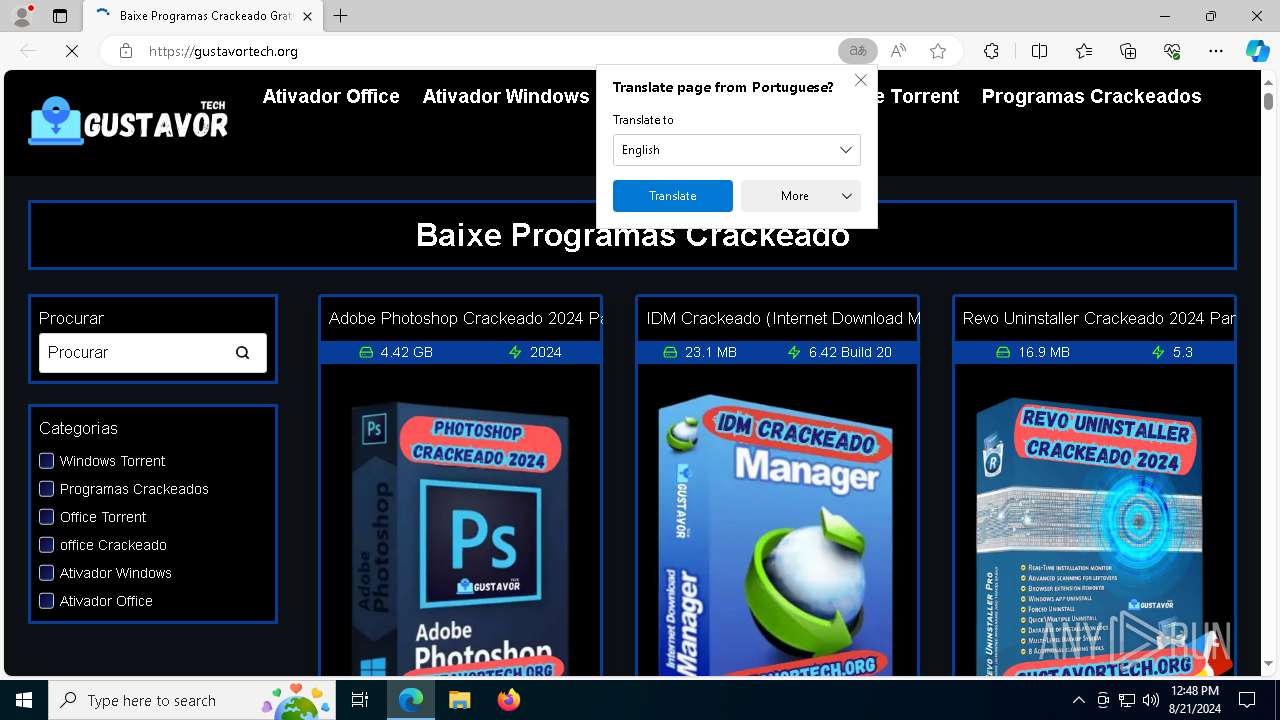
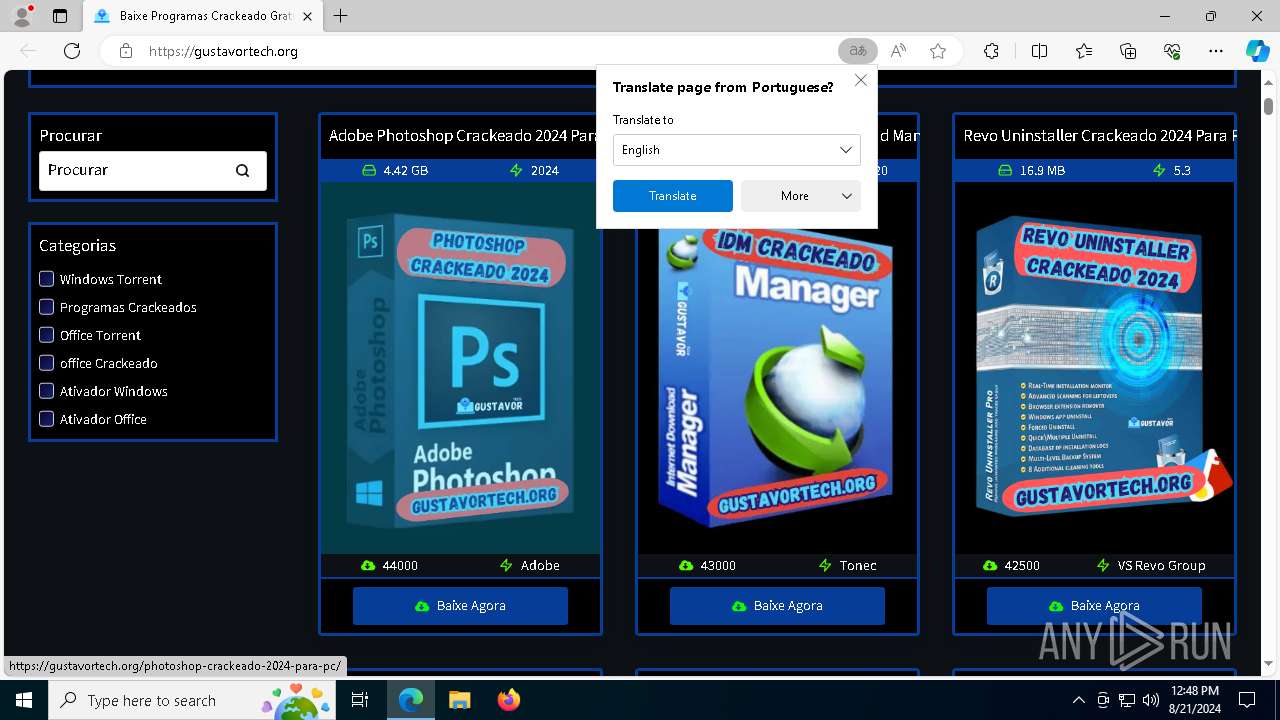
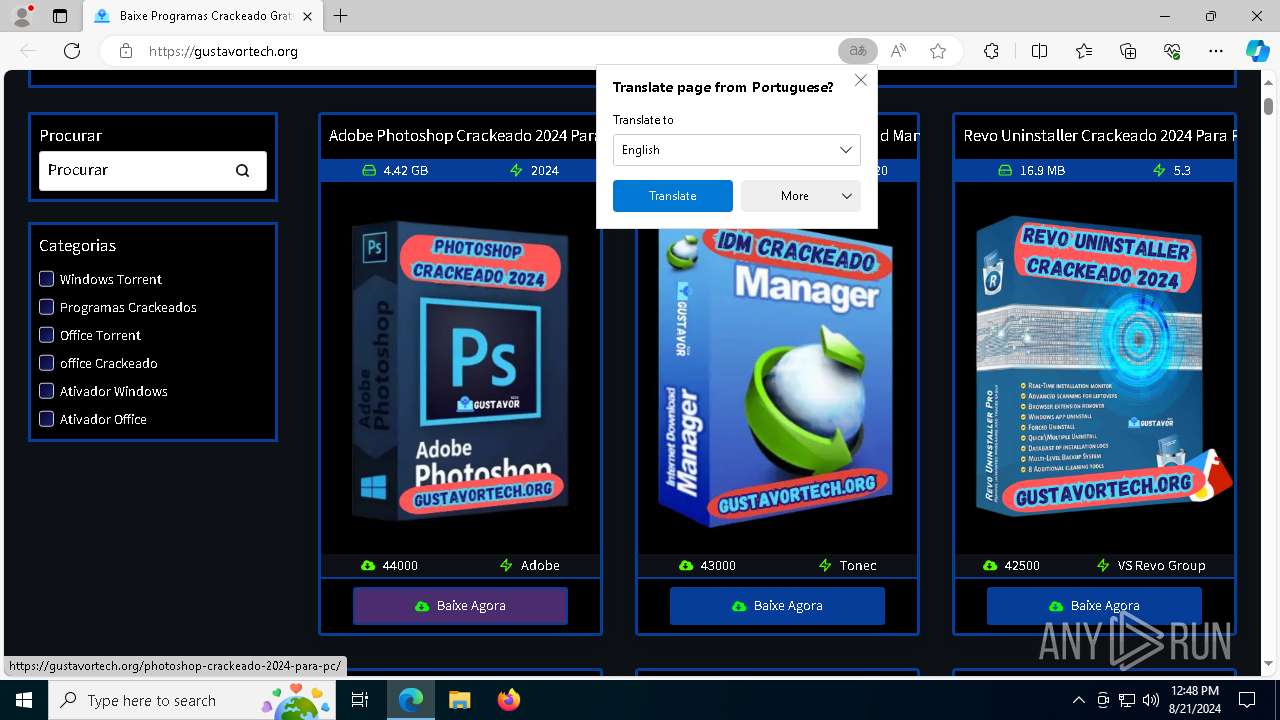
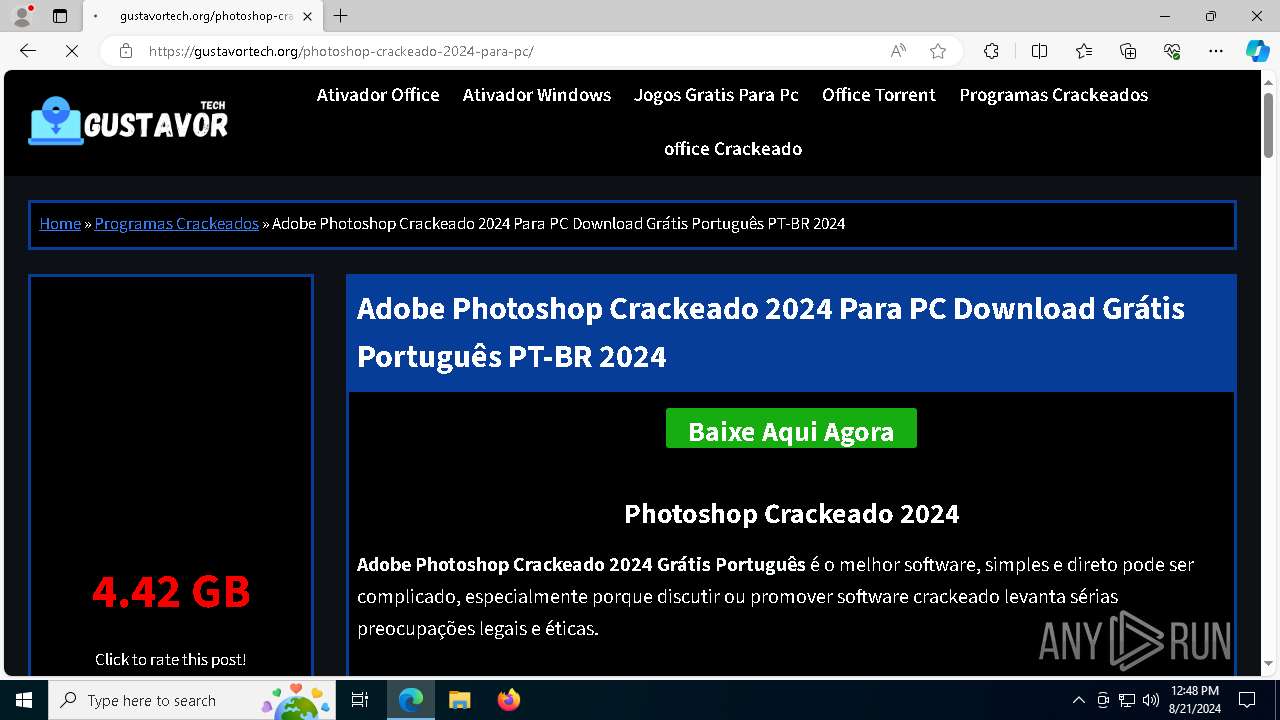
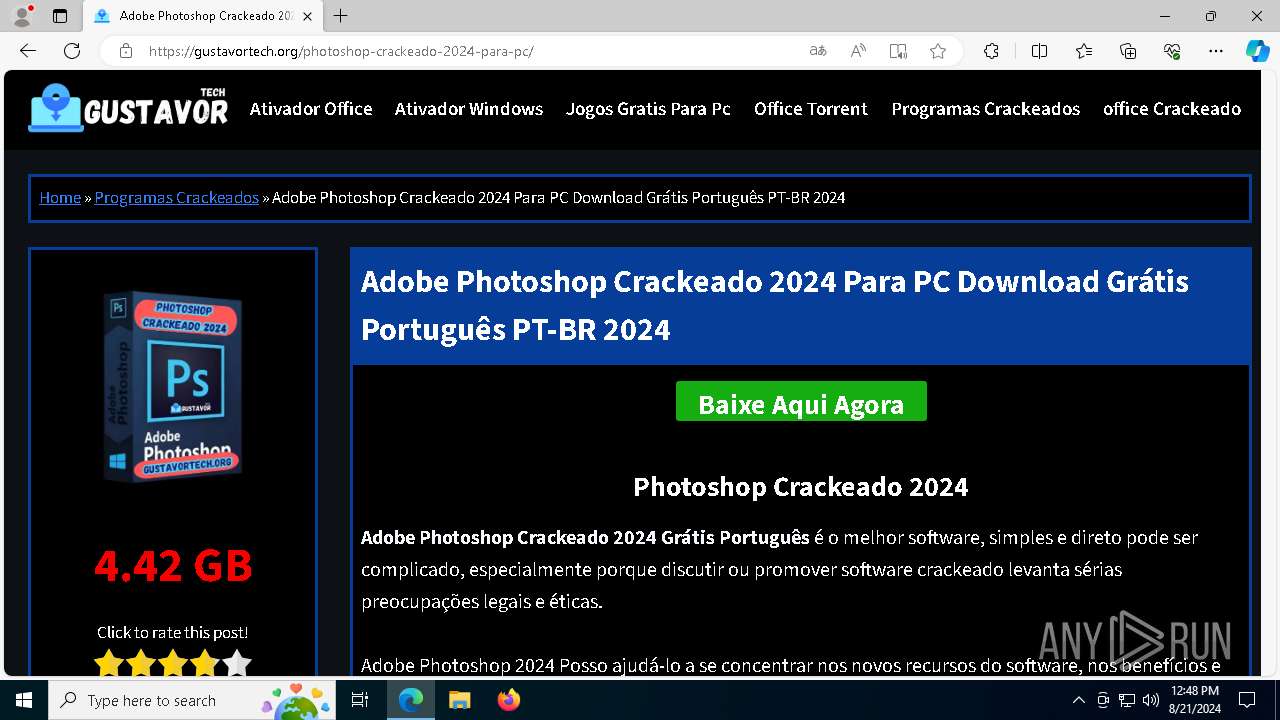
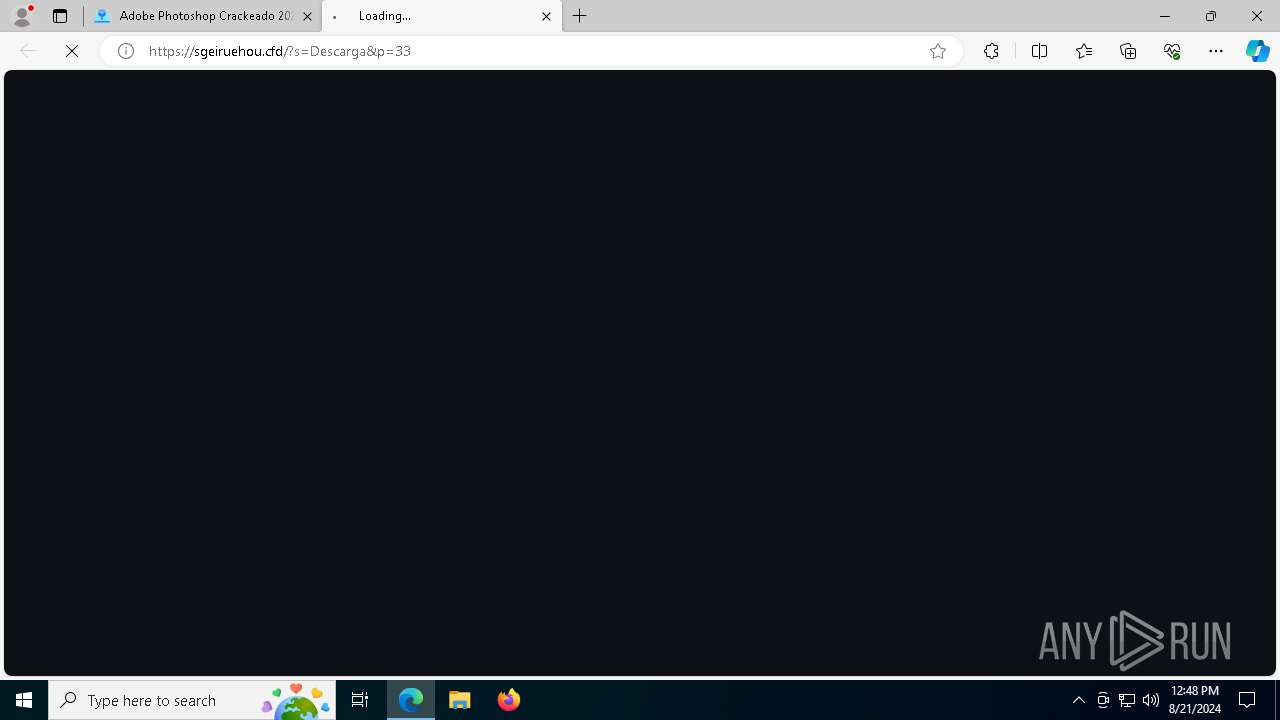
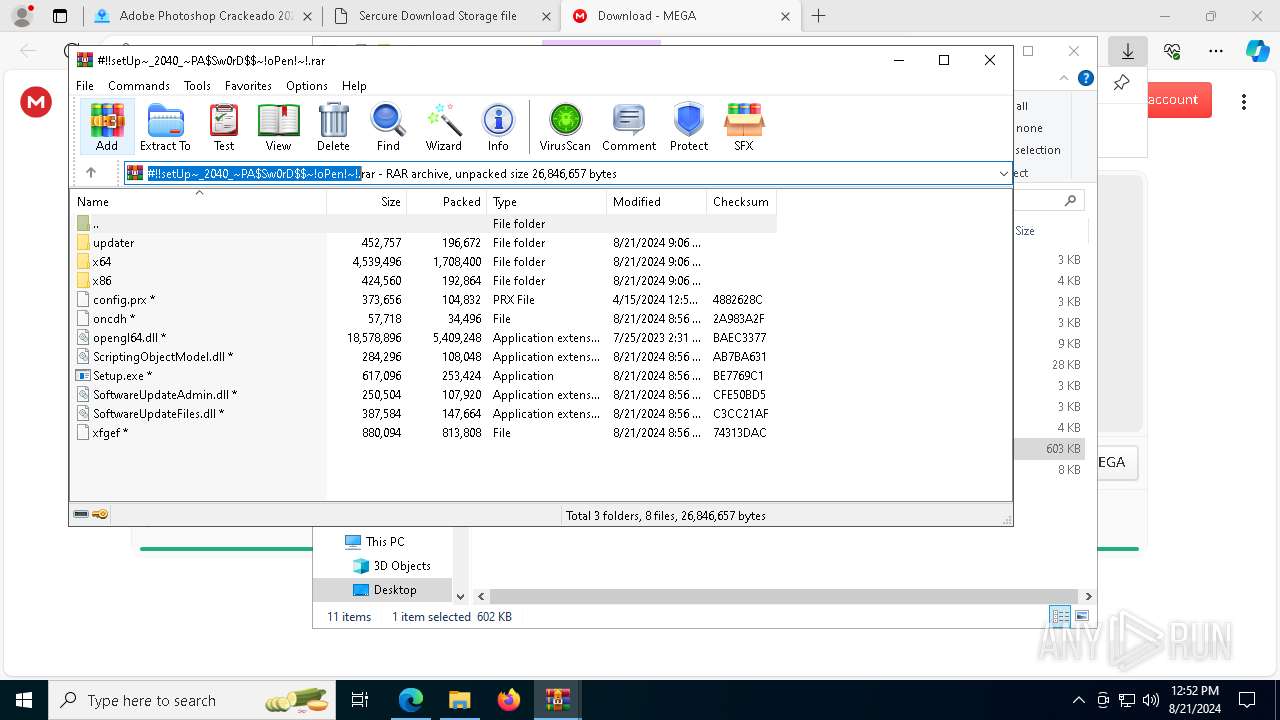
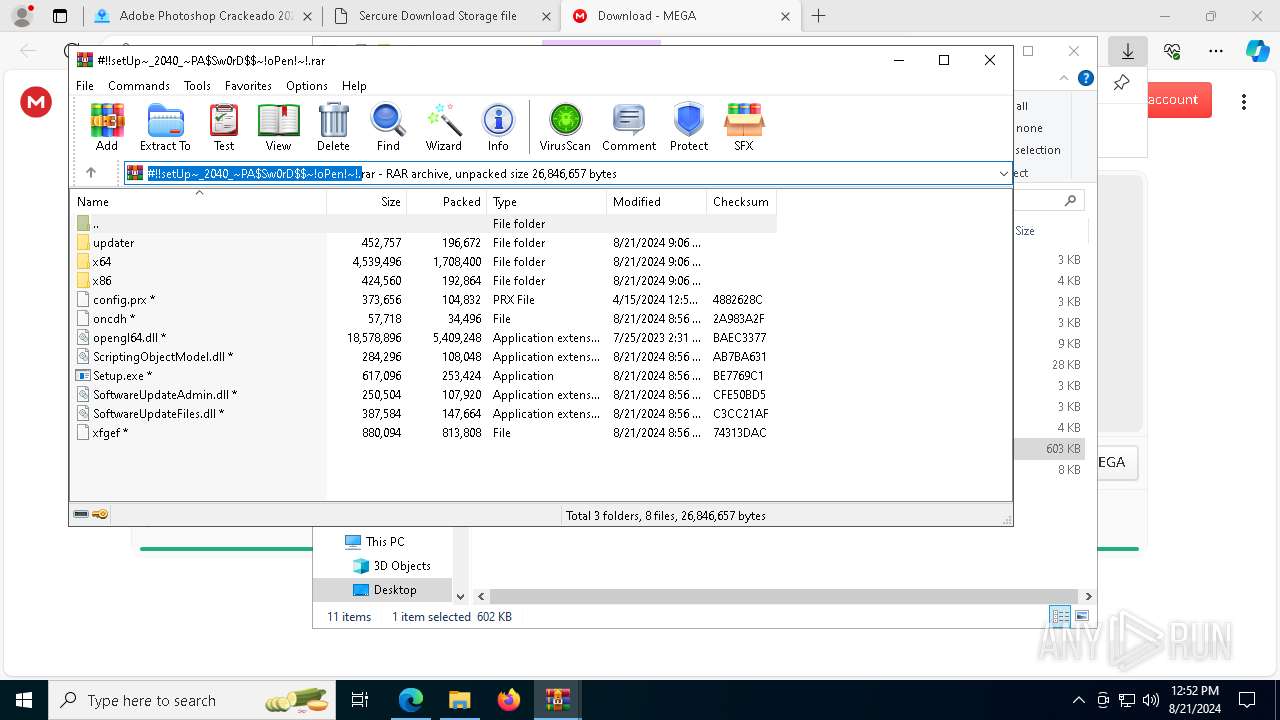
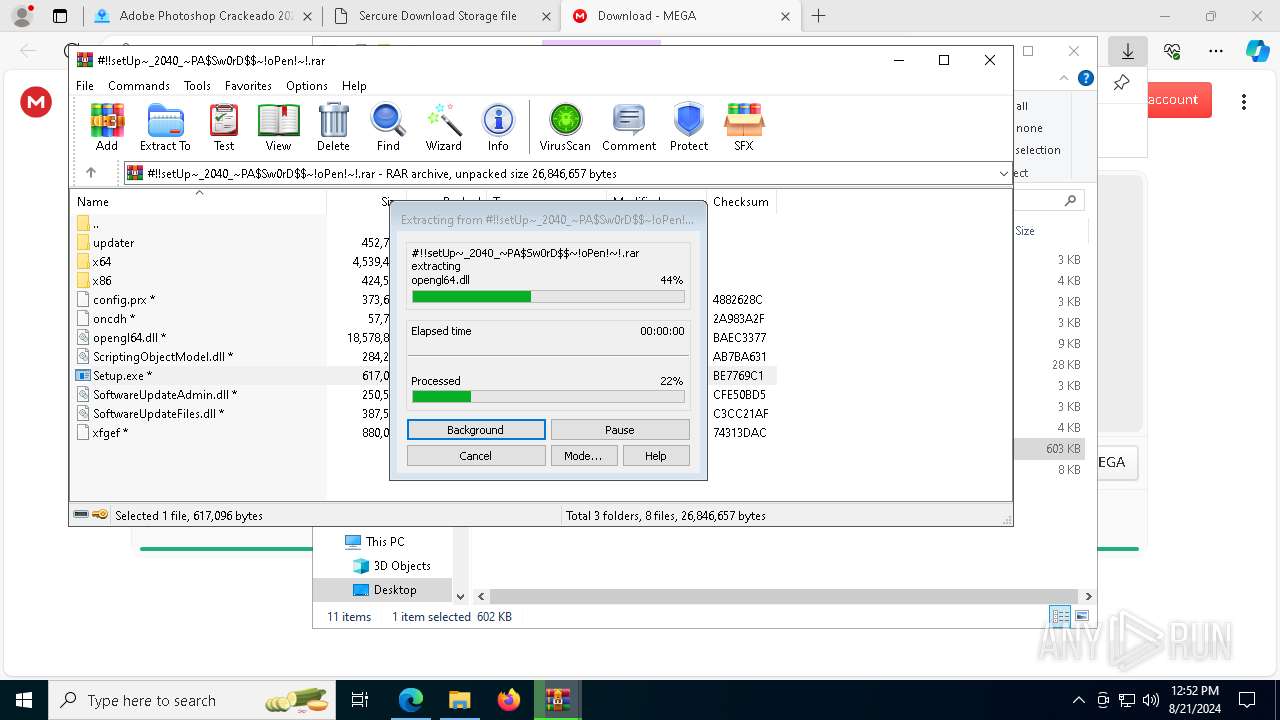
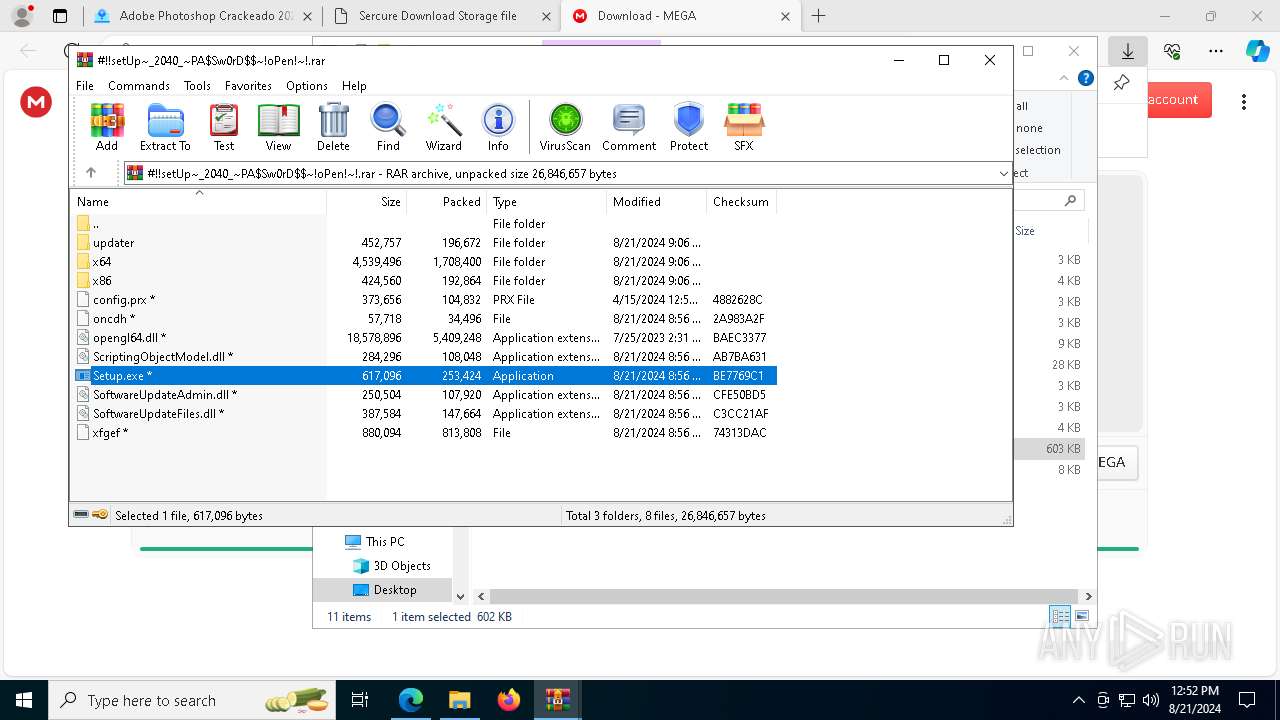
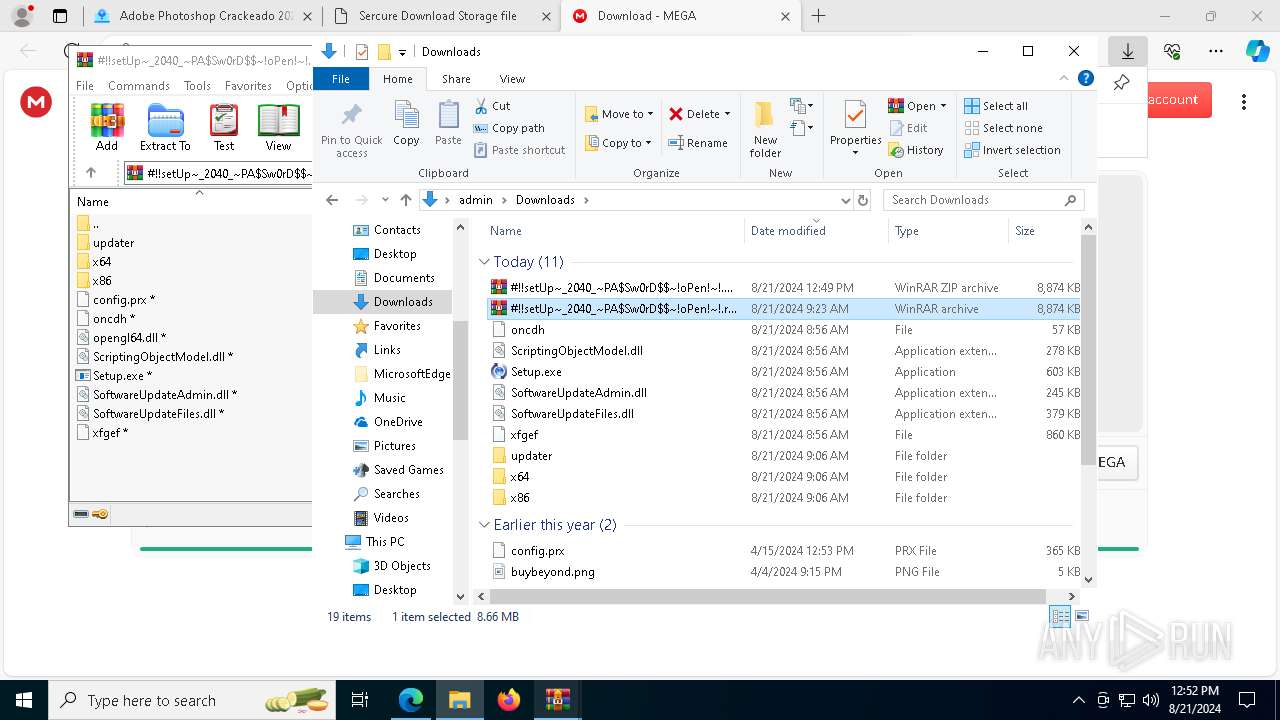
| URL: | gustavortech.org |
| Full analysis: | https://app.any.run/tasks/cfe0ea2a-4754-410d-a999-c47cebab4a39 |
| Verdict: | Malicious activity |
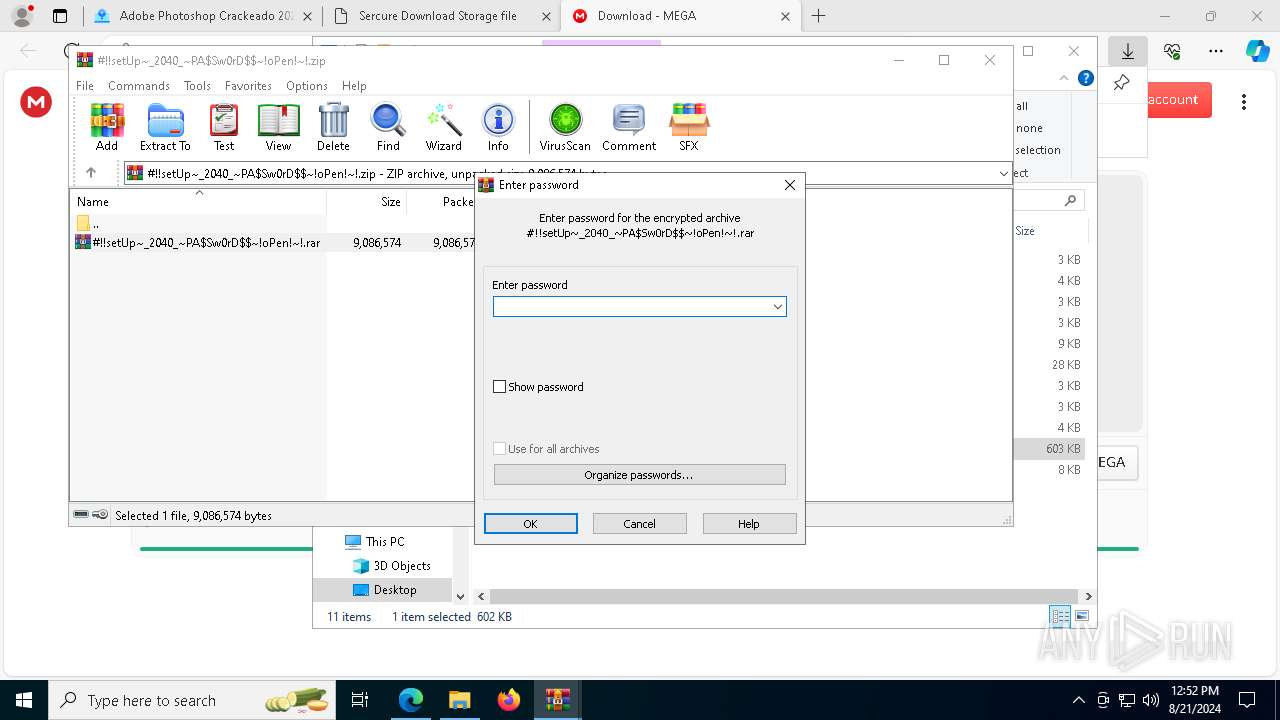
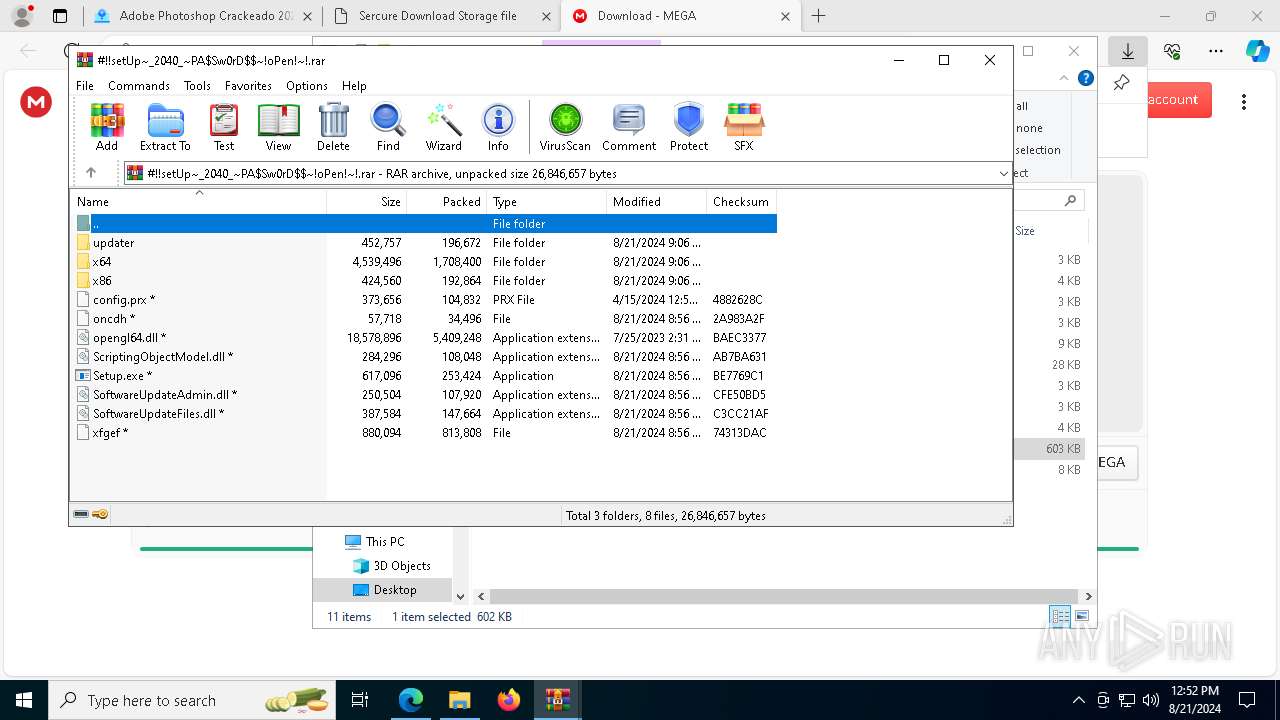
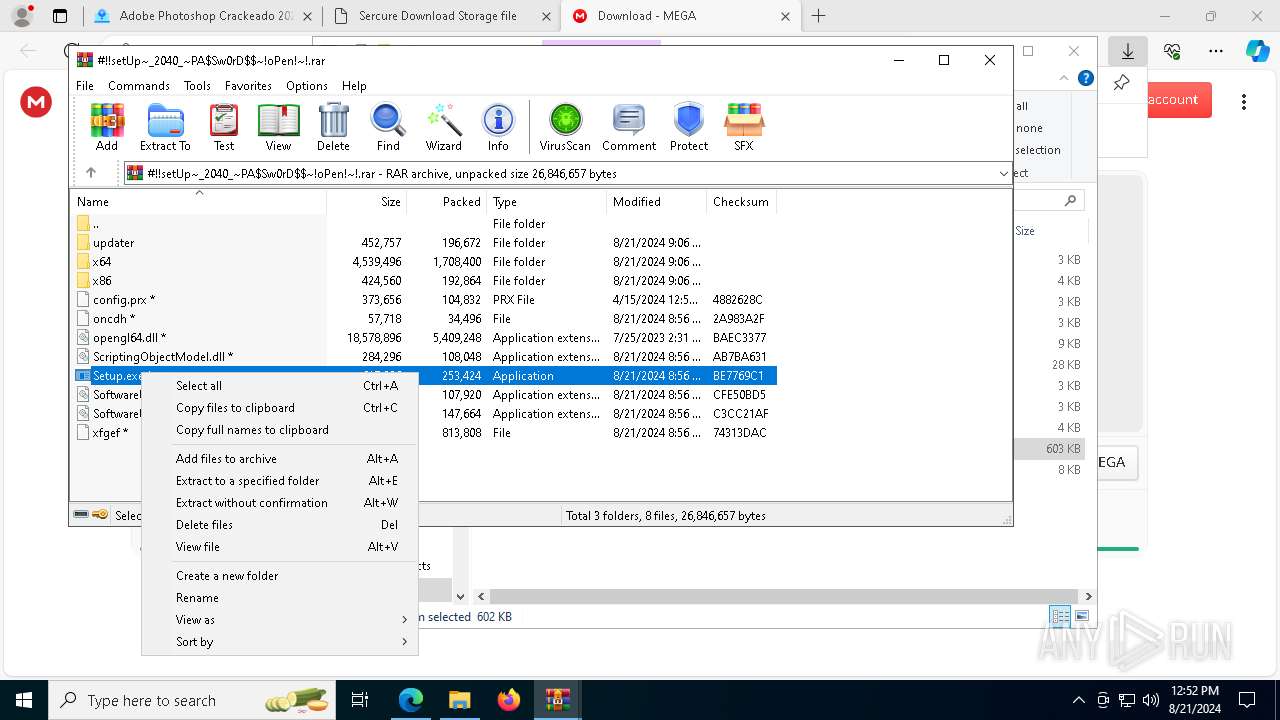
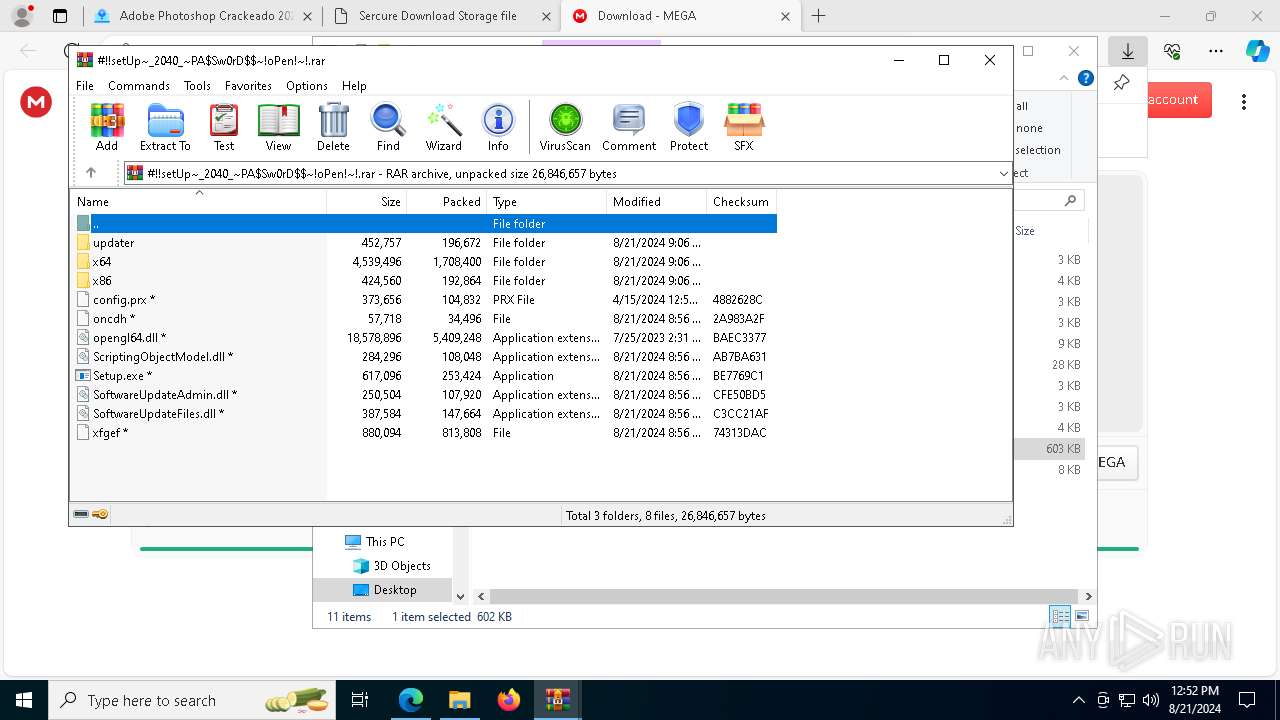
| Threats: | Amadey is a formidable Windows infostealer threat, characterized by its persistence mechanisms, modular design, and ability to execute various malicious tasks. |
| Analysis date: | August 21, 2024, 12:48:40 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MD5: | 09C960D74773A82DA7CF9599CACA8B3D |
| SHA1: | CC680CAFB69A617BA80A7E45973493FCA40A0801 |
| SHA256: | 2D3E8C152683FE5E1828C67F066FC393577992CAB27A89C1351AF4454D0BBD0A |
| SSDEEP: | 3:aETKXm6:rMm6 |
MALICIOUS
LUMMA has been detected (YARA)
- SearchIndexer.exe (PID: 2232)
Changes powershell execution policy (Bypass)
- SearchIndexer.exe (PID: 2232)
Bypass execution policy to execute commands
- powershell.exe (PID: 5720)
HIJACKLOADER has been detected (YARA)
- AOQKEXOGCGBH0OJ1SK3EAMN.exe (PID: 4248)
Probably downloads file via BitsAdmin (POWERSHELL)
- powershell.exe (PID: 5720)
AMADEY has been detected (SURICATA)
- explorer.exe (PID: 2728)
AMADEY has been detected (YARA)
- explorer.exe (PID: 2728)
Connects to the CnC server
- explorer.exe (PID: 2728)
SUSPICIOUS
Reads security settings of Internet Explorer
- WinRAR.exe (PID: 7456)
- WinRAR.exe (PID: 7756)
- U3DWB93Z76DBJUJ512IX.exe (PID: 3184)
- WinRAR.exe (PID: 4692)
Potential Corporate Privacy Violation
- msedge.exe (PID: 6848)
Application launched itself
- WinRAR.exe (PID: 7456)
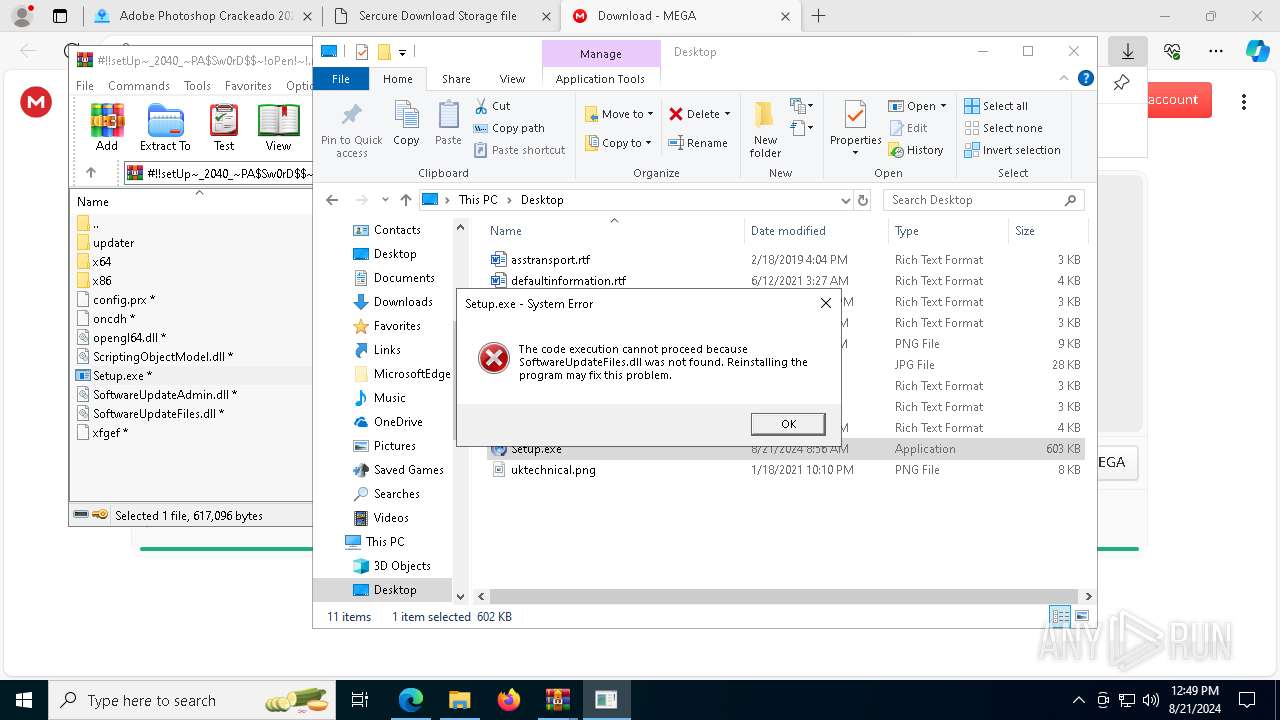
Process drops legitimate windows executable
- WinRAR.exe (PID: 7756)
- WinRAR.exe (PID: 4692)
- WinRAR.exe (PID: 6288)
Drops the executable file immediately after the start
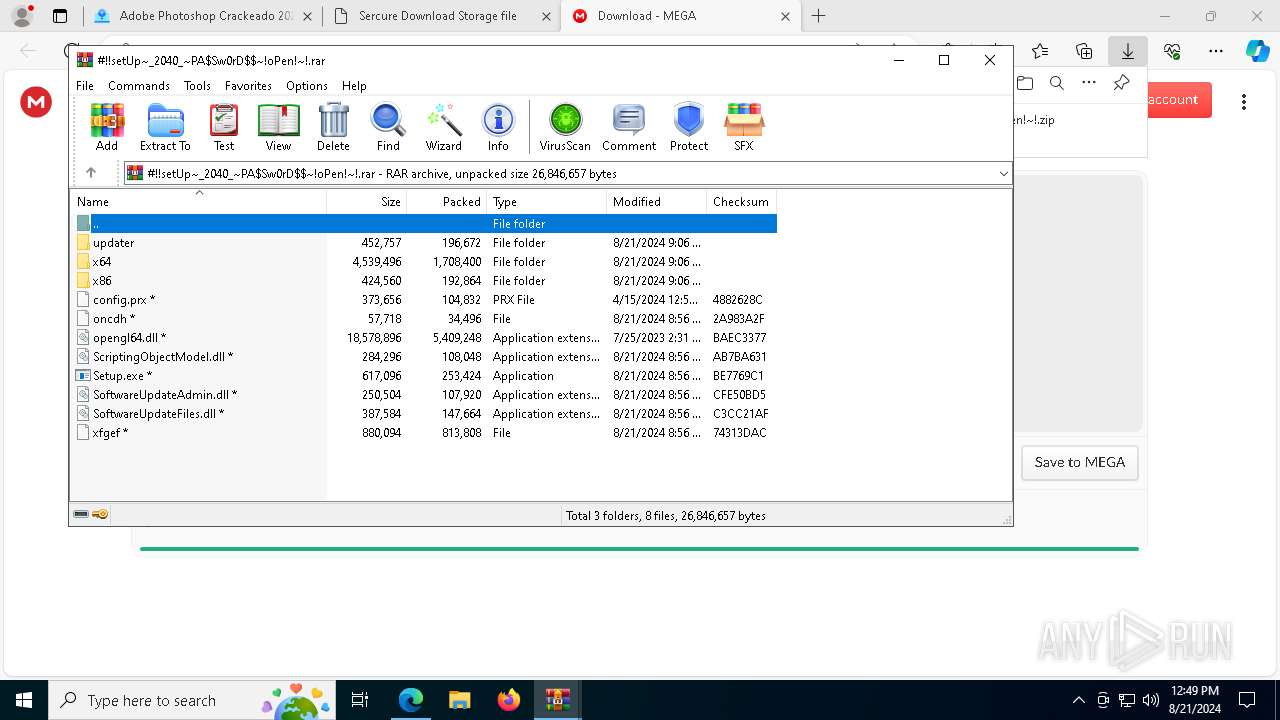
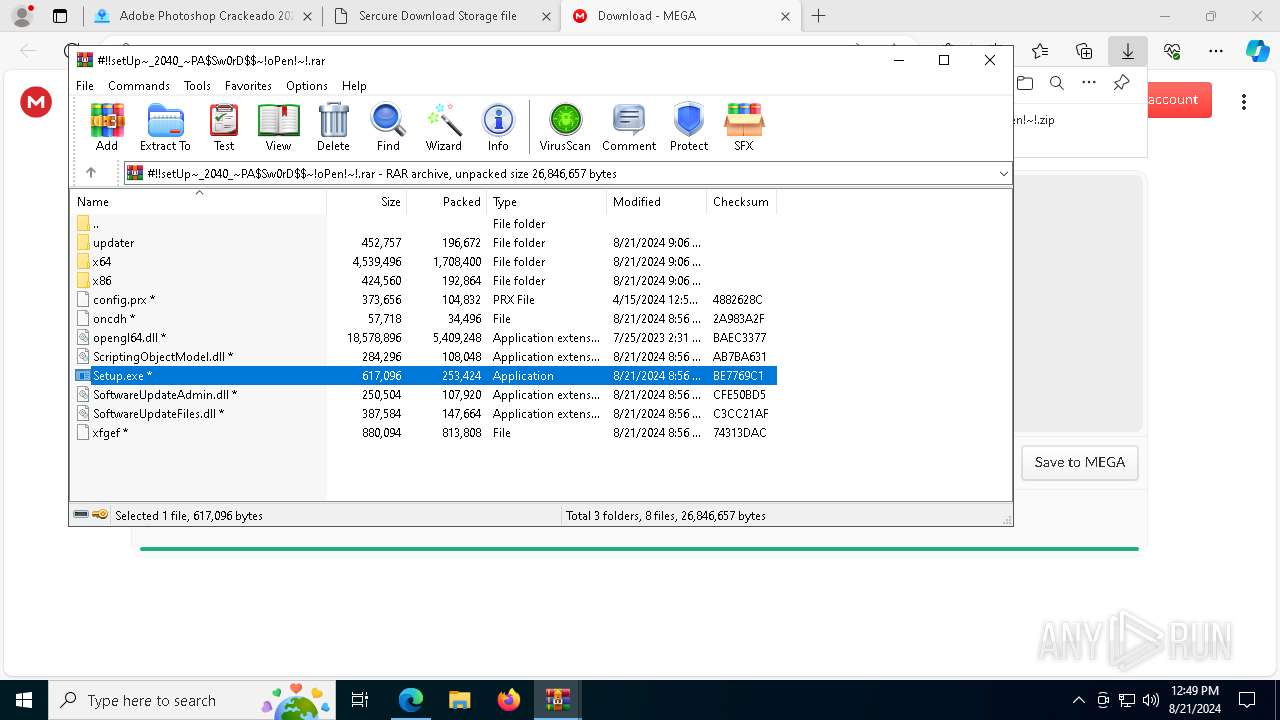
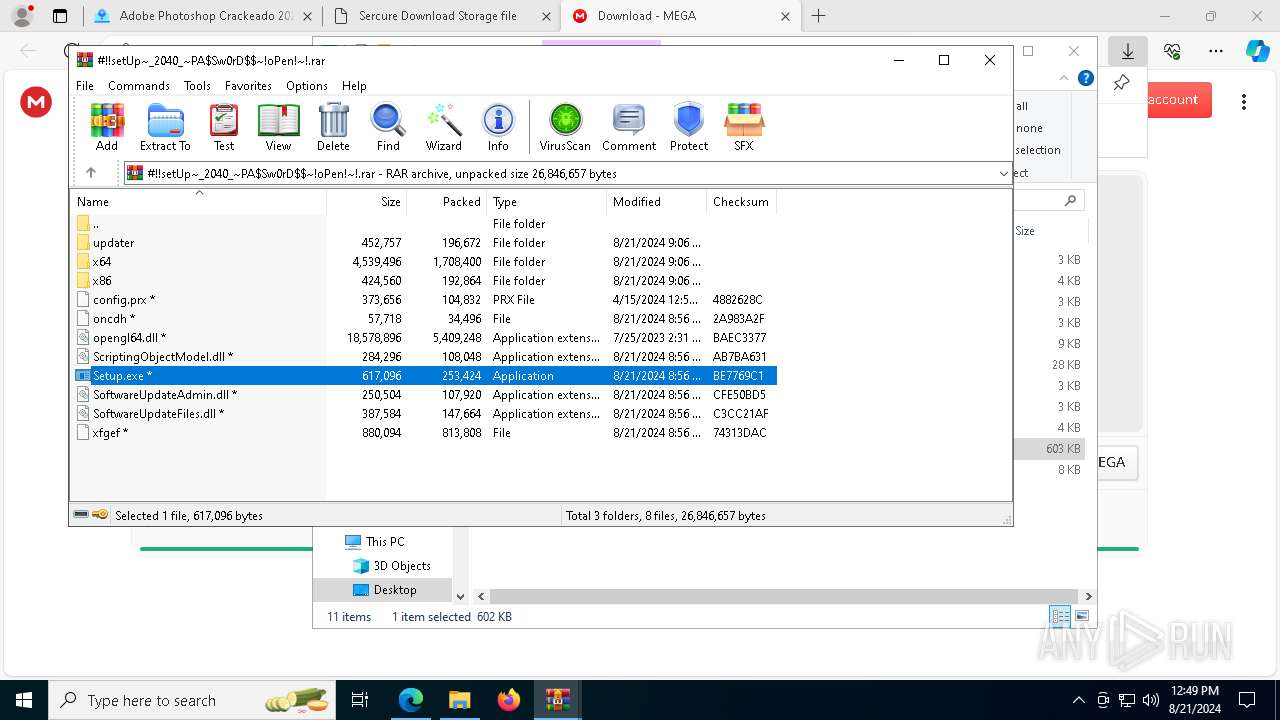
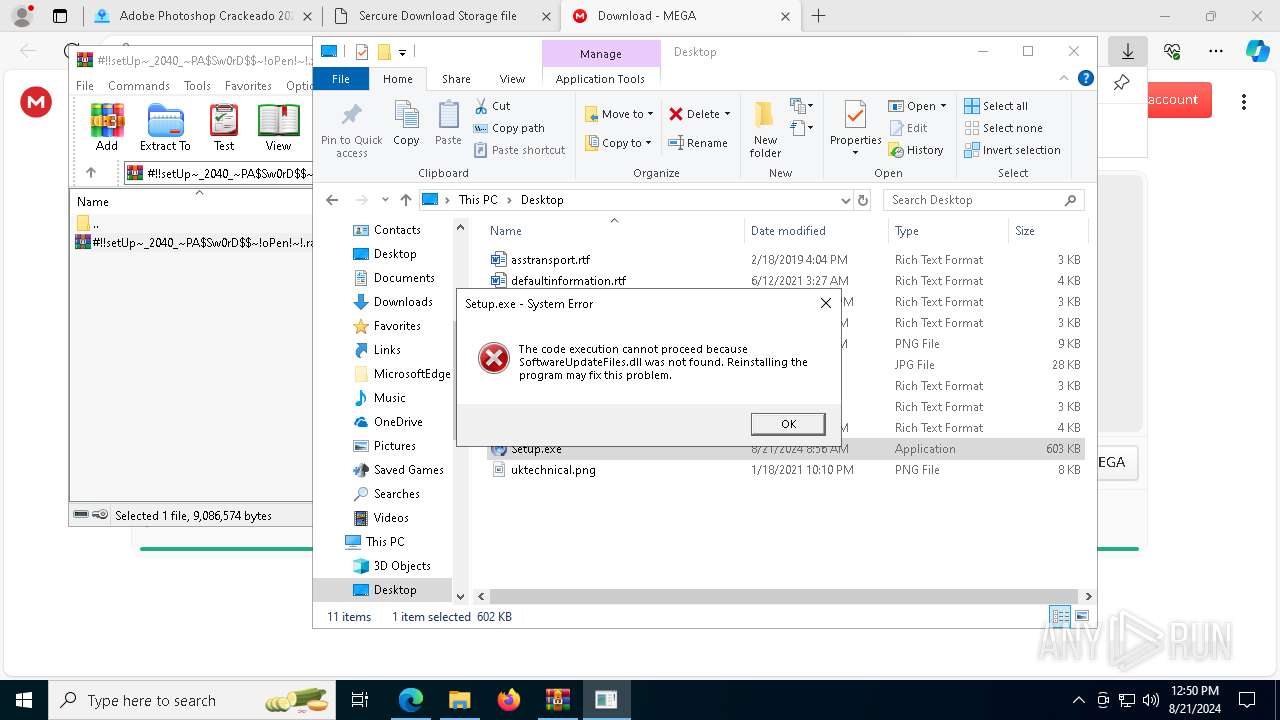
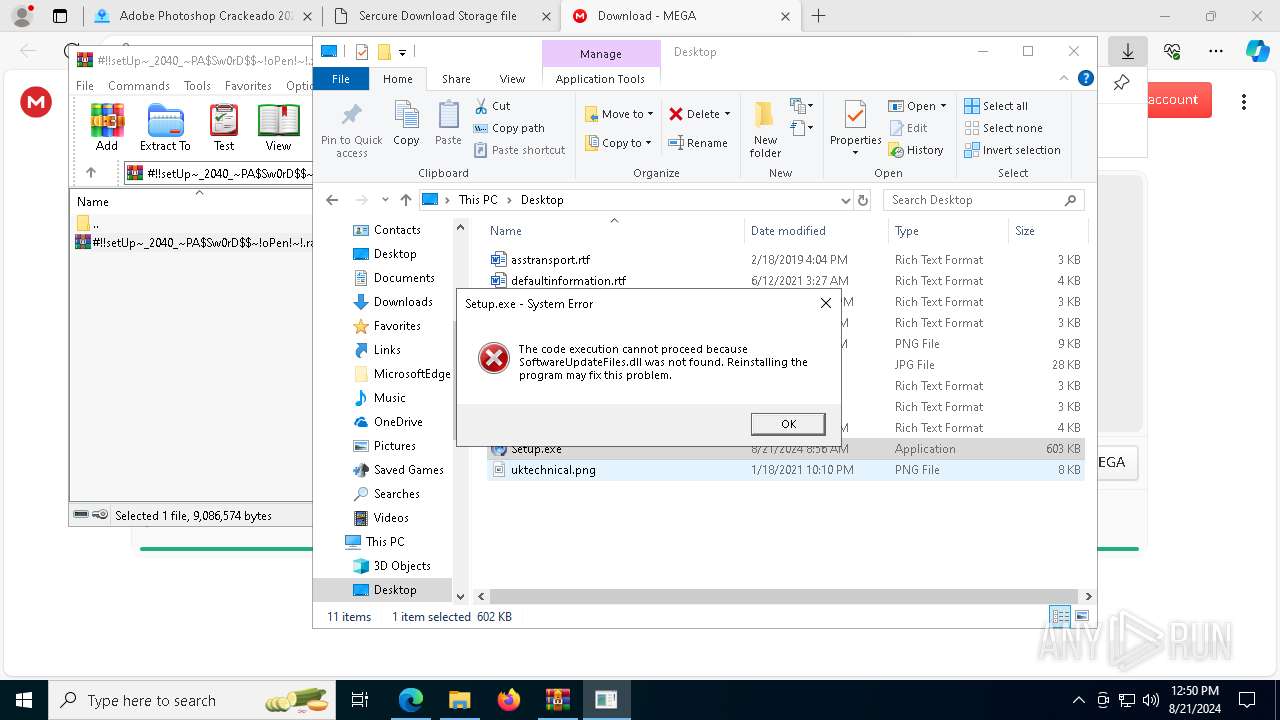
- Setup.exe (PID: 6112)
Executable content was dropped or overwritten
- SearchIndexer.exe (PID: 2232)
- Setup.exe (PID: 6112)
Searches for installed software
- SearchIndexer.exe (PID: 2232)
Reads the date of Windows installation
- U3DWB93Z76DBJUJ512IX.exe (PID: 3184)
Starts CMD.EXE for commands execution
- U3DWB93Z76DBJUJ512IX.exe (PID: 3184)
The executable file from the user directory is run by the CMD process
- U3DWB93Z76DBJUJ512IX.exe (PID: 888)
Starts POWERSHELL.EXE for commands execution
- SearchIndexer.exe (PID: 2232)
Gets or sets the security protocol (POWERSHELL)
- powershell.exe (PID: 5720)
Extracts files to a directory (POWERSHELL)
- powershell.exe (PID: 5720)
Starts application with an unusual extension
- Setup.exe (PID: 6112)
- Setup.exe (PID: 5612)
The process executes via Task Scheduler
- ArmourySocketServer.exe (PID: 892)
Contacting a server suspected of hosting an CnC
- explorer.exe (PID: 2728)
Connects to unusual port
- WWAHost.exe (PID: 6224)
The process executes Powershell scripts
- SearchIndexer.exe (PID: 2232)
INFO
Reads Microsoft Office registry keys
- msedge.exe (PID: 6944)
Reads Environment values
- identity_helper.exe (PID: 6176)
- AOQKEXOGCGBH0OJ1SK3EAMN.exe (PID: 4248)
Reads the computer name
- identity_helper.exe (PID: 6176)
- StrCmp.exe (PID: 448)
- more.com (PID: 300)
- U3DWB93Z76DBJUJ512IX.exe (PID: 3184)
- AOQKEXOGCGBH0OJ1SK3EAMN.exe (PID: 4248)
- U3DWB93Z76DBJUJ512IX.exe (PID: 888)
- Setup.exe (PID: 6112)
- ArmourySocketServer.exe (PID: 892)
- Setup.exe (PID: 5612)
- more.com (PID: 6148)
Checks supported languages
- identity_helper.exe (PID: 6176)
- Setup.exe (PID: 6112)
- StrCmp.exe (PID: 448)
- more.com (PID: 300)
- U3DWB93Z76DBJUJ512IX.exe (PID: 3184)
- Setup.exe (PID: 1744)
- U3DWB93Z76DBJUJ512IX.exe (PID: 888)
- AOQKEXOGCGBH0OJ1SK3EAMN.exe (PID: 4248)
- Setup.exe (PID: 5128)
- ArmourySocketServer.exe (PID: 892)
- Setup.exe (PID: 5612)
- more.com (PID: 6148)
The process uses the downloaded file
- msedge.exe (PID: 6944)
- msedge.exe (PID: 5984)
- WinRAR.exe (PID: 7456)
- WinRAR.exe (PID: 4048)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 7756)
- WinRAR.exe (PID: 4692)
- WinRAR.exe (PID: 6288)
Manual execution by a user
- Setup.exe (PID: 5128)
- mspaint.exe (PID: 4284)
- Setup.exe (PID: 1744)
- WINWORD.EXE (PID: 3880)
- WINWORD.EXE (PID: 4816)
- WinRAR.exe (PID: 6288)
- WinRAR.exe (PID: 4048)
Create files in a temporary directory
- Setup.exe (PID: 6112)
- more.com (PID: 300)
- SearchIndexer.exe (PID: 2232)
- U3DWB93Z76DBJUJ512IX.exe (PID: 3184)
- U3DWB93Z76DBJUJ512IX.exe (PID: 888)
- AOQKEXOGCGBH0OJ1SK3EAMN.exe (PID: 4248)
- comp.exe (PID: 448)
- ArmourySocketServer.exe (PID: 892)
- comp.exe (PID: 3692)
- comp.exe (PID: 7668)
- WWAHost.exe (PID: 6224)
- WWAHost.exe (PID: 1644)
- Setup.exe (PID: 5612)
- more.com (PID: 6148)
Reads the software policy settings
- SearchIndexer.exe (PID: 2232)
Application launched itself
- msedge.exe (PID: 6944)
Process checks computer location settings
- U3DWB93Z76DBJUJ512IX.exe (PID: 3184)
Creates files or folders in the user directory
- Setup.exe (PID: 6112)
Checks if a key exists in the options dictionary (POWERSHELL)
- powershell.exe (PID: 5720)
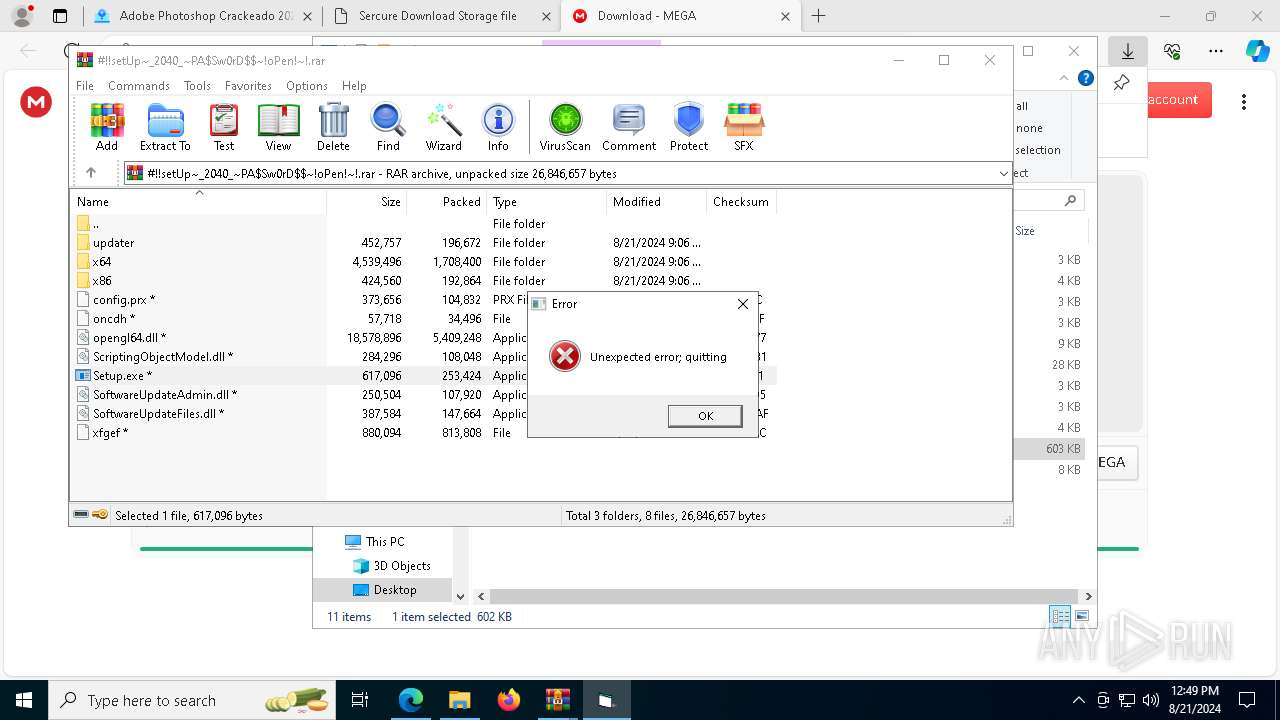
Script raised an exception (POWERSHELL)
- powershell.exe (PID: 5720)
Reads security settings of Internet Explorer
- explorer.exe (PID: 2728)
Checks proxy server information
- explorer.exe (PID: 2728)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Lumma
(PID) Process(2232) SearchIndexer.exe
C2 (9)consciousourwi.shop
interactiedovspm.shop
cagedwifedsozm.shop
charecteristicdxp.shop
muuudsaowis.shop
potentioallykeos.shop
southedhiscuso.shop
deicedosmzj.shop
weiggheticulop.shop
Amadey
(PID) Process(2728) explorer.exe
C2filetip-resourcecloud.com
Strings (123)SOFTWARE\Microsoft\Windows\CurrentVersion\Run
dll
random
filetip-resourcecloud3.com
cmd
kernel32.dll
Rem
WinDefender
e1
-executionpolicy remotesigned -File "
rb
CurrentBuild
"taskkill /f /im "
<c>
:::
Content-Disposition: form-data; name="data"; filename="
Comodo
-%lu
os:
ESET
GET
https://
360TotalSecurity
cred.dll|clip.dll|
"
Content-Type: application/octet-stream
DefaultSettings.YResolution
d1
/quiet
Startup
rundll32
ComputerName
exe
rundll32.exe
bi:
\0000
/h9fmdW5/index.php
ar:
Programs
pc:
|
SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\Shell Folders
=
/h9fmdW6/index.php
&&
" && ren
e2
\App
&unit=
--
un:
vs:
clip.dll
AVG
ProgramData\
Panda Security
shell32.dll
Main
%USERPROFILE%
dm:
0123456789
&& Exit"
\
wb
/Plugins/
av:
Avira
/k
http://
POST
Bitdefender
" && timeout 1 && del
sd:
+++
SOFTWARE\Microsoft\Windows NT\CurrentVersion
GetNativeSystemInfo
st=s
------
Hkbsse.exe
Sophos
filetip-resourcecloud2.com
#
S-%lu-
/h9fmdW7/index.php
Content-Type: application/x-www-form-urlencoded
zip
2016
msi
Kaspersky Lab
"
cred.dll
?scr=1
<d>
-unicode-
VideoID
filetip-resourcecloud.com
4aaa838562
r=
abcdefghijklmnopqrstuvwxyz0123456789-_
2019
cmd /C RMDIR /s/q
------
SOFTWARE\Microsoft\Windows\CurrentVersion\RunOnce
SYSTEM\CurrentControlSet\Control\ComputerName\ComputerName
og:
2022
%-lu
Content-Type: multipart/form-data; boundary=----
4.41
shutdown -s -t 0
ProductName
lv:
id:
Powershell.exe
DefaultSettings.XResolution
SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\User Shell Folders
AVAST Software
Doctor Web
Norton
.jpg
e0
ps1
SYSTEM\ControlSet001\Services\BasicDisplay\Video
SYSTEM\CurrentControlSet\Control\UnitedVideo\CONTROL\VIDEO\
Total processes
238
Monitored processes
98
Malicious processes
12
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 300 | C:\WINDOWS\SysWOW64\more.com | C:\Windows\SysWOW64\more.com | — | Setup.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: More Utility Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 448 | C:\Users\admin\AppData\Roaming\Cqfquickv1\ACMVNMQFDBZCIGXBYL\StrCmp.exe | C:\Users\admin\AppData\Roaming\Cqfquickv1\ACMVNMQFDBZCIGXBYL\StrCmp.exe | — | Setup.exe | |||||||||||
User: admin Company: aaa Integrity Level: MEDIUM Exit code: 0 Version: 1.00 Modules
| |||||||||||||||
| 448 | C:\WINDOWS\SysWOW64\comp.exe | C:\Windows\SysWOW64\comp.exe | — | U3DWB93Z76DBJUJ512IX.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: File Compare Utility Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 888 | C:\Users\admin\AppData\Local\Temp\U3DWB93Z76DBJUJ512IX.exe | C:\Users\admin\AppData\Local\Temp\U3DWB93Z76DBJUJ512IX.exe | — | cmd.exe | |||||||||||
User: admin Company: iTop Inc. Integrity Level: HIGH Description: iTop Easy Desktop Exit code: 1 Version: 1.0.0.5 Modules
| |||||||||||||||
| 892 | "C:\Users\admin\AppData\Roaming\ArmouryDevice\ArmourySocketServer.exe" | C:\Users\admin\AppData\Roaming\ArmouryDevice\ArmourySocketServer.exe | — | svchost.exe | |||||||||||
User: admin Company: iTop Inc. Integrity Level: HIGH Description: iTop Easy Desktop Exit code: 1 Version: 1.0.0.5 Modules
| |||||||||||||||
| 1492 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | comp.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1616 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=8080 --field-trial-handle=2388,i,7035916672007527728,13858201751926261423,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 1644 | C:\WINDOWS\SysWOW64\WWAHost.exe | C:\Windows\SysWOW64\WWAHost.exe | — | comp.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft WWA Host Exit code: 1 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
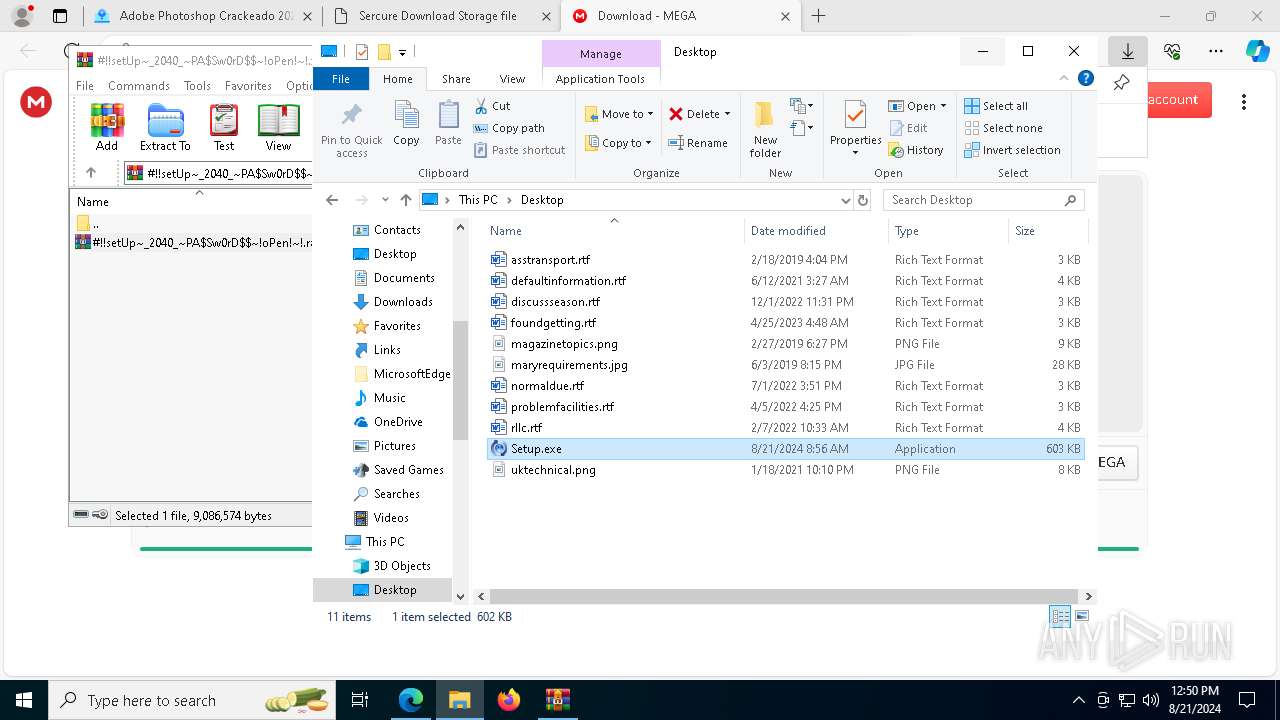
| 1744 | "C:\Users\admin\Desktop\Setup.exe" | C:\Users\admin\Desktop\Setup.exe | — | explorer.exe | |||||||||||
User: admin Company: Apple Inc. Integrity Level: MEDIUM Description: Apple Software Update Exit code: 3221225781 Version: 2.7.0.3 Modules
| |||||||||||||||
| 1744 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | comp.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
70 562
Read events
68 936
Write events
1 496
Delete events
130
Modification events
| (PID) Process: | (6944) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (6944) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
| (PID) Process: | (6944) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\ThirdParty |
| Operation: | write | Name: | StatusCodes |
Value: | |||
| (PID) Process: | (6944) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\ThirdParty |
| Operation: | write | Name: | StatusCodes |
Value: 01000000 | |||
| (PID) Process: | (6944) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | state |
Value: 1 | |||
| (PID) Process: | (6944) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\EdgeUpdate\ClientState\{56EB18F8-B008-4CBD-B6D2-8C97FE7E9062} |
| Operation: | write | Name: | dr |
Value: 1 | |||
| (PID) Process: | (6944) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\StabilityMetrics |
| Operation: | write | Name: | user_experience_metrics.stability.exited_cleanly |
Value: 0 | |||
| (PID) Process: | (6944) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge |
| Operation: | write | Name: | UsageStatsInSample |
Value: 1 | |||
| (PID) Process: | (6944) msedge.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\EdgeUpdate\ClientStateMedium\{56EB18F8-B008-4CBD-B6D2-8C97FE7E9062}\LastWasDefault |
| Operation: | write | Name: | S-1-5-21-1693682860-607145093-2874071422-1001 |
Value: D21E0E3FC77E2F00 | |||
| (PID) Process: | (6944) msedge.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\EdgeUpdate\ClientStateMedium\{56EB18F8-B008-4CBD-B6D2-8C97FE7E9062} |
| Operation: | write | Name: | usagestats |
Value: 0 | |||
Executable files
120
Suspicious files
489
Text files
287
Unknown types
6
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6944 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\parcel_tracking_db\LOG.old~RF11dfce.TMP | — | |
MD5:— | SHA256:— | |||
| 6944 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\parcel_tracking_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 6944 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\commerce_subscription_db\LOG.old~RF11df8f.TMP | — | |
MD5:— | SHA256:— | |||
| 6944 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\PersistentOriginTrials\LOG.old~RF11dfce.TMP | — | |
MD5:— | SHA256:— | |||
| 6944 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\commerce_subscription_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 6944 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\discounts_db\LOG.old~RF11df8f.TMP | — | |
MD5:— | SHA256:— | |||
| 6944 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\PersistentOriginTrials\LOG.old | — | |
MD5:— | SHA256:— | |||
| 6944 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\discounts_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 6944 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\EdgePushStorageWithConnectTokenAndKey\LOG.old~RF11dfdd.TMP | — | |
MD5:— | SHA256:— | |||
| 6944 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\EdgePushStorageWithConnectTokenAndKey\LOG.old | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
56
TCP/UDP connections
239
DNS requests
154
Threats
65
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
788 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
5336 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
6656 | svchost.exe | GET | 206 | 199.232.214.172:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/062b65bc-b6a4-4f5a-8413-7218292237fe?P1=1724803633&P2=404&P3=2&P4=PFzv3TL7O9NKuqK%2fwzoSpowLllKOnb9km34FAbXqxy8eoFi%2bxl7q1jecThdMqO7rvBxa5G7xzyEXgzc7ZL3CMA%3d%3d | unknown | — | — | whitelisted |
1432 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
5336 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
7672 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
6656 | svchost.exe | HEAD | 200 | 199.232.214.172:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/062b65bc-b6a4-4f5a-8413-7218292237fe?P1=1724803633&P2=404&P3=2&P4=PFzv3TL7O9NKuqK%2fwzoSpowLllKOnb9km34FAbXqxy8eoFi%2bxl7q1jecThdMqO7rvBxa5G7xzyEXgzc7ZL3CMA%3d%3d | unknown | — | — | whitelisted |
5336 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEApDqVCbATUviZV57HIIulA%3D | unknown | — | — | whitelisted |
6656 | svchost.exe | GET | 206 | 199.232.214.172:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/062b65bc-b6a4-4f5a-8413-7218292237fe?P1=1724803633&P2=404&P3=2&P4=PFzv3TL7O9NKuqK%2fwzoSpowLllKOnb9km34FAbXqxy8eoFi%2bxl7q1jecThdMqO7rvBxa5G7xzyEXgzc7ZL3CMA%3d%3d | unknown | — | — | whitelisted |
6656 | svchost.exe | GET | 206 | 199.232.214.172:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/062b65bc-b6a4-4f5a-8413-7218292237fe?P1=1724803633&P2=404&P3=2&P4=PFzv3TL7O9NKuqK%2fwzoSpowLllKOnb9km34FAbXqxy8eoFi%2bxl7q1jecThdMqO7rvBxa5G7xzyEXgzc7ZL3CMA%3d%3d | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
1356 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
3888 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
6848 | msedge.exe | 13.107.42.16:443 | config.edge.skype.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
6944 | msedge.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
6848 | msedge.exe | 162.159.137.54:443 | gustavortech.org | — | — | unknown |
6848 | msedge.exe | 162.159.137.54:80 | gustavortech.org | CLOUDFLARENET | — | unknown |
6848 | msedge.exe | 192.0.77.2:443 | i0.wp.com | — | — | unknown |
6848 | msedge.exe | 192.0.77.37:443 | c0.wp.com | — | — | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
config.edge.skype.com |
| whitelisted |
gustavortech.org |
| unknown |
edge.microsoft.com |
| whitelisted |
business.bing.com |
| whitelisted |
edge-mobile-static.azureedge.net |
| whitelisted |
bzib.nelreports.net |
| whitelisted |
www.bing.com |
| whitelisted |
c0.wp.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
6848 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] Cloudflare content delivery network (cdnjs .cloudflare .com) |
6848 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] Cloudflare content delivery network (cdnjs .cloudflare .com) |
6848 | msedge.exe | Potential Corporate Privacy Violation | ET INFO Browser Automation Toolkit in DNS Lookup (bablosoft .com) |
6848 | msedge.exe | Potential Corporate Privacy Violation | ET INFO Browser Automation Toolkit in TLS SNI (bablosoft .com) |
6848 | msedge.exe | Potential Corporate Privacy Violation | ET INFO Fingerprinting Service in DNS Lookup (customfingerprints .bablosoft .com) |
6848 | msedge.exe | Potential Corporate Privacy Violation | ET INFO Fingerprinting Service in DNS Lookup (customfingerprints .bablosoft .com) |
6848 | msedge.exe | Potential Corporate Privacy Violation | ET INFO Fingerprinting Service in TLS SNI (customfingerprints .bablosoft .com) |
6848 | msedge.exe | Potential Corporate Privacy Violation | ET INFO Browser Automation Toolkit in DNS Lookup (bablosoft .com) |
6848 | msedge.exe | Potential Corporate Privacy Violation | ET INFO Browser Automation Toolkit in DNS Lookup (bablosoft .com) |
6848 | msedge.exe | Potential Corporate Privacy Violation | ET INFO Browser Automation Toolkit in TLS SNI (bablosoft .com) |
1 ETPRO signatures available at the full report
Process | Message |
|---|---|
WINWORD.EXE | WebView2: Failed to find an installed WebView2 runtime or non-stable Microsoft Edge installation.
|
WINWORD.EXE | WebView2: Failed to find an installed WebView2 runtime or non-stable Microsoft Edge installation.
|
WINWORD.EXE | WebView2: Failed to find an installed WebView2 runtime or non-stable Microsoft Edge installation.
|
WINWORD.EXE | WebView2: Failed to find an installed WebView2 runtime or non-stable Microsoft Edge installation.
|
WINWORD.EXE | WebView2: Failed to find an installed WebView2 runtime or non-stable Microsoft Edge installation.
|
WINWORD.EXE | WebView2: Failed to find an installed WebView2 runtime or non-stable Microsoft Edge installation.
|
WINWORD.EXE | WebView2: Failed to find an installed WebView2 runtime or non-stable Microsoft Edge installation.
|
WINWORD.EXE | WebView2: Failed to find an installed WebView2 runtime or non-stable Microsoft Edge installation.
|
WINWORD.EXE | WebView2: Failed to find an installed WebView2 runtime or non-stable Microsoft Edge installation.
|