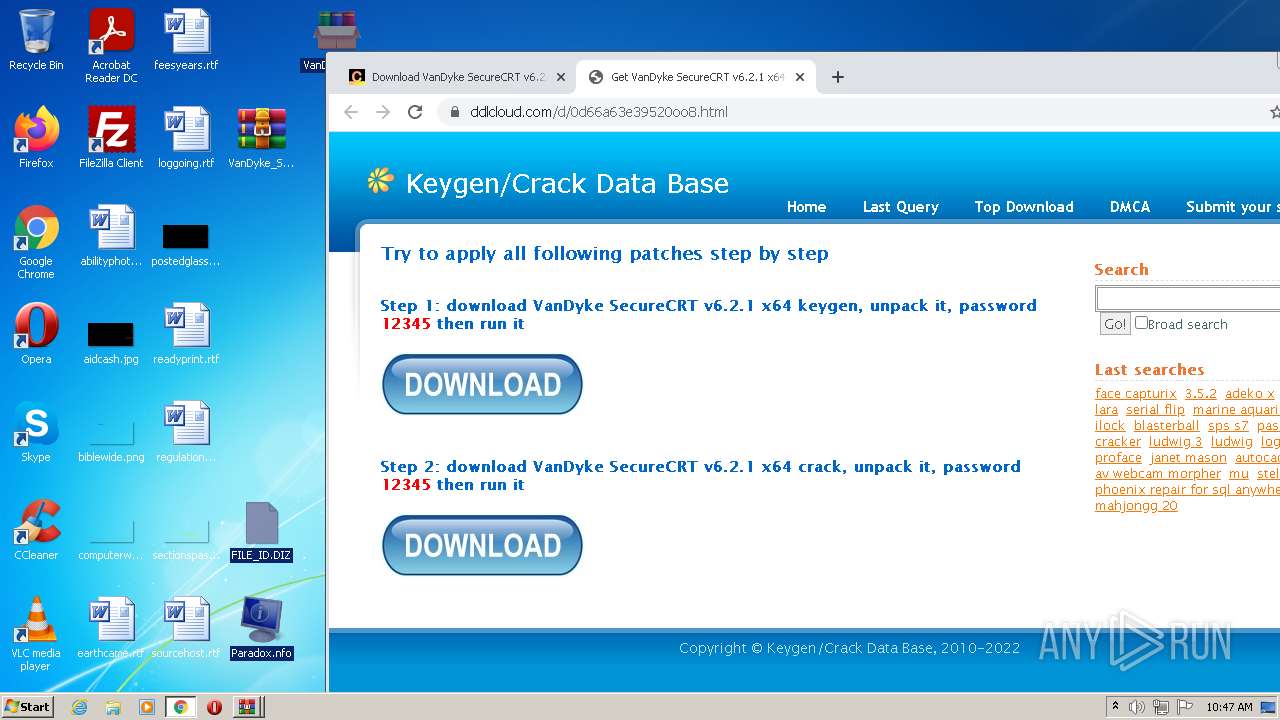
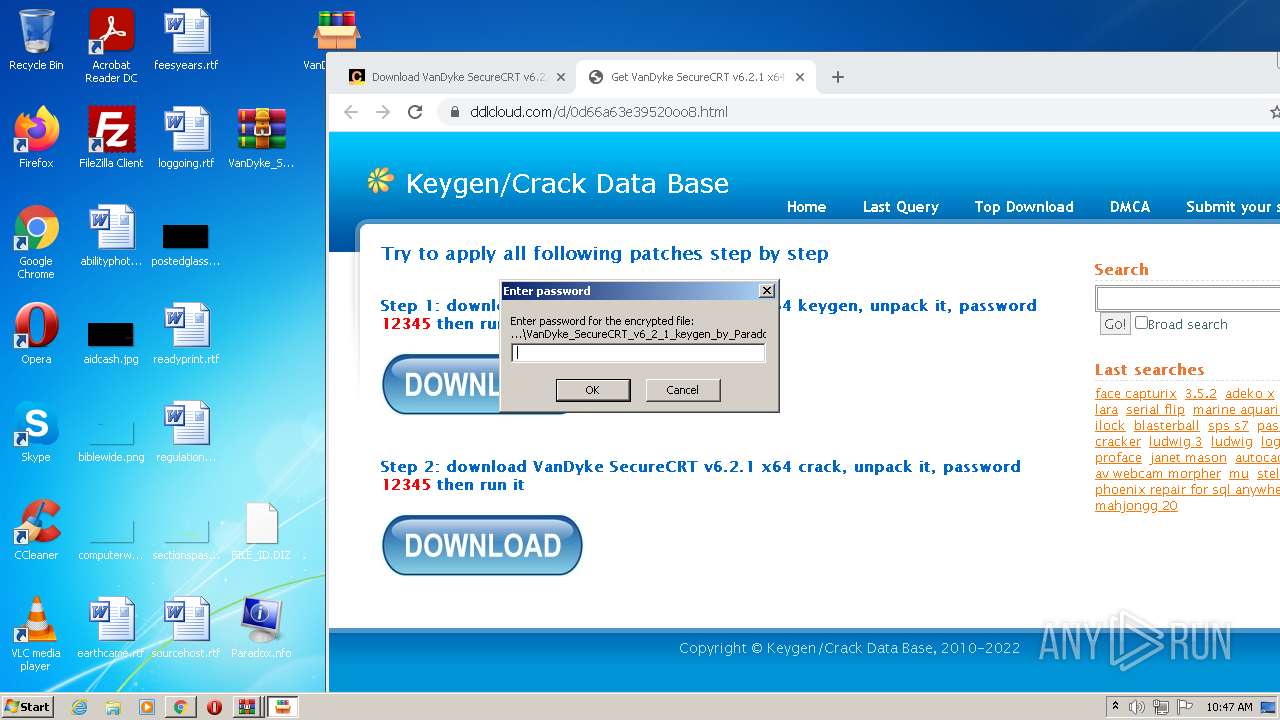
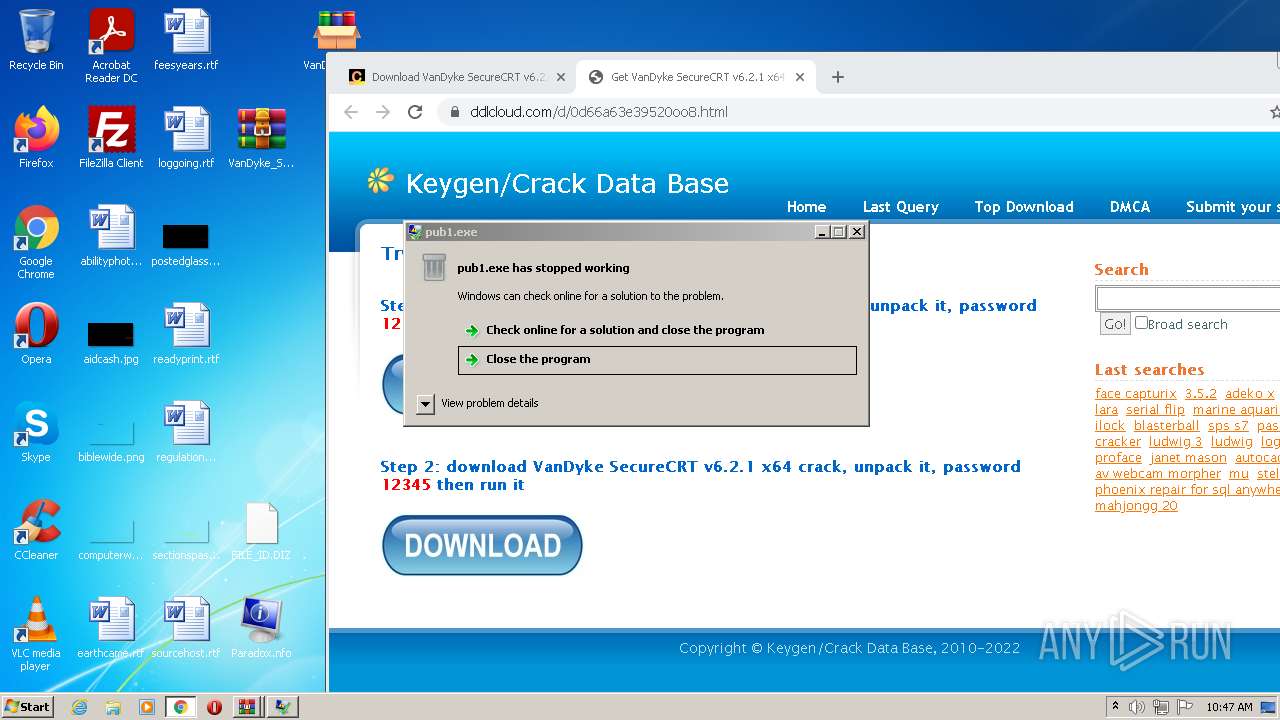
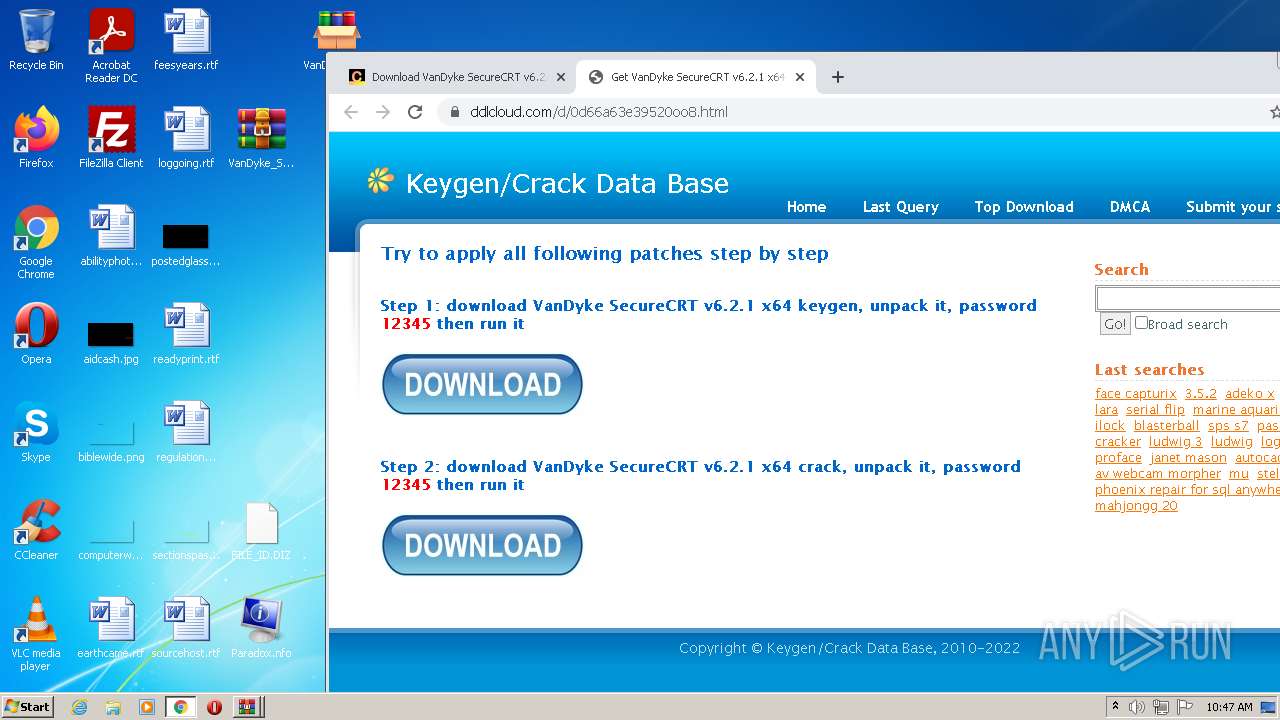
| URL: | https://cracksgurus.com/crack/VanDyke-SecureCRT-v6.2.1-x64-keygen-by-TBE-bee51a7910.html |
| Full analysis: | https://app.any.run/tasks/bc19eebf-67a0-4e4a-a84b-75dde6707fd4 |
| Verdict: | Malicious activity |
| Threats: | AZORult can steal banking information, including passwords and credit card details, as well as cryptocurrency. This constantly updated information stealer malware should not be taken lightly, as it continues to be an active threat. |
| Analysis date: | January 27, 2022, 10:46:10 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MD5: | 596E6D61BAA004CBA15C41D13E7C02F4 |
| SHA1: | FD712AB49F1D5658107CEF4C9F3155463E0F9FEC |
| SHA256: | 2AA71CAFFD894B54749F86119E563246062FFEAF943AB463AB370F5281B0FF15 |
| SSDEEP: | 3:N8KZzyTdXWKzE2Q2j63qLRR7DLIH5hg6j0n:2KcTdXWZ2Q2JX7XIHZ0n |
MALICIOUS
Application was dropped or rewritten from another process
- VanDyke_SecureCRT_v6_2_1_keygen_by_Paradox.exe (PID: 2072)
- keygen-step-1.exe (PID: 2212)
- keygen-step-6.exe (PID: 2776)
- keygen-step-4.exe (PID: 3704)
- keygen-pr.exe (PID: 3264)
- keygen-step-5.exe (PID: 2824)
- KiffAppE2.exe (PID: 2096)
- Crack.exe (PID: 2312)
- key.exe (PID: 2900)
- Crack.exe (PID: 3784)
- pub1.exe (PID: 148)
- lows.exe (PID: 3324)
- 2EDA.tmp.exe (PID: 684)
- key.exe (PID: 292)
- 34B7.tmp.exe (PID: 636)
Drops executable file immediately after starts
- keygen-step-5.exe (PID: 2824)
- keygen-step-4.exe (PID: 3704)
- keygen-pr.exe (PID: 3264)
Registers / Runs the DLL via REGSVR32.EXE
- keygen-step-5.exe (PID: 2824)
AZORULT was detected
- keygen-step-1.exe (PID: 2212)
Connects to CnC server
- keygen-step-1.exe (PID: 2212)
- key.exe (PID: 292)
Steals credentials from Web Browsers
- key.exe (PID: 292)
Changes settings of System certificates
- lows.exe (PID: 3324)
- Crack.exe (PID: 3784)
Detected Pony/Fareit Trojan
- key.exe (PID: 292)
Actions looks like stealing of personal data
- key.exe (PID: 292)
Runs injected code in another process
- rundll32.exe (PID: 2348)
Writes to a start menu file
- 2EDA.tmp.exe (PID: 684)
Application was injected by another process
- svchost.exe (PID: 924)
Loads dropped or rewritten executable
- rundll32.exe (PID: 2348)
PONY was detected
- key.exe (PID: 292)
SUSPICIOUS
Reads the computer name
- WinRAR.exe (PID: 1372)
- WinRAR.exe (PID: 1872)
- VanDyke_SecureCRT_v6_2_1_keygen_by_Paradox.exe (PID: 2072)
- keygen-step-1.exe (PID: 2212)
- keygen-step-6.exe (PID: 2776)
- keygen-step-5.exe (PID: 2824)
- keygen-step-4.exe (PID: 3704)
- keygen-pr.exe (PID: 3264)
- Crack.exe (PID: 2312)
- Crack.exe (PID: 3784)
- KiffAppE2.exe (PID: 2096)
- key.exe (PID: 2900)
- key.exe (PID: 292)
- lows.exe (PID: 3324)
- 34B7.tmp.exe (PID: 636)
Drops a file that was compiled in debug mode
- WinRAR.exe (PID: 1872)
- VanDyke_SecureCRT_v6_2_1_keygen_by_Paradox.exe (PID: 2072)
- keygen-step-4.exe (PID: 3704)
- keygen-step-6.exe (PID: 2776)
- 2EDA.tmp.exe (PID: 684)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 1872)
- VanDyke_SecureCRT_v6_2_1_keygen_by_Paradox.exe (PID: 2072)
- keygen-step-5.exe (PID: 2824)
- keygen-step-4.exe (PID: 3704)
- keygen-pr.exe (PID: 3264)
- Crack.exe (PID: 3784)
- keygen-step-6.exe (PID: 2776)
- 2EDA.tmp.exe (PID: 684)
Checks supported languages
- WinRAR.exe (PID: 1872)
- VanDyke_SecureCRT_v6_2_1_keygen_by_Paradox.exe (PID: 2072)
- WinRAR.exe (PID: 1372)
- keygen-step-1.exe (PID: 2212)
- cmd.exe (PID: 524)
- keygen-pr.exe (PID: 3264)
- keygen-step-6.exe (PID: 2776)
- keygen-step-4.exe (PID: 3704)
- keygen-step-5.exe (PID: 2824)
- key.exe (PID: 292)
- Crack.exe (PID: 2312)
- Crack.exe (PID: 3784)
- KiffAppE2.exe (PID: 2096)
- key.exe (PID: 2900)
- pub1.exe (PID: 148)
- lows.exe (PID: 3324)
- cmd.exe (PID: 1688)
- 2EDA.tmp.exe (PID: 684)
- 34B7.tmp.exe (PID: 636)
- cmd.exe (PID: 1784)
Drops a file with too old compile date
- VanDyke_SecureCRT_v6_2_1_keygen_by_Paradox.exe (PID: 2072)
- keygen-step-5.exe (PID: 2824)
Starts CMD.EXE for commands execution
- VanDyke_SecureCRT_v6_2_1_keygen_by_Paradox.exe (PID: 2072)
- lows.exe (PID: 3324)
- keygen-step-6.exe (PID: 2776)
Reads Environment values
- keygen-step-1.exe (PID: 2212)
- KiffAppE2.exe (PID: 2096)
- key.exe (PID: 2900)
- 34B7.tmp.exe (PID: 636)
Drops a file with a compile date too recent
- keygen-step-4.exe (PID: 3704)
- Crack.exe (PID: 3784)
- keygen-step-6.exe (PID: 2776)
Application launched itself
- Crack.exe (PID: 2312)
- key.exe (PID: 292)
Reads Windows Product ID
- key.exe (PID: 2900)
Reads the Windows organization settings
- key.exe (PID: 2900)
Reads Windows owner or organization settings
- key.exe (PID: 2900)
Creates files in the user directory
- keygen-step-6.exe (PID: 2776)
- key.exe (PID: 292)
- 2EDA.tmp.exe (PID: 684)
Loads DLL from Mozilla Firefox
- key.exe (PID: 292)
Adds / modifies Windows certificates
- lows.exe (PID: 3324)
- Crack.exe (PID: 3784)
Uses TASKKILL.EXE to kill process
- cmd.exe (PID: 1688)
Executed via WMI
- rundll32.exe (PID: 2348)
Dropped object may contain URLs of mainers pools
- keygen-step-6.exe (PID: 2776)
Starts CMD.EXE for self-deleting
- keygen-step-6.exe (PID: 2776)
Searches for installed software
- key.exe (PID: 292)
- key.exe (PID: 2900)
INFO
Checks supported languages
- chrome.exe (PID: 1536)
- chrome.exe (PID: 1888)
- chrome.exe (PID: 2972)
- chrome.exe (PID: 2840)
- chrome.exe (PID: 1236)
- chrome.exe (PID: 2708)
- chrome.exe (PID: 2464)
- chrome.exe (PID: 3972)
- chrome.exe (PID: 2764)
- chrome.exe (PID: 2992)
- chrome.exe (PID: 652)
- chrome.exe (PID: 2652)
- chrome.exe (PID: 2436)
- chrome.exe (PID: 2080)
- chrome.exe (PID: 2868)
- regsvr32.exe (PID: 3456)
- chrome.exe (PID: 3452)
- svchost.exe (PID: 924)
- taskkill.exe (PID: 2388)
- rundll32.exe (PID: 2348)
- chrome.exe (PID: 2540)
- PING.EXE (PID: 2096)
- chrome.exe (PID: 4036)
- chrome.exe (PID: 3200)
- chrome.exe (PID: 3880)
- chrome.exe (PID: 852)
- chrome.exe (PID: 3888)
- chrome.exe (PID: 3612)
Application launched itself
- chrome.exe (PID: 1536)
Reads the hosts file
- chrome.exe (PID: 1536)
- chrome.exe (PID: 3972)
Reads the computer name
- chrome.exe (PID: 2840)
- chrome.exe (PID: 3972)
- chrome.exe (PID: 1236)
- chrome.exe (PID: 1536)
- chrome.exe (PID: 2708)
- chrome.exe (PID: 2080)
- chrome.exe (PID: 2868)
- chrome.exe (PID: 2764)
- chrome.exe (PID: 2436)
- chrome.exe (PID: 3452)
- rundll32.exe (PID: 2348)
- PING.EXE (PID: 2096)
- taskkill.exe (PID: 2388)
Reads settings of System Certificates
- chrome.exe (PID: 3972)
- keygen-step-6.exe (PID: 2776)
- KiffAppE2.exe (PID: 2096)
- lows.exe (PID: 3324)
- Crack.exe (PID: 3784)
Manual execution by user
- WinRAR.exe (PID: 1872)
- VanDyke_SecureCRT_v6_2_1_keygen_by_Paradox.exe (PID: 2072)
Reads the date of Windows installation
- chrome.exe (PID: 2436)
Checks Windows Trust Settings
- keygen-step-6.exe (PID: 2776)
Reads Microsoft Office registry keys
- key.exe (PID: 2900)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
99
Monitored processes
48
Malicious processes
11
Suspicious processes
6
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 148 | "C:\Users\admin\AppData\Local\Temp\RarSFX1\pub1.exe" | C:\Users\admin\AppData\Local\Temp\RarSFX1\pub1.exe | keygen-step-4.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221225477 Modules
| |||||||||||||||
| 292 | "C:\Users\admin\AppData\Local\Temp\RarSFX2\key.exe" | C:\Users\admin\AppData\Local\Temp\RarSFX2\key.exe | keygen-pr.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 524 | C:\Windows\system32\cmd.exe /c ""C:\Users\admin\AppData\Local\Temp\RarSFX0\keygen.bat" " | C:\Windows\system32\cmd.exe | — | VanDyke_SecureCRT_v6_2_1_keygen_by_Paradox.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 636 | "C:\Users\admin\AppData\Roaming\34B7.tmp.exe" | C:\Users\admin\AppData\Roaming\34B7.tmp.exe | — | keygen-step-6.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 652 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=996,17487912810995670378,6278981821839091681,131072 --enable-features=PasswordImport --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=5 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=1736 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 684 | "C:\Users\admin\AppData\Roaming\2EDA.tmp.exe" | C:\Users\admin\AppData\Roaming\2EDA.tmp.exe | keygen-step-6.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 852 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --field-trial-handle=996,17487912810995670378,6278981821839091681,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --mojo-platform-channel-handle=1592 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 924 | C:\Windows\system32\svchost.exe -k netsvcs | C:\Windows\system32\svchost.exe | services.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1236 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=gpu-process --field-trial-handle=996,17487912810995670378,6278981821839091681,131072 --enable-features=PasswordImport --gpu-preferences=MAAAAAAAAADgACAwAAAAAAAAAAAAAAAAAABgAAAAAAAQAAAAAAAAAAAAAAAAAAAAKAAAAAQAAAAgAAAAAAAAACgAAAAAAAAAMAAAAAAAAAA4AAAAAAAAABAAAAAAAAAAAAAAAAUAAAAQAAAAAAAAAAAAAAAGAAAAEAAAAAAAAAABAAAABQAAABAAAAAAAAAAAQAAAAYAAAA= --use-gl=swiftshader-webgl --mojo-platform-channel-handle=1088 /prefetch:2 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 1372 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\Downloads\VanDyke_SecureCRT_v6_2_1_keygen_by_Paradox.zip" | C:\Program Files\WinRAR\WinRAR.exe | — | chrome.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
Total events
45 370
Read events
44 924
Write events
437
Delete events
9
Modification events
| (PID) Process: | (1536) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (1536) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
| (PID) Process: | (1536) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\ThirdParty |
| Operation: | write | Name: | StatusCodes |
Value: | |||
| (PID) Process: | (1536) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\ThirdParty |
| Operation: | write | Name: | StatusCodes |
Value: 01000000 | |||
| (PID) Process: | (1536) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 1 | |||
| (PID) Process: | (1536) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Update\ClientState\{8A69D345-D564-463c-AFF1-A69D9E530F96} |
| Operation: | write | Name: | dr |
Value: 1 | |||
| (PID) Process: | (1536) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome |
| Operation: | write | Name: | UsageStatsInSample |
Value: 0 | |||
| (PID) Process: | (1536) chrome.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Google\Update\ClientStateMedium\{8A69D345-D564-463C-AFF1-A69D9E530F96} |
| Operation: | write | Name: | usagestats |
Value: 0 | |||
| (PID) Process: | (1536) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Update\ClientState\{8A69D345-D564-463c-AFF1-A69D9E530F96} |
| Operation: | write | Name: | metricsid |
Value: | |||
| (PID) Process: | (1536) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Update\ClientState\{8A69D345-D564-463c-AFF1-A69D9E530F96} |
| Operation: | write | Name: | metricsid_installdate |
Value: 0 | |||
Executable files
20
Suspicious files
48
Text files
129
Unknown types
18
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1536 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\BrowserMetrics\BrowserMetrics-61F277F5-600.pma | — | |
MD5:— | SHA256:— | |||
| 1536 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Last Version | text | |
MD5:00046F773EFDD3C8F8F6D0F87A2B93DC | SHA256:593EDE11D17AF7F016828068BCA2E93CF240417563FB06DC8A579110AEF81731 | |||
| 1888 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\CrashpadMetrics.pma | binary | |
MD5:03C4F648043A88675A920425D824E1B3 | SHA256:F91DBB7C64B4582F529C968C480D2DCE1C8727390482F31E4355A27BB3D9B450 | |||
| 1536 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Site Characteristics Database\LOG.old~RF13e785.TMP | text | |
MD5:936EB7280DA791E6DD28EF3A9B46D39C | SHA256:CBAF2AFD831B32F6D1C12337EE5D2F090D6AE1F4DCB40B08BEF49BF52AD9721F | |||
| 1536 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Sync Data\LevelDB\LOG.old | text | |
MD5:5BD3C311F2136A7A88D3E197E55CF902 | SHA256:FA331915E1797E59979A3E4BCC2BD0D3DEAA039B94D4DB992BE251FD02A224B9 | |||
| 1536 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Site Characteristics Database\LOG.old | text | |
MD5:8FF312A95D60ED89857FEB720D80D4E1 | SHA256:946A57FAFDD28C3164D5AB8AB4971B21BD5EC5BFFF7554DBF832CB58CC37700B | |||
| 1536 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Crashpad\settings.dat | binary | |
MD5:9C016064A1F864C8140915D77CF3389A | SHA256:0E7265D4A8C16223538EDD8CD620B8820611C74538E420A88E333BE7F62AC787 | |||
| 1536 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Local Storage\leveldb\LOG.old~RF13e794.TMP | text | |
MD5:81F483F77EE490F35306A4F94DB2286B | SHA256:82434CE3C9D13F509EBEEBE3A7A1A1DE9AB4557629D9FC855761E0CFA45E8BCE | |||
| 1536 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Local Storage\leveldb\LOG.old | text | |
MD5:7721CDA9F5B73CE8A135471EB53B4E0E | SHA256:DD730C576766A46FFC84E682123248ECE1FF1887EC0ACAB22A5CE93A450F4500 | |||
| 1536 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Sync Data\LevelDB\LOG.old~RF13e775.TMP | text | |
MD5:64AD8ED3E666540337BA541C549F72F7 | SHA256:BECBDB08B5B37D203A85F2E974407334053BB1D2270F0B3C9A4DB963896F2206 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
66
TCP/UDP connections
61
DNS requests
44
Threats
32
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
924 | svchost.exe | HEAD | 200 | 74.125.104.199:80 | http://r2---sn-ixh7rn76.gvt1.com/edgedl/release2/chrome_component/adys6mm2sd23z36ns7e4hcs4hrqq_1.3.36.111/ihnlcenocehgdaegdmhbidjhnhdchfmm_1.3.36.111_win_ac5lwr5427en7czu7myxmee6c7xq.crx3?cms_redirect=yes&mh=8t&mip=196.244.192.6&mm=28&mn=sn-ixh7rn76&ms=nvh&mt=1643280028&mv=m&mvi=2&pl=24&rmhost=r3---sn-ixh7rn76.gvt1.com&shardbypass=yes | US | — | — | whitelisted |
292 | key.exe | POST | — | 185.177.93.149:80 | http://www.oldhorse.info/ | MD | — | — | malicious |
292 | key.exe | POST | — | 185.177.93.149:80 | http://www.oldhorse.info/ | MD | — | — | malicious |
924 | svchost.exe | GET | 302 | 142.250.186.110:80 | http://redirector.gvt1.com/edgedl/release2/chrome_component/adys6mm2sd23z36ns7e4hcs4hrqq_1.3.36.111/ihnlcenocehgdaegdmhbidjhnhdchfmm_1.3.36.111_win_ac5lwr5427en7czu7myxmee6c7xq.crx3 | US | html | 577 b | whitelisted |
924 | svchost.exe | GET | 302 | 142.250.186.110:80 | http://redirector.gvt1.com/edgedl/release2/chrome_component/adys6mm2sd23z36ns7e4hcs4hrqq_1.3.36.111/ihnlcenocehgdaegdmhbidjhnhdchfmm_1.3.36.111_win_ac5lwr5427en7czu7myxmee6c7xq.crx3 | US | html | 577 b | whitelisted |
924 | svchost.exe | GET | 206 | 74.125.104.199:80 | http://r2---sn-ixh7rn76.gvt1.com/edgedl/release2/chrome_component/adys6mm2sd23z36ns7e4hcs4hrqq_1.3.36.111/ihnlcenocehgdaegdmhbidjhnhdchfmm_1.3.36.111_win_ac5lwr5427en7czu7myxmee6c7xq.crx3?cms_redirect=yes&mh=8t&mip=196.244.192.6&mm=28&mn=sn-ixh7rn76&ms=nvh&mt=1643280028&mv=m&mvi=2&pl=24&rmhost=r3---sn-ixh7rn76.gvt1.com&shardbypass=yes | US | binary | 9.49 Kb | whitelisted |
924 | svchost.exe | GET | 302 | 142.250.186.110:80 | http://redirector.gvt1.com/edgedl/release2/chrome_component/adys6mm2sd23z36ns7e4hcs4hrqq_1.3.36.111/ihnlcenocehgdaegdmhbidjhnhdchfmm_1.3.36.111_win_ac5lwr5427en7czu7myxmee6c7xq.crx3 | US | html | 577 b | whitelisted |
292 | key.exe | POST | 200 | 185.177.93.149:80 | http://oldhorse.info/a.php | MD | — | — | malicious |
924 | svchost.exe | GET | 302 | 142.250.186.110:80 | http://redirector.gvt1.com/edgedl/release2/chrome_component/adys6mm2sd23z36ns7e4hcs4hrqq_1.3.36.111/ihnlcenocehgdaegdmhbidjhnhdchfmm_1.3.36.111_win_ac5lwr5427en7czu7myxmee6c7xq.crx3 | US | html | 577 b | whitelisted |
924 | svchost.exe | GET | 206 | 74.125.104.231:80 | http://r2---sn-ixh7yn7e.gvt1.com/edgedl/release2/chrome_component/adys6mm2sd23z36ns7e4hcs4hrqq_1.3.36.111/ihnlcenocehgdaegdmhbidjhnhdchfmm_1.3.36.111_win_ac5lwr5427en7czu7myxmee6c7xq.crx3?cms_redirect=yes&mh=8t&mip=196.244.192.6&mm=28&mn=sn-ixh7yn7e&ms=nvh&mt=1643280268&mv=m&mvi=2&pl=24&rmhost=r3---sn-ixh7yn7e.gvt1.com&shardbypass=yes | US | binary | 5.63 Kb | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3972 | chrome.exe | 104.16.19.94:443 | cdnjs.cloudflare.com | Cloudflare Inc | US | suspicious |
3972 | chrome.exe | 142.250.186.174:443 | clients2.google.com | Google Inc. | US | whitelisted |
3972 | chrome.exe | 172.67.197.202:443 | cracksgurus.com | — | US | unknown |
— | — | 142.250.186.35:443 | www.google.se | Google Inc. | US | whitelisted |
3972 | chrome.exe | 142.250.184.200:443 | www.googletagmanager.com | Google Inc. | US | suspicious |
3972 | chrome.exe | 142.250.186.68:443 | www.google.com | Google Inc. | US | whitelisted |
3972 | chrome.exe | 142.250.186.35:443 | www.google.se | Google Inc. | US | whitelisted |
3972 | chrome.exe | 142.250.74.195:443 | ssl.gstatic.com | Google Inc. | US | whitelisted |
3972 | chrome.exe | 35.190.80.1:443 | a.nel.cloudflare.com | Google Inc. | US | suspicious |
3972 | chrome.exe | 8.248.143.254:80 | ctldl.windowsupdate.com | Level 3 Communications, Inc. | US | malicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
clients2.google.com |
| whitelisted |
cracksgurus.com |
| malicious |
accounts.google.com |
| shared |
cdnjs.cloudflare.com |
| whitelisted |
www.googletagmanager.com |
| whitelisted |
static.cloudflareinsights.com |
| whitelisted |
www.google-analytics.com |
| whitelisted |
stats.g.doubleclick.net |
| whitelisted |
www.google.com |
| malicious |
www.google.se |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2212 | keygen-step-1.exe | A Network Trojan was detected | ET TROJAN Win32/AZORult V3.3 Client Checkin M2 |
2212 | keygen-step-1.exe | A Network Trojan was detected | AV TROJAN Azorult CnC Beacon |
2096 | KiffAppE2.exe | Potentially Bad Traffic | ET INFO Observed Let's Encrypt Certificate for Suspicious TLD (.xyz) |
— | — | Potentially Bad Traffic | ET INFO Observed DNS Query to .biz TLD |
3324 | lows.exe | A Network Trojan was detected | ET TROJAN GCleaner Downloader Activity M5 |
292 | key.exe | A Network Trojan was detected | ET TROJAN Fareit/Pony Downloader Checkin 2 |
292 | key.exe | Generic Protocol Command Decode | SURICATA HTTP invalid response chunk len |
292 | key.exe | A Network Trojan was detected | ET TROJAN Fareit/Pony Downloader Checkin 2 |
292 | key.exe | Generic Protocol Command Decode | SURICATA HTTP invalid response chunk len |
292 | key.exe | A Network Trojan was detected | ET TROJAN Fareit/Pony Downloader Checkin 2 |
9 ETPRO signatures available at the full report