| File name: | WinX86.exe |
| Full analysis: | https://app.any.run/tasks/fd36a8ea-c8cc-4461-9700-d8677679b3f7 |
| Verdict: | Malicious activity |
| Threats: | njRAT is a remote access trojan. It is one of the most widely accessible RATs on the market that features an abundance of educational information. Interested attackers can even find tutorials on YouTube. This allows it to become one of the most popular RATs in the world. |
| Analysis date: | November 08, 2023, 20:13:28 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386 Mono/.Net assembly, for MS Windows |
| MD5: | E7911FE55C371AAF85439A93CB91F8B2 |
| SHA1: | 7A2F9769D0B791535094ACF0B3978A55E8BF7E7E |
| SHA256: | 2C243B892B18C6589F54CA1C0BB7268F5B675742F340191DD6105C5984FBE87C |
| SSDEEP: | 768:+H6AO87FFXg8z/JLJqqiD8ZuSNupXYcI:+aAOkTXdzRL8E3NmX |
MALICIOUS
Drops the executable file immediately after the start
- WinX86.exe (PID: 3416)
- WinX86.exe (PID: 3544)
Create files in the Startup directory
- WinX86.exe (PID: 3544)
NjRAT is detected
- WinX86.exe (PID: 3544)
NJRAT has been detected (YARA)
- WinX86.exe (PID: 3544)
Changes the autorun value in the registry
- WinX86.exe (PID: 3544)
SUSPICIOUS
Starts itself from another location
- WinX86.exe (PID: 3416)
Reads the Internet Settings
- WinX86.exe (PID: 3416)
Uses NETSH.EXE to add a firewall rule or allowed programs
- WinX86.exe (PID: 3544)
Connects to unusual port
- WinX86.exe (PID: 3544)
INFO
Checks supported languages
- WinX86.exe (PID: 3416)
- WinX86.exe (PID: 3544)
- Builder.exe (PID: 3752)
- builder.exe (PID: 4052)
Create files in a temporary directory
- WinX86.exe (PID: 3416)
Reads the computer name
- WinX86.exe (PID: 3416)
- WinX86.exe (PID: 3544)
- Builder.exe (PID: 3752)
- builder.exe (PID: 4052)
Reads the machine GUID from the registry
- WinX86.exe (PID: 3416)
- WinX86.exe (PID: 3544)
- builder.exe (PID: 4052)
Reads Environment values
- WinX86.exe (PID: 3544)
Manual execution by a user
- WinRAR.exe (PID: 3604)
- Builder.exe (PID: 3752)
- Builder.exe (PID: 3840)
- builder.exe (PID: 4052)
- notepad.exe (PID: 4088)
Drops the executable file immediately after the start
- WinRAR.exe (PID: 3604)
Creates files or folders in the user directory
- WinX86.exe (PID: 3544)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
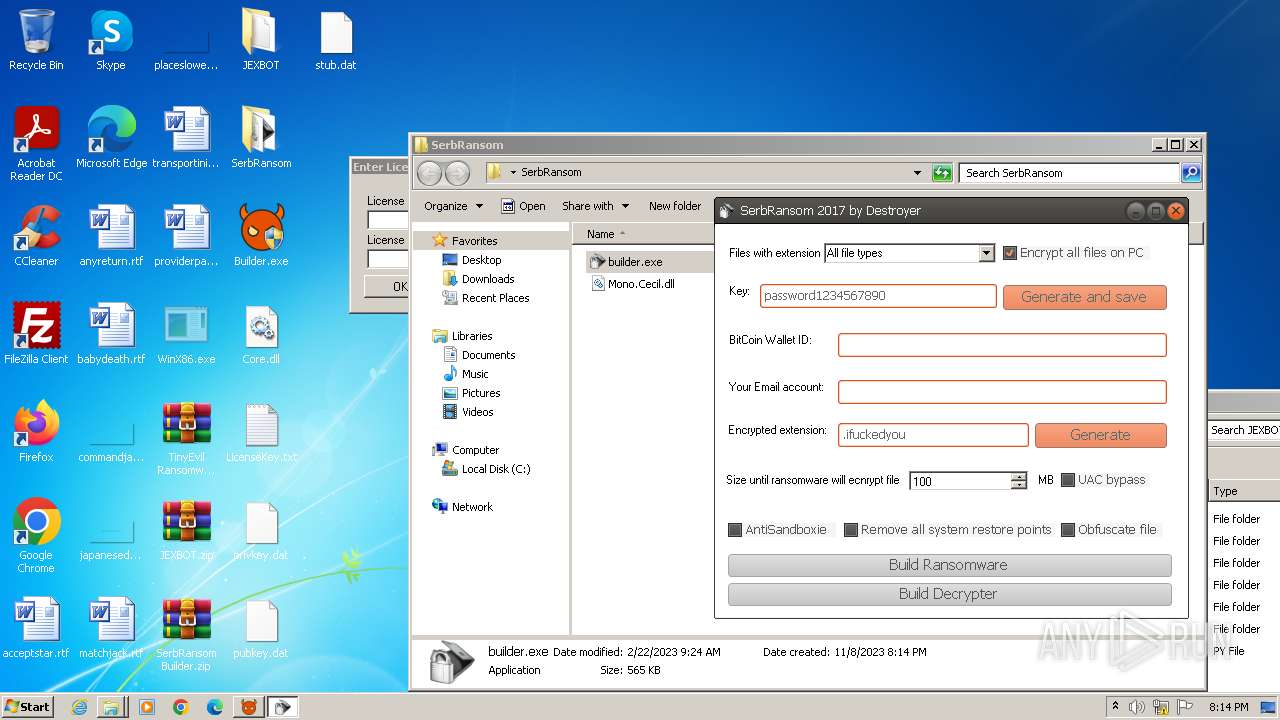
NjRat
(PID) Process(3544) WinX86.exe
C2VirusHack.freeddns.org
Ports1177
BotnetHacKed
Options
Auto-run registry keySoftware\Microsoft\Windows\CurrentVersion\Run\53710d2386d6e092dc178b8198b73fb8
Splitter|'|'|
Versionim523
TRiD
| .exe | | | Generic CIL Executable (.NET, Mono, etc.) (56.7) |
|---|---|---|
| .exe | | | Win64 Executable (generic) (21.3) |
| .scr | | | Windows screen saver (10.1) |
| .dll | | | Win32 Dynamic Link Library (generic) (5) |
| .exe | | | Win32 Executable (generic) (3.4) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2023:10:30 11:19:56+01:00 |
| ImageFileCharacteristics: | Executable, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 8 |
| CodeSize: | 35840 |
| InitializedDataSize: | 1536 |
| UninitializedDataSize: | - |
| EntryPoint: | 0xabce |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
Total processes
48
Monitored processes
8
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 3416 | "C:\Users\admin\Desktop\WinX86.exe" | C:\Users\admin\Desktop\WinX86.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 3508 | netsh firewall add allowedprogram "C:\Users\admin\AppData\Local\Temp\WinX86.exe" "WinX86.exe" ENABLE | C:\Windows\System32\netsh.exe | — | WinX86.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Network Command Shell Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3544 | "C:\Users\admin\AppData\Local\Temp\WinX86.exe" | C:\Users\admin\AppData\Local\Temp\WinX86.exe | WinX86.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
NjRat(PID) Process(3544) WinX86.exe C2VirusHack.freeddns.org Ports1177 BotnetHacKed Options Auto-run registry keySoftware\Microsoft\Windows\CurrentVersion\Run\53710d2386d6e092dc178b8198b73fb8 Splitter|'|'| Versionim523 | |||||||||||||||
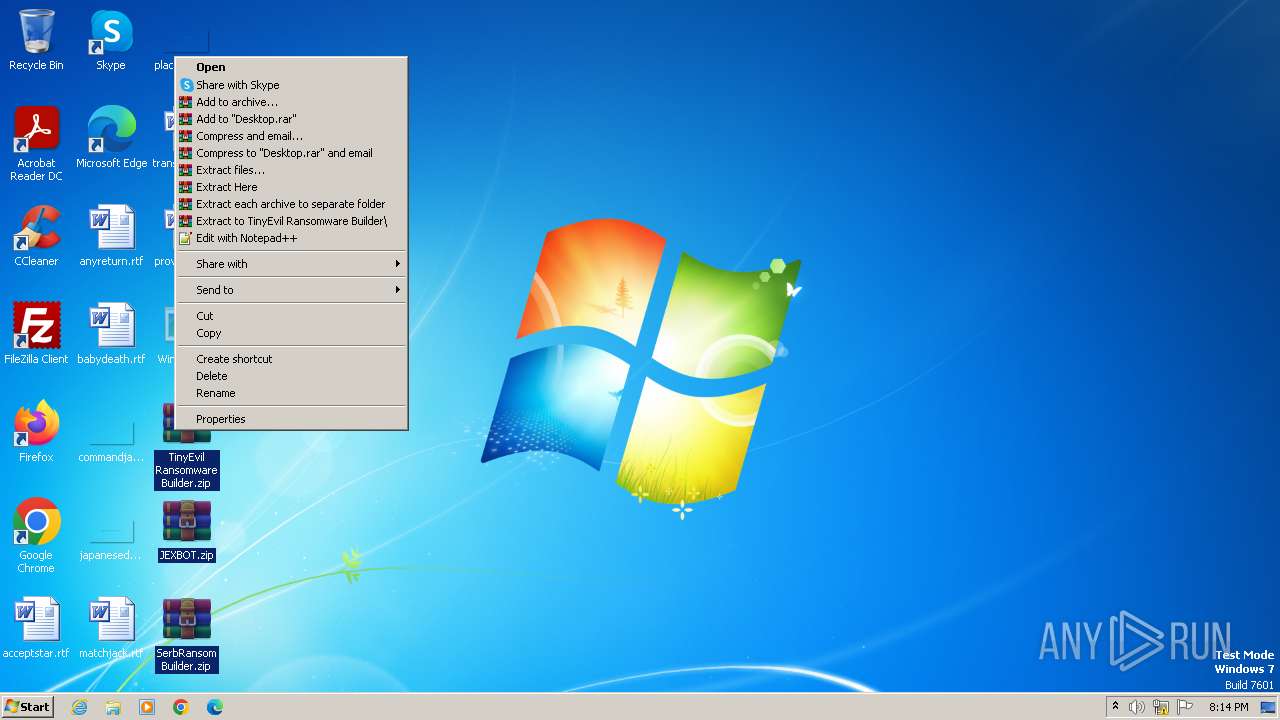
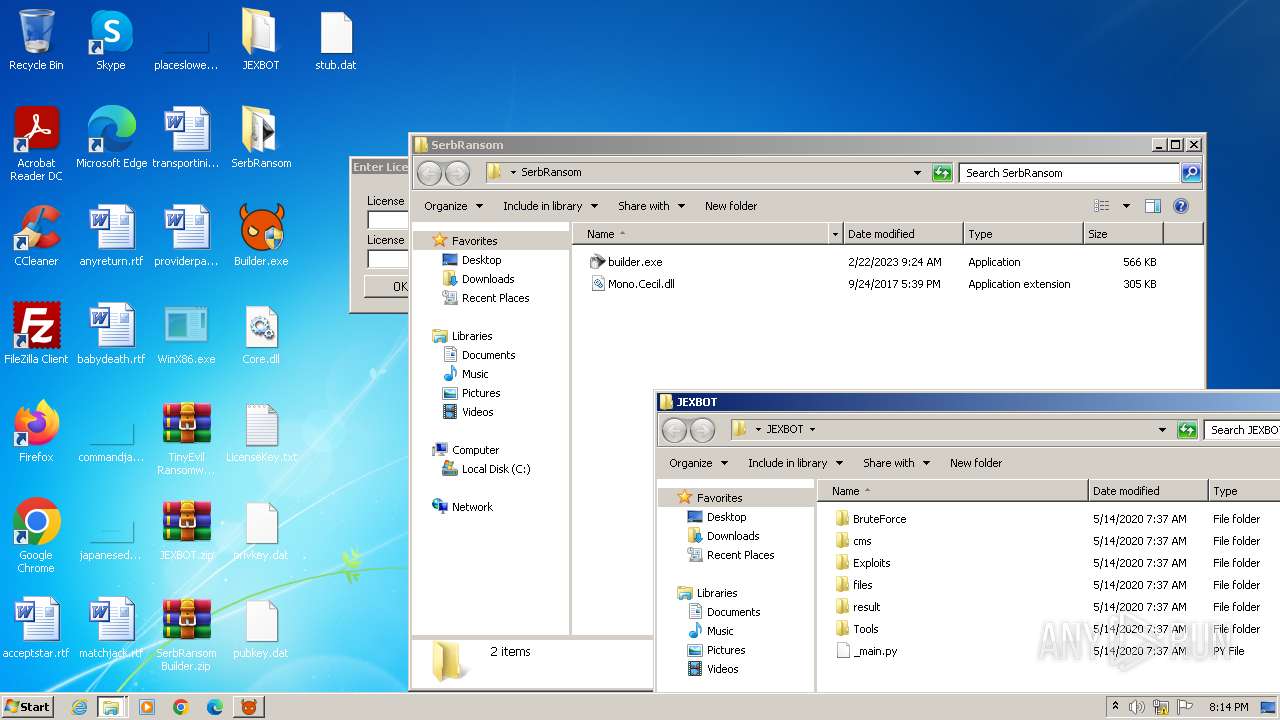
| 3604 | "C:\Program Files\WinRAR\WinRAR.exe" x -iext -ow -ver "-an=C:\Users\admin\Desktop\TinyEvil Ransomware Builder.zip" "-an=C:\Users\admin\Desktop\JEXBOT.zip" -- "C:\Users\admin\Desktop\SerbRansom Builder.zip" C:\Users\admin\Desktop\ | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 3752 | "C:\Users\admin\Desktop\Builder.exe" | C:\Users\admin\Desktop\Builder.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Description: TinyEvil Builder Exit code: 0 Version: 1.0.1.0 Modules
| |||||||||||||||
| 3840 | "C:\Users\admin\Desktop\Builder.exe" | C:\Users\admin\Desktop\Builder.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: TinyEvil Builder Exit code: 3221226540 Version: 1.0.1.0 Modules
| |||||||||||||||
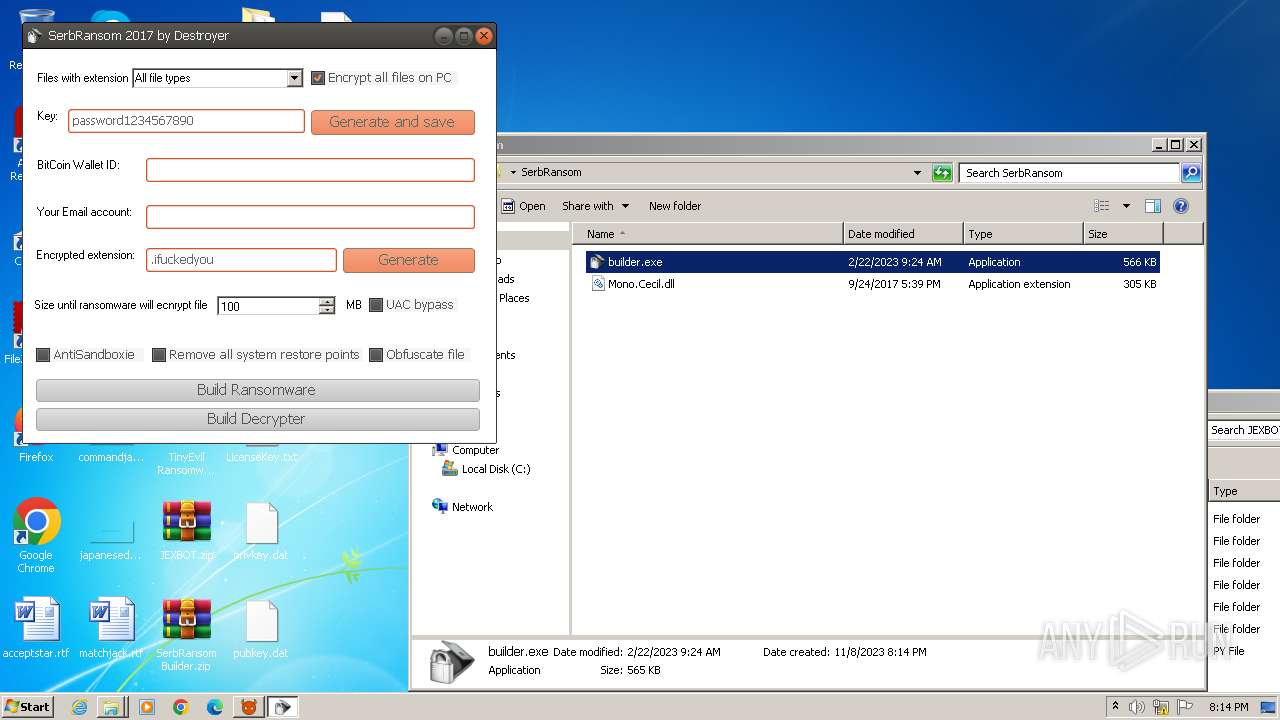
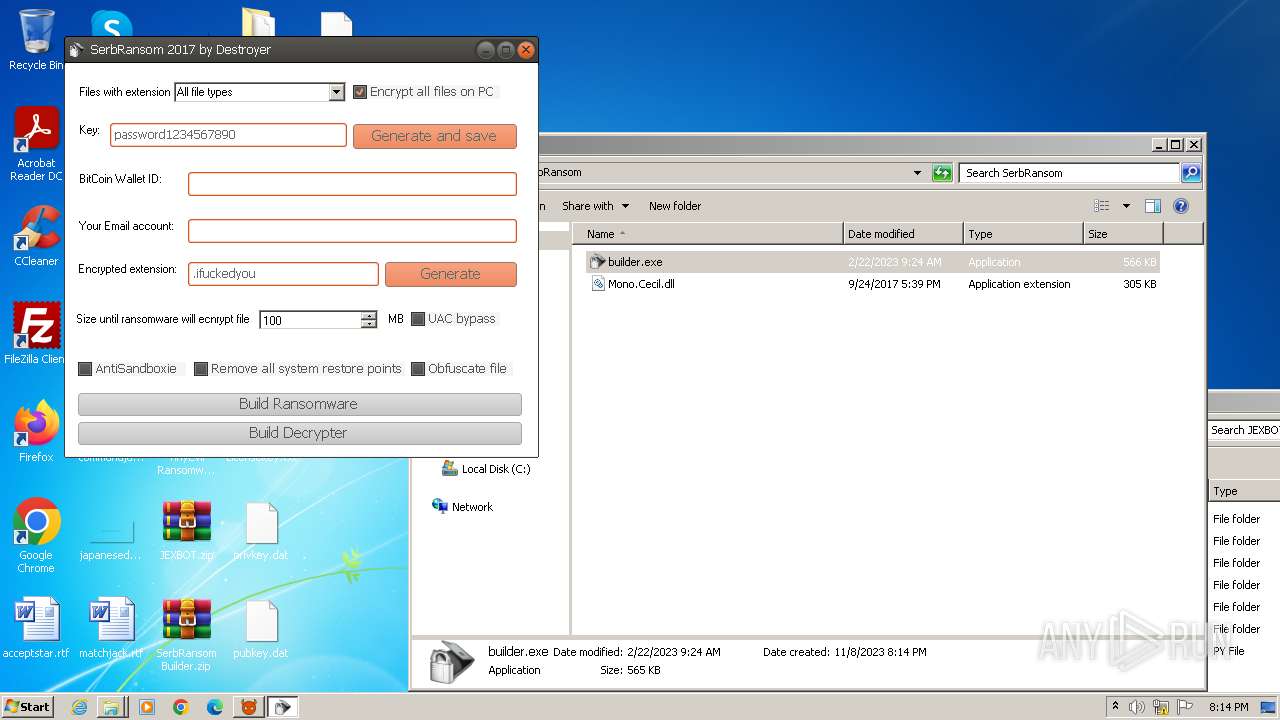
| 4052 | "C:\Users\admin\Desktop\SerbRansom\builder.exe" | C:\Users\admin\Desktop\SerbRansom\builder.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: Ransomware by Destroyer 2017 Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
| 4088 | "C:\Windows\system32\NOTEPAD.EXE" C:\Users\admin\Desktop\LicenseKey.txt | C:\Windows\System32\notepad.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
2 137
Read events
2 001
Write events
136
Delete events
0
Modification events
| (PID) Process: | (3416) WinX86.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (3416) WinX86.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (3416) WinX86.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (3416) WinX86.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (3544) WinX86.exe | Key: | HKEY_CURRENT_USER |
| Operation: | write | Name: | di |
Value: ! | |||
| (PID) Process: | (3508) netsh.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\17A\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3544) WinX86.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run |
| Operation: | write | Name: | 53710d2386d6e092dc178b8198b73fb8 |
Value: "C:\Users\admin\AppData\Local\Temp\WinX86.exe" .. | |||
| (PID) Process: | (3604) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3604) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3604) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
Executable files
7
Suspicious files
4
Text files
157
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3544 | WinX86.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\53710d2386d6e092dc178b8198b73fb8.exe | executable | |
MD5:E7911FE55C371AAF85439A93CB91F8B2 | SHA256:2C243B892B18C6589F54CA1C0BB7268F5B675742F340191DD6105C5984FBE87C | |||
| 3604 | WinRAR.exe | C:\Users\admin\Desktop\privkey.dat | text | |
MD5:0AD8858EEA2ECBD131BE587B503EDC65 | SHA256:A9C62A8AA361D36AB382739FDB14853773A6BEA4ABA1054D9B53F1FF22A58DDC | |||
| 3604 | WinRAR.exe | C:\Users\admin\Desktop\pubkey.dat | text | |
MD5:97526A5A909388144BC1A2DA2678B40E | SHA256:A9A7BAA57A1D7761C53E5D478E1BC2280B5046B647E34FE4212FF0FF6C01839F | |||
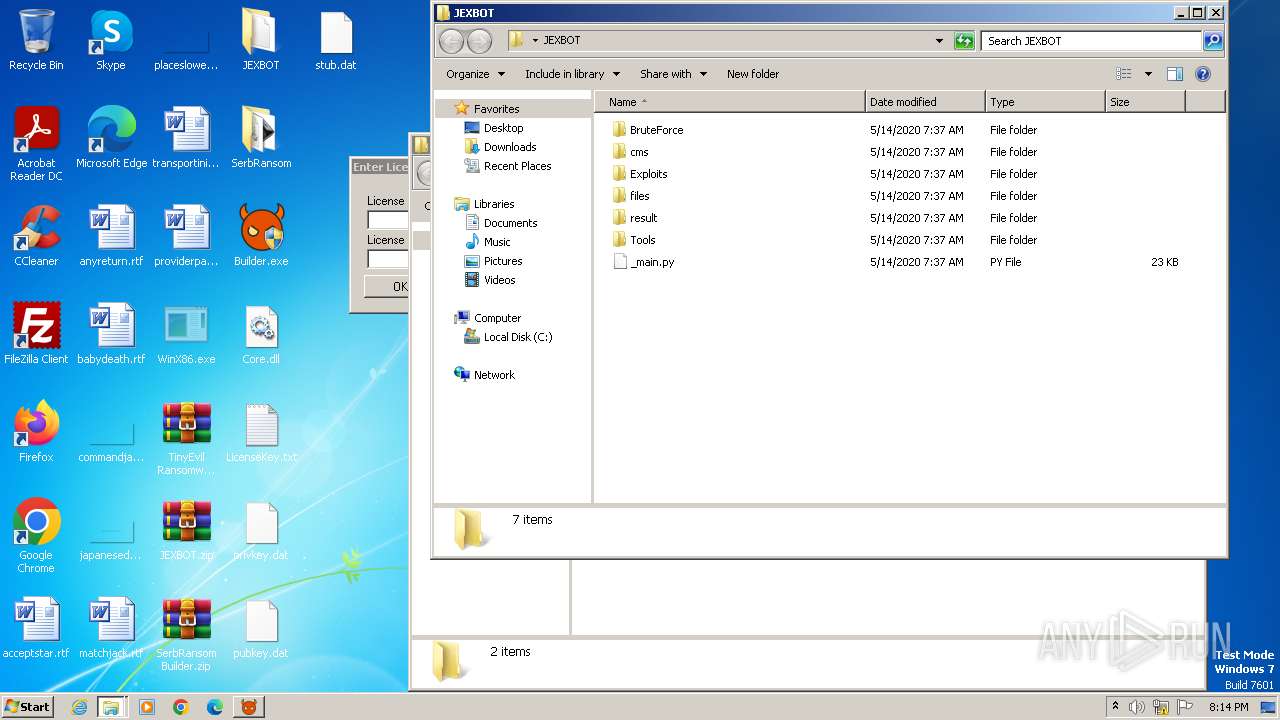
| 3604 | WinRAR.exe | C:\Users\admin\Desktop\JEXBOT\BruteForce\Drupal.py | text | |
MD5:967109130515A9F4B46D8622A9D61AFA | SHA256:E51A0986BD75D0C853DAA37A43EF6E11DCD7C65C6DF03B67DC1BE65BCFD052A8 | |||
| 3604 | WinRAR.exe | C:\Users\admin\Desktop\JEXBOT\cms\Wordpress.txt | text | |
MD5:61FB8C9645AC1EBD764F6D1EE1B372A1 | SHA256:EAFD195F0DA75006C0E15AF0A23E0D4FB92E4949336062DF48CA144CBC76F6DE | |||
| 3604 | WinRAR.exe | C:\Users\admin\Desktop\LicenseKey.txt | text | |
MD5:84781A263A5E1D6786A96B002437DB27 | SHA256:A67A9A6C0B1BF1F958B93C9F4ECE35E17FC7E98C0F11662FCC0589C19EAF4DF1 | |||
| 3604 | WinRAR.exe | C:\Users\admin\Desktop\JEXBOT\cms\joomla.txt | text | |
MD5:41DE774D492CA3B43D9DC4B8D26B3F60 | SHA256:AB7BD5F597C32B95058334EA111D7F7959D1D68C11892908FFE54FC0D4218639 | |||
| 3604 | WinRAR.exe | C:\Users\admin\Desktop\JEXBOT\BruteForce\Wordpress.py | text | |
MD5:BC8B72637F6101C8ED81556DEC286221 | SHA256:36BDA6E052EA5F04877D78AD806730AEF4B58327A61817A0D9616942301DF7B7 | |||
| 3604 | WinRAR.exe | C:\Users\admin\Desktop\stub.dat | executable | |
MD5:FFCB204A9D64F132960167CA7B380DCD | SHA256:A4E4AA7C4593DE0791B2C19E14EDC41CC612F26061AAC31A6366776692715D6D | |||
| 3604 | WinRAR.exe | C:\Users\admin\Desktop\JEXBOT\BruteForce\Opencart.py | text | |
MD5:9FADE6269AA69F00A6D9B61873309288 | SHA256:457BD4F2D7B30EE702436B1E473B3E14E82FD653B4DF4C047C35C33A2902CAEE | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
8
DNS requests
1
Threats
1
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2588 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
3544 | WinX86.exe | 197.34.178.217:1177 | VirusHack.freeddns.org | TE-AS | EG | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
VirusHack.freeddns.org |
| unknown |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1080 | svchost.exe | Potentially Bad Traffic | ET INFO DYNAMIC_DNS Query to a *.freeddns .org Domain |