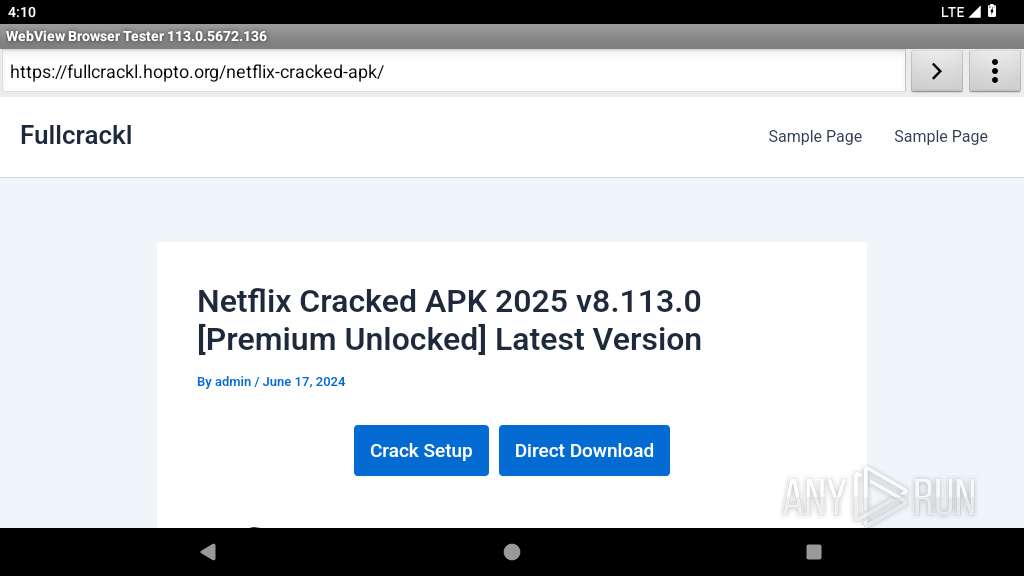
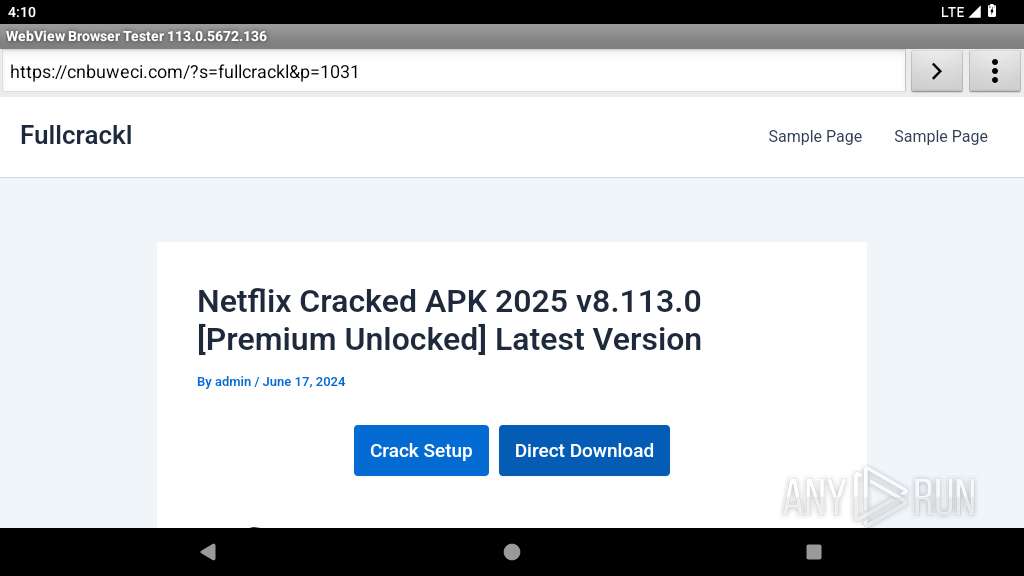
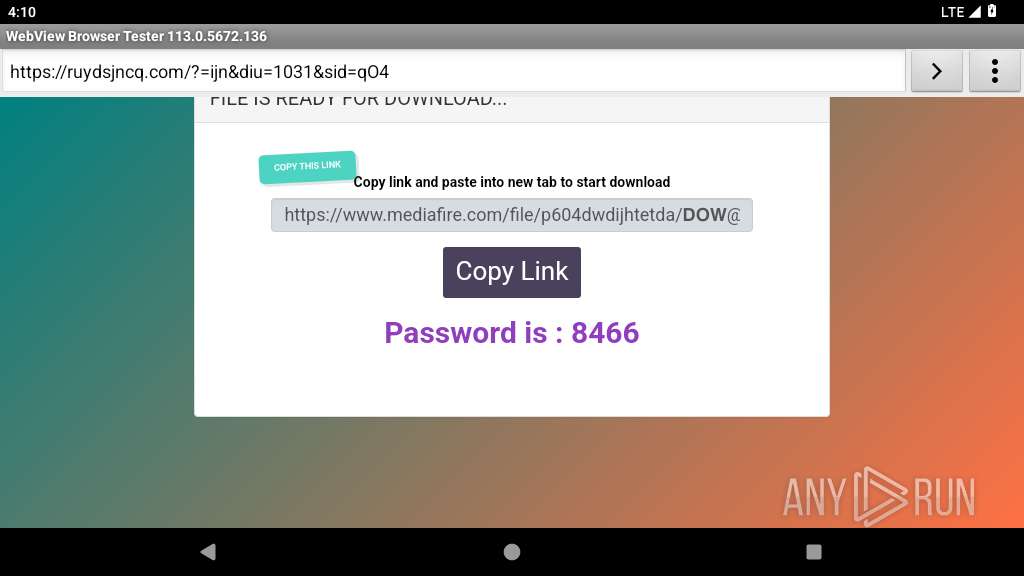
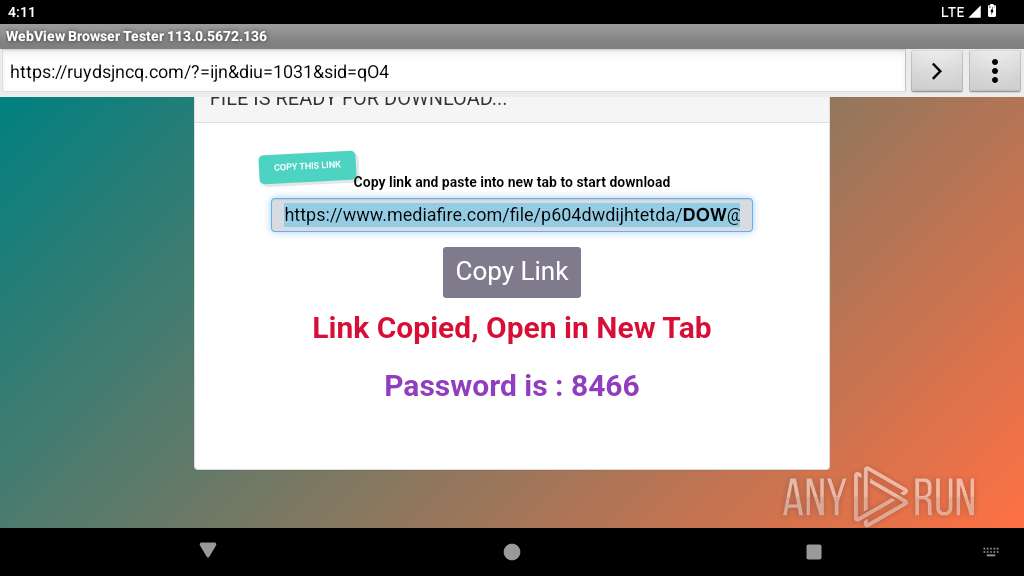
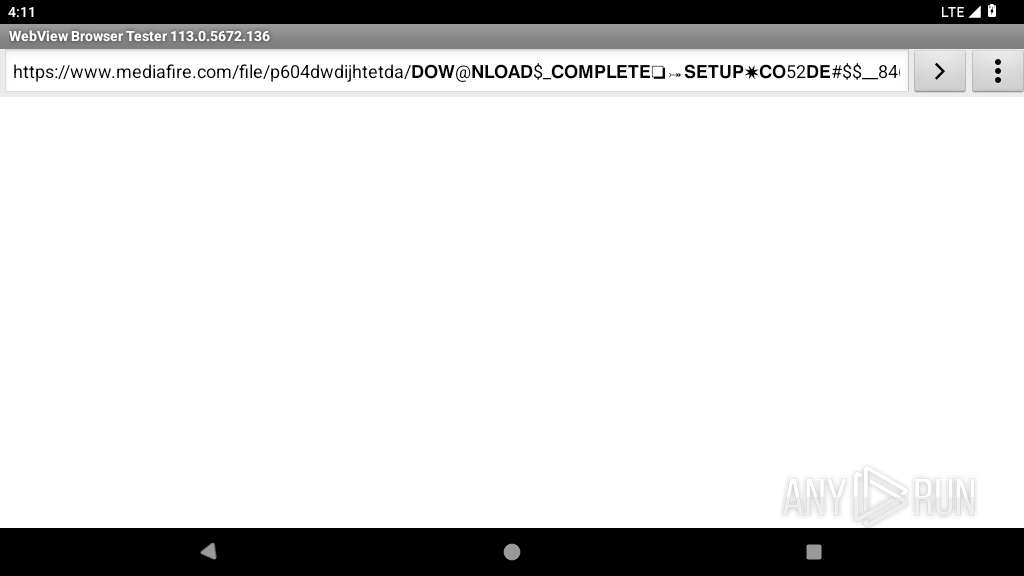
| URL: | https://fullcrackl.hopto.org/netflix-cracked-apk/ |
| Full analysis: | https://app.any.run/tasks/22bf42f7-0ac6-4b16-a44d-445b2c609c1a |
| Verdict: | Malicious activity |
| Threats: | Lumma is an information stealer, developed using the C programming language. It is offered for sale as a malware-as-a-service, with several plans available. It usually targets cryptocurrency wallets, login credentials, and other sensitive information on a compromised system. The malicious software regularly gets updates that improve and expand its functionality, making it a serious stealer threat. |
| Analysis date: | May 28, 2025, 16:10:38 |
| OS: | Android 14 |
| Tags: | |
| Indicators: | |
| MD5: | B8D332C9F876D012C52572928BFC77C6 |
| SHA1: | 4764B28790B11A8BB54161B0840C5287A08C1385 |
| SHA256: | 25D0186DAC6DF62E1E13B21DF456B24624E82F29775C337BD8A90BA6E1FA5AFB |
| SSDEEP: | 3:N805KVsoJ0TvZkh:20FTZ0 |
MALICIOUS
LUMMA has been detected (SURICATA)
- netd (PID: 341)
Stealers network behavior
- netd (PID: 341)
SUSPICIOUS
Contacting a server suspected of hosting an CnC
- netd (PID: 341)
INFO
No info indicators.
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
127
Monitored processes
5
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process |
|---|---|---|---|---|
| 341 | /system/bin/netd | /system/bin/netd | init | |
User: root Integrity Level: UNKNOWN Exit code: 0 | ||||
| 2221 | org.chromium.webview_shell | /system/bin/app_process64 | app_process64 | |
User: root Integrity Level: UNKNOWN Exit code: 0 | ||||
| 2247 | zygote | /system/bin/app_process32 | app_process32 | |
User: root Integrity Level: UNKNOWN Exit code: 0 | ||||
| 2249 | webview_zygote | /system/bin/app_process32 | — | app_process32 |
User: webview_zygote Integrity Level: UNKNOWN Exit code: 0 | ||||
| 2299 | zygote | /system/bin/app_process32 | app_process32 | |
User: root Integrity Level: UNKNOWN Exit code: 0 | ||||
Total events
0
Read events
0
Write events
0
Delete events
0
Modification events
Executable files
0
Suspicious files
0
Text files
0
Unknown types
0
Dropped files
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
1
TCP/UDP connections
52
DNS requests
36
Threats
7
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 204 | 172.217.18.99:80 | http://connectivitycheck.gstatic.com/generate_204 | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
446 | mdnsd | 224.0.0.251:5353 | — | — | — | unknown |
— | — | 172.217.18.99:80 | connectivitycheck.gstatic.com | GOOGLE | US | whitelisted |
— | — | 172.217.18.4:443 | www.google.com | GOOGLE | US | whitelisted |
— | — | 216.239.35.12:123 | time.android.com | — | — | whitelisted |
— | — | 64.233.167.81:443 | staging-remoteprovisioning.sandbox.googleapis.com | GOOGLE | US | whitelisted |
2247 | app_process32 | 142.250.185.227:443 | clientservices.googleapis.com | GOOGLE | US | whitelisted |
2221 | app_process64 | 195.66.210.81:443 | fullcrackl.hopto.org | Virtual Systems LLC | UA | suspicious |
2299 | app_process32 | 142.250.185.131:443 | update.googleapis.com | GOOGLE | US | whitelisted |
2299 | app_process32 | 172.217.16.206:443 | dl.google.com | GOOGLE | US | whitelisted |
2221 | app_process64 | 188.114.96.3:443 | windows11activators.com | CLOUDFLARENET | NL | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
connectivitycheck.gstatic.com |
| whitelisted |
www.google.com |
| whitelisted |
google.com |
| whitelisted |
time.android.com |
| whitelisted |
staging-remoteprovisioning.sandbox.googleapis.com |
| whitelisted |
clientservices.googleapis.com |
| whitelisted |
fullcrackl.hopto.org |
| unknown |
update.googleapis.com |
| whitelisted |
dl.google.com |
| whitelisted |
stats.wp.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
— | — | Misc activity | ET INFO Android Device Connectivity Check |
341 | netd | Potentially Bad Traffic | ET DYN_DNS DNS Query to DynDNS Domain *.hopto .org |
341 | netd | Domain Observed Used for C2 Detected | STEALER [ANY.RUN] Suspected Lumma domain by CrossDomain ( .iconbolt .com) |
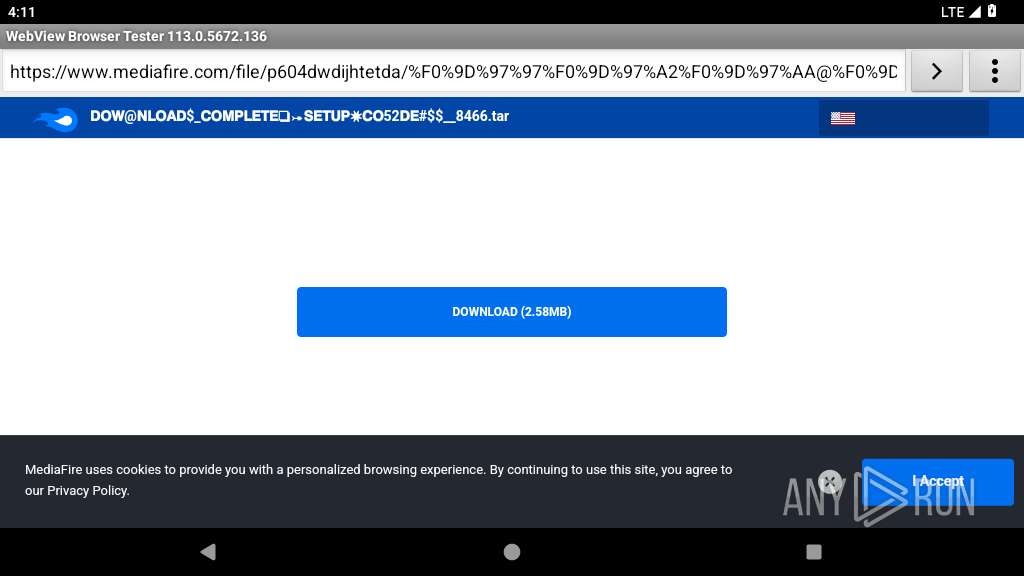
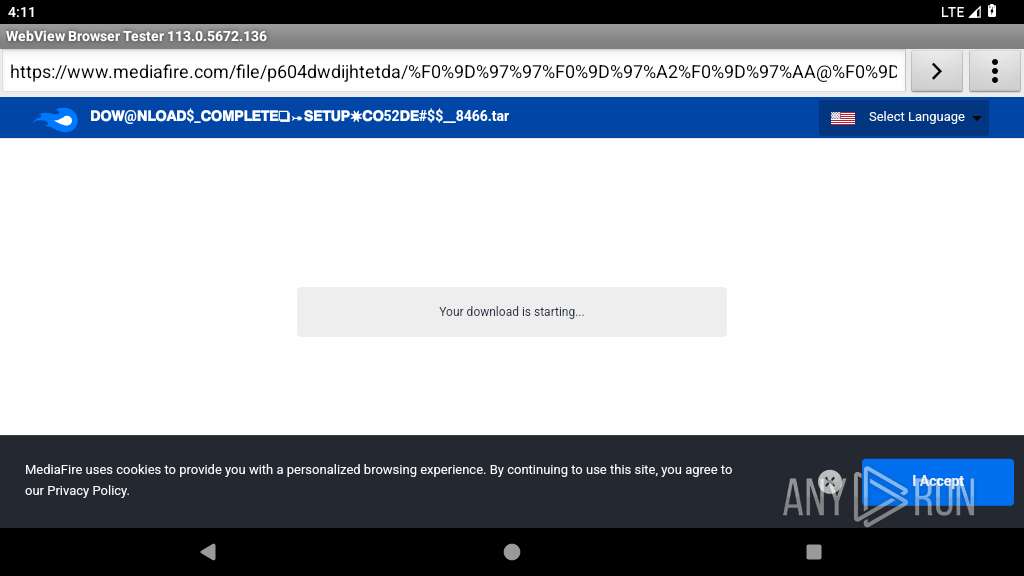
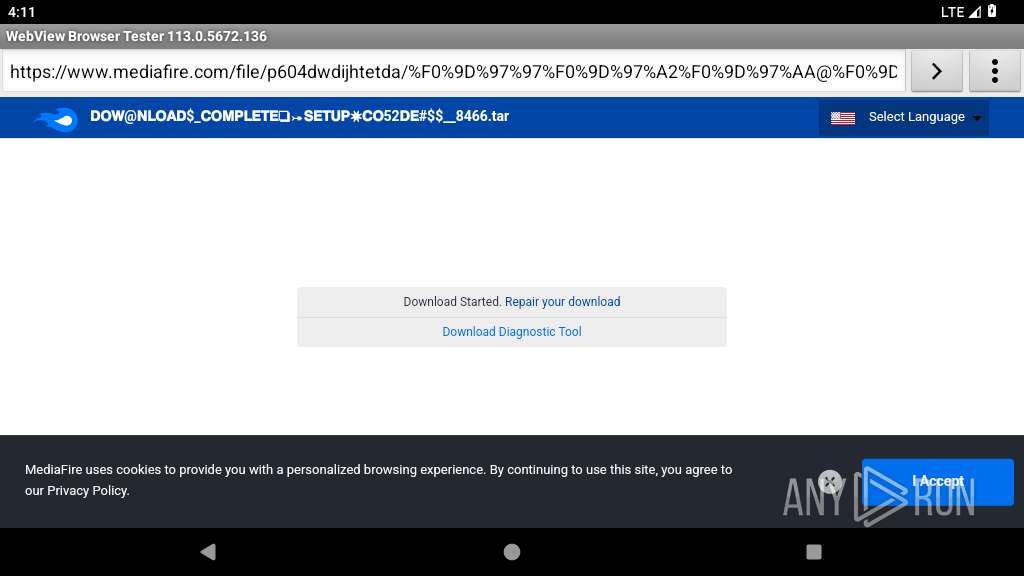
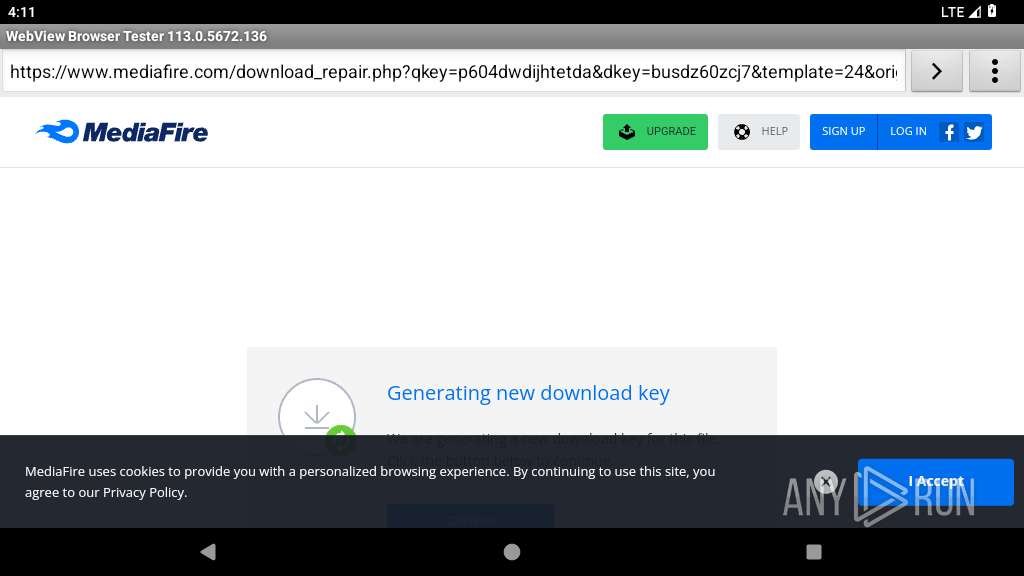
341 | netd | Potentially Bad Traffic | ET HUNTING File Sharing Related Domain (www .mediafire .com) in DNS Lookup |
341 | netd | Not Suspicious Traffic | INFO [ANY.RUN] Google Tag Manager analytics (googletagmanager .com) |
341 | netd | Potentially Bad Traffic | ET FILE_SHARING File Sharing Related Domain in DNS Lookup (download .mediafire .com) |
341 | netd | Not Suspicious Traffic | INFO [ANY.RUN] Google Hosted Libraries (ajax .googleapis .com) |