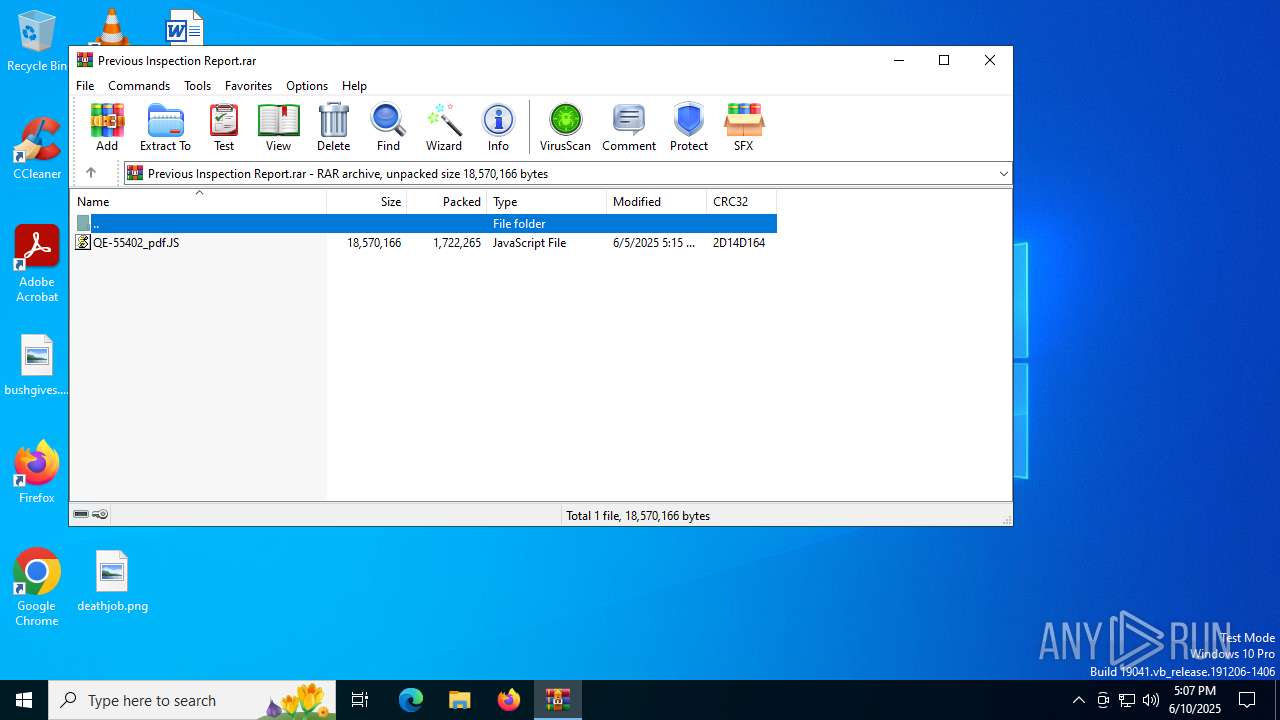
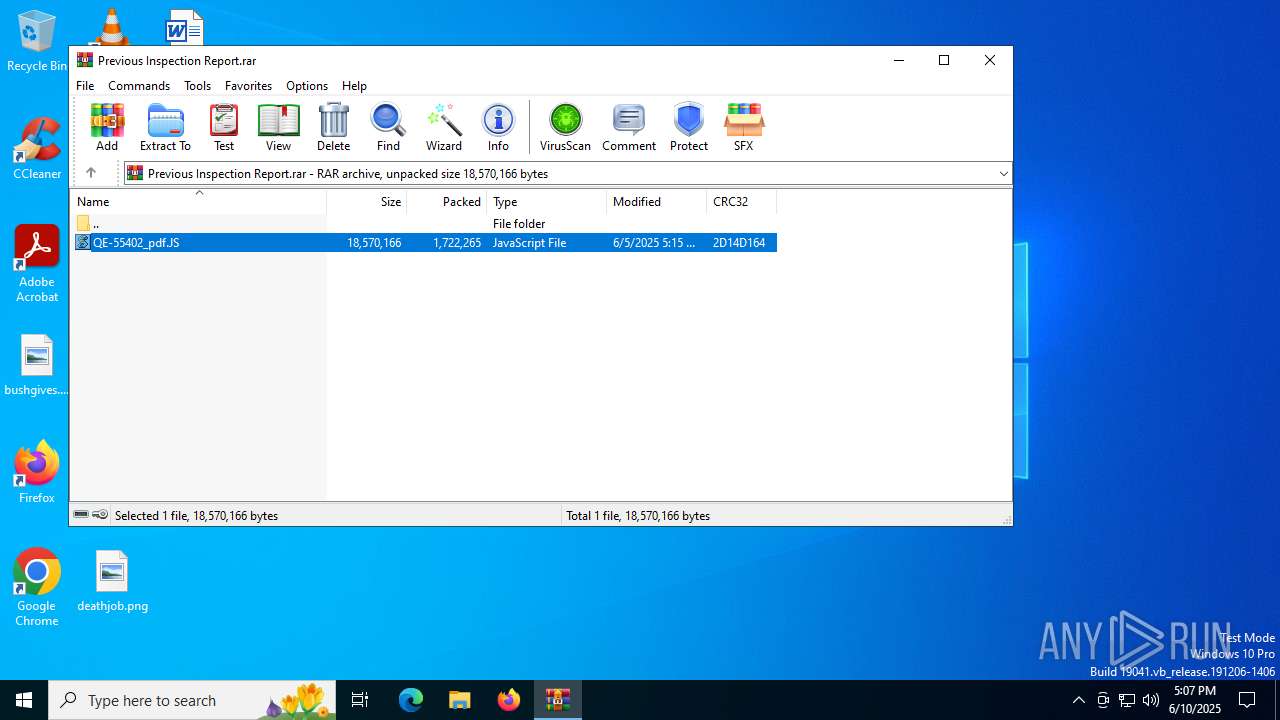
| File name: | Previous Inspection Report.rar |
| Full analysis: | https://app.any.run/tasks/413008fa-0823-457b-83f7-4b4e488cf744 |
| Verdict: | Malicious activity |
| Threats: | DBatLoader is a loader malware used for distributing payloads of different types, including WarzoneRAT and Formbook. It is employed in multi-stage attacks that usually start with a phishing email carrying a malicious attachment. |
| Analysis date: | June 10, 2025, 17:07:33 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-rar |
| File info: | RAR archive data, v5 |
| MD5: | 52B77416FF12F6BDE8BF0912721A331D |
| SHA1: | C4AEC5DB83F170F524C3712744C0410EF778ACF8 |
| SHA256: | 294062EB28A47920CAA070FAD31282AC044036B2949F959DBBA5460F21C2ECA9 |
| SSDEEP: | 49152:12GcvOlTWyIGGDOrXwup3MPXMO2vPhyJ0+tP8A4k4FIa0gVPSgyuxrSRQxhTbEeZ:12GcWVWVfyrAwad2Hh60nA4kIb0gLyu3 |
MALICIOUS
Uses base64 encoding (SCRIPT)
- wscript.exe (PID: 1948)
Detects the decoding of a binary file from Base64 (SCRIPT)
- wscript.exe (PID: 1948)
Gets path to any of the special folders (SCRIPT)
- wscript.exe (PID: 1948)
GENERIC has been found (auto)
- HEO.PIF (PID: 5424)
DBATLOADER has been detected (YARA)
- HEO.PIF (PID: 5424)
Uses Task Scheduler to run other applications
- cmd.exe (PID: 3864)
REMCOS mutex has been found
- veospjeE.pif (PID: 5612)
REMCOS has been detected
- veospjeE.pif (PID: 5612)
SUSPICIOUS
The process executes JS scripts
- WinRAR.exe (PID: 4500)
Script creates XML DOM node (SCRIPT)
- wscript.exe (PID: 1948)
Creates XML DOM element (SCRIPT)
- wscript.exe (PID: 1948)
Reads security settings of Internet Explorer
- WinRAR.exe (PID: 4500)
- HEO.PIF (PID: 5424)
Sets XML DOM element text (SCRIPT)
- wscript.exe (PID: 1948)
Creates a Stream, which may work with files, input/output devices, pipes, or TCP/IP sockets (SCRIPT)
- wscript.exe (PID: 1948)
Writes binary data to a Stream object (SCRIPT)
- wscript.exe (PID: 1948)
Creates FileSystem object to access computer's file system (SCRIPT)
- wscript.exe (PID: 1948)
Drops a file with a rarely used extension (PIF)
- wscript.exe (PID: 1948)
- esentutl.exe (PID: 3672)
- HEO.PIF (PID: 5424)
Saves data to a binary file (SCRIPT)
- wscript.exe (PID: 1948)
Runs shell command (SCRIPT)
- wscript.exe (PID: 1948)
Starts application with an unusual extension
- wscript.exe (PID: 1948)
- cmd.exe (PID: 6400)
- HEO.PIF (PID: 5424)
Executable content was dropped or overwritten
- wscript.exe (PID: 1948)
- esentutl.exe (PID: 3672)
- HEO.PIF (PID: 5424)
- veospjeE.pif (PID: 5612)
Starts CMD.EXE for commands execution
- HEO.PIF (PID: 5424)
Executing commands from ".cmd" file
- HEO.PIF (PID: 5424)
Runs PING.EXE to delay simulation
- cmd.exe (PID: 2864)
Likely accesses (executes) a file from the Public directory
- esentutl.exe (PID: 3672)
- alpha.pif (PID: 3924)
- alpha.pif (PID: 2524)
Starts itself from another location
- cmd.exe (PID: 6400)
Starts a Microsoft application from unusual location
- alpha.pif (PID: 3924)
- alpha.pif (PID: 2524)
There is functionality for taking screenshot (YARA)
- HEO.PIF (PID: 5424)
Created directory related to system
- alpha.pif (PID: 3924)
INFO
Reads Microsoft Office registry keys
- WinRAR.exe (PID: 4500)
Checks supported languages
- HEO.PIF (PID: 5424)
- alpha.pif (PID: 3924)
- veospjeE.pif (PID: 5612)
- alpha.pif (PID: 2524)
Reads the computer name
- HEO.PIF (PID: 5424)
Checks proxy server information
- HEO.PIF (PID: 5424)
Compiled with Borland Delphi (YARA)
- HEO.PIF (PID: 5424)
Creates files in the program directory
- HEO.PIF (PID: 5424)
The sample compiled with english language support
- esentutl.exe (PID: 3672)
- HEO.PIF (PID: 5424)
- veospjeE.pif (PID: 5612)
Reads the machine GUID from the registry
- HEO.PIF (PID: 5424)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .rar | | | RAR compressed archive (v5.0) (61.5) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (38.4) |
EXIF
ZIP
| FileVersion: | RAR v5 |
|---|---|
| CompressedSize: | 1722265 |
| UncompressedSize: | 18570166 |
| OperatingSystem: | Win32 |
| ArchivedFileName: | QE-55402_pdf.JP |
Total processes
152
Monitored processes
17
Malicious processes
5
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1332 | schtasks /create /sc minute /mo 10 /tn "Eejpsoev" /tr C:\\ProgramData\\Eejpsoev.url" | C:\Windows\SysWOW64\schtasks.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Task Scheduler Configuration Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1948 | "C:\Windows\System32\WScript.exe" "C:\Users\admin\AppData\Local\Temp\Rar$DIa4500.7224\QE-55402_pdf.JS" | C:\Windows\System32\wscript.exe | WinRAR.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft ® Windows Based Script Host Exit code: 0 Version: 5.812.10240.16384 Modules
| |||||||||||||||
| 2524 | C:\\Users\\Public\\alpha.pif /c mkdir "\\?\C:\Windows \SysWOW64" | C:\Users\Public\alpha.pif | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2612 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2864 | C:\WINDOWS\system32\cmd.exe /c C:\\ProgramData\\14886.cmd | C:\Windows\SysWOW64\cmd.exe | — | HEO.PIF | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3652 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3672 | C:\\Windows\\System32\\esentutl /y C:\\Windows\\System32\\cmd.exe /d C:\\Users\\Public\\alpha.pif /o | C:\Windows\SysWOW64\esentutl.exe | cmd.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Extensible Storage Engine Utilities for Microsoft(R) Windows(R) Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3864 | C:\WINDOWS\system32\cmd.exe /c C:\\ProgramData\\751.cmd | C:\Windows\SysWOW64\cmd.exe | — | HEO.PIF | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3924 | C:\\Users\\Public\\alpha.pif /c mkdir "\\?\C:\Windows " | C:\Users\Public\alpha.pif | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4500 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\Previous Inspection Report.rar" | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.91.0 Modules
| |||||||||||||||
Total events
3 797
Read events
3 785
Write events
12
Delete events
0
Modification events
| (PID) Process: | (4500) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (4500) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (4500) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (4500) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\Previous Inspection Report.rar | |||
| (PID) Process: | (4500) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (4500) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (4500) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (4500) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (4500) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\FileExts\.js\OpenWithProgids |
| Operation: | write | Name: | JSFile |
Value: | |||
| (PID) Process: | (1948) wscript.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows Script\Settings\Telemetry\wscript.exe |
| Operation: | write | Name: | JScriptSetScriptStateStarted |
Value: 1F7D170000000000 | |||
Executable files
5
Suspicious files
0
Text files
4
Unknown types
1
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 4500 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DIa4500.7224\QE-55402_pdf.JS | — | |
MD5:— | SHA256:— | |||
| 5424 | HEO.PIF | C:\Users\admin\Links\Eejpsoev.PIF | executable | |
MD5:739DA3C138F5BFB8CF0C72CB150E817E | SHA256:4A660C4E59A535C173B1AF94A722B3FD14244EA8E20BABFA98D65E3A3D553802 | |||
| 1948 | wscript.exe | C:\Users\admin\AppData\Local\Temp\HEO.PIF | executable | |
MD5:739DA3C138F5BFB8CF0C72CB150E817E | SHA256:4A660C4E59A535C173B1AF94A722B3FD14244EA8E20BABFA98D65E3A3D553802 | |||
| 5424 | HEO.PIF | C:\ProgramData\14886.cmd | text | |
MD5:9A020804EBA1FFAC2928D7C795144BBF | SHA256:A86C6C7A2BF9E12C45275A5E7EBEBD5E6D2BA302FE0A12600B7C9FDF283D9E63 | |||
| 5424 | HEO.PIF | C:\ProgramData\neo.cmd | text | |
MD5:5BAF253744AD26F35BA17DB6B80763E9 | SHA256:9CBB41E6C4F8565A6D121B770FCF3F15A6891C8DF8BFBA6D0414B3AD3298BDBA | |||
| 5424 | HEO.PIF | C:\ProgramData\751.cmd | text | |
MD5:55716B0C96DE0634D06B3EBB29C1FEFF | SHA256:69A03B911FF907713764326AEA9E283E71DC7D64D383735427346DB0484E57CB | |||
| 5424 | HEO.PIF | C:\ProgramData\Eejpsoev.url | url | |
MD5:D8BC27A27B642E32650086786897A28B | SHA256:215EE293D8B470D7307194108533CB7C3BA96DA829878DDA0553B2C3E1379276 | |||
| 5424 | HEO.PIF | C:\Users\admin\Links\veospjeE.pif | executable | |
MD5:C116D3604CEAFE7057D77FF27552C215 | SHA256:7BCDC2E607ABC65EF93AFD009C3048970D9E8D1C2A18FC571562396B13EBB301 | |||
| 5612 | veospjeE.pif | C:\Users\admin\AppData\Local\Temp\THE1E4.tmp | executable | |
MD5:C116D3604CEAFE7057D77FF27552C215 | SHA256:7BCDC2E607ABC65EF93AFD009C3048970D9E8D1C2A18FC571562396B13EBB301 | |||
| 5424 | HEO.PIF | C:\ProgramData\3076.cmd | text | |
MD5:1DF650CCA01129127D30063634AB5C03 | SHA256:EDD4094E7A82A6FF8BE65D6B075E9513BD15A6B74F8032B5C10CE18F7191FA60 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
5
TCP/UDP connections
24
DNS requests
14
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
7164 | svchost.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 23.216.77.42:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 2.16.253.202:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
5060 | SIHClient.exe | GET | 200 | 2.16.253.202:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
5060 | SIHClient.exe | GET | 200 | 2.16.253.202:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
5944 | MoUsoCoreWorker.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
7052 | RUXIMICS.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1268 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2336 | svchost.exe | 172.211.123.250:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
7164 | svchost.exe | 40.126.31.130:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
7164 | svchost.exe | 2.23.77.188:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
1268 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1268 | svchost.exe | 23.216.77.42:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
nexusrules.officeapps.live.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |