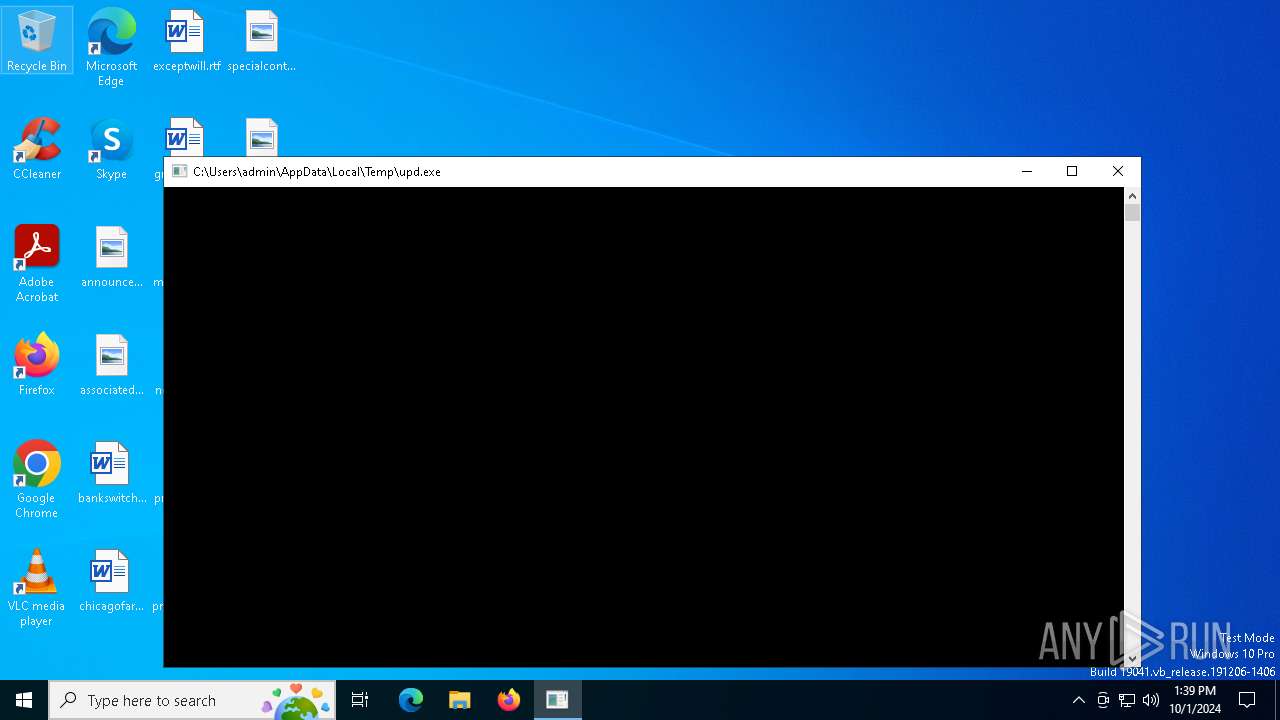
| download: | /app/upd.exe |
| Full analysis: | https://app.any.run/tasks/6a18fe33-1047-4738-89dc-0c80b82f1202 |
| Verdict: | Malicious activity |
| Threats: | MetaStealer is an info-stealing malware primarily targeting sensitive data like login credentials, payment details, and browser history. It typically infects systems via phishing emails or malicious downloads and can exfiltrate data to a command and control (C2) server. MetaStealer is known for its stealthy techniques, including evasion and persistence mechanisms, which make it difficult to detect. This malware has been actively used in various cyberattacks, particularly for financial theft and credential harvesting from individuals and organizations. |
| Analysis date: | October 01, 2024, 13:39:01 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (console) Intel 80386 Mono/.Net assembly, for MS Windows |
| MD5: | A549BF16626F77D157EC22CF3DF30090 |
| SHA1: | 4BC271C9394746A18DCE93874623C505AC43E2A3 |
| SHA256: | 2C23D6102086BE047725664D1E28A1C4366D51AE476EA80416E599584E95D163 |
| SSDEEP: | 12288:yL43c0HNjo2bGydAnjXuUx0QDy7ZPwG0mb8aPnCPRjHo9Np9Ix6mrGdzt9:yL43FtjoWGydAn7uUx0Yy7ZPw |
MALICIOUS
Connects to the CnC server
- MSBuild.exe (PID: 1360)
METASTEALER has been detected (SURICATA)
- MSBuild.exe (PID: 1360)
REDLINE has been detected (SURICATA)
- MSBuild.exe (PID: 1360)
Stealers network behavior
- MSBuild.exe (PID: 1360)
REDLINE has been detected (YARA)
- MSBuild.exe (PID: 1360)
SUSPICIOUS
Executable content was dropped or overwritten
- upd.exe (PID: 2240)
Checks for external IP
- svchost.exe (PID: 2256)
- MSBuild.exe (PID: 1360)
Potential Corporate Privacy Violation
- MSBuild.exe (PID: 1360)
INFO
Manual execution by a user
- firefox.exe (PID: 1696)
Application launched itself
- firefox.exe (PID: 1696)
- firefox.exe (PID: 2468)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
RedLine
(PID) Process(1360) MSBuild.exe
C2 (1)185.215.113.22:80
Botnet@purple_dxxd
Options
ErrorMessage
Keys
XorAnacrustic
TRiD
| .dll | | | Win32 Dynamic Link Library (generic) (38.3) |
|---|---|---|
| .exe | | | Win32 Executable (generic) (26.2) |
| .exe | | | Win16/32 Executable Delphi generic (12) |
| .exe | | | Generic Win/DOS Executable (11.6) |
| .exe | | | DOS Executable Generic (11.6) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2024:09:17 19:13:40+00:00 |
| ImageFileCharacteristics: | Executable, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 11 |
| CodeSize: | 79360 |
| InitializedDataSize: | 346624 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x6e00a |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 4 |
| Subsystem: | Windows command line |
| FileVersionNumber: | 0.0.3.4 |
| ProductVersionNumber: | 0.0.3.4 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
| Comments: | Shaping immersive experiences through visionary optics and digital innovation. |
| CompanyName: | ThinkVision Technologies Inc. |
| FileDescription: | ThinkVision Systems |
| FileVersion: | 0.0.3.4 |
| InternalName: | JackPeloci802Zachary.jar |
| LegalCopyright: | Copyright © 2026 |
| LegalTrademarks: | ThinkVision Technologies Trademark |
| OriginalFileName: | JackPeloci802Zachary.jar |
| ProductName: | ThinkVision OptiTech Suite |
| ProductVersion: | 0.0.3.4 |
| AssemblyVersion: | 0.0.0.0 |
Total processes
143
Monitored processes
14
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1360 | "C:\Windows\Microsoft.NET\Framework\v4.0.30319\MSBuild.exe" | C:\Windows\Microsoft.NET\Framework\v4.0.30319\MSBuild.exe | upd.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: MSBuild.exe Exit code: 0 Version: 4.8.9037.0 built by: NET481REL1 Modules
RedLine(PID) Process(1360) MSBuild.exe C2 (1)185.215.113.22:80 Botnet@purple_dxxd Options ErrorMessage Keys XorAnacrustic | |||||||||||||||
| 1536 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel=5440 -childID 3 -isForBrowser -prefsHandle 5616 -prefMapHandle 4768 -prefsLen 31161 -prefMapSize 244343 -jsInitHandle 1540 -jsInitLen 235124 -parentBuildID 20240213221259 -win32kLockedDown -appDir "C:\Program Files\Mozilla Firefox\browser" - {47324ef6-bed3-4d1d-bdfb-4f7c96a76f5a} 2468 "\\.\pipe\gecko-crash-server-pipe.2468" 1feb53d94d0 tab | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: LOW Description: Firefox Version: 123.0 Modules
| |||||||||||||||
| 1556 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel=5996 -childID 5 -isForBrowser -prefsHandle 6000 -prefMapHandle 6004 -prefsLen 31161 -prefMapSize 244343 -jsInitHandle 1540 -jsInitLen 235124 -parentBuildID 20240213221259 -win32kLockedDown -appDir "C:\Program Files\Mozilla Firefox\browser" - {9bd74d01-ce76-48dc-b137-48a21aa9e5af} 2468 "\\.\pipe\gecko-crash-server-pipe.2468" 1feb53c1d90 tab | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: LOW Description: Firefox Version: 123.0 Modules
| |||||||||||||||
| 1696 | "C:\Program Files\Mozilla Firefox\firefox.exe" | C:\Program Files\Mozilla Firefox\firefox.exe | — | explorer.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Exit code: 0 Version: 123.0 Modules
| |||||||||||||||
| 2240 | "C:\Users\admin\AppData\Local\Temp\upd.exe" | C:\Users\admin\AppData\Local\Temp\upd.exe | explorer.exe | ||||||||||||
User: admin Company: ThinkVision Technologies Inc. Integrity Level: MEDIUM Description: ThinkVision Systems Exit code: 0 Version: 0.0.3.4 Modules
| |||||||||||||||
| 2256 | C:\WINDOWS\system32\svchost.exe -k NetworkService -p -s Dnscache | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2468 | "C:\Program Files\Mozilla Firefox\firefox.exe" | C:\Program Files\Mozilla Firefox\firefox.exe | firefox.exe | ||||||||||||
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Version: 123.0 Modules
| |||||||||||||||
| 2952 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel=1816 -parentBuildID 20240213221259 -prefsHandle 1844 -prefMapHandle 1836 -prefsLen 30537 -prefMapSize 244343 -appDir "C:\Program Files\Mozilla Firefox\browser" - {00a509c8-4fcb-4509-8f00-4897b9e3d6c6} 2468 "\\.\pipe\gecko-crash-server-pipe.2468" 1fead3e7d10 gpu | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: LOW Description: Firefox Version: 123.0 Modules
| |||||||||||||||
| 4092 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel=4620 -childID 2 -isForBrowser -prefsHandle 4628 -prefMapHandle 4624 -prefsLen 36263 -prefMapSize 244343 -jsInitHandle 1540 -jsInitLen 235124 -parentBuildID 20240213221259 -win32kLockedDown -appDir "C:\Program Files\Mozilla Firefox\browser" - {e03dde00-e7f9-44f7-8bd0-ce87945572b1} 2468 "\\.\pipe\gecko-crash-server-pipe.2468" 1feb4631a10 tab | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: LOW Description: Firefox Version: 123.0 Modules
| |||||||||||||||
| 6112 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel=5424 -parentBuildID 20240213221259 -sandboxingKind 0 -prefsHandle 5192 -prefMapHandle 4336 -prefsLen 34713 -prefMapSize 244343 -win32kLockedDown -appDir "C:\Program Files\Mozilla Firefox\browser" - {e2bb3a72-4bee-4e24-a040-cabeba6ab785} 2468 "\\.\pipe\gecko-crash-server-pipe.2468" 1feb56fdd10 utility | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: LOW Description: Firefox Version: 123.0 Modules
| |||||||||||||||
Total events
13 968
Read events
13 953
Write events
15
Delete events
0
Modification events
| (PID) Process: | (1360) MSBuild.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\MSBuild_RASAPI32 |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
| (PID) Process: | (1360) MSBuild.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\MSBuild_RASAPI32 |
| Operation: | write | Name: | EnableAutoFileTracing |
Value: 0 | |||
| (PID) Process: | (1360) MSBuild.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\MSBuild_RASAPI32 |
| Operation: | write | Name: | EnableConsoleTracing |
Value: 0 | |||
| (PID) Process: | (1360) MSBuild.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\MSBuild_RASAPI32 |
| Operation: | write | Name: | FileTracingMask |
Value: | |||
| (PID) Process: | (1360) MSBuild.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\MSBuild_RASAPI32 |
| Operation: | write | Name: | ConsoleTracingMask |
Value: | |||
| (PID) Process: | (1360) MSBuild.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\MSBuild_RASAPI32 |
| Operation: | write | Name: | MaxFileSize |
Value: 1048576 | |||
| (PID) Process: | (1360) MSBuild.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\MSBuild_RASAPI32 |
| Operation: | write | Name: | FileDirectory |
Value: %windir%\tracing | |||
| (PID) Process: | (1360) MSBuild.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\MSBuild_RASMANCS |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
| (PID) Process: | (1360) MSBuild.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\MSBuild_RASMANCS |
| Operation: | write | Name: | EnableAutoFileTracing |
Value: 0 | |||
| (PID) Process: | (1360) MSBuild.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\MSBuild_RASMANCS |
| Operation: | write | Name: | EnableConsoleTracing |
Value: 0 | |||
Executable files
1
Suspicious files
126
Text files
10
Unknown types
1
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2240 | upd.exe | C:\Users\admin\AppData\Roaming\msvcp110.dll | executable | |
MD5:3AB545CDAFDBB57BFA4F078F7AEB4FC6 | SHA256:BA7DA375D2C40AD31ACDA978D021A8F7AD32C4A95AB79E35097925B71D62F545 | |||
| 2468 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\sessionCheckpoints.json.tmp | binary | |
MD5:EA8B62857DFDBD3D0BE7D7E4A954EC9A | SHA256:792955295AE9C382986222C6731C5870BD0E921E7F7E34CC4615F5CD67F225DA | |||
| 2468 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\storage\permanent\chrome\idb\3870112724rsegmnoittet-es.sqlite | — | |
MD5:— | SHA256:— | |||
| 2468 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\storage\permanent\chrome\idb\3870112724rsegmnoittet-es.sqlite-shm | binary | |
MD5:B7C14EC6110FA820CA6B65F5AEC85911 | SHA256:FD4C9FDA9CD3F9AE7C962B0DDF37232294D55580E1AA165AA06129B8549389EB | |||
| 2468 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\prefs-1.js | text | |
MD5:B7443D58BCB8646220F7D07CC2A78B2C | SHA256:2CCBEE35F43E0006112BAEC9F69A11B2882A505532060D335B1A9B48B2727CC8 | |||
| 2468 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\storage\permanent\chrome\idb\1657114595AmcateirvtiSty.sqlite-shm | binary | |
MD5:B7C14EC6110FA820CA6B65F5AEC85911 | SHA256:FD4C9FDA9CD3F9AE7C962B0DDF37232294D55580E1AA165AA06129B8549389EB | |||
| 2468 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\storage\permanent\chrome\idb\1451318868ntouromlalnodry--epcr.sqlite-shm | binary | |
MD5:B7C14EC6110FA820CA6B65F5AEC85911 | SHA256:FD4C9FDA9CD3F9AE7C962B0DDF37232294D55580E1AA165AA06129B8549389EB | |||
| 2468 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\storage\permanent\chrome\idb\3561288849sdhlie.sqlite-shm | binary | |
MD5:B7C14EC6110FA820CA6B65F5AEC85911 | SHA256:FD4C9FDA9CD3F9AE7C962B0DDF37232294D55580E1AA165AA06129B8549389EB | |||
| 2468 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\SiteSecurityServiceState.bin | binary | |
MD5:C618F0B73DFEE825CD655BA1053608D6 | SHA256:4D0AB3C96EE9770BF850FD8BB7D47DF28A1F6053B04F32CC561E6BB2A179647C | |||
| 2468 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\datareporting\glean\db\data.safe.tmp | dbf | |
MD5:4006DDC2918B16C7EF5516C58373842B | SHA256:269EA23B77EDE0874628BD8611BCC5A3E87E0C44CA8A821C0D028B929D4F468F | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
22
TCP/UDP connections
83
DNS requests
91
Threats
11
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2468 | firefox.exe | POST | 200 | 142.250.181.227:80 | http://o.pki.goog/wr2 | unknown | — | — | whitelisted |
2468 | firefox.exe | POST | 200 | 142.250.181.227:80 | http://o.pki.goog/wr2 | unknown | — | — | whitelisted |
2120 | MoUsoCoreWorker.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
6360 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
6644 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
4792 | SIHClient.exe | GET | 200 | 88.221.169.152:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
4792 | SIHClient.exe | GET | 200 | 88.221.169.152:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
2468 | firefox.exe | GET | 200 | 34.107.221.82:80 | http://detectportal.firefox.com/success.txt?ipv4 | unknown | — | — | whitelisted |
2468 | firefox.exe | GET | 200 | 34.107.221.82:80 | http://detectportal.firefox.com/canonical.html | unknown | — | — | whitelisted |
2468 | firefox.exe | POST | 200 | 95.101.54.107:80 | http://r10.o.lencr.org/ | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
876 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
2120 | MoUsoCoreWorker.exe | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
3888 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4324 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1360 | MSBuild.exe | 185.215.113.22:80 | — | 1337team Limited | SC | malicious |
876 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1360 | MSBuild.exe | 172.67.75.172:443 | api.ip.sb | CLOUDFLARENET | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
api.ip.sb |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
arc.msn.com |
| whitelisted |
fd.api.iris.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1360 | MSBuild.exe | Misc Attack | ET DROP Spamhaus DROP Listed Traffic Inbound group 32 |
1360 | MSBuild.exe | Potentially Bad Traffic | ET INFO Microsoft net.tcp Connection Initialization Activity |
1360 | MSBuild.exe | A Network Trojan was detected | ET MALWARE Redline Stealer TCP CnC Activity |
1360 | MSBuild.exe | A Network Trojan was detected | ET MALWARE [ANY.RUN] RedLine Stealer/MetaStealer Family Related (MC-NMF Authorization) |
1360 | MSBuild.exe | A Network Trojan was detected | ET MALWARE Redline Stealer TCP CnC - Id1Response |
1360 | MSBuild.exe | A Network Trojan was detected | ET MALWARE Redline Stealer TCP CnC Activity |
1360 | MSBuild.exe | A Network Trojan was detected | ET MALWARE Redline Stealer TCP CnC Activity |
1360 | MSBuild.exe | A Network Trojan was detected | ET MALWARE Redline Stealer TCP CnC Activity |
3 ETPRO signatures available at the full report