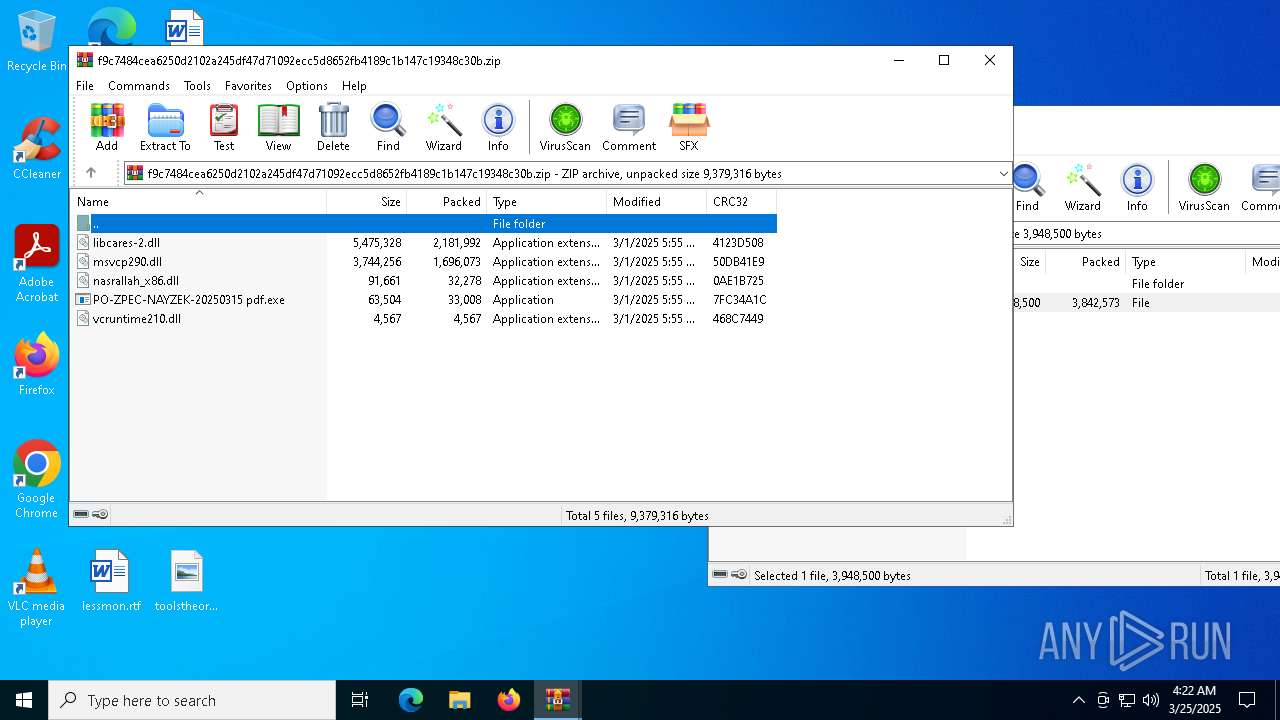
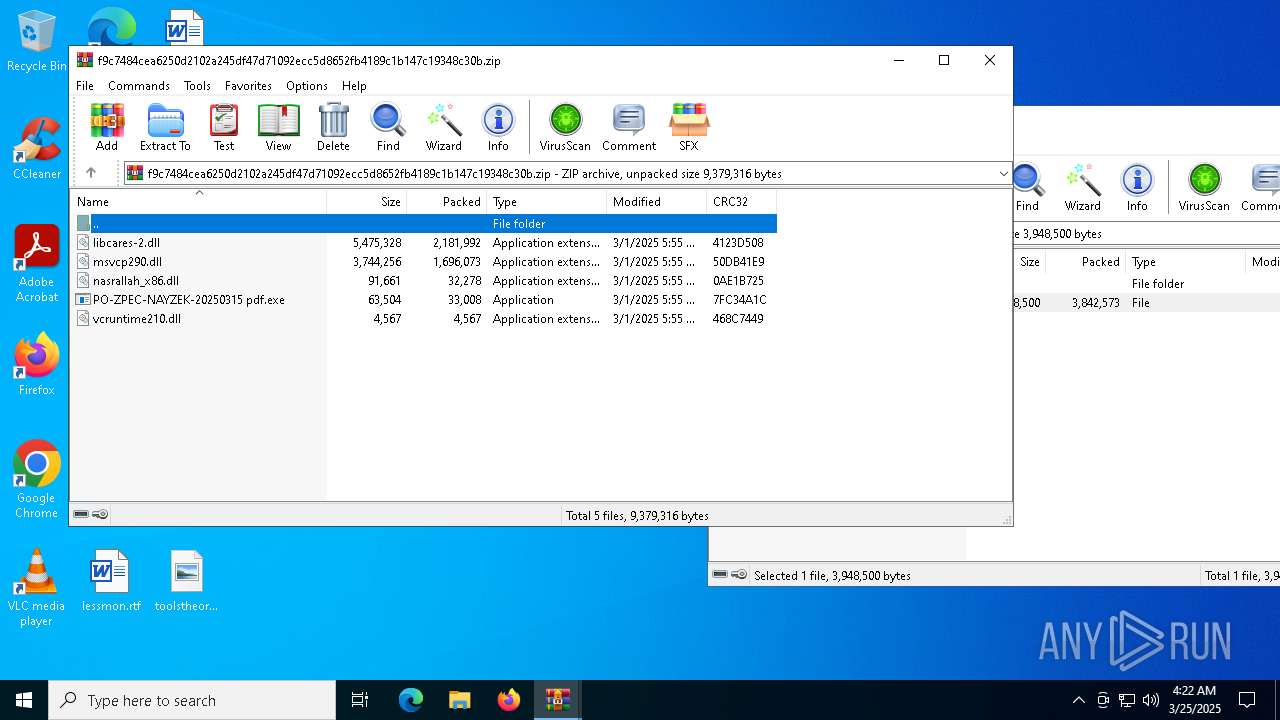
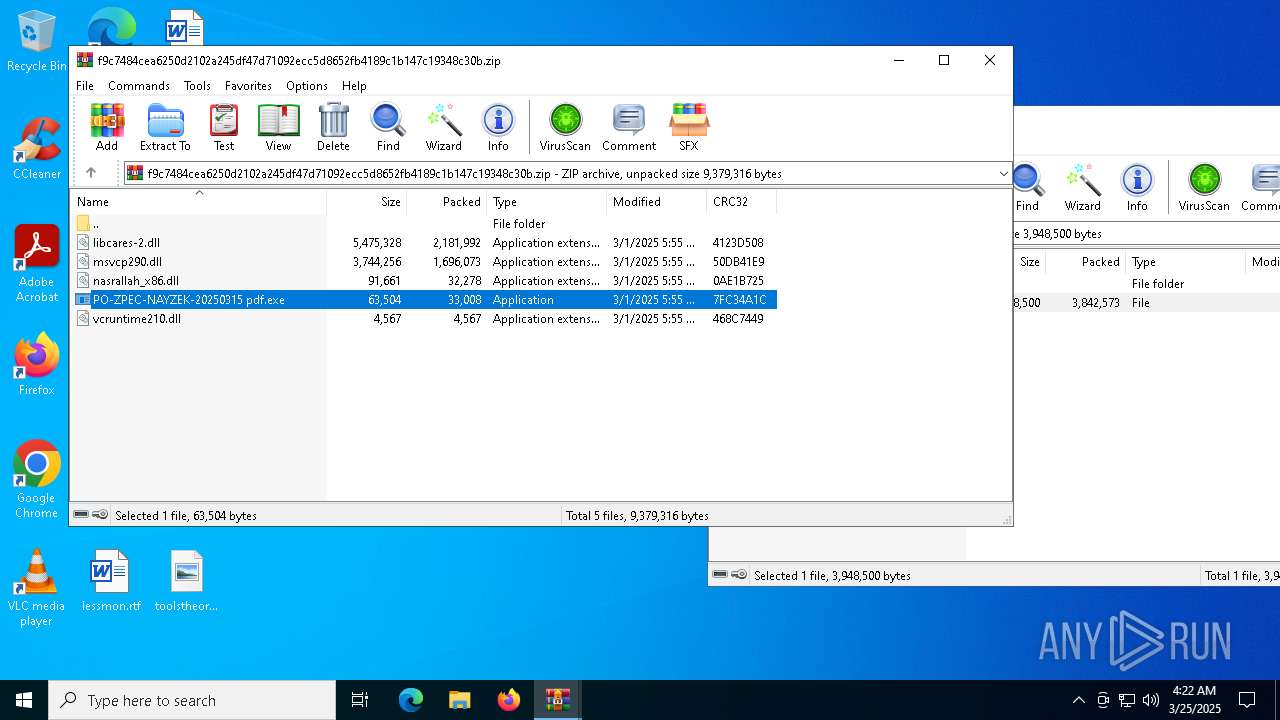
| File name: | 21832394308.zip |
| Full analysis: | https://app.any.run/tasks/f261406d-7656-4c0a-a567-463c04ee06f6 |
| Verdict: | Malicious activity |
| Threats: | A keylogger is a type of spyware that infects a system and has the ability to record every keystroke made on the device. This lets attackers collect personal information of victims, which may include their online banking credentials, as well as personal conversations. The most widespread vector of attack leading to a keylogger infection begins with a phishing email or link. Keylogging is also often present in remote access trojans as part of an extended set of malicious tools. |
| Analysis date: | March 25, 2025, 04:21:53 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=deflate |
| MD5: | 6C10CBB4F281EB96463CC8AA772D9782 |
| SHA1: | A3F3B4A812396842BE73AB5A33A89468638719DC |
| SHA256: | 2BFC738B69E8D715D8A2258C933534E6FBDD05350102016CD26360CCEF9613D0 |
| SSDEEP: | 98304:BrCIoxvJx50Ld5UlVyozeH03VUR5D2jmnYkBRuyUMhe1GFCbOgwk/iHIKcq3t1cM:BoWwydKs |
MALICIOUS
GENERIC has been found (auto)
- WinRAR.exe (PID: 1616)
- WinRAR.exe (PID: 6752)
- PO-ZPEC-NAYZEK-20250315 pdf.exe (PID: 1132)
Adds path to the Windows Defender exclusion list
- PO-ZPEC-NAYZEK-20250315 pdf.exe (PID: 1132)
Generic archive extractor
- WinRAR.exe (PID: 1616)
Changes Windows Defender settings
- PO-ZPEC-NAYZEK-20250315 pdf.exe (PID: 1132)
Changes the autorun value in the registry
- PO-ZPEC-NAYZEK-20250315 pdf.exe (PID: 1132)
SNAKEKEYLOGGER has been detected (SURICATA)
- AddInProcess32.exe (PID: 4944)
Actions looks like stealing of personal data
- AddInProcess32.exe (PID: 4944)
Steals credentials from Web Browsers
- AddInProcess32.exe (PID: 4944)
SUSPICIOUS
Script adds exclusion path to Windows Defender
- PO-ZPEC-NAYZEK-20250315 pdf.exe (PID: 1132)
Starts POWERSHELL.EXE for commands execution
- PO-ZPEC-NAYZEK-20250315 pdf.exe (PID: 1132)
Reads security settings of Internet Explorer
- WinRAR.exe (PID: 6752)
Checks for external IP
- svchost.exe (PID: 2196)
- AddInProcess32.exe (PID: 4944)
Executable content was dropped or overwritten
- PO-ZPEC-NAYZEK-20250315 pdf.exe (PID: 1132)
INFO
Creates files or folders in the user directory
- BackgroundTransferHost.exe (PID: 1012)
Checks supported languages
- PO-ZPEC-NAYZEK-20250315 pdf.exe (PID: 1132)
- AddInProcess32.exe (PID: 4944)
Reads security settings of Internet Explorer
- BackgroundTransferHost.exe (PID: 3240)
- BackgroundTransferHost.exe (PID: 1012)
- BackgroundTransferHost.exe (PID: 5112)
- BackgroundTransferHost.exe (PID: 5960)
- BackgroundTransferHost.exe (PID: 5124)
Checks proxy server information
- BackgroundTransferHost.exe (PID: 1012)
- AddInProcess32.exe (PID: 4944)
Manual execution by a user
- WinRAR.exe (PID: 6752)
Reads the software policy settings
- BackgroundTransferHost.exe (PID: 1012)
- AddInProcess32.exe (PID: 4944)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 6752)
Reads the computer name
- PO-ZPEC-NAYZEK-20250315 pdf.exe (PID: 1132)
- AddInProcess32.exe (PID: 4944)
Disables trace logs
- AddInProcess32.exe (PID: 4944)
Reads the machine GUID from the registry
- AddInProcess32.exe (PID: 4944)
Checks if a key exists in the options dictionary (POWERSHELL)
- powershell.exe (PID: 5352)
Script raised an exception (POWERSHELL)
- powershell.exe (PID: 5352)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | 0x0009 |
| ZipCompression: | Deflated |
| ZipModifyDate: | 1980:00:00 00:00:00 |
| ZipCRC: | 0xfaa31c77 |
| ZipCompressedSize: | 3842573 |
| ZipUncompressedSize: | 3948500 |
| ZipFileName: | f9c7484cea6250d2102a245df47d71092ecc5d8652fb4189c1b147c19348c30b |
Total processes
148
Monitored processes
15
Malicious processes
4
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 896 | C:\WINDOWS\system32\SppExtComObj.exe -Embedding | C:\Windows\System32\SppExtComObj.Exe | — | svchost.exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: KMS Connection Broker Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1012 | "BackgroundTransferHost.exe" -ServerName:BackgroundTransferHost.1 | C:\Windows\System32\BackgroundTransferHost.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Download/Upload Host Exit code: 1 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1132 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa6752.38223\PO-ZPEC-NAYZEK-20250315 pdf.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa6752.38223\PO-ZPEC-NAYZEK-20250315 pdf.exe | WinRAR.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 1616 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\AppData\Local\Temp\21832394308.zip | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.91.0 Modules
| |||||||||||||||
| 2096 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2196 | C:\WINDOWS\system32\svchost.exe -k NetworkService -p -s Dnscache | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3240 | "BackgroundTransferHost.exe" -ServerName:BackgroundTransferHost.1 | C:\Windows\System32\BackgroundTransferHost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Download/Upload Host Exit code: 1 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4008 | "C:\WINDOWS\System32\SLUI.exe" RuleId=3482d82e-ca2c-4e1f-8864-da0267b484b2;Action=AutoActivate;AppId=55c92734-d682-4d71-983e-d6ec3f16059f;SkuId=4de7cb65-cdf1-4de9-8ae8-e3cce27b9f2c;NotificationInterval=1440;Trigger=TimerEvent | C:\Windows\System32\slui.exe | — | SppExtComObj.Exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Activation Client Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4336 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | PO-ZPEC-NAYZEK-20250315 pdf.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4944 | "C:\Windows\Microsoft.NET\Framework\v4.0.30319\AddInProcess32.exe" | C:\Windows\Microsoft.NET\Framework\v4.0.30319\AddInProcess32.exe | PO-ZPEC-NAYZEK-20250315 pdf.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: AddInProcess.exe Version: 4.8.9037.0 built by: NET481REL1 Modules
| |||||||||||||||
Total events
12 610
Read events
12 563
Write events
47
Delete events
0
Modification events
| (PID) Process: | (1616) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (1616) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (1616) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (1616) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\21832394308.zip | |||
| (PID) Process: | (1616) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (1616) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (1616) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (1616) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (1616) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface |
| Operation: | write | Name: | ShowPassword |
Value: 0 | |||
| (PID) Process: | (5124) BackgroundTransferHost.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\CurrentVersion\AppContainer\Storage\microsoft.windows.contentdeliverymanager_cw5n1h2txyewy\Internet Settings\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
Executable files
6
Suspicious files
11
Text files
2
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1012 | BackgroundTransferHost.exe | C:\Users\admin\AppData\Local\Packages\Microsoft.Windows.ContentDeliveryManager_cw5n1h2txyewy\AC\BackgroundTransferApi\e3c58a6f-4988-497b-a689-8136d524716d.down_data | — | |
MD5:— | SHA256:— | |||
| 1616 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb1616.33711\f9c7484cea6250d2102a245df47d71092ecc5d8652fb4189c1b147c19348c30b | compressed | |
MD5:BF810322228B7AA578CF39F1FD77BA19 | SHA256:F9C7484CEA6250D2102A245DF47D71092ECC5D8652FB4189C1B147C19348C30B | |||
| 1012 | BackgroundTransferHost.exe | C:\Users\admin\AppData\Local\Packages\Microsoft.Windows.ContentDeliveryManager_cw5n1h2txyewy\AC\BackgroundTransferApi\e3c58a6f-4988-497b-a689-8136d524716d.be6c9ae1-47cd-4d4a-8346-b334d0ea9851.down_meta | binary | |
MD5:844783A4CF1111173907A9C8ED8FFF65 | SHA256:78A1576252CEF41DC88AF6023E8441715FD724CD6E6D44E8BF68801C5C1D566F | |||
| 6752 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa6752.38223\vcruntime210.dll | binary | |
MD5:8DE8A4C8674230296FBEE9A11635F9B4 | SHA256:3F15A6C253FADC5C01804DC33879687E46AF3ADF8DB46CC8CDC8CF1E6F9B6D4C | |||
| 6752 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa6752.38223\msvcp290.dll | executable | |
MD5:A4212A7A7D7295EBBBFDA999DDC04566 | SHA256:A239AA8CE43E328ACFB73B72CF2DA03F4C4082614C0486895806F14A6094D6F2 | |||
| 6752 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa6752.38223\PO-ZPEC-NAYZEK-20250315 pdf.exe | executable | |
MD5:FD3C8166E7FBBB64D12C1170B8F4BACF | SHA256:A52E245DD7937094711B10C479274A2CCCEA2DFB89F7D4C9F22879214718F92B | |||
| 1012 | BackgroundTransferHost.exe | C:\Users\admin\AppData\Local\Packages\Microsoft.Windows.ContentDeliveryManager_cw5n1h2txyewy\AC\BackgroundTransferApi\f0c6fec0-81c3-4aa6-bcfd-965126837641.up_meta_secure | binary | |
MD5:6F2053619E286E7E2BA3A157C6EC6DF4 | SHA256:0FAB21FD12728DD63236137F68B372B062AD77E6CA2DB95D0B05A50C8032171F | |||
| 6752 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa6752.38223\libcares-2.dll | executable | |
MD5:EAF7469E4D057CA1862C07A947237397 | SHA256:82E9342C53B47C40CDFE9934F61B3841F533F9AF21323830CA9F394854141C49 | |||
| 6752 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa6752.38223\nasrallah_x86.dll | binary | |
MD5:9609A8CA5B9F1D0C6CC371D1699A28DD | SHA256:D01F67BE48F902CE1C3E987379EBB4CD77B919530E9AE306997A635E54D3F348 | |||
| 1132 | PO-ZPEC-NAYZEK-20250315 pdf.exe | C:\Users\admin\SystemRootDoc\msvcp290.dll | executable | |
MD5:A4212A7A7D7295EBBBFDA999DDC04566 | SHA256:A239AA8CE43E328ACFB73B72CF2DA03F4C4082614C0486895806F14A6094D6F2 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
8
TCP/UDP connections
26
DNS requests
17
Threats
7
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
6544 | svchost.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
— | — | GET | 200 | 2.16.164.120:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5436 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
1180 | backgroundTaskHost.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
1012 | BackgroundTransferHost.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
5436 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
4944 | AddInProcess32.exe | GET | 200 | 193.122.6.168:80 | http://checkip.dyndns.org/ | unknown | — | — | whitelisted |
4944 | AddInProcess32.exe | GET | 502 | 193.122.6.168:80 | http://checkip.dyndns.org/ | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 20.73.194.208:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 2.16.164.120:80 | crl.microsoft.com | Akamai International B.V. | NL | whitelisted |
2104 | svchost.exe | 20.73.194.208:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2112 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
3216 | svchost.exe | 40.113.103.199:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6544 | svchost.exe | 40.126.32.133:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6544 | svchost.exe | 2.23.77.188:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
1180 | backgroundTaskHost.exe | 20.223.35.26:443 | arc.msn.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
crl.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
arc.msn.com |
| whitelisted |
www.bing.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2196 | svchost.exe | Device Retrieving External IP Address Detected | ET DYN_DNS External IP Lookup Domain in DNS Query (checkip .dyndns .org) |
4944 | AddInProcess32.exe | Device Retrieving External IP Address Detected | ET INFO External IP Lookup - checkip.dyndns.org |
4944 | AddInProcess32.exe | Device Retrieving External IP Address Detected | ET INFO 404/Snake/Matiex Keylogger Style External IP Check |
2196 | svchost.exe | Device Retrieving External IP Address Detected | INFO [ANY.RUN] External IP Address Lookup Domain (reallyfreegeoip .org) |
4944 | AddInProcess32.exe | Device Retrieving External IP Address Detected | ET INFO External IP Lookup - checkip.dyndns.org |
2196 | svchost.exe | Misc activity | ET INFO External IP Address Lookup Domain in DNS Lookup (reallyfreegeoip .org) |
4944 | AddInProcess32.exe | Misc activity | ET INFO External IP Lookup Service Domain (reallyfreegeoip .org) in TLS SNI |