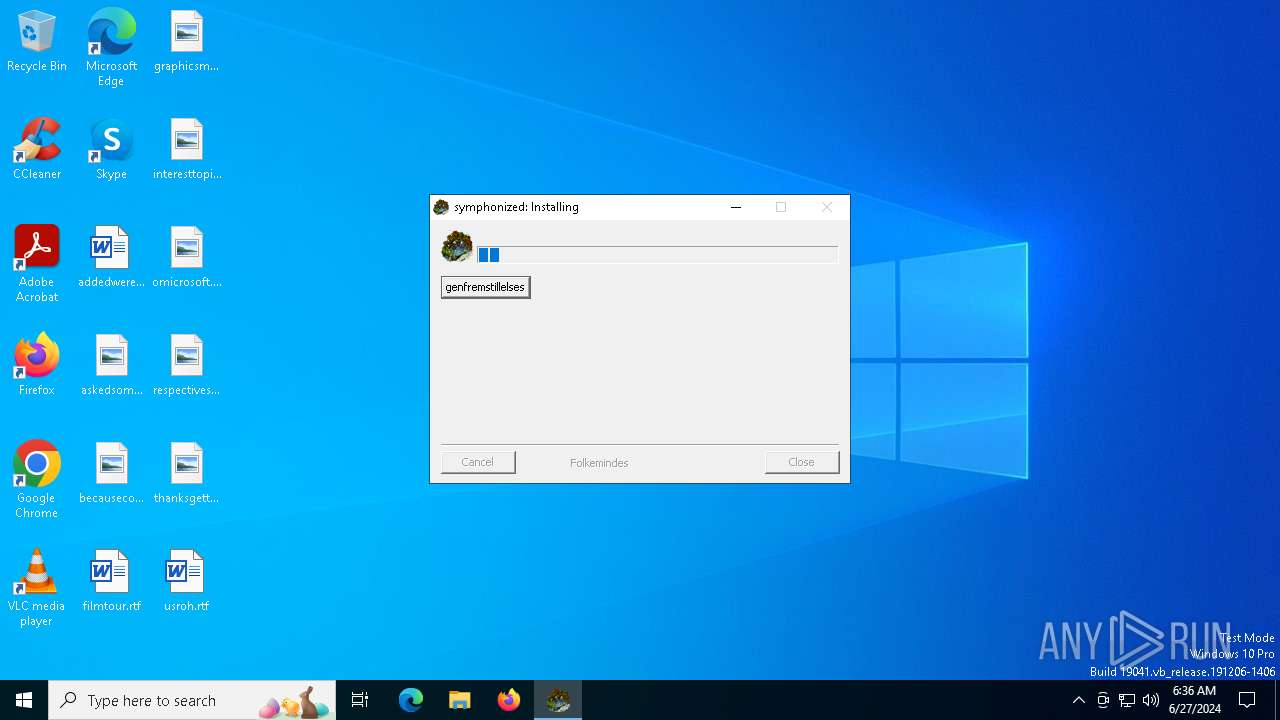
| File name: | 2a089fc9b24c5253a913526be0ac2ee62b911a96645cb70885d678c91dcb83c9.exe |
| Full analysis: | https://app.any.run/tasks/456ffe81-1d41-45c2-bd7c-1fcaeb735877 |
| Verdict: | Malicious activity |
| Threats: | GuLoader is an advanced downloader written in shellcode. It’s used by criminals to distribute other malware, notably trojans, on a large scale. It’s infamous for using anti-detection and anti-analysis capabilities. |
| Analysis date: | June 27, 2024, 06:36:25 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, Nullsoft Installer self-extracting archive |
| MD5: | C7EEFC30A9CDC5BAB3269CEFDE2D221E |
| SHA1: | 27914BC81BDC74D9607784D9E239F5437B1E8CB1 |
| SHA256: | 2A089FC9B24C5253A913526BE0AC2EE62B911A96645CB70885D678C91DCB83C9 |
| SSDEEP: | 24576:28Ub9rVrGnhVpjgzeVYe6oecpeSVhHgXJ2uDeOUlWBxaSGZ2vHG1UL0K:28Ub9rVrGnhPjgzeq/oeM/VhHgXJ2uDz |
MALICIOUS
Drops the executable file immediately after the start
- 2a089fc9b24c5253a913526be0ac2ee62b911a96645cb70885d678c91dcb83c9.exe (PID: 5964)
GULOADER has been detected (YARA)
- 2a089fc9b24c5253a913526be0ac2ee62b911a96645cb70885d678c91dcb83c9.exe (PID: 5964)
GULOADER SHELLCODE has been detected (YARA)
- 2a089fc9b24c5253a913526be0ac2ee62b911a96645cb70885d678c91dcb83c9.exe (PID: 5964)
SUSPICIOUS
Malware-specific behavior (creating "System.dll" in Temp)
- 2a089fc9b24c5253a913526be0ac2ee62b911a96645cb70885d678c91dcb83c9.exe (PID: 5964)
Executable content was dropped or overwritten
- 2a089fc9b24c5253a913526be0ac2ee62b911a96645cb70885d678c91dcb83c9.exe (PID: 5964)
The process creates files with name similar to system file names
- 2a089fc9b24c5253a913526be0ac2ee62b911a96645cb70885d678c91dcb83c9.exe (PID: 5964)
INFO
Creates files or folders in the user directory
- 2a089fc9b24c5253a913526be0ac2ee62b911a96645cb70885d678c91dcb83c9.exe (PID: 5964)
Create files in a temporary directory
- 2a089fc9b24c5253a913526be0ac2ee62b911a96645cb70885d678c91dcb83c9.exe (PID: 5964)
Checks supported languages
- 2a089fc9b24c5253a913526be0ac2ee62b911a96645cb70885d678c91dcb83c9.exe (PID: 5964)
Reads the computer name
- 2a089fc9b24c5253a913526be0ac2ee62b911a96645cb70885d678c91dcb83c9.exe (PID: 5964)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable MS Visual C++ (generic) (67.4) |
|---|---|---|
| .dll | | | Win32 Dynamic Link Library (generic) (14.2) |
| .exe | | | Win32 Executable (generic) (9.7) |
| .exe | | | Generic Win/DOS Executable (4.3) |
| .exe | | | DOS Executable Generic (4.3) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2017:08:01 00:33:55+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 6 |
| CodeSize: | 25088 |
| InitializedDataSize: | 118784 |
| UninitializedDataSize: | 1024 |
| EntryPoint: | 0x330d |
| OSVersion: | 4 |
| ImageVersion: | 6 |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 1.4.0.0 |
| ProductVersionNumber: | 1.4.0.0 |
| FileFlagsMask: | 0x0000 |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Windows, Latin1 |
| FileDescription: | kalaser nonsitting retractability |
| FileVersion: | 1.4.0.0 |
| OriginalFileName: | strabismical.exe |
| ProductName: | stables |
Total processes
137
Monitored processes
1
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 5964 | "C:\Users\admin\AppData\Local\Temp\2a089fc9b24c5253a913526be0ac2ee62b911a96645cb70885d678c91dcb83c9.exe" | C:\Users\admin\AppData\Local\Temp\2a089fc9b24c5253a913526be0ac2ee62b911a96645cb70885d678c91dcb83c9.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Description: kalaser nonsitting retractability Version: 1.4.0.0 Modules
| |||||||||||||||
Total events
3 162
Read events
3 161
Write events
1
Delete events
0
Modification events
| (PID) Process: | (5964) 2a089fc9b24c5253a913526be0ac2ee62b911a96645cb70885d678c91dcb83c9.exe | Key: | HKEY_CURRENT_USER\betnkningstids\Uninstall\solblnder |
| Operation: | write | Name: | Hypothecatory |
Value: 1 | |||
Executable files
1
Suspicious files
7
Text files
3
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 5964 | 2a089fc9b24c5253a913526be0ac2ee62b911a96645cb70885d678c91dcb83c9.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\skdeskindenes\bromamide\Ozonizing\Rentvistens.Afv | binary | |
MD5:EB73C2ADEBA3EAAB747A6017642FA015 | SHA256:F9FFC5682C0CA3CA62D49C769F5A878FAE886CDBB50BB5DFE73D73C790B97D02 | |||
| 5964 | 2a089fc9b24c5253a913526be0ac2ee62b911a96645cb70885d678c91dcb83c9.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\skdeskindenes\bromamide\Ozonizing\Jackhead\Randon17.vgr | gmc | |
MD5:7978BF27082616FAADE55B22394BBDDC | SHA256:B88A13EB0EEDB9BE6E1F809D0B8A55979186DB208858FEDCE5A59B28556B248B | |||
| 5964 | 2a089fc9b24c5253a913526be0ac2ee62b911a96645cb70885d678c91dcb83c9.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\skdeskindenes\bromamide\Ozonizing\Absorbable.sul | abr | |
MD5:6593DE223564535CE11D13BFB74348CA | SHA256:A57CB464F48B61E87ED20832F2D6EAE93C2669BB13850CB6186248E9B597364C | |||
| 5964 | 2a089fc9b24c5253a913526be0ac2ee62b911a96645cb70885d678c91dcb83c9.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\skdeskindenes\bromamide\Ozonizing\Kontrasignatur\skohornet.ser | abr | |
MD5:11825DAB7ECEA24188448D6DE7D605A5 | SHA256:E9F3CA77C307A76C115171B367B540D2615F30636A16EE986C852AEF5EAB6409 | |||
| 5964 | 2a089fc9b24c5253a913526be0ac2ee62b911a96645cb70885d678c91dcb83c9.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\skdeskindenes\bromamide\Ozonizing\Kontrasignatur\temperatures.ref | abr | |
MD5:17DF408E712C3359E4B58F95E4529F16 | SHA256:35D50D71AFA6B8169123458A8232CDE1E3D96E3A0E6734045714192B0930D1AA | |||
| 5964 | 2a089fc9b24c5253a913526be0ac2ee62b911a96645cb70885d678c91dcb83c9.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\skdeskindenes\bromamide\Ozonizing\Jackhead\primaveksel.txt | text | |
MD5:87308607BBEFDD32639F5BCAD963B8C2 | SHA256:A71BD44CA8EFDA96BA1083D1D36FC2148592CA881CFF674C71B7742A1866B012 | |||
| 5964 | 2a089fc9b24c5253a913526be0ac2ee62b911a96645cb70885d678c91dcb83c9.exe | C:\Users\admin\AppData\Local\Temp\tmc.ini | text | |
MD5:ECB33F100E1FCA0EB01B36757EF3CAC8 | SHA256:8734652A2A9E57B56D6CBD22FA9F305FC4691510606BCD2DFCA248D1BF9E79C7 | |||
| 5964 | 2a089fc9b24c5253a913526be0ac2ee62b911a96645cb70885d678c91dcb83c9.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\skdeskindenes\bromamide\Ozonizing\Jackhead\keelhauls.scr | abr | |
MD5:87A3CE82A211E6022D7145C99EEF5EDC | SHA256:66BF6C84307739696EB18D632B6A34755375E61F3C612DC273C7F8F25FCAD938 | |||
| 5964 | 2a089fc9b24c5253a913526be0ac2ee62b911a96645cb70885d678c91dcb83c9.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\skdeskindenes\bromamide\Ozonizing\Aircraft.Bif | binary | |
MD5:89816FE54E6E8CC40D0F8CF8D41CA866 | SHA256:DC6D55B53236ADBC2E7429B5F48A34397806B33139238E06579346BB8E569753 | |||
| 5964 | 2a089fc9b24c5253a913526be0ac2ee62b911a96645cb70885d678c91dcb83c9.exe | C:\Users\admin\AppData\Local\Temp\nssDBDC.tmp\System.dll | executable | |
MD5:55A26D7800446F1373056064C64C3CE8 | SHA256:904FD5481D72F4E03B01A455F848DEDD095D0FB17E33608E0D849F5196FB6FF8 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
7
TCP/UDP connections
63
DNS requests
15
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1544 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | unknown |
2872 | MoUsoCoreWorker.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | unknown |
2872 | MoUsoCoreWorker.exe | GET | 200 | 2.16.241.19:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | unknown |
692 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | unknown |
2400 | SIHClient.exe | GET | 200 | 2.18.97.123:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | unknown |
2400 | SIHClient.exe | GET | 200 | 2.18.97.123:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | unknown |
5736 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2476 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4032 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
6072 | RUXIMICS.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
2872 | MoUsoCoreWorker.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4656 | SearchApp.exe | 2.19.120.29:443 | r.bing.com | Akamai International B.V. | DE | unknown |
1544 | svchost.exe | 20.190.159.0:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
1544 | svchost.exe | 192.229.221.95:80 | — | EDGECAST | US | whitelisted |
1060 | svchost.exe | 2.19.246.123:443 | go.microsoft.com | AKAMAI-AS | DE | unknown |
3040 | OfficeClickToRun.exe | 13.78.111.198:443 | self.events.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | JP | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
r.bing.com |
| whitelisted |
login.live.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
self.events.data.microsoft.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
arc.msn.com |
| whitelisted |
fd.api.iris.microsoft.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |