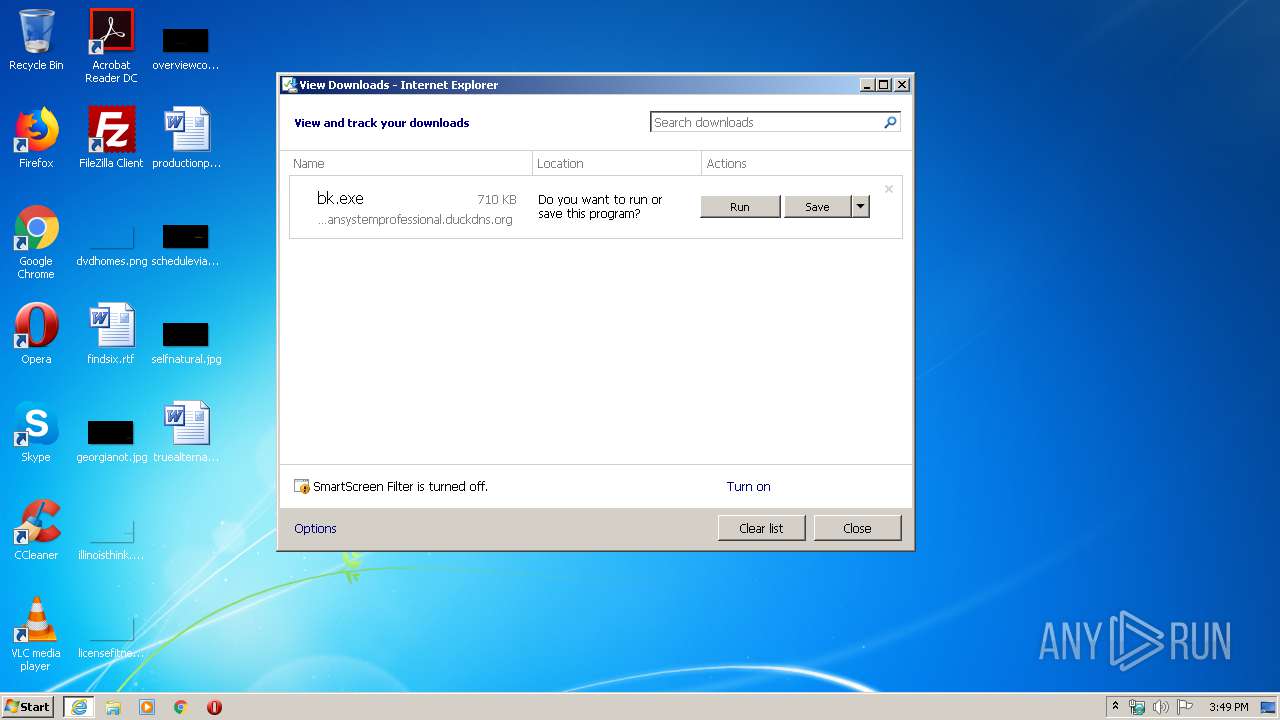
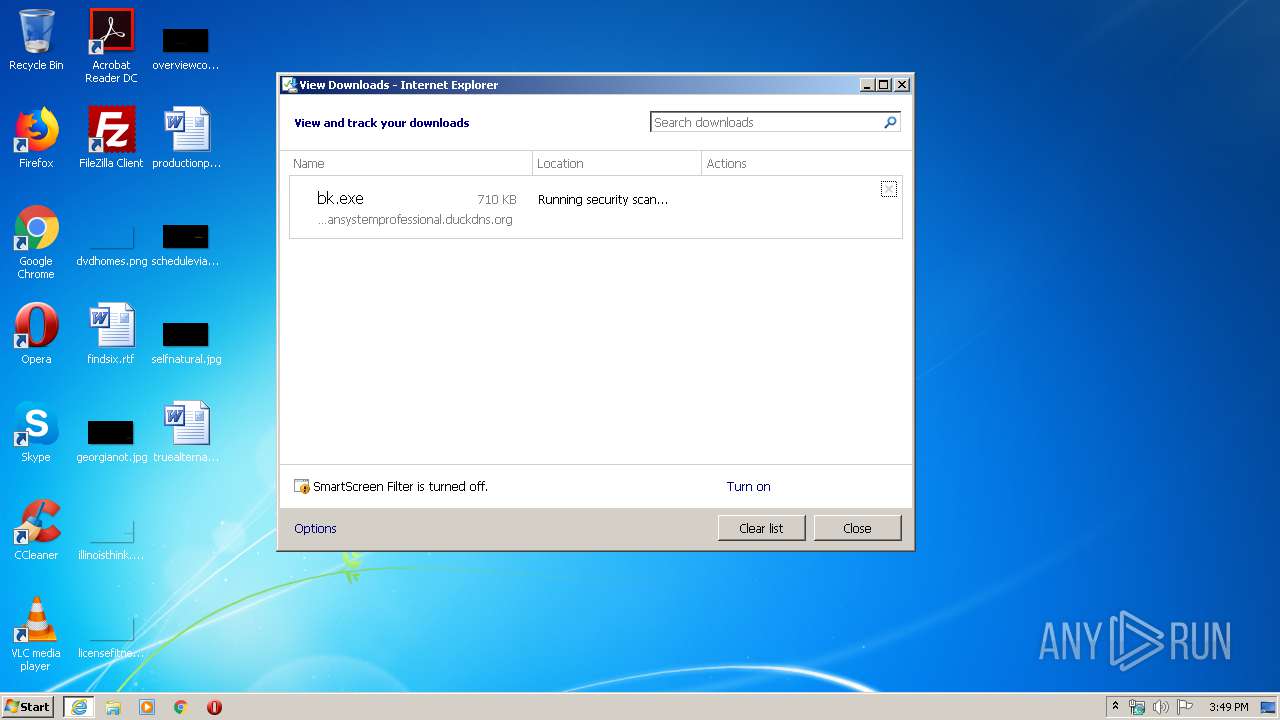
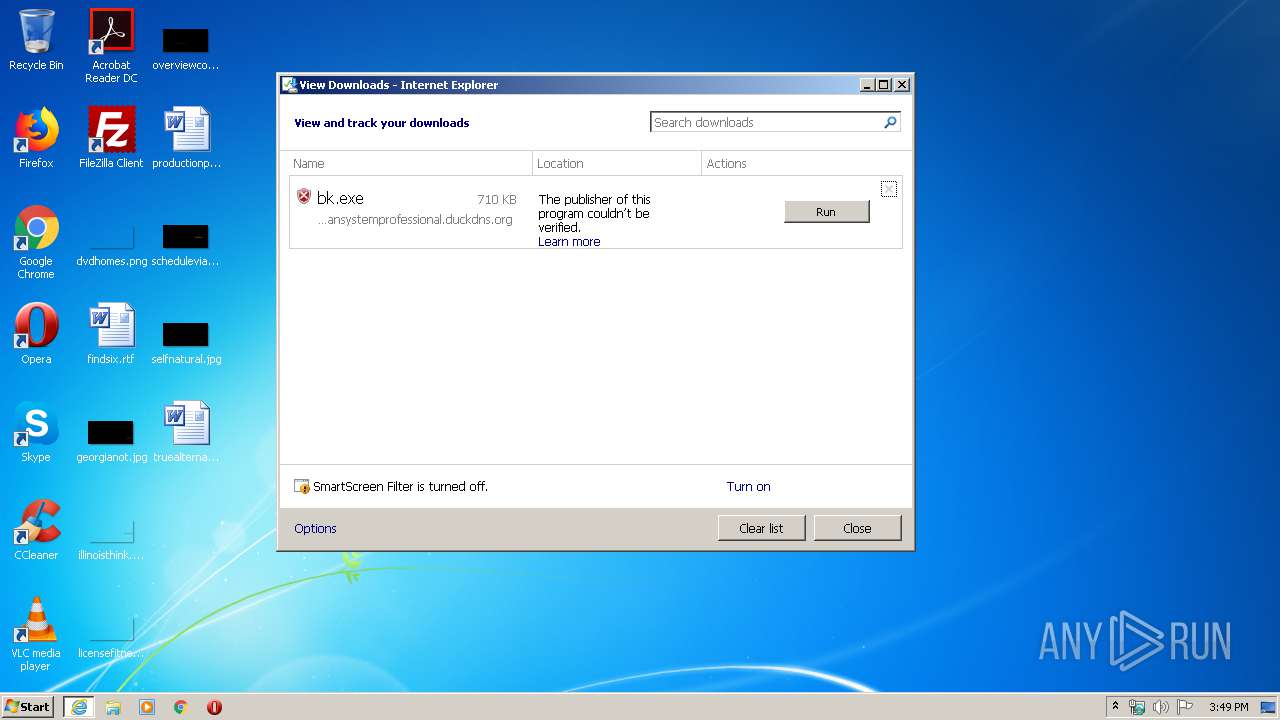
| URL: | http://easydatatransfercleansystemprofessional.duckdns.org/intel/bk.exe |
| Full analysis: | https://app.any.run/tasks/f41198a2-bffd-4ead-b227-ab745946d165 |
| Verdict: | Malicious activity |
| Threats: | FormBook is a data stealer that is being distributed as a MaaS. FormBook differs from a lot of competing malware by its extreme ease of use that allows even the unexperienced threat actors to use FormBook virus. |
| Analysis date: | March 30, 2020, 14:49:05 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MD5: | 9389857FDE772CB2066661BF5A663AC0 |
| SHA1: | 0EB27224D77AAC739D5E69F2C298483AC4A1B165 |
| SHA256: | 2A665FFD4DE021B5465CB6362C2F4BFCCD67269D6ABD77C232D7D012D3326350 |
| SSDEEP: | 3:N1KbUBKEViXqQgaGEWiKru0C:CUKDdgaGEWdC0C |
MALICIOUS
Downloads executable files from the Internet
- iexplore.exe (PID: 3112)
Writes to a start menu file
- chlz.exe (PID: 3252)
- chlz.exe (PID: 1232)
- chlz.exe (PID: 2544)
- chlz.exe (PID: 3624)
- chlz.exe (PID: 3740)
- chlz.exe (PID: 2664)
- chlz.exe (PID: 1440)
- chlz.exe (PID: 3992)
- chlz.exe (PID: 3796)
- chlz.exe (PID: 2132)
- chlz.exe (PID: 3852)
- chlz.exe (PID: 2728)
- chlz.exe (PID: 2704)
- chlz.exe (PID: 3168)
- chlz.exe (PID: 608)
- chlz.exe (PID: 376)
- chlz.exe (PID: 3884)
- chlz.exe (PID: 2600)
- chlz.exe (PID: 2516)
- chlz.exe (PID: 2424)
- chlz.exe (PID: 2528)
- chlz.exe (PID: 2520)
- chlz.exe (PID: 3492)
- chlz.exe (PID: 1352)
- chlz.exe (PID: 3008)
- chlz.exe (PID: 3508)
- chlz.exe (PID: 780)
- chlz.exe (PID: 3348)
- chlz.exe (PID: 740)
- chlz.exe (PID: 2948)
- chlz.exe (PID: 3104)
- chlz.exe (PID: 1488)
- chlz.exe (PID: 580)
- chlz.exe (PID: 4004)
- chlz.exe (PID: 2948)
- chlz.exe (PID: 3352)
- chlz.exe (PID: 2456)
- chlz.exe (PID: 3736)
- chlz.exe (PID: 580)
- chlz.exe (PID: 1860)
- chlz.exe (PID: 2128)
- chlz.exe (PID: 1876)
- chlz.exe (PID: 2920)
- chlz.exe (PID: 2120)
- chlz.exe (PID: 3664)
- chlz.exe (PID: 3948)
- chlz.exe (PID: 2748)
- chlz.exe (PID: 2484)
- chlz.exe (PID: 1248)
- chlz.exe (PID: 3388)
- chlz.exe (PID: 3732)
- chlz.exe (PID: 3356)
- chlz.exe (PID: 3388)
- chlz.exe (PID: 1156)
- chlz.exe (PID: 2960)
- chlz.exe (PID: 1196)
- chlz.exe (PID: 3504)
- chlz.exe (PID: 1136)
- chlz.exe (PID: 4004)
- chlz.exe (PID: 3888)
- chlz.exe (PID: 2600)
- chlz.exe (PID: 3580)
- chlz.exe (PID: 3072)
- chlz.exe (PID: 2356)
- chlz.exe (PID: 2984)
- chlz.exe (PID: 3580)
- chlz.exe (PID: 2648)
- chlz.exe (PID: 680)
- chlz.exe (PID: 2528)
- chlz.exe (PID: 3128)
- chlz.exe (PID: 2412)
Application was dropped or rewritten from another process
- chlz.exe (PID: 1780)
- bk.exe (PID: 2152)
- chlz.exe (PID: 3252)
- chlz.exe (PID: 2312)
- chlz.exe (PID: 1836)
- chlz.exe (PID: 312)
- chlz.exe (PID: 1232)
- chlz.exe (PID: 2544)
- chlz.exe (PID: 952)
- chlz.exe (PID: 940)
- chlz.exe (PID: 3624)
- chlz.exe (PID: 3460)
- chlz.exe (PID: 3740)
- chlz.exe (PID: 3692)
- chlz.exe (PID: 3540)
- chlz.exe (PID: 1440)
- chlz.exe (PID: 2496)
- chlz.exe (PID: 2684)
- chlz.exe (PID: 3216)
- chlz.exe (PID: 2664)
- chlz.exe (PID: 2904)
- chlz.exe (PID: 3992)
- chlz.exe (PID: 2596)
- chlz.exe (PID: 1332)
- chlz.exe (PID: 3796)
- chlz.exe (PID: 4064)
- chlz.exe (PID: 3108)
- chlz.exe (PID: 2132)
- chlz.exe (PID: 3824)
- chlz.exe (PID: 3408)
- chlz.exe (PID: 2452)
- chlz.exe (PID: 2728)
- chlz.exe (PID: 3852)
- chlz.exe (PID: 3300)
- chlz.exe (PID: 3320)
- chlz.exe (PID: 2988)
- chlz.exe (PID: 3168)
- chlz.exe (PID: 3528)
- chlz.exe (PID: 2220)
- chlz.exe (PID: 2704)
- chlz.exe (PID: 2628)
- chlz.exe (PID: 2768)
- chlz.exe (PID: 3516)
- chlz.exe (PID: 608)
- chlz.exe (PID: 2704)
- chlz.exe (PID: 3832)
- chlz.exe (PID: 376)
- chlz.exe (PID: 1840)
- chlz.exe (PID: 4032)
- chlz.exe (PID: 3884)
- chlz.exe (PID: 2992)
- chlz.exe (PID: 1492)
- chlz.exe (PID: 2600)
- chlz.exe (PID: 1632)
- chlz.exe (PID: 3892)
- chlz.exe (PID: 2516)
- chlz.exe (PID: 3180)
- chlz.exe (PID: 2856)
- chlz.exe (PID: 376)
- chlz.exe (PID: 2424)
- chlz.exe (PID: 2936)
- chlz.exe (PID: 3400)
- chlz.exe (PID: 2528)
- chlz.exe (PID: 3328)
- chlz.exe (PID: 2520)
- chlz.exe (PID: 3440)
- chlz.exe (PID: 3492)
- chlz.exe (PID: 3816)
- chlz.exe (PID: 3576)
- chlz.exe (PID: 332)
- chlz.exe (PID: 1352)
- chlz.exe (PID: 3004)
- chlz.exe (PID: 4092)
- chlz.exe (PID: 3860)
- chlz.exe (PID: 3008)
- chlz.exe (PID: 3640)
- chlz.exe (PID: 3508)
- chlz.exe (PID: 3760)
- chlz.exe (PID: 1948)
- chlz.exe (PID: 780)
- chlz.exe (PID: 2764)
- chlz.exe (PID: 4088)
- chlz.exe (PID: 3348)
- chlz.exe (PID: 548)
- chlz.exe (PID: 2624)
- chlz.exe (PID: 740)
- chlz.exe (PID: 3168)
- chlz.exe (PID: 280)
- chlz.exe (PID: 2948)
- chlz.exe (PID: 4076)
- chlz.exe (PID: 3592)
- chlz.exe (PID: 1488)
- chlz.exe (PID: 580)
- chlz.exe (PID: 3104)
- chlz.exe (PID: 2548)
- chlz.exe (PID: 3192)
- chlz.exe (PID: 880)
- chlz.exe (PID: 1784)
- chlz.exe (PID: 3608)
- chlz.exe (PID: 3120)
- chlz.exe (PID: 4052)
- chlz.exe (PID: 4004)
- chlz.exe (PID: 3376)
- chlz.exe (PID: 2948)
- chlz.exe (PID: 1380)
- chlz.exe (PID: 3964)
- chlz.exe (PID: 2672)
- chlz.exe (PID: 3352)
- chlz.exe (PID: 3064)
- chlz.exe (PID: 2456)
- chlz.exe (PID: 392)
- chlz.exe (PID: 2388)
- chlz.exe (PID: 2448)
- chlz.exe (PID: 3736)
- chlz.exe (PID: 3568)
- chlz.exe (PID: 580)
- chlz.exe (PID: 3864)
- chlz.exe (PID: 2824)
- chlz.exe (PID: 1860)
- chlz.exe (PID: 608)
- chlz.exe (PID: 3224)
- chlz.exe (PID: 2128)
- chlz.exe (PID: 3496)
- chlz.exe (PID: 3048)
- chlz.exe (PID: 1876)
- chlz.exe (PID: 3552)
- chlz.exe (PID: 2436)
- chlz.exe (PID: 2920)
- chlz.exe (PID: 3468)
- chlz.exe (PID: 2120)
- chlz.exe (PID: 3028)
- chlz.exe (PID: 3080)
- chlz.exe (PID: 2752)
- chlz.exe (PID: 3664)
- chlz.exe (PID: 2676)
- chlz.exe (PID: 2192)
- chlz.exe (PID: 3948)
- chlz.exe (PID: 3040)
- chlz.exe (PID: 2712)
- chlz.exe (PID: 316)
- chlz.exe (PID: 2144)
- chlz.exe (PID: 2748)
- chlz.exe (PID: 2484)
- chlz.exe (PID: 3712)
- chlz.exe (PID: 3732)
- chlz.exe (PID: 1696)
- chlz.exe (PID: 2868)
- chlz.exe (PID: 1008)
- chlz.exe (PID: 1248)
- chlz.exe (PID: 2908)
- chlz.exe (PID: 3624)
- chlz.exe (PID: 1156)
- chlz.exe (PID: 3664)
- chlz.exe (PID: 3236)
- chlz.exe (PID: 3388)
- chlz.exe (PID: 3768)
- chlz.exe (PID: 3356)
- chlz.exe (PID: 1516)
- chlz.exe (PID: 3388)
- chlz.exe (PID: 1708)
- chlz.exe (PID: 2076)
- chlz.exe (PID: 3276)
- chlz.exe (PID: 1400)
- chlz.exe (PID: 1392)
- chlz.exe (PID: 1196)
- chlz.exe (PID: 3096)
- chlz.exe (PID: 3244)
- chlz.exe (PID: 2960)
- chlz.exe (PID: 3380)
- chlz.exe (PID: 3504)
- chlz.exe (PID: 1136)
- chlz.exe (PID: 3688)
- chlz.exe (PID: 2428)
- chlz.exe (PID: 3084)
- chlz.exe (PID: 2068)
- chlz.exe (PID: 4004)
- chlz.exe (PID: 3604)
- chlz.exe (PID: 664)
- chlz.exe (PID: 2140)
- chlz.exe (PID: 3888)
- chlz.exe (PID: 944)
- chlz.exe (PID: 2600)
- chlz.exe (PID: 4012)
- chlz.exe (PID: 1872)
- chlz.exe (PID: 2588)
- chlz.exe (PID: 3600)
- chlz.exe (PID: 3072)
- chlz.exe (PID: 2472)
- chlz.exe (PID: 2372)
- chlz.exe (PID: 3580)
- chlz.exe (PID: 3884)
- chlz.exe (PID: 3580)
- chlz.exe (PID: 1744)
- chlz.exe (PID: 2356)
- chlz.exe (PID: 1268)
- chlz.exe (PID: 1064)
- chlz.exe (PID: 3476)
- chlz.exe (PID: 2984)
- chlz.exe (PID: 2888)
- chlz.exe (PID: 2716)
- chlz.exe (PID: 2648)
- chlz.exe (PID: 3264)
- chlz.exe (PID: 3384)
- chlz.exe (PID: 3700)
- chlz.exe (PID: 680)
- chlz.exe (PID: 4036)
- chlz.exe (PID: 3128)
- chlz.exe (PID: 1692)
- chlz.exe (PID: 3448)
- chlz.exe (PID: 2528)
- chlz.exe (PID: 3292)
- chlz.exe (PID: 3484)
- chlz.exe (PID: 1500)
- chlz.exe (PID: 2412)
Changes the autorun value in the registry
- lsm.exe (PID: 2524)
FORMBOOK was detected
- lsm.exe (PID: 2524)
- Firefox.exe (PID: 2828)
- explorer.exe (PID: 372)
Actions looks like stealing of personal data
- lsm.exe (PID: 2524)
Stealing of credential data
- lsm.exe (PID: 2524)
Runs app for hidden code execution
- explorer.exe (PID: 372)
Connects to CnC server
- explorer.exe (PID: 372)
Uses SVCHOST.EXE for hidden code execution
- explorer.exe (PID: 372)
SUSPICIOUS
Starts Internet Explorer
- explorer.exe (PID: 372)
Starts itself from another location
- bk.exe (PID: 2152)
Executable content was dropped or overwritten
- iexplore.exe (PID: 3972)
- iexplore.exe (PID: 3112)
- bk.exe (PID: 2152)
Creates files in the user directory
- bk.exe (PID: 2152)
- chlz.exe (PID: 3252)
- chlz.exe (PID: 1232)
- lsm.exe (PID: 2524)
- chlz.exe (PID: 2544)
- chlz.exe (PID: 3624)
- chlz.exe (PID: 3740)
- chlz.exe (PID: 1440)
- chlz.exe (PID: 2664)
- chlz.exe (PID: 3992)
- chlz.exe (PID: 3796)
- chlz.exe (PID: 2132)
- chlz.exe (PID: 3852)
- chlz.exe (PID: 2728)
- chlz.exe (PID: 3168)
- chlz.exe (PID: 2704)
- chlz.exe (PID: 608)
- chlz.exe (PID: 376)
- chlz.exe (PID: 3884)
- chlz.exe (PID: 2600)
- chlz.exe (PID: 2516)
- chlz.exe (PID: 2424)
- chlz.exe (PID: 2528)
- chlz.exe (PID: 2520)
- chlz.exe (PID: 3492)
- chlz.exe (PID: 1352)
- chlz.exe (PID: 3008)
- chlz.exe (PID: 3508)
- chlz.exe (PID: 780)
- chlz.exe (PID: 3348)
- chlz.exe (PID: 740)
- chlz.exe (PID: 2948)
- chlz.exe (PID: 1488)
- chlz.exe (PID: 3104)
- chlz.exe (PID: 580)
- chlz.exe (PID: 4004)
- chlz.exe (PID: 2948)
- chlz.exe (PID: 3352)
- chlz.exe (PID: 2456)
- chlz.exe (PID: 3736)
- chlz.exe (PID: 580)
- chlz.exe (PID: 1860)
- chlz.exe (PID: 2128)
- chlz.exe (PID: 1876)
- chlz.exe (PID: 2920)
- chlz.exe (PID: 2120)
- chlz.exe (PID: 3664)
- chlz.exe (PID: 3948)
- chlz.exe (PID: 2748)
- chlz.exe (PID: 2484)
- chlz.exe (PID: 1248)
- chlz.exe (PID: 3732)
- chlz.exe (PID: 3388)
- chlz.exe (PID: 3388)
- chlz.exe (PID: 3356)
- chlz.exe (PID: 1156)
- chlz.exe (PID: 1196)
- chlz.exe (PID: 2960)
- chlz.exe (PID: 3504)
- chlz.exe (PID: 1136)
- chlz.exe (PID: 4004)
- chlz.exe (PID: 3888)
- chlz.exe (PID: 2600)
- chlz.exe (PID: 3072)
- chlz.exe (PID: 3580)
- chlz.exe (PID: 2356)
- chlz.exe (PID: 2984)
- chlz.exe (PID: 3580)
- chlz.exe (PID: 2648)
- chlz.exe (PID: 680)
- chlz.exe (PID: 2528)
- chlz.exe (PID: 3128)
- chlz.exe (PID: 2412)
Application launched itself
- chlz.exe (PID: 2312)
- chlz.exe (PID: 1836)
- chlz.exe (PID: 2544)
- chlz.exe (PID: 940)
- chlz.exe (PID: 3408)
- chlz.exe (PID: 3740)
- chlz.exe (PID: 1440)
- chlz.exe (PID: 3692)
- chlz.exe (PID: 2684)
- chlz.exe (PID: 2904)
- chlz.exe (PID: 2664)
- chlz.exe (PID: 3992)
- chlz.exe (PID: 1332)
- chlz.exe (PID: 3796)
- chlz.exe (PID: 3108)
- chlz.exe (PID: 2132)
- chlz.exe (PID: 3624)
- chlz.exe (PID: 2452)
- chlz.exe (PID: 3852)
- chlz.exe (PID: 3320)
- chlz.exe (PID: 2728)
- chlz.exe (PID: 2768)
- chlz.exe (PID: 2220)
- chlz.exe (PID: 2704)
- chlz.exe (PID: 3168)
- chlz.exe (PID: 3516)
- chlz.exe (PID: 608)
- chlz.exe (PID: 3832)
- chlz.exe (PID: 4032)
- chlz.exe (PID: 3884)
- chlz.exe (PID: 2992)
- chlz.exe (PID: 2600)
- chlz.exe (PID: 3892)
- chlz.exe (PID: 376)
- chlz.exe (PID: 3400)
- chlz.exe (PID: 2528)
- chlz.exe (PID: 3180)
- chlz.exe (PID: 2520)
- chlz.exe (PID: 3816)
- chlz.exe (PID: 3492)
- chlz.exe (PID: 332)
- chlz.exe (PID: 4092)
- chlz.exe (PID: 3008)
- chlz.exe (PID: 3640)
- chlz.exe (PID: 3508)
- chlz.exe (PID: 1948)
- chlz.exe (PID: 4088)
- chlz.exe (PID: 2624)
- chlz.exe (PID: 280)
- chlz.exe (PID: 2948)
- chlz.exe (PID: 4076)
- chlz.exe (PID: 2548)
- chlz.exe (PID: 1784)
- chlz.exe (PID: 580)
- chlz.exe (PID: 4052)
- chlz.exe (PID: 3376)
- chlz.exe (PID: 4004)
- chlz.exe (PID: 3964)
- chlz.exe (PID: 2672)
- chlz.exe (PID: 2456)
- chlz.exe (PID: 2388)
- chlz.exe (PID: 3568)
- chlz.exe (PID: 580)
- chlz.exe (PID: 2824)
- chlz.exe (PID: 1860)
- chlz.exe (PID: 3224)
- chlz.exe (PID: 3048)
- chlz.exe (PID: 1876)
- chlz.exe (PID: 2436)
- chlz.exe (PID: 2920)
- chlz.exe (PID: 3028)
- chlz.exe (PID: 2752)
- chlz.exe (PID: 3664)
- chlz.exe (PID: 2192)
- chlz.exe (PID: 2712)
- chlz.exe (PID: 2144)
- chlz.exe (PID: 2484)
- chlz.exe (PID: 2868)
- chlz.exe (PID: 1248)
- chlz.exe (PID: 2908)
- chlz.exe (PID: 3388)
- chlz.exe (PID: 1156)
- chlz.exe (PID: 3624)
- chlz.exe (PID: 3236)
- chlz.exe (PID: 1516)
- chlz.exe (PID: 3276)
- chlz.exe (PID: 2960)
- chlz.exe (PID: 2076)
- chlz.exe (PID: 3380)
- chlz.exe (PID: 1196)
- chlz.exe (PID: 3096)
- chlz.exe (PID: 2428)
- chlz.exe (PID: 2068)
- chlz.exe (PID: 4004)
- chlz.exe (PID: 3604)
- chlz.exe (PID: 944)
- chlz.exe (PID: 1872)
- chlz.exe (PID: 3072)
- chlz.exe (PID: 2372)
- chlz.exe (PID: 3580)
- chlz.exe (PID: 2356)
- chlz.exe (PID: 3884)
- chlz.exe (PID: 3600)
- chlz.exe (PID: 3580)
- chlz.exe (PID: 3476)
- chlz.exe (PID: 2648)
- chlz.exe (PID: 2716)
- chlz.exe (PID: 3700)
- chlz.exe (PID: 4036)
- chlz.exe (PID: 3384)
- chlz.exe (PID: 3448)
- chlz.exe (PID: 2528)
- chlz.exe (PID: 3128)
- chlz.exe (PID: 2412)
Loads DLL from Mozilla Firefox
- lsm.exe (PID: 2524)
Uses NETSH.EXE for network configuration
- explorer.exe (PID: 372)
Starts CMD.EXE for commands execution
- explorer.exe (PID: 372)
Executes scripts
- explorer.exe (PID: 372)
Uses NETSTAT.EXE to discover network connections
- explorer.exe (PID: 372)
Uses IPCONFIG.EXE to discover IP address
- explorer.exe (PID: 372)
Uses RUNDLL32.EXE to load library
- explorer.exe (PID: 372)
INFO
Application launched itself
- iexplore.exe (PID: 3972)
Modifies the phishing filter of IE
- iexplore.exe (PID: 3972)
Reads Internet Cache Settings
- iexplore.exe (PID: 3972)
- iexplore.exe (PID: 3112)
Changes internet zones settings
- iexplore.exe (PID: 3972)
Manual execution by user
- lsm.exe (PID: 2524)
- autochk.exe (PID: 3536)
- autoconv.exe (PID: 3888)
- mstsc.exe (PID: 3260)
- cmstp.exe (PID: 1676)
- systray.exe (PID: 2644)
- NAPSTAT.EXE (PID: 3044)
- mstsc.exe (PID: 2084)
- netsh.exe (PID: 572)
- control.exe (PID: 3988)
- lsass.exe (PID: 1724)
- systray.exe (PID: 1932)
- cmd.exe (PID: 2004)
- cmmon32.exe (PID: 2392)
- nbtstat.exe (PID: 2812)
Reads the hosts file
- lsm.exe (PID: 2524)
Creates files in the user directory
- Firefox.exe (PID: 2828)
- iexplore.exe (PID: 3972)
Reads settings of System Certificates
- iexplore.exe (PID: 3972)
Adds / modifies Windows certificates
- iexplore.exe (PID: 3972)
Changes settings of System certificates
- iexplore.exe (PID: 3972)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
328
Monitored processes
296
Malicious processes
124
Suspicious processes
21
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 180 | "C:\Windows\System32\autoconv.exe" | C:\Windows\System32\autoconv.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Auto File System Conversion Utility Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 280 | "C:\Users\admin\AppData\Roaming\chlz\chlz.exe" 2 3168 11035875 | C:\Users\admin\AppData\Roaming\chlz\chlz.exe | — | chlz.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 312 | "C:\Users\admin\AppData\Roaming\chlz\chlz.exe" | C:\Users\admin\AppData\Roaming\chlz\chlz.exe | — | chlz.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 316 | "C:\Users\admin\AppData\Roaming\chlz\chlz.exe" | C:\Users\admin\AppData\Roaming\chlz\chlz.exe | — | chlz.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 332 | "C:\Users\admin\AppData\Roaming\chlz\chlz.exe" 2 3576 11011953 | C:\Users\admin\AppData\Roaming\chlz\chlz.exe | — | chlz.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 348 | "C:\Windows\System32\svchost.exe" | C:\Windows\System32\svchost.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Host Process for Windows Services Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 372 | C:\Windows\Explorer.EXE | C:\Windows\explorer.exe | — | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 376 | "C:\Users\admin\AppData\Roaming\chlz\chlz.exe" | C:\Users\admin\AppData\Roaming\chlz\chlz.exe | chlz.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 376 | "C:\Users\admin\AppData\Roaming\chlz\chlz.exe" 2 2856 10995890 | C:\Users\admin\AppData\Roaming\chlz\chlz.exe | — | chlz.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 392 | "C:\Users\admin\AppData\Roaming\chlz\chlz.exe" | C:\Users\admin\AppData\Roaming\chlz\chlz.exe | — | chlz.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
Total events
67 621
Read events
60 863
Write events
4 515
Delete events
2 243
Modification events
| (PID) Process: | (3972) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateLowDateTime |
Value: 1986065572 | |||
| (PID) Process: | (3972) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 30803618 | |||
| (PID) Process: | (3972) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (3972) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (3972) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (3972) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (3972) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | write | Name: | ProxyEnable |
Value: 0 | |||
| (PID) Process: | (3972) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Connections |
| Operation: | write | Name: | SavedLegacySettings |
Value: 46000000A1000000010000000000000000000000000000000000000000000000C0E333BBEAB1D301000000000000000000000000020000001700000000000000FE800000000000007D6CB050D9C573F70B000000000000006D00330032005C004D00530049004D004700330032002E0064006C000100000004AA400014AA4000040000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000002000000C0A8016400000000000000000000000000000000000000000800000000000000805D3F00983740000008000002000000000000600000002060040000B8A94000020000008802000060040000B8A9400004000000F8010000B284000088B64000B84B400043003A000000000000000000000000000000000000000000 | |||
| (PID) Process: | (3972) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
| (PID) Process: | (3972) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 1 | |||
Executable files
3
Suspicious files
86
Text files
75
Unknown types
4
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3112 | iexplore.exe | C:\Users\admin\Downloads\bk.exe.7fkn8kj.partial | — | |
MD5:— | SHA256:— | |||
| 3972 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\~DF6B11DA53548F2539.TMP | — | |
MD5:— | SHA256:— | |||
| 3972 | iexplore.exe | C:\Users\admin\Downloads\bk.exe.7fkn8kj.partial:Zone.Identifier | — | |
MD5:— | SHA256:— | |||
| 2152 | bk.exe | C:\Users\admin\AppData\Roaming\chlz\chlz.exe\:Zone.Identifier:$DATA | — | |
MD5:— | SHA256:— | |||
| 2152 | bk.exe | C:\Users\admin\AppData\Roaming\chlz\chlz.exe:ZoneIdentifier | — | |
MD5:— | SHA256:— | |||
| 3112 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\MFAQUS6V\bk[1].exe | executable | |
MD5:— | SHA256:— | |||
| 2524 | lsm.exe | C:\Users\admin\AppData\Roaming\149MTU1F\149logim.jpeg | image | |
MD5:— | SHA256:— | |||
| 2544 | chlz.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\chlz.vbs | text | |
MD5:— | SHA256:— | |||
| 3972 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Internet Explorer\Recovery\Active\{A21FF1BF-7295-11EA-972D-5254004A04AF}.dat | binary | |
MD5:— | SHA256:— | |||
| 1232 | chlz.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\chlz.vbs | text | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
27
TCP/UDP connections
35
DNS requests
18
Threats
40
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
372 | explorer.exe | GET | — | 185.106.39.167:80 | http://www.9911742.com/c9c/?Mv18=JiKWIDInMiDtnD599Q4eMxMSLLKdpo/s0tEfqq5vN4706PoptiZkGbOE1Kk2+3GoUQaexg==&VPx4=GfmXFTbpsV&sql=1 | RO | — | — | malicious |
372 | explorer.exe | GET | — | 50.63.202.67:80 | http://www.camsman.com/c9c/?Mv18=9jtm6BjDWvR/78FEdJ9Ptsp4p0/67EUcNH/AllztbwMuSInGwX+0NYZbMjydiY9TtJ6Hpw==&VPx4=GfmXFTbpsV&sql=1 | US | — | — | malicious |
372 | explorer.exe | POST | — | 50.63.202.89:80 | http://www.piwondesigns.com/c9c/ | US | — | — | malicious |
3972 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTBL0V27RVZ7LBduom%2FnYB45SPUEwQU5Z1ZMIJHWMys%2BghUNoZ7OrUETfACEA8sEMlbBsCTf7jUSfg%2BhWk%3D | US | der | 1.47 Kb | whitelisted |
3112 | iexplore.exe | GET | 200 | 109.169.89.118:80 | http://easydatatransfercleansystemprofessional.duckdns.org/intel/bk.exe | GB | executable | 710 Kb | malicious |
372 | explorer.exe | POST | — | 50.63.202.67:80 | http://www.camsman.com/c9c/ | US | — | — | malicious |
3972 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTBL0V27RVZ7LBduom%2FnYB45SPUEwQU5Z1ZMIJHWMys%2BghUNoZ7OrUETfACEA8sEMlbBsCTf7jUSfg%2BhWk%3D | US | der | 1.47 Kb | whitelisted |
372 | explorer.exe | GET | 200 | 52.213.114.86:80 | http://www.radyosesmarmaris.com/c9c/?Mv18=7/0rJqtKmM6BFYOiNN2qMQsEpn8I092sJTb1Ji6Bqn5XC+b6VCi1AYC/VFomXf/7YCZSPA==&VPx4=GfmXFTbpsV&sql=1 | IE | html | 2.84 Kb | malicious |
3972 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTBL0V27RVZ7LBduom%2FnYB45SPUEwQU5Z1ZMIJHWMys%2BghUNoZ7OrUETfACEA8sEMlbBsCTf7jUSfg%2BhWk%3D | US | der | 1.47 Kb | whitelisted |
372 | explorer.exe | POST | — | 185.106.39.167:80 | http://www.9911742.com/c9c/ | RO | — | — | malicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3112 | iexplore.exe | 109.169.89.118:80 | easydatatransfercleansystemprofessional.duckdns.org | iomart Cloud Services Limited. | GB | malicious |
3972 | iexplore.exe | 152.199.19.161:443 | iecvlist.microsoft.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
3972 | iexplore.exe | 204.79.197.200:443 | ieonline.microsoft.com | Microsoft Corporation | US | whitelisted |
372 | explorer.exe | 185.106.39.167:80 | www.9911742.com | — | RO | malicious |
3972 | iexplore.exe | 93.184.220.29:80 | ocsp.digicert.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
372 | explorer.exe | 50.63.202.89:80 | www.piwondesigns.com | GoDaddy.com, LLC | US | malicious |
372 | explorer.exe | 50.63.202.67:80 | www.camsman.com | GoDaddy.com, LLC | US | malicious |
372 | explorer.exe | 52.213.114.86:80 | www.radyosesmarmaris.com | Amazon.com, Inc. | IE | whitelisted |
— | — | 50.63.202.67:80 | www.camsman.com | GoDaddy.com, LLC | US | malicious |
372 | explorer.exe | 35.242.251.130:80 | www.explicit.store | — | US | malicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
easydatatransfercleansystemprofessional.duckdns.org |
| malicious |
iecvlist.microsoft.com |
| whitelisted |
r20swj13mr.microsoft.com |
| whitelisted |
www.wkmind.com |
| unknown |
ieonline.microsoft.com |
| whitelisted |
www.9911742.com |
| malicious |
ocsp.digicert.com |
| whitelisted |
www.piwondesigns.com |
| malicious |
www.majicbbvacuenta.com |
| unknown |
www.lifecode123.com |
| unknown |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1052 | svchost.exe | Misc activity | ET INFO DYNAMIC_DNS Query to *.duckdns. Domain |
3112 | iexplore.exe | Potentially Bad Traffic | ET CURRENT_EVENTS Terse alphanumeric executable downloader high likelihood of being hostile |
3112 | iexplore.exe | Potential Corporate Privacy Violation | ET POLICY PE EXE or DLL Windows file download HTTP |
372 | explorer.exe | A Network Trojan was detected | SPYWARE [PTsecurity] FormBook |
372 | explorer.exe | A Network Trojan was detected | SPYWARE [PTsecurity] FormBook |
372 | explorer.exe | A Network Trojan was detected | SPYWARE [PTsecurity] FormBook |
372 | explorer.exe | A Network Trojan was detected | SPYWARE [PTsecurity] FormBook |
372 | explorer.exe | A Network Trojan was detected | SPYWARE [PTsecurity] FormBook |
372 | explorer.exe | A Network Trojan was detected | SPYWARE [PTsecurity] FormBook |
372 | explorer.exe | A Network Trojan was detected | SPYWARE [PTsecurity] FormBook |
16 ETPRO signatures available at the full report