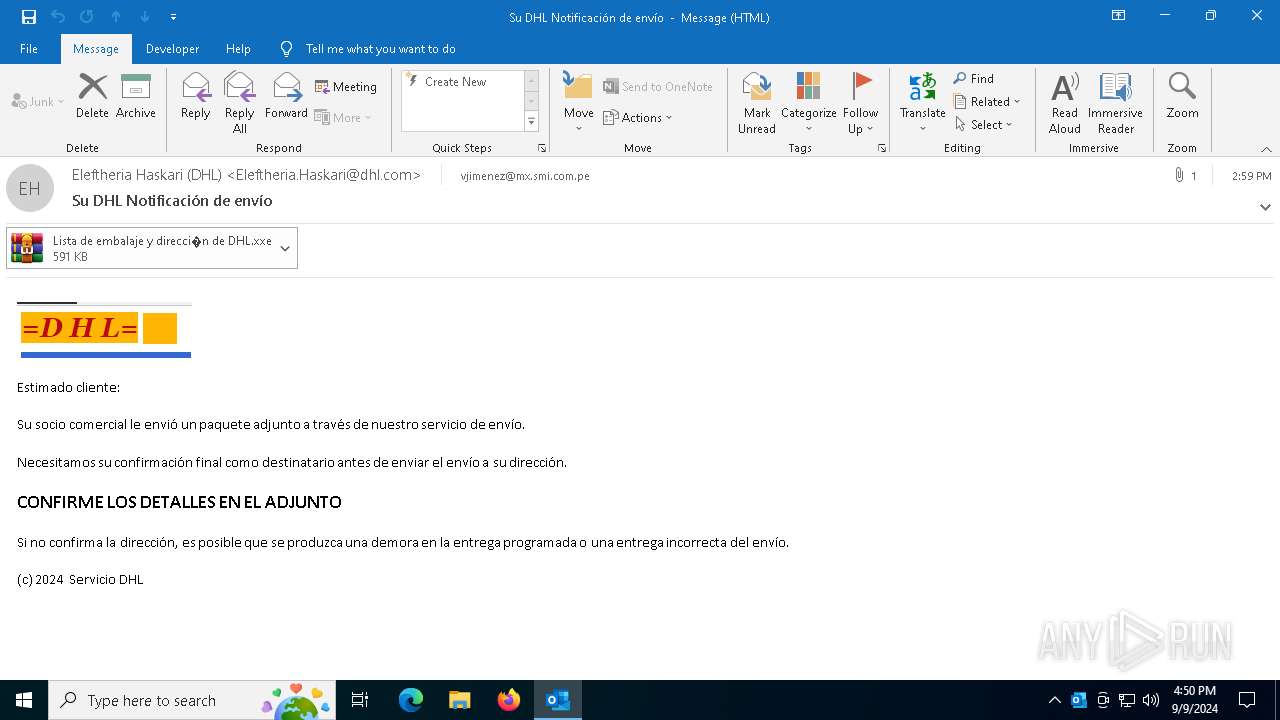
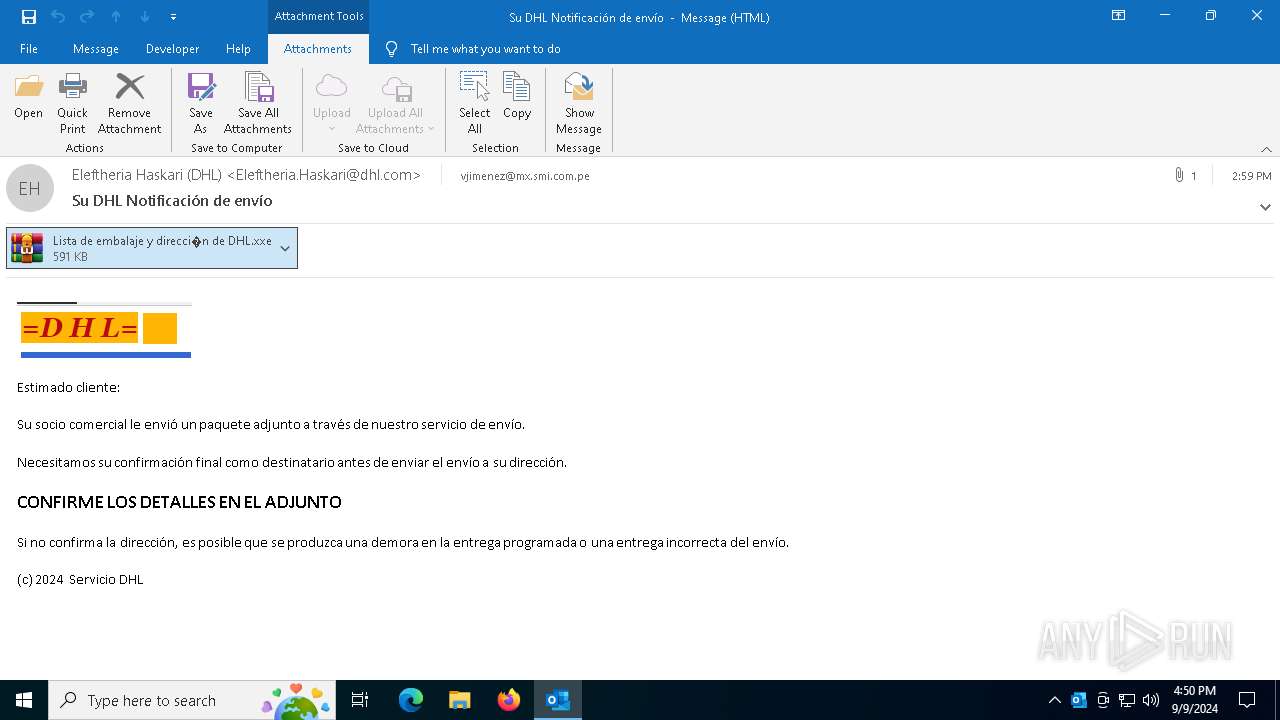
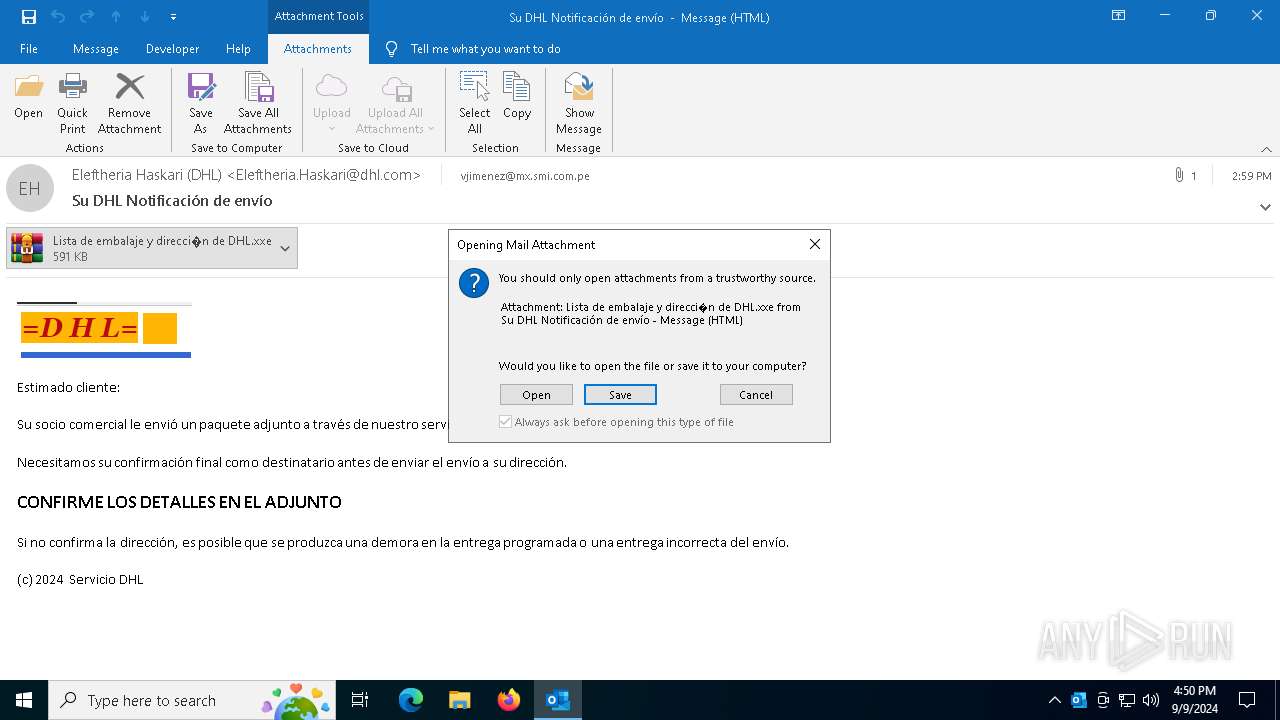
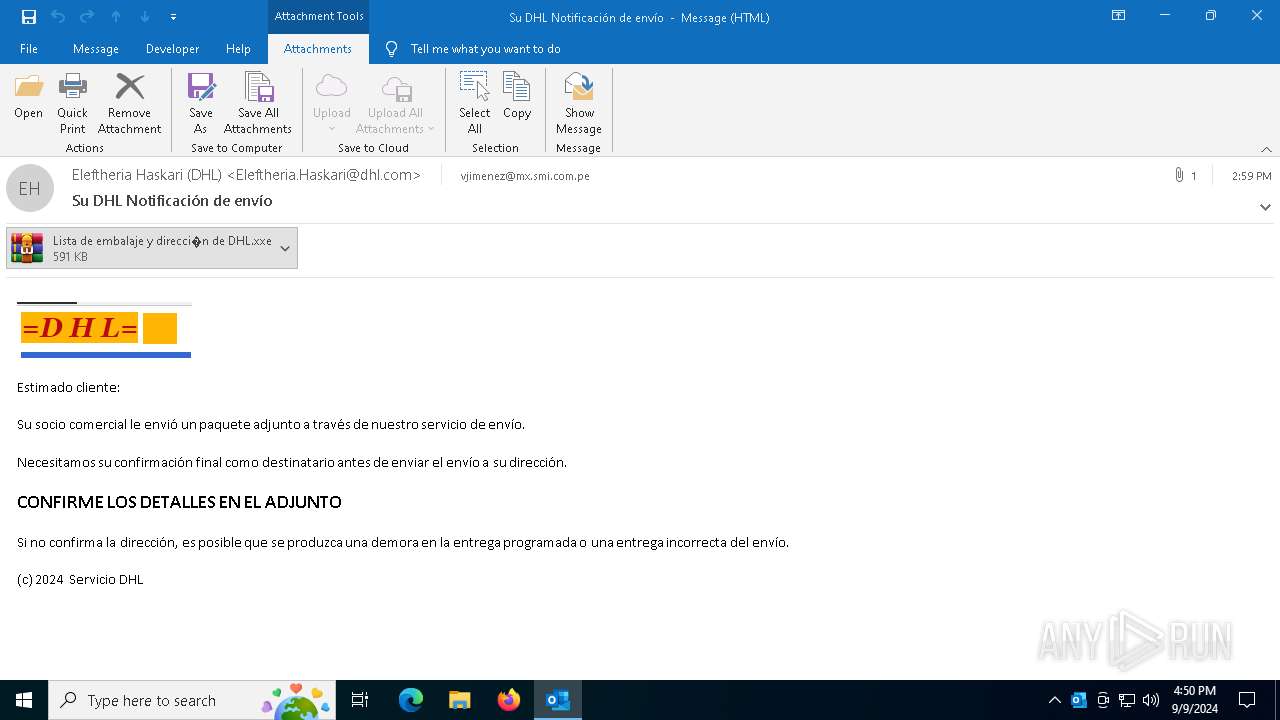
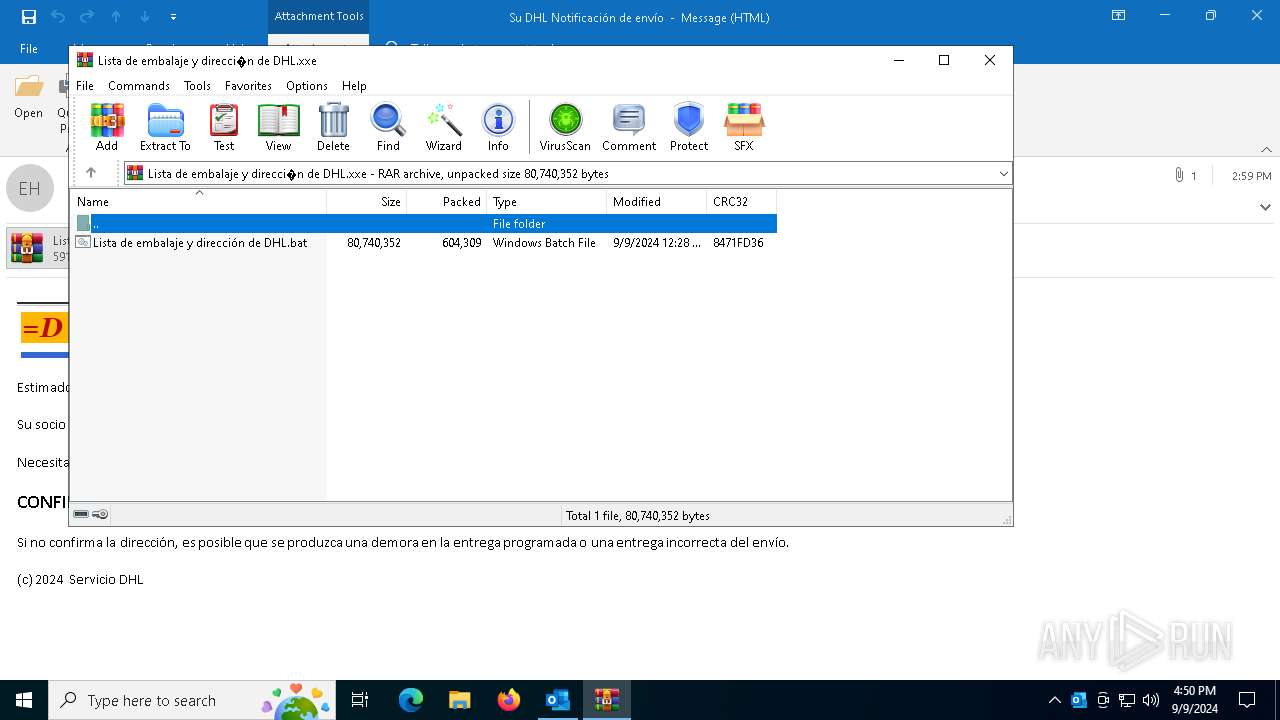
| File name: | Su DHL Notificación de envío.eml |
| Full analysis: | https://app.any.run/tasks/e1a33f04-b07b-432a-864f-a9976fa8bc04 |
| Verdict: | Malicious activity |
| Threats: | Agent Tesla is spyware that collects information about the actions of its victims by recording keystrokes and user interactions. It is falsely marketed as a legitimate software on the dedicated website where this malware is sold. |
| Analysis date: | September 09, 2024, 16:50:20 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | text/html |
| File info: | HTML document, ISO-8859 text, with very long lines (422), with CRLF line terminators |
| MD5: | EBE5091262B4740DE70B677D888E93ED |
| SHA1: | A2E623104328F1A68A57664F0955F273BB4913EB |
| SHA256: | 29B68D071742645DBDB0F7733D117CAD0E7F692AC6F278604928EA331D238FCF |
| SSDEEP: | 12288:dBqmxhCJAdaZzy3BasZgQKwulKuoYLWUKiHFJiLQNiQK8ZUTVfuCLeYLGOvMw:SVJjw1mnlKuTnl7NBNUTV2UeO+w |
MALICIOUS
Unusual execution from MS Outlook
- OUTLOOK.EXE (PID: 5700)
Steals credentials from Web Browsers
- RegSvcs.exe (PID: 1776)
Actions looks like stealing of personal data
- RegSvcs.exe (PID: 1776)
Attempt to transmit an email message via SMTP
- RegSvcs.exe (PID: 1776)
AGENTTESLA has been detected (YARA)
- RegSvcs.exe (PID: 1776)
AGENTTESLA has been detected (SURICATA)
- RegSvcs.exe (PID: 1776)
Stealers network behavior
- RegSvcs.exe (PID: 1776)
Connects to the CnC server
- RegSvcs.exe (PID: 1776)
SUSPICIOUS
Reads security settings of Internet Explorer
- WinRAR.exe (PID: 2484)
Starts application with an unusual extension
- WinRAR.exe (PID: 2484)
Executes application which crashes
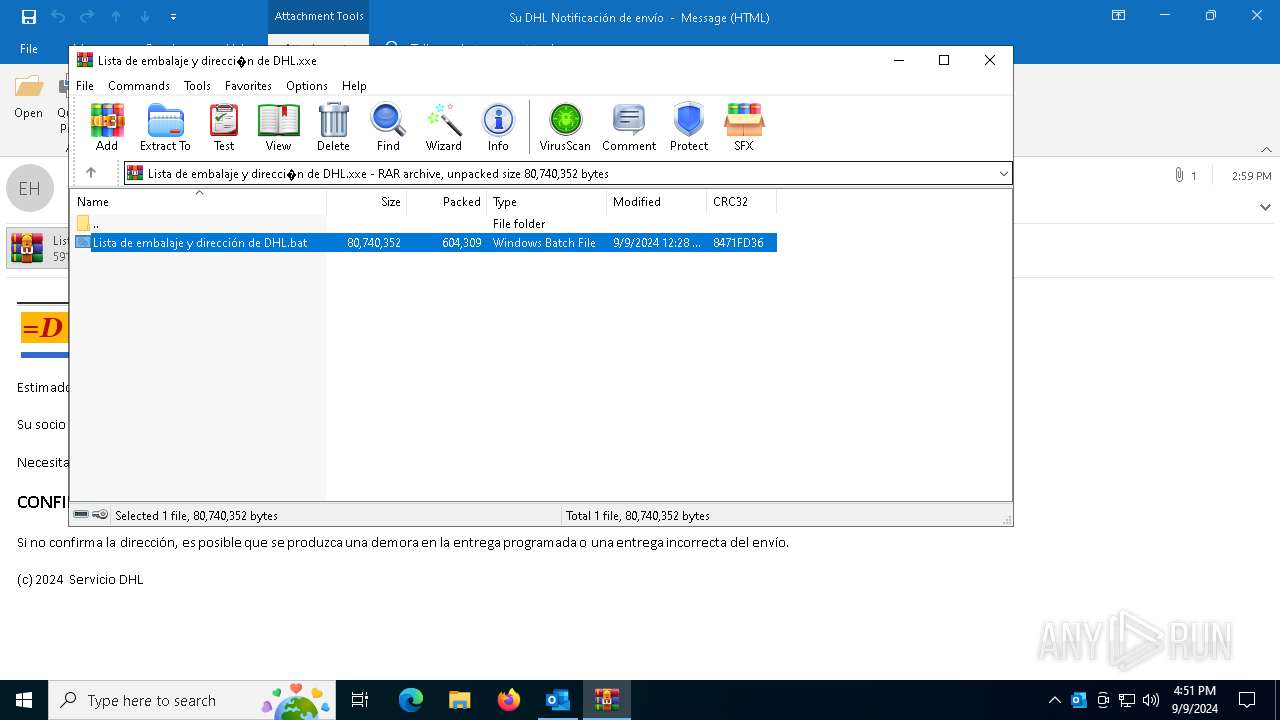
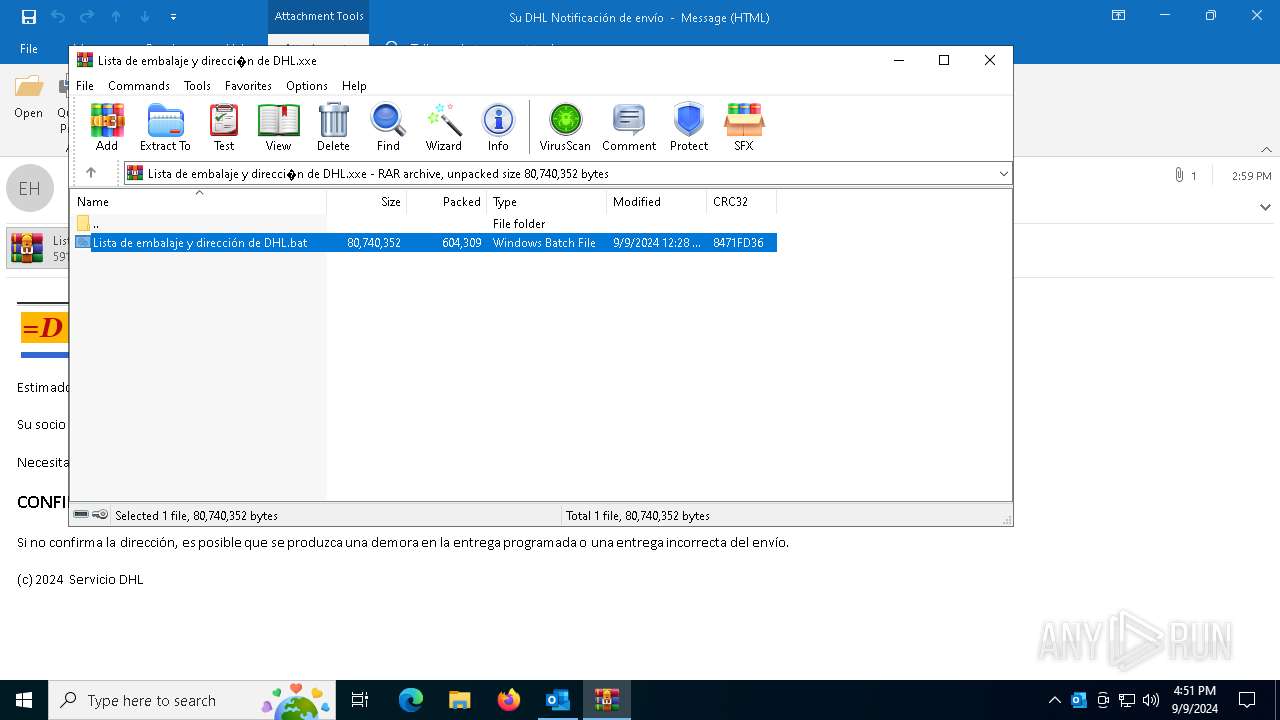
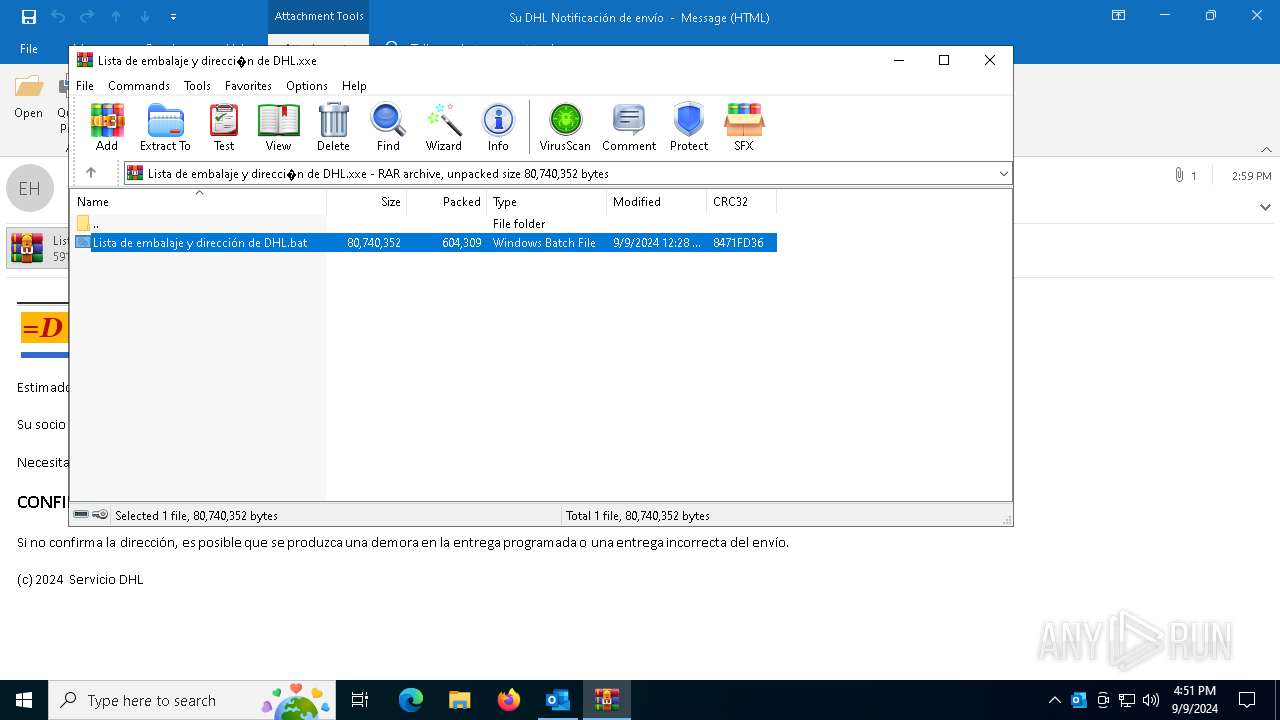
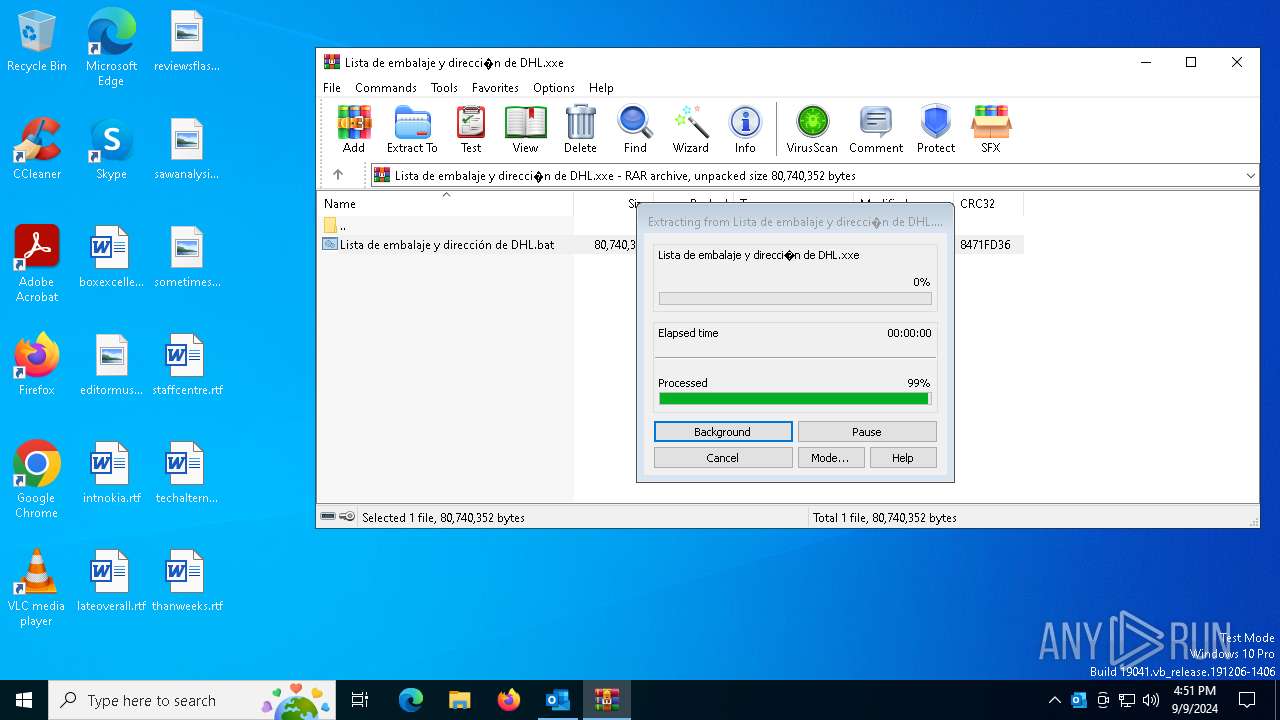
- Lista de embalaje y dirección de DHL.bat (PID: 4576)
Checks for external IP
- svchost.exe (PID: 2256)
- RegSvcs.exe (PID: 1776)
Connects to SMTP port
- RegSvcs.exe (PID: 1776)
Contacting a server suspected of hosting an CnC
- RegSvcs.exe (PID: 1776)
INFO
The process uses the downloaded file
- OUTLOOK.EXE (PID: 5700)
- WinRAR.exe (PID: 2484)
Reads mouse settings
- Lista de embalaje y dirección de DHL.bat (PID: 4576)
- Lista de embalaje y dirección de DHL.bat (PID: 2508)
Create files in a temporary directory
- Lista de embalaje y dirección de DHL.bat (PID: 4576)
- Lista de embalaje y dirección de DHL.bat (PID: 2508)
Checks supported languages
- Lista de embalaje y dirección de DHL.bat (PID: 4576)
- Lista de embalaje y dirección de DHL.bat (PID: 2508)
- RegSvcs.exe (PID: 1776)
Checks proxy server information
- WerFault.exe (PID: 2892)
- RegSvcs.exe (PID: 1776)
Creates files or folders in the user directory
- WerFault.exe (PID: 2892)
Reads the software policy settings
- WerFault.exe (PID: 2892)
Reads the computer name
- RegSvcs.exe (PID: 1776)
Reads the machine GUID from the registry
- RegSvcs.exe (PID: 1776)
Manual execution by a user
- Lista de embalaje y dirección de DHL.bat (PID: 2508)
- cmd.exe (PID: 4772)
Disables trace logs
- RegSvcs.exe (PID: 1776)
Attempt to transmit an email message via SMTP
- RegSvcs.exe (PID: 1776)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
AgentTesla
(PID) Process(1776) RegSvcs.exe
Protocolsmtp
Hostmail.flujoauditorias.cl
Port587
Usernamenedufile1@flujoauditorias.cl
Passwordl;0jGu7J;z_a
Total processes
138
Monitored processes
11
Malicious processes
1
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1776 | "C:\Users\admin\Desktop\Lista de embalaje y dirección de DHL.bat" | C:\Windows\Microsoft.NET\Framework\v4.0.30319\RegSvcs.exe | Lista de embalaje y dirección de DHL.bat | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft .NET Services Installation Utility Version: 4.8.9037.0 built by: NET481REL1 Modules
AgentTesla(PID) Process(1776) RegSvcs.exe Protocolsmtp Hostmail.flujoauditorias.cl Port587 Usernamenedufile1@flujoauditorias.cl Passwordl;0jGu7J;z_a | |||||||||||||||
| 2256 | C:\WINDOWS\system32\svchost.exe -k NetworkService -p -s Dnscache | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2484 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\Content.Outlook\PABBL7IH\Lista de embalaje y direcci�n de DHL.xxe" | C:\Program Files\WinRAR\WinRAR.exe | — | OUTLOOK.EXE | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.91.0 Modules
| |||||||||||||||
| 2508 | "C:\Users\admin\Desktop\Lista de embalaje y dirección de DHL.bat" | C:\Users\admin\Desktop\Lista de embalaje y dirección de DHL.bat | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 2892 | C:\WINDOWS\SysWOW64\WerFault.exe -u -p 4576 -s 832 | C:\Windows\SysWOW64\WerFault.exe | Lista de embalaje y dirección de DHL.bat | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Problem Reporting Exit code: 0 Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4576 | "C:\Users\admin\AppData\Local\Temp\Rar$DIa2484.45674\Lista de embalaje y dirección de DHL.bat" | C:\Users\admin\AppData\Local\Temp\Rar$DIa2484.45674\Lista de embalaje y dirección de DHL.bat | WinRAR.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221225477 Modules
| |||||||||||||||
| 4772 | "C:\WINDOWS\System32\cmd.exe" /C "C:\Users\admin\Desktop\Lista de embalaje y dirección de DHL.bat" | C:\Windows\System32\cmd.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5700 | "C:\Program Files\Microsoft Office\Root\Office16\OUTLOOK.EXE" /eml "C:\Users\admin\AppData\Local\Temp\Su DHL Notificación de envío.eml" | C:\Program Files\Microsoft Office\root\Office16\OUTLOOK.EXE | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Outlook Version: 16.0.16026.20146 Modules
| |||||||||||||||
| 5980 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6756 | "C:\Users\admin\AppData\Local\Temp\Rar$DIa2484.45674\Lista de embalaje y dirección de DHL.bat" | C:\Windows\Microsoft.NET\Framework\v4.0.30319\RegSvcs.exe | — | Lista de embalaje y dirección de DHL.bat | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft .NET Services Installation Utility Exit code: 4294967295 Version: 4.8.9037.0 built by: NET481REL1 Modules
| |||||||||||||||
Total events
18 415
Read events
17 234
Write events
1 042
Delete events
139
Modification events
| (PID) Process: | (5700) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\Common\ClientTelemetry\Sampling |
| Operation: | write | Name: | 6 |
Value: 01941A000000001000B24E9A3E06000000000000000600000000000000 | |||
| (PID) Process: | (5700) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\Common\CrashPersistence\OUTLOOK\5700 |
| Operation: | write | Name: | 0 |
Value: 0B0E1098A0229255501347A7991436F57D34F22300469399D28E86DBC0ED016A04102400449A7D64B29D01008500A907556E6B6E6F776EC906022222CA0DC2190000C91003783634C511C42CD2120B6F00750074006C006F006F006B002E00650078006500C51620C517808004C91808323231322D44656300 | |||
| (PID) Process: | (5700) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Outlook\Diagnostics |
| Operation: | delete value | Name: | BootCommand |
Value: | |||
| (PID) Process: | (5700) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Outlook\Diagnostics |
| Operation: | delete value | Name: | BootFailureCount |
Value: | |||
| (PID) Process: | (5700) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Outlook\Diagnostics\BootDiagnosticsDataPreviousSession |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (5700) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Outlook\Diagnostics\BootDiagnosticsDataPreviousSession |
| Operation: | write | Name: | CantBootResolution |
Value: BootSuccess | |||
| (PID) Process: | (5700) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Outlook\Diagnostics\BootDiagnosticsDataPreviousSession |
| Operation: | write | Name: | ProfileBeingOpened |
Value: Outlook | |||
| (PID) Process: | (5700) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Outlook\Diagnostics\BootDiagnosticsDataPreviousSession |
| Operation: | write | Name: | SessionId |
Value: C3D8E96E-C1AF-4750-8D52-F4E28119C131 | |||
| (PID) Process: | (5700) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Outlook\Diagnostics\BootDiagnosticsDataPreviousSession |
| Operation: | write | Name: | BootDiagnosticsLogFile |
Value: C:\Users\admin\AppData\Local\Temp\Outlook Logging\OUTLOOK_16_0_16026_20146-20240718T1116060318-1644.etl | |||
| (PID) Process: | (5700) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Outlook\Diagnostics |
| Operation: | delete value | Name: | ProfileBeingOpened |
Value: | |||
Executable files
0
Suspicious files
17
Text files
10
Unknown types
1
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 5700 | OUTLOOK.EXE | C:\Users\admin\Documents\Outlook Files\Outlook1.pst | — | |
MD5:— | SHA256:— | |||
| 2484 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DIa2484.45674\Lista de embalaje y dirección de DHL.bat | — | |
MD5:— | SHA256:— | |||
| 5700 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Office\16.0\WebServiceCache\AllUsers\officeclient.microsoft.com\9B8EE094-835A-46A9-A335-98F98ACB04B0 | xml | |
MD5:25EB601B92A5095FA4FFF26842962FEF | SHA256:E799F2B5F1E43FE334D4648F04AA3EC2A5DCE82D674C8CF309085505FA081E89 | |||
| 5700 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Temp\olkC915.tmp | binary | |
MD5:A7826B477AB04C5049EE0ECDE5DE7DC3 | SHA256:1E00A38125830E2762DA0FBAD215A54B607A7DE38DC25B78E5DC3A9739692A4B | |||
| 5700 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\Content.Outlook\PABBL7IH\Lista de embalaje y direcci�n de DHL.xxe:Zone.Identifier | text | |
MD5:FBCCF14D504B7B2DBCB5A5BDA75BD93B | SHA256:EACD09517CE90D34BA562171D15AC40D302F0E691B439F91BE1B6406E25F5913 | |||
| 4576 | Lista de embalaje y dirección de DHL.bat | C:\Users\admin\AppData\Local\Temp\Sheitan | binary | |
MD5:88C48D77BBCBBED6183098D7A7EF6902 | SHA256:C82F4DA7C5E476FB6E8ED62860B7DF3A4A33198AA5E0AECB005D83B3D7040749 | |||
| 5700 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\TokenBroker\Cache\56a61aeb75d8f5be186c26607f4bb213abe7c5ec.tbres | binary | |
MD5:6AD081C8710387C3BF68899FA0767FBB | SHA256:D9B6254875AB93F9E6B31BB5B1FEC2DFE22D8EBAFB323BE89C17A8EF28D50B7A | |||
| 5700 | OUTLOOK.EXE | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\E2C6CBAF0AF08CF203BA74BF0D0AB6D5_6372E0472AFF76BB926C97818BC773B9 | binary | |
MD5:FB6D48DAD9B7772689E7F825B3774772 | SHA256:D21E170115828F1CAB36A101F06C2212596BFBC6BCDAE8EC2CF34E48FBBE6F19 | |||
| 2892 | WerFault.exe | C:\ProgramData\Microsoft\Windows\WER\ReportArchive\AppCrash_Lista de embalaj_645ff58da4843211f89a9e38d59186adcf9111b7_b2c59fd9_b26af575-1bad-4efa-b316-b96b2044c457\Report.wer | — | |
MD5:— | SHA256:— | |||
| 5700 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Office\16.0\AddInClassifierCache\OfficeSharedEntitiesUpdated.bin | text | |
MD5:3557C980E3F5D6A84C6A3BDC7B418186 | SHA256:58D67A25D84FD15AA992380AA36B2F6BA9E77E0499537487EE2305C812A2543A | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
8
TCP/UDP connections
47
DNS requests
26
Threats
13
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2120 | MoUsoCoreWorker.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
5700 | OUTLOOK.EXE | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEA77flR%2B3w%2FxBpruV2lte6A%3D | unknown | — | — | whitelisted |
5700 | OUTLOOK.EXE | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
4056 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
4056 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
2892 | WerFault.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
1776 | RegSvcs.exe | GET | 200 | 208.95.112.1:80 | http://ip-api.com/line/?fields=hosting | unknown | — | — | shared |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
608 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
2120 | MoUsoCoreWorker.exe | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
— | — | 40.126.32.76:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
3888 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
— | — | 40.113.110.67:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
2036 | svchost.exe | 40.126.32.76:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4324 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
officeclient.microsoft.com |
| whitelisted |
ecs.office.com |
| whitelisted |
roaming.officeapps.live.com |
| whitelisted |
omex.cdn.office.net |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2256 | svchost.exe | Device Retrieving External IP Address Detected | INFO [ANY.RUN] External IP Check (ip-api .com) |
2256 | svchost.exe | Device Retrieving External IP Address Detected | ET INFO External IP Lookup Domain in DNS Lookup (ip-api .com) |
1776 | RegSvcs.exe | Device Retrieving External IP Address Detected | ET POLICY External IP Lookup ip-api.com |
1776 | RegSvcs.exe | Device Retrieving External IP Address Detected | POLICY [ANY.RUN] External Hosting Lookup by ip-api |
1776 | RegSvcs.exe | Malware Command and Control Activity Detected | ET MALWARE MSIL/Kryptik.XSY Data Exfil via SMTP |
1776 | RegSvcs.exe | Misc activity | INFO [ANY.RUN] SMTP email client opens transfer with server (EHLO) |
1776 | RegSvcs.exe | A Network Trojan was detected | STEALER [ANY.RUN] AgentTesla Exfiltration SMTP (Base64 encoded) |
1776 | RegSvcs.exe | A Network Trojan was detected | STEALER [ANY.RUN] AgentTesla Exfiltration (raw TCP) |
1776 | RegSvcs.exe | Misc activity | INFO [ANY.RUN] SMTP email client opens transfer with server (EHLO) |
1776 | RegSvcs.exe | A Network Trojan was detected | ET MALWARE AgentTesla Exfil Via SMTP |
3 ETPRO signatures available at the full report