| URL: | https://tinyurl.com/26p9htts? |
| Full analysis: | https://app.any.run/tasks/94ec5cb1-be04-44e0-ba5d-5b7dc236bea4 |
| Verdict: | Malicious activity |
| Threats: | Lumma is an information stealer, developed using the C programming language. It is offered for sale as a malware-as-a-service, with several plans available. It usually targets cryptocurrency wallets, login credentials, and other sensitive information on a compromised system. The malicious software regularly gets updates that improve and expand its functionality, making it a serious stealer threat. |
| Analysis date: | April 23, 2025, 08:50:39 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MD5: | FB63C66BE3D8D9D226173B02121A595B |
| SHA1: | F7F20589F6EE032389DBB5D05212D795BB8CEBC7 |
| SHA256: | 2C682060990B6163A9C61FEBEC9B066866058CD3FAEBBD03E378C288D0858BC2 |
| SSDEEP: | 3:N8EzLdIYan:2End5an |
MALICIOUS
Actions looks like stealing of personal data
- xd.com (PID: 7668)
Steals credentials from Web Browsers
- xd.com (PID: 7668)
Changes the autorun value in the registry
- GF2T9M0MJAMCQ1XM68H.exe (PID: 2384)
LUMMA mutex has been found
- xd.com (PID: 7668)
SUSPICIOUS
Reads security settings of Internet Explorer
- WinRAR.exe (PID: 8140)
- WinRAR.exe (PID: 4220)
- GF2T9M0MJAMCQ1XM68H.exe (PID: 2384)
Application launched itself
- WinRAR.exe (PID: 8140)
- WinRAR.exe (PID: 4220)
Process drops legitimate windows executable
- WinRAR.exe (PID: 5156)
Executable content was dropped or overwritten
- Setup.exe (PID: 5384)
- xd.com (PID: 7668)
- GF2T9M0MJAMCQ1XM68H.exe (PID: 2384)
Starts application with an unusual extension
- Setup.exe (PID: 5384)
Searches for installed software
- xd.com (PID: 7668)
Found regular expressions for crypto-addresses (YARA)
- GF2T9M0MJAMCQ1XM68H.exe (PID: 2384)
INFO
Checks supported languages
- Setup.exe (PID: 5384)
- GF2T9M0MJAMCQ1XM68H.exe (PID: 2384)
- xd.com (PID: 7668)
The sample compiled with english language support
- WinRAR.exe (PID: 5156)
- Setup.exe (PID: 5384)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 5156)
Reads the computer name
- Setup.exe (PID: 5384)
- GF2T9M0MJAMCQ1XM68H.exe (PID: 2384)
- xd.com (PID: 7668)
Creates files in the program directory
- Setup.exe (PID: 5384)
- GF2T9M0MJAMCQ1XM68H.exe (PID: 2384)
Create files in a temporary directory
- Setup.exe (PID: 5384)
- xd.com (PID: 7668)
Compiled with Borland Delphi (YARA)
- Setup.exe (PID: 5384)
The sample compiled with chinese language support
- Setup.exe (PID: 5384)
Checks proxy server information
- GF2T9M0MJAMCQ1XM68H.exe (PID: 2384)
Reads the machine GUID from the registry
- GF2T9M0MJAMCQ1XM68H.exe (PID: 2384)
Reads the software policy settings
- xd.com (PID: 7668)
- GF2T9M0MJAMCQ1XM68H.exe (PID: 2384)
Creates files or folders in the user directory
- GF2T9M0MJAMCQ1XM68H.exe (PID: 2384)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
194
Monitored processes
6
Malicious processes
3
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2384 | "C:\Users\admin\AppData\Local\Temp\GF2T9M0MJAMCQ1XM68H.exe" | C:\Users\admin\AppData\Local\Temp\GF2T9M0MJAMCQ1XM68H.exe | xd.com | ||||||||||||
User: admin Integrity Level: MEDIUM Modules
| |||||||||||||||
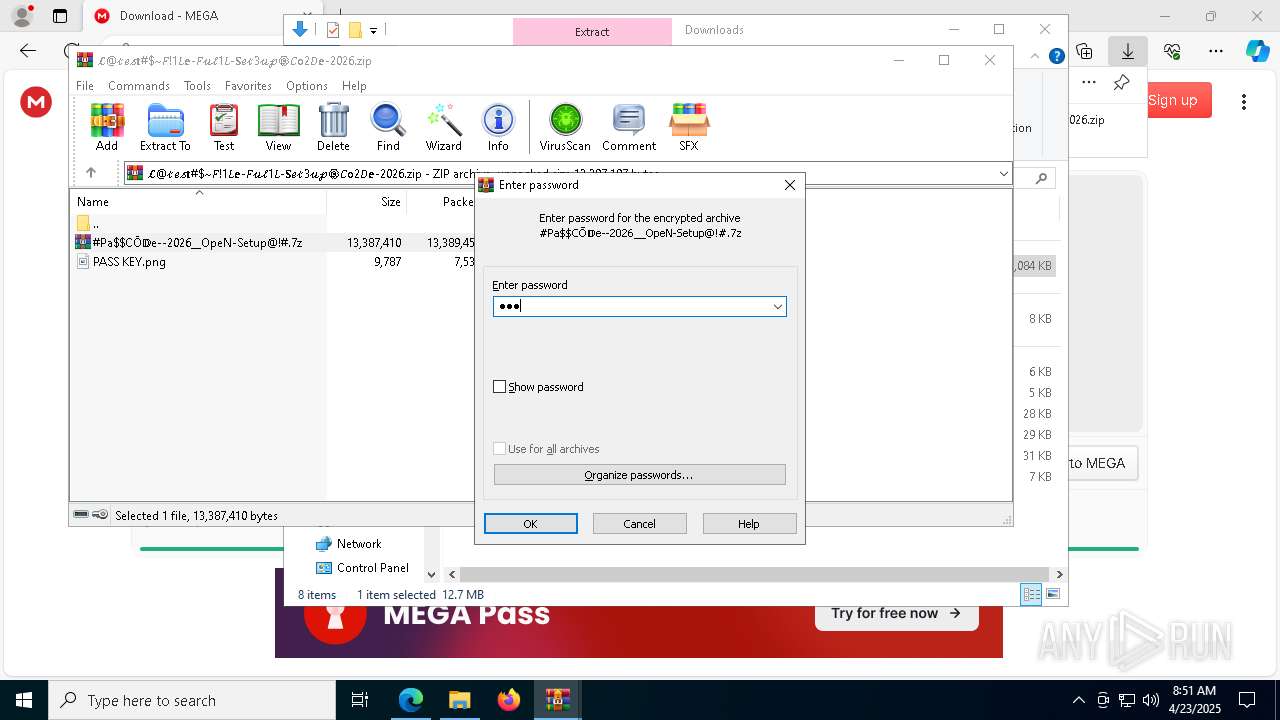
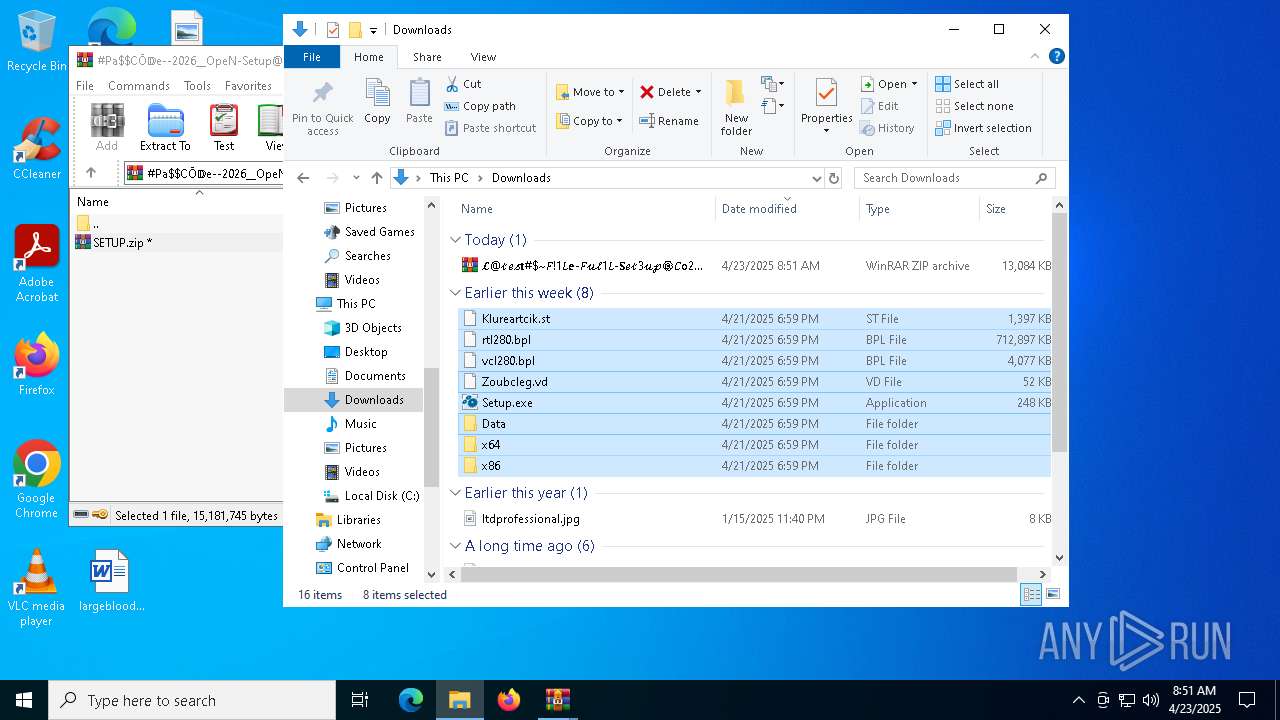
| 4220 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\AppData\Local\Temp\Rar$DIa8140.8174\#Pa$CŌ𝔻e--2026__OpeN-Setup@!#.7z | C:\Program Files\WinRAR\WinRAR.exe | — | WinRAR.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
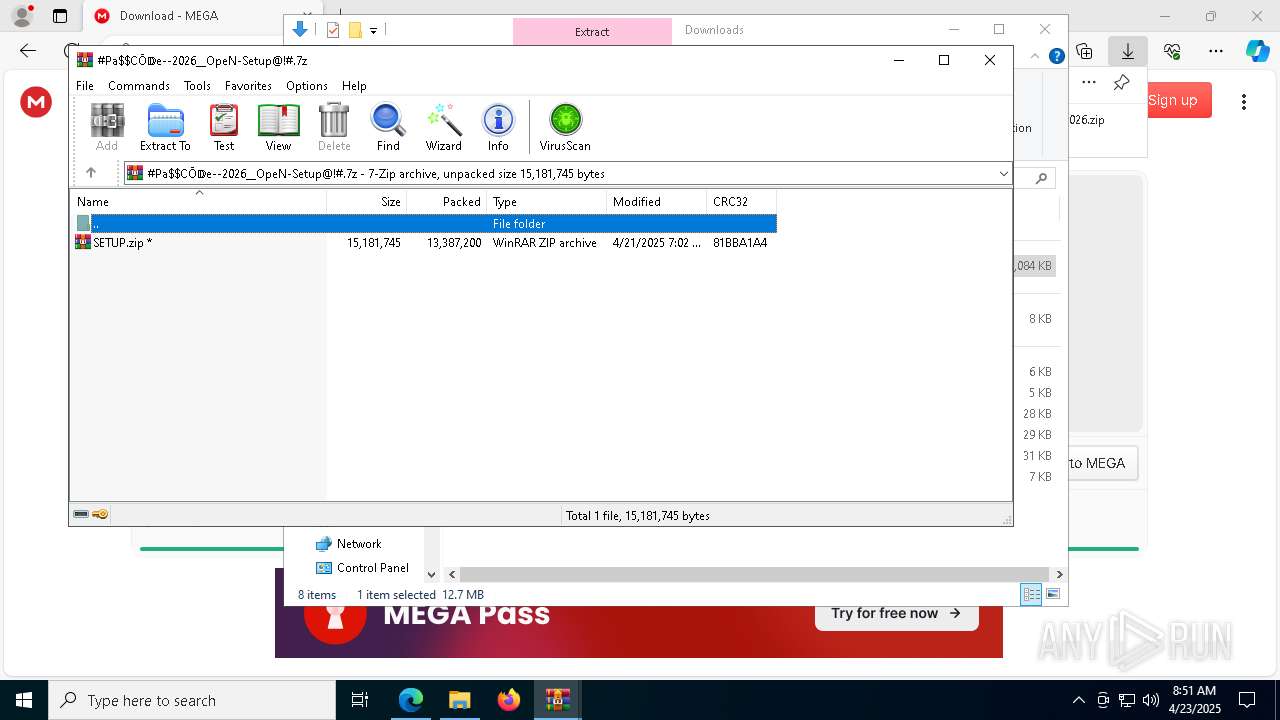
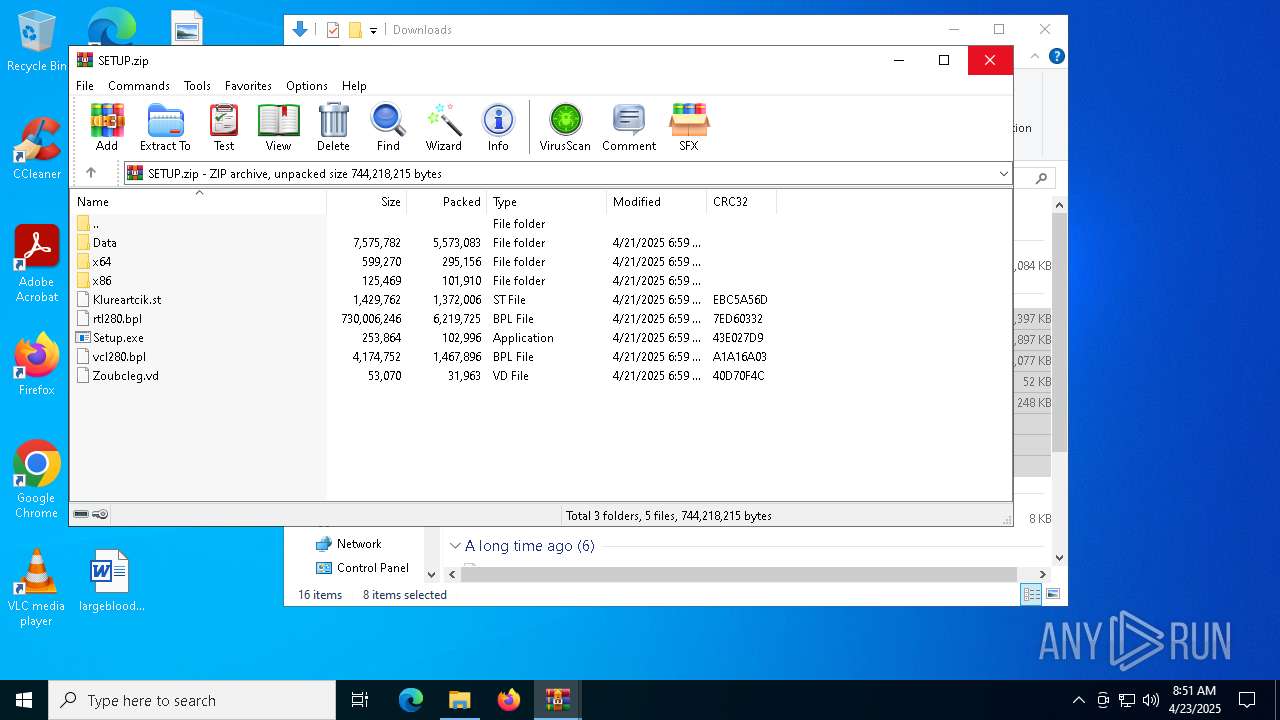
| 5156 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\AppData\Local\Temp\Rar$DIb4220.8487\SETUP.zip | C:\Program Files\WinRAR\WinRAR.exe | WinRAR.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
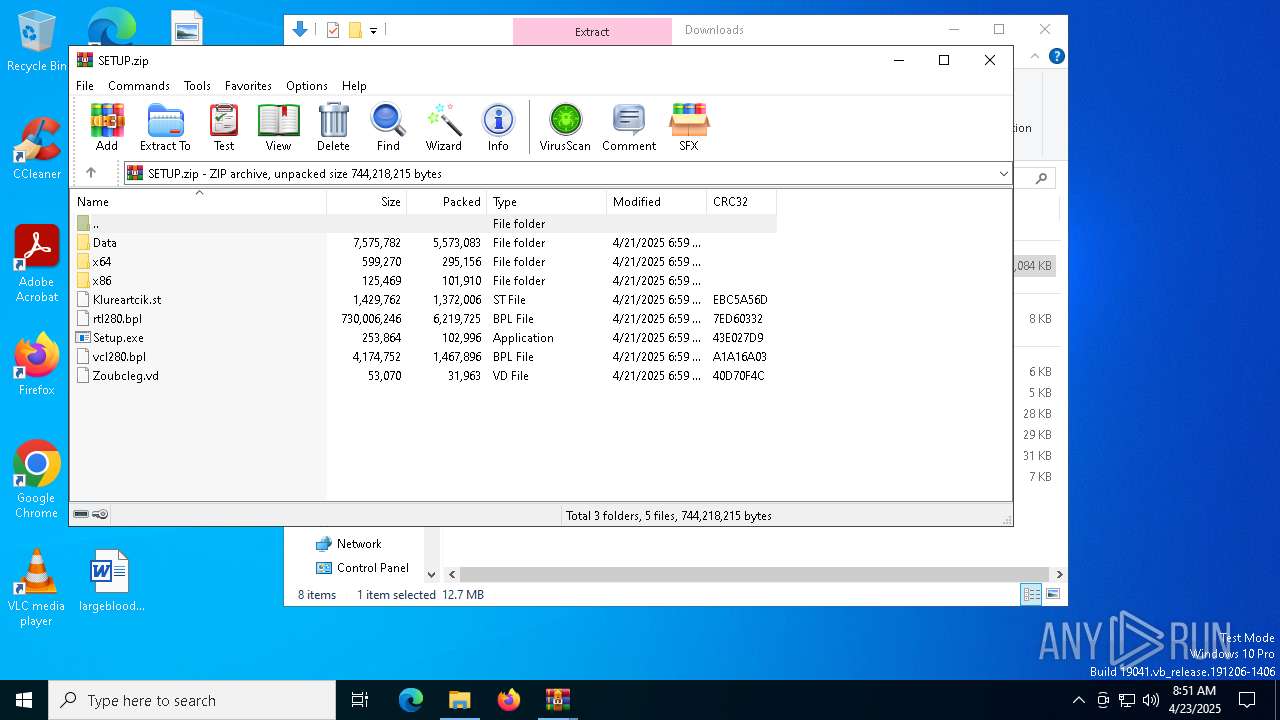
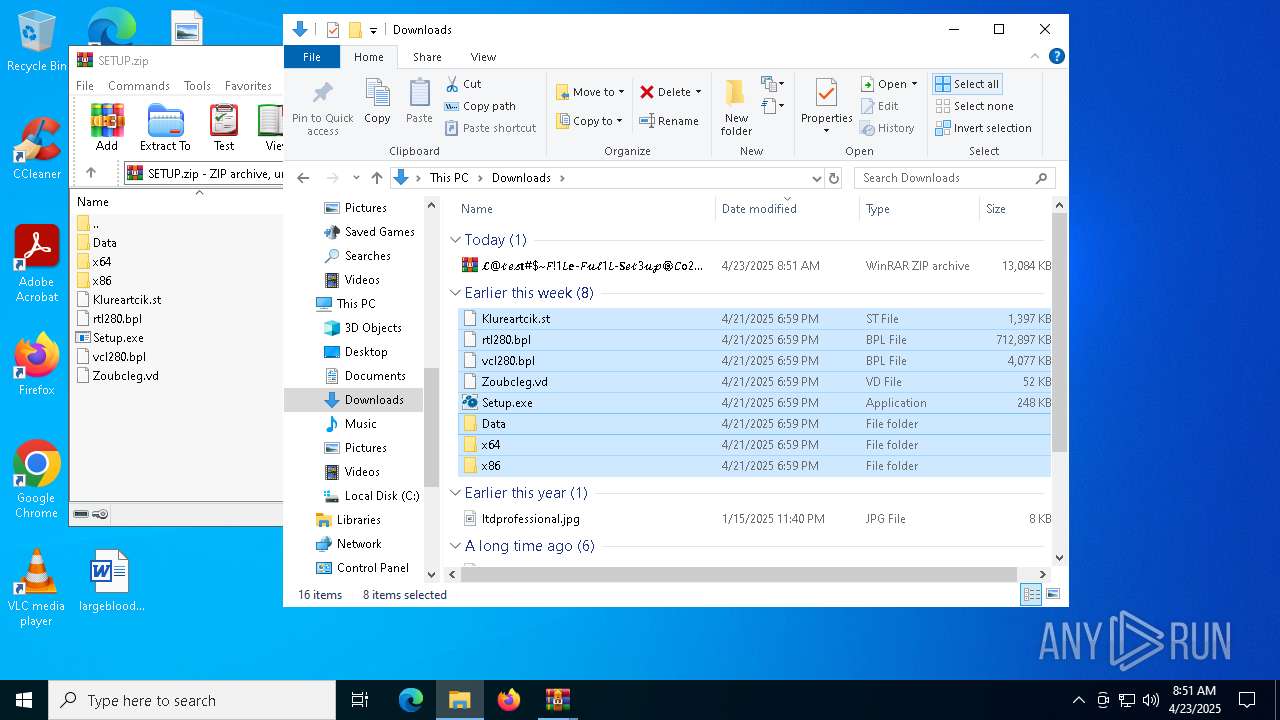
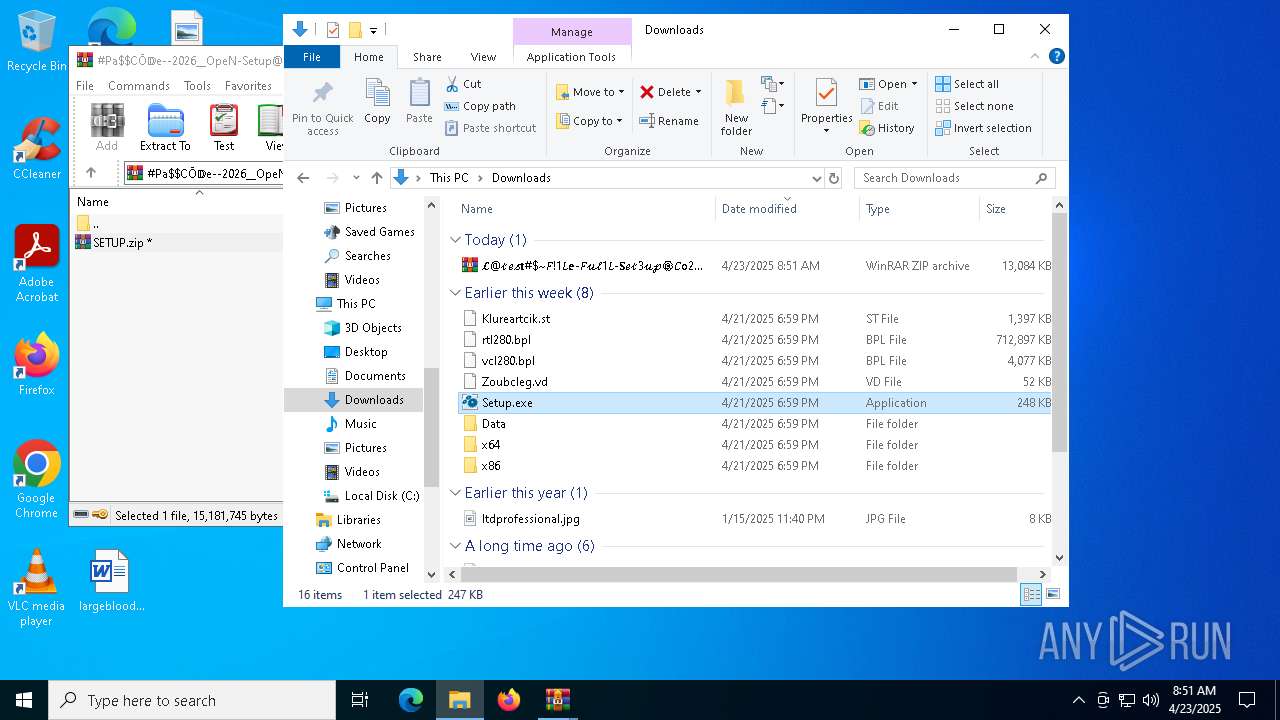
| 5384 | "C:\Users\admin\Downloads\Setup.exe" | C:\Users\admin\Downloads\Setup.exe | explorer.exe | ||||||||||||
User: admin Company: Neowise Software Integrity Level: MEDIUM Description: Updates utility for RoboTask Exit code: 0 Version: 9.8.1.292 Modules
| |||||||||||||||
| 7668 | C:\Users\admin\AppData\Local\Temp\xd.com | C:\Users\admin\AppData\Local\Temp\xd.com | Setup.exe | ||||||||||||
User: admin Company: ASUSTek Compputer Inc. Integrity Level: MEDIUM Description: AAC MB HAL Exit code: 0 Version: 1.3.9.6 Modules
| |||||||||||||||
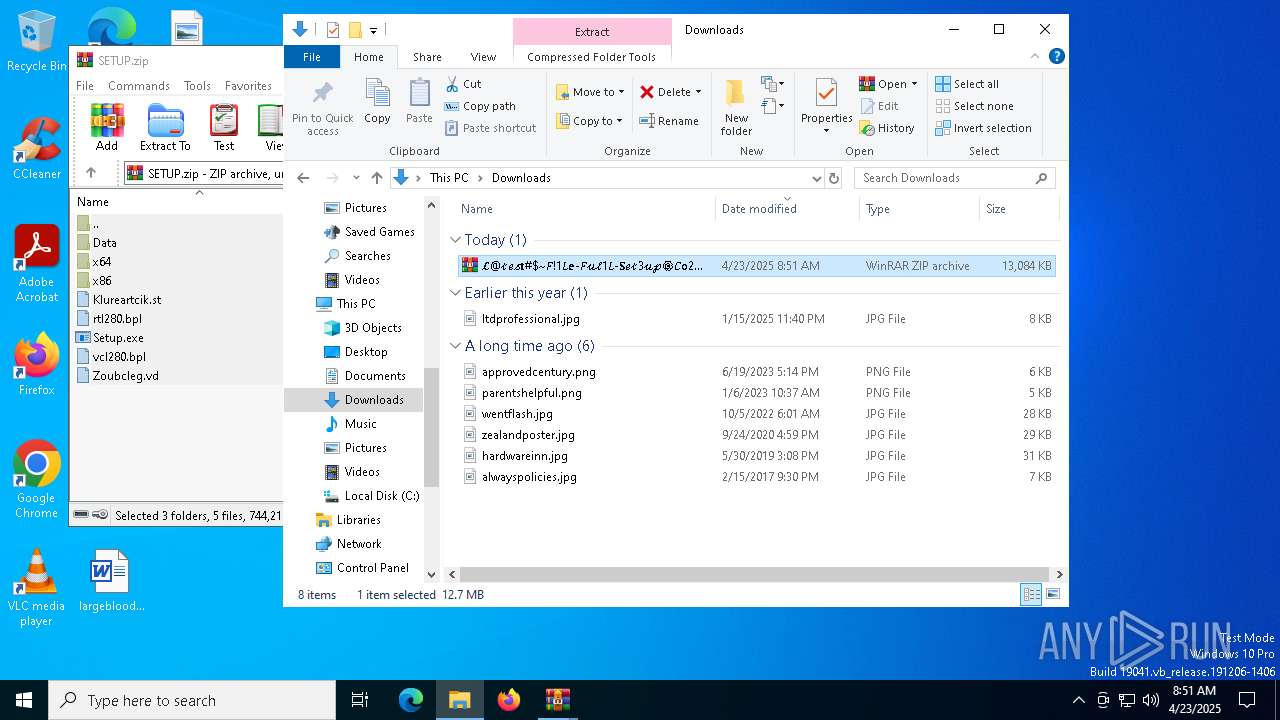
| 8140 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\Downloads\𝓛@𝓉𝑒𝓈𝐭#$~𝐹!1𝐿𝐞-𝐹𝓊𝓁1𝐿-𝐒𝑒𝓉3𝓊𝓅⚙️𝐶𝐨2𝐷𝐞-2026.zip" | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
Total events
5 854
Read events
5 795
Write events
59
Delete events
0
Modification events
| (PID) Process: | (8140) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (8140) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (8140) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (8140) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Downloads\𝓛@𝓉𝑒𝓈𝐭#$~𝐹!1𝐿𝐞-𝐹𝓊𝓁1𝐿-𝐒𝑒𝓉3𝓊𝓅⚙️𝐶𝐨2𝐷𝐞-2026.zip | |||
| (PID) Process: | (8140) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (8140) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (8140) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (8140) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (4220) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface |
| Operation: | write | Name: | ShowPassword |
Value: 0 | |||
| (PID) Process: | (4220) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
Executable files
11
Suspicious files
37
Text files
67
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 8140 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DIa8140.8174\#Pa$CŌ𝔻e--2026__OpeN-Setup@!#.7z | — | |
MD5:— | SHA256:— | |||
| 5156 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa5156.9195\rtl280.bpl | — | |
MD5:— | SHA256:— | |||
| 5156 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa5156.9195\Data\Belarusian.txt | text | |
MD5:2684AD2980CAF78DF11F768A4C8010F0 | SHA256:2291246A75BDCB07E5B11B59B8C8620AED6A0671C8BBC8F552E2A747BCC1D698 | |||
| 5156 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa5156.9195\Data\010.phpt | text | |
MD5:0DF0C68B989558B13BDF12563662F97D | SHA256:9DD63682CF21F89B0AD54253AADAF0C894ADF56C70A61D0277E5125E2C276219 | |||
| 5156 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa5156.9195\Data\bug73460-002.phpt | text | |
MD5:D3BC5B63F2E2631BB77FF5784776F391 | SHA256:FB5C64A6643C83264AF0BF40E867969BDC5981CD8908933F4312D93AC8AA9C7A | |||
| 5156 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa5156.9195\vcl280.bpl | executable | |
MD5:EA19AE89806F60DD84DB3185099B3D88 | SHA256:6E9FF31DC5D209C094C688FA854C33A965C95DDCBA6CFE6C432596E0D1A09517 | |||
| 5156 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa5156.9195\Data\8859-7.txt | text | |
MD5:22786452BFC098BA284C5D31FC61B745 | SHA256:FE7CE66A91023F73E2118B49D49867E311E91D9E3F3B46329004D7A5A15FAED9 | |||
| 5156 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa5156.9195\Data\056.phpt | text | |
MD5:CAE613BFDED20BB9691C7EAE7D42E103 | SHA256:2F603BAA0B1AD1DCE3B01B389D5A76F23F7B91594BE6E7B2A2541CA7E1B24A9C | |||
| 5156 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa5156.9195\Data\area_element.c | text | |
MD5:19C4657F93148D837A4DAC256DC9B8D8 | SHA256:D7AA1E1F367866FB4CE16CCA63CF966C512C868B8BB38B4A237C478EA4E3D538 | |||
| 5156 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa5156.9195\Data\bug53885.phpt | text | |
MD5:EC9E92D16499A2F925F2688DDA88085B | SHA256:78D3EE494E769805DEC8BBDBE08B2C9B0F3F9DF4978E3E79E9E4632AA70E3881 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
29
TCP/UDP connections
133
DNS requests
135
Threats
37
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 2.16.164.49:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 2.16.164.49:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
— | — | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
— | — | HEAD | 200 | 199.232.210.172:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/bf8090eb-6e5c-4c51-9250-5bf9b46cf160?P1=1745626154&P2=404&P3=2&P4=QgLnWocjS%2fJ%2b%2bgRAE7kh2ub1%2fk%2fVFxNC3cuxyj3GwDvJuHRbfllUEKz8ZWmwF%2f%2bTKCaDtDSR5TEcG%2fXfTKxZdQ%3d%3d | unknown | — | — | whitelisted |
— | — | GET | 206 | 199.232.210.172:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/bf8090eb-6e5c-4c51-9250-5bf9b46cf160?P1=1745626154&P2=404&P3=2&P4=QgLnWocjS%2fJ%2b%2bgRAE7kh2ub1%2fk%2fVFxNC3cuxyj3GwDvJuHRbfllUEKz8ZWmwF%2f%2bTKCaDtDSR5TEcG%2fXfTKxZdQ%3d%3d | unknown | — | — | whitelisted |
— | — | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
— | — | GET | 206 | 199.232.210.172:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/bf8090eb-6e5c-4c51-9250-5bf9b46cf160?P1=1745626154&P2=404&P3=2&P4=QgLnWocjS%2fJ%2b%2bgRAE7kh2ub1%2fk%2fVFxNC3cuxyj3GwDvJuHRbfllUEKz8ZWmwF%2f%2bTKCaDtDSR5TEcG%2fXfTKxZdQ%3d%3d | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 2.16.164.49:80 | crl.microsoft.com | Akamai International B.V. | NL | whitelisted |
— | — | 95.101.149.131:80 | www.microsoft.com | Akamai International B.V. | NL | whitelisted |
— | — | 239.255.255.250:1900 | — | — | — | whitelisted |
— | — | 104.18.111.161:443 | tinyurl.com | — | — | whitelisted |
— | — | 195.66.210.137:443 | pc4download.com | — | — | unknown |
— | — | 13.107.42.16:443 | config.edge.skype.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
— | — | 150.171.27.11:443 | edge.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
tinyurl.com |
| whitelisted |
config.edge.skype.com |
| whitelisted |
edge.microsoft.com |
| whitelisted |
business.bing.com |
| whitelisted |
edge-mobile-static.azureedge.net |
| whitelisted |
pc4download.com |
| unknown |
Threats
PID | Process | Class | Message |
|---|---|---|---|
— | — | Not Suspicious Traffic | INFO [ANY.RUN] URL Shortener TinyURL (tinyurl .com) |
— | — | Misc activity | INFO [ANY.RUN] Possible short link service (tinyurl .com) |
— | — | Misc activity | INFO [ANY.RUN] Possible short link service (tinyurl .com) |
— | — | Not Suspicious Traffic | INFO [ANY.RUN] URL Shortener TinyURL (tinyurl .com) |
— | — | Misc activity | INFO [ANY.RUN] Possible short link service (tinyurl .com) |
— | — | Not Suspicious Traffic | INFO [ANY.RUN] URL Shortener TinyURL (tinyurl .com) |
— | — | Not Suspicious Traffic | INFO [ANY.RUN] Cloudflare content delivery network (cdnjs .cloudflare .com) |
— | — | Not Suspicious Traffic | INFO [ANY.RUN] Cloudflare content delivery network (cdnjs .cloudflare .com) |
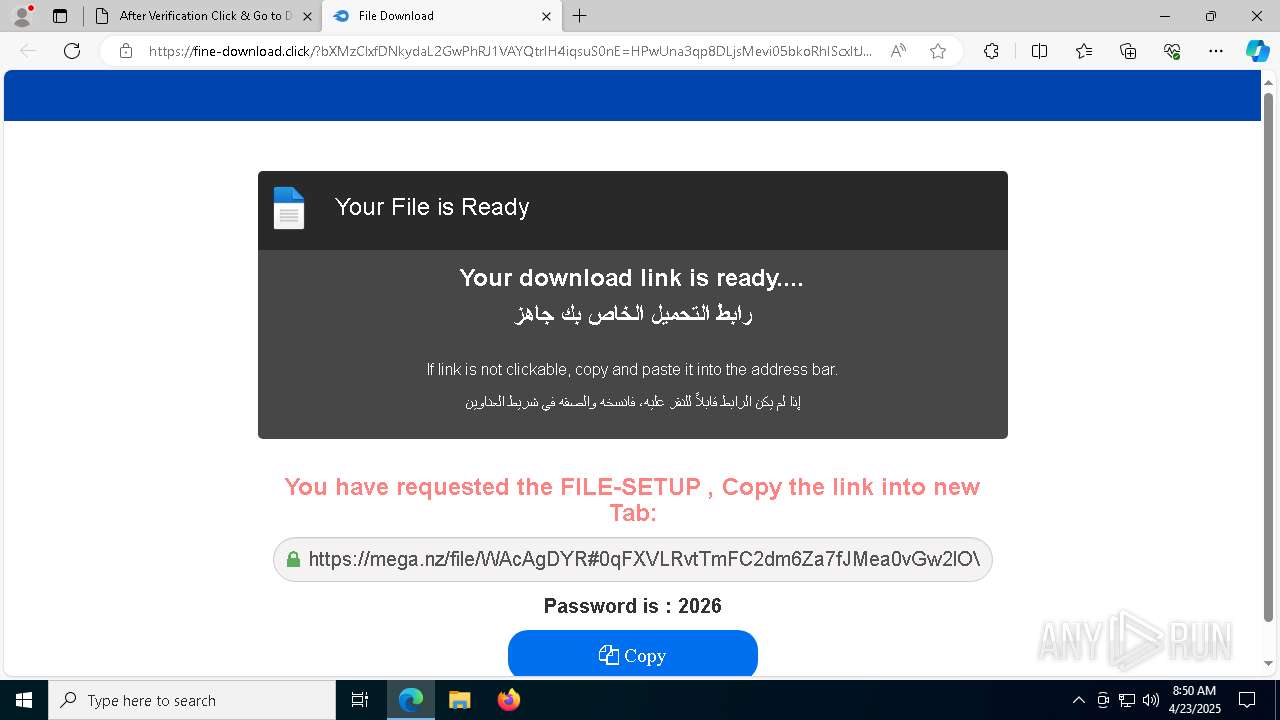
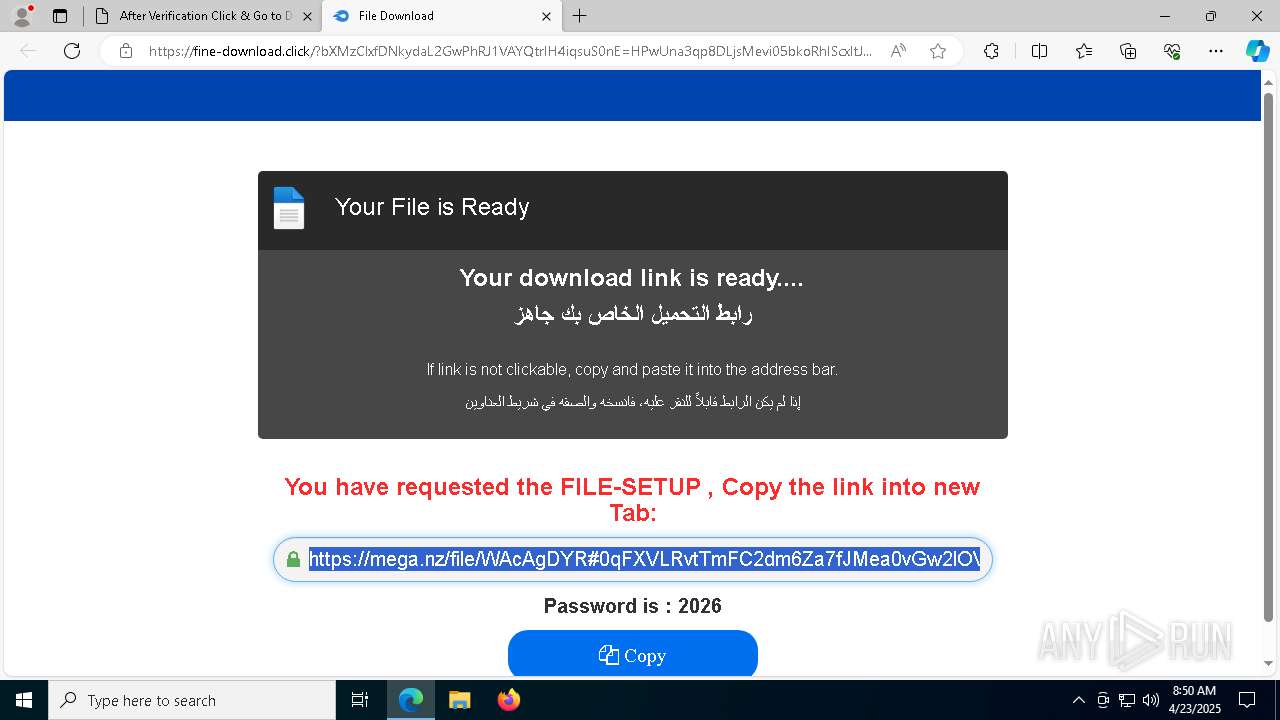
— | — | Misc activity | ET FILE_SHARING File Sharing Related Domain in DNS Lookup (mega .nz) |
— | — | Misc activity | ET FILE_SHARING File Sharing Related Domain in DNS Lookup (mega .nz) |