| File name: | Se adjunta nueva lista de pedidos.zip |
| Full analysis: | https://app.any.run/tasks/1522978b-b97a-4825-a3a7-d1b920a72d97 |
| Verdict: | Malicious activity |
| Threats: | FormBook is a data stealer that is being distributed as a MaaS. FormBook differs from a lot of competing malware by its extreme ease of use that allows even the unexperienced threat actors to use FormBook virus. |
| Analysis date: | August 12, 2022, 18:53:30 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract |
| MD5: | 4FED4FDB3354FD91CEEBC8E10A543146 |
| SHA1: | 929AEF6022B33C47B60998508D8B03808228E391 |
| SHA256: | 2B0ABA9B768F1F4449A65B2E85F0B94DDE5C9CA639F3DDB38184EB65B6ED02D5 |
| SSDEEP: | 6144:OlzUPZH09VW3uK4M2KDm9KrRUFPgoiyDajzmsUtdbcPzkCAiY83vgXuUkPYolYH6:czUZQg3u3eDmQCgoiyDqzm7bwkCVv/Ht |
MALICIOUS
Drops executable file immediately after starts
- WinRAR.exe (PID: 3448)
- Explorer.EXE (PID: 588)
- Se adjunta nueva lista de pedidos.exe (PID: 2744)
Application was dropped or rewritten from another process
- Se adjunta nueva lista de pedidos.exe (PID: 2744)
- Se adjunta nueva lista de pedidos.exe (PID: 3884)
Changes settings of System certificates
- Se adjunta nueva lista de pedidos.exe (PID: 2744)
- Se adjunta nueva lista de pedidos.exe (PID: 3884)
Changes the autorun value in the registry
- Se adjunta nueva lista de pedidos.exe (PID: 2744)
Actions looks like stealing of personal data
- cmstp.exe (PID: 1988)
FORMBOOK detected by memory dumps
- cmstp.exe (PID: 1988)
Connects to CnC server
- Explorer.EXE (PID: 588)
FORMBOOK was detected
- Explorer.EXE (PID: 588)
SUSPICIOUS
Checks supported languages
- WinRAR.exe (PID: 3448)
- Se adjunta nueva lista de pedidos.exe (PID: 2744)
- cmd.exe (PID: 2980)
- Se adjunta nueva lista de pedidos.exe (PID: 3884)
- cmd.exe (PID: 3492)
Reads the computer name
- WinRAR.exe (PID: 3448)
- Se adjunta nueva lista de pedidos.exe (PID: 2744)
- cmd.exe (PID: 2980)
- Se adjunta nueva lista de pedidos.exe (PID: 3884)
- cmd.exe (PID: 3492)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 3448)
- Se adjunta nueva lista de pedidos.exe (PID: 2744)
Drops a file with a compile date too recent
- WinRAR.exe (PID: 3448)
- Explorer.EXE (PID: 588)
- Se adjunta nueva lista de pedidos.exe (PID: 2744)
Adds / modifies Windows certificates
- Se adjunta nueva lista de pedidos.exe (PID: 2744)
- Se adjunta nueva lista de pedidos.exe (PID: 3884)
Reads Environment values
- cmstp.exe (PID: 1988)
Reads default file associations for system extensions
- Explorer.EXE (PID: 588)
Loads DLL from Mozilla Firefox
- cmstp.exe (PID: 1988)
INFO
Manual execution by user
- Se adjunta nueva lista de pedidos.exe (PID: 2744)
- cmstp.exe (PID: 1988)
- Se adjunta nueva lista de pedidos.exe (PID: 3884)
Reads settings of System Certificates
- Se adjunta nueva lista de pedidos.exe (PID: 2744)
- Se adjunta nueva lista de pedidos.exe (PID: 3884)
Checks Windows Trust Settings
- Se adjunta nueva lista de pedidos.exe (PID: 2744)
- Se adjunta nueva lista de pedidos.exe (PID: 3884)
Reads Microsoft Office registry keys
- Explorer.EXE (PID: 588)
Checks supported languages
- cmstp.exe (PID: 1988)
- Firefox.exe (PID: 772)
- Explorer.EXE (PID: 588)
- taskhost.exe (PID: 3780)
Reads the computer name
- cmstp.exe (PID: 1988)
- Firefox.exe (PID: 772)
- taskhost.exe (PID: 3780)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Formbook
(PID) Process(1988) cmstp.exe
C2www.xctech.world/3nop/�
Decoys and strings (143)USERNAME
LOCALAPPDATA
USERPROFILE
APPDATA
TEMP
ProgramFiles
CommonProgramFiles
ALLUSERSPROFILE
/c copy "
/c del "
\Run
\Policies
\Explorer
\Registry\User
\Registry\Machine
\SOFTWARE\Microsoft\Windows\CurrentVersion
Office\15.0\Outlook\Profiles\Outlook\
NT\CurrentVersion\Windows Messaging Subsystem\Profiles\Outlook\
\SOFTWARE\Mozilla\Mozilla
\Mozilla
Username:
Password:
formSubmitURL
usernameField
encryptedUsername
encryptedPassword
\logins.json
\signons.sqlite
\Microsoft\Vault\
SELECT encryptedUsername, encryptedPassword, formSubmitURL FROM moz_logins
\Google\Chrome\User Data\Default\Login Data
SELECT origin_url, username_value, password_value FROM logins
.exe
.com
.scr
.pif
.cmd
.bat
ms
win
gdi
mfc
vga
igfx
user
help
config
update
regsvc
chkdsk
systray
audiodg
certmgr
autochk
taskhost
colorcpl
services
IconCache
ThumbCache
Cookies
SeDebugPrivilege
SeShutdownPrivilege
\BaseNamedObjects
config.php
POST
HTTP/1.1
Host:
Connection: close
Content-Length:
Cache-Control: no-cache
Origin: http://
User-Agent: Mozilla Firefox/4.0
Content-Type: application/x-www-form-urlencoded
Accept: */*
Referer: http://
Accept-Language: en-US
Accept-Encoding: gzip, deflate
dat=
f-start
slot999.site
hagsahoy.com
howdyart.com
orders-marketplace.com
ranaa.email
masterlink.guru
archershut.com
weikumcommunications.com
dphardmoney.com
shjyutie.com
vivaberlin.net
mycto.today
curvygirlugc.com
otnmp.cfd
alwrists.com
propercandlecompany.com
allindustry-bg.com
theyoungbizacademy.com
expand658170.com
leslainesdumouchon.com
suptisa.com
picnic-in-andong.com
wanligui.com
cesarjunaro.com
kuxita.xyz
simpkecpr.com
microsoftsecuritys.com
responsefactor.com
polyggroup.com
talonxmfg.biz
jam-nins.com
picuar.com
familysafehidingplaces.com
centericehockey.com
appleidd.info
igctsansculottism.sbs
guiaestilosaude.online
happysscribe.com
tizzbizz.com
qcorretor.com
baremaster.online
liputanlima.com
ontherighttrack.systems
zzza002.xyz
k-aashirwaad.com
stillwatersagawork.com
skindoze.com
asdjmhfg.xyz
refaccionariafgnogales.com
hunn.pro
tlland.group
homebizen.com
newszi.xyz
nicetimecafe.net
qdbs.cloud
ebtl.wtf
dchasss.com
kijangjantan.tech
elegant-story.com
glimtmedia.com
1dot.online
neatneighborncclean.com
marionarzel.com
app-arthrex.com
f-end
Modules (42)kernel32.dll
advapi32.dll
ws2_32.dll
svchost.exe
msiexec.exe
wuauclt.exe
lsass.exe
wlanext.exe
msg.exe
lsm.exe
dwm.exe
help.exe
chkdsk.exe
cmmon32.exe
nbtstat.exe
spoolsv.exe
rdpclip.exe
control.exe
taskhost.exe
rundll32.exe
systray.exe
audiodg.exe
wininit.exe
services.exe
autochk.exe
autoconv.exe
autofmt.exe
cmstp.exe
colorcpl.exe
cscript.exe
explorer.exe
WWAHost.exe
ipconfig.exe
msdt.exe
mstsc.exe
NAPSTAT.EXE
netsh.exe
NETSTAT.EXE
raserver.exe
wscript.exe
wuapp.exe
cmd.exe
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
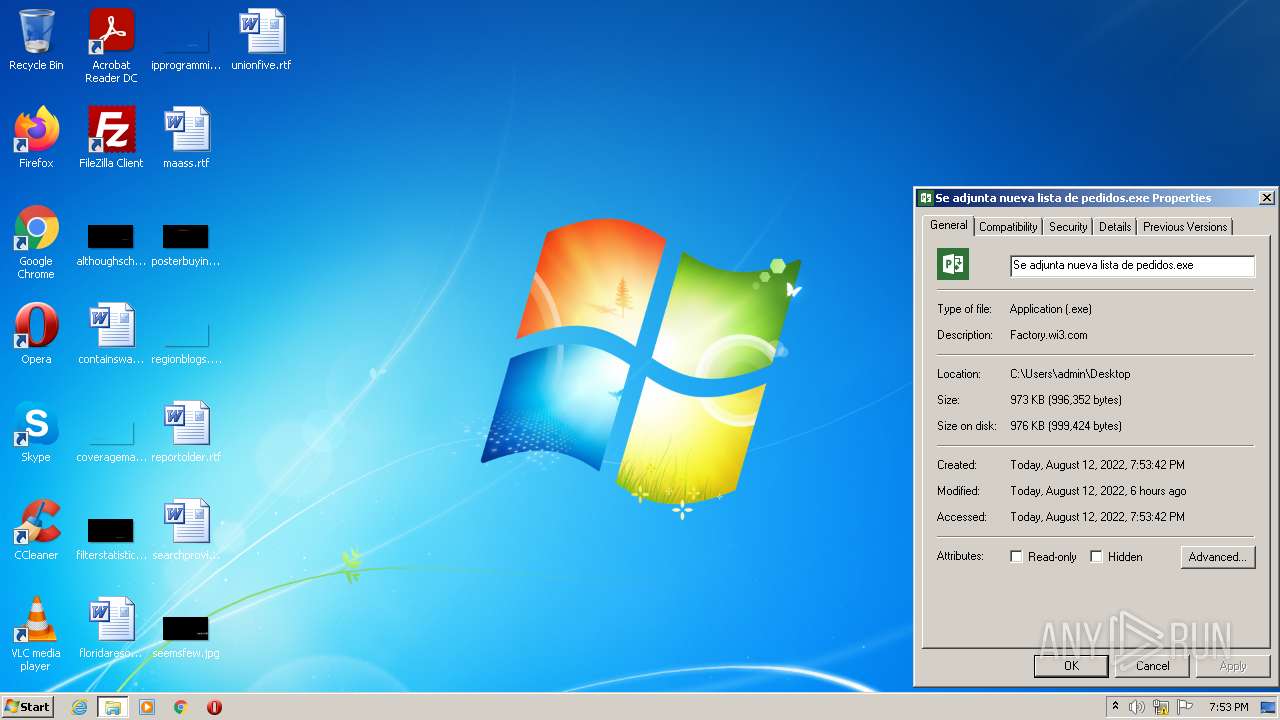
| ZipFileName: | Se adjunta nueva lista de pedidos.exe |
|---|---|
| ZipUncompressedSize: | 996352 |
| ZipCompressedSize: | 374596 |
| ZipCRC: | 0xa52468c1 |
| ZipModifyDate: | 2022:08:12 13:10:18 |
| ZipCompression: | Deflated |
| ZipBitFlag: | 0x0808 |
| ZipRequiredVersion: | 20 |
Total processes
49
Monitored processes
9
Malicious processes
4
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 588 | C:\Windows\Explorer.EXE | C:\Windows\Explorer.EXE | — | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 772 | "C:\Program Files\Mozilla Firefox\Firefox.exe" | C:\Program Files\Mozilla Firefox\Firefox.exe | — | cmstp.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Exit code: 0 Version: 83.0 Modules
| |||||||||||||||
| 1988 | "C:\Windows\System32\cmstp.exe" | C:\Windows\System32\cmstp.exe | Explorer.EXE | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Connection Manager Profile Installer Exit code: 0 Version: 7.02.7600.16385 (win7_rtm.090713-1255) Modules
Formbook(PID) Process(1988) cmstp.exe C2www.xctech.world/3nop/� Decoys and strings (143)USERNAME LOCALAPPDATA USERPROFILE APPDATA TEMP ProgramFiles CommonProgramFiles ALLUSERSPROFILE /c copy " /c del " \Run \Policies \Explorer \Registry\User \Registry\Machine \SOFTWARE\Microsoft\Windows\CurrentVersion Office\15.0\Outlook\Profiles\Outlook\ NT\CurrentVersion\Windows Messaging Subsystem\Profiles\Outlook\ \SOFTWARE\Mozilla\Mozilla \Mozilla Username: Password: formSubmitURL usernameField encryptedUsername encryptedPassword \logins.json \signons.sqlite \Microsoft\Vault\ SELECT encryptedUsername, encryptedPassword, formSubmitURL FROM moz_logins \Google\Chrome\User Data\Default\Login Data SELECT origin_url, username_value, password_value FROM logins .exe .com .scr .pif .cmd .bat ms win gdi mfc vga igfx user help config update regsvc chkdsk systray audiodg certmgr autochk taskhost colorcpl services IconCache ThumbCache Cookies SeDebugPrivilege SeShutdownPrivilege \BaseNamedObjects config.php POST HTTP/1.1 Host: Connection: close Content-Length: Cache-Control: no-cache Origin: http:// User-Agent: Mozilla Firefox/4.0 Content-Type: application/x-www-form-urlencoded Accept: */* Referer: http:// Accept-Language: en-US Accept-Encoding: gzip, deflate
dat= f-start slot999.site hagsahoy.com howdyart.com orders-marketplace.com ranaa.email masterlink.guru archershut.com weikumcommunications.com dphardmoney.com shjyutie.com vivaberlin.net mycto.today curvygirlugc.com otnmp.cfd alwrists.com propercandlecompany.com allindustry-bg.com theyoungbizacademy.com expand658170.com leslainesdumouchon.com suptisa.com picnic-in-andong.com wanligui.com cesarjunaro.com kuxita.xyz simpkecpr.com microsoftsecuritys.com responsefactor.com polyggroup.com talonxmfg.biz jam-nins.com picuar.com familysafehidingplaces.com centericehockey.com appleidd.info igctsansculottism.sbs guiaestilosaude.online happysscribe.com tizzbizz.com qcorretor.com baremaster.online liputanlima.com ontherighttrack.systems zzza002.xyz k-aashirwaad.com stillwatersagawork.com skindoze.com asdjmhfg.xyz refaccionariafgnogales.com hunn.pro tlland.group homebizen.com newszi.xyz nicetimecafe.net qdbs.cloud ebtl.wtf dchasss.com kijangjantan.tech elegant-story.com glimtmedia.com 1dot.online neatneighborncclean.com marionarzel.com app-arthrex.com f-end Modules (42)kernel32.dll advapi32.dll ws2_32.dll svchost.exe msiexec.exe wuauclt.exe lsass.exe wlanext.exe msg.exe lsm.exe dwm.exe help.exe chkdsk.exe cmmon32.exe nbtstat.exe spoolsv.exe rdpclip.exe control.exe taskhost.exe rundll32.exe systray.exe audiodg.exe wininit.exe services.exe autochk.exe autoconv.exe autofmt.exe cmstp.exe colorcpl.exe cscript.exe explorer.exe WWAHost.exe ipconfig.exe msdt.exe mstsc.exe NAPSTAT.EXE netsh.exe NETSTAT.EXE raserver.exe wscript.exe wuapp.exe cmd.exe | |||||||||||||||
| 2744 | "C:\Users\admin\Desktop\Se adjunta nueva lista de pedidos.exe" | C:\Users\admin\Desktop\Se adjunta nueva lista de pedidos.exe | Explorer.EXE | ||||||||||||
User: admin Company: e-m-Factory Integrity Level: MEDIUM Description: Factory.wi3.com Exit code: 0 Version: 2.69.0.0 Modules
| |||||||||||||||
| 2980 | "C:\Windows\System32\cmd.exe" | C:\Windows\System32\cmd.exe | — | Se adjunta nueva lista de pedidos.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 3448 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\Se adjunta nueva lista de pedidos.zip" | C:\Program Files\WinRAR\WinRAR.exe | Explorer.EXE | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 3492 | "C:\Windows\System32\cmd.exe" | C:\Windows\System32\cmd.exe | — | Se adjunta nueva lista de pedidos.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 3780 | "C:\Windows\System32\taskhost.exe" | C:\Windows\System32\taskhost.exe | — | Explorer.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Host Process for Windows Tasks Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3884 | "C:\Users\admin\Desktop\Se adjunta nueva lista de pedidos.exe" | C:\Users\admin\Desktop\Se adjunta nueva lista de pedidos.exe | Explorer.EXE | ||||||||||||
User: admin Company: e-m-Factory Integrity Level: HIGH Description: Factory.wi3.com Exit code: 0 Version: 2.69.0.0 Modules
| |||||||||||||||
Total events
19 731
Read events
18 838
Write events
890
Delete events
3
Modification events
| (PID) Process: | (3448) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (3448) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (3448) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\16C\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3448) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\virtio_ivshmem_master_build.zip | |||
| (PID) Process: | (3448) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (3448) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\Se adjunta nueva lista de pedidos.zip | |||
| (PID) Process: | (3448) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3448) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3448) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (3448) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
Executable files
3
Suspicious files
8
Text files
6
Unknown types
2
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 588 | Explorer.EXE | C:\Users\admin\Desktop\Se adjunta nueva lista de pedidos.exe | executable | |
MD5:— | SHA256:— | |||
| 3448 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3448.7775\Se adjunta nueva lista de pedidos.exe | executable | |
MD5:— | SHA256:— | |||
| 2744 | Se adjunta nueva lista de pedidos.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\6BADA8974A10C4BD62CC921D13E43B18_1DC6D7385EA816C957BA2B715AC5C442 | der | |
MD5:— | SHA256:— | |||
| 2744 | Se adjunta nueva lista de pedidos.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\NL2WCZ11.txt | text | |
MD5:— | SHA256:— | |||
| 2744 | Se adjunta nueva lista de pedidos.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\80237EE4964FC9C409AAF55BF996A292_C5130A0BDC8C859A2757D77746C10868 | binary | |
MD5:— | SHA256:— | |||
| 2744 | Se adjunta nueva lista de pedidos.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\80237EE4964FC9C409AAF55BF996A292_C5130A0BDC8C859A2757D77746C10868 | der | |
MD5:— | SHA256:— | |||
| 2744 | Se adjunta nueva lista de pedidos.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\6BADA8974A10C4BD62CC921D13E43B18_1DC6D7385EA816C957BA2B715AC5C442 | binary | |
MD5:— | SHA256:— | |||
| 2744 | Se adjunta nueva lista de pedidos.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\VE7C69O4.txt | text | |
MD5:— | SHA256:— | |||
| 2744 | Se adjunta nueva lista de pedidos.exe | C:\Users\Public\Libraries\Uewqcscdj.exe | executable | |
MD5:— | SHA256:— | |||
| 2744 | Se adjunta nueva lista de pedidos.exe | C:\Users\Public\Libraries\jdcscqweU.url | text | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
10
TCP/UDP connections
17
DNS requests
11
Threats
21
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
588 | Explorer.EXE | GET | — | 198.54.117.210:80 | http://www.howdyart.com/3nop/?OtfL=ZWeuCBjDUrXJeWoqD0IPMzsFSPSxibcJj/AddvcsWxs/E6WL+v9PeOaRP2LB1b1W8eXEyw==&V4bDn=lx4pYz9p0VsLZt&sql=1 | US | — | — | malicious |
2744 | Se adjunta nueva lista de pedidos.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTBL0V27RVZ7LBduom%2FnYB45SPUEwQU5Z1ZMIJHWMys%2BghUNoZ7OrUETfACEA%2BnRyLFPYjID1ie%2Bx%2BdSjo%3D | US | der | 1.47 Kb | whitelisted |
2744 | Se adjunta nueva lista de pedidos.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAqvpsXKY8RRQeo74ffHUxc%3D | US | der | 471 b | whitelisted |
588 | Explorer.EXE | GET | 404 | 91.184.0.100:80 | http://www.ranaa.email/3nop/?V4bDn=lx4pYz9p0VsLZt&OtfL=yMZYgScXJIvUHoH3OizUi/RKOG5S8QVEE00/Sn1aDoKpB/wKR3UFrjj9/MI7vLID0ZQ4bQ==&sql=1 | NL | html | 196 b | malicious |
588 | Explorer.EXE | POST | 404 | 91.184.0.100:80 | http://www.ranaa.email/3nop/ | NL | html | 196 b | malicious |
588 | Explorer.EXE | POST | 404 | 91.184.0.100:80 | http://www.ranaa.email/3nop/ | NL | html | 196 b | malicious |
588 | Explorer.EXE | POST | 404 | 91.184.0.100:80 | http://www.ranaa.email/3nop/ | NL | html | 196 b | malicious |
2744 | Se adjunta nueva lista de pedidos.exe | GET | 200 | 93.184.221.240:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?3d763b7475f26406 | US | compressed | 4.70 Kb | whitelisted |
588 | Explorer.EXE | POST | 405 | 198.54.117.210:80 | http://www.howdyart.com/3nop/ | US | html | 154 b | malicious |
588 | Explorer.EXE | POST | 405 | 198.54.117.210:80 | http://www.howdyart.com/3nop/ | US | html | 154 b | malicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2744 | Se adjunta nueva lista de pedidos.exe | 13.107.43.13:443 | onedrive.live.com | Microsoft Corporation | US | malicious |
2744 | Se adjunta nueva lista de pedidos.exe | 93.184.220.29:80 | ocsp.digicert.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
2744 | Se adjunta nueva lista de pedidos.exe | 93.184.221.240:80 | ctldl.windowsupdate.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
2744 | Se adjunta nueva lista de pedidos.exe | 13.107.42.12:443 | btz6og.ph.files.1drv.com | Microsoft Corporation | US | suspicious |
3884 | Se adjunta nueva lista de pedidos.exe | 13.107.42.12:443 | btz6og.ph.files.1drv.com | Microsoft Corporation | US | suspicious |
3884 | Se adjunta nueva lista de pedidos.exe | 13.107.42.13:443 | onedrive.live.com | Microsoft Corporation | US | malicious |
— | — | 91.184.0.100:80 | www.ranaa.email | Hostnet B.V. | NL | malicious |
588 | Explorer.EXE | 198.54.117.210:80 | www.howdyart.com | Namecheap, Inc. | US | malicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
onedrive.live.com |
| shared |
ctldl.windowsupdate.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
btz6og.ph.files.1drv.com |
| suspicious |
www.ranaa.email |
| malicious |
www.howdyart.com |
| malicious |
www.tlland.group |
| unknown |
Threats
PID | Process | Class | Message |
|---|---|---|---|
588 | Explorer.EXE | Generic Protocol Command Decode | SURICATA HTTP Unexpected Request body |
588 | Explorer.EXE | A Network Trojan was detected | ET TROJAN FormBook CnC Checkin (GET) |
588 | Explorer.EXE | A Network Trojan was detected | ET TROJAN FormBook CnC Checkin (GET) |
588 | Explorer.EXE | A Network Trojan was detected | ET TROJAN FormBook CnC Checkin (GET) |
588 | Explorer.EXE | Potentially Bad Traffic | AV INFO HTTP Request to a *.email Domain |
588 | Explorer.EXE | Potentially Bad Traffic | AV INFO HTTP Request to a *.email Domain |
588 | Explorer.EXE | Generic Protocol Command Decode | SURICATA HTTP Unexpected Request body |
588 | Explorer.EXE | Generic Protocol Command Decode | SURICATA HTTP Unexpected Request body |
588 | Explorer.EXE | Potentially Bad Traffic | AV INFO HTTP Request to a *.email Domain |
588 | Explorer.EXE | Potentially Bad Traffic | AV INFO HTTP Request to a *.email Domain |
4 ETPRO signatures available at the full report