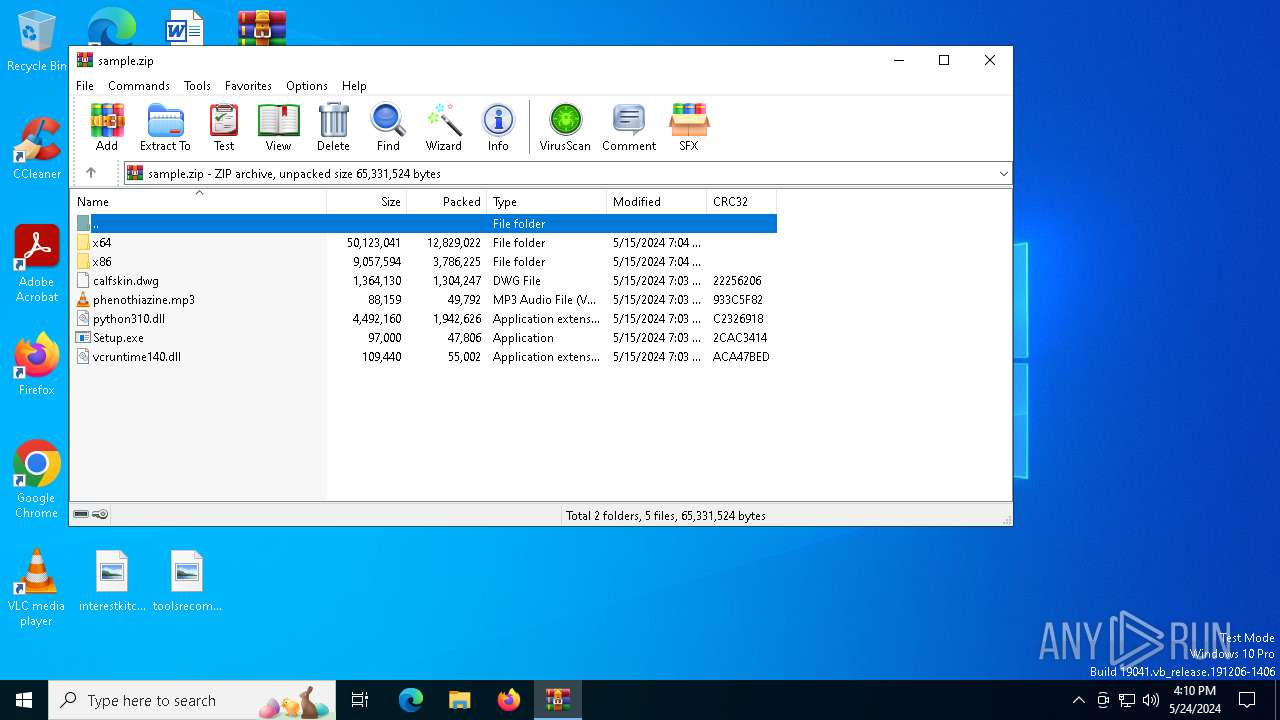
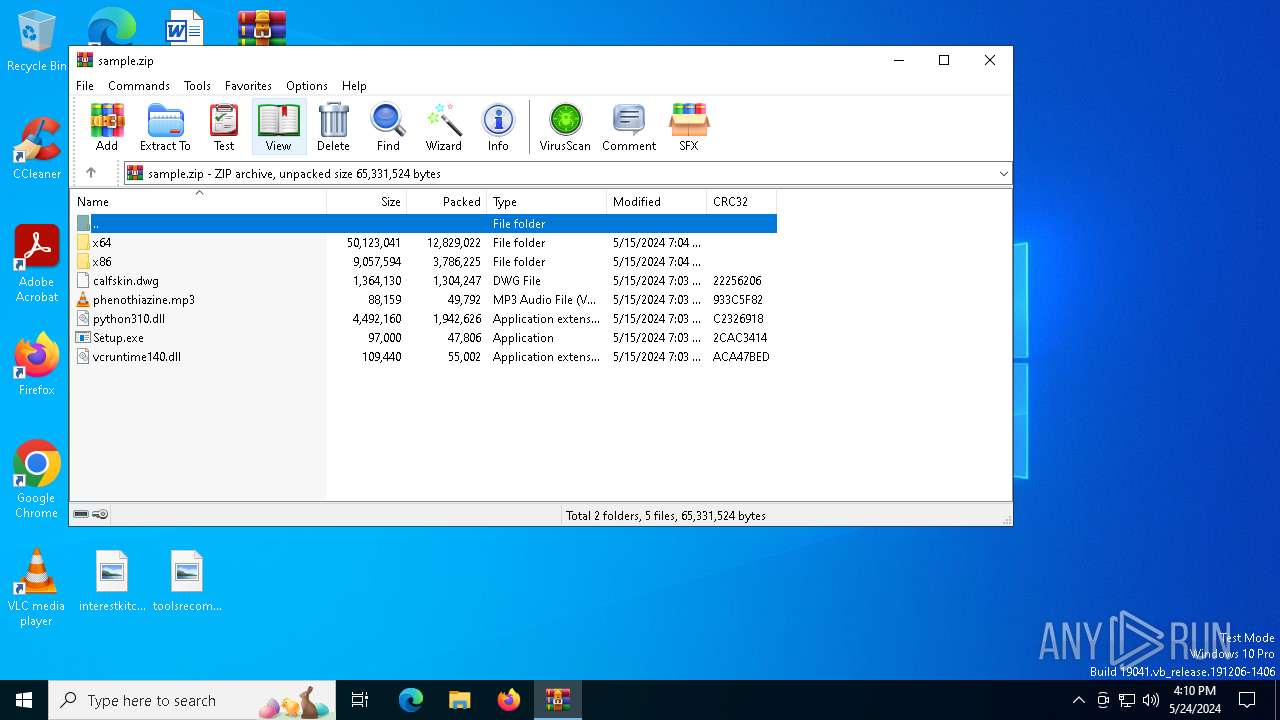
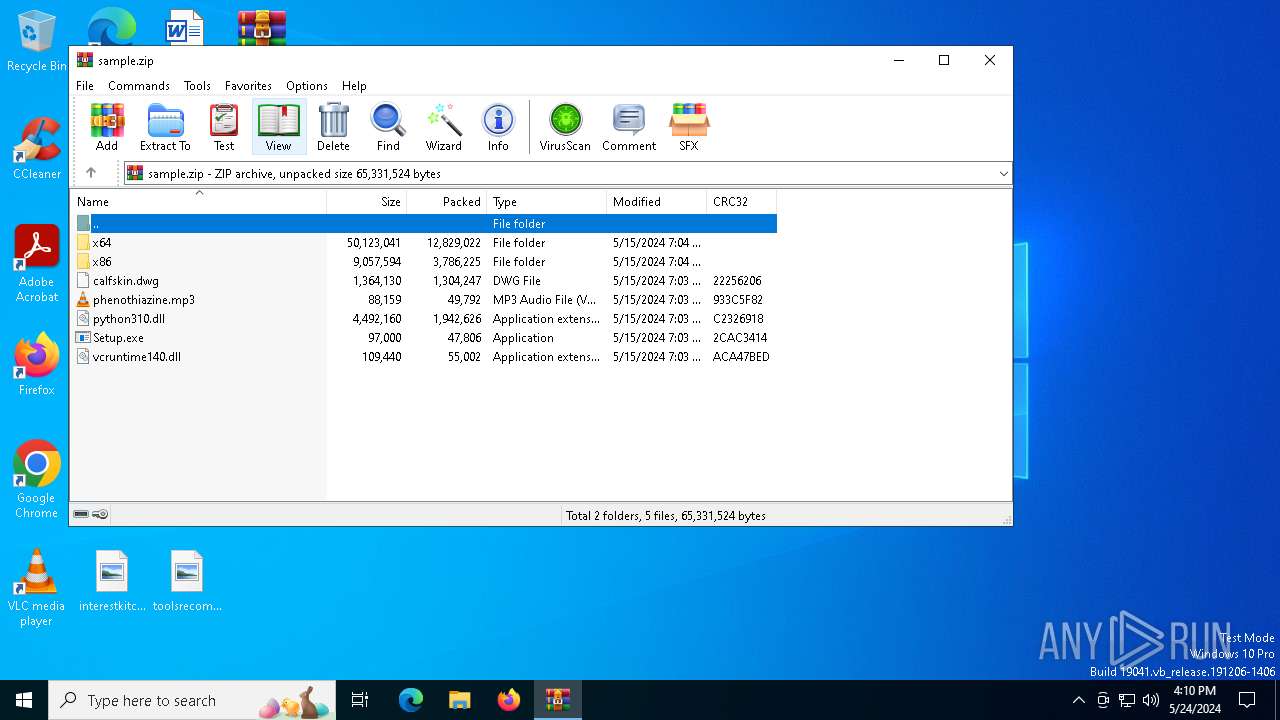
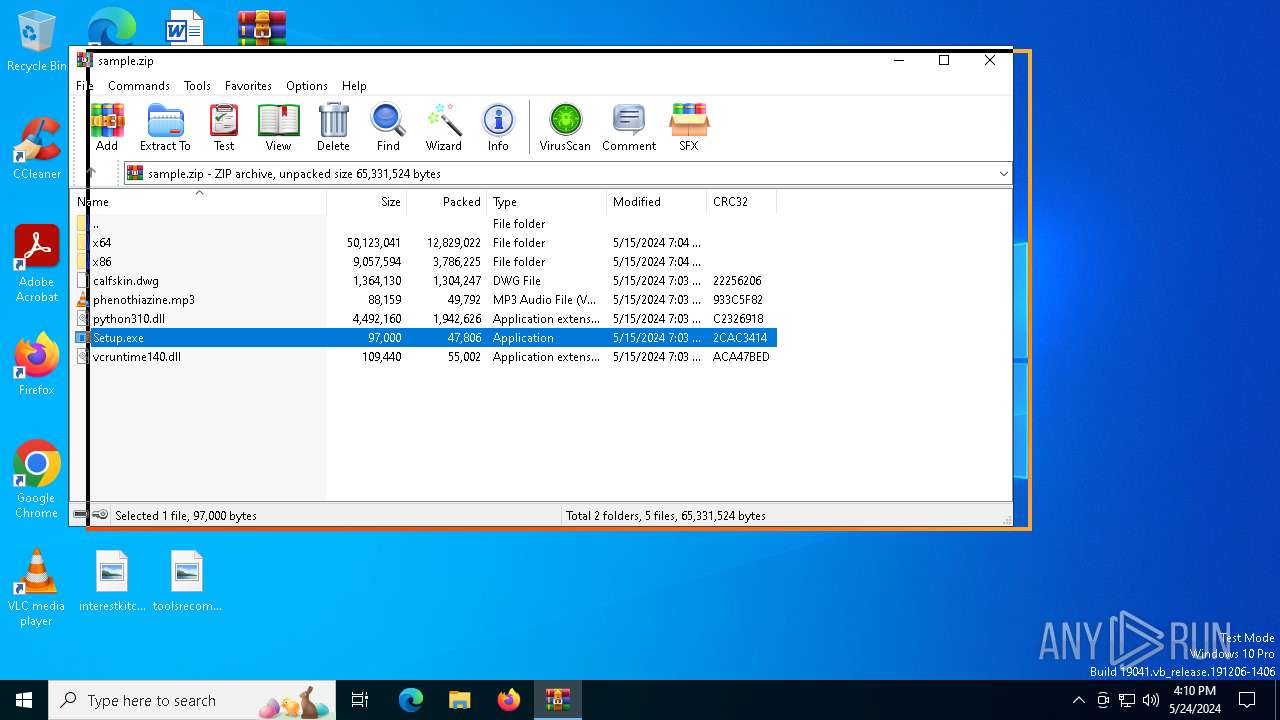
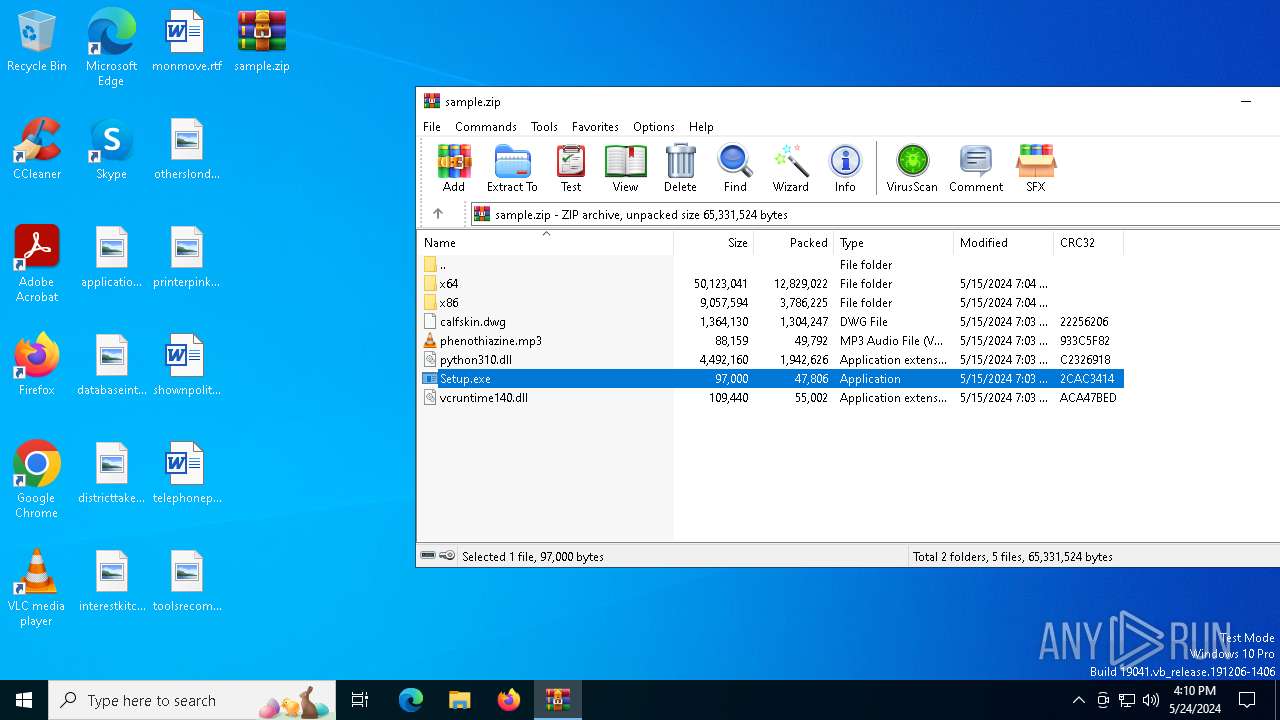
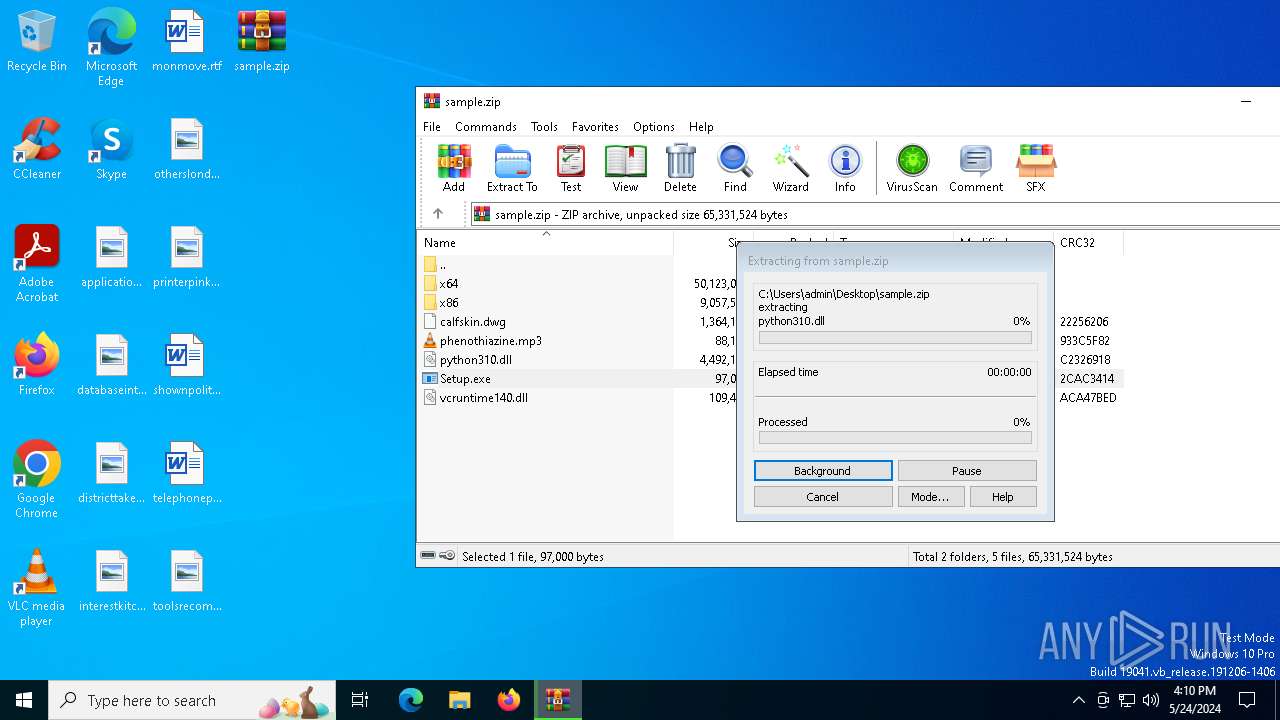
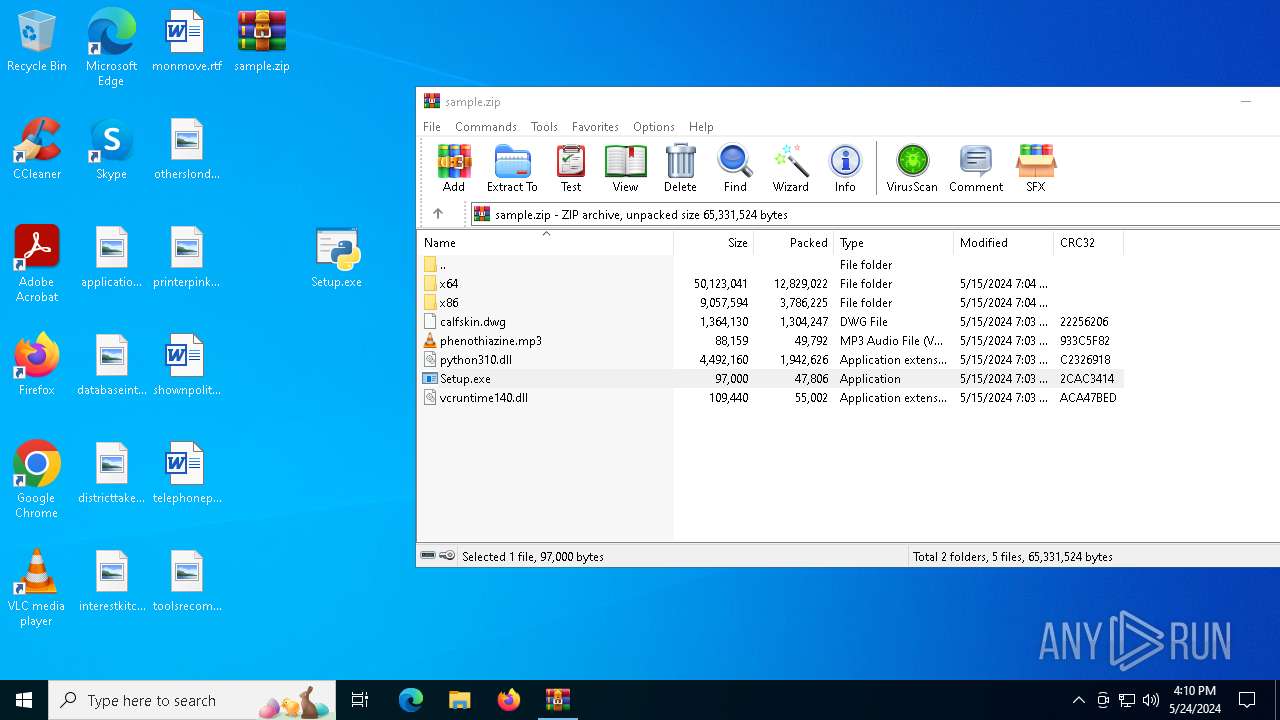
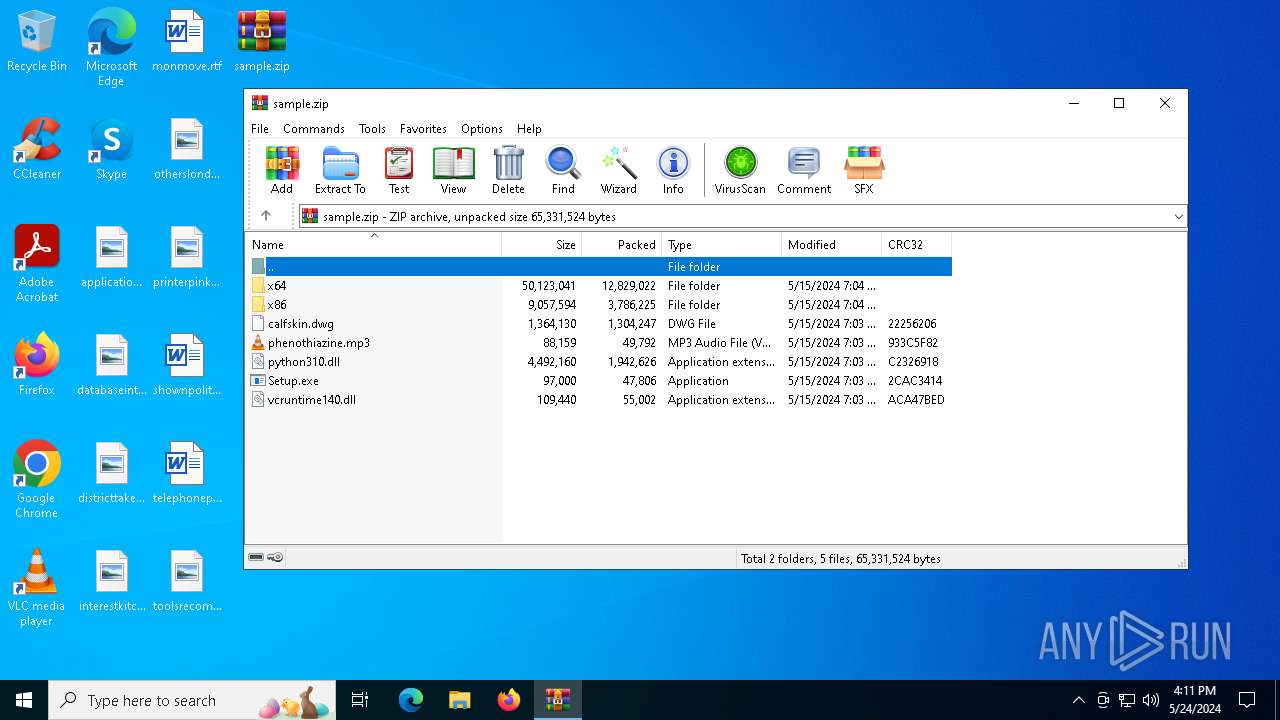
| File name: | sample.zip |
| Full analysis: | https://app.any.run/tasks/9690f29f-6b18-4eef-95a9-91c3ff5f98fc |
| Verdict: | Malicious activity |
| Threats: | HijackLoader is a modular malware acting as a vehicle for distributing different types of malicious software on compromised systems. It gained prominence during the summer of 2023 and has since been used in multiple attacks against organizations from various sectors, including hospitality businesses. |
| Analysis date: | May 24, 2024, 16:09:52 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=deflate |
| MD5: | 4501D61ED00C1D8AC0A281D8951A0F31 |
| SHA1: | 6CF40207E325E8DFC504F5D2544050AA7581576D |
| SHA256: | 2924BA5DBC28096149D847B2C6843D7978F034D620930D9CD93644F309B52EE2 |
| SSDEEP: | 98304:mDfxwDVPJ3nOh7EA068gIRM0cHqsM9rxxpvjoX7j7DVnehTEiX8il7cvKg2Z1Bsb:L2ffBjkerrLLIpVeSCaAVlww+iNJ |
MALICIOUS
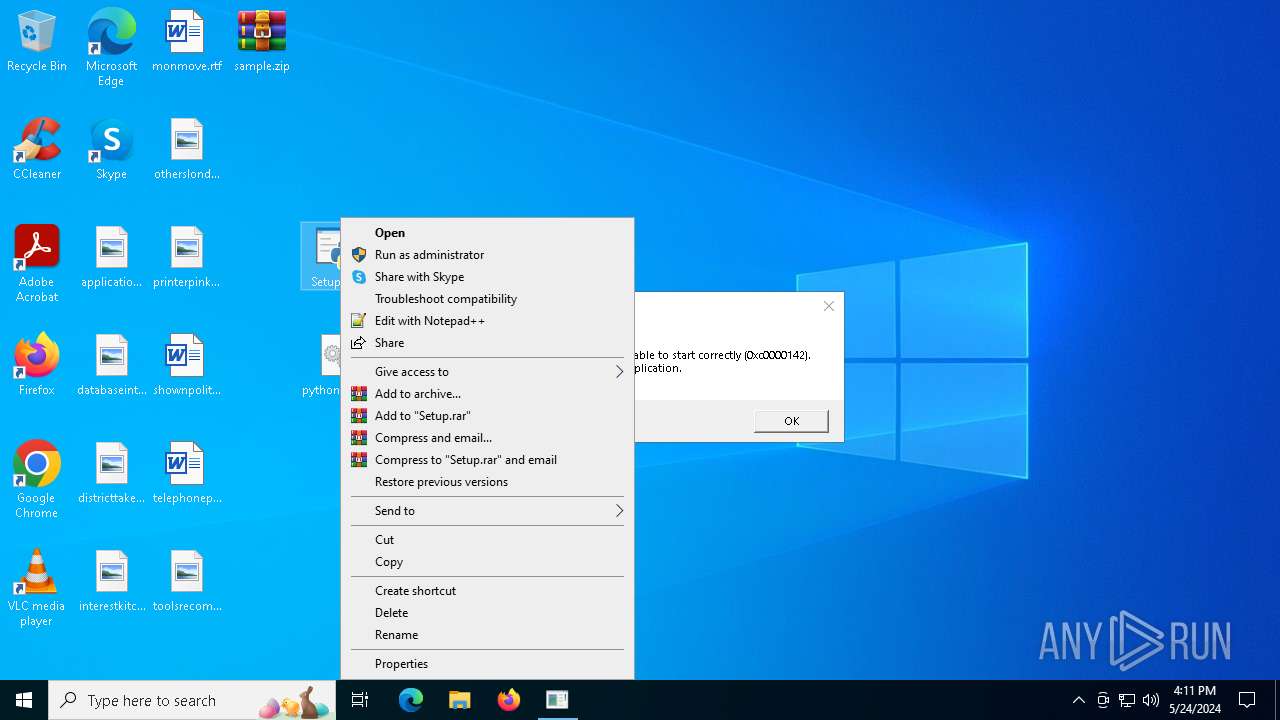
Drops the executable file immediately after the start
- Setup.exe (PID: 5932)
- WinRAR.exe (PID: 4340)
HIJACKLOADER has been detected (YARA)
- comp.exe (PID: 3644)
- Autha.au3 (PID: 1016)
LUMMA has been detected (YARA)
- comp.exe (PID: 3644)
- Autha.au3 (PID: 1016)
LUMMA has been detected (SURICATA)
- Autha.au3 (PID: 1016)
SUSPICIOUS
The process creates files with name similar to system file names
- WinRAR.exe (PID: 4340)
Process drops legitimate windows executable
- WinRAR.exe (PID: 4340)
- Setup.exe (PID: 5932)
Loads Python modules
- Setup.exe (PID: 5932)
- Setup.exe (PID: 4988)
- Setup.exe (PID: 4004)
Reads security settings of Internet Explorer
- WinRAR.exe (PID: 4340)
The process drops C-runtime libraries
- Setup.exe (PID: 5932)
Executable content was dropped or overwritten
- Setup.exe (PID: 5932)
- comp.exe (PID: 3644)
Starts application with an unusual extension
- comp.exe (PID: 3644)
Contacting a server suspected of hosting an CnC
- Autha.au3 (PID: 1016)
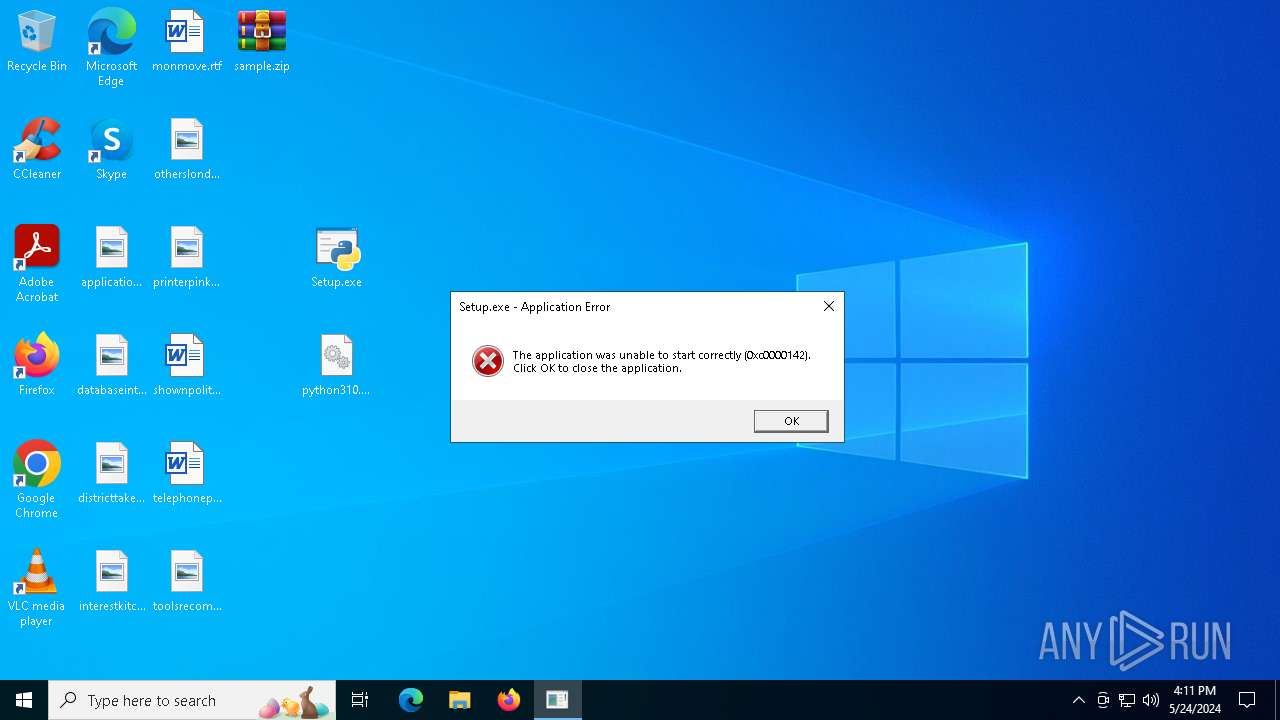
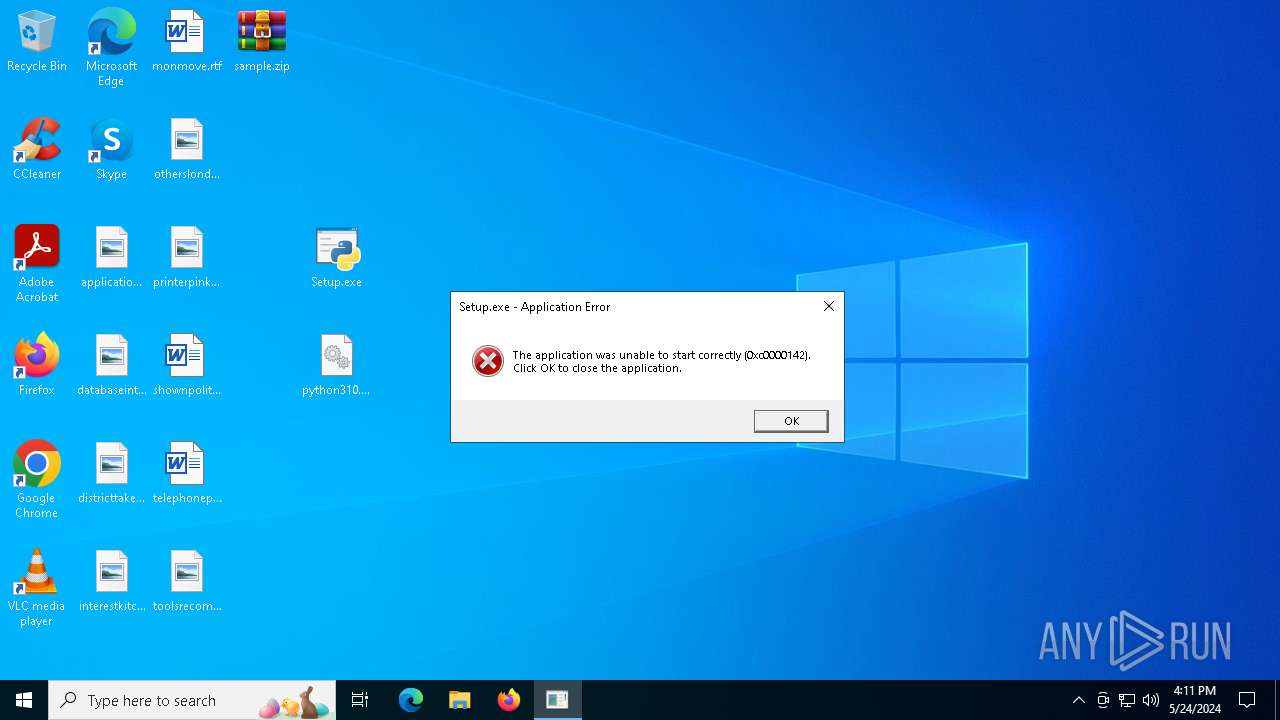
Executes application which crashes
- Setup.exe (PID: 4004)
- Setup.exe (PID: 4988)
INFO
Checks supported languages
- Setup.exe (PID: 5932)
- Autha.au3 (PID: 1016)
- Setup.exe (PID: 4004)
- Setup.exe (PID: 4988)
Reads the computer name
- Setup.exe (PID: 5932)
- Autha.au3 (PID: 1016)
Creates files or folders in the user directory
- Setup.exe (PID: 5932)
- WerFault.exe (PID: 4940)
- WerFault.exe (PID: 3692)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 4340)
Create files in a temporary directory
- comp.exe (PID: 3644)
- Setup.exe (PID: 5932)
Drops the executable file immediately after the start
- comp.exe (PID: 3644)
Manual execution by a user
- WinRAR.exe (PID: 2592)
- Setup.exe (PID: 4004)
- Setup.exe (PID: 4988)
Reads the machine GUID from the registry
- Autha.au3 (PID: 1016)
Reads the software policy settings
- Autha.au3 (PID: 1016)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Lumma
(PID) Process(3644) comp.exe
C2 (9)sofaprivateawarderysj.shop
smallelementyjdui.shop
evokeoutlooklits.shop
tendencyportionjsuk.shop
headraisepresidensu.shop
prideconstituiiosjk.shop
appetitesallooonsj.shop
minorittyeffeoos.shop
lineagelasserytailsd.shop
(PID) Process(1016) Autha.au3
C2 (9)sofaprivateawarderysj.shop
smallelementyjdui.shop
evokeoutlooklits.shop
tendencyportionjsuk.shop
headraisepresidensu.shop
prideconstituiiosjk.shop
appetitesallooonsj.shop
minorittyeffeoos.shop
lineagelasserytailsd.shop
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2024:05:16 03:03:44 |
| ZipCRC: | 0x2cac3414 |
| ZipCompressedSize: | 47806 |
| ZipUncompressedSize: | 97000 |
| ZipFileName: | Setup.exe |
Total processes
119
Monitored processes
10
Malicious processes
4
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1016 | C:\Users\admin\AppData\Local\Temp\Autha.au3 | C:\Users\admin\AppData\Local\Temp\Autha.au3 | comp.exe | ||||||||||||
User: admin Company: AutoIt Team Integrity Level: MEDIUM Description: AutoIt v3 Script Exit code: 0 Version: 3, 3, 14, 5 Modules
Lumma(PID) Process(1016) Autha.au3 C2 (9)sofaprivateawarderysj.shop smallelementyjdui.shop evokeoutlooklits.shop tendencyportionjsuk.shop headraisepresidensu.shop prideconstituiiosjk.shop appetitesallooonsj.shop minorittyeffeoos.shop lineagelasserytailsd.shop | |||||||||||||||
| 2592 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\Desktop\sample.zip" | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 3644 | C:\WINDOWS\SysWOW64\comp.exe | C:\Windows\SysWOW64\comp.exe | Setup.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: File Compare Utility Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
Lumma(PID) Process(3644) comp.exe C2 (9)sofaprivateawarderysj.shop smallelementyjdui.shop evokeoutlooklits.shop tendencyportionjsuk.shop headraisepresidensu.shop prideconstituiiosjk.shop appetitesallooonsj.shop minorittyeffeoos.shop lineagelasserytailsd.shop | |||||||||||||||
| 3692 | C:\WINDOWS\system32\WerFault.exe -u -p 4988 -s 244 | C:\Windows\System32\WerFault.exe | — | Setup.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Problem Reporting Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3740 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | comp.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4004 | "C:\Users\admin\Desktop\Setup.exe" | C:\Users\admin\Desktop\Setup.exe | explorer.exe | ||||||||||||
User: admin Company: Python Software Foundation Integrity Level: MEDIUM Description: Python Exit code: 3221225794 Version: 3.10.0 Modules
| |||||||||||||||
| 4340 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\Desktop\sample.zip | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 4940 | C:\WINDOWS\system32\WerFault.exe -u -p 4004 -s 228 | C:\Windows\System32\WerFault.exe | — | Setup.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Problem Reporting Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4988 | "C:\Users\admin\Desktop\Setup.exe" | C:\Users\admin\Desktop\Setup.exe | explorer.exe | ||||||||||||
User: admin Company: Python Software Foundation Integrity Level: HIGH Description: Python Exit code: 3221225794 Version: 3.10.0 Modules
| |||||||||||||||
| 5932 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa4340.34558\Setup.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa4340.34558\Setup.exe | WinRAR.exe | ||||||||||||
User: admin Company: Python Software Foundation Integrity Level: MEDIUM Description: Python Exit code: 1 Version: 3.10.0 Modules
| |||||||||||||||
Total events
16 650
Read events
16 573
Write events
72
Delete events
5
Modification events
| (PID) Process: | (4340) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (4340) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (4340) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\GoogleChromeEnterpriseBundle64.zip | |||
| (PID) Process: | (4340) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\sample.zip | |||
| (PID) Process: | (4340) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (4340) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (4340) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (4340) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (4340) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\ArcColumnWidths |
| Operation: | write | Name: | name |
Value: 256 | |||
| (PID) Process: | (4340) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\ArcColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
Executable files
136
Suspicious files
8
Text files
7
Unknown types
6
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 4340 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa4340.34558\python310.dll | executable | |
MD5:854459684E529745F811BB42EFBA70C4 | SHA256:07A8F318D28220DDA5373075D9A8D9846A0100A2029ADE86240AAD715A710CA9 | |||
| 4340 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa4340.34558\x64\ComExtractor | executable | |
MD5:36848DD965FF265D696FFF4F2D51935E | SHA256:D66EE1D1E44FEB03D7821062CE27E92DA0FA78F7E47A451B7B1D4B94860DD309 | |||
| 4340 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa4340.34558\phenothiazine.mp3 | binary | |
MD5:532547938E453D08E077053E0A4CE91D | SHA256:FE96FEAA19C2115DD64372E6E9B3F68D3B82D90CCCD9997BA48EC5AD2FC189E0 | |||
| 4340 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa4340.34558\vcruntime140.dll | executable | |
MD5:49C96CECDA5C6C660A107D378FDFC3D4 | SHA256:69320F278D90EFAAEB67E2A1B55E5B0543883125834C812C8D9C39676E0494FC | |||
| 4340 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa4340.34558\x64\App.xbf | xbf | |
MD5:FC6F983B839F1D0702C0D40F107313FB | SHA256:358B9F84ED4326FC989FB70F5D6D17E8E268EABB476B9E3EF6270872B00189F3 | |||
| 4340 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa4340.34558\x64\AzureKeyVaultDgssLib.dll | executable | |
MD5:34AE0787CDFCB920753763251DCF83DE | SHA256:3EEE708FDCC68FE76AC4CC7ADBA90201912C63CD815717F91A5EABBA1170AF0D | |||
| 4340 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa4340.34558\calfskin.dwg | binary | |
MD5:6B89F1FCD2AAEE22AB998A7C2294CC12 | SHA256:5C09E3F22F62EAB57C12DEC41E3CA7FCA196052D4DAF2E96CB434C5EF328319C | |||
| 4340 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa4340.34558\x64\NvStereoUtilityOGL_[1MB]_[1].exe | executable | |
MD5:017CD77D01314E72A973FF0C7882453D | SHA256:C2C71318A17F7F767E5D203D22B48F27EECAE46A4F37082D7B413C51DA6183B3 | |||
| 4340 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa4340.34558\x64\WinUiBootstrapper.dll | executable | |
MD5:290538FCEAE682F2CFC3580E01FA7D28 | SHA256:C0CFD5ECD4FA7C78EEE91C4A2E7963E805513A88AD376772108B9B0C54BB8551 | |||
| 4340 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa4340.34558\x64\RepackagerStartPage.xbf | xbf | |
MD5:B77B52B21F44A30643F800322C78F9F9 | SHA256:19643ABF5047635E3D9A81F94BBF2B7E0EA6D2631D0BEAACE56511692ACF6E14 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
4
TCP/UDP connections
8
DNS requests
2
Threats
3
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 4.231.128.59:443 | https://settings-win.data.microsoft.com/settings/v3.0/WSD/WaasMedic?os=Windows&osVer=10.0.19041.1.amd64fre.vb_release.191206-&appVer=10.0.19041.3758&ring=Retail&sku=48&deviceClass=Windows.Desktop&locale=en-US&deviceId=BAD99146-31D3-4EC6-A1A4-BE76F32BA5D4 | unknown | binary | 3.41 Kb | unknown |
2908 | OfficeClickToRun.exe | POST | — | 20.189.173.4:443 | https://self.events.data.microsoft.com/OneCollector/1.0/ | unknown | — | — | unknown |
1016 | Autha.au3 | POST | 200 | null:443 | https://evokeoutlooklits.shop/api | unknown | text | 10.5 Kb | unknown |
1016 | Autha.au3 | POST | 200 | null:443 | https://evokeoutlooklits.shop/api | unknown | text | 2 b | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 239.255.255.250:1900 | — | — | — | unknown |
— | — | 51.124.78.146:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | NL | unknown |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1016 | Autha.au3 | 188.114.96.3:443 | evokeoutlooklits.shop | CLOUDFLARENET | NL | unknown |
2908 | OfficeClickToRun.exe | 20.189.173.4:443 | self.events.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
evokeoutlooklits.shop |
| malicious |
self.events.data.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2184 | svchost.exe | Domain Observed Used for C2 Detected | ET MALWARE Lumma Stealer Related CnC Domain in DNS Lookup (evokeoutlooklits .shop) |
1016 | Autha.au3 | Domain Observed Used for C2 Detected | ET MALWARE Observed Lumma Stealer Related Domain (evokeoutlooklits .shop in TLS SNI) |
1016 | Autha.au3 | A Network Trojan was detected | STEALER [ANY.RUN] Lumma Stealer TLS Connection |