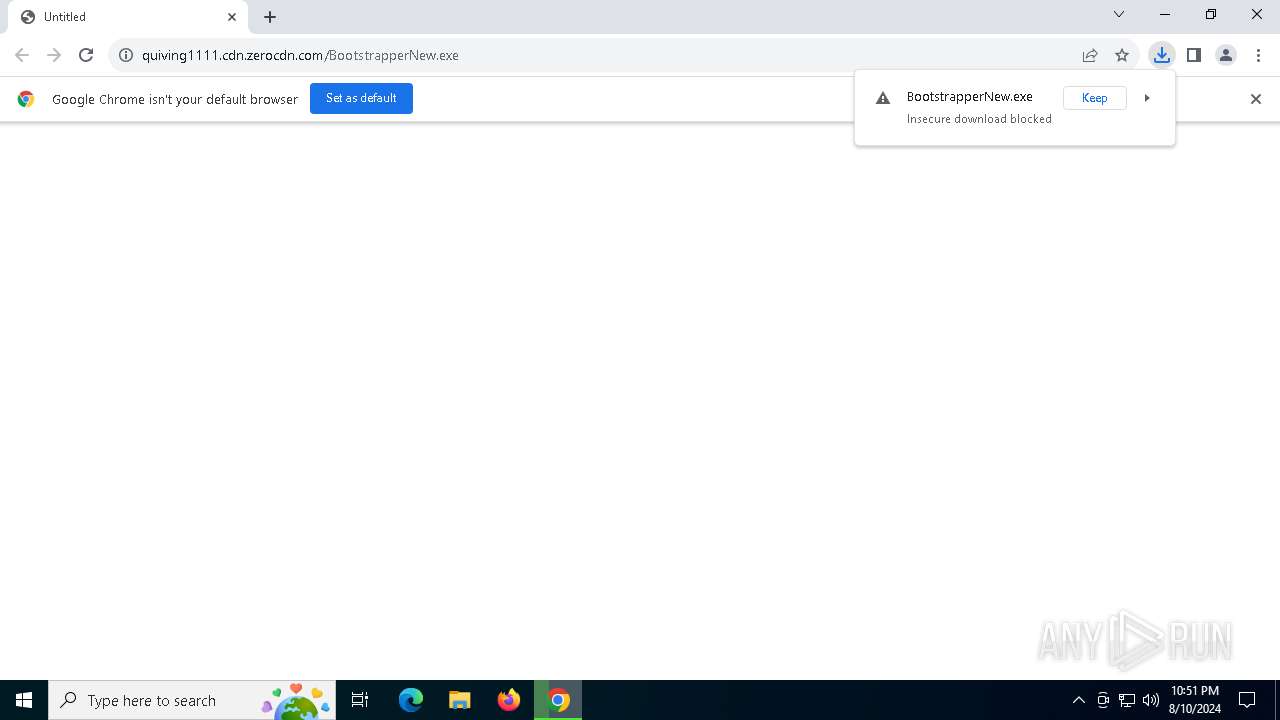
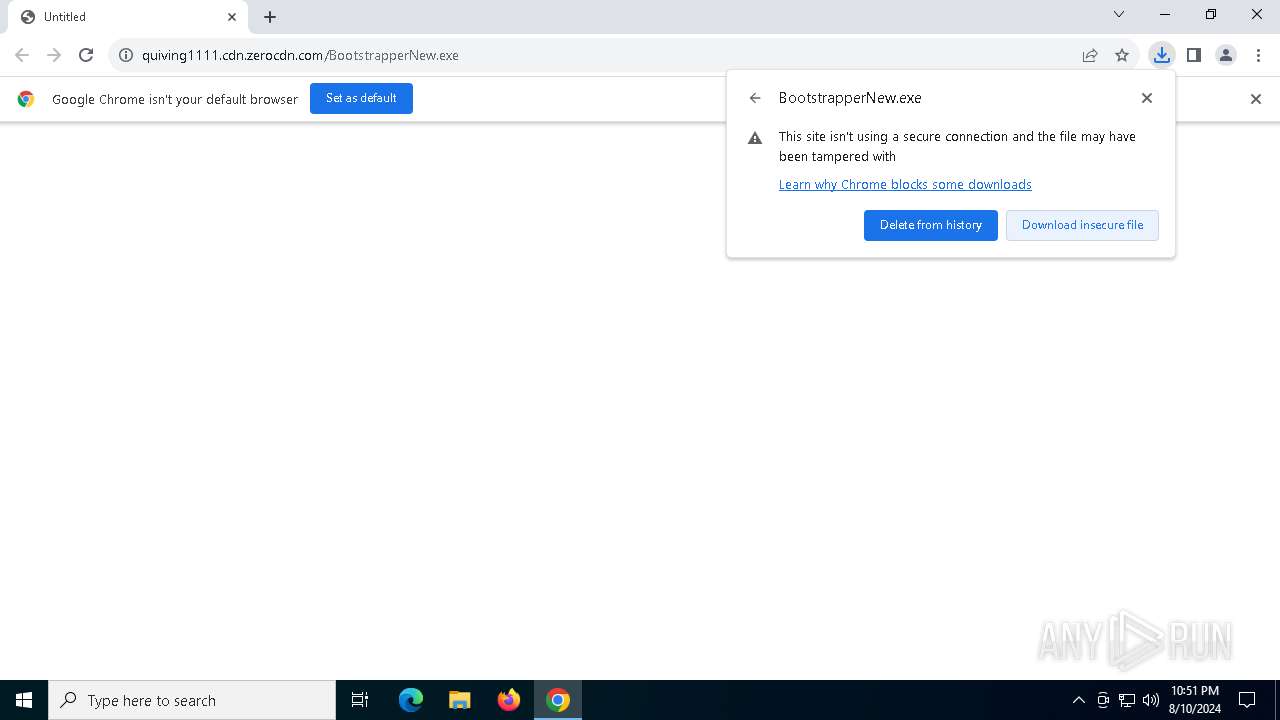
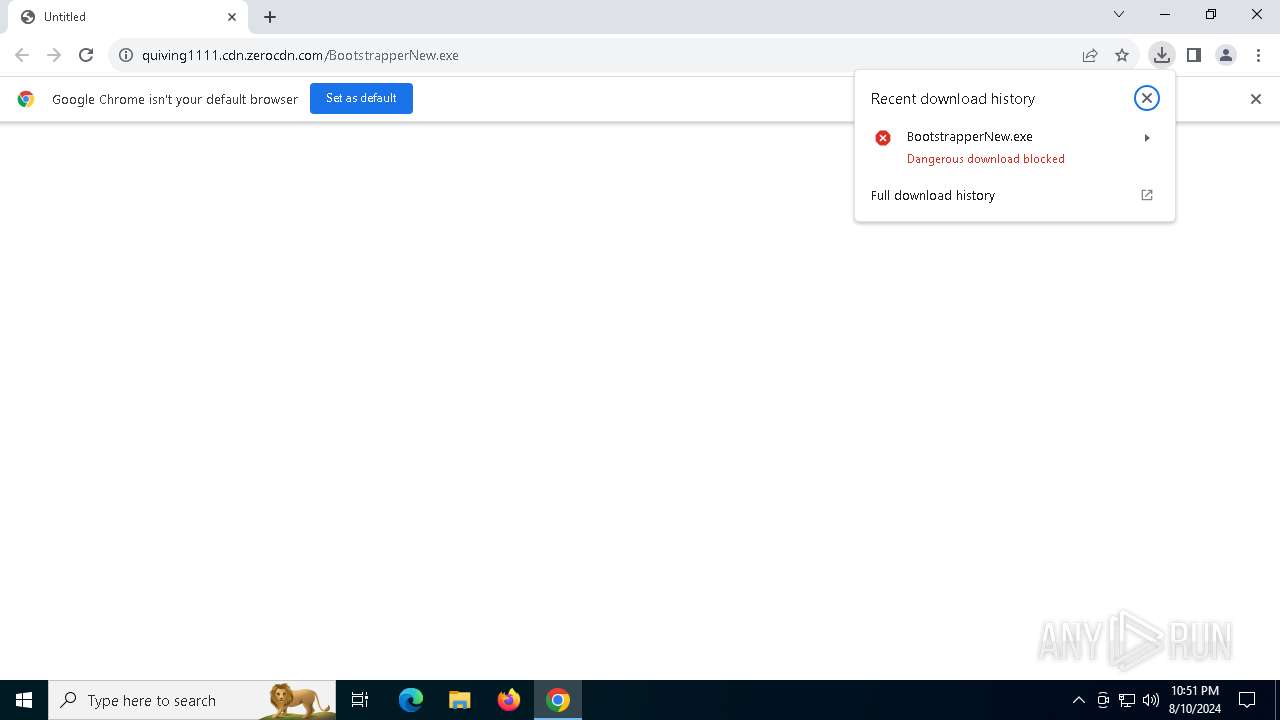
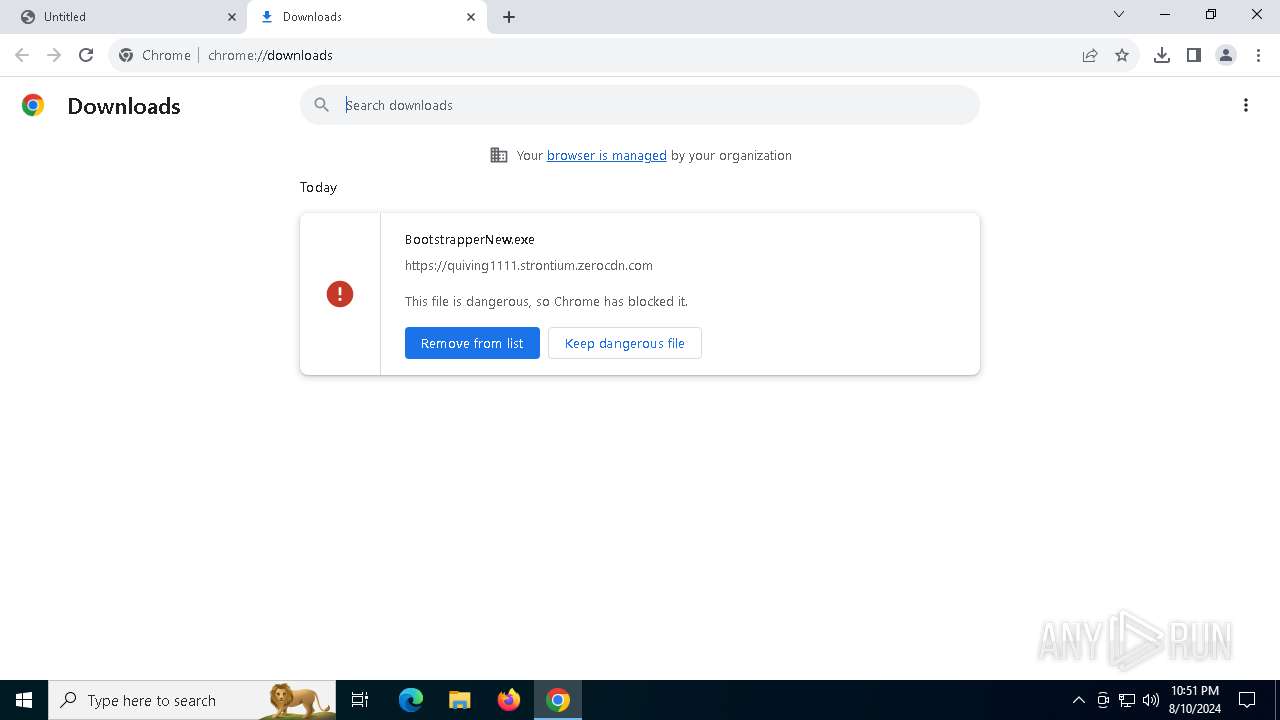
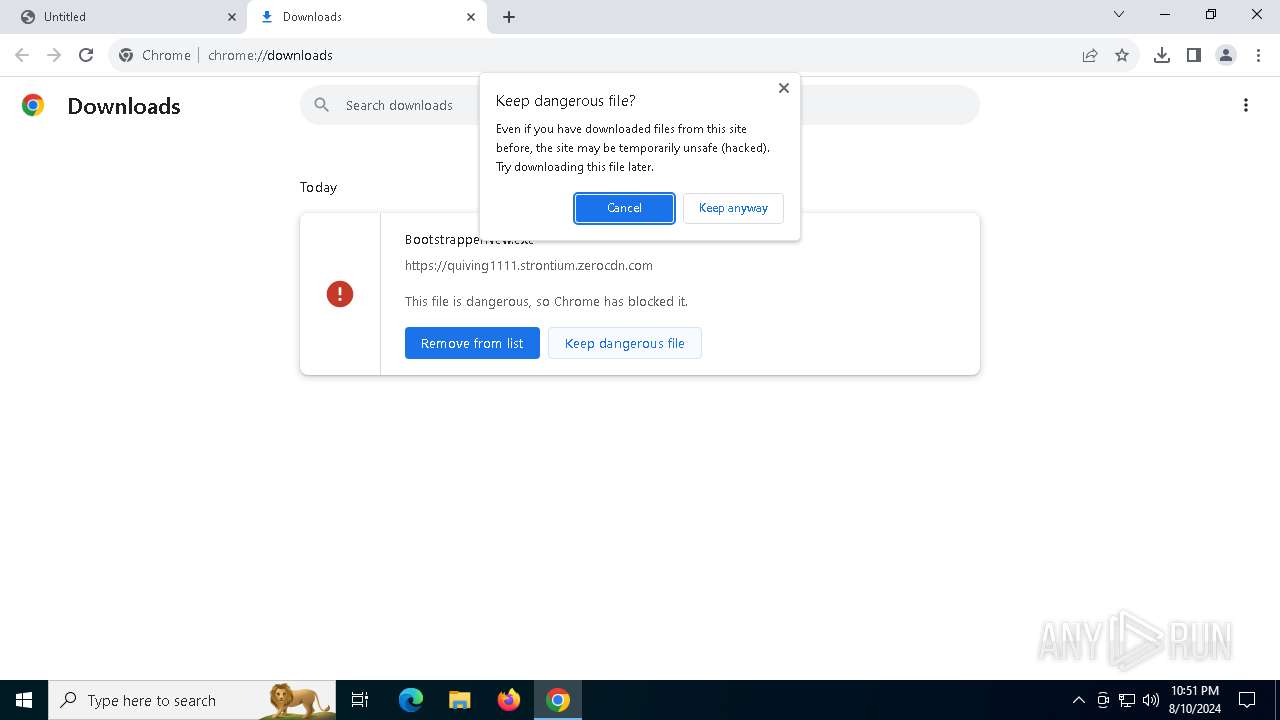
| URL: | http://quiving1111.cdn.zerocdn.com/BootstrapperNew.exe |
| Full analysis: | https://app.any.run/tasks/4a5ebf62-7ff0-448b-bfa1-f389d3c29ce1 |
| Verdict: | Malicious activity |
| Threats: | Blank Grabber is an infostealer written in Python. It is designed to steal a wide array of data, such as browser login credentials, crypto wallets, Telegram sessions, and Discord tokens. It is an open-source malware, with its code available on GitHub and regularly receiving updates. Blank Grabber builder’s simple interface lets threat actors even with basic skills to deploy it and conduct attacks. |
| Analysis date: | August 10, 2024, 22:51:06 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MD5: | E29AB2321FE0C9E3C89B5B29B0CDBDEF |
| SHA1: | DDAEBCCE4CB993641921CDC6FF8451BEF1F6B119 |
| SHA256: | 2649233AAD6E537DCD353CD839A54AD0344E6062B52E14EDF36CDE8363E1E54E |
| SSDEEP: | 3:N1KP3SXAXKW/GTbKRWC40Cn:CvSCKW/8NCS |
MALICIOUS
Bypass User Account Control (ComputerDefaults)
- ComputerDefaults.exe (PID: 6368)
Adds path to the Windows Defender exclusion list
- BootstrapperNew.exe (PID: 7700)
- cmd.exe (PID: 4436)
- cmd.exe (PID: 5300)
Windows Defender preferences modified via 'Set-MpPreference'
- cmd.exe (PID: 2340)
Antivirus name has been found in the command line (generic signature)
- cmd.exe (PID: 2340)
- MpCmdRun.exe (PID: 2700)
BLANKGRABBER has been detected (SURICATA)
- BootstrapperNew.exe (PID: 7700)
Stealers network behavior
- BootstrapperNew.exe (PID: 7700)
SUSPICIOUS
Process drops legitimate windows executable
- BootstrapperNew.exe (PID: 8048)
- chrome.exe (PID: 6420)
- BootstrapperNew.exe (PID: 7700)
- BootstrapperNew.exe (PID: 1536)
Process drops python dynamic module
- BootstrapperNew.exe (PID: 8048)
- BootstrapperNew.exe (PID: 1536)
Drops the executable file immediately after the start
- BootstrapperNew.exe (PID: 8048)
- BootstrapperNew.exe (PID: 1536)
- BootstrapperNew.exe (PID: 7700)
Executable content was dropped or overwritten
- BootstrapperNew.exe (PID: 8048)
- BootstrapperNew.exe (PID: 7700)
- BootstrapperNew.exe (PID: 1536)
The process drops C-runtime libraries
- BootstrapperNew.exe (PID: 8048)
- BootstrapperNew.exe (PID: 1536)
Application launched itself
- BootstrapperNew.exe (PID: 8048)
- BootstrapperNew.exe (PID: 1536)
Starts CMD.EXE for commands execution
- BootstrapperNew.exe (PID: 8068)
- BootstrapperNew.exe (PID: 7700)
Uses REG/REGEDIT.EXE to modify registry
- cmd.exe (PID: 8096)
- cmd.exe (PID: 8184)
- cmd.exe (PID: 7668)
Starts POWERSHELL.EXE for commands execution
- cmd.exe (PID: 4436)
- cmd.exe (PID: 2340)
- cmd.exe (PID: 5300)
- cmd.exe (PID: 8036)
- cmd.exe (PID: 7016)
Uses WEVTUTIL.EXE to query events from a log or log file
- cmd.exe (PID: 7648)
- cmd.exe (PID: 7248)
Found strings related to reading or modifying Windows Defender settings
- BootstrapperNew.exe (PID: 7700)
- BootstrapperNew.exe (PID: 8068)
Script disables Windows Defender's real-time protection
- cmd.exe (PID: 2340)
Uses WMIC.EXE to obtain a list of video controllers
- cmd.exe (PID: 5976)
- cmd.exe (PID: 2728)
- cmd.exe (PID: 6628)
Uses WMIC.EXE to obtain Windows Installer data
- cmd.exe (PID: 7128)
- cmd.exe (PID: 6976)
Get information on the list of running processes
- BootstrapperNew.exe (PID: 7700)
- cmd.exe (PID: 7960)
- cmd.exe (PID: 1984)
- cmd.exe (PID: 8056)
Script disables Windows Defender's IPS
- cmd.exe (PID: 2340)
Script adds exclusion path to Windows Defender
- cmd.exe (PID: 4436)
- cmd.exe (PID: 5300)
Uses TASKKILL.EXE to kill process
- cmd.exe (PID: 5172)
- cmd.exe (PID: 7832)
- cmd.exe (PID: 5624)
- cmd.exe (PID: 8188)
- cmd.exe (PID: 8168)
- cmd.exe (PID: 188)
- cmd.exe (PID: 4436)
- cmd.exe (PID: 4576)
The executable file from the user directory is run by the CMD process
- rar.exe (PID: 6640)
Uses WMIC.EXE to obtain operating system information
- cmd.exe (PID: 6620)
Uses WMIC.EXE to obtain computer system information
- cmd.exe (PID: 6704)
Checks for external IP
- svchost.exe (PID: 2256)
- BootstrapperNew.exe (PID: 7700)
INFO
Application launched itself
- chrome.exe (PID: 6420)
Executable content was dropped or overwritten
- chrome.exe (PID: 6420)
Reads Microsoft Office registry keys
- chrome.exe (PID: 6420)
Attempting to use instant messaging service
- svchost.exe (PID: 2256)
- BootstrapperNew.exe (PID: 7700)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
253
Monitored processes
122
Malicious processes
8
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 188 | C:\WINDOWS\system32\cmd.exe /c "taskkill /F /PID 6764" | C:\Windows\System32\cmd.exe | — | BootstrapperNew.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 128 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1076 | wmic path win32_VideoController get name | C:\Windows\System32\wbem\WMIC.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: WMI Commandline Utility Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1104 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1168 | "C:\WINDOWS\system32\ComputerDefaults.exe" --nouacbypass | C:\Windows\System32\ComputerDefaults.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Set Program Access and Computer Defaults Control Panel Exit code: 3221226540 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1184 | taskkill /F /PID 6684 | C:\Windows\System32\taskkill.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Terminates Processes Exit code: 128 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1236 | tasklist /FO LIST | C:\Windows\System32\tasklist.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Lists the current running tasks Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1288 | REG QUERY HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Control\Class\{4D36E968-E325-11CE-BFC1-08002BE10318}\0000\ProviderName 2 | C:\Windows\System32\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Console Tool Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1452 | wmic os get Caption | C:\Windows\System32\wbem\WMIC.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: WMI Commandline Utility Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1536 | "C:\Users\admin\Downloads\BootstrapperNew.exe" | C:\Users\admin\Downloads\BootstrapperNew.exe | ComputerDefaults.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Grant more screen time Exit code: 0 Version: 10.0.19041.4355 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1984 | C:\WINDOWS\system32\cmd.exe /c "tasklist /FO LIST" | C:\Windows\System32\cmd.exe | — | BootstrapperNew.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
55 576
Read events
55 521
Write events
51
Delete events
4
Modification events
| (PID) Process: | (6420) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (6420) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
| (PID) Process: | (6420) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\ThirdParty |
| Operation: | write | Name: | StatusCodes |
Value: | |||
| (PID) Process: | (6420) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\ThirdParty |
| Operation: | write | Name: | StatusCodes |
Value: 01000000 | |||
| (PID) Process: | (6420) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 1 | |||
| (PID) Process: | (6420) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Update\ClientState\{8A69D345-D564-463c-AFF1-A69D9E530F96} |
| Operation: | write | Name: | dr |
Value: 1 | |||
| (PID) Process: | (6420) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\StabilityMetrics |
| Operation: | write | Name: | user_experience_metrics.stability.exited_cleanly |
Value: 0 | |||
| (PID) Process: | (6420) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome |
| Operation: | write | Name: | UsageStatsInSample |
Value: 0 | |||
| (PID) Process: | (6420) chrome.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Google\Update\ClientStateMedium\{8A69D345-D564-463C-AFF1-A69D9E530F96} |
| Operation: | write | Name: | usagestats |
Value: 0 | |||
| (PID) Process: | (6420) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Update\ClientState\{8A69D345-D564-463c-AFF1-A69D9E530F96} |
| Operation: | write | Name: | metricsid |
Value: | |||
Executable files
41
Suspicious files
50
Text files
41
Unknown types
3
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6420 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\PersistentOriginTrials\LOG.old | — | |
MD5:— | SHA256:— | |||
| 6420 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\chrome_cart_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 6420 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\coupon_db\LOG.old~RFe70c7.TMP | — | |
MD5:— | SHA256:— | |||
| 6420 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\parcel_tracking_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 6420 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\discounts_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 6420 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\coupon_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 6420 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\commerce_subscription_db\LOG.old~RFe70c7.TMP | — | |
MD5:— | SHA256:— | |||
| 6420 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\commerce_subscription_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 6420 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Crashpad\settings.dat | binary | |
MD5:FC81892AC822DCBB09441D3B58B47125 | SHA256:FB077C966296D02D50CCBF7F761D2A3311A206A784A7496F331C2B0D6AD205C8 | |||
| 6420 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Sync Data\LevelDB\LOG.old | text | |
MD5:723783C35EAEEE1492EDB30847AE6750 | SHA256:C29323F784CF873BF34992E7A2B4630B19641BF42980109E31D5AF2D487DF6F8 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
11
TCP/UDP connections
55
DNS requests
36
Threats
7
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3376 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
5336 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
3376 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
3376 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
6184 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
376 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
6420 | chrome.exe | GET | 200 | 172.64.149.23:80 | http://ocsp.comodoca.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBRTtU9uFqgVGHhJwXZyWCNXmVR5ngQUoBEKIz6W8Qfs4q8p74Klf9AwpLQCEEj8k7RgVZSNNqfJionWlBY%3D | unknown | — | — | whitelisted |
6420 | chrome.exe | GET | 200 | 172.64.149.23:80 | http://ocsp.sectigo.com/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBRd0JozUYXMqqW4y4zJTrLcMCRSkAQUgTKSQSsozUbIxKLGKjkS7EipPxQCEQC%2FsVABu%2FWS1JYqd5fqc2%2Bj | unknown | — | — | whitelisted |
6420 | chrome.exe | GET | 200 | 172.64.149.23:80 | http://ocsp.sectigo.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSdE3gf41WAic8Uh9lF92%2BIJqh5qwQUMuuSmv81lkgvKEBCcCA2kVwXheYCEDPXCKiRQFMZ4qW70zm5rW4%3D | unknown | — | — | whitelisted |
7700 | BootstrapperNew.exe | GET | 200 | 208.95.112.1:80 | http://ip-api.com/json/?fields=225545 | unknown | — | — | shared |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
5116 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
1076 | RUXIMICS.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
2120 | MoUsoCoreWorker.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
3888 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
6420 | chrome.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
6684 | chrome.exe | 64.233.167.84:443 | accounts.google.com | GOOGLE | US | unknown |
6684 | chrome.exe | 176.58.48.48:443 | quiving1111.cdn.zerocdn.com | DigitalOne AG | RU | unknown |
6684 | chrome.exe | 176.58.48.48:80 | quiving1111.cdn.zerocdn.com | DigitalOne AG | RU | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
quiving1111.cdn.zerocdn.com |
| unknown |
accounts.google.com |
| whitelisted |
quiving1111.strontium.zerocdn.com |
| unknown |
www.google.com |
| whitelisted |
www.bing.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
login.live.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2256 | svchost.exe | Device Retrieving External IP Address Detected | INFO [ANY.RUN] External IP Check (ip-api .com) |
2256 | svchost.exe | Device Retrieving External IP Address Detected | ET INFO External IP Lookup Domain in DNS Lookup (ip-api .com) |
7700 | BootstrapperNew.exe | Device Retrieving External IP Address Detected | ET POLICY External IP Lookup ip-api.com |
2256 | svchost.exe | Misc activity | ET INFO Observed Discord Domain in DNS Lookup (discordapp .com) |
7700 | BootstrapperNew.exe | Device Retrieving External IP Address Detected | ET POLICY External IP Lookup ip-api.com |
7700 | BootstrapperNew.exe | Misc activity | ET INFO Observed Discord Domain (discordapp .com in TLS SNI) |
7700 | BootstrapperNew.exe | A Network Trojan was detected | STEALER [ANY.RUN] BlankGrabber (SkochGrabber) Generic External IP Check |