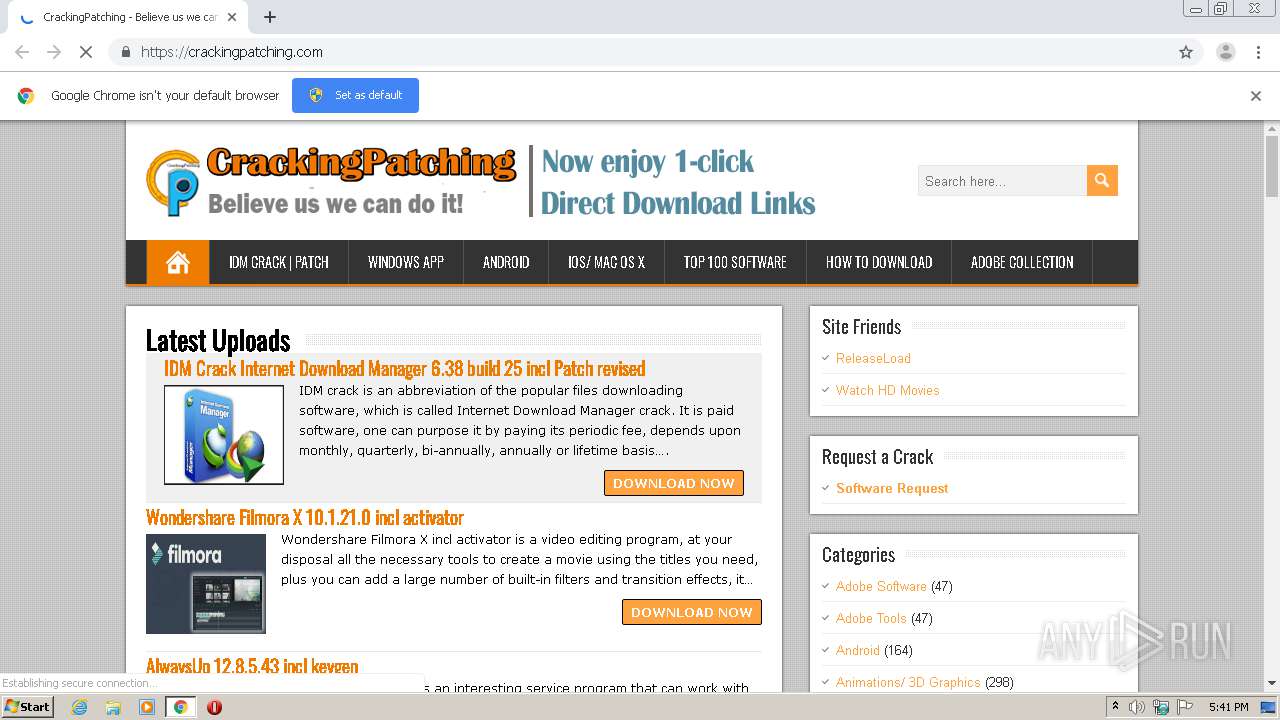
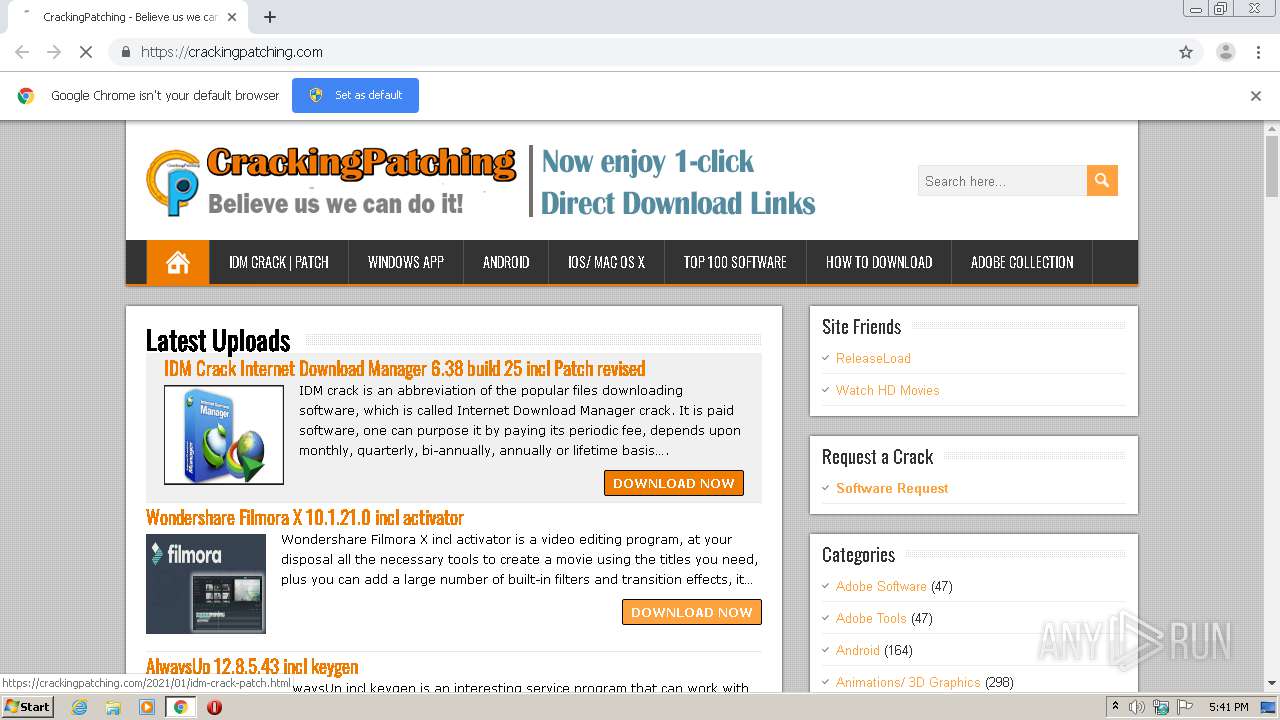
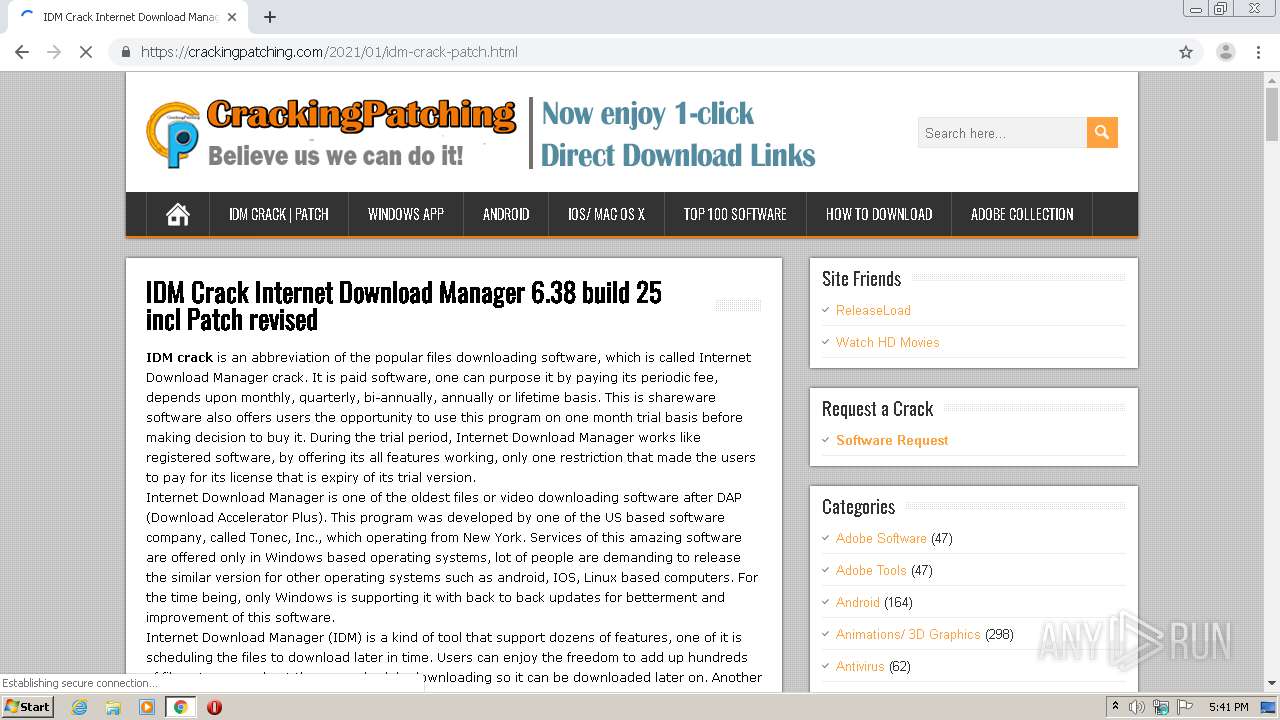
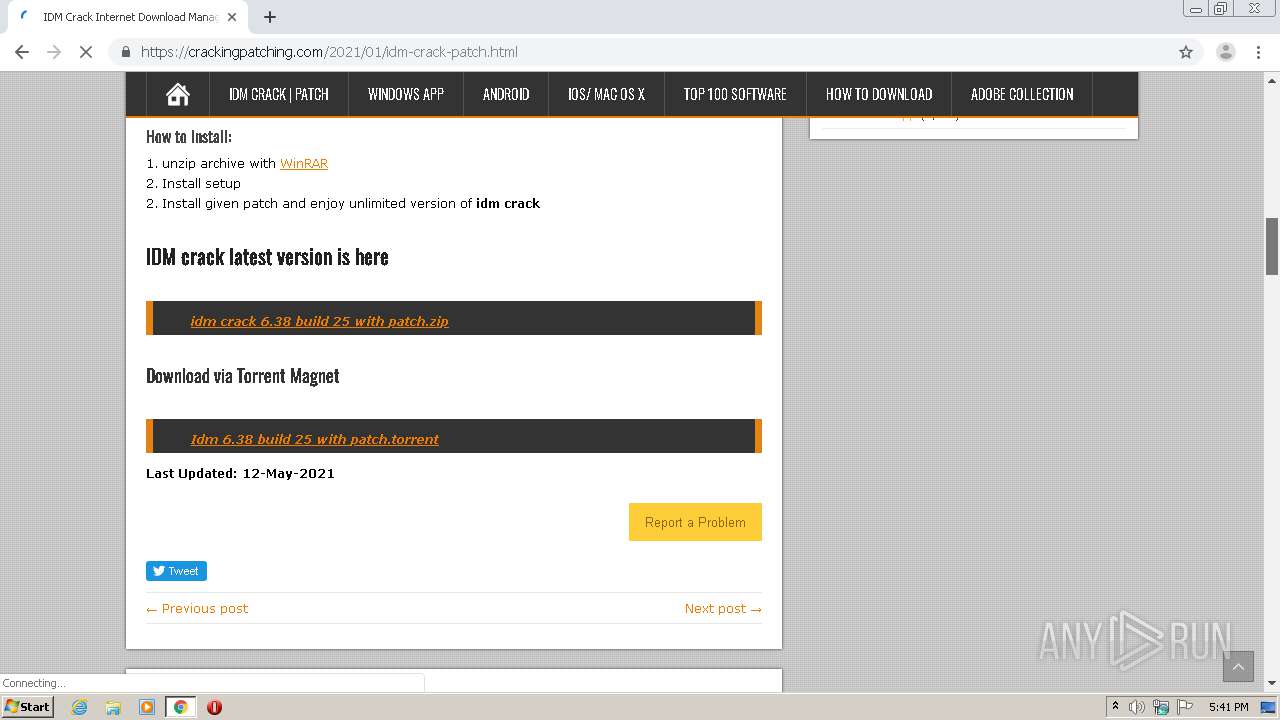
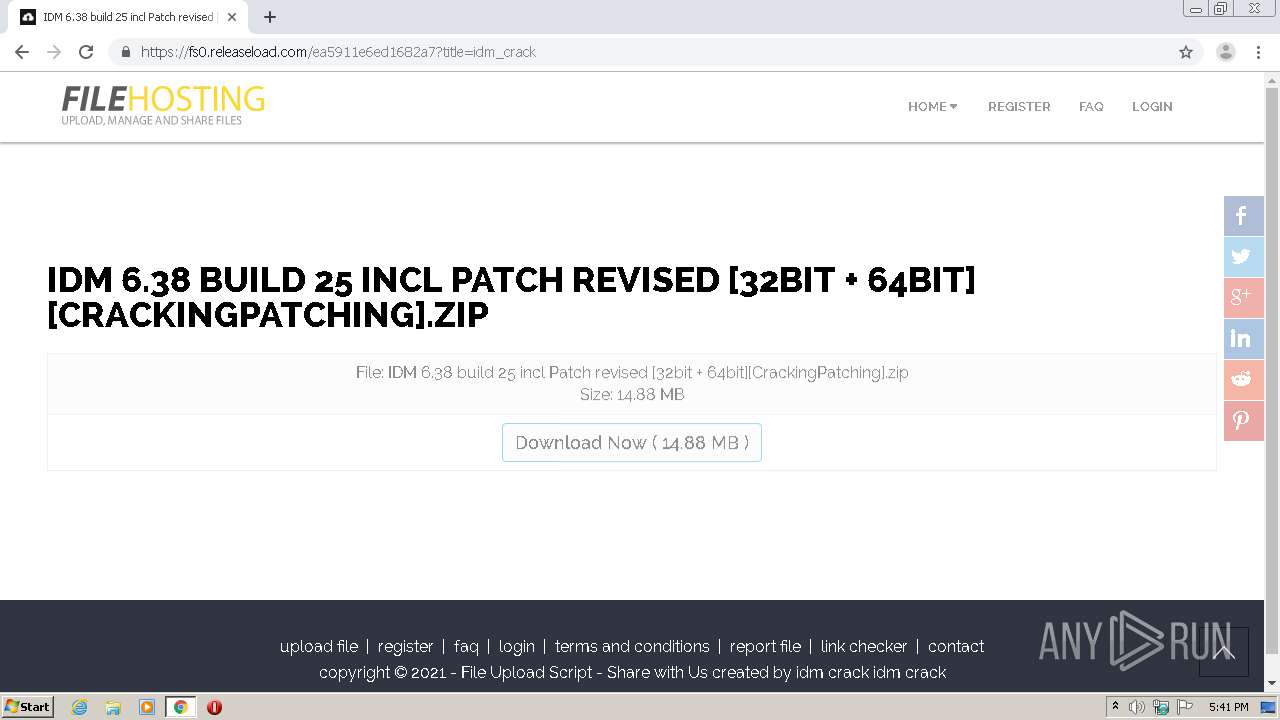
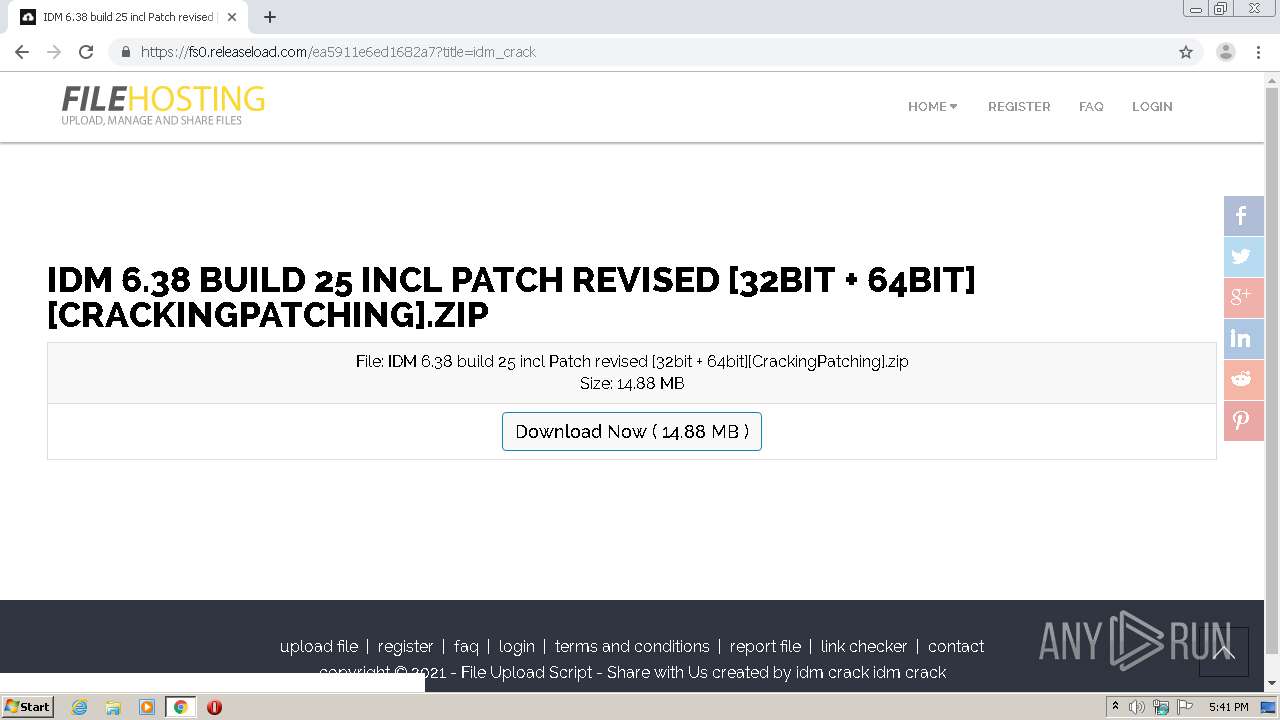
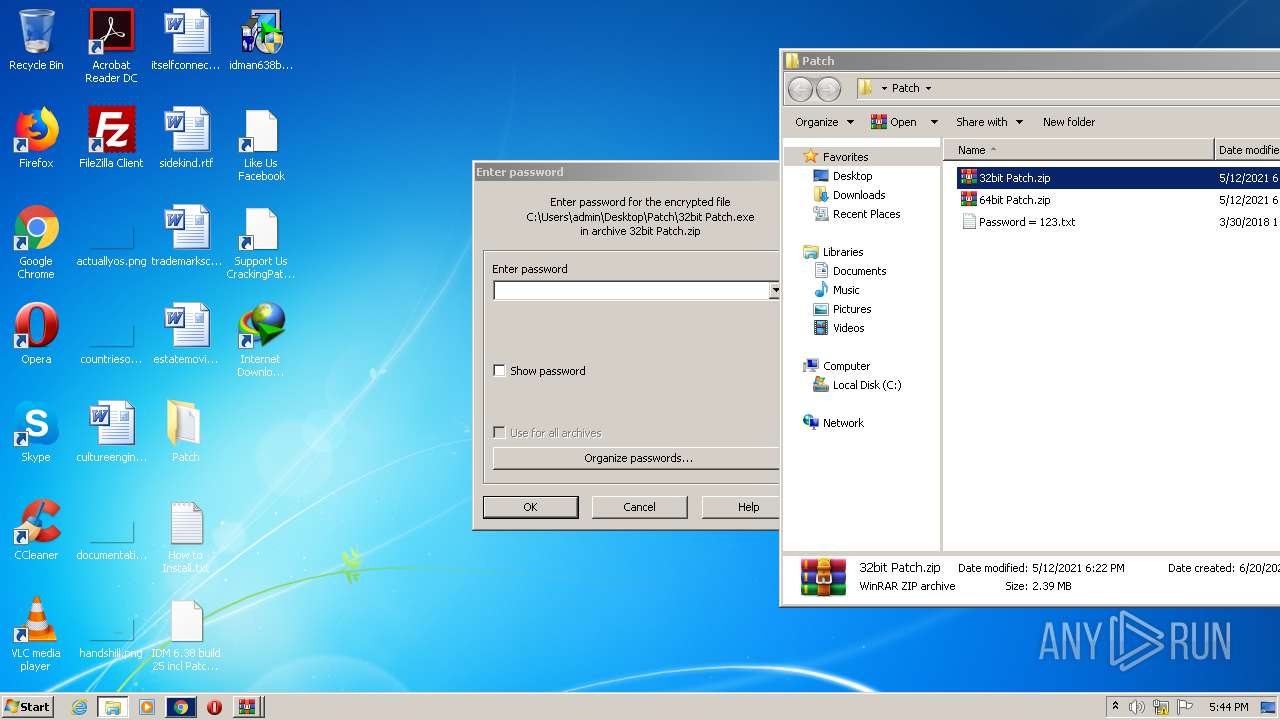
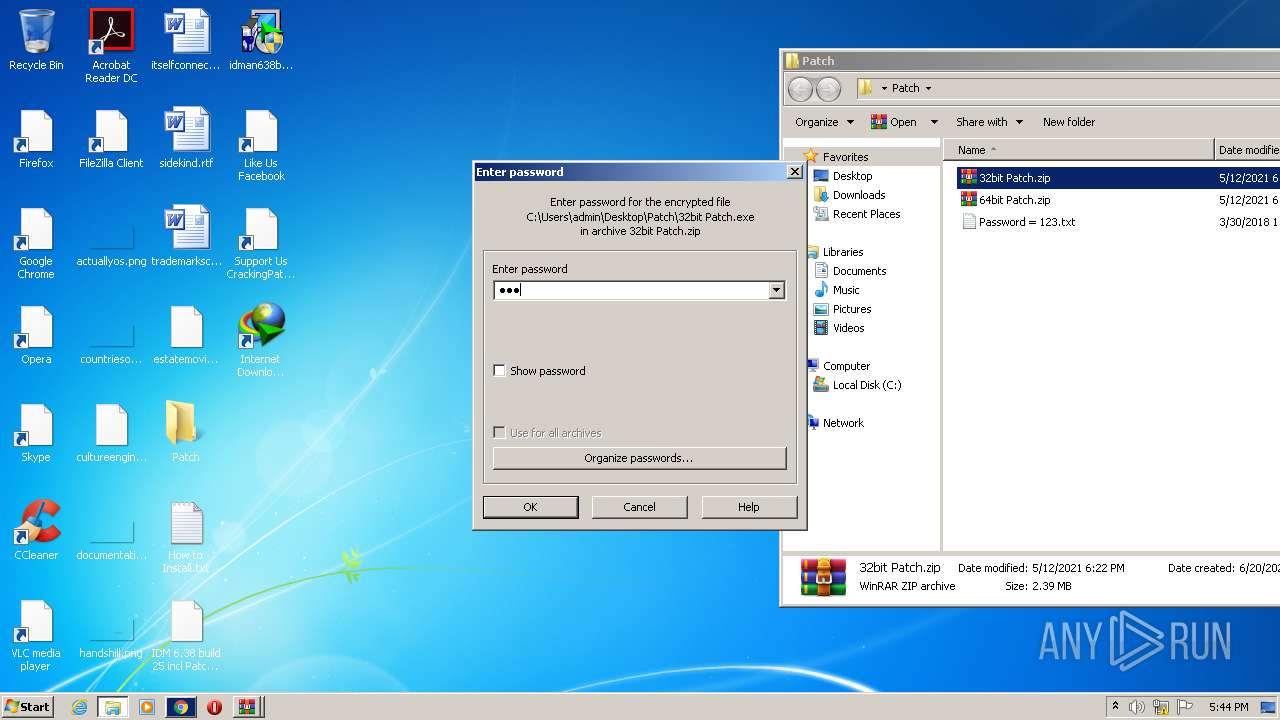
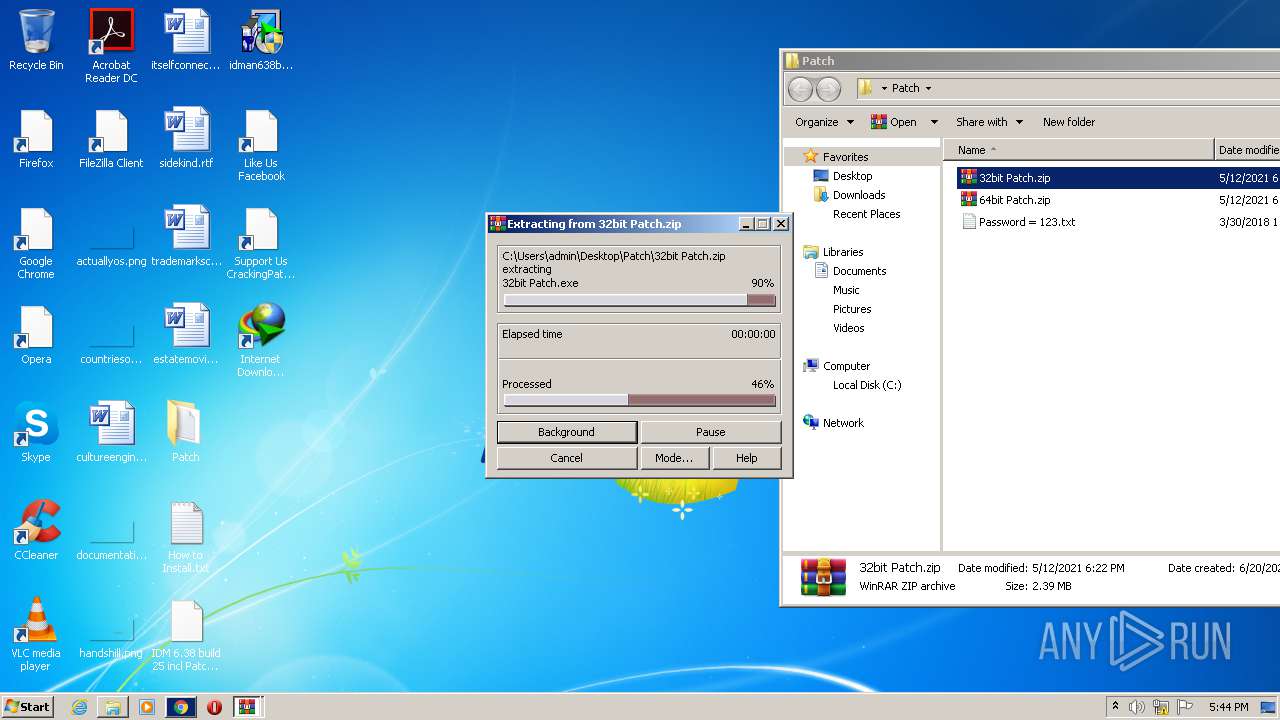
| URL: | https://crackingpatching.com |
| Full analysis: | https://app.any.run/tasks/e9a10df5-ad7d-403c-aaf9-906a95cf26a5 |
| Verdict: | Malicious activity |
| Threats: | Ransomware is a type of malicious software that locks users out of their system or data using different methods to force them to pay a ransom. Most often, such programs encrypt files on an infected machine and demand a fee to be paid in exchange for the decryption key. Additionally, such programs can be used to steal sensitive information from the compromised computer and even conduct DDoS attacks against affected organizations to pressure them into paying. |
| Analysis date: | June 20, 2021, 16:41:11 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MD5: | 06A22889B0F3C2F72BF62E53AFC6F336 |
| SHA1: | A199516A614354AFE70B6DCAE2CAF20C63A660E4 |
| SHA256: | 2B5516D3720B8342D91460D1E761BBC4362F67021E15D41AF704F844F0EE491E |
| SSDEEP: | 3:N8K/W5K7T:2KO5K7T |
MALICIOUS
Application was dropped or rewritten from another process
- idman638build25.exe (PID: 1672)
- idman638build25.exe (PID: 3536)
- 32bit Patch.exe (PID: 2060)
- 32bit Patch.exe (PID: 1492)
Changes settings of System certificates
- IDMan.exe (PID: 3192)
Starts NET.EXE for service management
- Uninstall.exe (PID: 3124)
Changes the autorun value in the registry
- rundll32.exe (PID: 2908)
- IDMan.exe (PID: 3192)
Drops executable file immediately after starts
- rundll32.exe (PID: 2908)
REMCOS was detected
- IDMan.exe (PID: 3192)
Executes PowerShell scripts
- cmd.exe (PID: 1428)
SUSPICIOUS
Executable content was dropped or overwritten
- WinRAR.exe (PID: 2040)
- IDMan.exe (PID: 3192)
- WinRAR.exe (PID: 3332)
- rundll32.exe (PID: 2908)
- 32bit Patch.exe (PID: 1492)
Creates files like Ransomware instruction
- WinRAR.exe (PID: 2040)
Creates a software uninstall entry
- IDM1.tmp (PID: 3696)
- 32bit Patch.exe (PID: 1492)
Starts application with an unusual extension
- idman638build25.exe (PID: 1672)
Creates files in the program directory
- IDM1.tmp (PID: 3696)
- IDMan.exe (PID: 3192)
- 32bit Patch.exe (PID: 1492)
- cmd.exe (PID: 1428)
Creates files in the user directory
- IDM1.tmp (PID: 3696)
- IDMan.exe (PID: 3192)
- powershell.exe (PID: 4788)
- powershell.exe (PID: 4868)
- powershell.exe (PID: 4648)
Creates/Modifies COM task schedule object
- IDM1.tmp (PID: 3696)
- IDMan.exe (PID: 3192)
- Uninstall.exe (PID: 3124)
Creates a directory in Program Files
- IDM1.tmp (PID: 3696)
Adds / modifies Windows certificates
- IDMan.exe (PID: 3192)
Drops a file that was compiled in debug mode
- IDMan.exe (PID: 3192)
- rundll32.exe (PID: 2908)
- 32bit Patch.exe (PID: 1492)
Uses RUNDLL32.EXE to load library
- Uninstall.exe (PID: 3124)
Removes files from Windows directory
- rundll32.exe (PID: 2908)
Creates or modifies windows services
- Uninstall.exe (PID: 3124)
Creates files in the driver directory
- rundll32.exe (PID: 2908)
Creates files in the Windows directory
- rundll32.exe (PID: 2908)
Drops a file with too old compile date
- WinRAR.exe (PID: 3332)
- 32bit Patch.exe (PID: 1492)
Starts Internet Explorer
- 32bit Patch.exe (PID: 1492)
Starts CMD.EXE for commands execution
- 32bit Patch.exe (PID: 1492)
- cmd.exe (PID: 1428)
Application launched itself
- cmd.exe (PID: 1428)
Uses TASKKILL.EXE to kill process
- cmd.exe (PID: 1428)
Uses WHOAMI.EXE to obtaining logged on user information
- cmd.exe (PID: 2264)
Uses REG.EXE to modify Windows registry
- cmd.exe (PID: 1428)
Executed via COM
- idmBroker.exe (PID: 6080)
INFO
Reads the hosts file
- chrome.exe (PID: 2208)
- chrome.exe (PID: 4032)
Application launched itself
- chrome.exe (PID: 2208)
- firefox.exe (PID: 924)
- firefox.exe (PID: 4012)
- iexplore.exe (PID: 2072)
- iexplore.exe (PID: 2508)
Manual execution by user
- idman638build25.exe (PID: 3536)
- idman638build25.exe (PID: 1672)
- WinRAR.exe (PID: 3332)
- firefox.exe (PID: 924)
- 32bit Patch.exe (PID: 2060)
- 32bit Patch.exe (PID: 1492)
Reads settings of System Certificates
- IDMan.exe (PID: 3192)
- iexplore.exe (PID: 2684)
- iexplore.exe (PID: 3308)
- iexplore.exe (PID: 2072)
- iexplore.exe (PID: 2508)
Dropped object may contain Bitcoin addresses
- IDMan.exe (PID: 3192)
Creates files in the user directory
- firefox.exe (PID: 4012)
- iexplore.exe (PID: 3308)
- iexplore.exe (PID: 2684)
Reads CPU info
- firefox.exe (PID: 4012)
Creates files in the program directory
- firefox.exe (PID: 4012)
Changes settings of System certificates
- pingsender.exe (PID: 2140)
- iexplore.exe (PID: 3308)
- iexplore.exe (PID: 2684)
Adds / modifies Windows certificates
- pingsender.exe (PID: 2140)
- iexplore.exe (PID: 2684)
- iexplore.exe (PID: 3308)
Changes internet zones settings
- iexplore.exe (PID: 2508)
- iexplore.exe (PID: 2072)
Reads internet explorer settings
- iexplore.exe (PID: 2684)
- iexplore.exe (PID: 3308)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
363
Monitored processes
307
Malicious processes
6
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 784 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1004,12449369484839315640,9803373241219076618,131072 --enable-features=PasswordImport --disable-gpu-compositing --lang=en-US --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=11406277018777982743 --renderer-client-id=23 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=3796 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 904 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1004,12449369484839315640,9803373241219076618,131072 --enable-features=PasswordImport --disable-gpu-compositing --lang=en-US --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=17421979736369538133 --renderer-client-id=31 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=5140 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 924 | "C:\Program Files\Mozilla Firefox\firefox.exe" https://www.internetdownloadmanager.com/support/installffextfrommozillasite.html | C:\Program Files\Mozilla Firefox\firefox.exe | — | explorer.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Exit code: 0 Version: 68.0.1 Modules
| |||||||||||||||
| 1008 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1004,12449369484839315640,9803373241219076618,131072 --enable-features=PasswordImport --disable-gpu-compositing --lang=en-US --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=13993423142522942858 --renderer-client-id=14 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=2924 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 1428 | cmd /c ""C:\Program Files\Internet Download Manager\IDM_Cleaner.bat" " | C:\Windows\system32\cmd.exe | — | 32bit Patch.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 1472 | reg query "HKLM\Software\Classes\Wow6432Node\CLSID\{E6871B76-C3C8-44DD-B947-ABFFE144860D}" | C:\Windows\system32\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Console Tool Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1472 | REG DELETE "HKCU\Software\Classes\Wow6432Node\CLSID\{D5B91409-A8CA-4973-9A0B-59F713D25671}" /f | C:\Windows\system32\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Console Tool Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
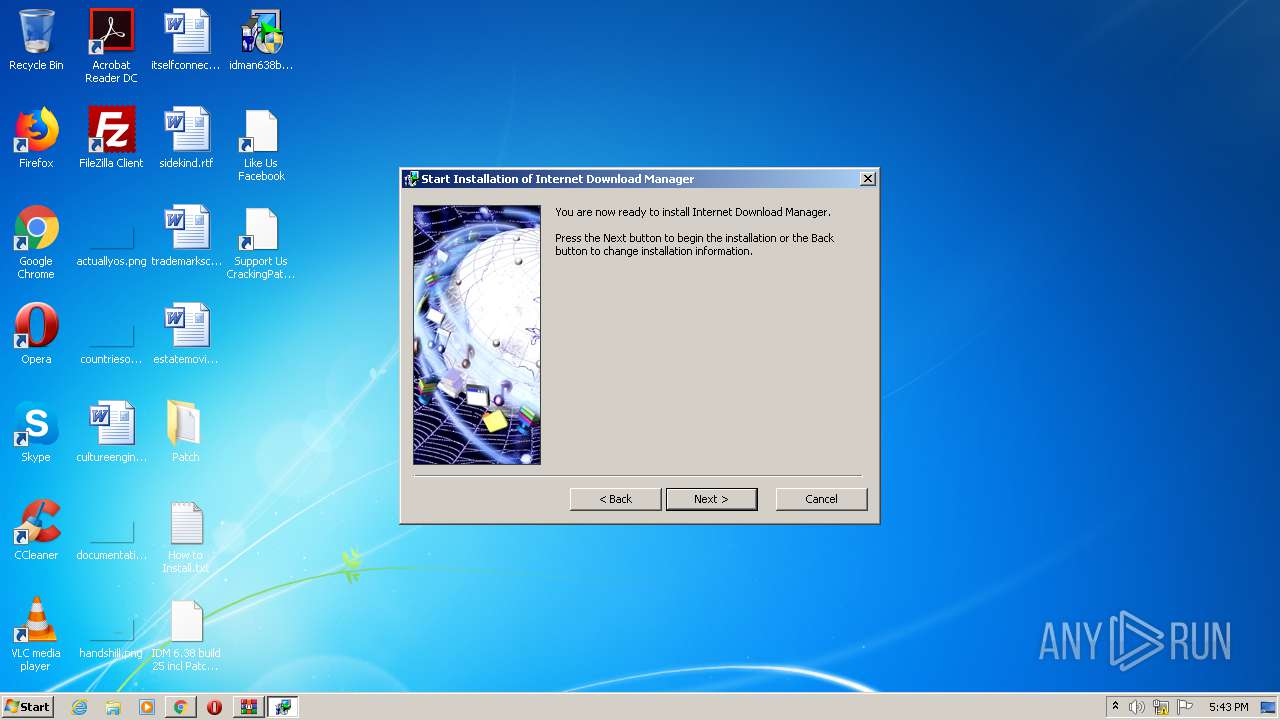
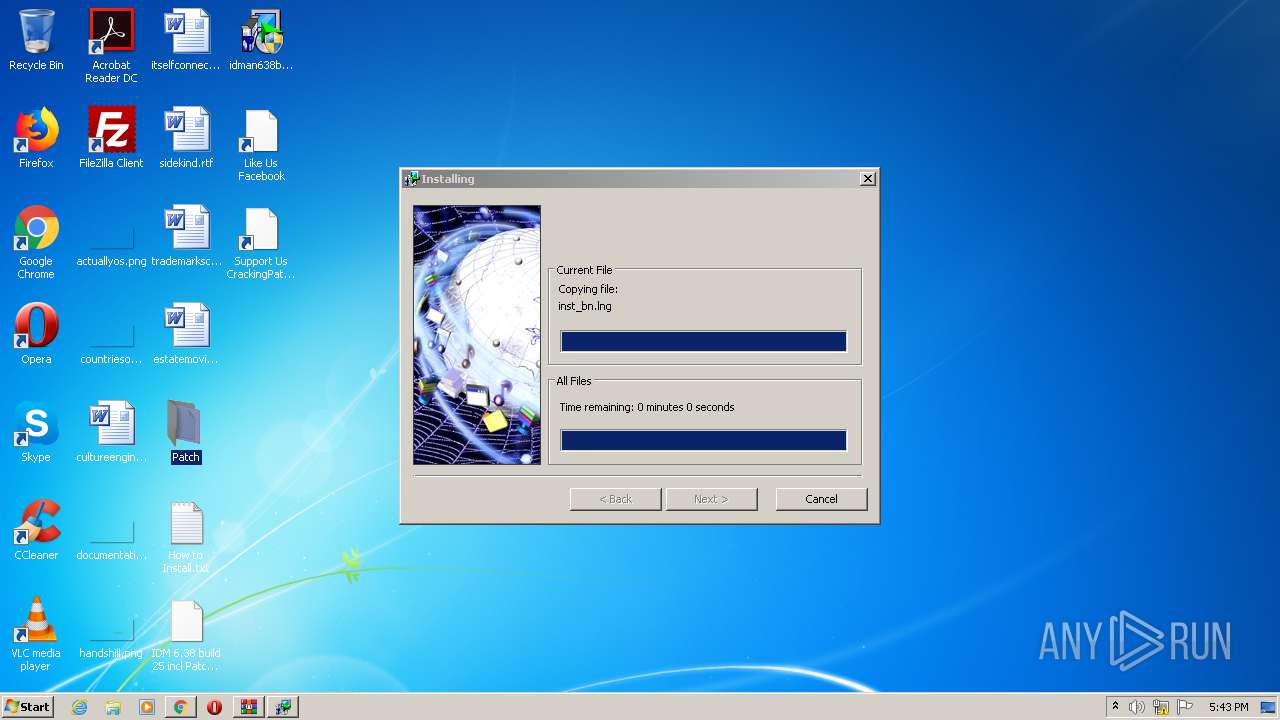
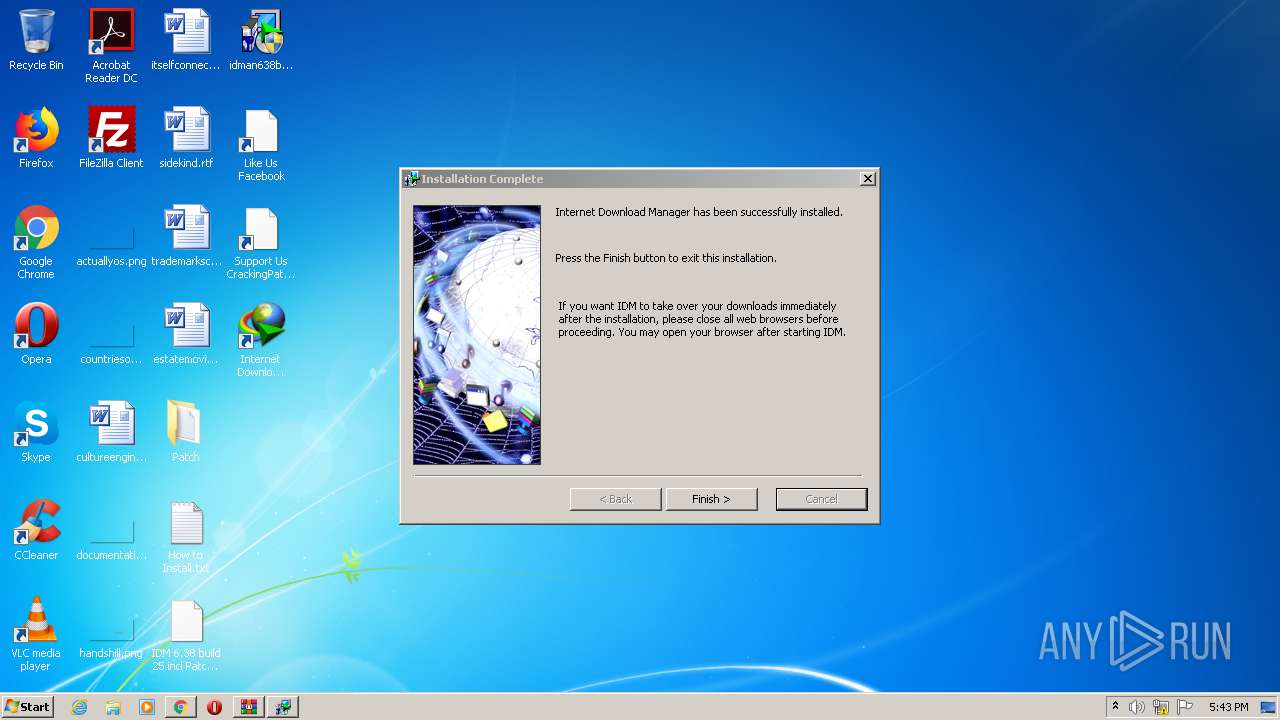
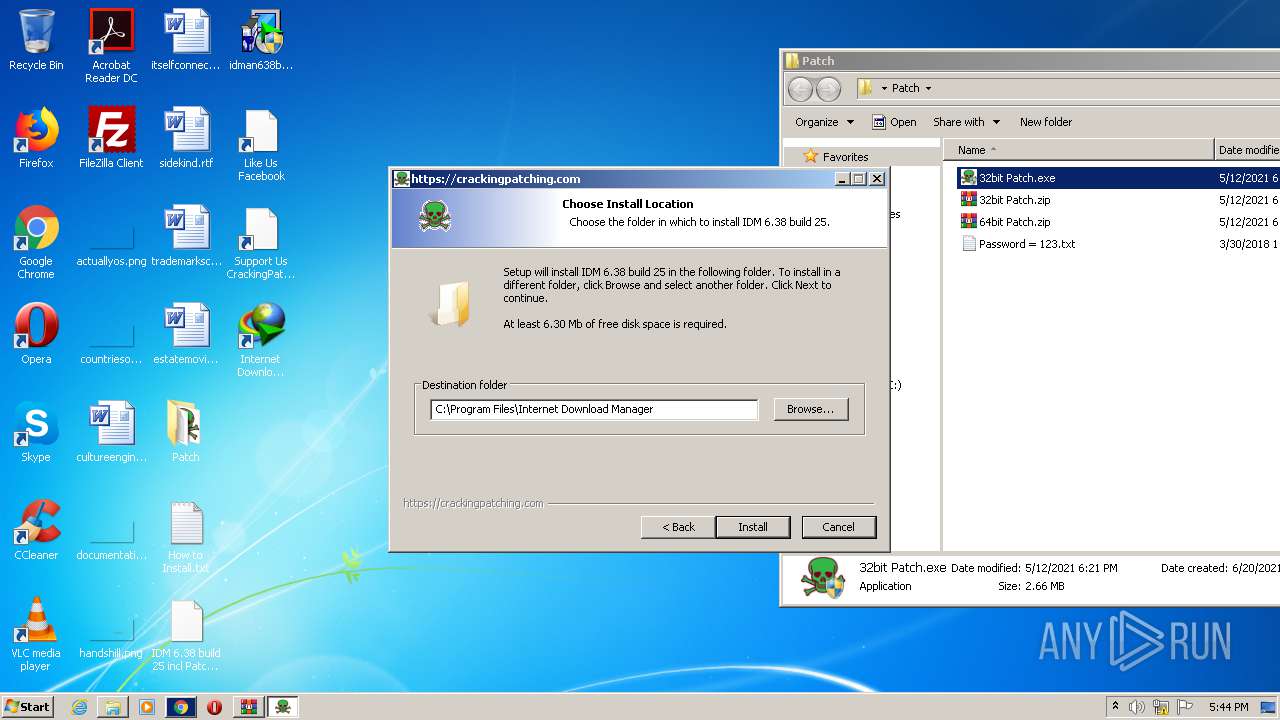
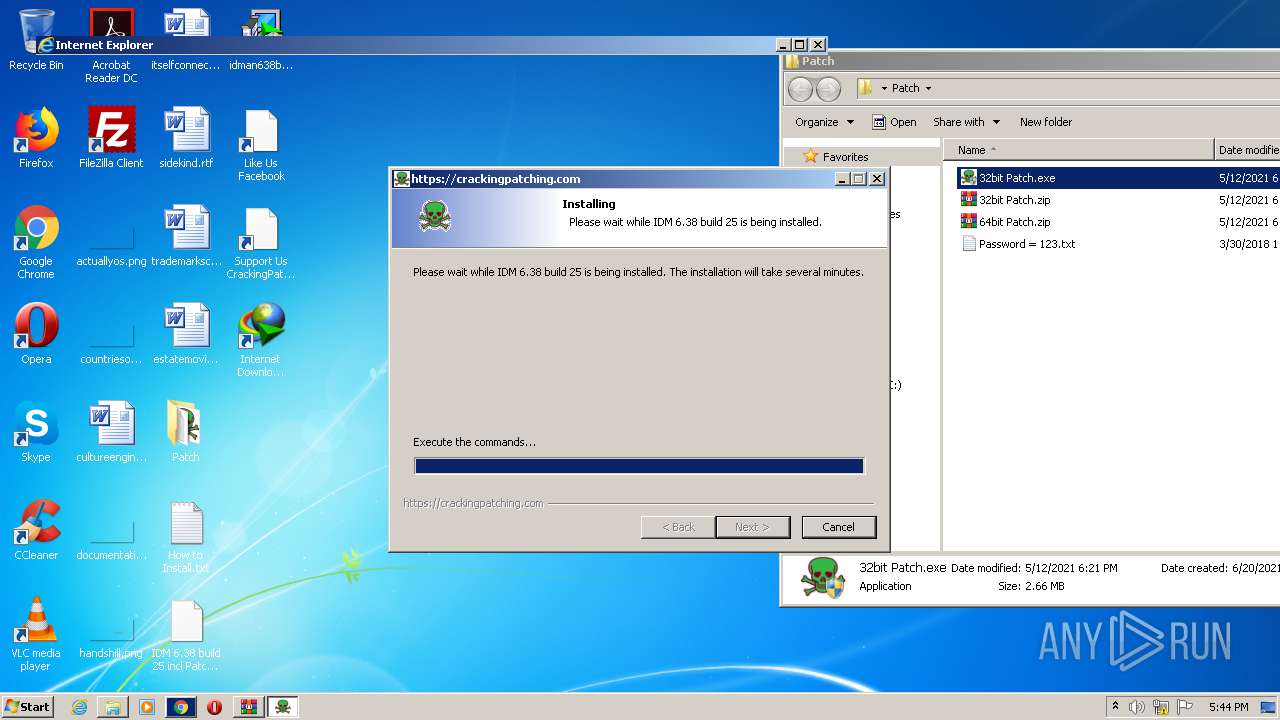
| 1492 | "C:\Users\admin\Desktop\Patch\32bit Patch.exe" | C:\Users\admin\Desktop\Patch\32bit Patch.exe | explorer.exe | ||||||||||||
User: admin Company: CrackingPatching Integrity Level: HIGH Description: IDM 6.38 build 25 6.38.25 Installation Exit code: 0 Version: 6.38.25 Modules
| |||||||||||||||
| 1496 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1004,12449369484839315640,9803373241219076618,131072 --enable-features=PasswordImport --disable-gpu-compositing --lang=en-US --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=5393188999808088254 --renderer-client-id=13 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=3284 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 1544 | REG DELETE "HKCU\Software\Classes\CLSID\{79873CC5-3951-43ED-BDF9-D8759474B6FD}" /f | C:\Windows\system32\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Console Tool Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
5 437
Read events
3 973
Write events
1 364
Delete events
100
Modification events
| (PID) Process: | (2208) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (2208) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
| (PID) Process: | (2208) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\ThirdParty |
| Operation: | write | Name: | StatusCodes |
Value: | |||
| (PID) Process: | (2208) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\ThirdParty |
| Operation: | write | Name: | StatusCodes |
Value: 01000000 | |||
| (PID) Process: | (2208) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 1 | |||
| (PID) Process: | (2208) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Update\ClientState\{8A69D345-D564-463c-AFF1-A69D9E530F96} |
| Operation: | write | Name: | dr |
Value: 1 | |||
| (PID) Process: | (1880) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BrowserExitCodes |
| Operation: | write | Name: | 2208-13268680883746750 |
Value: 259 | |||
| (PID) Process: | (2208) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome |
| Operation: | write | Name: | UsageStatsInSample |
Value: 0 | |||
| (PID) Process: | (2208) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BrowserExitCodes |
| Operation: | delete value | Name: | 3252-13245750958665039 |
Value: 0 | |||
| (PID) Process: | (2208) chrome.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Google\Update\ClientStateMedium\{8A69D345-D564-463C-AFF1-A69D9E530F96} |
| Operation: | write | Name: | usagestats |
Value: 0 | |||
Executable files
16
Suspicious files
411
Text files
356
Unknown types
100
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2208 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\BrowserMetrics\BrowserMetrics-60CF6FB4-8A0.pma | — | |
MD5:— | SHA256:— | |||
| 2208 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\498fe102-77d6-4477-86ae-8b1a097f42c3.tmp | — | |
MD5:— | SHA256:— | |||
| 2208 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Feature Engagement Tracker\AvailabilityDB\LOG.old | — | |
MD5:— | SHA256:— | |||
| 2208 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\data_reduction_proxy_leveldb\000048.dbtmp | — | |
MD5:— | SHA256:— | |||
| 2208 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Site Characteristics Database\LOG.old~RF13e080.TMP | text | |
MD5:— | SHA256:— | |||
| 2208 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Sync Data\LevelDB\LOG.old~RF13e080.TMP | text | |
MD5:— | SHA256:— | |||
| 2208 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\BudgetDatabase\LOG.old~RF13e0ce.TMP | text | |
MD5:— | SHA256:— | |||
| 2208 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Feature Engagement Tracker\EventDB\LOG.old~RF13e10c.TMP | text | |
MD5:— | SHA256:— | |||
| 2208 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\shared_proto_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 2208 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\shared_proto_db\LOG.old~RF13e2f1.TMP | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
88
TCP/UDP connections
234
DNS requests
120
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2684 | iexplore.exe | GET | 304 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTBL0V27RVZ7LBduom%2FnYB45SPUEwQU5Z1ZMIJHWMys%2BghUNoZ7OrUETfACEAo3h2ReX7SMIk79G%2B0UDDw%3D | US | — | — | whitelisted |
4032 | chrome.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTfqhLjKLEJQZPin0KCzkdAQpVYowQUsT7DaQP4v0cB1JgmGggC72NkK8MCEAKXB1YM1Knrv%2BJy8eCW2II%3D | US | der | 471 b | whitelisted |
3192 | IDMan.exe | GET | 304 | 93.184.221.240:80 | http://www.download.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab | US | compressed | 58.6 Kb | whitelisted |
2684 | iexplore.exe | GET | 200 | 151.139.128.14:80 | http://ocsp.comodoca.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBRTtU9uFqgVGHhJwXZyWCNXmVR5ngQUoBEKIz6W8Qfs4q8p74Klf9AwpLQCEDlyRDr5IrdR19NsEN0xNZU%3D | US | der | 471 b | whitelisted |
2684 | iexplore.exe | GET | 200 | 151.139.128.14:80 | http://ocsp.comodoca.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBRTtU9uFqgVGHhJwXZyWCNXmVR5ngQUoBEKIz6W8Qfs4q8p74Klf9AwpLQCEDlyRDr5IrdR19NsEN0xNZU%3D | US | der | 471 b | whitelisted |
2684 | iexplore.exe | GET | 200 | 151.139.128.14:80 | http://ocsp.usertrust.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTNMNJMNDqCqx8FcBWK16EHdimS6QQUU3m%2FWqorSs9UgOHYm8Cd8rIDZssCEH1bUSa0droR23QWC7xTDac%3D | US | der | 727 b | whitelisted |
2684 | iexplore.exe | GET | 200 | 151.139.128.14:80 | http://ocsp.usertrust.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTNMNJMNDqCqx8FcBWK16EHdimS6QQUU3m%2FWqorSs9UgOHYm8Cd8rIDZssCEH1bUSa0droR23QWC7xTDac%3D | US | der | 727 b | whitelisted |
2684 | iexplore.exe | GET | 304 | 151.139.128.14:80 | http://ocsp.usertrust.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTNMNJMNDqCqx8FcBWK16EHdimS6QQUU3m%2FWqorSs9UgOHYm8Cd8rIDZssCEH1bUSa0droR23QWC7xTDac%3D | US | der | 727 b | whitelisted |
2684 | iexplore.exe | GET | 304 | 151.139.128.14:80 | http://ocsp.usertrust.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTNMNJMNDqCqx8FcBWK16EHdimS6QQUU3m%2FWqorSs9UgOHYm8Cd8rIDZssCEH1bUSa0droR23QWC7xTDac%3D | US | der | 727 b | whitelisted |
2684 | iexplore.exe | GET | 200 | 151.139.128.14:80 | http://ocsp.usertrust.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTNMNJMNDqCqx8FcBWK16EHdimS6QQUU3m%2FWqorSs9UgOHYm8Cd8rIDZssCEH1bUSa0droR23QWC7xTDac%3D | US | der | 727 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4032 | chrome.exe | 172.67.219.95:443 | crackingpatching.com | — | US | malicious |
4032 | chrome.exe | 172.217.23.237:443 | accounts.google.com | Google Inc. | US | unknown |
4032 | chrome.exe | 192.0.77.37:443 | c0.wp.com | Automattic, Inc | US | suspicious |
4032 | chrome.exe | 216.58.201.66:443 | pagead2.googlesyndication.com | Google Inc. | US | whitelisted |
4032 | chrome.exe | 142.250.185.195:443 | fonts.gstatic.com | Google Inc. | US | whitelisted |
4032 | chrome.exe | 142.250.185.142:443 | apis.google.com | Google Inc. | US | whitelisted |
4032 | chrome.exe | 93.184.220.66:443 | platform.twitter.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
4032 | chrome.exe | 192.0.77.2:443 | i0.wp.com | Automattic, Inc | US | suspicious |
4032 | chrome.exe | 157.240.236.1:443 | connect.facebook.net | — | US | unknown |
4032 | chrome.exe | 192.0.76.3:443 | stats.wp.com | Automattic, Inc | US | suspicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
crackingpatching.com |
| malicious |
accounts.google.com |
| shared |
c0.wp.com |
| whitelisted |
fonts.googleapis.com |
| whitelisted |
pagead2.googlesyndication.com |
| whitelisted |
0.gravatar.com |
| whitelisted |
1.gravatar.com |
| whitelisted |
2.gravatar.com |
| whitelisted |
fonts.gstatic.com |
| whitelisted |
apis.google.com |
| whitelisted |