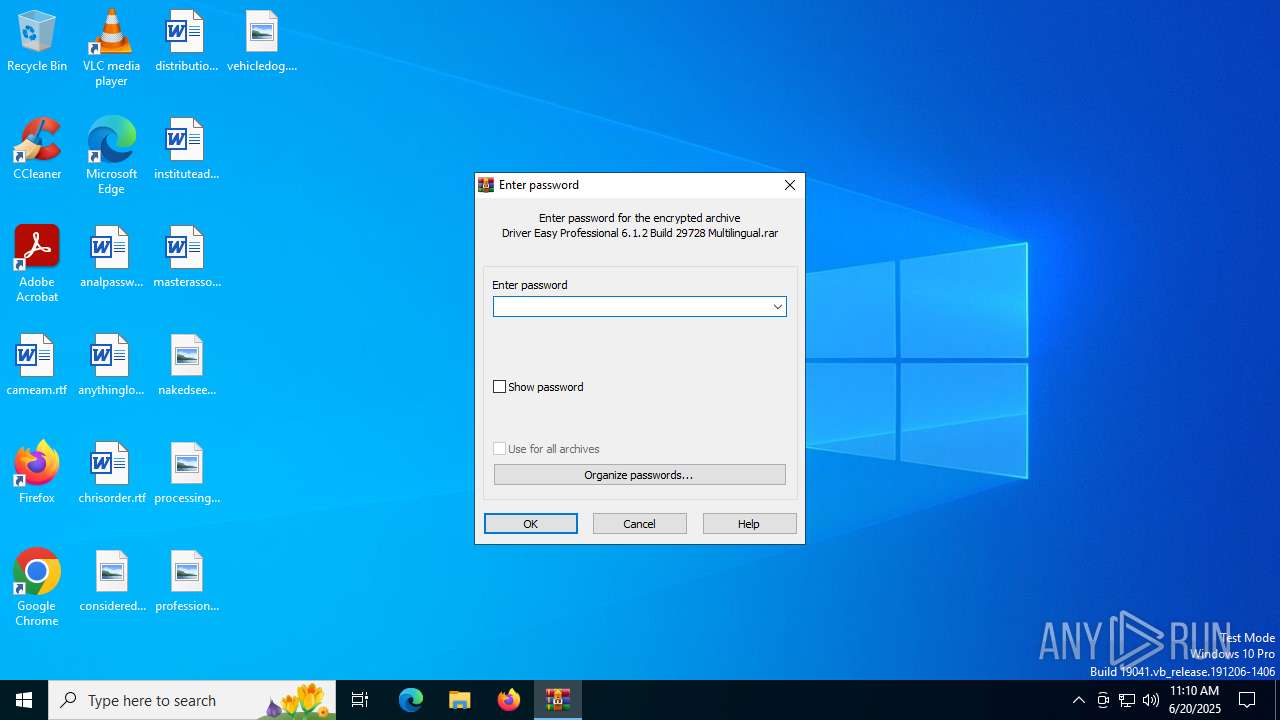
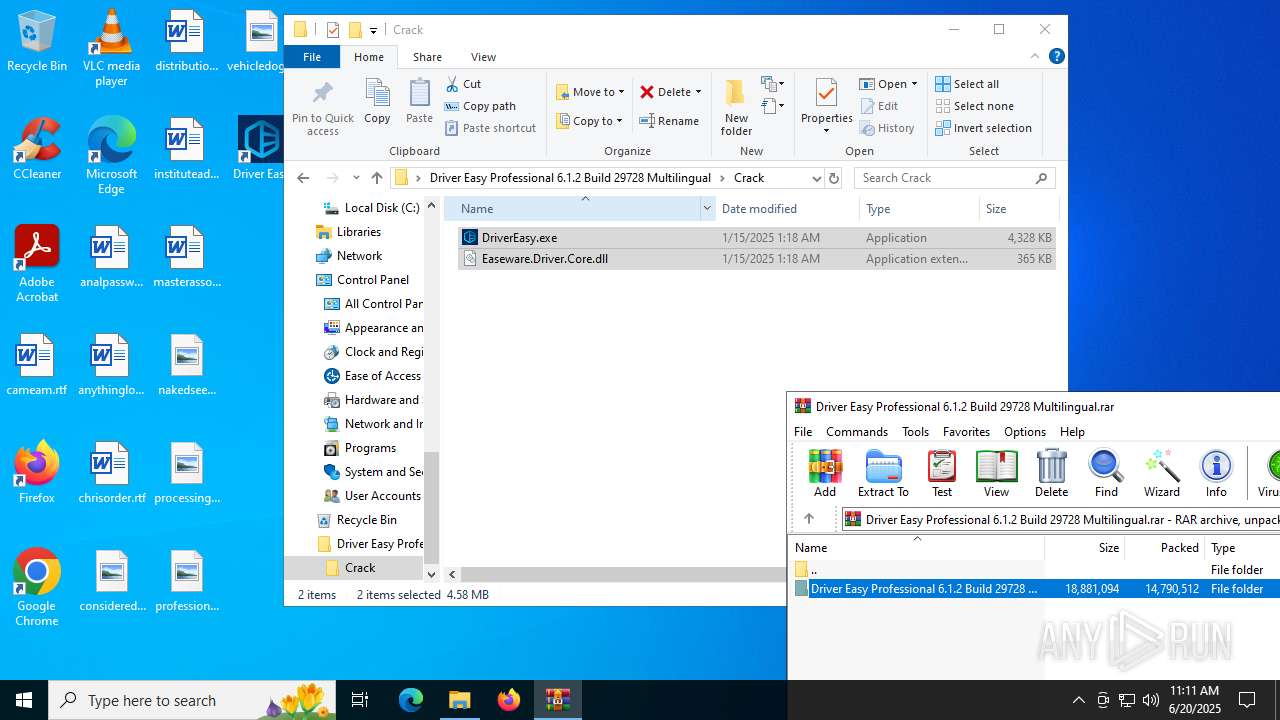
| File name: | Driver Easy Professional 6.1.2 Build 29728 Multilingual.rar |
| Full analysis: | https://app.any.run/tasks/02149975-3793-4129-b47a-653207754998 |
| Verdict: | Malicious activity |
| Threats: | Lumma is an information stealer, developed using the C programming language. It is offered for sale as a malware-as-a-service, with several plans available. It usually targets cryptocurrency wallets, login credentials, and other sensitive information on a compromised system. The malicious software regularly gets updates that improve and expand its functionality, making it a serious stealer threat. |
| Analysis date: | June 20, 2025, 11:10:17 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-rar |
| File info: | RAR archive data, v5 |
| MD5: | 16B5B4558AA30C2A6436C91DCAE4FE4C |
| SHA1: | 29E7BD378261B466AA820339C7D7A3CF38A53CF9 |
| SHA256: | 2BB11D3B6E6DF436D52B1020AFBA1F5BAB66BF1A715E1A18F149075DF9AEDE28 |
| SSDEEP: | 196608:VgKAEMZfxZAjFLGsqvbSCix4eeZQ1pCVc96D:VgKoxZAtG4Ci76D |
MALICIOUS
LUMMA mutex has been found
- DriverEasy_Setup.exe (PID: 4944)
- DriverEasy_Setup.exe (PID: 2552)
SUSPICIOUS
Searches for installed software
- DriverEasy_Setup.exe (PID: 4944)
- DriverEasy_Setup.exe (PID: 2552)
Executable content was dropped or overwritten
- Update.exe (PID: 6688)
- Update.exe (PID: 4012)
- Update.tmp (PID: 4944)
- DriverEasy.exe (PID: 5620)
Reads security settings of Internet Explorer
- Update.tmp (PID: 4216)
- DriverEasy.exe (PID: 7092)
- DriverEasy.exe (PID: 5620)
Reads the Windows owner or organization settings
- Update.tmp (PID: 4944)
Drops 7-zip archiver for unpacking
- Update.tmp (PID: 4944)
There is functionality for taking screenshot (YARA)
- DriverEasy.exe (PID: 7092)
- DriverEasy.exe (PID: 5620)
Application launched itself
- DriverEasy.exe (PID: 7092)
Reads the date of Windows installation
- DriverEasy.exe (PID: 7092)
Drops a system driver (possible attempt to evade defenses)
- DriverEasy.exe (PID: 5620)
The process checks if it is being run in the virtual environment
- DriverEasy.exe (PID: 5620)
There is functionality for VM detection VirtualBox (YARA)
- DriverEasy.exe (PID: 5620)
INFO
Checks supported languages
- DriverEasy_Setup.exe (PID: 4944)
- DriverEasy_Setup.exe (PID: 2552)
- Update.exe (PID: 6688)
- Update.exe (PID: 4012)
- Update.tmp (PID: 4944)
- Update.tmp (PID: 4216)
- Easeware.CheckScheduledScan.exe (PID: 316)
- Easeware.ConfigLanguageFromSetup.exe (PID: 2864)
- DriverEasy.exe (PID: 7092)
- DriverEasy.exe (PID: 5620)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 6188)
Manual execution by a user
- DriverEasy_Setup.exe (PID: 4944)
- DriverEasy_Setup.exe (PID: 1328)
- DriverEasy_Setup.exe (PID: 2552)
- Update.exe (PID: 6688)
- DriverEasy.exe (PID: 7092)
Reads the machine GUID from the registry
- DriverEasy_Setup.exe (PID: 4944)
- DriverEasy_Setup.exe (PID: 2552)
- DriverEasy.exe (PID: 7092)
- DriverEasy.exe (PID: 5620)
Reads the computer name
- DriverEasy_Setup.exe (PID: 4944)
- DriverEasy_Setup.exe (PID: 2552)
- Update.tmp (PID: 4216)
- Update.exe (PID: 4012)
- Update.tmp (PID: 4944)
- Easeware.CheckScheduledScan.exe (PID: 316)
- Easeware.ConfigLanguageFromSetup.exe (PID: 2864)
- DriverEasy.exe (PID: 7092)
- DriverEasy.exe (PID: 5620)
Reads the software policy settings
- DriverEasy_Setup.exe (PID: 4944)
- DriverEasy_Setup.exe (PID: 2552)
- DriverEasy.exe (PID: 7092)
- slui.exe (PID: 2512)
Create files in a temporary directory
- Update.exe (PID: 6688)
- Update.exe (PID: 4012)
- Update.tmp (PID: 4944)
Process checks computer location settings
- Update.tmp (PID: 4216)
- DriverEasy.exe (PID: 7092)
The sample compiled with russian language support
- Update.tmp (PID: 4944)
Creates files in the program directory
- Update.tmp (PID: 4944)
Creates a software uninstall entry
- Update.tmp (PID: 4944)
Creates files or folders in the user directory
- Easeware.ConfigLanguageFromSetup.exe (PID: 2864)
Compiled with Borland Delphi (YARA)
- Update.tmp (PID: 4216)
- Update.exe (PID: 6688)
Detects InnoSetup installer (YARA)
- Update.tmp (PID: 4216)
- Update.exe (PID: 6688)
Reads security settings of Internet Explorer
- dllhost.exe (PID: 4920)
The sample compiled with english language support
- Update.tmp (PID: 4944)
- DriverEasy.exe (PID: 5620)
The sample compiled with french language support
- Update.tmp (PID: 4944)
Disables trace logs
- DriverEasy.exe (PID: 7092)
CPUZ mutex has been found
- DriverEasy.exe (PID: 5620)
Reads Environment values
- DriverEasy.exe (PID: 5620)
- DriverEasy.exe (PID: 7092)
Checks proxy server information
- DriverEasy.exe (PID: 7092)
- slui.exe (PID: 2512)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .rar | | | RAR compressed archive (v5.0) (61.5) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (38.4) |
EXIF
ZIP
| FileVersion: | RAR v5 |
|---|
Total processes
166
Monitored processes
16
Malicious processes
2
Suspicious processes
3
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 316 | "C:\Program Files\Easeware\DriverEasy\Easeware.CheckScheduledScan.exe" -create "Driver Easy Scheduled Scan" "C:\Program Files\Easeware\DriverEasy\DriverEasy.exe" | C:\Program Files\Easeware\DriverEasy\Easeware.CheckScheduledScan.exe | — | Update.tmp | |||||||||||
User: admin Company: Easeware Integrity Level: HIGH Description: Easeware.CheckScheduledScan Exit code: 0 Version: 1.0.1.0 Modules
| |||||||||||||||
| 1328 | "C:\Users\admin\Desktop\Driver Easy Professional 6.1.2 Build 29728 Multilingual\DriverEasy_Setup.exe" | C:\Users\admin\Desktop\Driver Easy Professional 6.1.2 Build 29728 Multilingual\DriverEasy_Setup.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221226540 Modules
| |||||||||||||||
| 1352 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | Easeware.ConfigLanguageFromSetup.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2512 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2552 | "C:\Users\admin\Desktop\Driver Easy Professional 6.1.2 Build 29728 Multilingual\DriverEasy_Setup.exe" | C:\Users\admin\Desktop\Driver Easy Professional 6.1.2 Build 29728 Multilingual\DriverEasy_Setup.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 2864 | "C:\Program Files\Easeware\DriverEasy\Easeware.ConfigLanguageFromSetup.exe" DriverEasy en True True | C:\Program Files\Easeware\DriverEasy\Easeware.ConfigLanguageFromSetup.exe | — | Update.tmp | |||||||||||
User: admin Company: Easeware Integrity Level: HIGH Description: Easeware.ConfigLanguageFromSetup Exit code: 0 Version: 1.0.4.0 Modules
| |||||||||||||||
| 4012 | "C:\Users\admin\Desktop\Driver Easy Professional 6.1.2 Build 29728 Multilingual\Update.exe" /SPAWNWND=$20292 /NOTIFYWND=$902FE | C:\Users\admin\Desktop\Driver Easy Professional 6.1.2 Build 29728 Multilingual\Update.exe | Update.tmp | ||||||||||||
User: admin Company: Easeware Integrity Level: HIGH Description: Driver Easy Setup Exit code: 0 Version: 6.1.2.29728 Modules
| |||||||||||||||
| 4216 | "C:\Users\admin\AppData\Local\Temp\is-17IAG.tmp\Update.tmp" /SL5="$902FE,5886360,1001472,C:\Users\admin\Desktop\Driver Easy Professional 6.1.2 Build 29728 Multilingual\Update.exe" | C:\Users\admin\AppData\Local\Temp\is-17IAG.tmp\Update.tmp | — | Update.exe | |||||||||||
User: admin Company: Easeware Integrity Level: MEDIUM Description: Setup/Uninstall Exit code: 0 Version: 51.1052.0.0 Modules
| |||||||||||||||
| 4648 | C:\WINDOWS\System32\rundll32.exe C:\WINDOWS\System32\shell32.dll,SHCreateLocalServerRunDll {9aa46009-3ce0-458a-a354-715610a075e6} -Embedding | C:\Windows\System32\rundll32.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4920 | C:\WINDOWS\system32\DllHost.exe /Processid:{3AD05575-8857-4850-9277-11B85BDB8E09} | C:\Windows\System32\dllhost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: COM Surrogate Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
22 704
Read events
22 653
Write events
51
Delete events
0
Modification events
| (PID) Process: | (6188) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (6188) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (6188) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (6188) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\Driver Easy Professional 6.1.2 Build 29728 Multilingual.rar | |||
| (PID) Process: | (6188) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (6188) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (6188) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (6188) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (6188) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface |
| Operation: | write | Name: | ShowPassword |
Value: 0 | |||
| (PID) Process: | (4944) Update.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Classes\drivereasy |
| Operation: | write | Name: | URL Protocol |
Value: C:\Program Files\Easeware\DriverEasy\DriverEasy.exe | |||
Executable files
53
Suspicious files
7
Text files
80
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6188 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb6188.14234\Driver Easy Professional 6.1.2 Build 29728 Multilingual\DriverEasy_Setup.exe | executable | |
MD5:508C9F6F267F8225A036A099B8EF00EA | SHA256:89EABA5095758C079AD0741FAB8265B33F2E54C59D120C3D39E2BE1E6D8DAA87 | |||
| 6188 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb6188.14234\Driver Easy Professional 6.1.2 Build 29728 Multilingual\Crack\Easeware.Driver.Core.dll | executable | |
MD5:5FBED1A129A4B373540FBC1ABB139BD1 | SHA256:1366C09D3205A0811B34505D0838AECA9BA608E536720011D894C9E0C0AD2D9C | |||
| 6688 | Update.exe | C:\Users\admin\AppData\Local\Temp\is-17IAG.tmp\Update.tmp | executable | |
MD5:837CE9A9590EDB33504129AEC963B0D5 | SHA256:EFB5EA13A4AE93765324C6D1F052D7FCD46B9697C07D36738282B402BB9431F7 | |||
| 6188 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb6188.14234\Driver Easy Professional 6.1.2 Build 29728 Multilingual\Readme.txt | text | |
MD5:4D6EFB754425805ACB799486198AB25A | SHA256:4E7F065810DCD6BB07F91D441F5311C68F5BB05355EEFE3AA2A8A5936F022A06 | |||
| 4012 | Update.exe | C:\Users\admin\AppData\Local\Temp\is-KMSP1.tmp\Update.tmp | executable | |
MD5:837CE9A9590EDB33504129AEC963B0D5 | SHA256:EFB5EA13A4AE93765324C6D1F052D7FCD46B9697C07D36738282B402BB9431F7 | |||
| 4944 | Update.tmp | C:\Users\admin\AppData\Local\Temp\is-AIPKT.tmp\innocallback.dll | executable | |
MD5:1C55AE5EF9980E3B1028447DA6105C75 | SHA256:6AFA2D104BE6EFE3D9A2AB96DBB75DB31565DAD64DD0B791E402ECC25529809F | |||
| 4944 | Update.tmp | C:\Users\admin\AppData\Local\Temp\is-AIPKT.tmp\botva2.dll | executable | |
MD5:67965A5957A61867D661F05AE1F4773E | SHA256:450B9B0BA25BF068AFBC2B23D252585A19E282939BF38326384EA9112DFD0105 | |||
| 6188 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb6188.14234\Driver Easy Professional 6.1.2 Build 29728 Multilingual\Update.exe | executable | |
MD5:064C4BA64B08BE1E39486A0FECCCDADB | SHA256:FAE2CDCB8B566128CA110CF9BAD3EB604542603ADD5DE1A3676D6F75078D3F67 | |||
| 4944 | Update.tmp | C:\Users\admin\AppData\Local\Temp\is-AIPKT.tmp\isxdl.dll | executable | |
MD5:48AD1A1C893CE7BF456277A0A085ED01 | SHA256:B0CC4697B2FD1B4163FDDCA2050FC62A9E7D221864F1BD11E739144C90B685B3 | |||
| 4944 | Update.tmp | C:\Users\admin\AppData\Local\Temp\is-AIPKT.tmp\installation_bg.png | image | |
MD5:DE2910024C97296F74DB2929DD967810 | SHA256:DD2B1935E615891A2E29430CB2ADB9A07245510C16BB9336D76CBE8C48F79938 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
8
TCP/UDP connections
47
DNS requests
27
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3100 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
5944 | MoUsoCoreWorker.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
5944 | MoUsoCoreWorker.exe | GET | 200 | 23.55.104.172:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
7092 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
7092 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
2940 | svchost.exe | GET | 200 | 23.209.209.135:80 | http://x1.c.lencr.org/ | unknown | — | — | whitelisted |
3720 | backgroundTaskHost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEA77flR%2B3w%2FxBpruV2lte6A%3D | unknown | — | — | whitelisted |
4692 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
5944 | MoUsoCoreWorker.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1268 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
2468 | RUXIMICS.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2336 | svchost.exe | 172.211.123.250:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
3100 | svchost.exe | 20.190.159.68:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
3100 | svchost.exe | 2.17.190.73:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
4944 | DriverEasy_Setup.exe | 85.90.196.155:443 | gewgb.xyz | — | UA | unknown |
5944 | MoUsoCoreWorker.exe | 23.55.104.172:80 | crl.microsoft.com | Akamai International B.V. | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
gewgb.xyz |
| unknown |
nexusrules.officeapps.live.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |