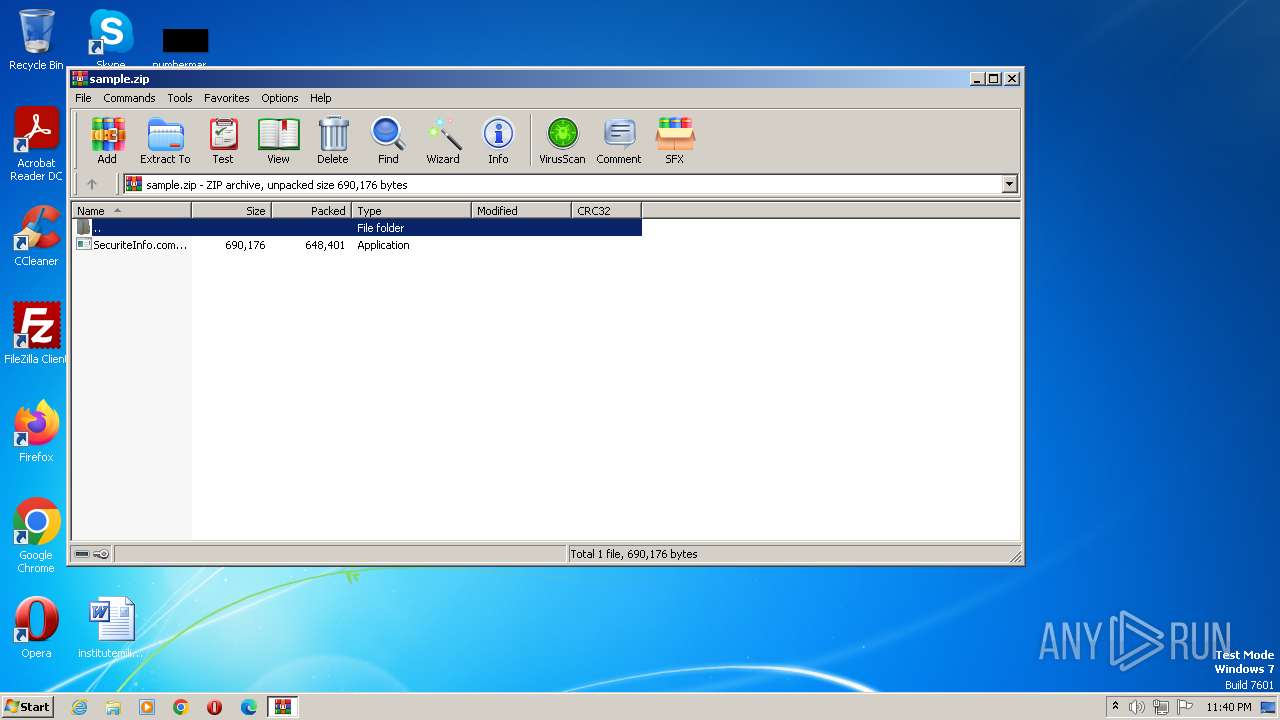
| File name: | sample.zip |
| Full analysis: | https://app.any.run/tasks/0fb71e2f-4ce6-4039-9e0f-90b8d901ee7b |
| Verdict: | Malicious activity |
| Threats: | Agent Tesla is spyware that collects information about the actions of its victims by recording keystrokes and user interactions. It is falsely marketed as a legitimate software on the dedicated website where this malware is sold. |
| Analysis date: | July 26, 2023, 22:39:57 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract |
| MD5: | 79B5CE321D0AAF6044D600C123F1C2C9 |
| SHA1: | 5ACB1A34EB459F69FDC9362E05742B1B268ECFD2 |
| SHA256: | 2BB932AD45C06D8084E4781DA418C0E03E4B08D88BBB17872E8500D22B9E8D7D |
| SSDEEP: | 12288:W3mN4o9HHPr3YaEs1tcSFUNRhyXTiihoyGHn3PrlZidrCY80mvCTm:9pJrEst+smiK3pZAz80mvim |
MALICIOUS
Application was dropped or rewritten from another process
- SecuriteInfo.com.Trojan.PackedNET.2200.8496.10942.exe (PID: 564)
- SecuriteInfo.com.Trojan.PackedNET.2200.8496.10942.exe (PID: 2616)
AGENTTESLA detected by memory dumps
- SecuriteInfo.com.Trojan.PackedNET.2200.8496.10942.exe (PID: 2616)
Steals credentials from Web Browsers
- SecuriteInfo.com.Trojan.PackedNET.2200.8496.10942.exe (PID: 2616)
Actions looks like stealing of personal data
- SecuriteInfo.com.Trojan.PackedNET.2200.8496.10942.exe (PID: 2616)
SUSPICIOUS
Reads the Internet Settings
- SecuriteInfo.com.Trojan.PackedNET.2200.8496.10942.exe (PID: 2616)
- SecuriteInfo.com.Trojan.PackedNET.2200.8496.10942.exe (PID: 564)
Application launched itself
- SecuriteInfo.com.Trojan.PackedNET.2200.8496.10942.exe (PID: 564)
Accesses Microsoft Outlook profiles
- SecuriteInfo.com.Trojan.PackedNET.2200.8496.10942.exe (PID: 2616)
Adds/modifies Windows certificates
- SecuriteInfo.com.Trojan.PackedNET.2200.8496.10942.exe (PID: 564)
Connects to SMTP port
- SecuriteInfo.com.Trojan.PackedNET.2200.8496.10942.exe (PID: 2616)
Reads settings of System Certificates
- SecuriteInfo.com.Trojan.PackedNET.2200.8496.10942.exe (PID: 2616)
INFO
Executable content was dropped or overwritten
- WinRAR.exe (PID: 2852)
Manual execution by a user
- SecuriteInfo.com.Trojan.PackedNET.2200.8496.10942.exe (PID: 564)
- chrome.exe (PID: 1304)
The process uses the downloaded file
- chrome.exe (PID: 3912)
- chrome.exe (PID: 1880)
Checks supported languages
- SecuriteInfo.com.Trojan.PackedNET.2200.8496.10942.exe (PID: 564)
- SecuriteInfo.com.Trojan.PackedNET.2200.8496.10942.exe (PID: 2616)
Reads the computer name
- SecuriteInfo.com.Trojan.PackedNET.2200.8496.10942.exe (PID: 564)
- SecuriteInfo.com.Trojan.PackedNET.2200.8496.10942.exe (PID: 2616)
Reads Environment values
- SecuriteInfo.com.Trojan.PackedNET.2200.8496.10942.exe (PID: 2616)
Reads the machine GUID from the registry
- SecuriteInfo.com.Trojan.PackedNET.2200.8496.10942.exe (PID: 564)
- SecuriteInfo.com.Trojan.PackedNET.2200.8496.10942.exe (PID: 2616)
The process checks LSA protection
- SecuriteInfo.com.Trojan.PackedNET.2200.8496.10942.exe (PID: 2616)
- SecuriteInfo.com.Trojan.PackedNET.2200.8496.10942.exe (PID: 564)
Application launched itself
- chrome.exe (PID: 1304)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
AgentTesla
(PID) Process(2616) SecuriteInfo.com.Trojan.PackedNET.2200.8496.10942.exe
Protocolsmtp
Hostmail.sgbumperscar.com
Port587
Usernameptt-mary@sgbumperscar.com
Passwordtien3012m
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipFileName: | SecuriteInfo.com.Trojan.PackedNET.2200.8496.10942.exe |
|---|---|
| ZipUncompressedSize: | - |
| ZipCompressedSize: | - |
| ZipCRC: | 0x00000000 |
| ZipModifyDate: | 1980:00:00 00:00:00 |
| ZipCompression: | Unknown (99) |
| ZipBitFlag: | 0x0009 |
| ZipRequiredVersion: | 20 |
Total processes
73
Monitored processes
35
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 348 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=network.mojom.NetworkService --lang=en-US --service-sandbox-type=none --mojo-platform-channel-handle=1364 --field-trial-handle=1212,i,11258979954019980813,16139273992487653836,131072 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | chrome.exe | ||||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 564 | "C:\Users\admin\Desktop\SecuriteInfo.com.Trojan.PackedNET.2200.8496.10942.exe" | C:\Users\admin\Desktop\SecuriteInfo.com.Trojan.PackedNET.2200.8496.10942.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Integrity Level: HIGH Description: QLPhim Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
| 1012 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --disable-gpu-compositing --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=29 --mojo-platform-channel-handle=4420 --field-trial-handle=1212,i,11258979954019980813,16139273992487653836,131072 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 1024 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=audio.mojom.AudioService --lang=en-US --service-sandbox-type=audio --mojo-platform-channel-handle=1328 --field-trial-handle=1212,i,11258979954019980813,16139273992487653836,131072 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 1040 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=crashpad-handler "--user-data-dir=C:\Users\admin\AppData\Local\Google\Chrome\User Data" /prefetch:7 --monitor-self-annotation=ptype=crashpad-handler "--database=C:\Users\admin\AppData\Local\Google\Chrome\User Data\Crashpad" --url=https://clients2.google.com/cr/report --annotation=channel= --annotation=plat=Win32 --annotation=prod=Chrome --annotation=ver=109.0.5414.120 --initial-client-data=0xc8,0xcc,0xd0,0x9c,0xd4,0x6ce08b38,0x6ce08b48,0x6ce08b54 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 1104 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --disable-gpu-compositing --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=18 --mojo-platform-channel-handle=804 --field-trial-handle=1212,i,11258979954019980813,16139273992487653836,131072 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 1284 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --lang=en-US --service-sandbox-type=service --mojo-platform-channel-handle=3368 --field-trial-handle=1212,i,11258979954019980813,16139273992487653836,131072 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 1304 | "C:\Program Files\Google\Chrome\Application\chrome.exe" | C:\Program Files\Google\Chrome\Application\chrome.exe | explorer.exe | ||||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 1392 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --lang=en-US --service-sandbox-type=service --mojo-platform-channel-handle=3660 --field-trial-handle=1212,i,11258979954019980813,16139273992487653836,131072 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 1836 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --disable-gpu-compositing --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=17 --mojo-platform-channel-handle=1948 --field-trial-handle=1212,i,11258979954019980813,16139273992487653836,131072 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
Total events
8 164
Read events
8 039
Write events
124
Delete events
1
Modification events
| (PID) Process: | (2852) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\178\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2852) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\virtio_ivshmem_master_build.zip | |||
| (PID) Process: | (2852) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (2852) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\phacker.zip | |||
| (PID) Process: | (2852) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (2852) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (2852) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (2852) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (2852) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\MainWin |
| Operation: | write | Name: | Placement |
Value: 2C0000000000000001000000FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF42000000420000000204000037020000 | |||
| (PID) Process: | (2852) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\General |
| Operation: | write | Name: | LastFolder |
Value: C:\Users\admin\Desktop | |||
Executable files
6
Suspicious files
678
Text files
136
Unknown types
8
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1304 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\commerce_subscription_db\LOG.old~RF1125b5.TMP | — | |
MD5:— | SHA256:— | |||
| 1304 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\commerce_subscription_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 1304 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Site Characteristics Database\LOG.old | text | |
MD5:D5C9ECBD2DCA29D89266782824D7AF99 | SHA256:D22D1243ACC064A30823180D0E583C853E9395367C78C2AD9DE59A463904F702 | |||
| 2852 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb2852.20022\SecuriteInfo.com.Trojan.PackedNET.2200.8496.10942.exe | executable | |
MD5:179975642C1E6FE458E446AAA9328596 | SHA256:AB701AC288408C45B6A0D0D7CC7F71B44309CD32B64544A3244511098EE20BF6 | |||
| 1304 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Extension State\LOG.old~RF112f98.TMP | text | |
MD5:771E7B9DB84D4E259FE7435752F83623 | SHA256:9EA3C9F63A2EC70A754ED8F5F377D1CF8D86FF4ABABF253293167AB421E1D944 | |||
| 1304 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\shared_proto_db\metadata\LOG.old | text | |
MD5:7C1C23F006788D107F8A01B852CC6701 | SHA256:9FA4E627077EDCBEC8AAA1ED2DD5538E630790893F88F02F1E9CC863E6A27848 | |||
| 1304 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Crashpad\settings.dat | binary | |
MD5:9C016064A1F864C8140915D77CF3389A | SHA256:0E7265D4A8C16223538EDD8CD620B8820611C74538E420A88E333BE7F62AC787 | |||
| 1304 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Site Characteristics Database\LOG.old~RF1125b5.TMP | text | |
MD5:C214500EDB0B5F56B9D3D27B32964AB2 | SHA256:6254FD03CFC08A142D6AEB8C037D25D42564C0CC6F294A3716DF19FDF254EBCE | |||
| 1304 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Local Storage\leveldb\LOG.old~RF11277a.TMP | text | |
MD5:74174B4F8AEB3CFDC18745625ED7865C | SHA256:419223BAED85740D27E427C390FDCA869AE1F4089A8415DE13CC4305F6907FDF | |||
| 1304 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Session Storage\LOG.old | text | |
MD5:99EC94B2503FAD33EDAF99779EBA5BC8 | SHA256:DC554AB7EDCAD375F39ED106CA1EF9A89FB8D9063A4D08F377F2C80D66799D7E | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
13
TCP/UDP connections
144
DNS requests
114
Threats
1
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
868 | svchost.exe | HEAD | 200 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/cxpsjblnoxgjoqggdsbvujtof4_58/khaoiebndkojlmppeemjhbpbandiljpe_58_win_advr4ucepztwtigvw3fduftsvbeq.crx3 | US | — | — | whitelisted |
348 | chrome.exe | GET | 204 | 142.250.184.195:80 | http://www.gstatic.com/generate_204 | US | — | — | whitelisted |
868 | svchost.exe | HEAD | 200 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/delta-update/lmelglejhemejginpboagddgdfbepgmp/1.e29e642db998c8147d0a35c42b80be2cb85e013bb1288a80d3ceaba0289bccd8/1.248d99a92d5adc640c1fdf1d26c3821298c74646ab8fa6d1b94f2b984075eead/7d46b596714f69b716a2283ee42e5181d1d6ac8d41689239338e038ee98ca6f7.crxd | US | binary | 5.46 Kb | whitelisted |
868 | svchost.exe | HEAD | 200 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/ad62d4tkq2bdt5z2zyx3aawqfcxa_2981/jflookgnkcckhobaglndicnbbgbonegd_2981_all_kxzjyll3bml7uhowed3e3qnnam.crx3 | US | binary | 4.96 Kb | whitelisted |
868 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/ad62d4tkq2bdt5z2zyx3aawqfcxa_2981/jflookgnkcckhobaglndicnbbgbonegd_2981_all_kxzjyll3bml7uhowed3e3qnnam.crx3 | US | binary | 23.2 Kb | whitelisted |
868 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/g4ptxcyjfyndlflbodcujfvinq_8138/hfnkpimlhhgieaddgfemjhofmfblmnib_8138_all_gm7aajixvtxy7qkjpwua74zaoa.crx3 | US | binary | 9.67 Kb | whitelisted |
868 | svchost.exe | HEAD | 200 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/g4ptxcyjfyndlflbodcujfvinq_8138/hfnkpimlhhgieaddgfemjhofmfblmnib_8138_all_gm7aajixvtxy7qkjpwua74zaoa.crx3 | US | binary | 3.49 Kb | whitelisted |
868 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/g4ptxcyjfyndlflbodcujfvinq_8138/hfnkpimlhhgieaddgfemjhofmfblmnib_8138_all_gm7aajixvtxy7qkjpwua74zaoa.crx3 | US | binary | 4.96 Kb | whitelisted |
868 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/ad62d4tkq2bdt5z2zyx3aawqfcxa_2981/jflookgnkcckhobaglndicnbbgbonegd_2981_all_kxzjyll3bml7uhowed3e3qnnam.crx3 | US | binary | 36.4 Kb | whitelisted |
868 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/g4ptxcyjfyndlflbodcujfvinq_8138/hfnkpimlhhgieaddgfemjhofmfblmnib_8138_all_gm7aajixvtxy7qkjpwua74zaoa.crx3 | US | binary | 11.0 Kb | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
2720 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
348 | chrome.exe | 142.250.184.227:443 | clientservices.googleapis.com | GOOGLE | US | whitelisted |
1304 | chrome.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
348 | chrome.exe | 142.250.181.237:443 | accounts.google.com | GOOGLE | US | suspicious |
348 | chrome.exe | 216.58.212.132:443 | www.google.com | — | — | whitelisted |
348 | chrome.exe | 142.250.186.131:443 | update.googleapis.com | GOOGLE | US | whitelisted |
348 | chrome.exe | 142.250.184.238:443 | encrypted-tbn0.gstatic.com | GOOGLE | US | whitelisted |
348 | chrome.exe | 142.250.186.37:443 | mail.google.com | GOOGLE | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
clientservices.googleapis.com |
| whitelisted |
accounts.google.com |
| shared |
www.google.com |
| malicious |
encrypted-tbn0.gstatic.com |
| whitelisted |
update.googleapis.com |
| whitelisted |
gmail.com |
| shared |
mail.google.com |
| shared |
optimizationguide-pa.googleapis.com |
| whitelisted |
api.ipify.org |
| shared |
www.googleapis.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2616 | SecuriteInfo.com.Trojan.PackedNET.2200.8496.10942.exe | Successful Credential Theft Detected | STEALER [ANY.RUN] Attempt to exfiltrate via SMTP |