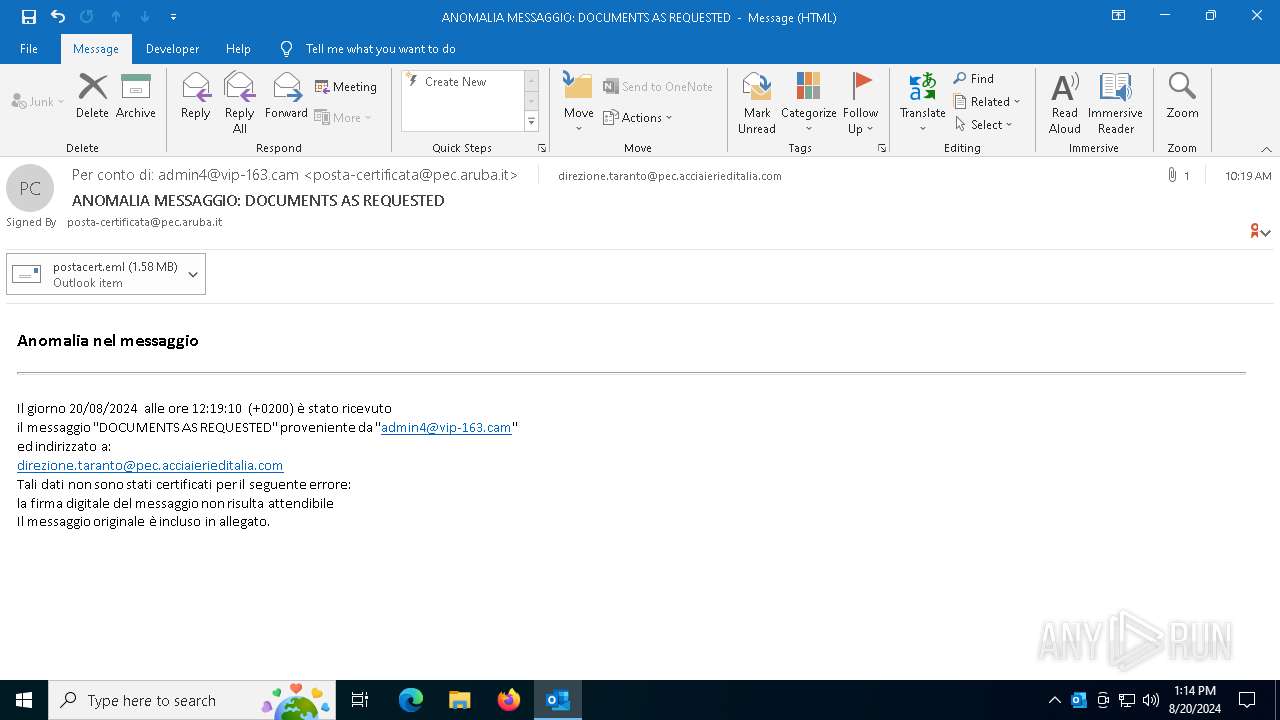
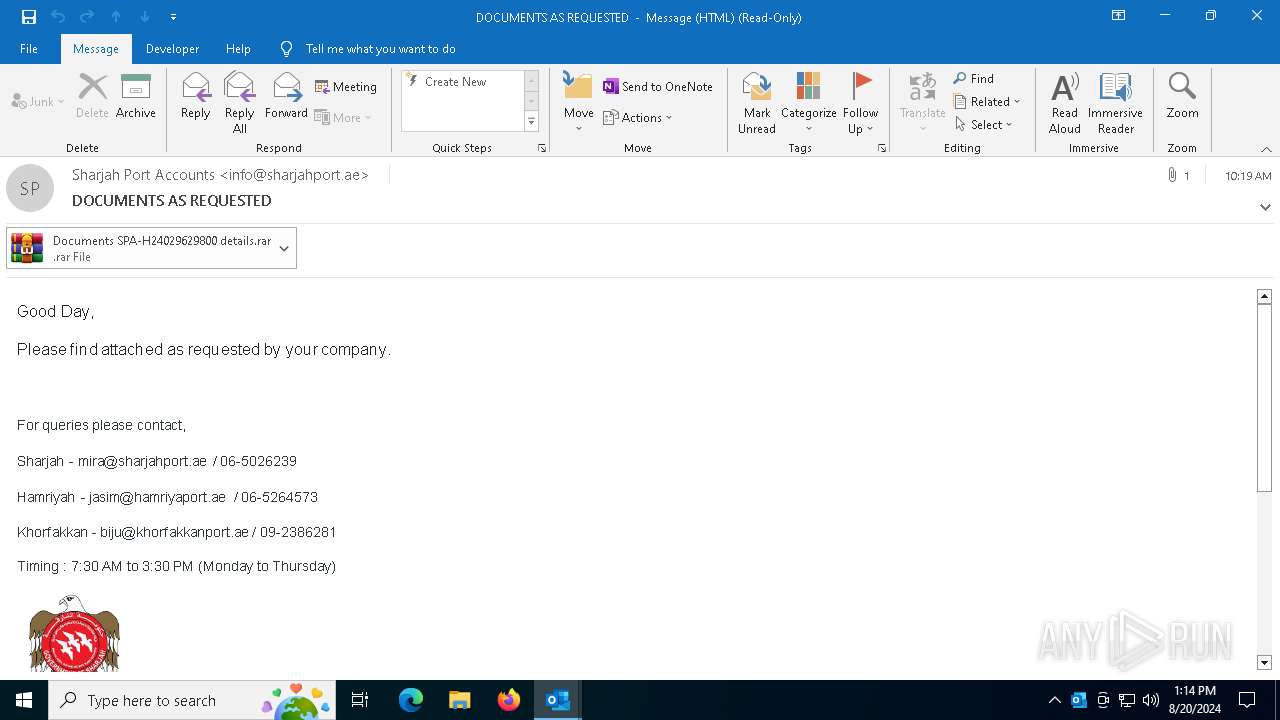
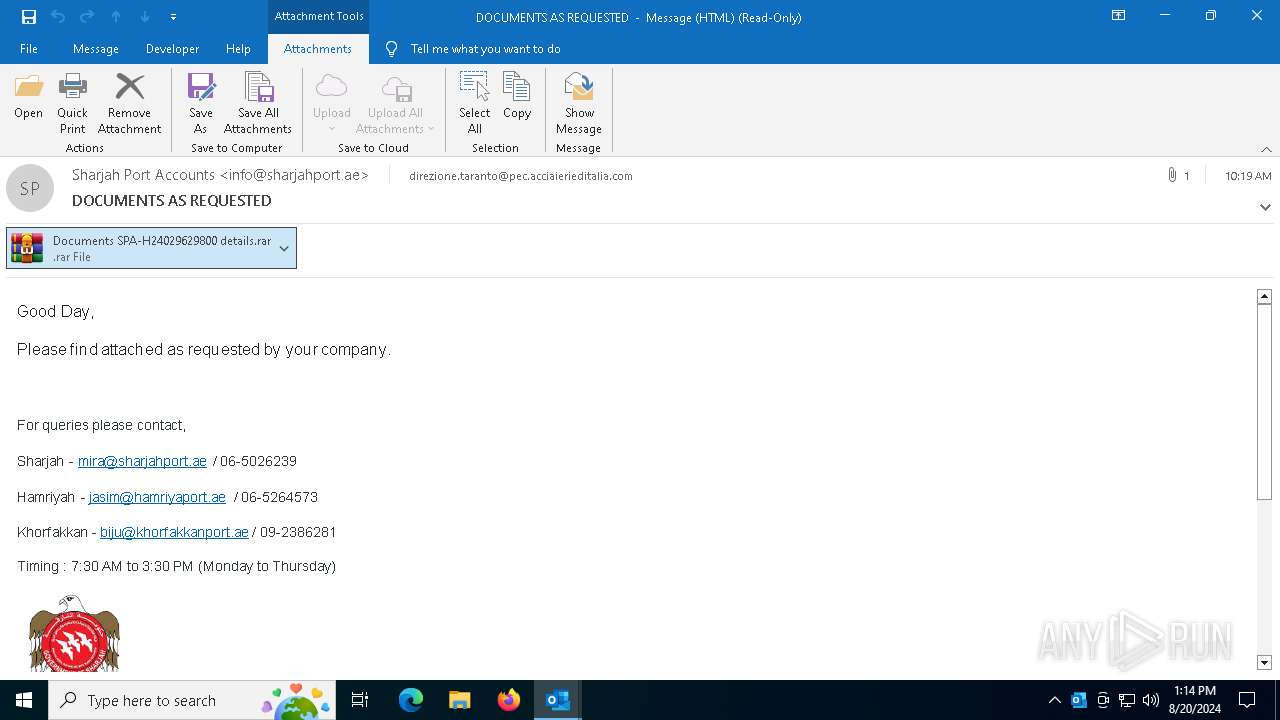
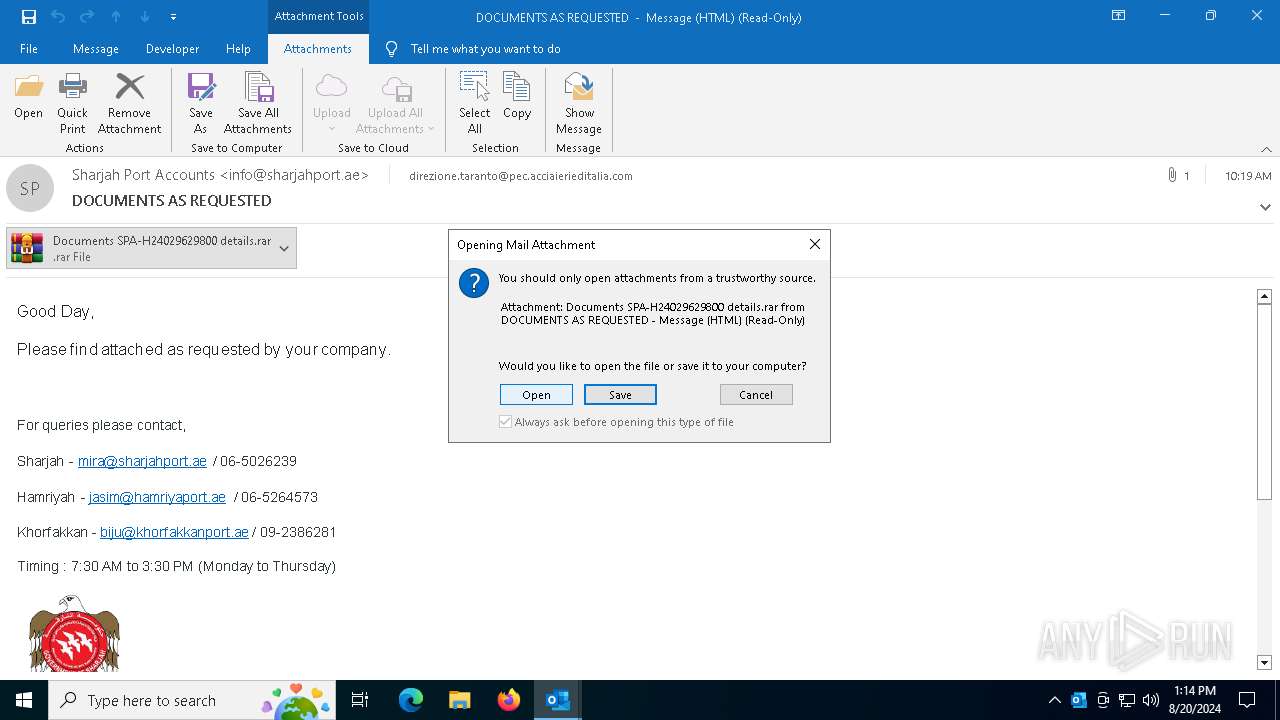
| File name: | DOCUMENTS AS REQUESTED.eml |
| Full analysis: | https://app.any.run/tasks/dcfa63de-f795-42ff-9f71-6e022310867c |
| Verdict: | Malicious activity |
| Threats: | Agent Tesla is spyware that collects information about the actions of its victims by recording keystrokes and user interactions. It is falsely marketed as a legitimate software on the dedicated website where this malware is sold. |
| Analysis date: | August 20, 2024, 13:14:06 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | message/rfc822 |
| File info: | SMTP mail, ASCII text, with CRLF line terminators |
| MD5: | 13FF0CE463AF1F264AB0E2488B81B8FF |
| SHA1: | 9BBF9BAA574B7640B69787C7D3BE0641EF1AFAC5 |
| SHA256: | 2861025125BAE69F557047C48BCD25159F83CE704689B9A490209241BDD3B758 |
| SSDEEP: | 49152:GFF9h1nMr6ld/HrxPtIxbNNJMULC8rir6TgPK:n |
MALICIOUS
Actions looks like stealing of personal data
- CasPol.exe (PID: 6284)
- InstallUtil.exe (PID: 4296)
- jsc.exe (PID: 1104)
Steals credentials from Web Browsers
- CasPol.exe (PID: 6284)
- InstallUtil.exe (PID: 4296)
- jsc.exe (PID: 1104)
AGENTTESLA has been detected (SURICATA)
- CasPol.exe (PID: 6284)
- InstallUtil.exe (PID: 4296)
Scans artifacts that could help determine the target
- CasPol.exe (PID: 6284)
- InstallUtil.exe (PID: 4296)
- jsc.exe (PID: 1104)
AGENTTESLA has been detected (YARA)
- CasPol.exe (PID: 6284)
- InstallUtil.exe (PID: 4296)
Connects to the CnC server
- CasPol.exe (PID: 6284)
- InstallUtil.exe (PID: 4296)
Stealers network behavior
- CasPol.exe (PID: 6284)
- InstallUtil.exe (PID: 4296)
SUSPICIOUS
Reads security settings of Internet Explorer
- WinRAR.exe (PID: 6580)
- CasPol.exe (PID: 6284)
Process drops legitimate windows executable
- OUTLOOK.EXE (PID: 6692)
- WinRAR.exe (PID: 6580)
The process drops C-runtime libraries
- OUTLOOK.EXE (PID: 6692)
Drops the executable file immediately after the start
- OUTLOOK.EXE (PID: 6692)
Checks for external IP
- CasPol.exe (PID: 6284)
- InstallUtil.exe (PID: 4296)
- jsc.exe (PID: 1104)
Connects to SMTP port
- CasPol.exe (PID: 6284)
- InstallUtil.exe (PID: 4296)
INFO
The process uses the downloaded file
- OUTLOOK.EXE (PID: 6692)
- WinRAR.exe (PID: 6580)
Reads the software policy settings
- CasPol.exe (PID: 6284)
- InstallUtil.exe (PID: 4296)
- jsc.exe (PID: 1104)
Reads the computer name
- CasPol.exe (PID: 6284)
- aDocuments SPA-H24029629800 details.exe (PID: 7036)
- InstallUtil.exe (PID: 4296)
- aDocuments SPA-H24029629800 details.exe (PID: 2080)
- aDocuments SPA-H24029629800 details.exe (PID: 7136)
- jsc.exe (PID: 1104)
Disables trace logs
- CasPol.exe (PID: 6284)
- InstallUtil.exe (PID: 4296)
- jsc.exe (PID: 1104)
Reads Environment values
- CasPol.exe (PID: 6284)
- InstallUtil.exe (PID: 4296)
- jsc.exe (PID: 1104)
Reads the machine GUID from the registry
- CasPol.exe (PID: 6284)
- InstallUtil.exe (PID: 4296)
- jsc.exe (PID: 1104)
Checks proxy server information
- CasPol.exe (PID: 6284)
- InstallUtil.exe (PID: 4296)
- jsc.exe (PID: 1104)
Reads Microsoft Office registry keys
- CasPol.exe (PID: 6284)
- InstallUtil.exe (PID: 4296)
- jsc.exe (PID: 1104)
Manual execution by a user
- aDocuments SPA-H24029629800 details.exe (PID: 7036)
- aDocuments SPA-H24029629800 details.exe (PID: 2080)
Checks supported languages
- InstallUtil.exe (PID: 4296)
- aDocuments SPA-H24029629800 details.exe (PID: 7036)
- aDocuments SPA-H24029629800 details.exe (PID: 7136)
- CasPol.exe (PID: 6284)
- aDocuments SPA-H24029629800 details.exe (PID: 2080)
- jsc.exe (PID: 1104)
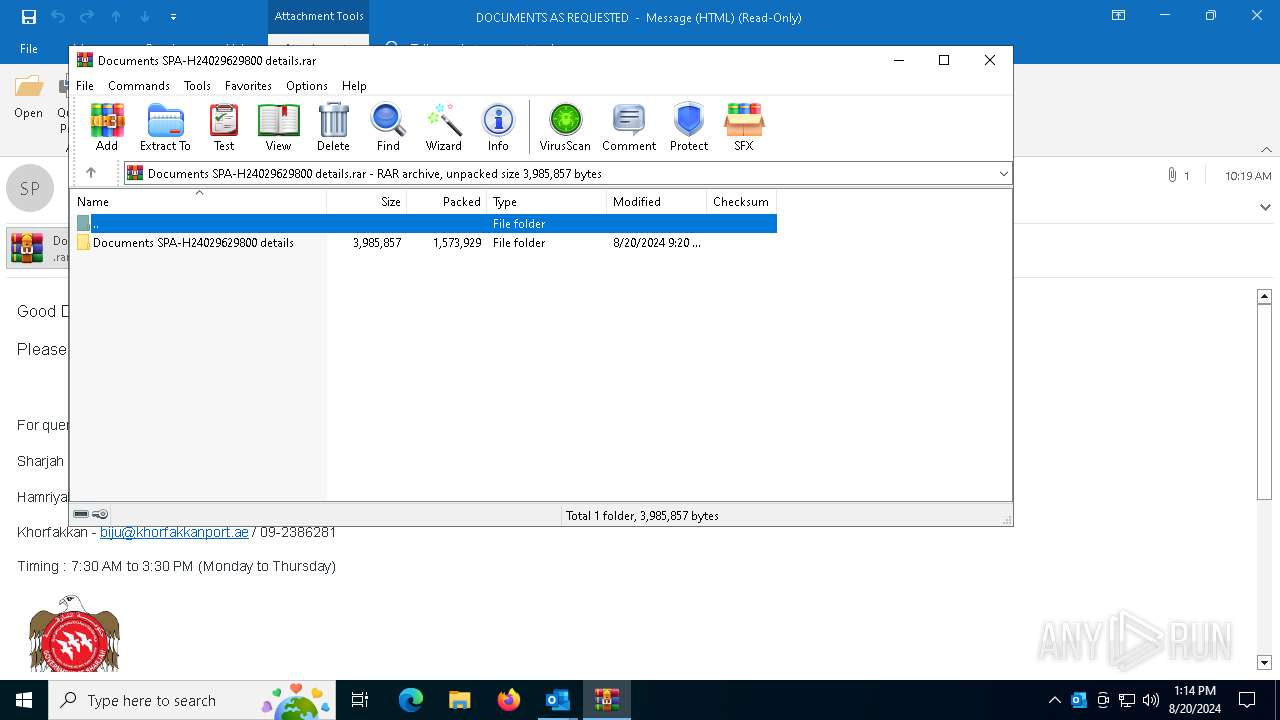
Executable content was dropped or overwritten
- WinRAR.exe (PID: 6580)
Attempt to transmit an email message via SMTP
- InstallUtil.exe (PID: 4296)
- CasPol.exe (PID: 6284)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
AgentTesla
(PID) Process(6284) CasPol.exe
Protocolsmtp
Host162.254.34.31
Port587
Usernamesendxsenses@vetrys.shop
PasswordM992uew1mw6Z
(PID) Process(4296) InstallUtil.exe
Protocolsmtp
Host162.254.34.31
Port587
Usernamesendxsenses@vetrys.shop
PasswordM992uew1mw6Z
TRiD
| .eml | | | E-Mail message (Var. 1) (100) |
|---|
Total processes
144
Monitored processes
13
Malicious processes
7
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1104 | "C:\Windows\Microsoft.NET\Framework\v4.0.30319\jsc.exe" | C:\Windows\Microsoft.NET\Framework\v4.0.30319\jsc.exe | aDocuments SPA-H24029629800 details.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: jsc.exe Version: 14.8.9037.0 built by: NET481REL1 Modules
| |||||||||||||||
| 1640 | C:\WINDOWS\System32\rundll32.exe C:\WINDOWS\System32\shell32.dll,SHCreateLocalServerRunDll {9aa46009-3ce0-458a-a354-715610a075e6} -Embedding | C:\Windows\System32\rundll32.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2080 | "C:\Users\admin\Downloads\Documents SPA-H24029629800 details\aDocuments SPA-H24029629800 details.exe" | C:\Users\admin\Downloads\Documents SPA-H24029629800 details\aDocuments SPA-H24029629800 details.exe | — | explorer.exe | |||||||||||
User: admin Company: JetBrains s.r.o. Integrity Level: MEDIUM Description: OpenJDK Platform binary Exit code: 4294967295 Version: 17.0.11.0 Modules
| |||||||||||||||
| 3272 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | aDocuments SPA-H24029629800 details.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4296 | "C:\Windows\Microsoft.NET\Framework\v4.0.30319\installutil.exe" | C:\Windows\Microsoft.NET\Framework\v4.0.30319\InstallUtil.exe | aDocuments SPA-H24029629800 details.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: .NET Framework installation utility Version: 4.8.9037.0 built by: NET481REL1 Modules
AgentTesla(PID) Process(4296) InstallUtil.exe Protocolsmtp Host162.254.34.31 Port587 Usernamesendxsenses@vetrys.shop PasswordM992uew1mw6Z | |||||||||||||||
| 5740 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | aDocuments SPA-H24029629800 details.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6284 | "C:\Windows\Microsoft.NET\Framework\v4.0.30319\CasPol.exe" | C:\Windows\Microsoft.NET\Framework\v4.0.30319\CasPol.exe | aDocuments SPA-H24029629800 details.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft .NET Framework CAS Policy Manager Version: 4.8.9037.0 built by: NET481REL1 Modules
AgentTesla(PID) Process(6284) CasPol.exe Protocolsmtp Host162.254.34.31 Port587 Usernamesendxsenses@vetrys.shop PasswordM992uew1mw6Z | |||||||||||||||
| 6572 | "C:\Program Files\Microsoft Office\root\VFS\ProgramFilesCommonX64\Microsoft Shared\OFFICE16\ai.exe" "EF6C2C3C-2437-4596-AFBB-6318420D2FF0" "57476AB8-FE8E-4B98-BCF3-CF22B02F4D80" "6692" | C:\Program Files\Microsoft Office\root\VFS\ProgramFilesCommonX64\Microsoft Shared\OFFICE16\ai.exe | — | OUTLOOK.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Artificial Intelligence (AI) Host for the Microsoft® Windows® Operating System and Platform x64. Version: 0.12.2.0 Modules
| |||||||||||||||
| 6580 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\Content.Outlook\0X2ME8NR\Documents SPA-H24029629800 details.rar" | C:\Program Files\WinRAR\WinRAR.exe | OUTLOOK.EXE | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.91.0 Modules
| |||||||||||||||
| 6692 | "C:\Program Files\Microsoft Office\Root\Office16\OUTLOOK.EXE" /eml "C:\Users\admin\AppData\Local\Temp\DOCUMENTS AS REQUESTED.eml" | C:\Program Files\Microsoft Office\root\Office16\OUTLOOK.EXE | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Outlook Version: 16.0.16026.20146 Modules
| |||||||||||||||
Total events
30 231
Read events
29 069
Write events
1 042
Delete events
120
Modification events
| (PID) Process: | (6692) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\Common\ClientTelemetry\Sampling |
| Operation: | write | Name: | 6 |
Value: 01941A000000001000B24E9A3E06000000000000000600000000000000 | |||
| (PID) Process: | (6692) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\Common\CrashPersistence\OUTLOOK\6692 |
| Operation: | write | Name: | 0 |
Value: 0B0E10798840D9D66B544197F34DE6DBF3AA692300469DFE88DAADE0BCED016A04102400449A7D64B29D01008500A907556E6B6E6F776EC906022222CA0DC2190000C91003783634C511A434D2120B6F00750074006C006F006F006B002E00650078006500C51620C517808004C91808323231322D44656300 | |||
| (PID) Process: | (6692) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Outlook\Diagnostics |
| Operation: | delete value | Name: | BootCommand |
Value: | |||
| (PID) Process: | (6692) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Outlook\Diagnostics |
| Operation: | delete value | Name: | BootFailureCount |
Value: | |||
| (PID) Process: | (6692) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Outlook\Diagnostics\BootDiagnosticsDataPreviousSession |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (6692) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Outlook\Diagnostics\BootDiagnosticsDataPreviousSession |
| Operation: | write | Name: | CantBootResolution |
Value: BootSuccess | |||
| (PID) Process: | (6692) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Outlook\Diagnostics\BootDiagnosticsDataPreviousSession |
| Operation: | write | Name: | ProfileBeingOpened |
Value: Outlook | |||
| (PID) Process: | (6692) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Outlook\Diagnostics\BootDiagnosticsDataPreviousSession |
| Operation: | write | Name: | SessionId |
Value: C3D8E96E-C1AF-4750-8D52-F4E28119C131 | |||
| (PID) Process: | (6692) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Outlook\Diagnostics\BootDiagnosticsDataPreviousSession |
| Operation: | write | Name: | BootDiagnosticsLogFile |
Value: C:\Users\admin\AppData\Local\Temp\Outlook Logging\OUTLOOK_16_0_16026_20146-20240718T1116060318-1644.etl | |||
| (PID) Process: | (6692) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Outlook\Diagnostics |
| Operation: | delete value | Name: | ProfileBeingOpened |
Value: | |||
Executable files
18
Suspicious files
14
Text files
9
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6692 | OUTLOOK.EXE | C:\Users\admin\Documents\Outlook Files\Outlook1.pst | — | |
MD5:— | SHA256:— | |||
| 6692 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Temp\olkE675.tmp | text | |
MD5:0BE4A4FB8A19644185B2268354FB1662 | SHA256:7E9DC27FF3D225EB9B748441AA54F1B5786E375D80825F6ED06D180642E8F581 | |||
| 6692 | OUTLOOK.EXE | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\8978867674A468B0A6CFCD9BFC4B5FB4_9C0DCAF0DF7E8982AC428151E748EB1A | binary | |
MD5:06C74E61EAC23658139DF9EBE7ABF640 | SHA256:8E0B1B954615582A05D0C2DFB734B5E70A4168EBACCB306E1E93CC070FFB60E8 | |||
| 6692 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Temp\olkE7FF.tmp | text | |
MD5:1DB06B7487262E94E51F625F6F41366F | SHA256:991684D508F287349749CCE86EFEE16F66A8E989E96145B1B4003A04570B391B | |||
| 6692 | OUTLOOK.EXE | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\2915F375DF1BCD2F43025E66B08E7956_6D3DCD2A31326D78242DE6A9193C3742 | binary | |
MD5:C24F1267D12A528D162E0DA5D56F4F78 | SHA256:8E8BB805D4ABDAAEEAB39DE92477817E0ACDBF2DCDA70FD6F4EB24B8CCA3D2B6 | |||
| 6692 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Temp\olkE78F.tmp | html | |
MD5:0894F2C4BF7C7B8A5A3228DA950150ED | SHA256:67AE8CFE704D091F54CC4C1119A49E62DA0D77369EBDB2EC0B1B7854076C8281 | |||
| 6692 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Temp\olkE83E.tmp | binary | |
MD5:F2DC431F5C7E0FC03E864AD688B53BF7 | SHA256:2ABF9F0731B54C8D835B0A586E4E5973274C823726FD0486FC7F9367E04A0221 | |||
| 6692 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\TokenBroker\Cache\089d66ba04a8cec4bdc5267f42f39cf84278bb67.tbres | binary | |
MD5:93B6220856349EC5DF8CD11384CA18FE | SHA256:0313C287A8E561A88B7796EF2400BC8BA938069422087819C0276AE98E76E40A | |||
| 6692 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\TokenBroker\Cache\56a61aeb75d8f5be186c26607f4bb213abe7c5ec.tbres | binary | |
MD5:C23843DA615AFBA7A79B0DCF4A539E5B | SHA256:D15828E66E70323EA735E8F0D999D686B4F7ACDFD4AB387D014B7A4D428BBD24 | |||
| 6692 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Office\16.0\AddInClassifierCache\OfficeSharedEntities.bin | text | |
MD5:CC90D669144261B198DEAD45AA266572 | SHA256:89C701EEFF939A44F28921FD85365ECD87041935DCD0FE0BAF04957DA12C9899 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
6
TCP/UDP connections
42
DNS requests
23
Threats
22
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
6692 | OUTLOOK.EXE | GET | 200 | 109.70.240.130:80 | http://ocsp07.actalis.it/VA/AUTH-ROOT/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSw4x5v4bTlizjNRmTdkYSy7q0R9gQUUtiIOsifeGbtifN7OHCUyQICNtACEGgEO9xMsFqJEX4b%2FWkncfc%3D | unknown | — | — | whitelisted |
1656 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
6692 | OUTLOOK.EXE | GET | 200 | 93.39.128.41:80 | http://ca1.agid.gov.it/OCSP/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ0IUzpe7WXs2Kz%2F8Hu0KjsJ0iwvgQUpf2FBQ7D8dZlSiBs4ttNYJMriqACEBrFm5M%2FFFBkmWPhM9eNZcw%3D | unknown | — | — | whitelisted |
6692 | OUTLOOK.EXE | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEA77flR%2B3w%2FxBpruV2lte6A%3D | unknown | — | — | whitelisted |
4436 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
7052 | SIHClient.exe | GET | 200 | 88.221.169.152:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2120 | MoUsoCoreWorker.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4760 | RUXIMICS.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
3540 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6692 | OUTLOOK.EXE | 52.113.194.132:443 | ecs.office.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | unknown |
6692 | OUTLOOK.EXE | 109.70.240.130:80 | ocsp07.actalis.it | Aruba S.p.A. | IT | unknown |
6692 | OUTLOOK.EXE | 93.39.128.41:80 | ca1.agid.gov.it | Fastweb | IT | unknown |
6692 | OUTLOOK.EXE | 2.19.126.151:443 | omex.cdn.office.net | Akamai International B.V. | DE | unknown |
6692 | OUTLOOK.EXE | 52.111.236.4:443 | messaging.lifecycle.office.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
3540 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
ecs.office.com |
| whitelisted |
ocsp07.actalis.it |
| unknown |
ca1.agid.gov.it |
| whitelisted |
omex.cdn.office.net |
| whitelisted |
messaging.lifecycle.office.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2256 | svchost.exe | Misc activity | ET INFO External IP Lookup Domain (ipify .org) in DNS Lookup |
6284 | CasPol.exe | Misc activity | ET INFO External IP Address Lookup Domain (ipify .org) in TLS SNI |
6284 | CasPol.exe | A Network Trojan was detected | STEALER [ANY.RUN] AgentTesla Exfiltration (raw TCP) |
4296 | InstallUtil.exe | Misc activity | ET INFO External IP Address Lookup Domain (ipify .org) in TLS SNI |
4296 | InstallUtil.exe | A Network Trojan was detected | STEALER [ANY.RUN] AgentTesla Exfiltration (raw TCP) |
1104 | jsc.exe | Misc activity | ET INFO External IP Address Lookup Domain (ipify .org) in TLS SNI |
— | — | A Network Trojan was detected | STEALER [ANY.RUN] AgentTesla Exfiltration (raw TCP) |
6284 | CasPol.exe | A Network Trojan was detected | ET MALWARE AgentTesla Exfil Via SMTP |
6284 | CasPol.exe | Misc activity | INFO [ANY.RUN] SMTP email client opens transfer with server (EHLO) |
4296 | InstallUtil.exe | A Network Trojan was detected | ET MALWARE AgentTesla Exfil Via SMTP |
9 ETPRO signatures available at the full report