| File name: | 2025-05-16_14e2a2b412520ecadf671372b752ce0e_amadey_darkgate_elex_gcleaner_smoke-loader |
| Full analysis: | https://app.any.run/tasks/6a8cb92b-ebbc-42ad-b025-b9e31f0634c5 |
| Verdict: | Malicious activity |
| Threats: | A backdoor is a type of cybersecurity threat that allows attackers to secretly compromise a system and conduct malicious activities, such as stealing data and modifying files. Backdoors can be difficult to detect, as they often use legitimate system applications to evade defense mechanisms. Threat actors often utilize special malware, such as PlugX, to establish backdoors on target devices. |
| Analysis date: | May 16, 2025, 04:34:44 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, 8 sections |
| MD5: | 14E2A2B412520ECADF671372B752CE0E |
| SHA1: | 3688C66AF2D09AA481828311BDED707B116714FE |
| SHA256: | 2D748C6CDB0DD6B5BC5F7BDD5D15F50B9D008D0D75CB68DF1E72B8F01084C2EC |
| SSDEEP: | 49152:53HzLnqOaNMCFJ6kPvO1cg0i7wDfe9Hx8KPJDH1LsE:Vr7ayGJ6kHOS7Dfen8KPJD6E |
MALICIOUS
XRED mutex has been found
- 2025-05-16_14e2a2b412520ecadf671372b752ce0e_amadey_darkgate_elex_gcleaner_smoke-loader.exe (PID: 7608)
- Synaptics.exe (PID: 7860)
- Synaptics.exe (PID: 7948)
XRED has been detected
- 2025-05-16_14e2a2b412520ecadf671372b752ce0e_amadey_darkgate_elex_gcleaner_smoke-loader.exe (PID: 7608)
XRED has been detected (YARA)
- Synaptics.exe (PID: 7860)
Changes the autorun value in the registry
- 2025-05-16_14e2a2b412520ecadf671372b752ce0e_amadey_darkgate_elex_gcleaner_smoke-loader.exe (PID: 7608)
SUSPICIOUS
Executable content was dropped or overwritten
- 2025-05-16_14e2a2b412520ecadf671372b752ce0e_amadey_darkgate_elex_gcleaner_smoke-loader.exe (PID: 7608)
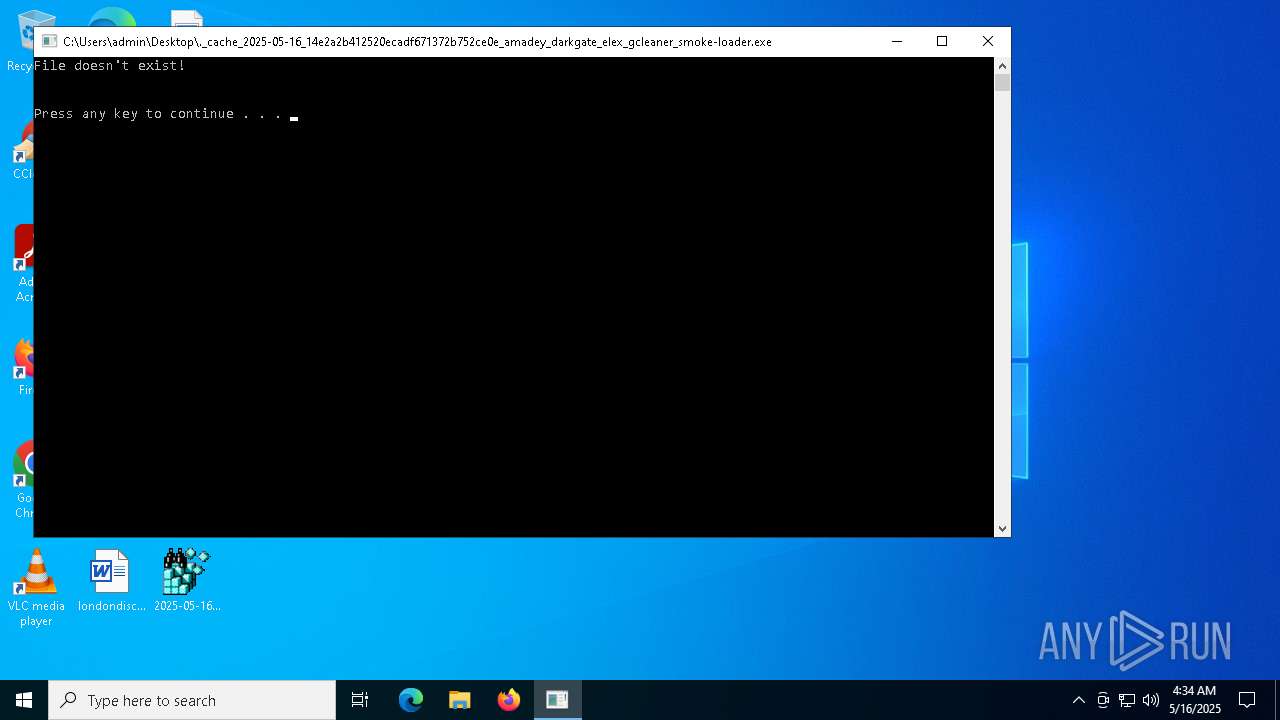
Starts CMD.EXE for commands execution
- ._cache_2025-05-16_14e2a2b412520ecadf671372b752ce0e_amadey_darkgate_elex_gcleaner_smoke-loader.exe (PID: 7656)
Reads security settings of Internet Explorer
- Synaptics.exe (PID: 7860)
- 2025-05-16_14e2a2b412520ecadf671372b752ce0e_amadey_darkgate_elex_gcleaner_smoke-loader.exe (PID: 7608)
There is functionality for communication over UDP network (YARA)
- Synaptics.exe (PID: 7860)
There is functionality for communication dyndns network (YARA)
- Synaptics.exe (PID: 7860)
There is functionality for taking screenshot (YARA)
- Synaptics.exe (PID: 7860)
INFO
Checks supported languages
- 2025-05-16_14e2a2b412520ecadf671372b752ce0e_amadey_darkgate_elex_gcleaner_smoke-loader.exe (PID: 7608)
- ._cache_2025-05-16_14e2a2b412520ecadf671372b752ce0e_amadey_darkgate_elex_gcleaner_smoke-loader.exe (PID: 7656)
- Synaptics.exe (PID: 7948)
- Synaptics.exe (PID: 7860)
The sample compiled with turkish language support
- 2025-05-16_14e2a2b412520ecadf671372b752ce0e_amadey_darkgate_elex_gcleaner_smoke-loader.exe (PID: 7608)
Process checks computer location settings
- 2025-05-16_14e2a2b412520ecadf671372b752ce0e_amadey_darkgate_elex_gcleaner_smoke-loader.exe (PID: 7608)
Reads the computer name
- Synaptics.exe (PID: 7860)
- Synaptics.exe (PID: 7948)
- 2025-05-16_14e2a2b412520ecadf671372b752ce0e_amadey_darkgate_elex_gcleaner_smoke-loader.exe (PID: 7608)
Creates files in the program directory
- Synaptics.exe (PID: 7860)
- 2025-05-16_14e2a2b412520ecadf671372b752ce0e_amadey_darkgate_elex_gcleaner_smoke-loader.exe (PID: 7608)
Auto-launch of the file from Registry key
- 2025-05-16_14e2a2b412520ecadf671372b752ce0e_amadey_darkgate_elex_gcleaner_smoke-loader.exe (PID: 7608)
Manual execution by a user
- Synaptics.exe (PID: 7948)
Checks proxy server information
- Synaptics.exe (PID: 7860)
- slui.exe (PID: 7268)
Compiled with Borland Delphi (YARA)
- conhost.exe (PID: 7664)
- Synaptics.exe (PID: 7860)
- slui.exe (PID: 7268)
Reads the software policy settings
- Synaptics.exe (PID: 7860)
- slui.exe (PID: 7268)
Create files in a temporary directory
- Synaptics.exe (PID: 7860)
Reads the machine GUID from the registry
- Synaptics.exe (PID: 7860)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable Borland Delphi 7 (96.4) |
|---|---|---|
| .exe | | | Win32 Executable Delphi generic (2) |
| .exe | | | Win32 Executable (generic) (0.6) |
| .exe | | | Win16/32 Executable Delphi generic (0.3) |
| .exe | | | Generic Win/DOS Executable (0.2) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 1992:06:19 22:22:17+00:00 |
| ImageFileCharacteristics: | Executable, No line numbers, No symbols, Bytes reversed lo, 32-bit, Bytes reversed hi |
| PEType: | PE32 |
| LinkerVersion: | 2.25 |
| CodeSize: | 629760 |
| InitializedDataSize: | 797696 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x9ab80 |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 1.0.0.4 |
| ProductVersionNumber: | 1.0.0.4 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Turkish |
| CharacterSet: | Windows, Turkish |
| CompanyName: | Synaptics |
| FileDescription: | Synaptics Pointing Device Driver |
| FileVersion: | 1.0.0.4 |
| InternalName: | - |
| LegalCopyright: | - |
| LegalTrademarks: | - |
| OriginalFileName: | - |
| ProductName: | Synaptics Pointing Device Driver |
| ProductVersion: | 1.0.0.0 |
| Comments: | - |
Total processes
132
Monitored processes
8
Malicious processes
3
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2196 | C:\WINDOWS\system32\svchost.exe -k NetworkService -p -s Dnscache | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7268 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7608 | "C:\Users\admin\Desktop\2025-05-16_14e2a2b412520ecadf671372b752ce0e_amadey_darkgate_elex_gcleaner_smoke-loader.exe" | C:\Users\admin\Desktop\2025-05-16_14e2a2b412520ecadf671372b752ce0e_amadey_darkgate_elex_gcleaner_smoke-loader.exe | explorer.exe | ||||||||||||
User: admin Company: Synaptics Integrity Level: MEDIUM Description: Synaptics Pointing Device Driver Exit code: 0 Version: 1.0.0.4 Modules
| |||||||||||||||
| 7656 | "C:\Users\admin\Desktop\._cache_2025-05-16_14e2a2b412520ecadf671372b752ce0e_amadey_darkgate_elex_gcleaner_smoke-loader.exe" | C:\Users\admin\Desktop\._cache_2025-05-16_14e2a2b412520ecadf671372b752ce0e_amadey_darkgate_elex_gcleaner_smoke-loader.exe | — | 2025-05-16_14e2a2b412520ecadf671372b752ce0e_amadey_darkgate_elex_gcleaner_smoke-loader.exe | |||||||||||
User: admin Integrity Level: MEDIUM Modules
| |||||||||||||||
| 7664 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | ._cache_2025-05-16_14e2a2b412520ecadf671372b752ce0e_amadey_darkgate_elex_gcleaner_smoke-loader.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7720 | C:\WINDOWS\system32\cmd.exe /c pause | C:\Windows\SysWOW64\cmd.exe | — | ._cache_2025-05-16_14e2a2b412520ecadf671372b752ce0e_amadey_darkgate_elex_gcleaner_smoke-loader.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7860 | "C:\ProgramData\Synaptics\Synaptics.exe" InjUpdate | C:\ProgramData\Synaptics\Synaptics.exe | 2025-05-16_14e2a2b412520ecadf671372b752ce0e_amadey_darkgate_elex_gcleaner_smoke-loader.exe | ||||||||||||
User: admin Company: Synaptics Integrity Level: HIGH Description: Synaptics Pointing Device Driver Version: 1.0.0.4 Modules
| |||||||||||||||
| 7948 | C:\ProgramData\Synaptics\Synaptics.exe | C:\ProgramData\Synaptics\Synaptics.exe | explorer.exe | ||||||||||||
User: admin Company: Synaptics Integrity Level: MEDIUM Description: Synaptics Pointing Device Driver Exit code: 0 Version: 1.0.0.4 Modules
| |||||||||||||||
Total events
7 879
Read events
7 873
Write events
6
Delete events
0
Modification events
| (PID) Process: | (7608) 2025-05-16_14e2a2b412520ecadf671372b752ce0e_amadey_darkgate_elex_gcleaner_smoke-loader.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer |
| Operation: | write | Name: | SlowContextMenuEntries |
Value: 6024B221EA3A6910A2DC08002B30309D0A010000BD0E0C47735D584D9CEDE91E22E23282770100000114020000000000C0000000000000468D0000006078A409B011A54DAFA526D86198A780390100009AD298B2EDA6DE11BA8CA68E55D895936E000000 | |||
| (PID) Process: | (7608) 2025-05-16_14e2a2b412520ecadf671372b752ce0e_amadey_darkgate_elex_gcleaner_smoke-loader.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Run |
| Operation: | write | Name: | Synaptics Pointing Device Driver |
Value: C:\ProgramData\Synaptics\Synaptics.exe | |||
| (PID) Process: | (7608) 2025-05-16_14e2a2b412520ecadf671372b752ce0e_amadey_darkgate_elex_gcleaner_smoke-loader.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer |
| Operation: | write | Name: | SlowContextMenuEntries |
Value: 6024B221EA3A6910A2DC08002B30309D0A010000BD0E0C47735D584D9CEDE91E22E23282770100000114020000000000C0000000000000468D0000006078A409B011A54DAFA526D86198A7803901000060B81DB4E48ED2119906E49FADC173CAAC000000 | |||
| (PID) Process: | (7860) Synaptics.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (7860) Synaptics.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (7860) Synaptics.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
Executable files
4
Suspicious files
0
Text files
1
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 7608 | 2025-05-16_14e2a2b412520ecadf671372b752ce0e_amadey_darkgate_elex_gcleaner_smoke-loader.exe | C:\Users\admin\Desktop\._cache_2025-05-16_14e2a2b412520ecadf671372b752ce0e_amadey_darkgate_elex_gcleaner_smoke-loader.exe | executable | |
MD5:C2EA8C8DB6F0352A521CE9CF6168A7AD | SHA256:CA4647673219BCF2A5235DBD4B469F65BAC8C9745B43FE4552D781F621FCD0A1 | |||
| 7608 | 2025-05-16_14e2a2b412520ecadf671372b752ce0e_amadey_darkgate_elex_gcleaner_smoke-loader.exe | C:\ProgramData\Synaptics\Synaptics.exe | executable | |
MD5:14E2A2B412520ECADF671372B752CE0E | SHA256:2D748C6CDB0DD6B5BC5F7BDD5D15F50B9D008D0D75CB68DF1E72B8F01084C2EC | |||
| 7608 | 2025-05-16_14e2a2b412520ecadf671372b752ce0e_amadey_darkgate_elex_gcleaner_smoke-loader.exe | C:\ProgramData\Synaptics\RCXDBFA.tmp | executable | |
MD5:E1A4263F782E8961EECEB1857733ACB9 | SHA256:9FBB18A5BED27B6F2C695A783C692AEF6835B810AC0CF1C246F7AC421E7BA84E | |||
| 7860 | Synaptics.exe | C:\Users\admin\AppData\Local\Temp\ktBPSnt.ini | html | |
MD5:E33A59548771698DD6EB12ECE9BFED96 | SHA256:1B875CB0E0305169C3E7593E1E8817055A03909C20350AFC13A56FAF3CA71023 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
10
TCP/UDP connections
59
DNS requests
21
Threats
8
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
7860 | Synaptics.exe | GET | 200 | 69.42.215.252:80 | http://freedns.afraid.org/api/?action=getdyndns&sha=a30fa98efc092684e8d1c5cff797bcc613562978 | unknown | — | — | whitelisted |
8072 | SIHClient.exe | GET | 200 | 23.216.77.6:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut_2010-06-23.crl | unknown | — | — | whitelisted |
8072 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20Update%20Signing%20CA%202.1.crl | unknown | — | — | whitelisted |
8072 | SIHClient.exe | GET | 200 | 23.216.77.6:80 | http://crl.microsoft.com/pki/crl/products/MicTimStaPCA_2010-07-01.crl | unknown | — | — | whitelisted |
8072 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
8072 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Signing%20CA%202.1.crl | unknown | — | — | whitelisted |
8072 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20Update%20Signing%20CA%202.2.crl | unknown | — | — | whitelisted |
8072 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Signing%20CA%202.2.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 23.216.77.6:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 20.190.160.131:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 172.211.123.249:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
— | — | 23.216.77.6:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
6544 | svchost.exe | 20.190.160.131:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 23.35.229.160:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
2104 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
7860 | Synaptics.exe | 69.42.215.252:80 | freedns.afraid.org | AWKNET | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
login.live.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
xred.mooo.com |
| whitelisted |
freedns.afraid.org |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2196 | svchost.exe | Potentially Bad Traffic | ET DYN_DNS DYNAMIC_DNS Query to Abused Domain *.mooo.com |
— | — | A Network Trojan was detected | ET HUNTING Suspicious User-Agent Containing .exe |
— | — | A Network Trojan was detected | ET MALWARE Snake Keylogger Payload Request (GET) |
— | — | A Network Trojan was detected | ET HUNTING Suspicious User-Agent Containing .exe |
— | — | A Network Trojan was detected | ET HUNTING Suspicious User-Agent Containing .exe |
— | — | A Network Trojan was detected | ET HUNTING Suspicious User-Agent Containing .exe |
— | — | A Network Trojan was detected | ET HUNTING Suspicious User-Agent Containing .exe |
— | — | A Network Trojan was detected | ET HUNTING Suspicious User-Agent Containing .exe |