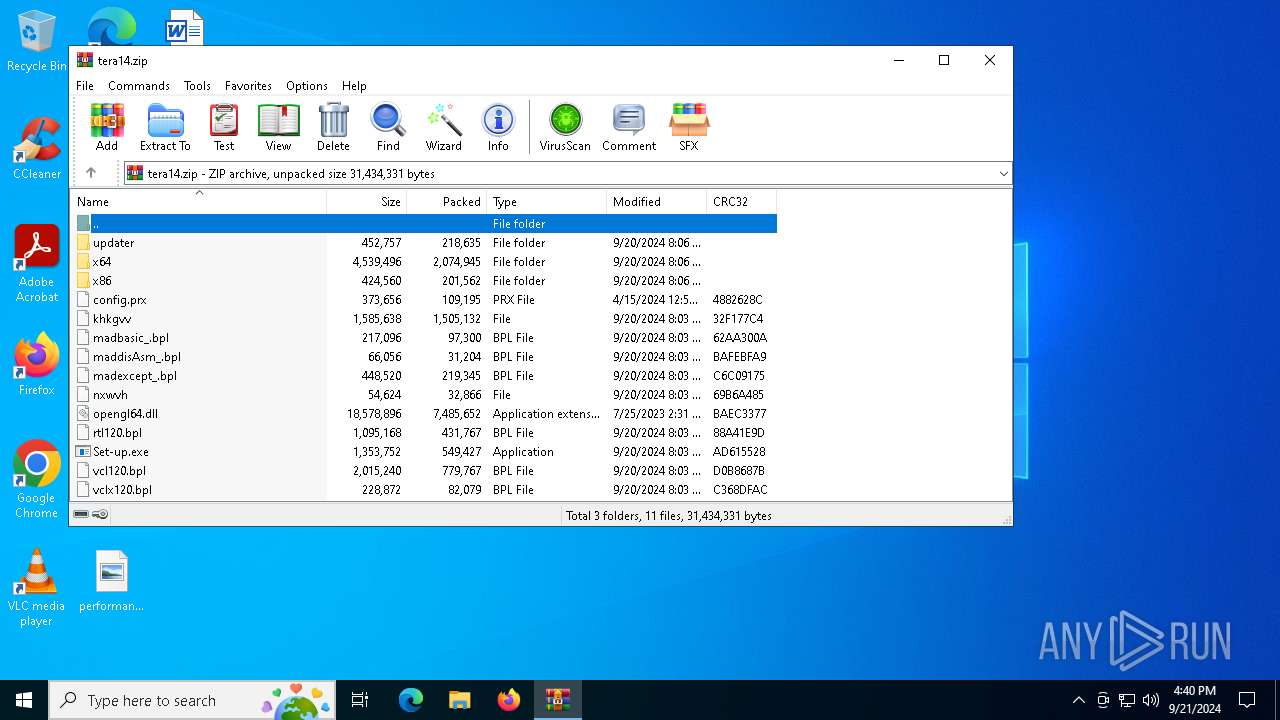
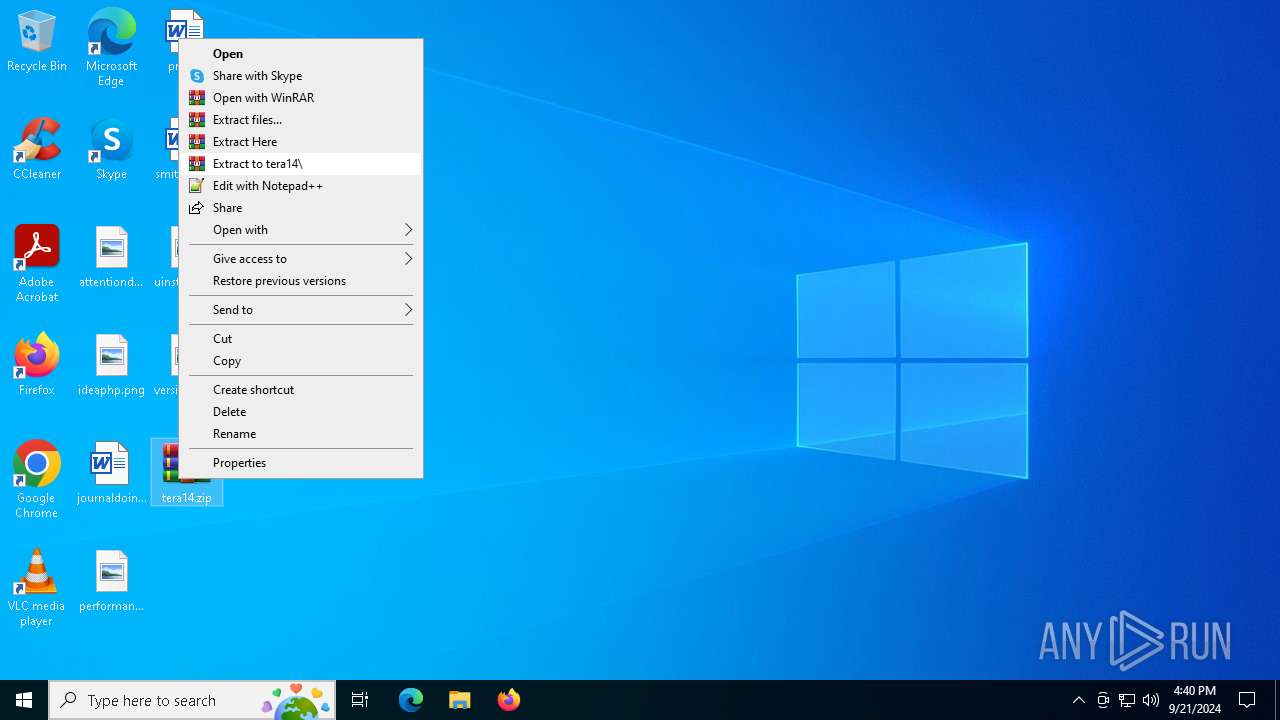
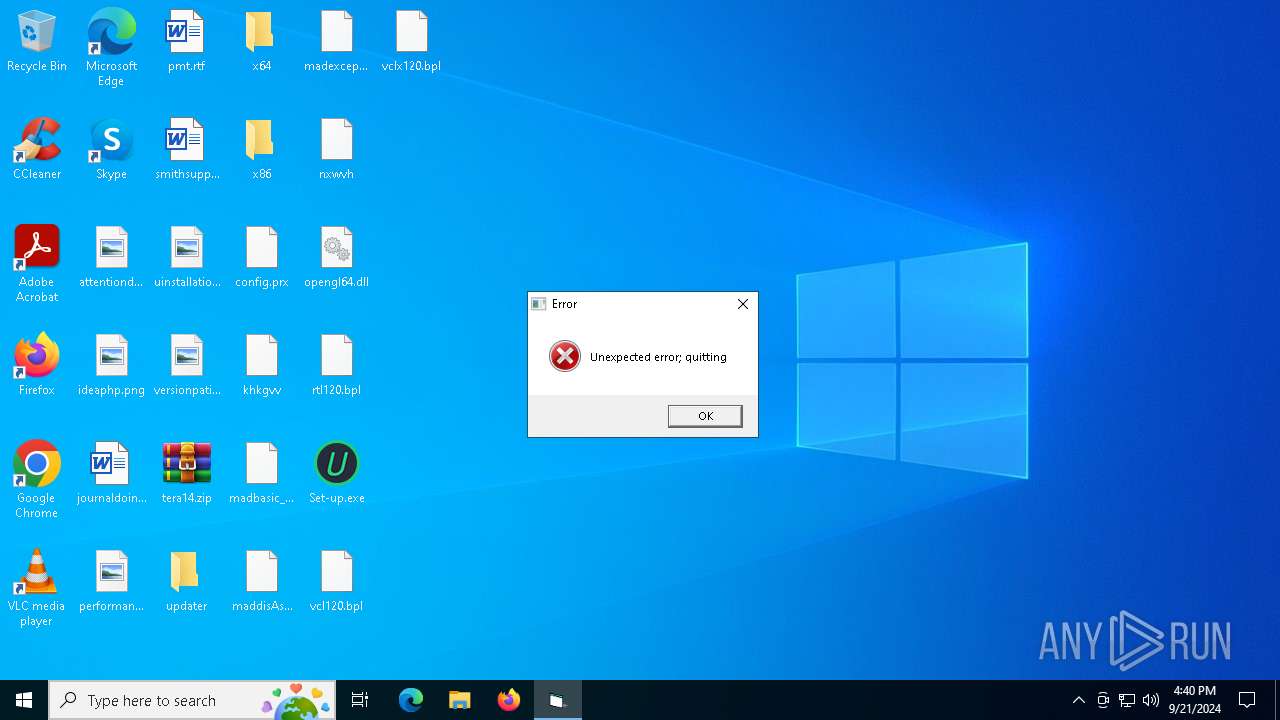
| File name: | tera14.zip |
| Full analysis: | https://app.any.run/tasks/c9c56edb-58f4-4dad-b0a6-297ccae49b12 |
| Verdict: | Malicious activity |
| Threats: | Lumma is an information stealer, developed using the C programming language. It is offered for sale as a malware-as-a-service, with several plans available. It usually targets cryptocurrency wallets, login credentials, and other sensitive information on a compromised system. The malicious software regularly gets updates that improve and expand its functionality, making it a serious stealer threat. |
| Analysis date: | September 21, 2024, 16:39:54 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v1.0 to extract, compression method=store |
| MD5: | 562FC4EA0D47268C01AE0E43BA3010AB |
| SHA1: | 79AA31AD79EC4D2D0B807DF781C3E978E2EE0A13 |
| SHA256: | 2BCAC4BA96DF04E060168D6A7EECE18EF20EDDCF8B6C503351B38BAD16BDC444 |
| SSDEEP: | 98304:t0ueVlhtqW/Kfv7q+Rrlv9kFYzcjakr3gLTwLfroNbJXi1SclrKnAGQ1IzXpd3Ub:RwJ9vaGxnmv3H9z5/DKMs+Q |
MALICIOUS
LUMMA has been detected (SURICATA)
- Obscure.a3x (PID: 6404)
Stealers network behavior
- Obscure.a3x (PID: 6404)
SUSPICIOUS
Process drops legitimate windows executable
- WinRAR.exe (PID: 4232)
- WinRAR.exe (PID: 3784)
Executable content was dropped or overwritten
- Set-up.exe (PID: 6892)
- more.com (PID: 6788)
Starts application with an unusual extension
- more.com (PID: 6788)
- Set-up.exe (PID: 7036)
- Set-up.exe (PID: 6892)
- more.com (PID: 736)
INFO
Manual execution by a user
- Set-up.exe (PID: 6892)
- WinRAR.exe (PID: 4232)
- Set-up.exe (PID: 7036)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 4232)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 10 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | None |
| ZipModifyDate: | 2024:09:21 01:06:22 |
| ZipCRC: | 0x00000000 |
| ZipCompressedSize: | - |
| ZipUncompressedSize: | - |
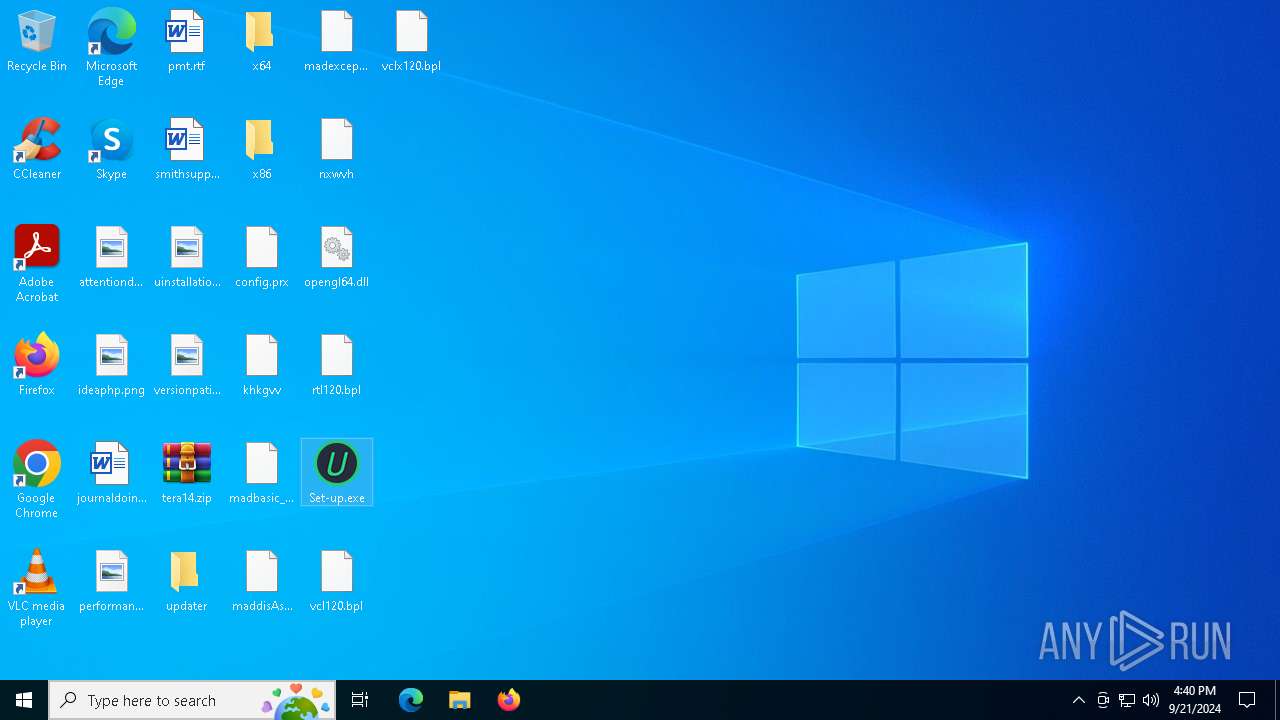
| ZipFileName: | updater/ |
Total processes
130
Monitored processes
11
Malicious processes
2
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 736 | C:\WINDOWS\SysWOW64\more.com | C:\Windows\SysWOW64\more.com | — | Set-up.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: More Utility Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2376 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | more.com | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3784 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\Desktop\tera14.zip | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 3908 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | more.com | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4088 | C:\Users\admin\AppData\Roaming\plug\LBNBHFGUYROWCSLXJFZUGPD\StrCmp.exe | C:\Users\admin\AppData\Roaming\plug\LBNBHFGUYROWCSLXJFZUGPD\StrCmp.exe | — | Set-up.exe | |||||||||||
User: admin Company: aaa Integrity Level: MEDIUM Exit code: 0 Version: 1.00 Modules
| |||||||||||||||
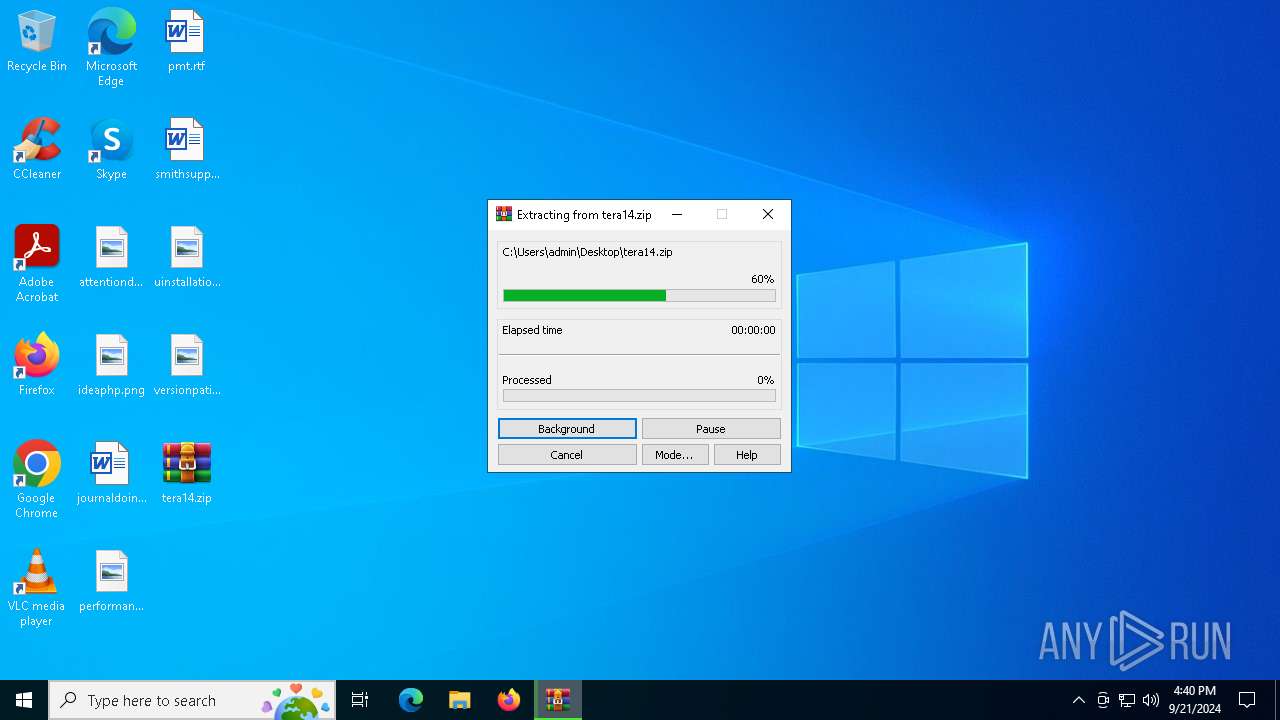
| 4232 | "C:\Program Files\WinRAR\WinRAR.exe" x -iext -ow -ver -- "C:\Users\admin\Desktop\tera14.zip" C:\Users\admin\Desktop\ | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 5740 | C:\Users\admin\AppData\Local\Temp\Obscure.a3x | C:\Users\admin\AppData\Local\Temp\Obscure.a3x | — | more.com | |||||||||||
User: admin Company: AutoIt Team Integrity Level: MEDIUM Description: AutoIt v3 Script (Beta) Exit code: 0 Version: 3, 3, 15, 1 Modules
| |||||||||||||||
| 6404 | C:\Users\admin\AppData\Local\Temp\Obscure.a3x | C:\Users\admin\AppData\Local\Temp\Obscure.a3x | more.com | ||||||||||||
User: admin Company: AutoIt Team Integrity Level: MEDIUM Description: AutoIt v3 Script (Beta) Exit code: 0 Version: 3, 3, 15, 1 Modules
| |||||||||||||||
| 6788 | C:\WINDOWS\SysWOW64\more.com | C:\Windows\SysWOW64\more.com | Set-up.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: More Utility Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6892 | "C:\Users\admin\Desktop\Set-up.exe" | C:\Users\admin\Desktop\Set-up.exe | explorer.exe | ||||||||||||
User: admin Company: IObit Integrity Level: MEDIUM Description: ScreenShot Exit code: 1 Version: 1.0.0.57 Modules
| |||||||||||||||
Total events
4 850
Read events
4 830
Write events
20
Delete events
0
Modification events
| (PID) Process: | (3784) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\GoogleChromeEnterpriseBundle64.zip | |||
| (PID) Process: | (3784) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\tera14.zip | |||
| (PID) Process: | (3784) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3784) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3784) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (3784) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (3784) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\MainWin |
| Operation: | write | Name: | Placement |
Value: 2C0000000000000001000000FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF3D0000002D000000FD03000016020000 | |||
| (PID) Process: | (3784) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\ArcColumnWidths |
| Operation: | write | Name: | name |
Value: 256 | |||
| (PID) Process: | (3784) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\ArcColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3784) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\ArcColumnWidths |
| Operation: | write | Name: | psize |
Value: 80 | |||
Executable files
37
Suspicious files
8
Text files
1
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 4232 | WinRAR.exe | C:\Users\admin\Desktop\x64\tradingnetworkingsockets.dll | executable | |
MD5:3CF26CE759C5E261FE3ECC6451B8B08E | SHA256:FC4A65FF603BF1F4BFE323DE1866145AE1E006AA656799FD134DFA63D92D47C1 | |||
| 4232 | WinRAR.exe | C:\Users\admin\Desktop\x86\api-ms-win-core-processthreads-l1-1-1.dll | executable | |
MD5:29001F316CCFC800E2246743DF9B15B3 | SHA256:E5EA2C21FB225090F7D0DB6C6990D67B1558D8E834E86513BC8BA7A43C4E7B36 | |||
| 4232 | WinRAR.exe | C:\Users\admin\Desktop\x86\api-ms-win-core-string-l1-1-0.dll | executable | |
MD5:2E5C29FC652F432B89A1AFE187736C4D | SHA256:3807DB7ACF1B40C797E4D4C14A12C3806346AE56B25E205E600BE3E635C18D4F | |||
| 4232 | WinRAR.exe | C:\Users\admin\Desktop\x86\api-ms-win-crt-convert-l1-1-0.dll | executable | |
MD5:3E415147CCD7C712618868BDD7A200CD | SHA256:77B69E829BDC26C7B2474BE6B8A2382345B2957E23046897E40992A8157A7BA1 | |||
| 4232 | WinRAR.exe | C:\Users\admin\Desktop\x86\api-ms-win-core-timezone-l1-1-0.dll | executable | |
MD5:69DF2CCE4528C9E38D04A461BA1F992B | SHA256:A108A8F20DED00E742A1F818EF00EB425990B6B24A2BCD060DEA4D7F06D3F165 | |||
| 4232 | WinRAR.exe | C:\Users\admin\Desktop\x86\api-ms-win-crt-filesystem-l1-1-0.dll | executable | |
MD5:14F407D94C77B1B0039AE2C89B07A2FF | SHA256:85B1B189CE9E3C6F4D2EFDD4CD82B0807F681BEA2D28851CAAF545990DE99000 | |||
| 4232 | WinRAR.exe | C:\Users\admin\Desktop\x86\api-ms-win-core-synch-l1-1-0.dll | executable | |
MD5:979C67BA244E5328A1A2E588FF748E86 | SHA256:8BB38A7A59FBAA792B3D5F34F94580429588C8C592929CBD307AFD5579762ABC | |||
| 4232 | WinRAR.exe | C:\Users\admin\Desktop\x86\api-ms-win-core-rtlsupport-l1-1-0.dll | executable | |
MD5:0069FD29263C0DD90314C48BBCE852EF | SHA256:D11093FDC1D5C9213B9B2886CE91DB3DED17EF8DAE1615A8C7FFBC55B8E3F79B | |||
| 4232 | WinRAR.exe | C:\Users\admin\Desktop\x86\api-ms-win-crt-conio-l1-1-0.dll | executable | |
MD5:7190CBFAD2D7773D3B88CCC25533A651 | SHA256:4AEEAE0AC9F6C1B0B8835067EA3B7FC429F353565F18DE7858F4EA5D6F72072E | |||
| 4232 | WinRAR.exe | C:\Users\admin\Desktop\x86\api-ms-win-core-util-l1-1-0.dll | executable | |
MD5:C6553959AECD5BAC01C0673CFDF86B68 | SHA256:68BD9C086D210EB14E78F00988BA88CEAF9056C8F10746AB024990F8512A2296 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
12
TCP/UDP connections
25
DNS requests
6
Threats
1
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2120 | MoUsoCoreWorker.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | POST | 200 | 188.114.96.3:443 | https://ohhyhousedmxznw.shop/api | unknown | text | 15 b | unknown |
— | — | POST | 200 | 188.114.97.3:443 | https://ohhyhousedmxznw.shop/api | unknown | text | 15 b | unknown |
— | — | POST | 200 | 188.114.97.3:443 | https://ohhyhousedmxznw.shop/api | unknown | text | 15 b | unknown |
— | — | POST | 200 | 188.114.96.3:443 | https://ohhyhousedmxznw.shop/api | unknown | text | 16.5 Kb | unknown |
— | — | POST | 200 | 188.114.96.3:443 | https://ohhyhousedmxznw.shop/api | unknown | text | 15 b | unknown |
— | — | POST | 200 | 188.114.97.3:443 | https://ohhyhousedmxznw.shop/api | unknown | text | 15 b | unknown |
— | — | POST | 200 | 188.114.96.3:443 | https://ohhyhousedmxznw.shop/api | unknown | text | 48 b | unknown |
6008 | svchost.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
3004 | RUXIMICS.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
6008 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
3004 | RUXIMICS.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
2120 | MoUsoCoreWorker.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
3888 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
2120 | MoUsoCoreWorker.exe | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
6008 | svchost.exe | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
3004 | RUXIMICS.exe | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
2120 | MoUsoCoreWorker.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
browser.pipe.aria.microsoft.com |
| whitelisted |
ohhyhousedmxznw.shop |
| unknown |
Threats
PID | Process | Class | Message |
|---|---|---|---|
6404 | Obscure.a3x | A Network Trojan was detected | STEALER [ANY.RUN] Lumma Stealer TLS Connection |