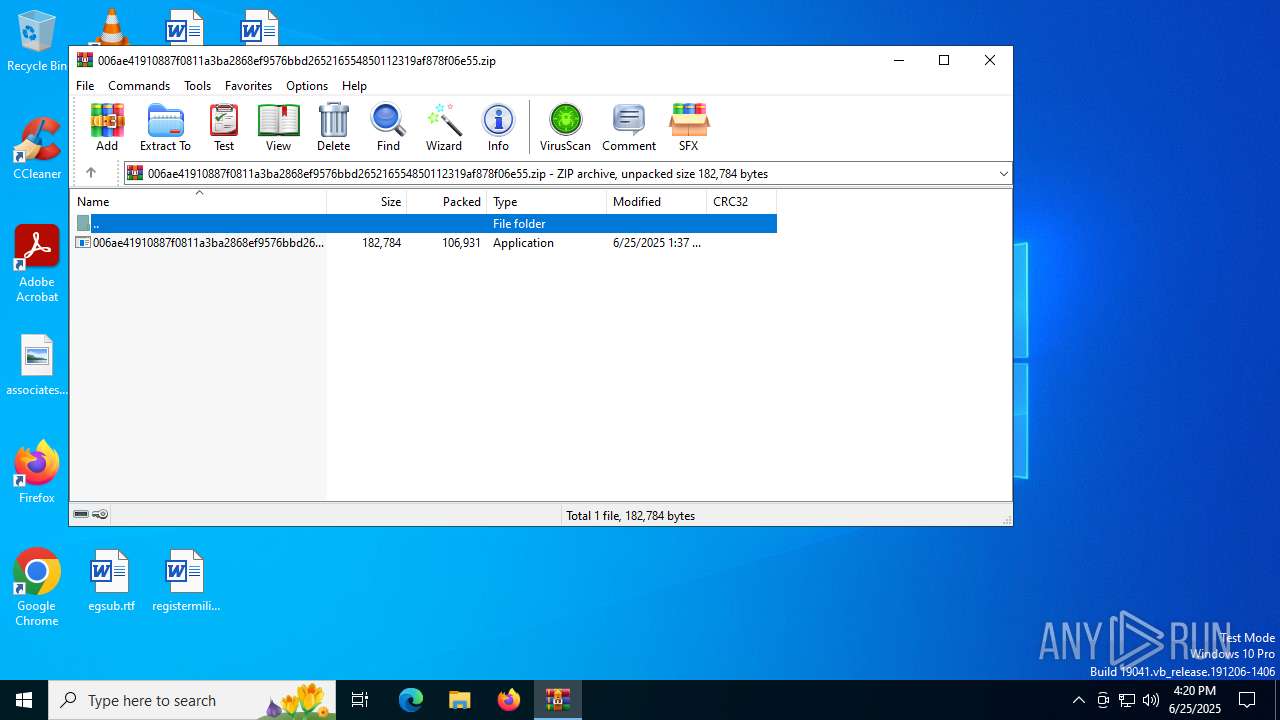
| File name: | 006ae41910887f0811a3ba2868ef9576bbd265216554850112319af878f06e55.zip |
| Full analysis: | https://app.any.run/tasks/64d3e029-890a-4263-81d5-87eb68a6cf6c |
| Verdict: | Malicious activity |
| Threats: | Play aka PlayCrypt ransomware group has been successfully targeting corporations, municipal entities, and infrastruction all over the world for about three years. It infiltrates networks via software vulnerabilities, phishing links and compromised websites. The ransomware abuses Windows system services to evade detection and maintain persistence. Play encrypts user files and steals sensitive data while demanding a ransom. |
| Analysis date: | June 25, 2025, 16:20:29 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
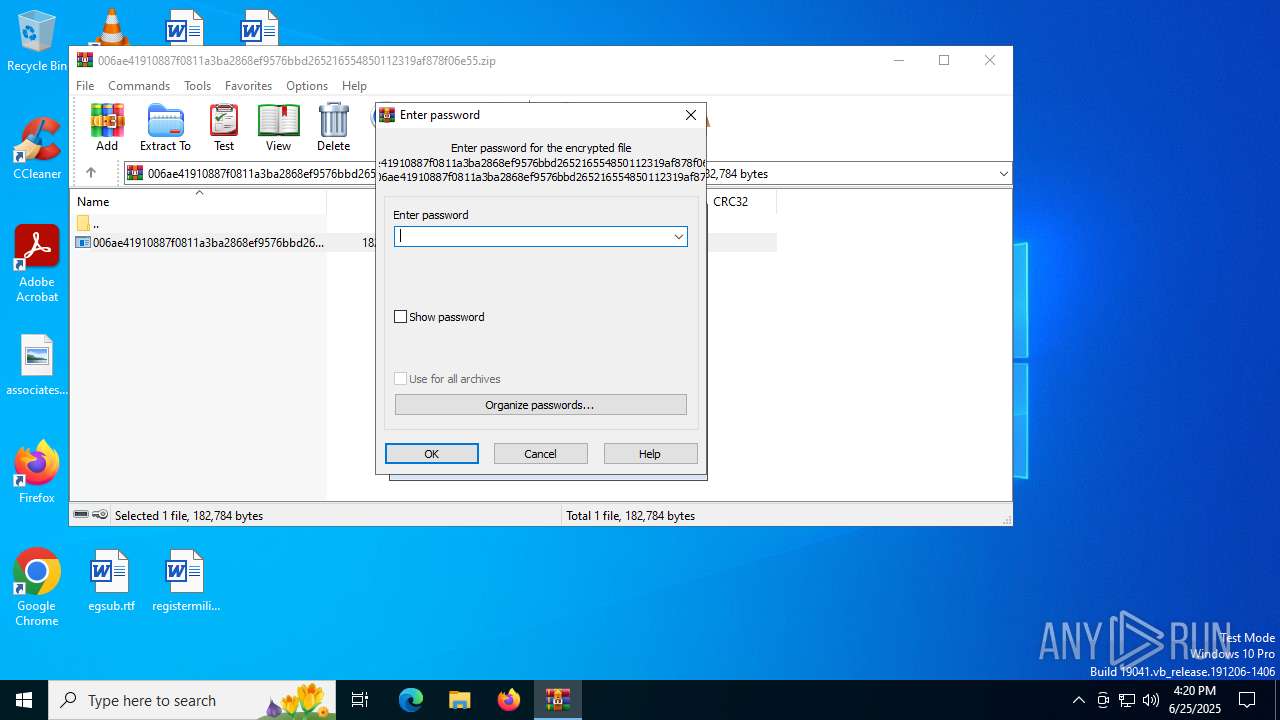
| File info: | Zip archive data, at least v5.1 to extract, compression method=AES Encrypted |
| MD5: | 1C7F72F198E8A3E83C6B765F91690B64 |
| SHA1: | EE8ADAB9C57E46C1AFEAEA6D58513DCCDC5AB1D6 |
| SHA256: | 279B25DB7337F315897D92001B7BAE24E13BA0D8208AB6B3E5FD0679910A9E20 |
| SSDEEP: | 3072:DfmOuRgWv8/dmNs5hW6v9MW6McsIjcWyybsUJsxv3jeSXnzP9nO:D+BRgJgGwyMNMkbsUeZCS5O |
MALICIOUS
Generic archive extractor
- WinRAR.exe (PID: 7080)
PLAY has been detected
- 006ae41910887f0811a3ba2868ef9576bbd265216554850112319af878f06e55.exe (PID: 5372)
RANSOMWARE has been detected
- 006ae41910887f0811a3ba2868ef9576bbd265216554850112319af878f06e55.exe (PID: 5372)
SUSPICIOUS
Reads security settings of Internet Explorer
- WinRAR.exe (PID: 7080)
Creates file in the systems drive root
- 006ae41910887f0811a3ba2868ef9576bbd265216554850112319af878f06e55.exe (PID: 5372)
Write to the desktop.ini file (may be used to cloak folders)
- 006ae41910887f0811a3ba2868ef9576bbd265216554850112319af878f06e55.exe (PID: 5372)
INFO
Executable content was dropped or overwritten
- WinRAR.exe (PID: 7080)
Checks supported languages
- 006ae41910887f0811a3ba2868ef9576bbd265216554850112319af878f06e55.exe (PID: 5372)
Creates files or folders in the user directory
- 006ae41910887f0811a3ba2868ef9576bbd265216554850112319af878f06e55.exe (PID: 5372)
Reads the computer name
- 006ae41910887f0811a3ba2868ef9576bbd265216554850112319af878f06e55.exe (PID: 5372)
Manual execution by a user
- WINWORD.EXE (PID: 640)
- WINWORD.EXE (PID: 868)
Checks proxy server information
- slui.exe (PID: 5576)
Reads the software policy settings
- slui.exe (PID: 5576)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 51 |
|---|---|
| ZipBitFlag: | 0x0003 |
| ZipCompression: | Unknown (99) |
| ZipModifyDate: | 2025:06:25 13:37:16 |
| ZipCRC: | 0x5a9cdce9 |
| ZipCompressedSize: | 106931 |
| ZipUncompressedSize: | 182784 |
| ZipFileName: | 006ae41910887f0811a3ba2868ef9576bbd265216554850112319af878f06e55.exe |
Total processes
143
Monitored processes
5
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 640 | "C:\Program Files\Microsoft Office\Root\Office16\WINWORD.EXE" /n "C:\Users\admin\Desktop\recommendacross.rtf" /o "" | C:\Program Files\Microsoft Office\root\Office16\WINWORD.EXE | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Word Version: 16.0.16026.20146 Modules
| |||||||||||||||
| 868 | "C:\Program Files\Microsoft Office\Root\Office16\WINWORD.EXE" /n "C:\Users\admin\Desktop\registermilitary.rtf" /o "" | C:\Program Files\Microsoft Office\root\Office16\WINWORD.EXE | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Word Version: 16.0.16026.20146 Modules
| |||||||||||||||
| 5372 | "C:\Users\admin\AppData\Local\Temp\Rar$EXb7080.25858\006ae41910887f0811a3ba2868ef9576bbd265216554850112319af878f06e55.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXb7080.25858\006ae41910887f0811a3ba2868ef9576bbd265216554850112319af878f06e55.exe | WinRAR.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Modules
| |||||||||||||||
| 5576 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7080 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\AppData\Local\Temp\006ae41910887f0811a3ba2868ef9576bbd265216554850112319af878f06e55.zip | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.91.0 Modules
| |||||||||||||||
Total events
6 722
Read events
6 667
Write events
55
Delete events
0
Modification events
| (PID) Process: | (7080) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (7080) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (7080) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (7080) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (7080) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (7080) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\006ae41910887f0811a3ba2868ef9576bbd265216554850112319af878f06e55.zip | |||
| (PID) Process: | (7080) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (7080) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (7080) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (7080) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
Executable files
1
Suspicious files
10
Text files
1
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 5372 | 006ae41910887f0811a3ba2868ef9576bbd265216554850112319af878f06e55.exe | C:\Program Files\Adobe\Acrobat DC\Acrobat\AcroCEF\icudtl.dat | — | |
MD5:— | SHA256:— | |||
| 7080 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXb7080.25858\006ae41910887f0811a3ba2868ef9576bbd265216554850112319af878f06e55.exe | executable | |
MD5:223EFF1610B432A1F1AA06C60BD7B9A6 | SHA256:006AE41910887F0811A3BA2868EF9576BBD265216554850112319AF878F06E55 | |||
| 5372 | 006ae41910887f0811a3ba2868ef9576bbd265216554850112319af878f06e55.exe | C:\bootTel.dat.PLAY | binary | |
MD5:3CCF2E19A951EE2C1C99FB062389342A | SHA256:29F42B4AD28A7C6AF9194AC36C14FDB065F7AD79D63980C3910D6132401C0600 | |||
| 5372 | 006ae41910887f0811a3ba2868ef9576bbd265216554850112319af878f06e55.exe | C:\Program Files\Adobe\Acrobat DC\Acrobat\1494870C-9912-C184-4CC9-B401-A53F4D8DE290.pdf | binary | |
MD5:E0AF12F92720FF97849547A83AA05371 | SHA256:7966173DBE30A13D2D532FBFAC0EF7E367FEAE4178D3846282124FBF8979E214 | |||
| 5372 | 006ae41910887f0811a3ba2868ef9576bbd265216554850112319af878f06e55.exe | C:\Program Files\Adobe\Acrobat DC\Acrobat\AcroCEF\LICENSE.txt | binary | |
MD5:D0A98598E7BF8B451AEEE3244C66CFD2 | SHA256:8B0591C5396C68A6D0DB17739812C1AF28BDA921E4650CD7BF711ED6899C1F7E | |||
| 5372 | 006ae41910887f0811a3ba2868ef9576bbd265216554850112319af878f06e55.exe | C:\Users\admin\AppData\Local\VirtualStore\ReadMe.txt | text | |
MD5:AF5C0A0FD6FA8BC8E59F6221A1705EE6 | SHA256:6E55ACC025EA4888FDF070A1707B6E04A509B24772E81D64595EA6B2848DD71F | |||
| 5372 | 006ae41910887f0811a3ba2868ef9576bbd265216554850112319af878f06e55.exe | C:\Program Files\Adobe\Acrobat DC\Acrobat\AcroCEF\vk_swiftshader_icd.json.PLAY | binary | |
MD5:4073D3CC5F24153BB21FCE5DB7AD59AA | SHA256:D4860C14D4D183FE11E306B9785570FA9497E094F34694BA85D7D4361F93FF94 | |||
| 5372 | 006ae41910887f0811a3ba2868ef9576bbd265216554850112319af878f06e55.exe | C:\$Recycle.Bin\S-1-5-21-1693682860-607145093-2874071422-1001\desktop.ini.PLAY | binary | |
MD5:33A8E98530836D7780FEEDABBBAB1596 | SHA256:0BD55C5800698E8B2A4E625CD833B920103ABCA5AB064E2E7ED62FCD766A978F | |||
| 5372 | 006ae41910887f0811a3ba2868ef9576bbd265216554850112319af878f06e55.exe | C:\Program Files\Adobe\Acrobat DC\Acrobat\acrobat_reader_appicon_16.png.PLAY | binary | |
MD5:7C665072C229E06D3BF666BF1F6F59DB | SHA256:9E1E3271B68A85840D916D1B7A09E1DF856A6E2B3E5DA790BD3057DD13CDB581 | |||
| 5372 | 006ae41910887f0811a3ba2868ef9576bbd265216554850112319af878f06e55.exe | C:\Program Files\Adobe\Acrobat DC\Acrobat\AcroCEF\vk_swiftshader_icd.json | binary | |
MD5:4073D3CC5F24153BB21FCE5DB7AD59AA | SHA256:D4860C14D4D183FE11E306B9785570FA9497E094F34694BA85D7D4361F93FF94 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
6
TCP/UDP connections
23
DNS requests
19
Threats
1
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1268 | svchost.exe | GET | 200 | 23.48.23.156:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
4312 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
7028 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
7028 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
2940 | svchost.exe | GET | 200 | 23.209.209.135:80 | http://x1.c.lencr.org/ | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
1268 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
5944 | MoUsoCoreWorker.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4680 | RUXIMICS.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1268 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
1268 | svchost.exe | 23.48.23.156:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
1268 | svchost.exe | 95.101.149.131:80 | www.microsoft.com | Akamai International B.V. | NL | whitelisted |
4312 | svchost.exe | 40.126.31.1:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4312 | svchost.exe | 2.17.190.73:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
nexusrules.officeapps.live.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
— | — | Unknown Traffic | ET USER_AGENTS Microsoft Dr Watson User-Agent (MSDW) |