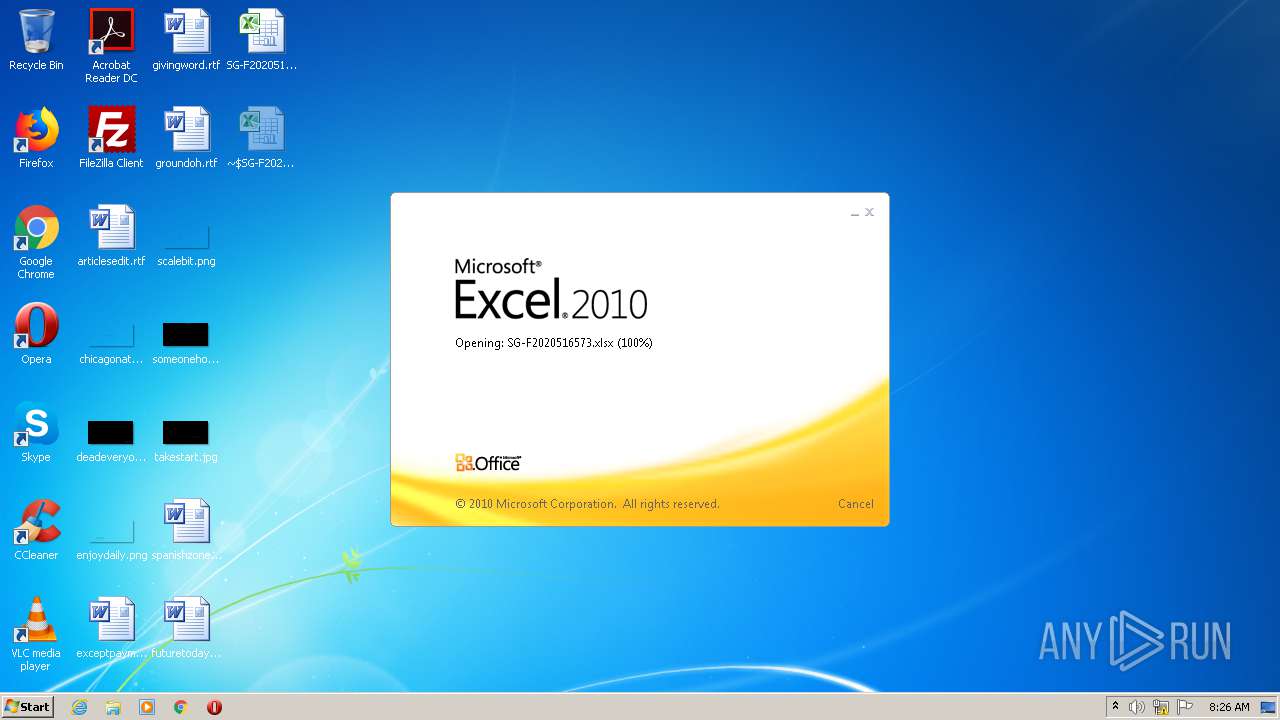
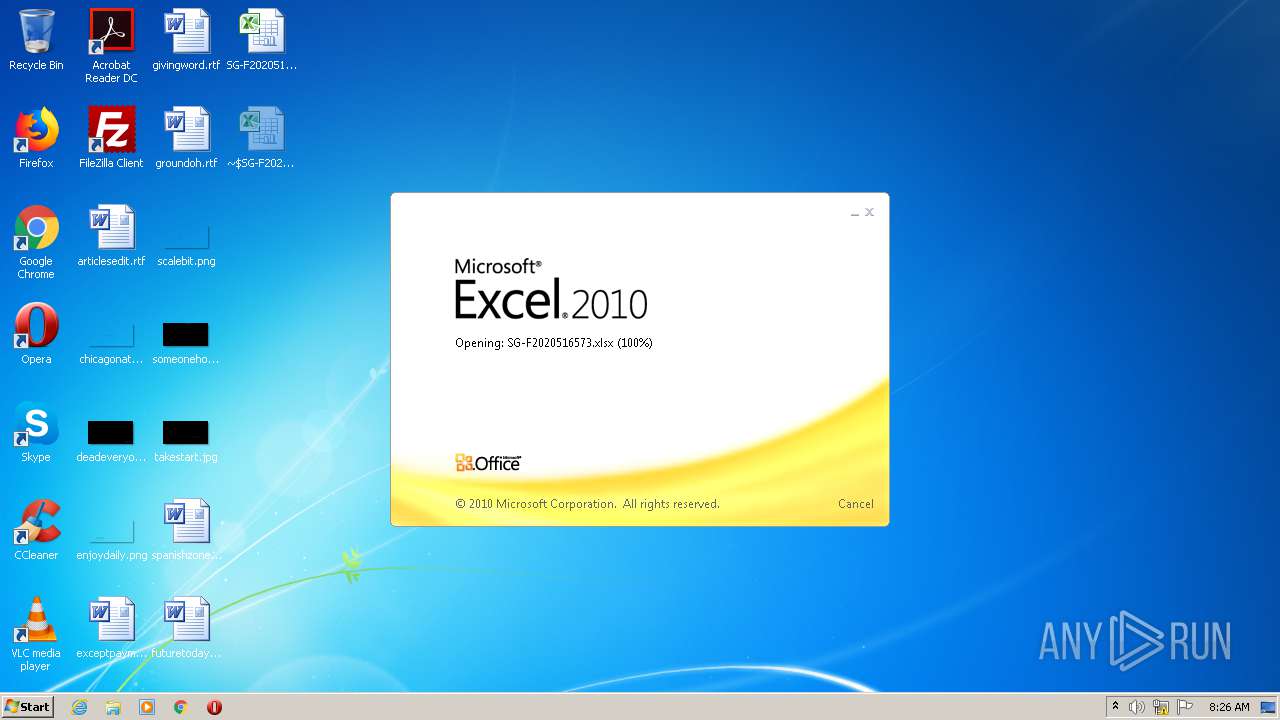
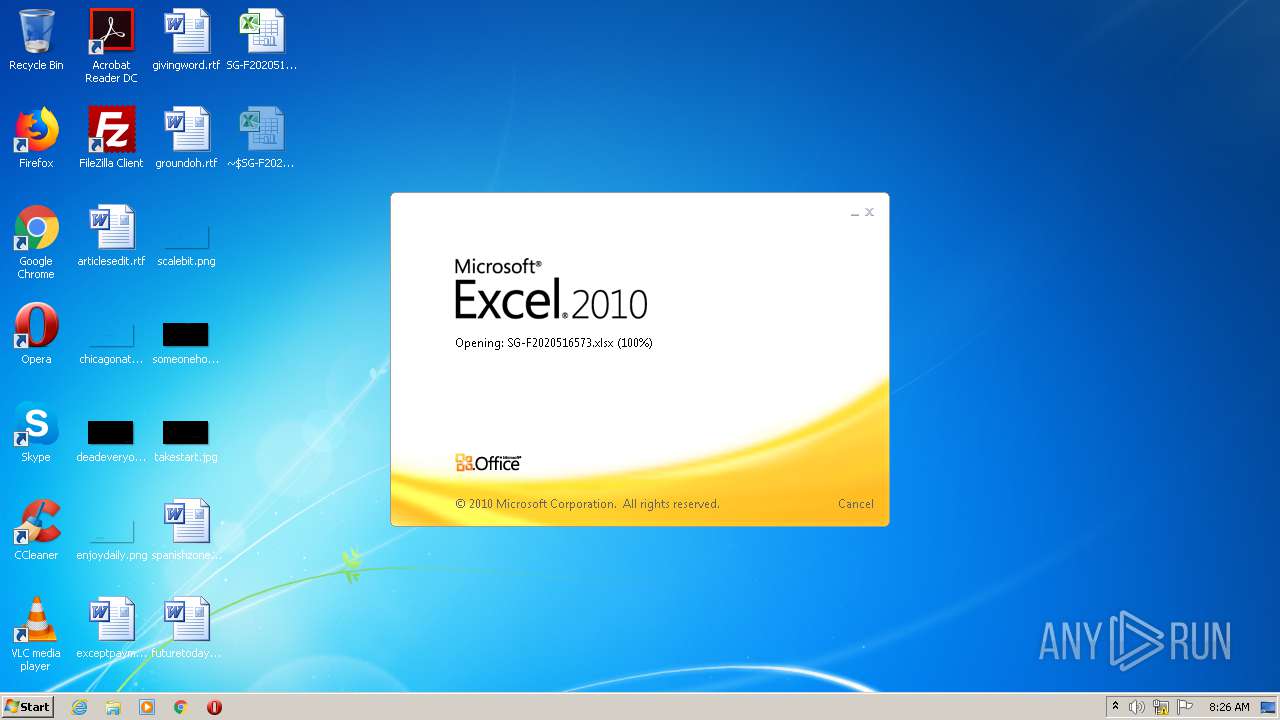
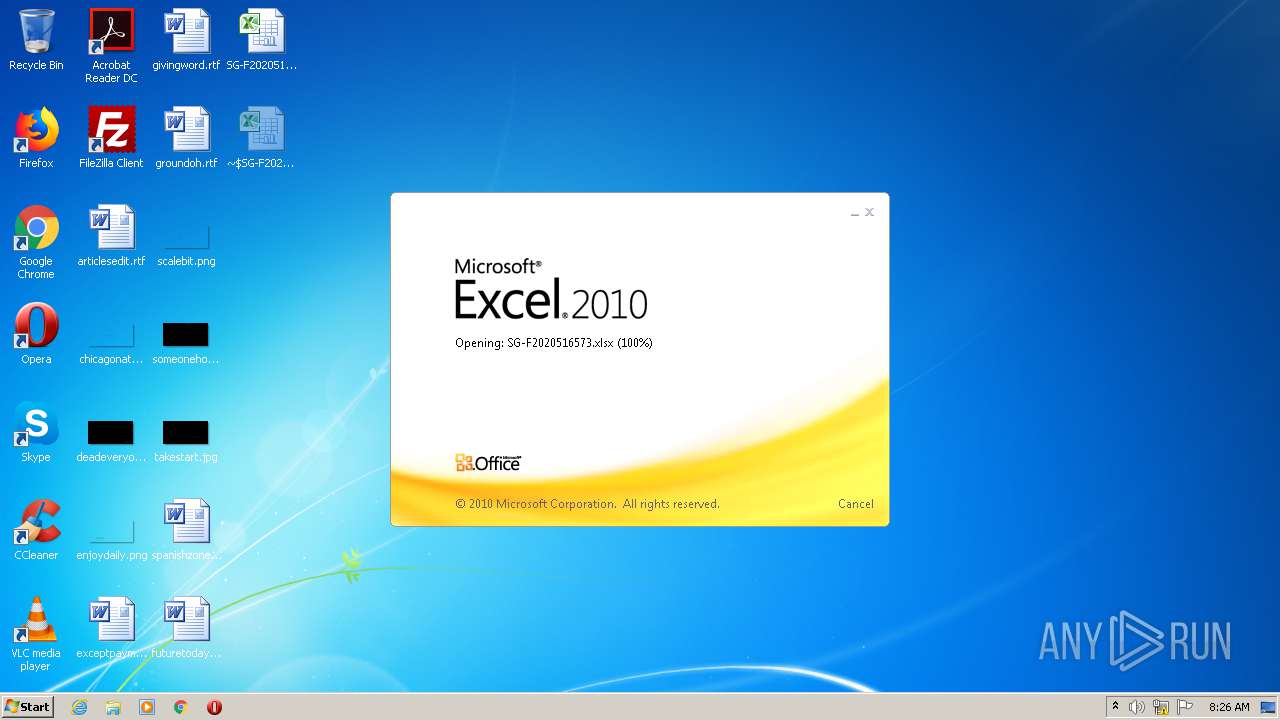
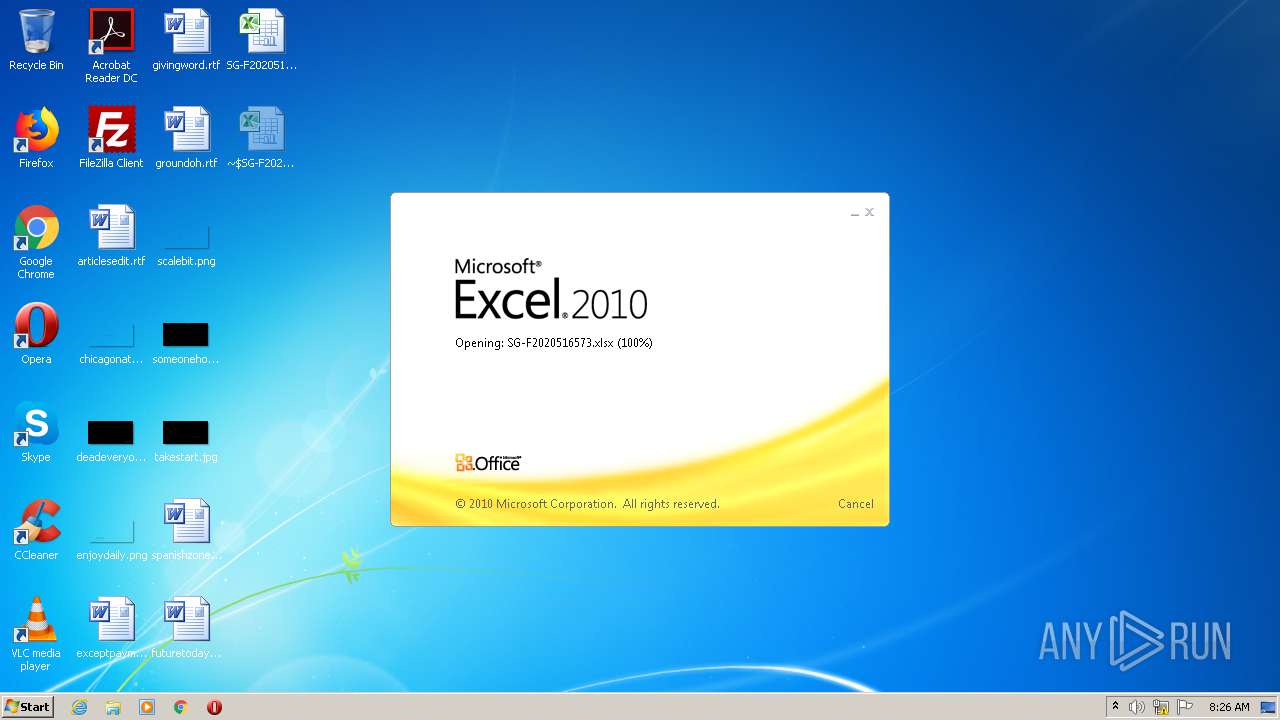
| File name: | SG-F2020516573.xlsx |
| Full analysis: | https://app.any.run/tasks/184fd03a-ce4b-463b-baba-6788cb523975 |
| Verdict: | Malicious activity |
| Threats: | Agent Tesla is spyware that collects information about the actions of its victims by recording keystrokes and user interactions. It is falsely marketed as a legitimate software on the dedicated website where this malware is sold. |
| Analysis date: | October 20, 2020, 07:25:09 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/encrypted |
| File info: | CDFV2 Encrypted |
| MD5: | 905322C9293EC9BC1F2157957FA01687 |
| SHA1: | A75561BBF407CD1407C4FFDDB60995DB5E0F217A |
| SHA256: | 2A670C20AEA3EA3E3A5E9B2B1349EE44170ADAA6B69F85CE7333E7797D725B61 |
| SSDEEP: | 3072:EXk47DQyjtbQtkyiZLFRZR5UBlbgOQiWHGJsy+OUACCUduYBbDB:EXz7RbQyHzwBlRQiWmyxAKduYtB |
MALICIOUS
Application was dropped or rewritten from another process
- vbc.exe (PID: 1880)
- vbc.exe (PID: 3912)
Equation Editor starts application (CVE-2017-11882)
- EQNEDT32.EXE (PID: 3204)
Changes the autorun value in the registry
- vbc.exe (PID: 1880)
AGENTTESLA was detected
- vbc.exe (PID: 3912)
Actions looks like stealing of personal data
- vbc.exe (PID: 3912)
SUSPICIOUS
Executed via COM
- EQNEDT32.EXE (PID: 3204)
- WINWORD.EXE (PID: 3228)
Executable content was dropped or overwritten
- EQNEDT32.EXE (PID: 3204)
- vbc.exe (PID: 1880)
Reads Internet Cache Settings
- EQNEDT32.EXE (PID: 3204)
Application launched itself
- vbc.exe (PID: 1880)
Creates files in the user directory
- vbc.exe (PID: 1880)
- vbc.exe (PID: 3912)
Reads the cookies of Google Chrome
- vbc.exe (PID: 3912)
Reads the cookies of Mozilla Firefox
- vbc.exe (PID: 3912)
INFO
Reads Microsoft Office registry keys
- EXCEL.EXE (PID: 2488)
- WINWORD.EXE (PID: 3228)
Reads Internet Cache Settings
- EXCEL.EXE (PID: 2488)
- WINWORD.EXE (PID: 3228)
Creates files in the user directory
- WINWORD.EXE (PID: 3228)
- EXCEL.EXE (PID: 2488)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
44
Monitored processes
5
Malicious processes
3
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1880 | "C:\Users\Public\vbc.exe" | C:\Users\Public\vbc.exe | EQNEDT32.EXE | ||||||||||||
User: admin Integrity Level: MEDIUM Description: Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
| 2488 | "C:\Program Files\Microsoft Office\Office14\EXCEL.EXE" /dde | C:\Program Files\Microsoft Office\Office14\EXCEL.EXE | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Excel Exit code: 0 Version: 14.0.6024.1000 Modules
| |||||||||||||||
| 3204 | "C:\Program Files\Common Files\Microsoft Shared\EQUATION\EQNEDT32.EXE" -Embedding | C:\Program Files\Common Files\Microsoft Shared\EQUATION\EQNEDT32.EXE | svchost.exe | ||||||||||||
User: admin Company: Design Science, Inc. Integrity Level: MEDIUM Description: Microsoft Equation Editor Exit code: 0 Version: 00110900 Modules
| |||||||||||||||
| 3228 | "C:\Program Files\Microsoft Office\Office14\WINWORD.EXE" -Embedding | C:\Program Files\Microsoft Office\Office14\WINWORD.EXE | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Word Exit code: 0 Version: 14.0.6024.1000 Modules
| |||||||||||||||
| 3912 | "C:\Users\Public\vbc.exe" | C:\Users\Public\vbc.exe | vbc.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Description: Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
Total events
1 454
Read events
845
Write events
560
Delete events
49
Modification events
| (PID) Process: | (2488) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Excel\Resiliency\StartupItems |
| Operation: | write | Name: | sq6 |
Value: 73713600B8090000010000000000000000000000 | |||
| (PID) Process: | (2488) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: Off | |||
| (PID) Process: | (2488) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1041 |
Value: Off | |||
| (PID) Process: | (2488) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1046 |
Value: Off | |||
| (PID) Process: | (2488) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1036 |
Value: Off | |||
| (PID) Process: | (2488) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1031 |
Value: Off | |||
| (PID) Process: | (2488) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1040 |
Value: Off | |||
| (PID) Process: | (2488) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1049 |
Value: Off | |||
| (PID) Process: | (2488) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 3082 |
Value: Off | |||
| (PID) Process: | (2488) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1042 |
Value: Off | |||
Executable files
3
Suspicious files
28
Text files
11
Unknown types
5
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2488 | EXCEL.EXE | C:\Users\admin\AppData\Local\Temp\CVR4173.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 2488 | EXCEL.EXE | C:\Users\admin\AppData\Local\Temp\Cab59AF.tmp | — | |
MD5:— | SHA256:— | |||
| 2488 | EXCEL.EXE | C:\Users\admin\AppData\Local\Temp\Tar59B0.tmp | — | |
MD5:— | SHA256:— | |||
| 3228 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\CVR7871.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 3228 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\{53294F03-AD79-463A-8BAD-480A49B00D1A} | — | |
MD5:— | SHA256:— | |||
| 3228 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\{CDC9439B-4500-43C6-847A-2CA43DADE48C} | — | |
MD5:— | SHA256:— | |||
| 3204 | EQNEDT32.EXE | C:\Users\admin\AppData\Local\Temp\Cab9F4D.tmp | — | |
MD5:— | SHA256:— | |||
| 3204 | EQNEDT32.EXE | C:\Users\admin\AppData\Local\Temp\Tar9F4E.tmp | — | |
MD5:— | SHA256:— | |||
| 2488 | EXCEL.EXE | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\E49827401028F7A0F97B5576C77A26CB_7CE95D8DCA26FE957E7BD7D76F353B08 | der | |
MD5:— | SHA256:— | |||
| 2488 | EXCEL.EXE | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\E49827401028F7A0F97B5576C77A26CB_7CE95D8DCA26FE957E7BD7D76F353B08 | binary | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
4
TCP/UDP connections
14
DNS requests
10
Threats
10
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3204 | EQNEDT32.EXE | GET | 302 | 160.153.133.172:80 | http://itravel.co.tz/Img/VKO.exe | US | html | 217 b | suspicious |
2488 | EXCEL.EXE | GET | 200 | 2.16.186.27:80 | http://ocsp.int-x3.letsencrypt.org/MFMwUTBPME0wSzAJBgUrDgMCGgUABBR%2B5mrncpqz%2FPiiIGRsFqEtYHEIXQQUqEpqYwR93brm0Tm3pkVl7%2FOo7KECEgRdOGfpmJ2mlstt7PChgpkhyA%3D%3D | unknown | der | 527 b | whitelisted |
2488 | EXCEL.EXE | GET | 200 | 2.16.186.35:80 | http://isrg.trustid.ocsp.identrust.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBRv9GhNQxLSSGKBnMArPUcsHYovpgQUxKexpHsscfrb4UuQdf%2FEFWCFiRACEAoBQUIAAAFThXNqC4Xspwg%3D | unknown | der | 1.37 Kb | whitelisted |
1052 | svchost.exe | GET | 200 | 2.16.186.74:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | der | 1.11 Kb | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2488 | EXCEL.EXE | 76.223.86.4:443 | rb.gy | AT&T Services, Inc. | US | suspicious |
3228 | WINWORD.EXE | 76.223.86.4:443 | rb.gy | AT&T Services, Inc. | US | suspicious |
3204 | EQNEDT32.EXE | 160.153.133.172:80 | itravel.co.tz | GoDaddy.com, LLC | US | suspicious |
3204 | EQNEDT32.EXE | 160.153.133.172:443 | itravel.co.tz | GoDaddy.com, LLC | US | suspicious |
1052 | svchost.exe | 2.16.186.74:80 | crl.microsoft.com | Akamai International B.V. | — | whitelisted |
3912 | vbc.exe | 174.129.214.20:443 | api.ipify.org | Amazon.com, Inc. | US | suspicious |
3912 | vbc.exe | 162.241.85.194:587 | mail.hkoffice365.com | CyrusOne LLC | US | malicious |
844 | svchost.exe | 76.223.86.4:443 | rb.gy | AT&T Services, Inc. | US | suspicious |
2488 | EXCEL.EXE | 160.153.133.172:80 | itravel.co.tz | GoDaddy.com, LLC | US | suspicious |
2488 | EXCEL.EXE | 2.16.186.35:80 | isrg.trustid.ocsp.identrust.com | Akamai International B.V. | — | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
rb.gy |
| whitelisted |
isrg.trustid.ocsp.identrust.com |
| whitelisted |
ocsp.int-x3.letsencrypt.org |
| whitelisted |
itravel.co.tz |
| suspicious |
crl.microsoft.com |
| whitelisted |
api.ipify.org |
| shared |
mail.hkoffice365.com |
| malicious |
Threats
PID | Process | Class | Message |
|---|---|---|---|
3912 | vbc.exe | Misc activity | SUSPICIOUS [PTsecurity] ipify.org External IP Check |
3912 | vbc.exe | Misc activity | SUSPICIOUS [PTsecurity] ipify.org External IP Check |
3912 | vbc.exe | Generic Protocol Command Decode | SURICATA Applayer Detect protocol only one direction |
3912 | vbc.exe | A Network Trojan was detected | SPYWARE [PTsecurity] AgentTesla Exfiltration |
3912 | vbc.exe | Generic Protocol Command Decode | SURICATA Applayer Detect protocol only one direction |
3912 | vbc.exe | A Network Trojan was detected | SPYWARE [PTsecurity] AgentTesla Exfiltration |
3912 | vbc.exe | A Network Trojan was detected | ET TROJAN AgentTesla Exfil Via SMTP |
3912 | vbc.exe | A Network Trojan was detected | SPYWARE [PTsecurity] AgentTesla Exfiltration |
2 ETPRO signatures available at the full report