RestartManager\Session0000 |
| Operation: | write | Name: | SessionHash |
Value: 172BC66E6C02F4F830EE22EFFD08E3D9A2C87210309D8B73C3A7B5E3AAF57C48 | |||
Executable files
82
Suspicious files
18
Text files
1 904
Unknown types
14
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 5720 | wKNvchW.exe | C:\Users\admin\AppData\Local\Temp\_MEI57202\_queue.pyd | executable | |
MD5:DE0A5977D4692BC1D60A01D852B07271 | SHA256:4C1B88BF2D4E3ACA4E09D7793C8D53AA4985EBE572288A04175210F44D35C25B | |||
| 5720 | wKNvchW.exe | C:\Users\admin\AppData\Local\Temp\_MEI57202\_tcl_data\auto.tcl | text | |
MD5:97EFA9EBE840EA051F9706504C8BD783 | SHA256:08113823951619D659EB03A1F6ACD2F9500E1264795219125A5DF7B83CABCB99 | |||
| 5720 | wKNvchW.exe | C:\Users\admin\AppData\Local\Temp\_MEI57202\_ssl.pyd | executable | |
MD5:6E6E510E8FA4555C9FD671981BBE513A | SHA256:CC5C21C1B5A8890D2BB14FD5CFAB5114D2B427E17DCC567578EBB3F7D4B014E8 | |||
| 5720 | wKNvchW.exe | C:\Users\admin\AppData\Local\Temp\_MEI57202\_socket.pyd | executable | |
MD5:1AD8628499A107382153348A14A1DFC7 | SHA256:7A20FE96274F554CC527C65F42A8DE9CF0C201852BEDDDC12E44D9106BAB728F | |||
| 5720 | wKNvchW.exe | C:\Users\admin\AppData\Local\Temp\_MEI57202\_hashlib.pyd | executable | |
MD5:692837EB1FCB73EF33A1474B18DFC7CD | SHA256:D674D53F7E2F906FBAF0D19AB871F9CFF53956D40B3CE003A2B4B44B549D4B92 | |||
| 5720 | wKNvchW.exe | C:\Users\admin\AppData\Local\Temp\_MEI57202\_tcl_data\clock.tcl | text | |
MD5:31BB1CACF5D128F77C0922800D3E111A | SHA256:BD1C2DC481A582EF9EAB301468EC7E7C3A284C57617FB2F4A8A97C22576FC762 | |||
| 5720 | wKNvchW.exe | C:\Users\admin\AppData\Local\Temp\_MEI57202\_overlapped.pyd | executable | |
MD5:1F4BC255F94F24B5ED50102F3467E19D | SHA256:028103F36B2120B456F0EEEAFF0EBB41DF6D1F7D31ACFE7D8F54F5DDDC6EC082 | |||
| 5720 | wKNvchW.exe | C:\Users\admin\AppData\Local\Temp\_MEI57202\_lzma.pyd | executable | |
MD5:0D549F688E0B2424B549AFCAC58D5FA7 | SHA256:80DF30ED0F2C532C07EA7FDC44836E40A8EBD9E7611365A1A26989147E1A4210 | |||
| 5720 | wKNvchW.exe | C:\Users\admin\AppData\Local\Temp\_MEI57202\VCRUNTIME140_1.dll | executable | |
MD5:C0C0B4C611561F94798B62EB43097722 | SHA256:497A280550443E3E9F89E428E51CB795139CA8944D5DEDD54A7083C00E7164E5 | |||
| 5720 | wKNvchW.exe | C:\Users\admin\AppData\Local\Temp\_MEI57202\VCRUNTIME140.dll | executable | |
MD5:32DA96115C9D783A0769312C0482A62D | SHA256:8B10C53241726B0ACC9F513157E67FCB01C166FEC69E5E38CA6AADA8F9A3619F | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
31
TCP/UDP connections
40
DNS requests
23
Threats
28
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5616 | ramez.exe | POST | 200 | 185.156.72.96:80 | http://185.156.72.96/te4h2nus/index.php | unknown | — | — | unknown |
5616 | ramez.exe | GET | 200 | 185.156.72.2:80 | http://185.156.72.2/files/7892865167/wKNvchW.exe | unknown | — | — | unknown |
4168 | svchost.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 2.16.241.19:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 2.23.246.101:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
5616 | ramez.exe | POST | 200 | 185.156.72.96:80 | http://185.156.72.96/te4h2nus/index.php | unknown | — | — | unknown |
5616 | ramez.exe | POST | 200 | 185.156.72.96:80 | http://185.156.72.96/te4h2nus/index.php | unknown | — | — | unknown |
5616 | ramez.exe | GET | 200 | 163.181.92.203:80 | http://ocsp.digicert.cn/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEA%2FgMquETQMxBsUMjhPIsGg%3D | unknown | — | — | whitelisted |
5616 | ramez.exe | POST | 200 | 185.156.72.96:80 | http://185.156.72.96/te4h2nus/index.php | unknown | — | — | unknown |
5616 | ramez.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAhflMAthXvozBT%2FU%2B2iPio%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
5944 | MoUsoCoreWorker.exe | 4.231.128.59:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1268 | svchost.exe | 4.231.128.59:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4172 | RUXIMICS.exe | 4.231.128.59:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5616 | ramez.exe | 185.156.72.96:80 | — | Tov Vaiz Partner | RU | unknown |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
5616 | ramez.exe | 185.156.72.2:80 | — | Tov Vaiz Partner | RU | unknown |
2336 | svchost.exe | 172.211.123.249:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
4168 | svchost.exe | 20.190.160.3:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4168 | svchost.exe | 2.23.77.188:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
nexusrules.officeapps.live.com |
| whitelisted |
melonity-cdn.fra1.cdn.digitaloceanspaces.com |
| whitelisted |
ocsp.digicert.cn |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
5616 | ramez.exe | Malware Command and Control Activity Detected | BOTNET [ANY.RUN] Amadey HTTP POST Request (st=s) |
5616 | ramez.exe | Malware Command and Control Activity Detected | ET MALWARE Amadey CnC Response |
5616 | ramez.exe | Potentially Bad Traffic | ET INFO Executable Download from dotted-quad Host |
5616 | ramez.exe | Potential Corporate Privacy Violation | ET INFO PE EXE or DLL Windows file download HTTP |
5616 | ramez.exe | Misc activity | ET INFO Packed Executable Download |
5616 | ramez.exe | Potentially Bad Traffic | ET INFO Executable Retrieved With Minimal HTTP Headers - Potential Second Stage Download |
5616 | ramez.exe | Potentially Bad Traffic | ET HUNTING SUSPICIOUS Dotted Quad Host MZ Response |
5616 | ramez.exe | Potentially Bad Traffic | ET INFO Executable Download from dotted-quad Host |
2864 | 4GeyKOG.exe | Potentially Bad Traffic | ET INFO Executable Download from dotted-quad Host |
2864 | 4GeyKOG.exe | Potentially Bad Traffic | ET HUNTING Request for EXE via WinHTTP M2 |