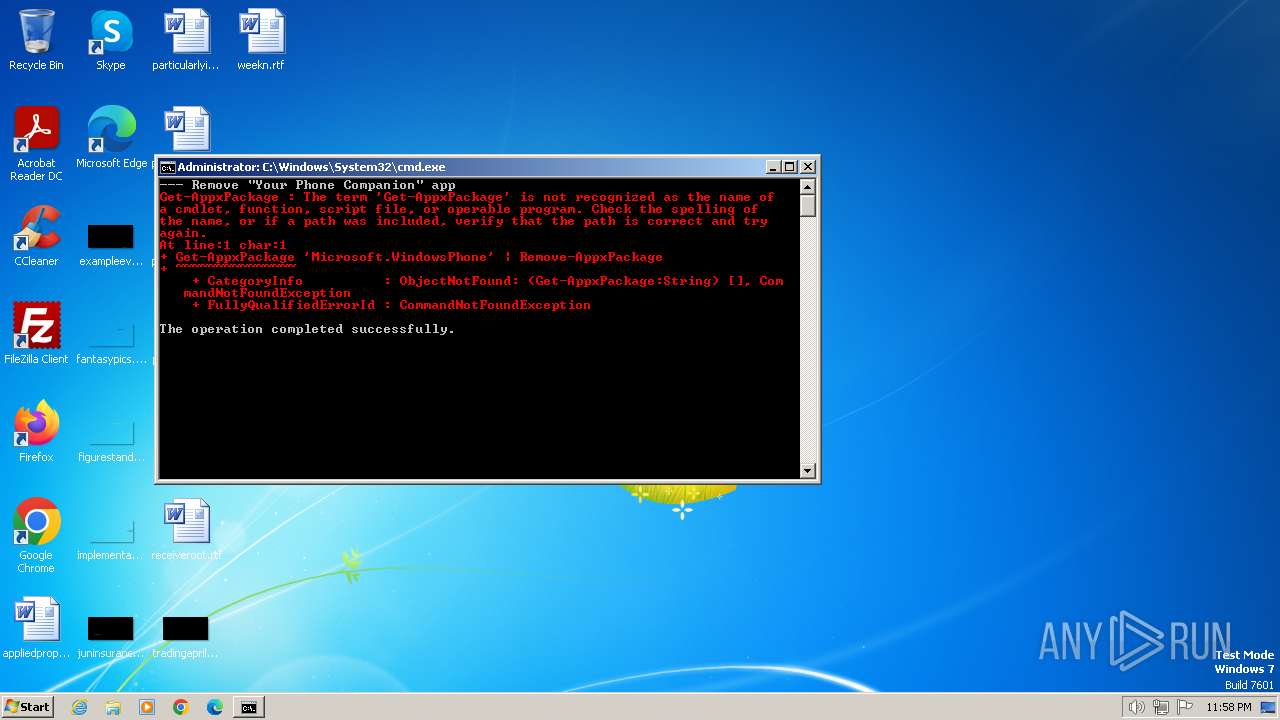
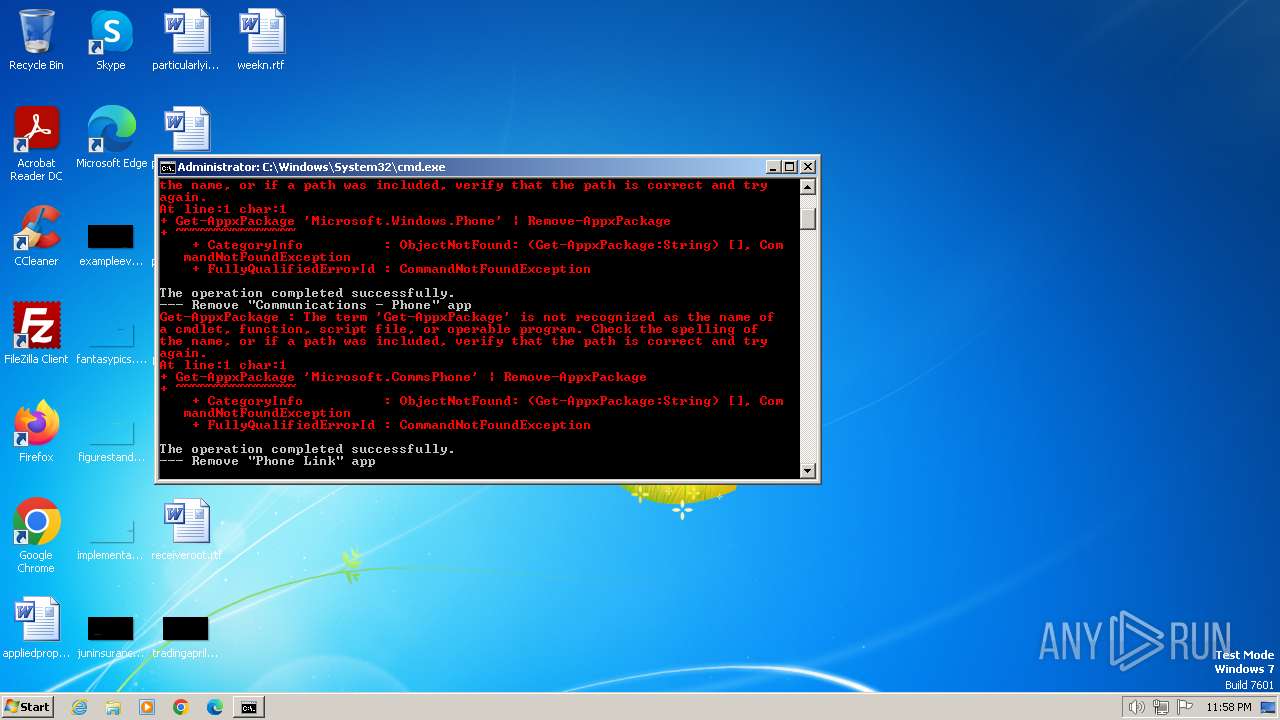
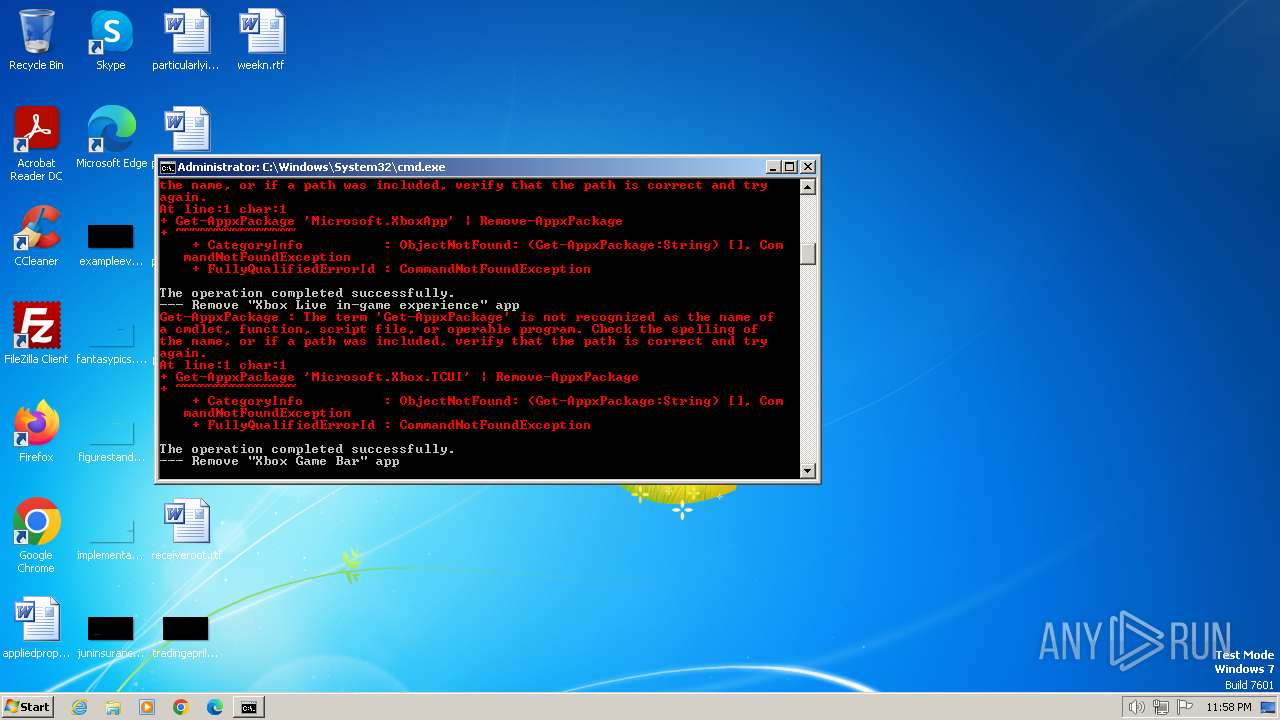
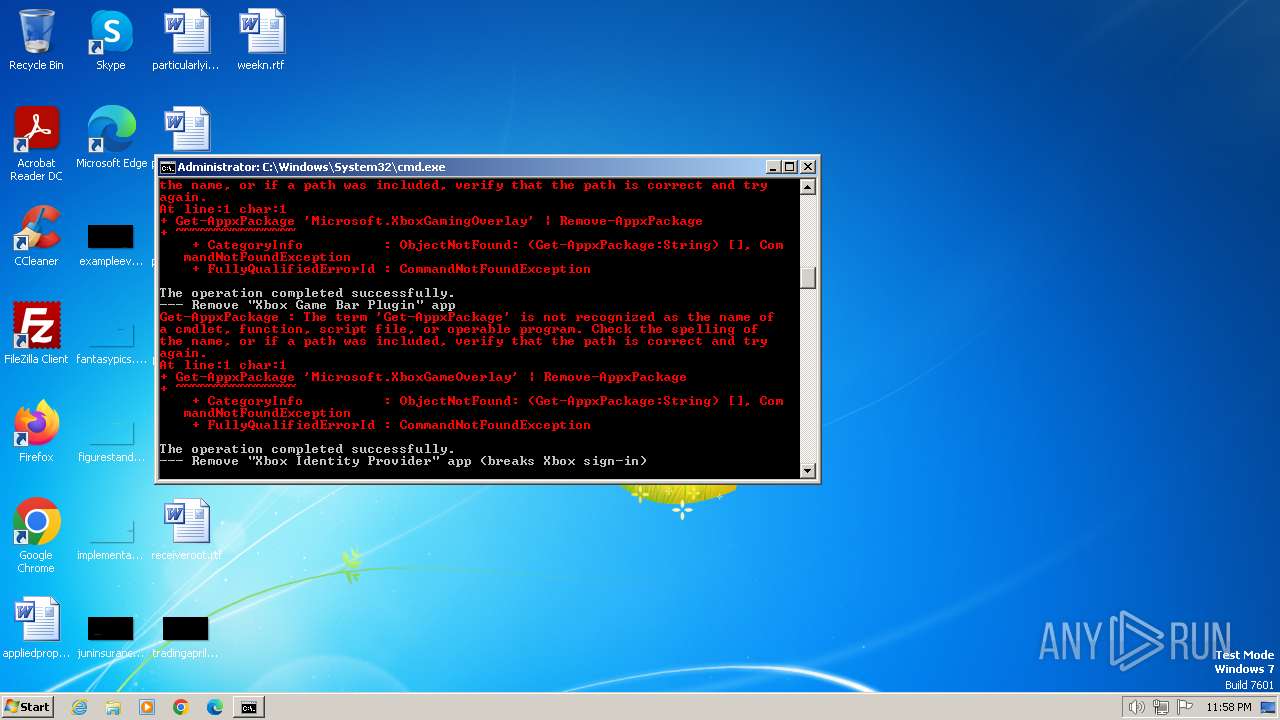
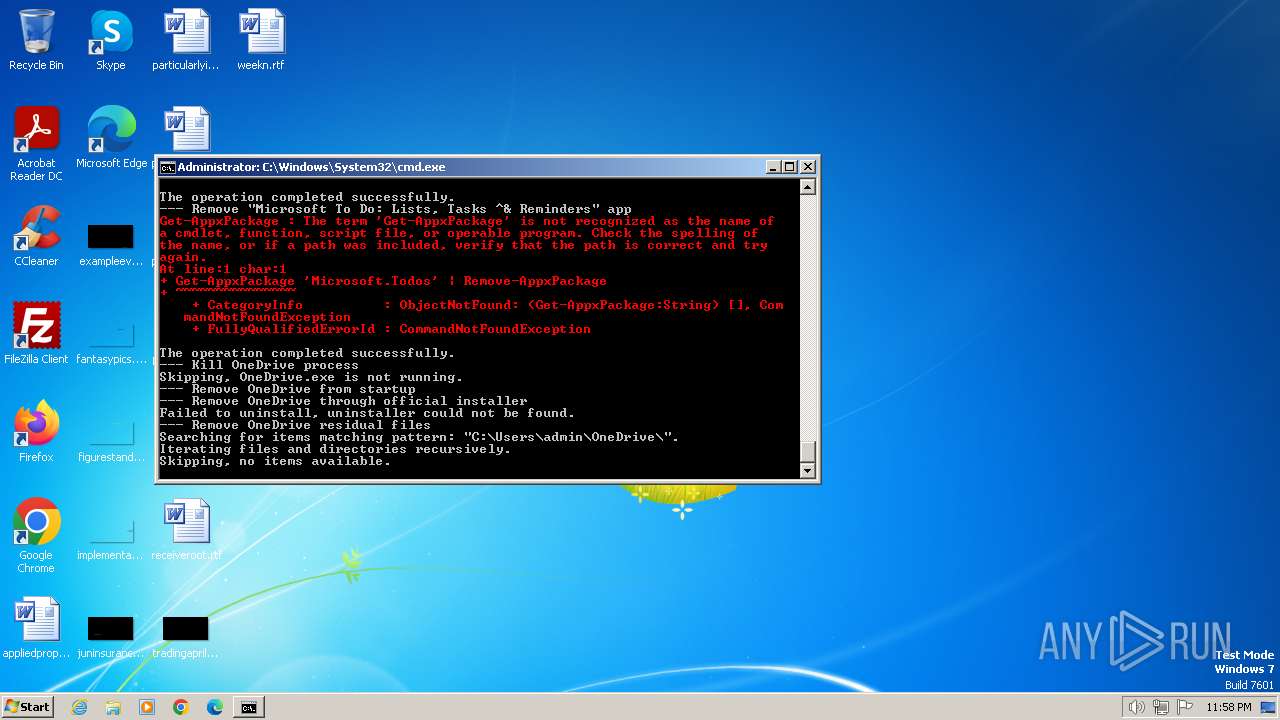
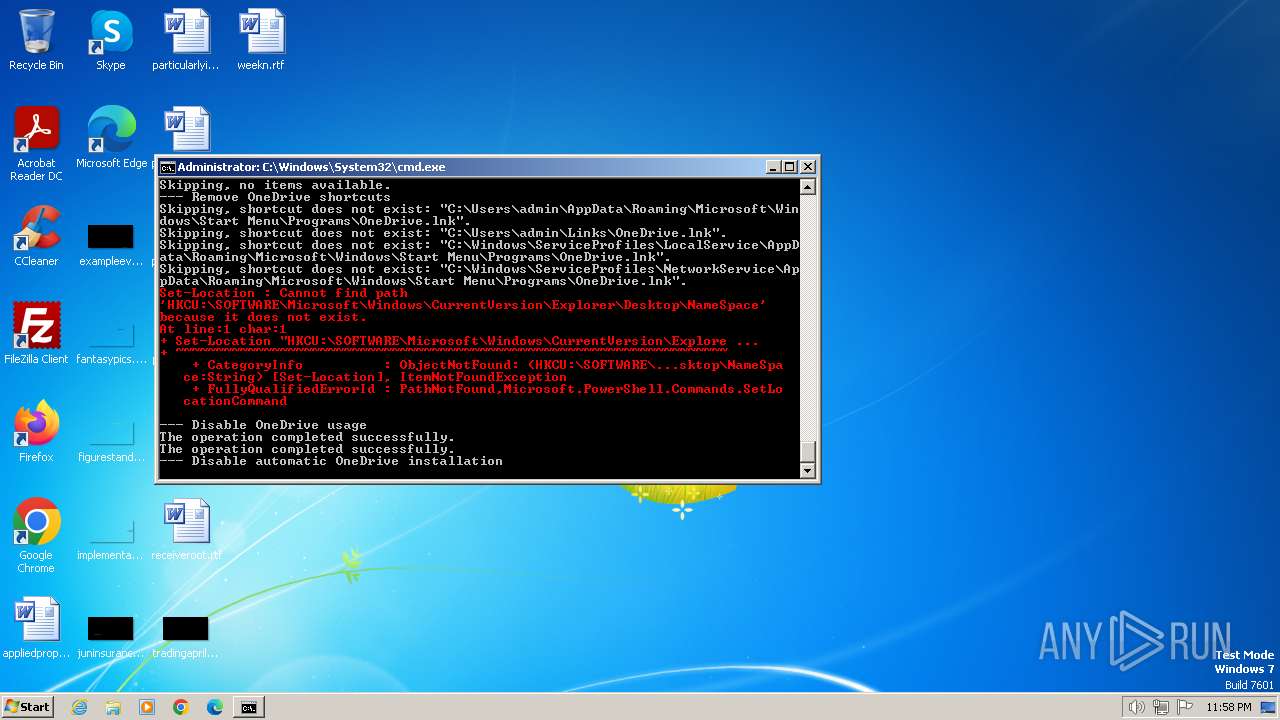
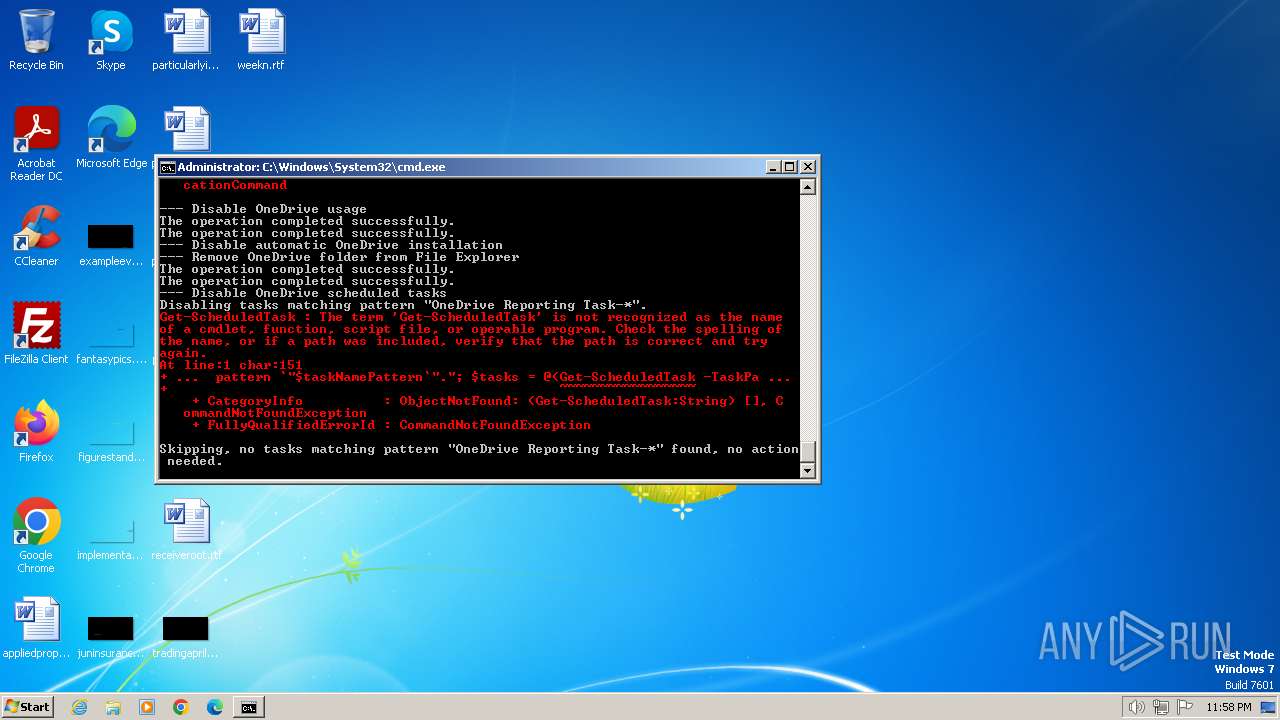
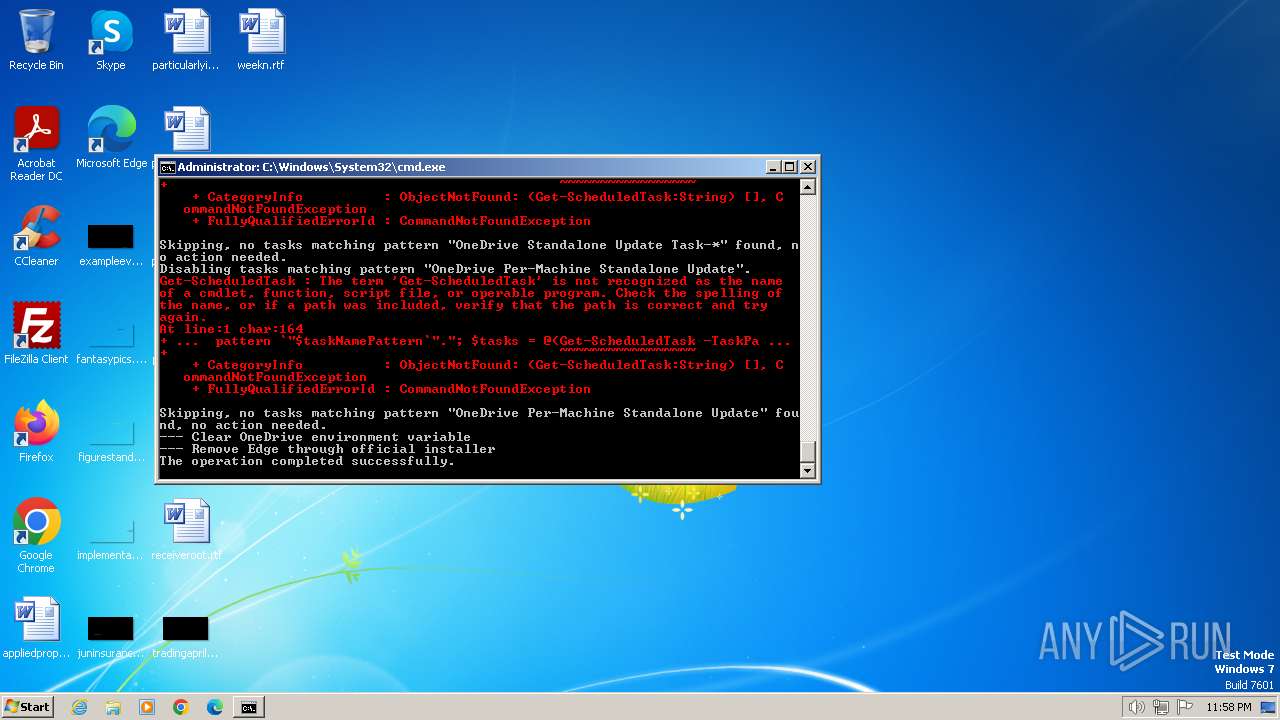
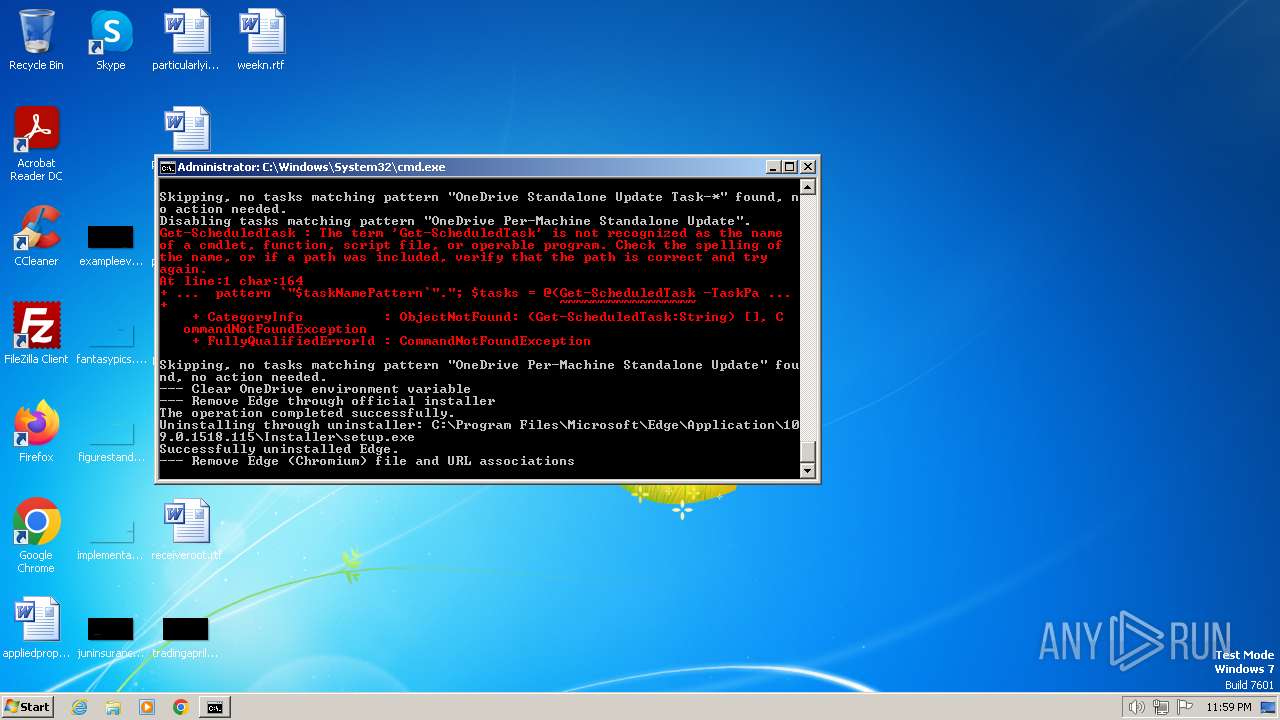
| File name: | privacy-script.bat |
| Full analysis: | https://app.any.run/tasks/fb01dbf5-3d78-47e4-bb11-f53cc175b18a |
| Verdict: | Malicious activity |
| Threats: | GuLoader is an advanced downloader written in shellcode. It’s used by criminals to distribute other malware, notably trojans, on a large scale. It’s infamous for using anti-detection and anti-analysis capabilities. |
| Analysis date: | January 17, 2024, 23:58:14 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | text/x-msdos-batch |
| File info: | DOS batch file, UTF-8 Unicode text, with very long lines, with CRLF line terminators |
| MD5: | 7D641533D3FED9861E124C75463CB549 |
| SHA1: | E968847928639D05B0BC1FA3D3877CEF11765AA8 |
| SHA256: | 29129CCE6FE13D915B351078070C193F97302DD2DB949B74F9398C66C8AE98FC |
| SSDEEP: | 1536:4YYEF4HjXoafkU4aAlYZkSFQ46+FpgNqvDbfjyqXPFL0r5k:Iyoh |
MALICIOUS
Changes powershell execution policy (Unrestricted)
- cmd.exe (PID: 1864)
Detected an obfuscated command line used with Guloader
- powershell.exe (PID: 3756)
- powershell.exe (PID: 2020)
- powershell.exe (PID: 2420)
- powershell.exe (PID: 1796)
Actions looks like stealing of personal data
- setup.exe (PID: 1484)
Drops the executable file immediately after the start
- setup.exe (PID: 1484)
SUSPICIOUS
Reads the Internet Settings
- powershell.exe (PID: 392)
- powershell.exe (PID: 1972)
- powershell.exe (PID: 2192)
- powershell.exe (PID: 2660)
- powershell.exe (PID: 2060)
- powershell.exe (PID: 2540)
- powershell.exe (PID: 2988)
- powershell.exe (PID: 2652)
- powershell.exe (PID: 3000)
- powershell.exe (PID: 3244)
- powershell.exe (PID: 664)
- powershell.exe (PID: 1736)
- powershell.exe (PID: 2692)
- powershell.exe (PID: 3416)
- powershell.exe (PID: 3652)
- powershell.exe (PID: 4076)
- powershell.exe (PID: 864)
- powershell.exe (PID: 1696)
- powershell.exe (PID: 3804)
- powershell.exe (PID: 844)
- powershell.exe (PID: 1560)
- powershell.exe (PID: 1496)
- powershell.exe (PID: 1924)
- powershell.exe (PID: 3064)
- powershell.exe (PID: 2112)
- powershell.exe (PID: 1268)
- powershell.exe (PID: 2524)
- powershell.exe (PID: 2364)
- powershell.exe (PID: 784)
- powershell.exe (PID: 3216)
- powershell.exe (PID: 3096)
- powershell.exe (PID: 3276)
- powershell.exe (PID: 3532)
- powershell.exe (PID: 3680)
- powershell.exe (PID: 3024)
- powershell.exe (PID: 2584)
- powershell.exe (PID: 2800)
- powershell.exe (PID: 2960)
- powershell.exe (PID: 2500)
- powershell.exe (PID: 1528)
- MicrosoftEdgeUpdate.exe (PID: 3072)
- MicrosoftEdgeUpdate.exe (PID: 2364)
- MicrosoftEdgeUpdate.exe (PID: 3152)
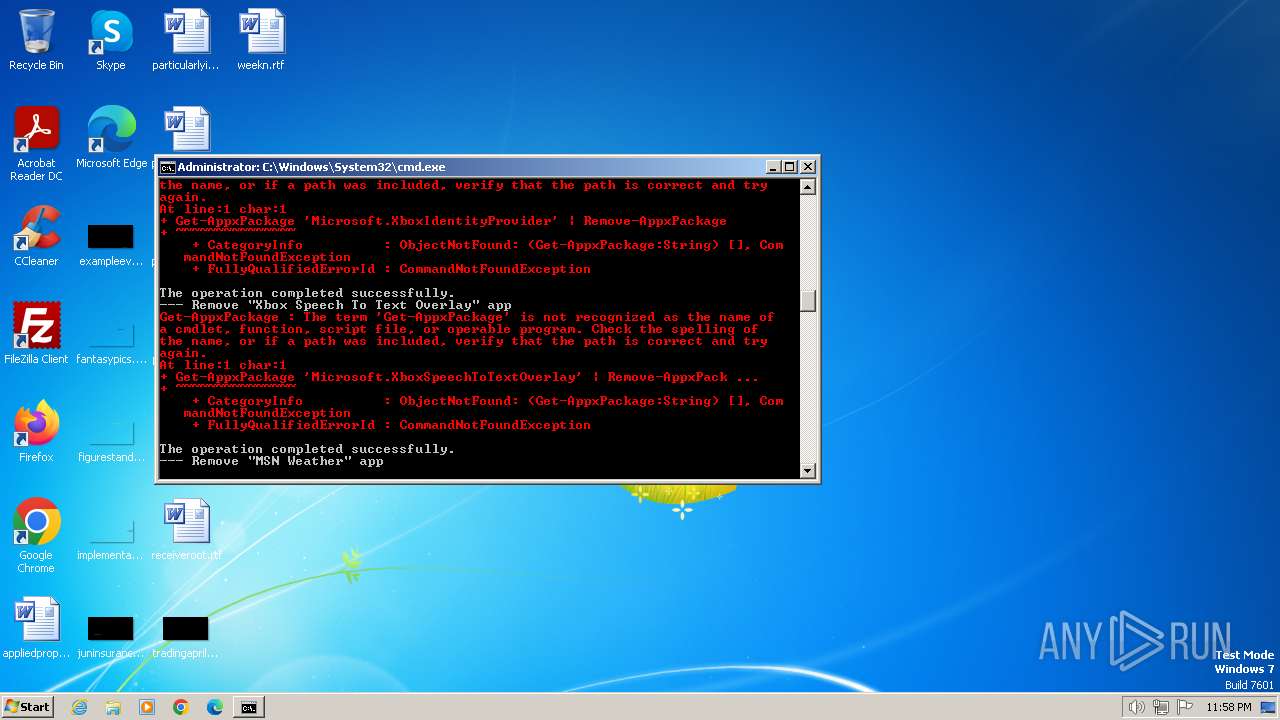
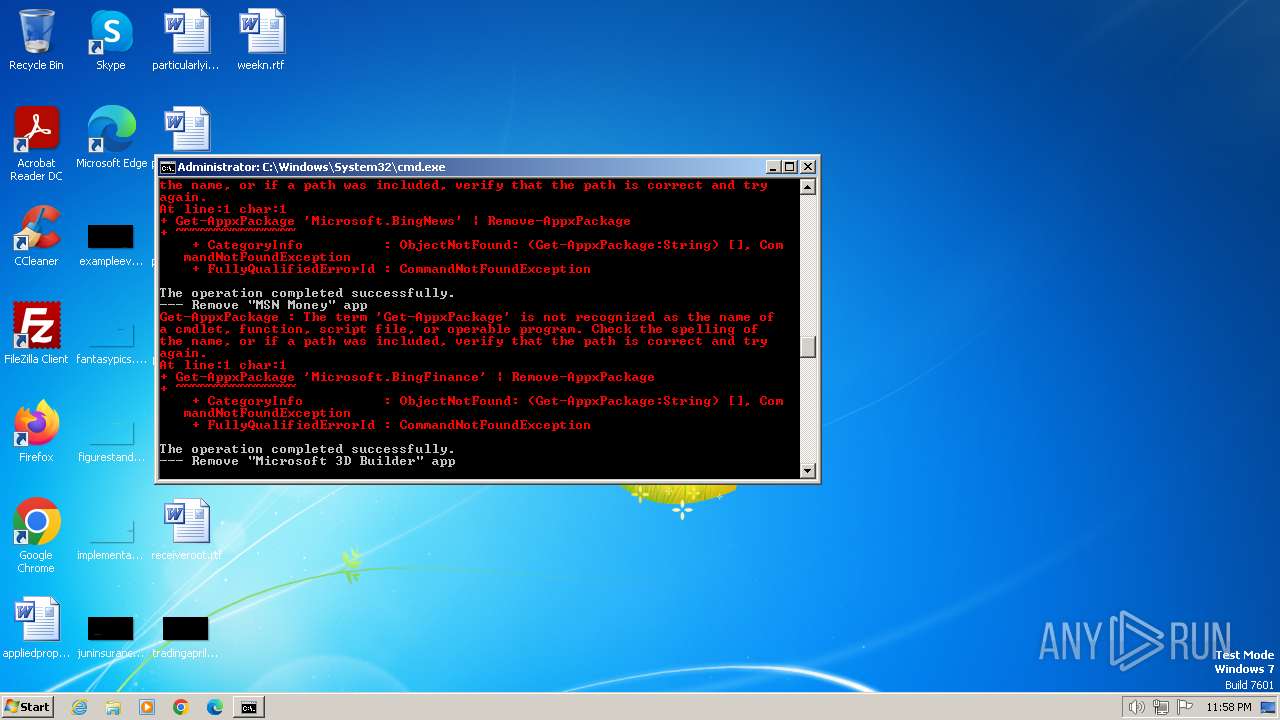
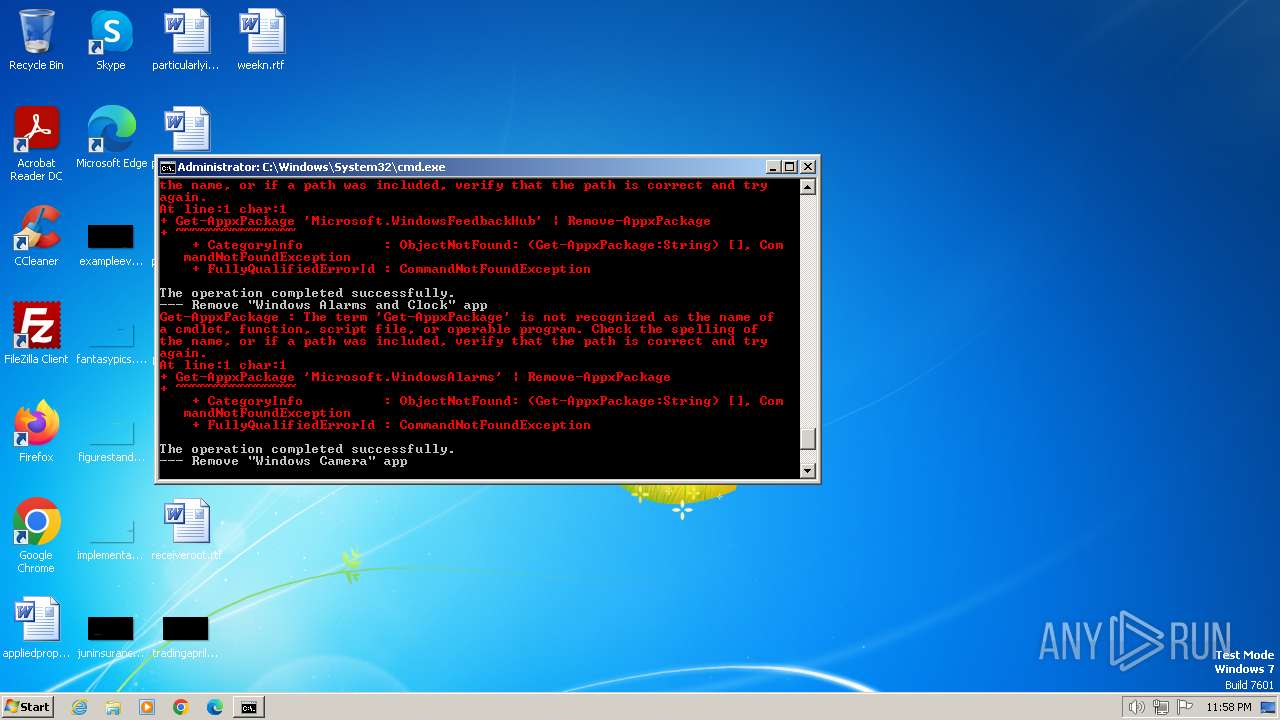
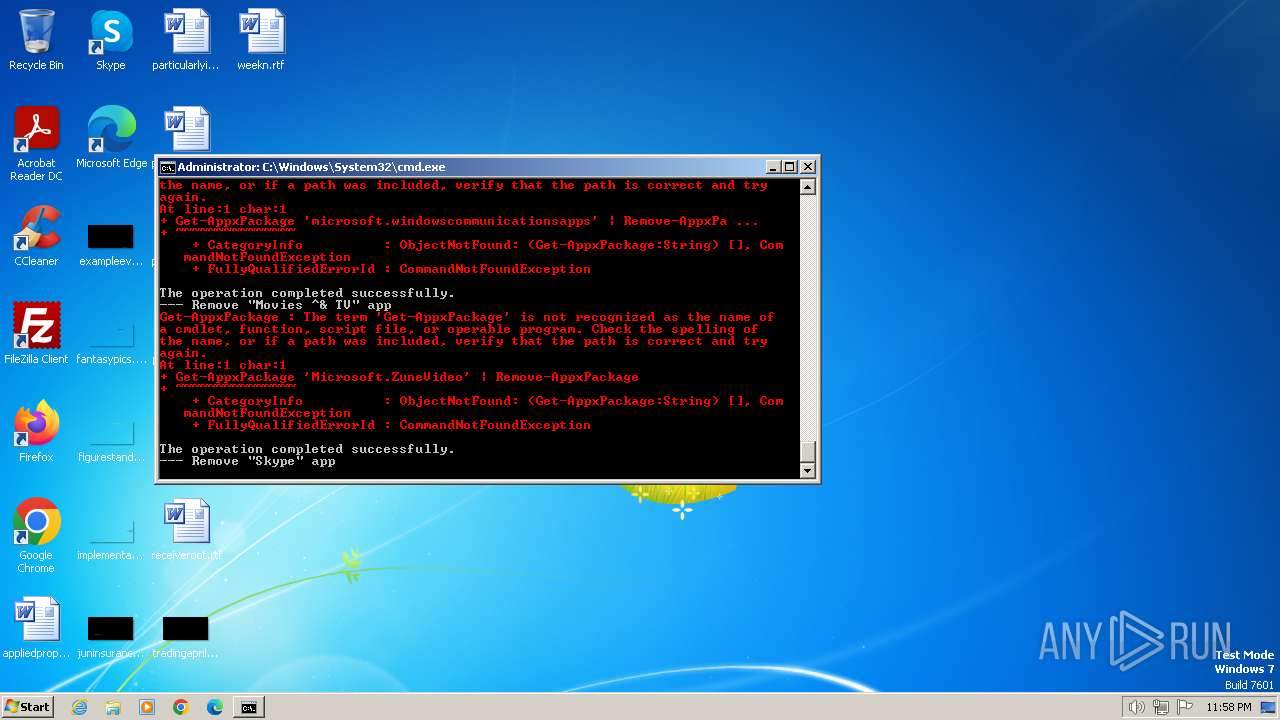
Executing commands from a ".bat" file
- powershell.exe (PID: 392)
Starts CMD.EXE for commands execution
- powershell.exe (PID: 392)
- powershell.exe (PID: 2020)
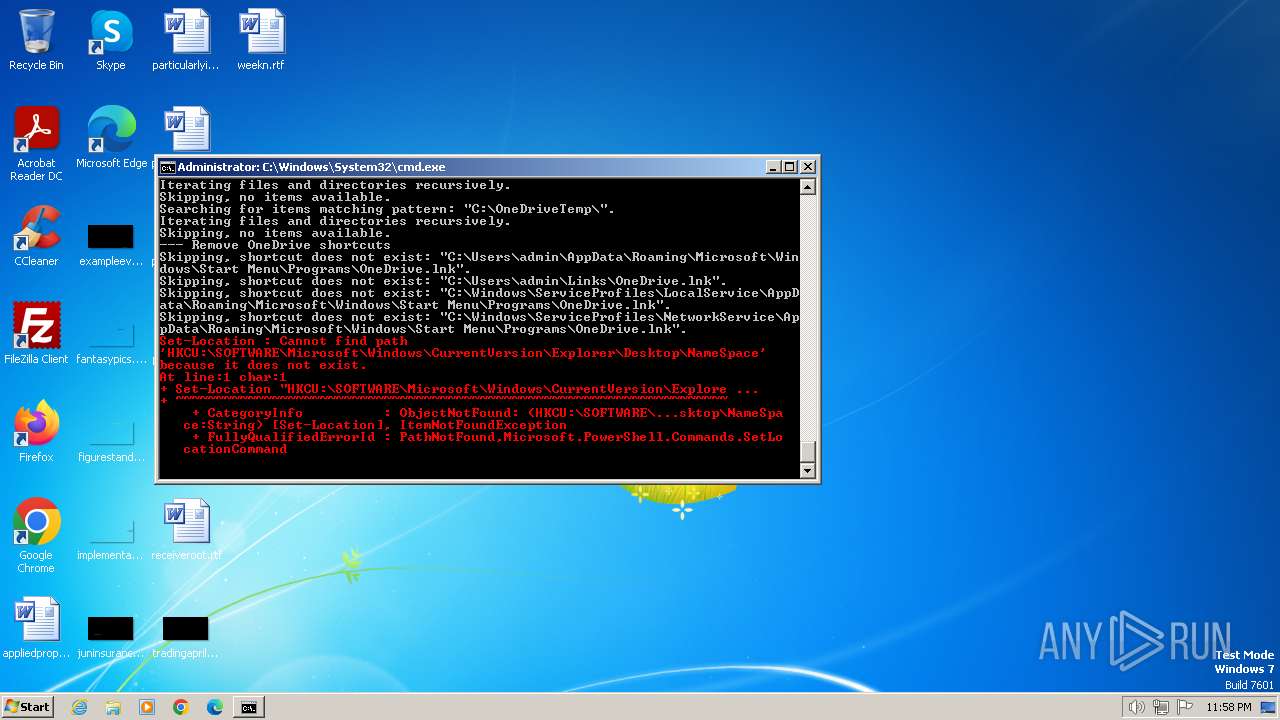
Uses REG/REGEDIT.EXE to modify registry
- cmd.exe (PID: 1864)
- powershell.exe (PID: 2468)
Using PowerShell to operate with local accounts
- powershell.exe (PID: 1736)
- powershell.exe (PID: 2192)
- powershell.exe (PID: 1972)
- powershell.exe (PID: 2060)
- powershell.exe (PID: 2692)
- powershell.exe (PID: 664)
- powershell.exe (PID: 2660)
- powershell.exe (PID: 3064)
- powershell.exe (PID: 2652)
- powershell.exe (PID: 3000)
- powershell.exe (PID: 2988)
- powershell.exe (PID: 3244)
- powershell.exe (PID: 4076)
- powershell.exe (PID: 3652)
- powershell.exe (PID: 3416)
- powershell.exe (PID: 3804)
- powershell.exe (PID: 1696)
- powershell.exe (PID: 864)
- powershell.exe (PID: 1496)
- powershell.exe (PID: 844)
- powershell.exe (PID: 1560)
- powershell.exe (PID: 1924)
- powershell.exe (PID: 2540)
- powershell.exe (PID: 1268)
- powershell.exe (PID: 2112)
- powershell.exe (PID: 2364)
- powershell.exe (PID: 2524)
- powershell.exe (PID: 1528)
- powershell.exe (PID: 784)
- powershell.exe (PID: 3024)
- powershell.exe (PID: 3216)
- powershell.exe (PID: 3096)
- powershell.exe (PID: 3276)
- powershell.exe (PID: 3680)
- powershell.exe (PID: 3532)
- powershell.exe (PID: 2800)
- powershell.exe (PID: 2584)
- powershell.exe (PID: 2960)
Starts POWERSHELL.EXE for commands execution
- cmd.exe (PID: 128)
- cmd.exe (PID: 1864)
Get information on the list of running processes
- cmd.exe (PID: 1864)
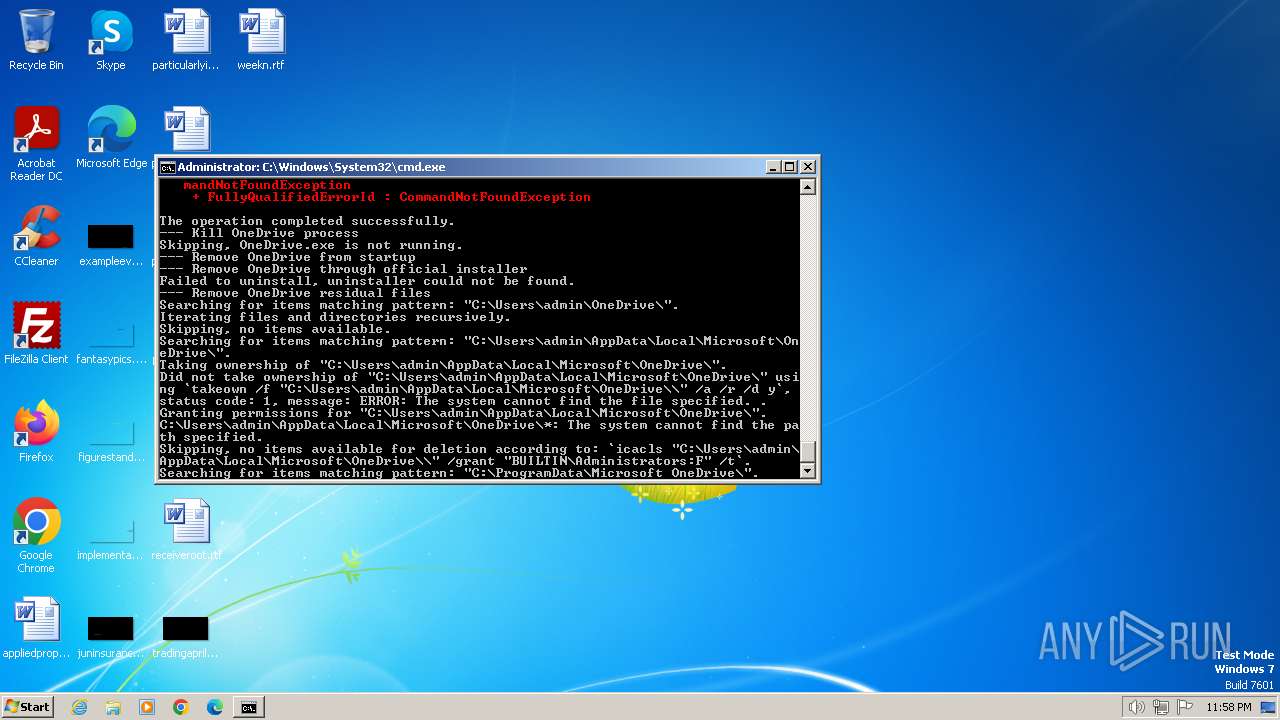
Takes ownership (TAKEOWN.EXE)
- cmd.exe (PID: 2204)
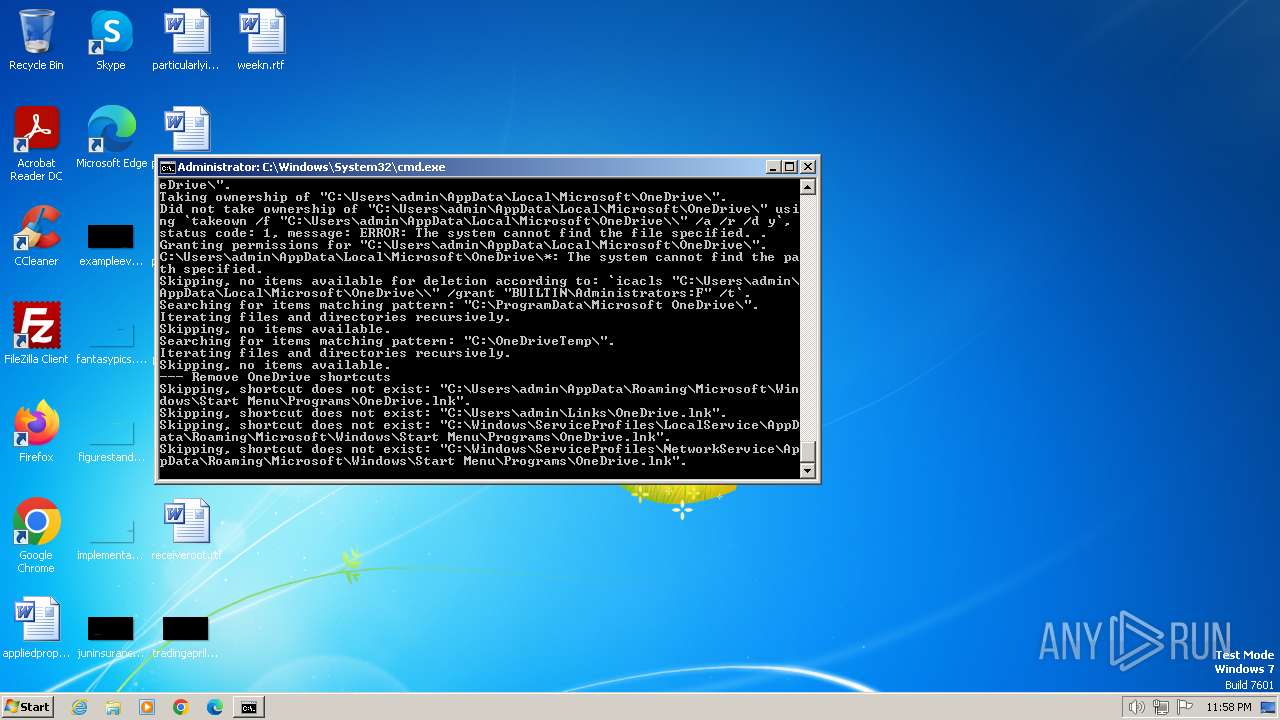
Uses ICACLS.EXE to modify access control lists
- cmd.exe (PID: 2080)
Powershell scripting: start process
- cmd.exe (PID: 1864)
Process drops legitimate windows executable
- setup.exe (PID: 1484)
- MicrosoftEdgeUpdate.exe (PID: 3072)
Executable content was dropped or overwritten
- setup.exe (PID: 1484)
Checks Windows Trust Settings
- MicrosoftEdgeUpdate.exe (PID: 2364)
- MicrosoftEdgeUpdate.exe (PID: 3072)
- MicrosoftEdgeUpdate.exe (PID: 3152)
Application launched itself
- MicrosoftEdgeUpdate.exe (PID: 3072)
Reads settings of System Certificates
- MicrosoftEdgeUpdate.exe (PID: 2364)
- MicrosoftEdgeUpdate.exe (PID: 3072)
- MicrosoftEdgeUpdate.exe (PID: 3152)
Reads security settings of Internet Explorer
- MicrosoftEdgeUpdate.exe (PID: 2364)
- MicrosoftEdgeUpdate.exe (PID: 3152)
- MicrosoftEdgeUpdate.exe (PID: 3072)
Probably obfuscated PowerShell command line is found
- cmd.exe (PID: 1864)
INFO
Manual execution by a user
- wmpnscfg.exe (PID: 3420)
- explorer.exe (PID: 956)
Reads the computer name
- wmpnscfg.exe (PID: 3420)
- setup.exe (PID: 1484)
- MicrosoftEdgeUpdate.exe (PID: 2364)
- MicrosoftEdgeUpdate.exe (PID: 3152)
- MicrosoftEdgeUpdate.exe (PID: 3168)
- MicrosoftEdgeUpdate.exe (PID: 3172)
- MicrosoftEdgeUpdate.exe (PID: 3072)
Checks supported languages
- wmpnscfg.exe (PID: 3420)
- setup.exe (PID: 1484)
- MicrosoftEdgeUpdate.exe (PID: 3072)
- MicrosoftEdgeUpdate.exe (PID: 2364)
- MicrosoftEdgeUpdate.exe (PID: 3168)
- MicrosoftEdgeUpdate.exe (PID: 3172)
- MicrosoftEdgeUpdate.exe (PID: 3152)
Reads the machine GUID from the registry
- setup.exe (PID: 1484)
Create files in a temporary directory
- setup.exe (PID: 1484)
- MicrosoftEdgeUpdate.exe (PID: 3072)
- MicrosoftEdgeUpdate.exe (PID: 2364)
- MicrosoftEdgeUpdate.exe (PID: 3152)
Checks proxy server information
- MicrosoftEdgeUpdate.exe (PID: 3072)
- MicrosoftEdgeUpdate.exe (PID: 2364)
- MicrosoftEdgeUpdate.exe (PID: 3152)
Reads Environment values
- MicrosoftEdgeUpdate.exe (PID: 2364)
- MicrosoftEdgeUpdate.exe (PID: 3152)
- MicrosoftEdgeUpdate.exe (PID: 3072)
Creates files or folders in the user directory
- MicrosoftEdgeUpdate.exe (PID: 3072)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
183
Monitored processes
140
Malicious processes
12
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 128 | C:\Windows\system32\cmd.exe /c ""C:\Users\admin\AppData\Local\Temp\privacy-script.bat" " | C:\Windows\System32\cmd.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 324 | icacls "C:\Users\admin\AppData\Local\Microsoft\OneDrive\\" /grant "BUILTIN\Administrators:F" /t | C:\Windows\System32\icacls.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Exit code: 3 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 392 | PowerShell Start -Verb RunAs '"C:\Users\admin\AppData\Local\Temp\privacy-script.bat"' | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 10.0.14409.1005 (rs1_srvoob.161208-1155) Modules
| |||||||||||||||
| 392 | reg add "HKLM\Software\Microsoft\Windows\CurrentVersion\Policies\Explorer" /v "HideSCAMeetNow" /t REG_DWORD /d 1 /f | C:\Windows\System32\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Console Tool Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 548 | reg delete "HKCR\.mht\OpenWithProgIds" /v "MSEdgeMHT" /f | C:\Windows\System32\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Console Tool Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 552 | reg add "HKCR\Wow6432Node\{018D5C66-4533-4307-9B53-224DE2ED1FE6}" /v "System.IsPinnedToNameSpaceTree" /d "0" /t REG_DWORD /f | C:\Windows\System32\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Console Tool Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 604 | reg add "HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Appx\AppxAllUserStore\Deprovisioned\microsoft.windowscommunicationsapps_8wekyb3d8bbwe" /f | C:\Windows\System32\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Console Tool Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 664 | PowerShell -ExecutionPolicy Unrestricted -Command "Get-AppxPackage 'Microsoft.XboxApp' | Remove-AppxPackage" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows PowerShell Exit code: 1 Version: 10.0.14409.1005 (rs1_srvoob.161208-1155) Modules
| |||||||||||||||
| 784 | PowerShell -ExecutionPolicy Unrestricted -Command "Get-AppxPackage 'Microsoft.Print3D' | Remove-AppxPackage" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows PowerShell Exit code: 1 Version: 10.0.14409.1005 (rs1_srvoob.161208-1155) Modules
| |||||||||||||||
| 844 | reg add "HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Appx\AppxAllUserStore\Deprovisioned\Microsoft.WindowsPhone_8wekyb3d8bbwe" /f | C:\Windows\System32\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Console Tool Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
44 609
Read events
43 731
Write events
450
Delete events
428
Modification events
| (PID) Process: | (392) powershell.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (392) powershell.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (392) powershell.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (392) powershell.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (1972) powershell.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (1972) powershell.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (1972) powershell.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (1972) powershell.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (1736) powershell.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (1736) powershell.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
Executable files
3
Suspicious files
106
Text files
3
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 392 | powershell.exe | C:\Users\admin\AppData\Local\Temp\rgk0a0v2.v5t.psm1 | binary | |
MD5:C4CA4238A0B923820DCC509A6F75849B | SHA256:— | |||
| 1736 | powershell.exe | C:\Users\admin\AppData\Local\Temp\oj0b0mgv.jqz.ps1 | binary | |
MD5:C4CA4238A0B923820DCC509A6F75849B | SHA256:— | |||
| 392 | powershell.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\PowerShell\StartupProfileData-NonInteractive | binary | |
MD5:446DD1CF97EABA21CF14D03AEBC79F27 | SHA256:A7DE5177C68A64BD48B36D49E2853799F4EBCFA8E4761F7CC472F333DC5F65CF | |||
| 392 | powershell.exe | C:\Users\admin\AppData\Local\Temp\jwrijadc.nds.ps1 | binary | |
MD5:C4CA4238A0B923820DCC509A6F75849B | SHA256:— | |||
| 2060 | powershell.exe | C:\Users\admin\AppData\Local\Temp\kcv2tmqq.m0t.ps1 | binary | |
MD5:C4CA4238A0B923820DCC509A6F75849B | SHA256:— | |||
| 2692 | powershell.exe | C:\Users\admin\AppData\Local\Temp\o3gf5u2r.w1m.ps1 | binary | |
MD5:C4CA4238A0B923820DCC509A6F75849B | SHA256:— | |||
| 664 | powershell.exe | C:\Users\admin\AppData\Local\Temp\tlhmifpe.4ax.ps1 | binary | |
MD5:C4CA4238A0B923820DCC509A6F75849B | SHA256:— | |||
| 2192 | powershell.exe | C:\Users\admin\AppData\Local\Temp\fboou0qo.yju.psm1 | binary | |
MD5:C4CA4238A0B923820DCC509A6F75849B | SHA256:— | |||
| 2692 | powershell.exe | C:\Users\admin\AppData\Local\Temp\xyndgnqt.pld.psm1 | binary | |
MD5:C4CA4238A0B923820DCC509A6F75849B | SHA256:— | |||
| 2660 | powershell.exe | C:\Users\admin\AppData\Local\Temp\e2wu2k50.qpj.ps1 | binary | |
MD5:C4CA4238A0B923820DCC509A6F75849B | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
3
TCP/UDP connections
11
DNS requests
5
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3072 | MicrosoftEdgeUpdate.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | binary | 471 b | unknown |
2364 | MicrosoftEdgeUpdate.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | binary | 471 b | unknown |
2364 | MicrosoftEdgeUpdate.exe | GET | 200 | 184.24.77.202:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?4797b76144f31d94 | unknown | compressed | 4.66 Kb | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2364 | MicrosoftEdgeUpdate.exe | 13.107.42.16:443 | config.edge.skype.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
2364 | MicrosoftEdgeUpdate.exe | 20.44.10.122:443 | self.events.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
3072 | MicrosoftEdgeUpdate.exe | 20.44.10.122:443 | self.events.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
2364 | MicrosoftEdgeUpdate.exe | 184.24.77.202:80 | ctldl.windowsupdate.com | Akamai International B.V. | DE | unknown |
3072 | MicrosoftEdgeUpdate.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
2364 | MicrosoftEdgeUpdate.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
3152 | MicrosoftEdgeUpdate.exe | 20.44.10.122:443 | self.events.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
config.edge.skype.com |
| whitelisted |
self.events.data.microsoft.com |
| whitelisted |
ctldl.windowsupdate.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |