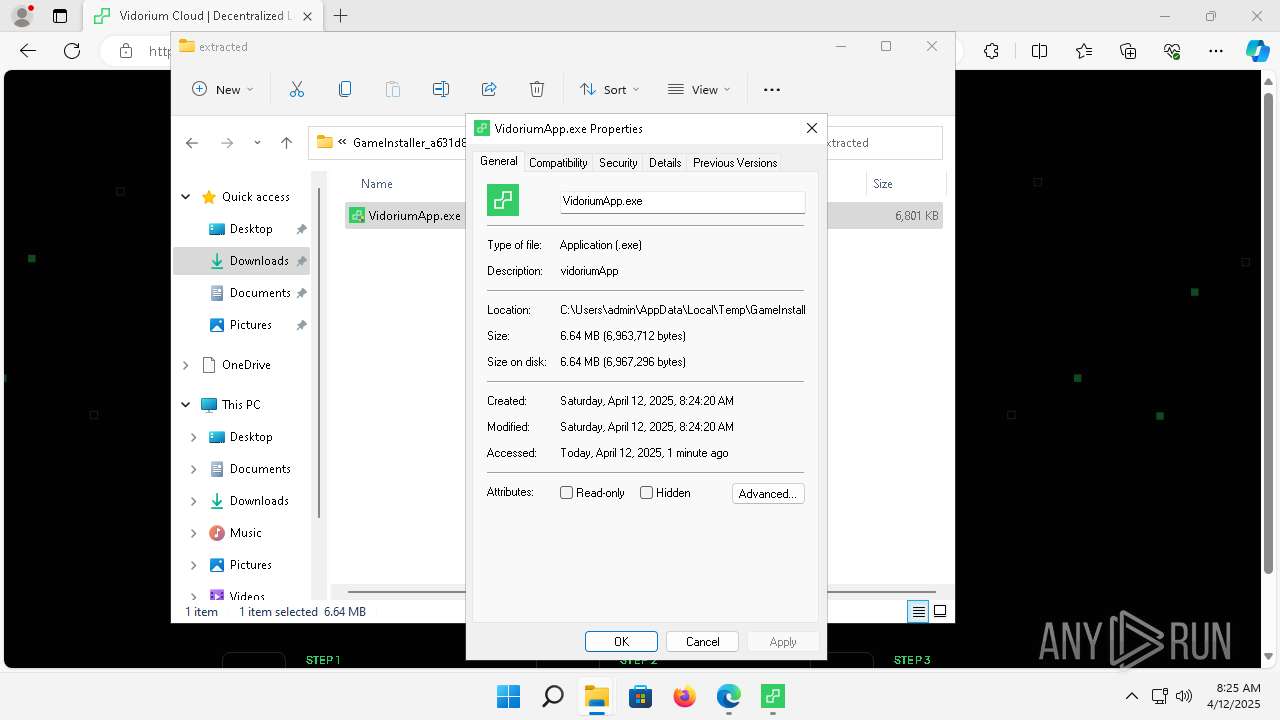
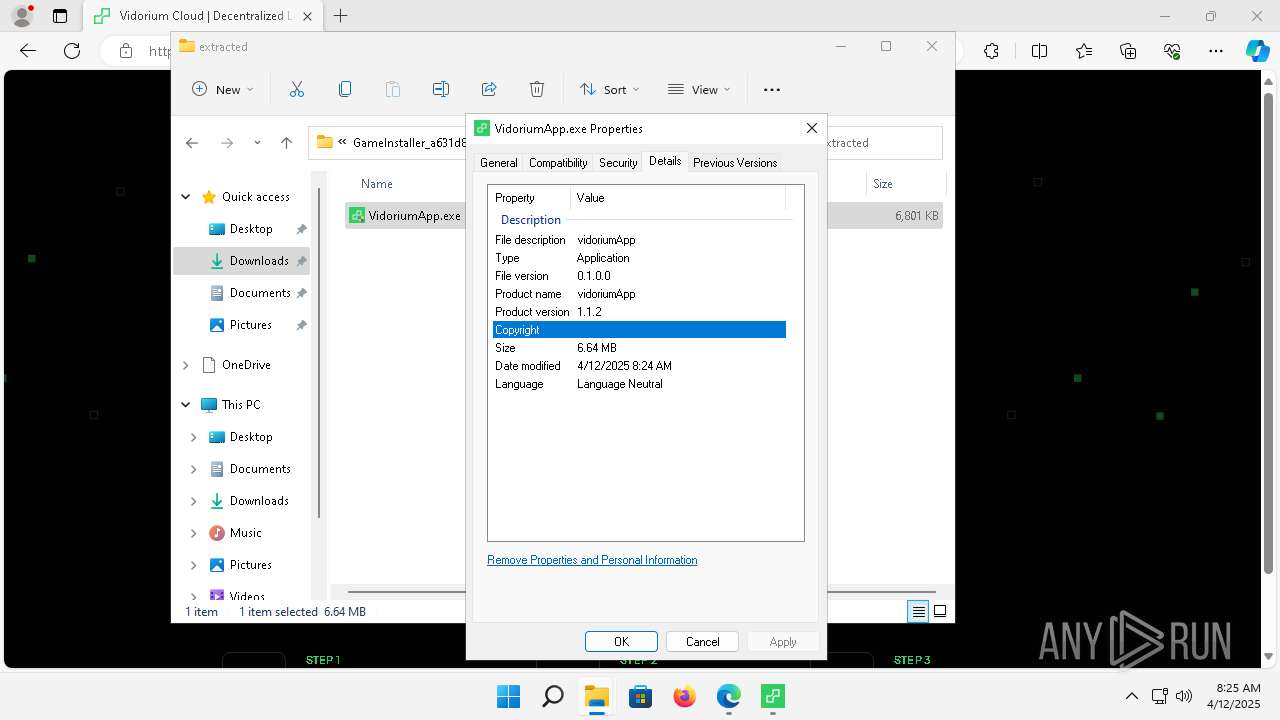
| URL: | vidorium.com |
| Full analysis: | https://app.any.run/tasks/14da09c5-283c-4b2d-8695-3f9c2b1ac9ab |
| Verdict: | Malicious activity |
| Threats: | Rhadamanthys is a C++ information-stealing malware that extracts sensitive data from infiltrated machines. Its layered operational chain and advanced evasion tactics make it a major risk in cybersecurity landscapes. |
| Analysis date: | April 12, 2025, 08:22:30 |
| OS: | Windows 11 Professional (build: 22000, 64 bit) |
| Tags: | |
| Indicators: | |
| MD5: | 49E4E19D89CCE51B71F05C4DFA698989 |
| SHA1: | 0FE7D666F4F06F1E886DF99AFEFE4BBB64464B55 |
| SHA256: | 2C55FF61A3A3215D3B76A6DC13ADF2034519EE53B081087A41DBDB2DDD7C5F1C |
| SSDEEP: | 3:kCI2:kS |
MALICIOUS
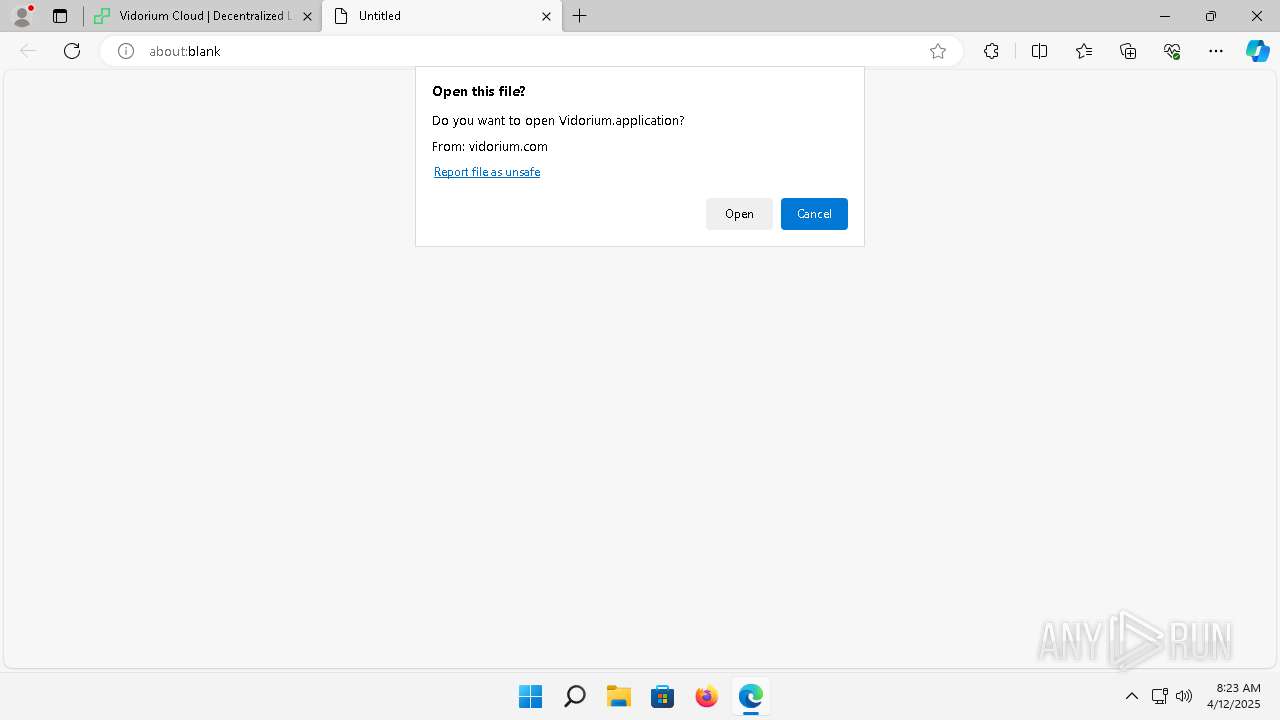
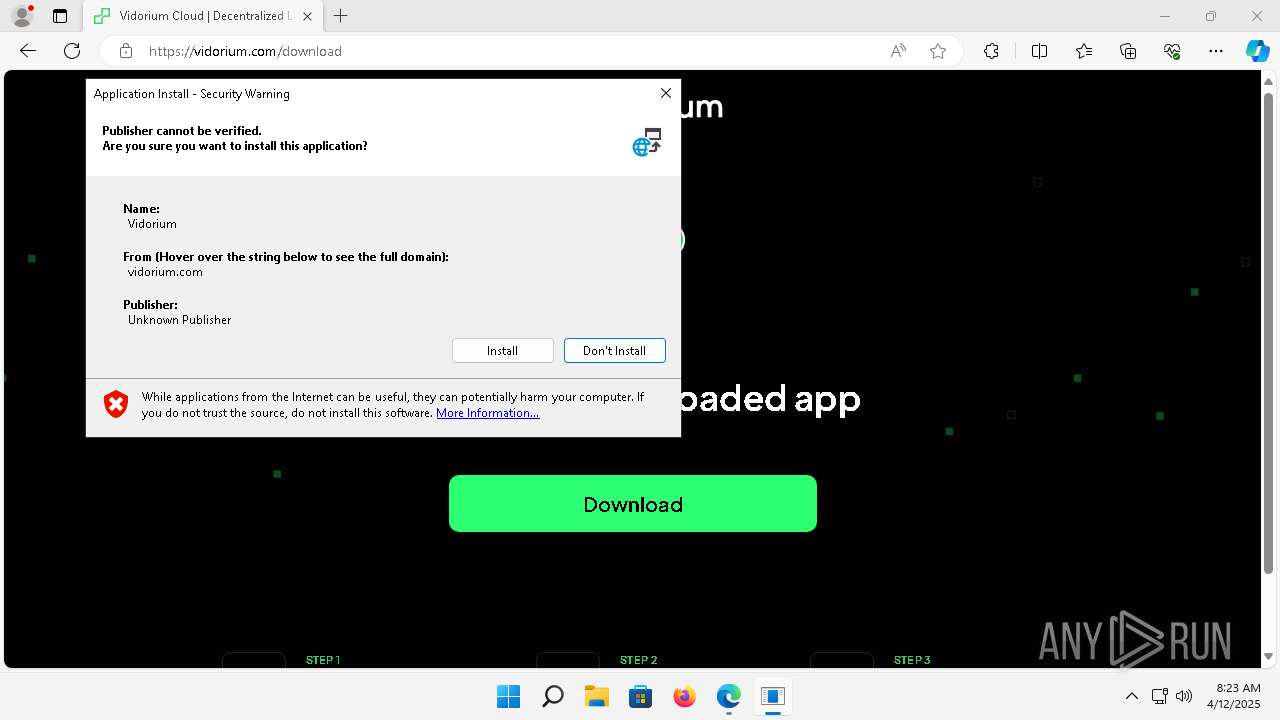
Executing a file with an untrusted certificate
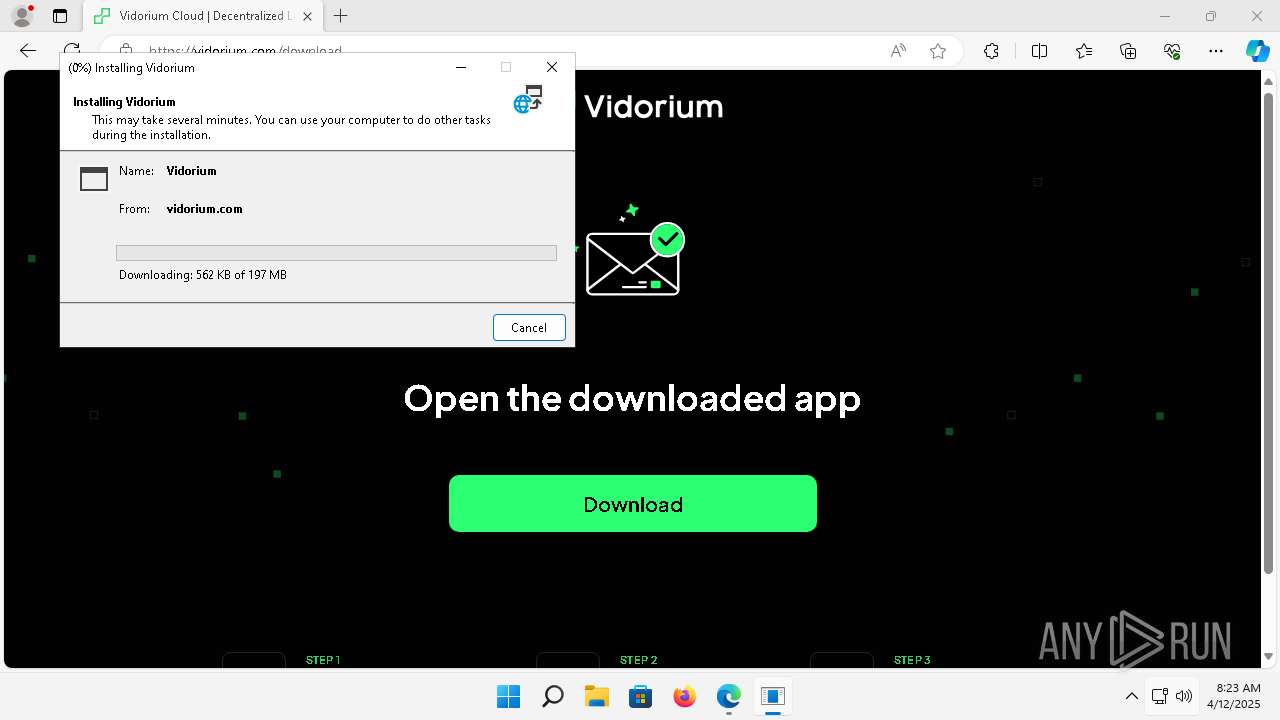
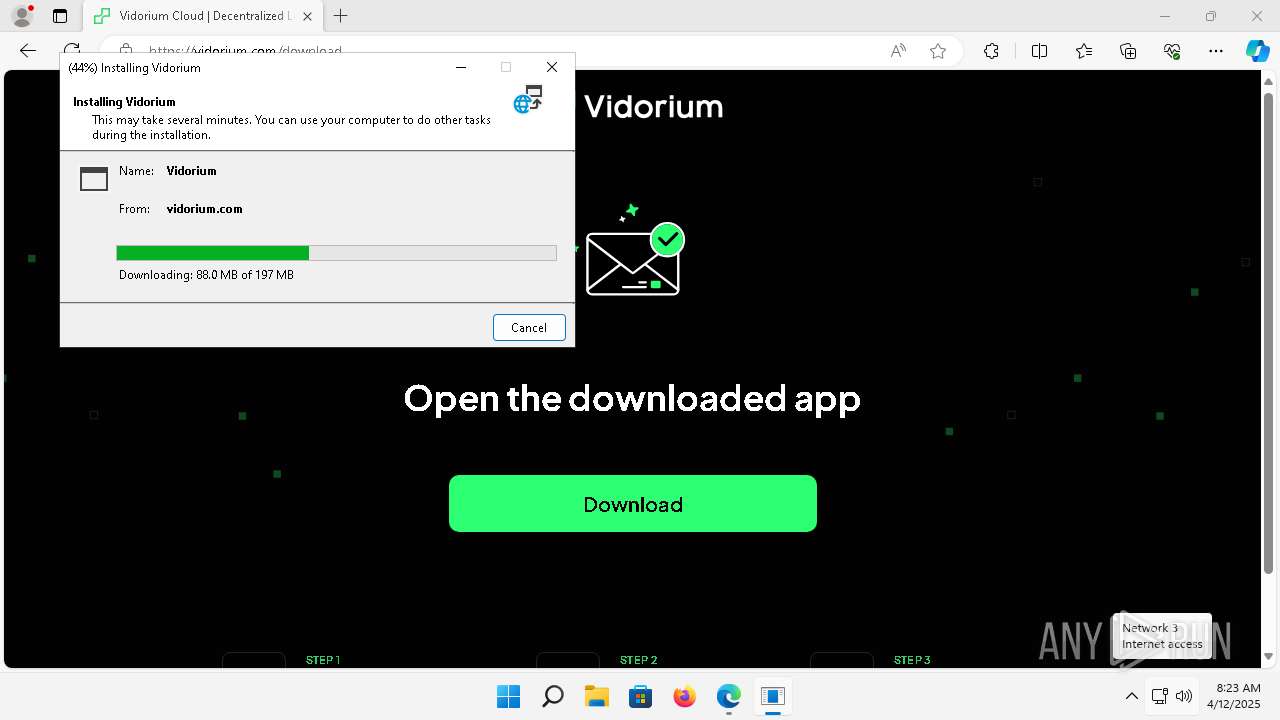
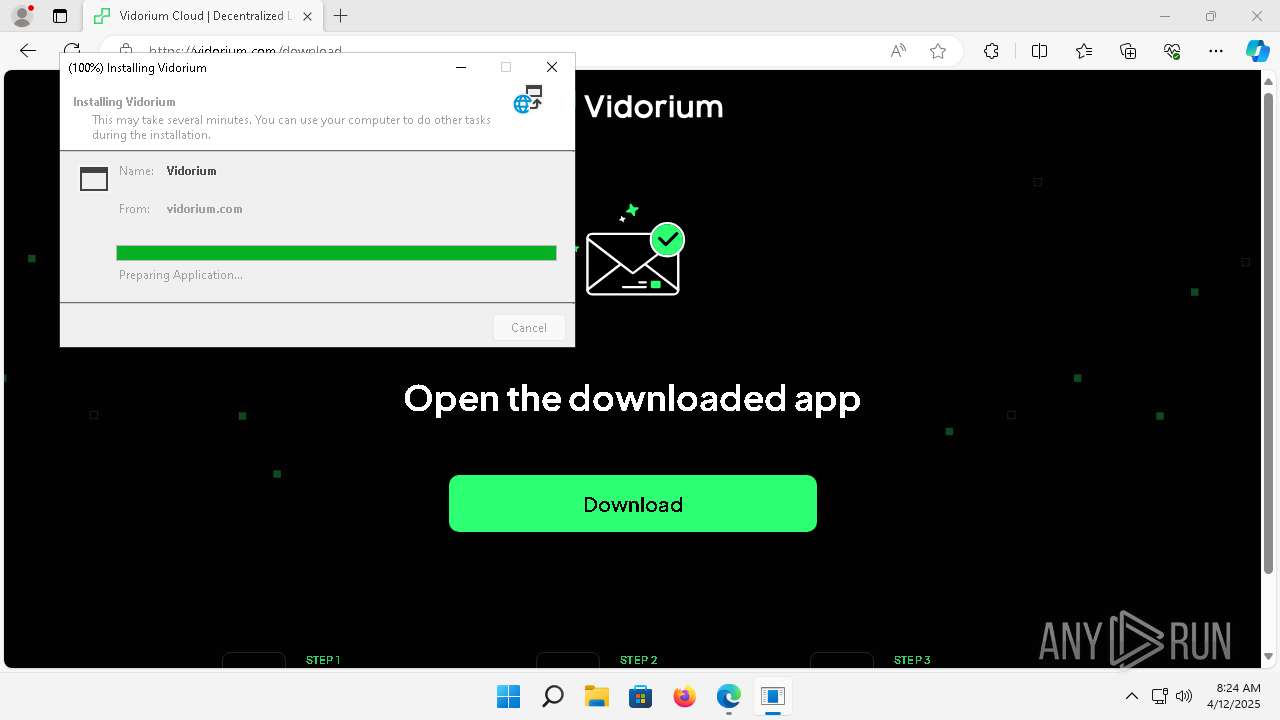
- Launcher.exe (PID: 6676)
- Vidorium.exe (PID: 4948)
- P0Ju5FQGgK.exe (PID: 6820)
- vldi6L0nB8.exe (PID: 6712)
- P0Ju5FQGgK.exe (PID: 3376)
The DLL Hijacking
- msedgewebview2.exe (PID: 1204)
Adds path to the Windows Defender exclusion list
- VidoriumApp.exe (PID: 4816)
Changes Windows Defender settings
- VidoriumApp.exe (PID: 4816)
RHADAMANTHYS mutex has been found
- vldi6L0nB8.exe (PID: 6712)
- svchost.exe (PID: 5196)
Actions looks like stealing of personal data
- chrome.exe (PID: 6132)
- msedge.exe (PID: 948)
STEALC has been detected (SURICATA)
- P0Ju5FQGgK.exe (PID: 3376)
Connects to the CnC server
- P0Ju5FQGgK.exe (PID: 3376)
RHADAMANTHYS has been detected (SURICATA)
- svchost.exe (PID: 6200)
SUSPICIOUS
Reads settings of System Certificates
- dfsvc.exe (PID: 6220)
- Vidorium.exe (PID: 4948)
- msedgewebview2.exe (PID: 6592)
- VidoriumApp.exe (PID: 4816)
- chrome.exe (PID: 6132)
Uses RUNDLL32.EXE to load library
- msedge.exe (PID: 3816)
Reads the Internet Settings
- dfsvc.exe (PID: 6220)
- Vidorium.exe (PID: 4948)
- msedgewebview2.exe (PID: 6592)
- VidoriumApp.exe (PID: 4816)
- P0Ju5FQGgK.exe (PID: 3376)
- chrome.exe (PID: 6132)
- msedge.exe (PID: 1216)
- msedge.exe (PID: 948)
Reads Internet Explorer settings
- dfsvc.exe (PID: 6220)
Executable content was dropped or overwritten
- dfsvc.exe (PID: 6220)
- Vidorium.exe (PID: 4948)
- VidoriumApp.exe (PID: 4816)
- msedgewebview2.exe (PID: 440)
- msedgewebview2.exe (PID: 6320)
Reads security settings of Internet Explorer
- dfsvc.exe (PID: 6220)
- msedgewebview2.exe (PID: 6592)
- Vidorium.exe (PID: 4948)
- VidoriumApp.exe (PID: 4816)
- P0Ju5FQGgK.exe (PID: 3376)
The process drops C-runtime libraries
- dfsvc.exe (PID: 6220)
Process drops legitimate windows executable
- dfsvc.exe (PID: 6220)
- msedgewebview2.exe (PID: 440)
Searches for installed software
- dfsvc.exe (PID: 6220)
- svchost.exe (PID: 6200)
- msedgewebview2.exe (PID: 6592)
Creates a software uninstall entry
- dfsvc.exe (PID: 6220)
Reads the date of Windows installation
- Vidorium.exe (PID: 4948)
- VidoriumApp.exe (PID: 4816)
Application launched itself
- msedgewebview2.exe (PID: 6592)
- P0Ju5FQGgK.exe (PID: 6820)
Checks for external IP
- VidoriumApp.exe (PID: 4816)
Potential Corporate Privacy Violation
- VidoriumApp.exe (PID: 4816)
The process hide an interactive prompt from the user
- VidoriumApp.exe (PID: 4816)
Starts POWERSHELL.EXE for commands execution
- VidoriumApp.exe (PID: 4816)
Script adds exclusion path to Windows Defender
- VidoriumApp.exe (PID: 4816)
There is functionality for taking screenshot (YARA)
- VidoriumApp.exe (PID: 4816)
The process checks if it is being run in the virtual environment
- svchost.exe (PID: 5196)
Contacting a server suspected of hosting an CnC
- P0Ju5FQGgK.exe (PID: 3376)
Connects to the server without a host name
- P0Ju5FQGgK.exe (PID: 3376)
Loads DLL from Mozilla Firefox
- svchost.exe (PID: 6200)
INFO
Reads the computer name
- identity_helper.exe (PID: 6592)
- dfsvc.exe (PID: 6220)
- Launcher.exe (PID: 6676)
- Vidorium.exe (PID: 4948)
- VidoriumApp.exe (PID: 4816)
- msedgewebview2.exe (PID: 6592)
- msedgewebview2.exe (PID: 5216)
- msedgewebview2.exe (PID: 1204)
- chrome.exe (PID: 6132)
- P0Ju5FQGgK.exe (PID: 3376)
- msedge.exe (PID: 948)
- msedge.exe (PID: 1216)
- msedgewebview2.exe (PID: 1380)
- msedgewebview2.exe (PID: 1336)
- msedgewebview2.exe (PID: 4636)
Application launched itself
- msedge.exe (PID: 3816)
- chrome.exe (PID: 6132)
- msedge.exe (PID: 1216)
- msedge.exe (PID: 948)
Checks supported languages
- identity_helper.exe (PID: 6592)
- dfsvc.exe (PID: 6220)
- Launcher.exe (PID: 6676)
- Vidorium.exe (PID: 4948)
- VidoriumApp.exe (PID: 4816)
- msedgewebview2.exe (PID: 1164)
- msedgewebview2.exe (PID: 6592)
- msedgewebview2.exe (PID: 6544)
- msedgewebview2.exe (PID: 1088)
- msedgewebview2.exe (PID: 5216)
- msedgewebview2.exe (PID: 1204)
- msedgewebview2.exe (PID: 6236)
- msedgewebview2.exe (PID: 4312)
- P0Ju5FQGgK.exe (PID: 6820)
- vldi6L0nB8.exe (PID: 6712)
- chrome.exe (PID: 6132)
- P0Ju5FQGgK.exe (PID: 3376)
- msedge.exe (PID: 948)
- msedge.exe (PID: 1216)
- wmprph.exe (PID: 4192)
- msedgewebview2.exe (PID: 4452)
- msedgewebview2.exe (PID: 5348)
- msedgewebview2.exe (PID: 440)
- msedgewebview2.exe (PID: 1300)
- msedgewebview2.exe (PID: 6248)
- msedgewebview2.exe (PID: 2868)
- msedgewebview2.exe (PID: 1380)
- msedgewebview2.exe (PID: 6320)
- msedgewebview2.exe (PID: 4528)
- msedgewebview2.exe (PID: 1336)
- msedgewebview2.exe (PID: 4636)
Creates files or folders in the user directory
- dfsvc.exe (PID: 6220)
- Launcher.exe (PID: 6676)
- msedgewebview2.exe (PID: 6544)
- msedgewebview2.exe (PID: 6592)
- msedgewebview2.exe (PID: 5216)
- P0Ju5FQGgK.exe (PID: 6820)
Disables trace logs
- dfsvc.exe (PID: 6220)
Reads the machine GUID from the registry
- dfsvc.exe (PID: 6220)
- Launcher.exe (PID: 6676)
- msedgewebview2.exe (PID: 6592)
- chrome.exe (PID: 6132)
- wmprph.exe (PID: 4192)
- msedgewebview2.exe (PID: 1380)
Checks proxy server information
- dfsvc.exe (PID: 6220)
- Vidorium.exe (PID: 4948)
- msedgewebview2.exe (PID: 6592)
- VidoriumApp.exe (PID: 4816)
- P0Ju5FQGgK.exe (PID: 3376)
- chrome.exe (PID: 6132)
- msedge.exe (PID: 1216)
- msedge.exe (PID: 948)
Process checks whether UAC notifications are on
- dfsvc.exe (PID: 6220)
Reads Environment values
- identity_helper.exe (PID: 6592)
- dfsvc.exe (PID: 6220)
- msedge.exe (PID: 948)
- chrome.exe (PID: 6132)
- msedge.exe (PID: 1216)
- msedgewebview2.exe (PID: 6592)
Create files in a temporary directory
- dfsvc.exe (PID: 6220)
- Vidorium.exe (PID: 4948)
- msedgewebview2.exe (PID: 6592)
- VidoriumApp.exe (PID: 4816)
- svchost.exe (PID: 6200)
- chrome.exe (PID: 6132)
- msedge.exe (PID: 948)
- msedge.exe (PID: 1216)
Reads the software policy settings
- dfsvc.exe (PID: 6220)
- Vidorium.exe (PID: 4948)
- VidoriumApp.exe (PID: 4816)
- msedgewebview2.exe (PID: 6592)
The sample compiled with english language support
- dfsvc.exe (PID: 6220)
- VidoriumApp.exe (PID: 4816)
- msedgewebview2.exe (PID: 6320)
- msedge.exe (PID: 5960)
Creates files in the program directory
- Vidorium.exe (PID: 4948)
Manual execution by a user
- msedgewebview2.exe (PID: 6592)
- msedge.exe (PID: 816)
- msedge.exe (PID: 1612)
Script raised an exception (POWERSHELL)
- powershell.exe (PID: 2572)
- powershell.exe (PID: 2140)
- powershell.exe (PID: 3352)
Application based on Rust
- VidoriumApp.exe (PID: 4816)
Checks if a key exists in the options dictionary (POWERSHELL)
- powershell.exe (PID: 2572)
- powershell.exe (PID: 3352)
- powershell.exe (PID: 2140)
Process checks computer location settings
- msedge.exe (PID: 948)
- msedge.exe (PID: 1216)
Executable content was dropped or overwritten
- msedge.exe (PID: 5960)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
238
Monitored processes
126
Malicious processes
15
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 8 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=4060 --field-trial-handle=2132,i,4376602714035184738,16510944388497468200,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.92 Modules
| |||||||||||||||
| 388 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=5184 --field-trial-handle=2132,i,4376602714035184738,16510944388497468200,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.92 Modules
| |||||||||||||||
| 440 | \??\C:\Windows\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.22000.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 440 | "C:\Program Files (x86)\Microsoft\EdgeWebView\Application\103.0.1264.77\msedgewebview2.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --lang=en-US --service-sandbox-type=utility --noerrdialogs --user-data-dir="C:\Users\admin\AppData\Local\VidoriumApp\EBWebView" --webview-exe-name=VidoriumApp.exe --webview-exe-version=1.1.2 --embedded-browser-webview=1 --embedded-browser-webview-dpi-awareness=2 --edge-webview-custom-scheme --mojo-platform-channel-handle=1440 --field-trial-handle=1884,i,12230872643994050004,5441706798476958355,131072 --enable-features=RemoveRedirectionBitmap --disable-features=msPdfOOUI,msSmartScreenProtection,msWebOOUI /prefetch:8 | C:\Program Files (x86)\Microsoft\EdgeWebView\Application\103.0.1264.77\msedgewebview2.exe | msedgewebview2.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge WebView2 Exit code: 0 Version: 103.0.1264.77 Modules
| |||||||||||||||
| 444 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=renderer --no-appcompat-clear --disable-gpu-compositing --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=12 --mojo-platform-channel-handle=5096 --field-trial-handle=2132,i,4376602714035184738,16510944388497468200,262144 --variations-seed-version /prefetch:1 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.92 Modules
| |||||||||||||||
| 704 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=5080 --field-trial-handle=2132,i,4376602714035184738,16510944388497468200,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.92 Modules
| |||||||||||||||
| 816 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --explicitly-allowed-ports=8000 --disable-gpu --new-window --flag-switches-begin --flag-switches-end --do-not-de-elevate http://127.0.0.1:8000/0ad0faf0/42246678 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.92 Modules
| |||||||||||||||
| 948 | --user-data-dir="C:\Users\admin\AppData\Local\Temp\chr9566.tmp" --explicitly-allowed-ports=8000 --disable-gpu --new-window "http://127.0.0.1:8000/0ad0faf0/5fdaec0d" | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.92 Modules
| |||||||||||||||
| 996 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=network.mojom.NetworkService --lang=en-US --service-sandbox-type=none --no-appcompat-clear --mojo-platform-channel-handle=2124 --field-trial-handle=2032,i,18391847662070447746,13414939250201206841,262144 --variations-seed-version /prefetch:3 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.92 Modules
| |||||||||||||||
| 1044 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=entity_extraction_service.mojom.Extractor --lang=en-US --service-sandbox-type=entity_extraction --onnx-enabled-for-ee --no-appcompat-clear --mojo-platform-channel-handle=7420 --field-trial-handle=2132,i,4376602714035184738,16510944388497468200,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Version: 122.0.2365.92 Modules
| |||||||||||||||
Total events
47 839
Read events
47 409
Write events
407
Delete events
23
Modification events
| (PID) Process: | (3816) msedge.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (3816) msedge.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
| (PID) Process: | (3816) msedge.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Edge\ThirdParty |
| Operation: | write | Name: | StatusCodes |
Value: | |||
| (PID) Process: | (3816) msedge.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Edge\ThirdParty |
| Operation: | write | Name: | StatusCodes |
Value: 01000000 | |||
| (PID) Process: | (3816) msedge.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | state |
Value: 1 | |||
| (PID) Process: | (3816) msedge.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\EdgeUpdate\ClientState\{56EB18F8-B008-4CBD-B6D2-8C97FE7E9062} |
| Operation: | write | Name: | dr |
Value: 1 | |||
| (PID) Process: | (3816) msedge.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Edge |
| Operation: | write | Name: | UsageStatsInSample |
Value: 1 | |||
| (PID) Process: | (5512) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (5512) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (5512) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
Executable files
69
Suspicious files
1 284
Text files
251
Unknown types
1
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3816 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Profile 1\discounts_db\LOG.old~RF16333a.TMP | — | |
MD5:— | SHA256:— | |||
| 3816 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Profile 1\parcel_tracking_db\LOG.old~RF16333a.TMP | — | |
MD5:— | SHA256:— | |||
| 3816 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Profile 1\discounts_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 3816 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Profile 1\commerce_subscription_db\LOG.old~RF16333a.TMP | — | |
MD5:— | SHA256:— | |||
| 3816 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Profile 1\commerce_subscription_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 3816 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Profile 1\PersistentOriginTrials\LOG.old~RF16333a.TMP | — | |
MD5:— | SHA256:— | |||
| 3816 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Profile 1\PersistentOriginTrials\LOG.old | — | |
MD5:— | SHA256:— | |||
| 3816 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Profile 1\EdgePushStorageWithConnectTokenAndKey\LOG.old~RF163349.TMP | — | |
MD5:— | SHA256:— | |||
| 3816 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Profile 1\EdgePushStorageWithConnectTokenAndKey\LOG.old | — | |
MD5:— | SHA256:— | |||
| 3816 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Profile 1\parcel_tracking_db\LOG.old | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
76
TCP/UDP connections
257
DNS requests
260
Threats
23
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2352 | smartscreen.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEApDqVCbATUviZV57HIIulA%3D | unknown | — | — | whitelisted |
2352 | smartscreen.exe | GET | 200 | 199.232.210.172:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?94d365f90bd0cd77 | unknown | — | — | whitelisted |
4404 | svchost.exe | HEAD | 200 | 199.232.210.172:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/5d32607d-eea9-44fc-ac55-77800b9862a5?P1=1744953271&P2=404&P3=2&P4=Wh7PqIht0NiQJwpMkZ1DxauYIKVNo8kXWwLqdgfXb9khzmqQGOIH0PutTPeW2uxUU9eREcuJ20tF31xlLI%2bMGA%3d%3d | unknown | — | — | whitelisted |
2768 | svchost.exe | GET | 200 | 199.232.214.172:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/pinrulesstl.cab?1d5b84cd7c0ff512 | unknown | — | — | whitelisted |
4404 | svchost.exe | GET | 206 | 199.232.210.172:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/5d32607d-eea9-44fc-ac55-77800b9862a5?P1=1744953271&P2=404&P3=2&P4=Wh7PqIht0NiQJwpMkZ1DxauYIKVNo8kXWwLqdgfXb9khzmqQGOIH0PutTPeW2uxUU9eREcuJ20tF31xlLI%2bMGA%3d%3d | unknown | — | — | whitelisted |
6220 | dfsvc.exe | GET | 200 | 199.232.214.172:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab?2acd7b0de79f21c2 | unknown | — | — | whitelisted |
2768 | svchost.exe | GET | 200 | 199.232.214.172:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/pinrulesstl.cab?4dd4673b063e3e0b | unknown | — | — | whitelisted |
2768 | svchost.exe | GET | 200 | 199.232.214.172:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab?888ed9d23ef7362b | unknown | — | — | whitelisted |
1352 | svchost.exe | GET | 200 | 184.24.77.24:80 | http://www.msftconnecttest.com/connecttest.txt | unknown | — | — | whitelisted |
4404 | svchost.exe | GET | 206 | 199.232.210.172:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/5d32607d-eea9-44fc-ac55-77800b9862a5?P1=1744953271&P2=404&P3=2&P4=Wh7PqIht0NiQJwpMkZ1DxauYIKVNo8kXWwLqdgfXb9khzmqQGOIH0PutTPeW2uxUU9eREcuJ20tF31xlLI%2bMGA%3d%3d | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
1352 | svchost.exe | 184.24.77.4:80 | — | Akamai International B.V. | DE | unknown |
2352 | smartscreen.exe | 20.191.45.158:443 | checkappexec.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
2352 | smartscreen.exe | 199.232.210.172:80 | ctldl.windowsupdate.com | FASTLY | US | whitelisted |
3952 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
3816 | msedge.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
2352 | smartscreen.exe | 2.17.190.73:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
2528 | msedge.exe | 13.107.42.16:443 | config.edge.skype.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
2528 | msedge.exe | 142.250.185.110:443 | clients2.google.com | GOOGLE | US | whitelisted |
2528 | msedge.exe | 150.171.28.11:443 | edge.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
2528 | msedge.exe | 13.107.6.158:443 | business.bing.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
checkappexec.microsoft.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
ctldl.windowsupdate.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
config.edge.skype.com |
| whitelisted |
vidorium.com |
| unknown |
edge.microsoft.com |
| whitelisted |
clients2.google.com |
| whitelisted |
edge-mobile-static.azureedge.net |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2528 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] Requests to a free CDN for open source projects (jsdelivr .net) |
2528 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] Requests to a free CDN for open source projects (jsdelivr .net) |
2528 | msedge.exe | Misc activity | INFO [ANY.RUN] Possible short link service (t .co) |
2528 | msedge.exe | Misc activity | INFO [ANY.RUN] Possible short link service (t .co) |
2528 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] Requests to a free CDN for open source projects (jsdelivr .net) |
2528 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] Requests to a free CDN for open source projects (jsdelivr .net) |
1352 | svchost.exe | Misc activity | ET INFO Microsoft Connection Test |
1664 | svchost.exe | Misc activity | ET INFO External IP Lookup Domain (ipify .org) in DNS Lookup |
4816 | VidoriumApp.exe | Misc activity | ET INFO External IP Address Lookup Domain (ipify .org) in TLS SNI |
4816 | VidoriumApp.exe | Misc activity | ET INFO External IP Address Lookup Domain (ipify .org) in TLS SNI |
Process | Message |
|---|---|
dfsvc.exe |
*** Status originated: -1073741811
*** Source File: onecore\com\netfx\windowsbuilt\iso_legacy\base\isolation\hier_hierarchy.cpp, line 231
|
dfsvc.exe |
*** Status originated: -1073741811
*** Source File: onecore\com\netfx\windowsbuilt\iso_legacy\base\isolation\hier_hierarchy.cpp, line 231
|
dfsvc.exe |
*** Status originated: -1073741811
*** Source File: onecore\com\netfx\windowsbuilt\iso_legacy\base\isolation\hier_hierarchy.cpp, line 231
|
dfsvc.exe |
*** Status originated: -1073741811
*** Source File: onecore\com\netfx\windowsbuilt\iso_legacy\base\isolation\hier_hierarchy.cpp, line 231
|
dfsvc.exe |
*** Status originated: -1073741811
*** Source File: onecore\com\netfx\windowsbuilt\iso_legacy\base\isolation\hier_hierarchy.cpp, line 231
|
dfsvc.exe |
*** Status originated: -1073741772
*** Source File: onecore\com\netfx\windowsbuilt\iso_legacy\base\isolation\win32\isoreg_direct.cpp, line 1128
|
msedgewebview2.exe | RecursiveDirectoryCreate( C:\Users\admin\AppData\Local\VidoriumApp directory exists )
|
chrome.exe | RecursiveDirectoryCreate( C:\Users\admin\AppData\Local\Temp\chr83B2.tmp directory exists )
|
msedge.exe | RecursiveDirectoryCreate( C:\Users\admin\AppData\Local\Temp\chr9566.tmp directory exists )
|
msedge.exe | RecursiveDirectoryCreate( C:\Users\admin\AppData\Local\Temp\chr98D2.tmp directory exists )
|