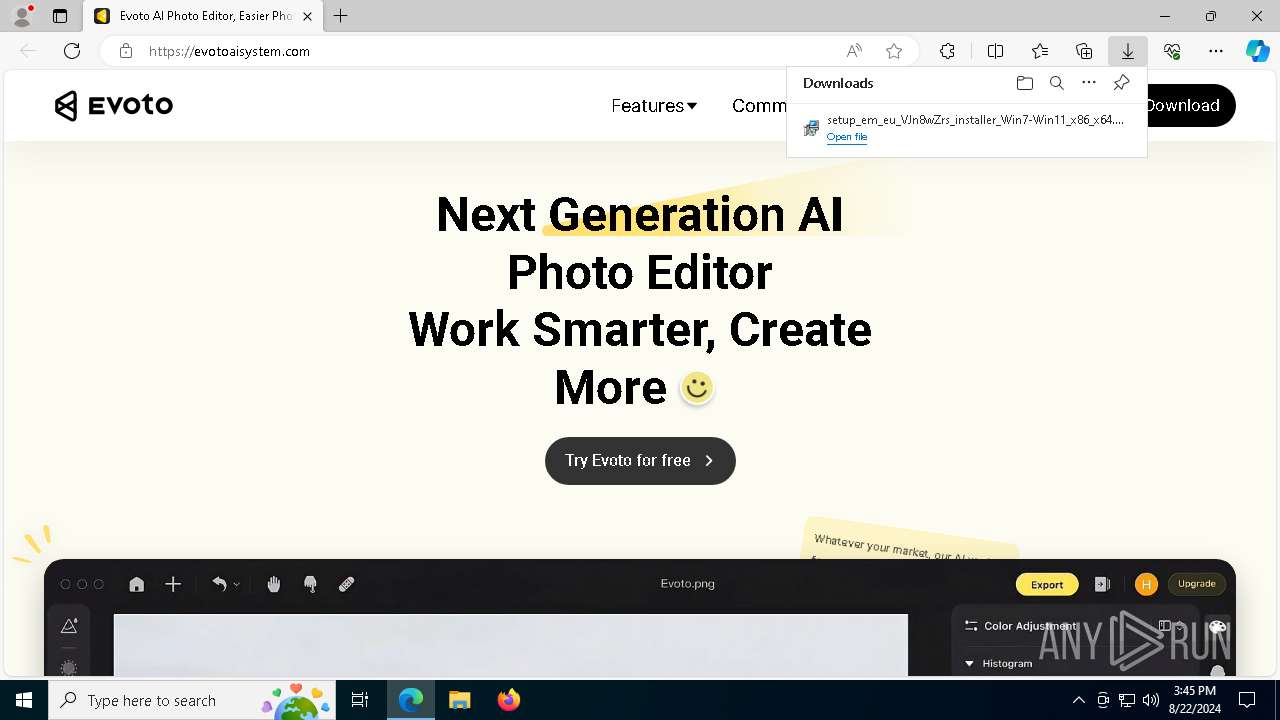
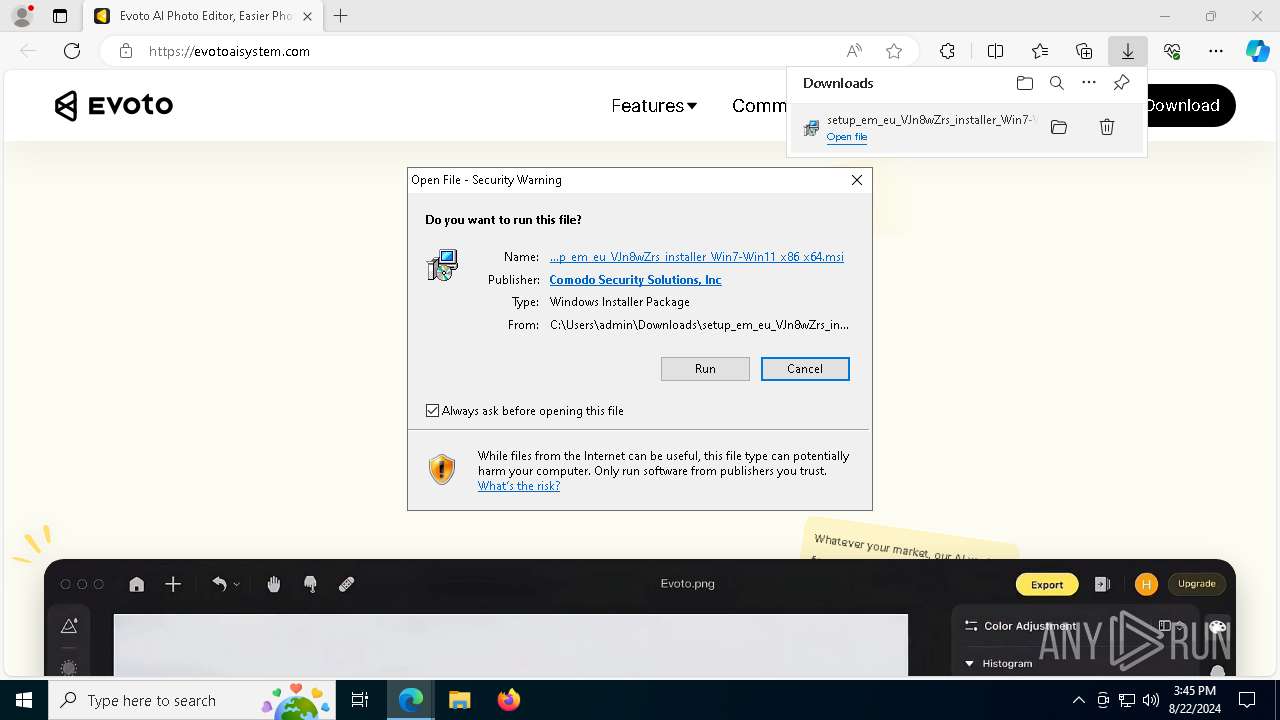
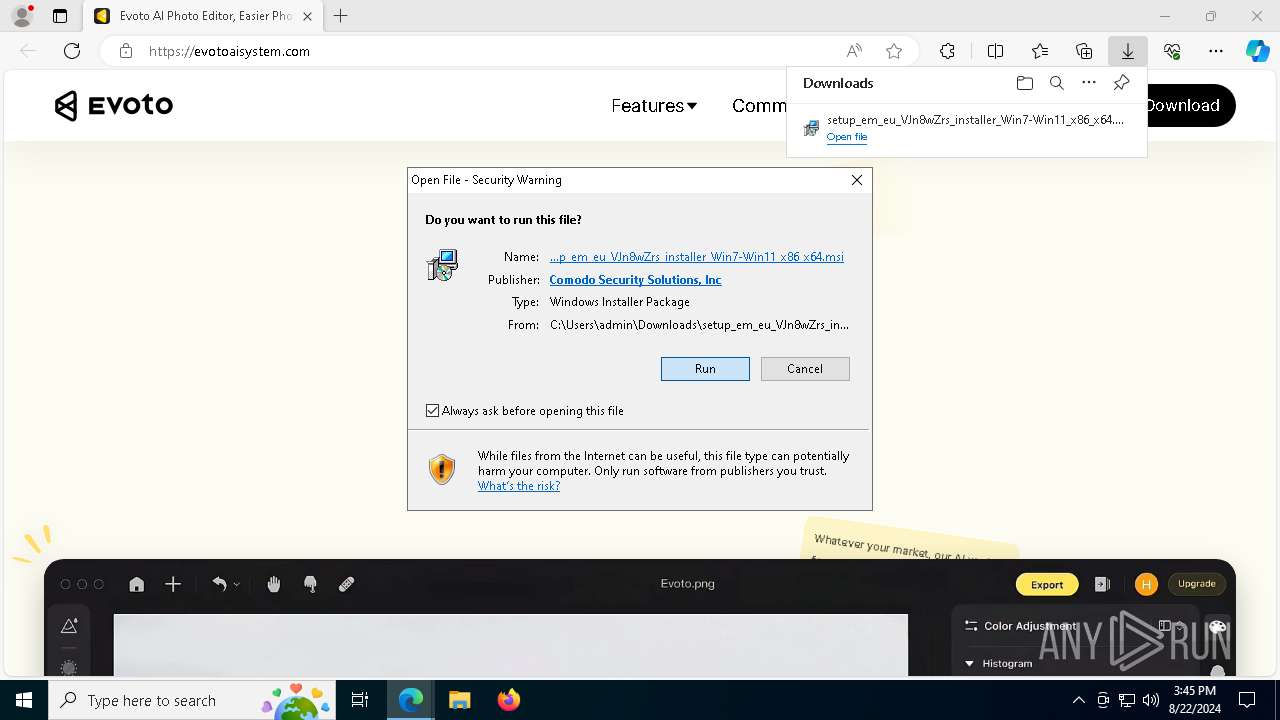
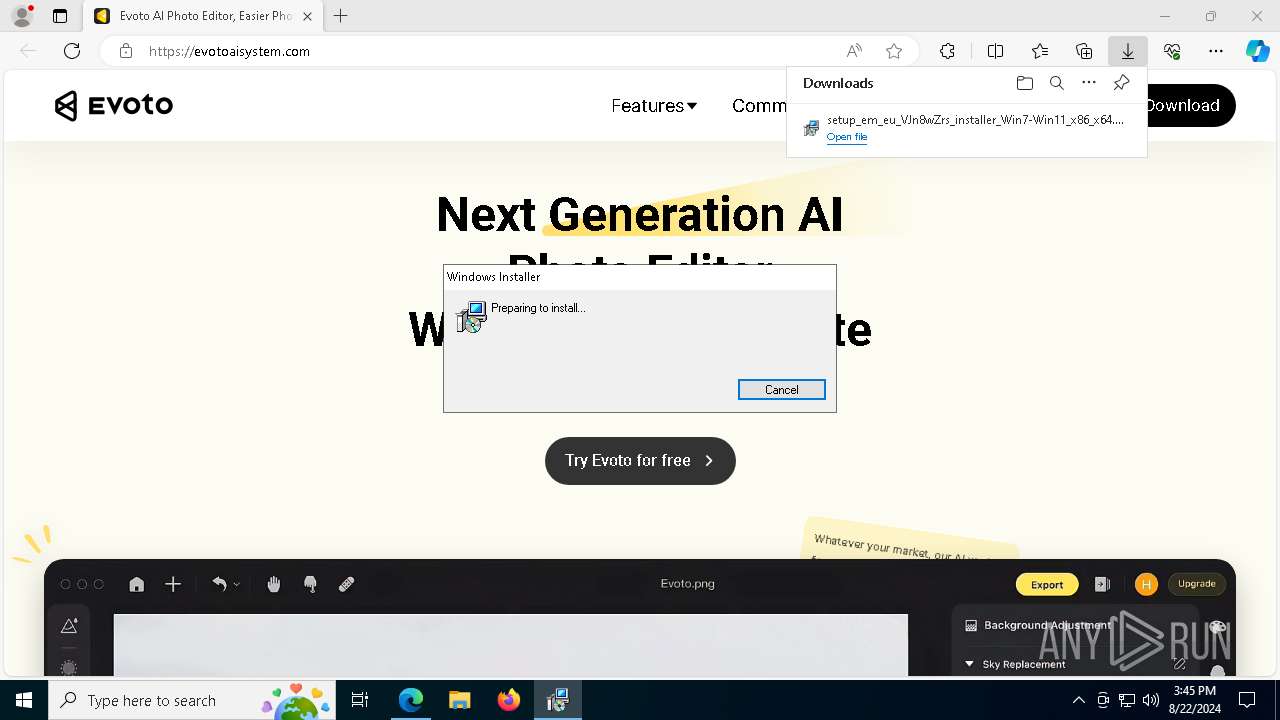
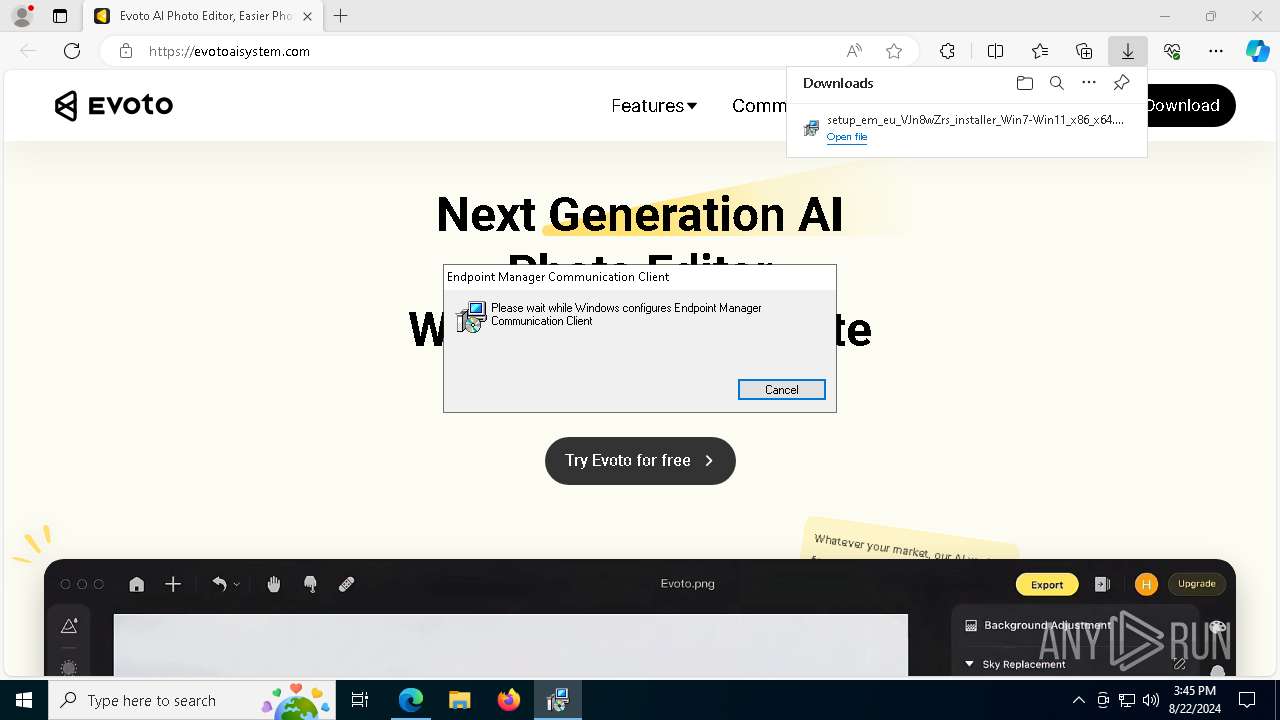
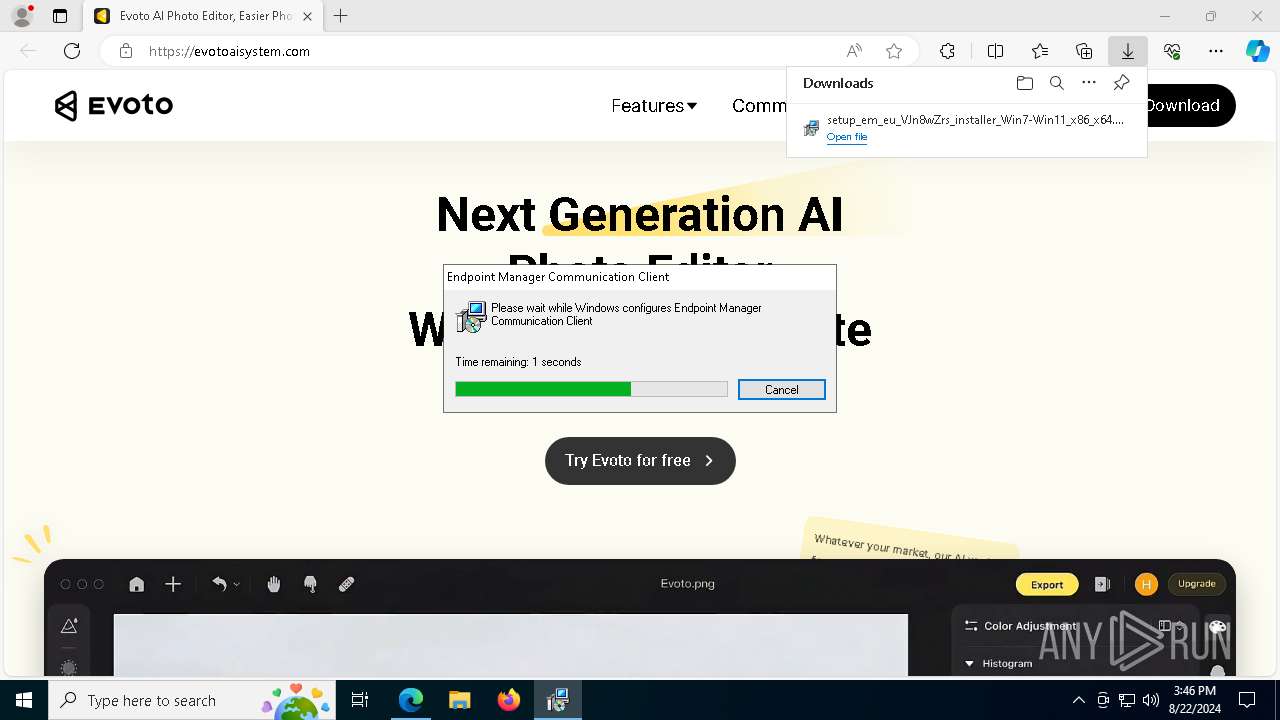
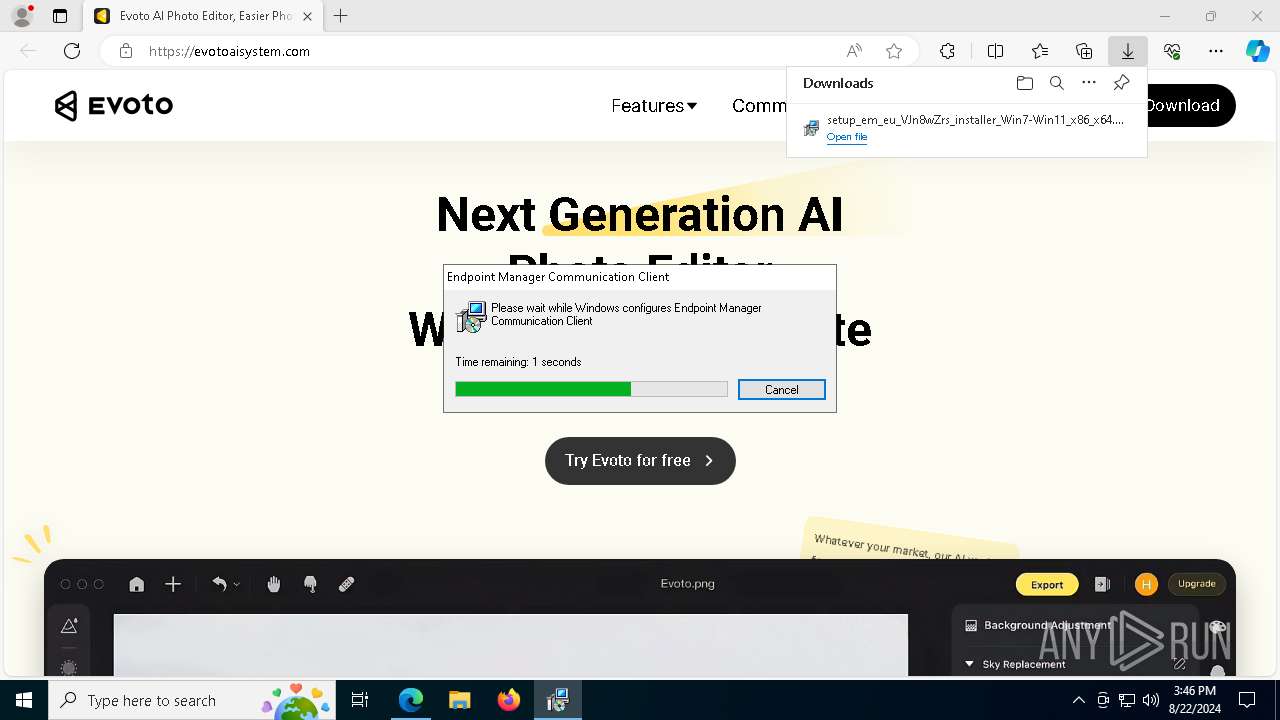
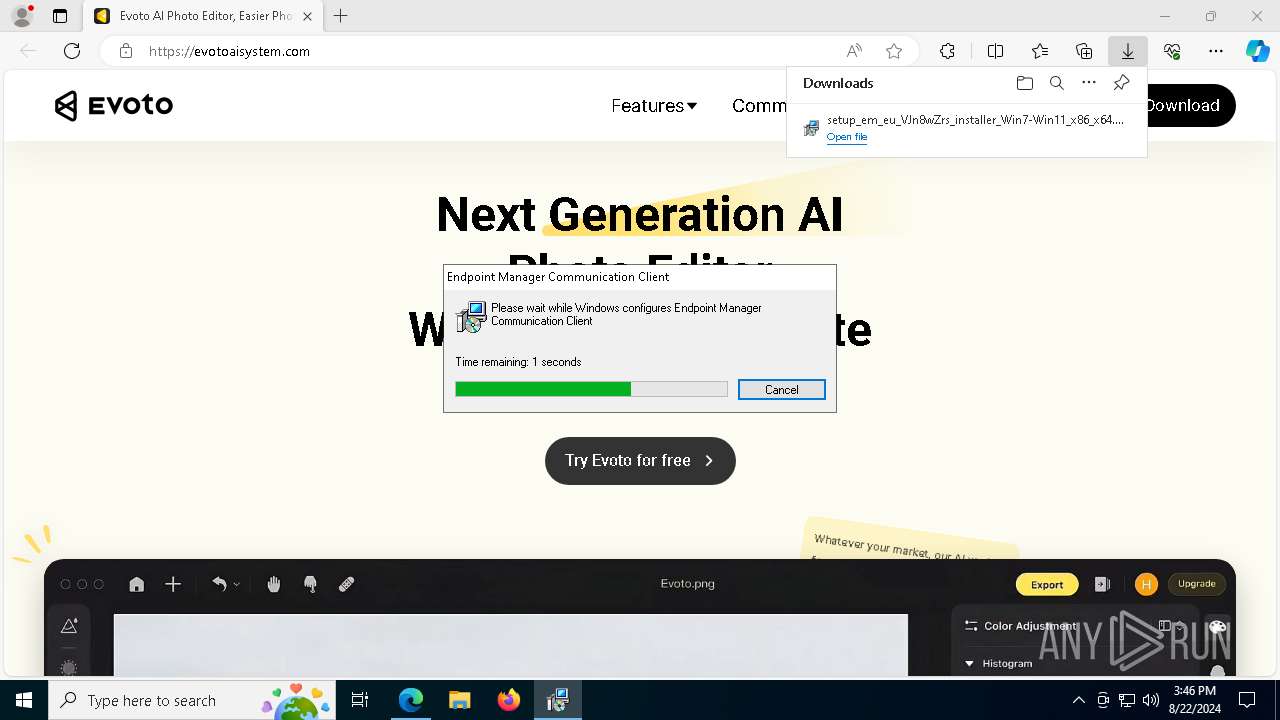
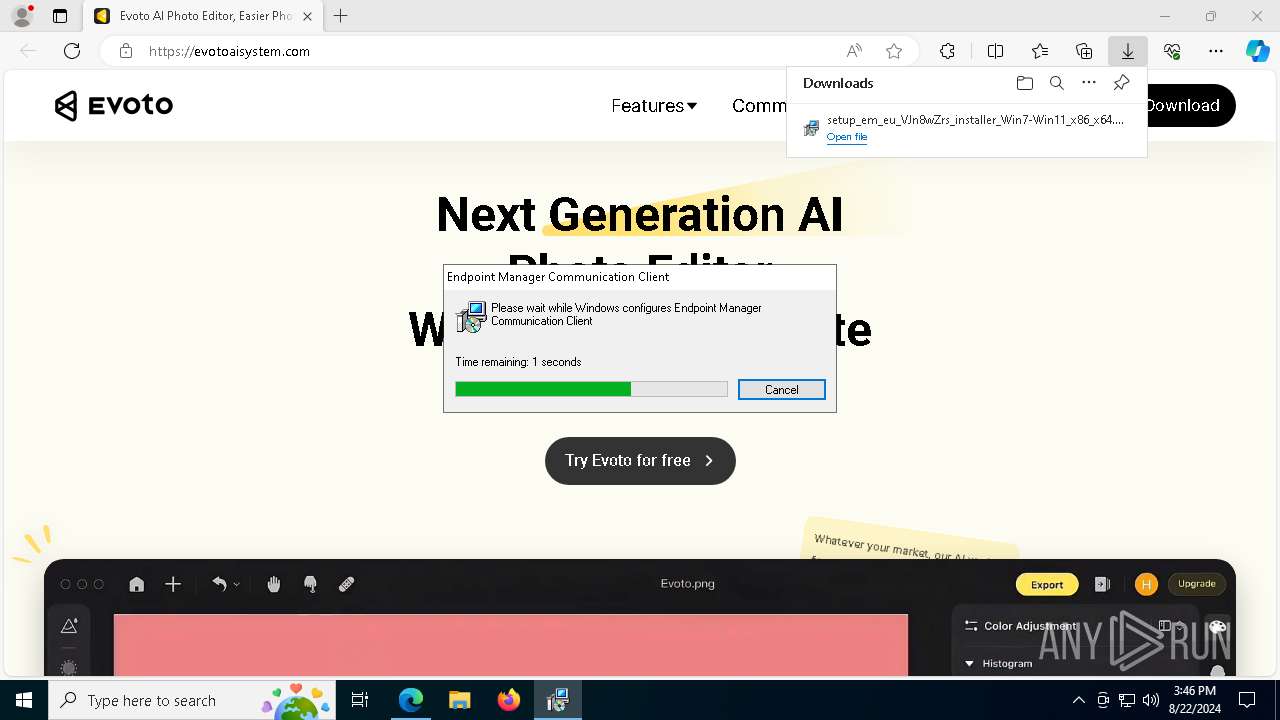
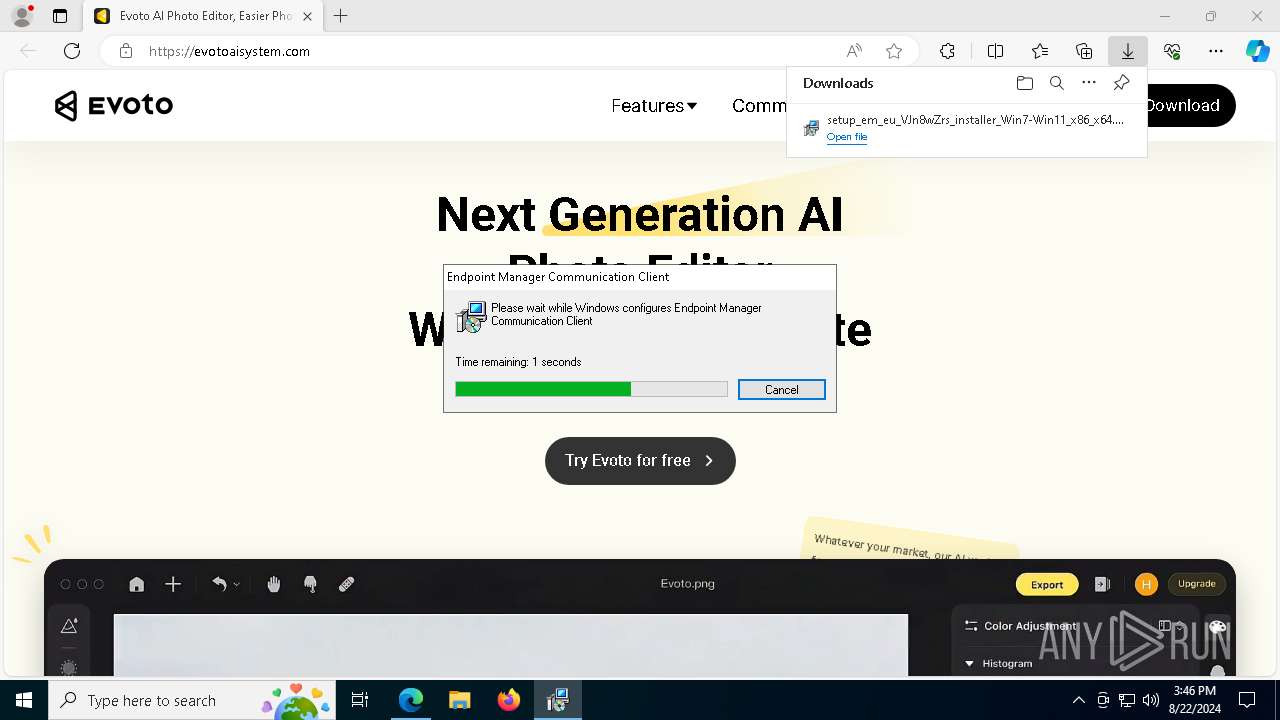
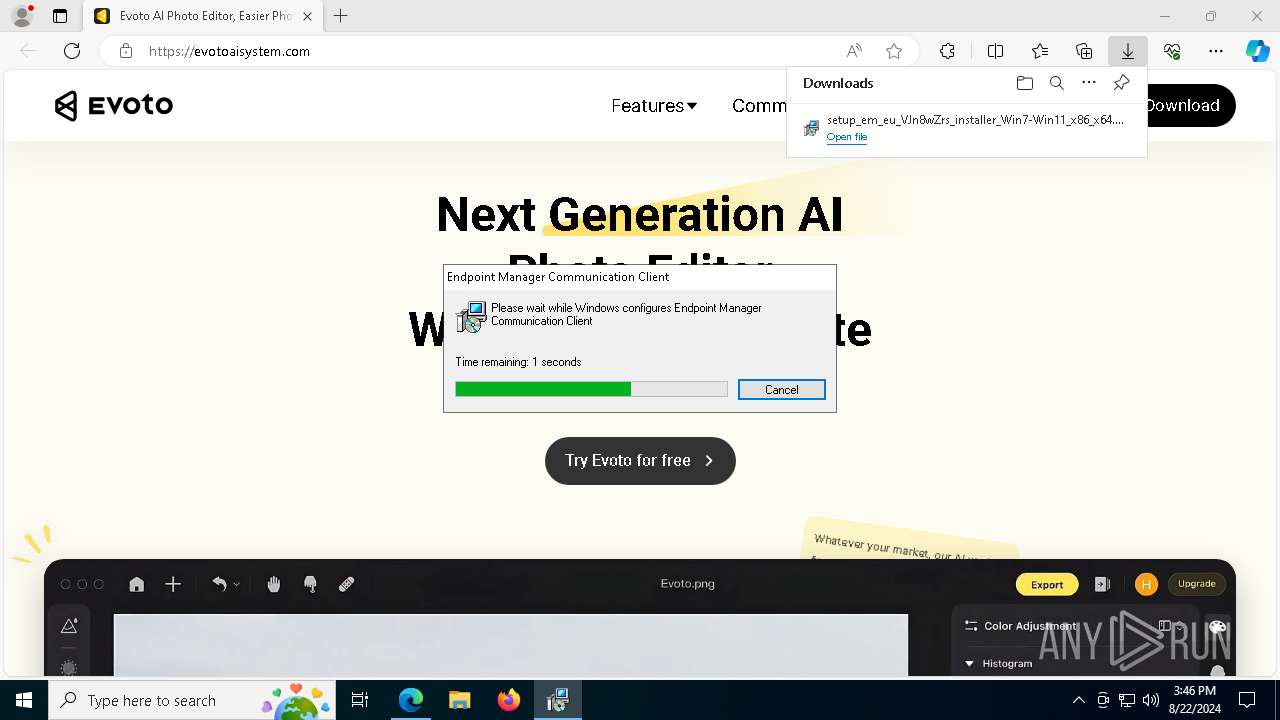
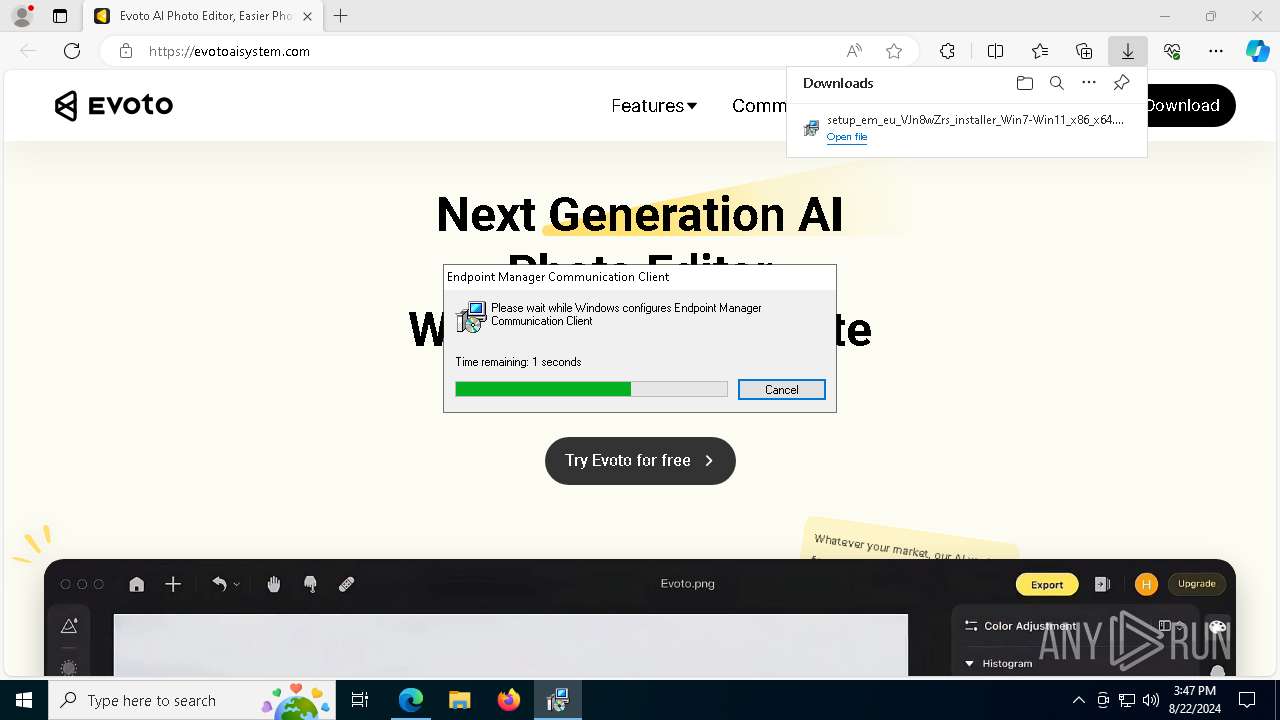
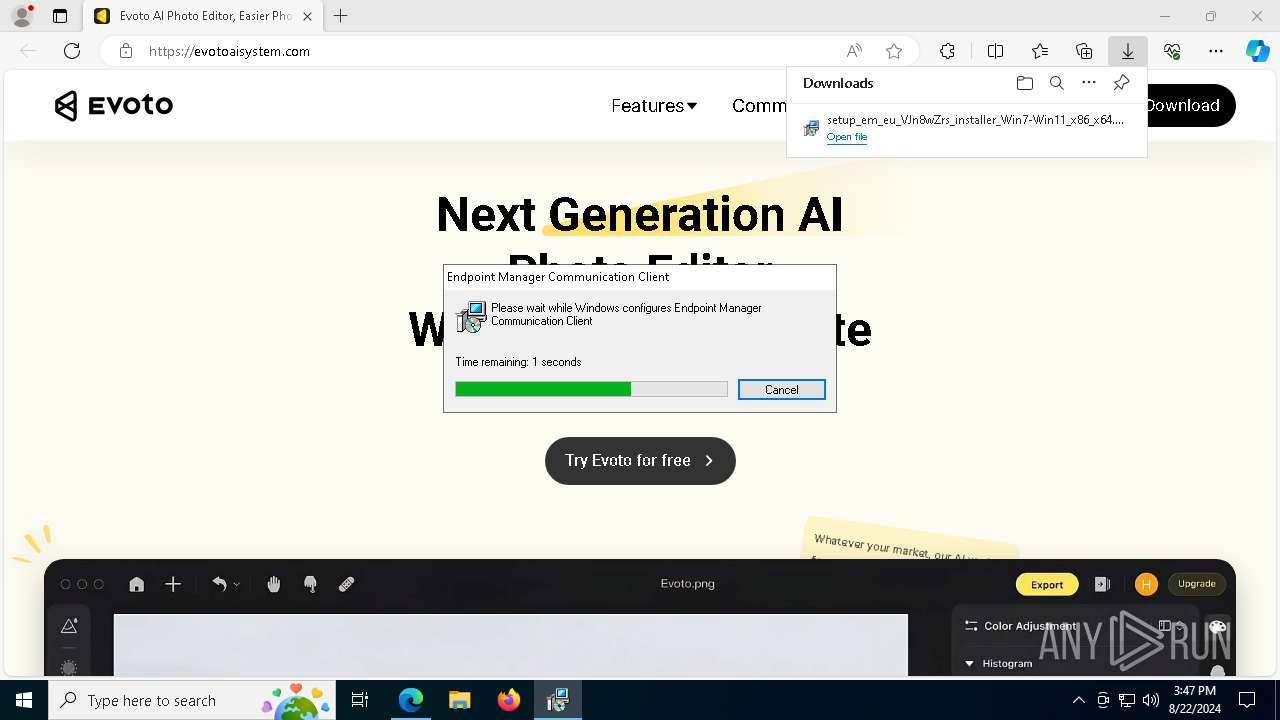
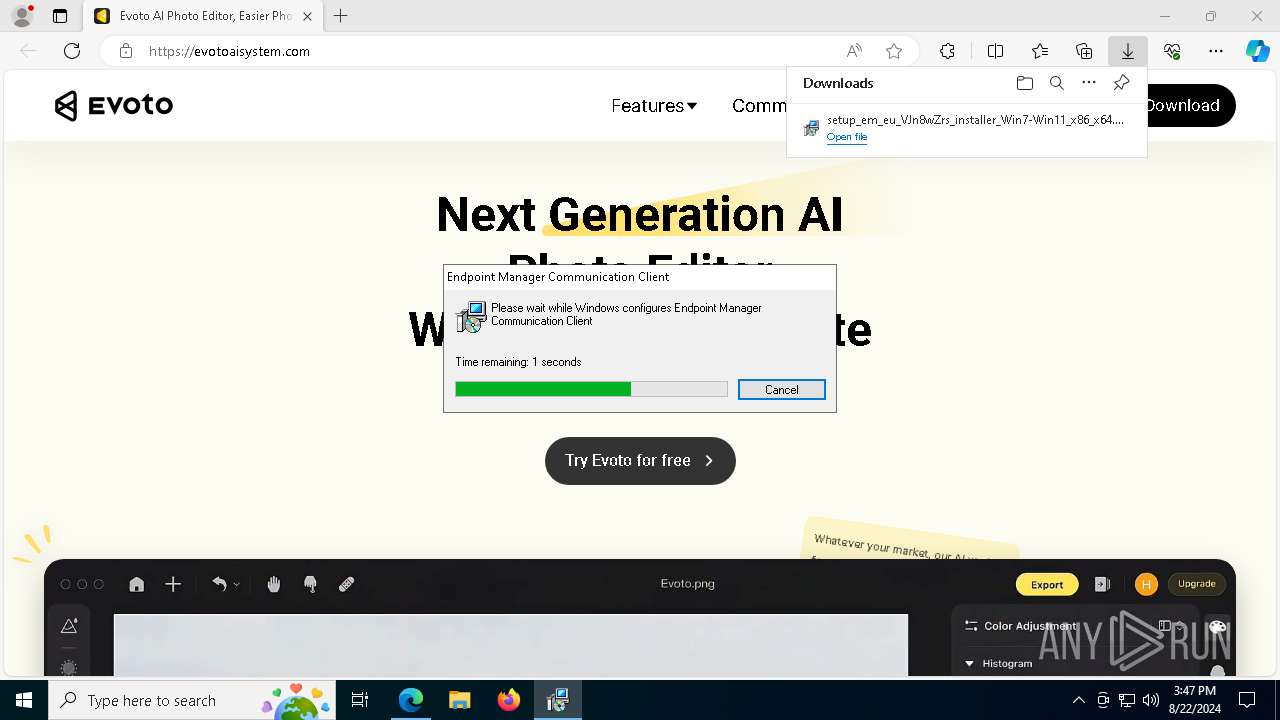
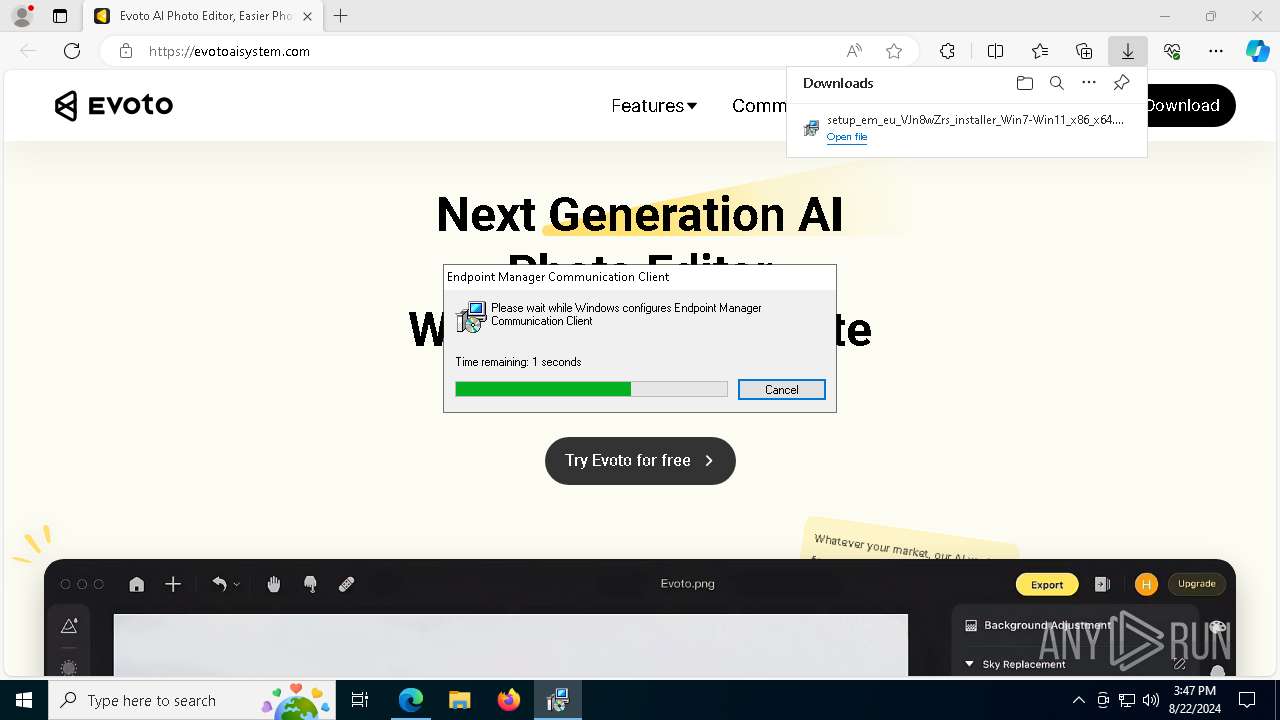
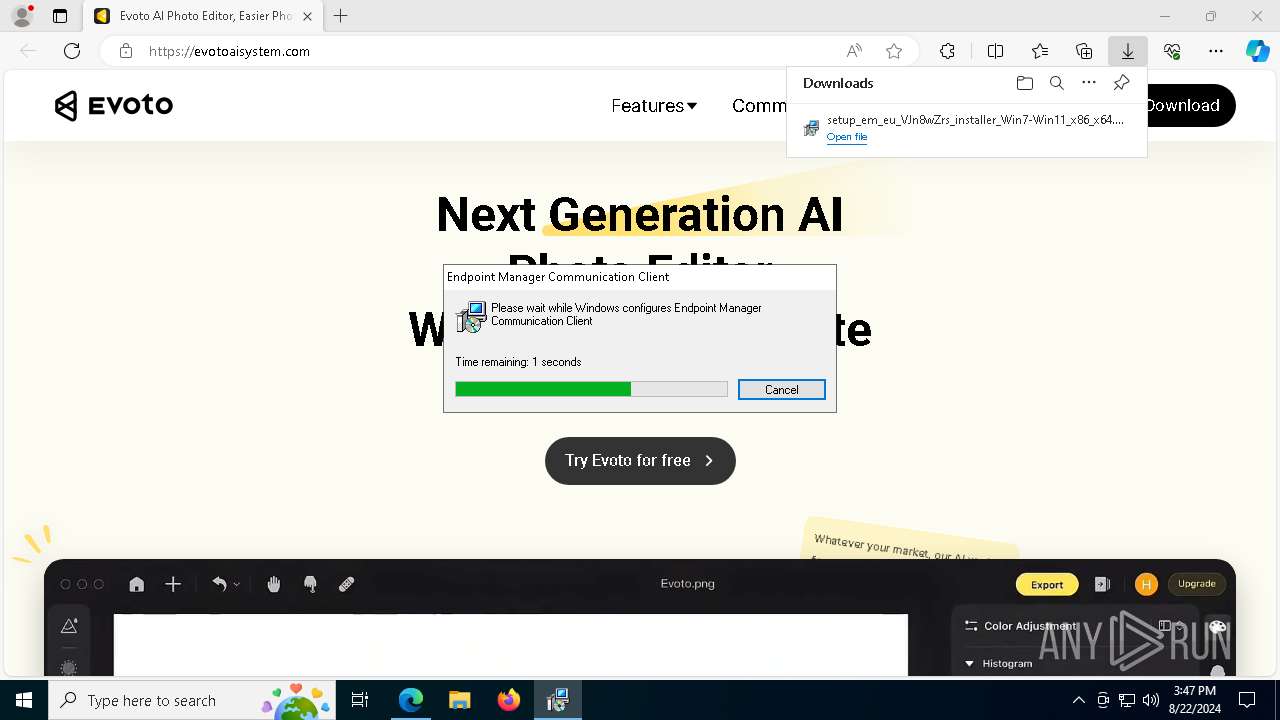
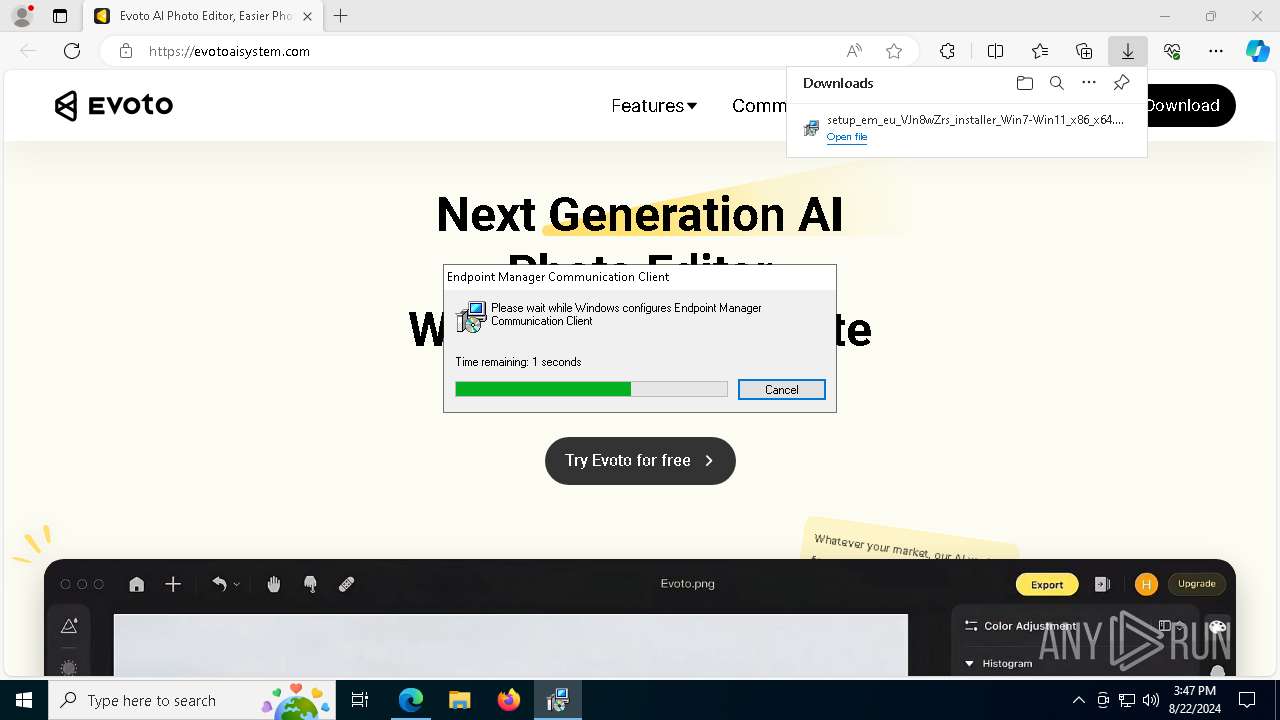
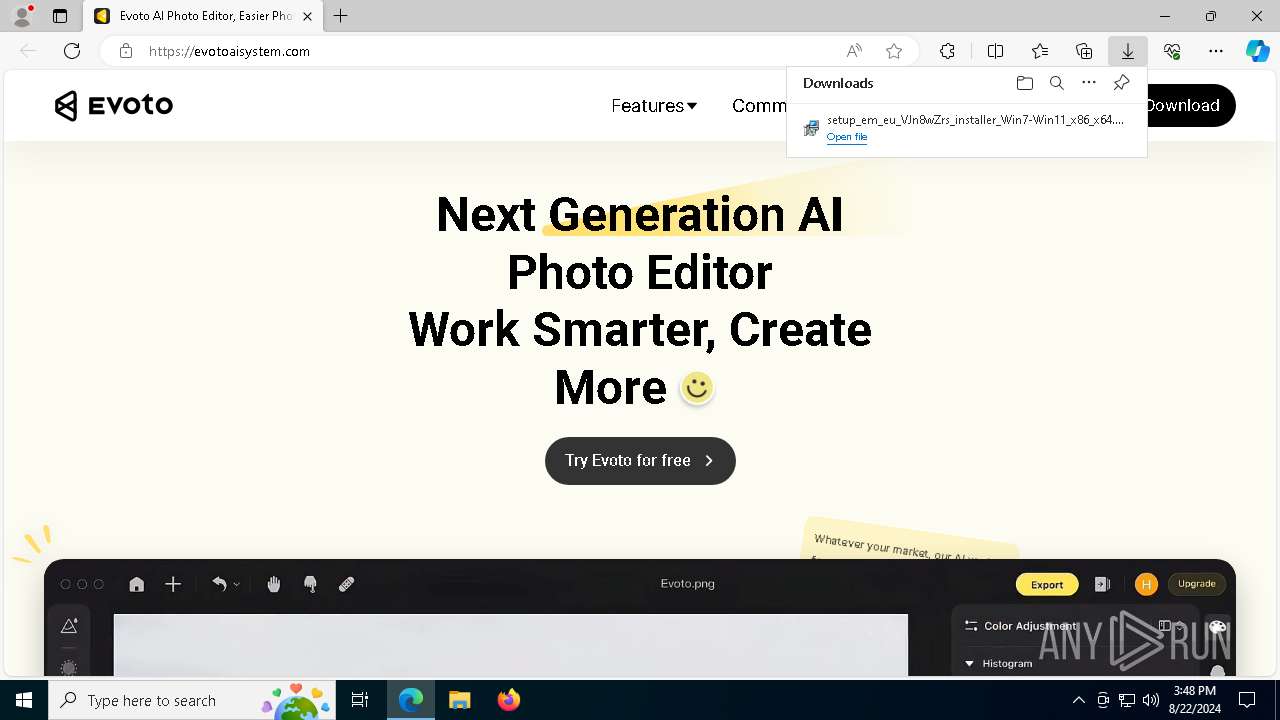
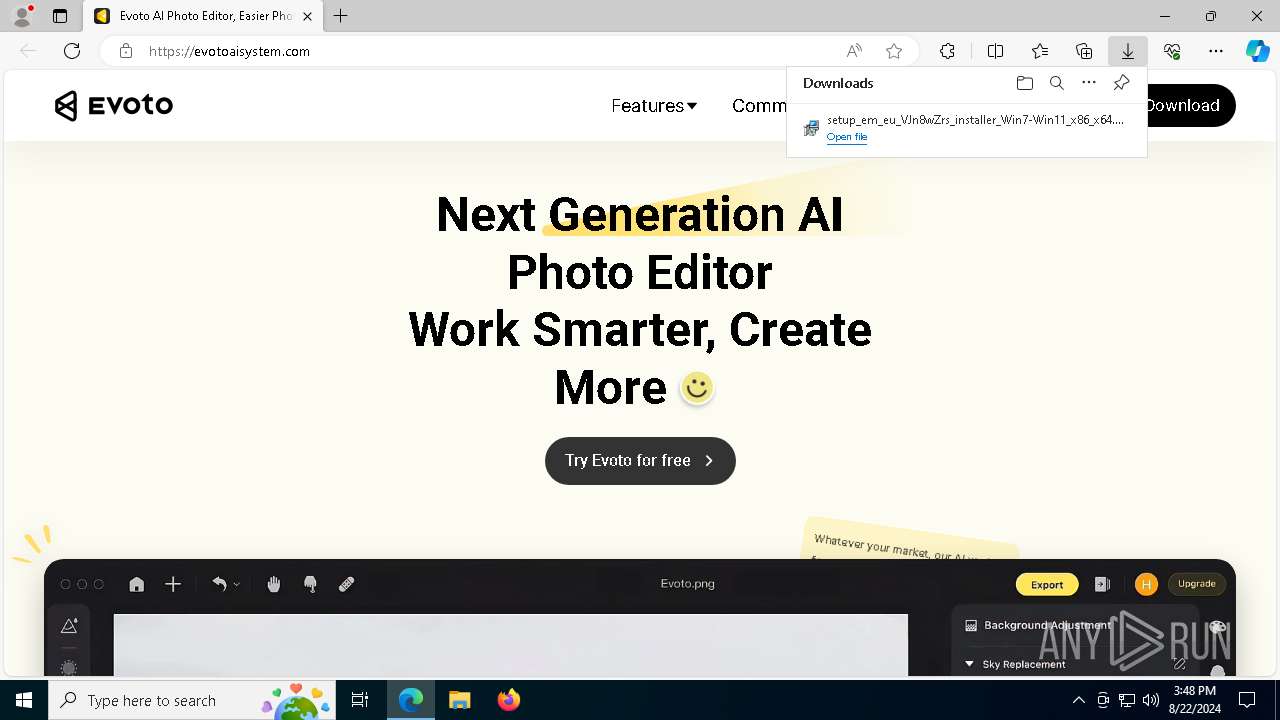
| URL: | evotoaisystem.com |
| Full analysis: | https://app.any.run/tasks/606fb92a-2524-42ec-a3e8-35ec19d88f60 |
| Verdict: | Malicious activity |
| Threats: | Rhadamanthys is a C++ information-stealing malware that extracts sensitive data from infiltrated machines. Its layered operational chain and advanced evasion tactics make it a major risk in cybersecurity landscapes. |
| Analysis date: | August 22, 2024, 15:43:29 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MD5: | 7A5B2A067917EAB33C7A833A31382ED8 |
| SHA1: | 76CE48EE5A4E194E7B25BAD8C87561FDE7DE44C6 |
| SHA256: | 25BB21DAD3C062217FE9814655096E64F772EF2880499BB2F1979F4645854F4F |
| SSDEEP: | 3:2OcWYKI:2zWYKI |
MALICIOUS
Changes the autorun value in the registry
- msiexec.exe (PID: 6276)
RHADAMANTHYS has been detected (SURICATA)
- OpenWith.exe (PID: 7468)
SUSPICIOUS
The process verifies whether the antivirus software is installed
- msiexec.exe (PID: 5544)
- cmd.exe (PID: 7904)
- msiexec.exe (PID: 6280)
- cmd.exe (PID: 3672)
- conhost.exe (PID: 2816)
- RmmService.exe (PID: 3696)
- ITSMAgent.exe (PID: 4680)
- ITSMAgent.exe (PID: 2268)
- ITSMAgent.exe (PID: 5724)
- RmmService.exe (PID: 3840)
- RmmService.exe (PID: 3140)
- RmmService.exe (PID: 6304)
- ITSMService.exe (PID: 2324)
- python_x86_Lib.exe (PID: 6112)
- msiexec.exe (PID: 6276)
Executes as Windows Service
- VSSVC.exe (PID: 8124)
- ITSMService.exe (PID: 2324)
- WmiApSrv.exe (PID: 5304)
- RmmService.exe (PID: 6304)
Checks Windows Trust Settings
- msiexec.exe (PID: 6276)
Reads the Windows owner or organization settings
- msiexec.exe (PID: 6276)
Drops the executable file immediately after the start
- msiexec.exe (PID: 6276)
- python_x86_Lib.exe (PID: 6112)
- RmmService.exe (PID: 3140)
The process creates files with name similar to system file names
- msiexec.exe (PID: 6276)
Process drops legitimate windows executable
- msiexec.exe (PID: 6276)
Starts CMD.EXE for commands execution
- msiexec.exe (PID: 2900)
- python_x86_Lib.exe (PID: 6112)
- RmmService.exe (PID: 3140)
- RmmService.exe (PID: 3840)
Process drops python dynamic module
- python_x86_Lib.exe (PID: 6112)
Executable content was dropped or overwritten
- python_x86_Lib.exe (PID: 6112)
- RmmService.exe (PID: 3140)
Reads security settings of Internet Explorer
- python_x86_Lib.exe (PID: 6112)
Reads the date of Windows installation
- python_x86_Lib.exe (PID: 6112)
The process drops C-runtime libraries
- msiexec.exe (PID: 6276)
Executing commands from ".cmd" file
- python_x86_Lib.exe (PID: 6112)
Loads Python modules
- RmmService.exe (PID: 3696)
- RmmService.exe (PID: 3140)
- RmmService.exe (PID: 6304)
- RmmService.exe (PID: 3840)
Searches for installed software
- ITSMService.exe (PID: 2324)
Found regular expressions for crypto-addresses (YARA)
- ITSMService.exe (PID: 2324)
The process checks if it is being run in the virtual environment
- RmmService.exe (PID: 6304)
- OpenWith.exe (PID: 7468)
Application launched itself
- RmmService.exe (PID: 6304)
The executable file from the user directory is run by the CMD process
- AutoIt3.exe (PID: 5148)
- AutoIt3.exe (PID: 6260)
Executes application which crashes
- MicrosoftEdgeUpdateCore.exe (PID: 4100)
- MicrosoftEdgeUpdateCore.exe (PID: 6552)
Contacting a server suspected of hosting an CnC
- OpenWith.exe (PID: 7468)
INFO
Application launched itself
- msedge.exe (PID: 6560)
Reads Microsoft Office registry keys
- msedge.exe (PID: 6560)
Checks supported languages
- identity_helper.exe (PID: 7736)
- msiexec.exe (PID: 6276)
- msiexec.exe (PID: 6280)
- python_x86_Lib.exe (PID: 6112)
- msiexec.exe (PID: 2900)
- ITSMAgent.exe (PID: 5724)
- ITSMService.exe (PID: 2324)
- ITSMAgent.exe (PID: 4680)
- ITSMAgent.exe (PID: 2268)
- RmmService.exe (PID: 3696)
- RmmService.exe (PID: 3140)
- RmmService.exe (PID: 3840)
- RmmService.exe (PID: 6304)
- AutoIt3.exe (PID: 6260)
- AutoIt3.exe (PID: 5148)
- MicrosoftEdgeUpdateCore.exe (PID: 6552)
- MicrosoftEdgeUpdateCore.exe (PID: 4100)
Reads the computer name
- identity_helper.exe (PID: 7736)
- msiexec.exe (PID: 6276)
- msiexec.exe (PID: 6280)
- msiexec.exe (PID: 2900)
- python_x86_Lib.exe (PID: 6112)
- ITSMService.exe (PID: 2324)
- ITSMAgent.exe (PID: 5724)
- ITSMAgent.exe (PID: 4680)
- ITSMAgent.exe (PID: 2268)
- RmmService.exe (PID: 3696)
- RmmService.exe (PID: 3840)
- RmmService.exe (PID: 6304)
- RmmService.exe (PID: 3140)
Reads Environment values
- identity_helper.exe (PID: 7736)
- ITSMService.exe (PID: 2324)
The process uses the downloaded file
- msedge.exe (PID: 780)
- msedge.exe (PID: 6560)
Reads security settings of Internet Explorer
- msiexec.exe (PID: 5544)
Reads the software policy settings
- msiexec.exe (PID: 5544)
- msiexec.exe (PID: 6276)
Reads the machine GUID from the registry
- msiexec.exe (PID: 6276)
- ITSMService.exe (PID: 2324)
- RmmService.exe (PID: 3140)
- RmmService.exe (PID: 3840)
Executable content was dropped or overwritten
- msiexec.exe (PID: 6276)
Creates files in the program directory
- python_x86_Lib.exe (PID: 6112)
- ITSMService.exe (PID: 2324)
- RmmService.exe (PID: 3696)
- RmmService.exe (PID: 6304)
- RmmService.exe (PID: 3840)
- RmmService.exe (PID: 3140)
Create files in a temporary directory
- python_x86_Lib.exe (PID: 6112)
- RmmService.exe (PID: 3840)
- RmmService.exe (PID: 3140)
Process checks computer location settings
- python_x86_Lib.exe (PID: 6112)
Creates a software uninstall entry
- msiexec.exe (PID: 6276)
Checks proxy server information
- RmmService.exe (PID: 3140)
- RmmService.exe (PID: 3840)
Reads mouse settings
- AutoIt3.exe (PID: 5148)
- AutoIt3.exe (PID: 6260)
Reads CPU info
- AutoIt3.exe (PID: 5148)
- AutoIt3.exe (PID: 6260)
Reads Windows Product ID
- AutoIt3.exe (PID: 6260)
- AutoIt3.exe (PID: 5148)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
233
Monitored processes
82
Malicious processes
16
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 460 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=5584 --field-trial-handle=2420,i,4698734022829198231,10326577520936011705,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 780 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=quarantine.mojom.Quarantine --lang=en-US --service-sandbox-type=none --no-appcompat-clear --mojo-platform-channel-handle=5468 --field-trial-handle=2420,i,4698734022829198231,10326577520936011705,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 1064 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | RmmService.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1072 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=6808 --field-trial-handle=2420,i,4698734022829198231,10326577520936011705,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 1104 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=gpu-process --disable-gpu-sandbox --use-gl=disabled --gpu-vendor-id=5140 --gpu-device-id=140 --gpu-sub-system-id=0 --gpu-revision=0 --gpu-driver-version=10.0.19041.3636 --no-appcompat-clear --gpu-preferences=WAAAAAAAAADoAAAMAAAAAAAAAAAAAAAAAABgAAAAAAA4AAAAAAAAAAAAAABEAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAGAAAAAAAAAAYAAAAAAAAAAgAAAAAAAAACAAAAAAAAAAIAAAAAAAAAA== --mojo-platform-channel-handle=5464 --field-trial-handle=2420,i,4698734022829198231,10326577520936011705,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 1360 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=5672 --field-trial-handle=2420,i,4698734022829198231,10326577520936011705,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 1440 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | RmmService.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2144 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=7184 --field-trial-handle=2420,i,4698734022829198231,10326577520936011705,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 2268 | "C:\Program Files (x86)\COMODO\Endpoint Manager\ITSMAgent.exe" | C:\Program Files (x86)\COMODO\Endpoint Manager\ITSMAgent.exe | ITSMService.exe | ||||||||||||
User: admin Company: COMODO Integrity Level: MEDIUM Description: Endpoint Manager Tray Application Exit code: 0 Version: 9.1.48792.24030 Modules
| |||||||||||||||
| 2324 | "C:\Program Files (x86)\COMODO\Endpoint Manager\ITSMService.exe" | C:\Program Files (x86)\COMODO\Endpoint Manager\ITSMService.exe | services.exe | ||||||||||||
User: SYSTEM Company: COMODO Integrity Level: SYSTEM Description: Endpoint Manager Service Application Version: 9.1.48792.24030 Modules
| |||||||||||||||
Total events
38 605
Read events
37 929
Write events
652
Delete events
24
Modification events
| (PID) Process: | (6560) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (6560) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
| (PID) Process: | (6560) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\ThirdParty |
| Operation: | write | Name: | StatusCodes |
Value: | |||
| (PID) Process: | (6560) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\ThirdParty |
| Operation: | write | Name: | StatusCodes |
Value: 01000000 | |||
| (PID) Process: | (6560) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | state |
Value: 1 | |||
| (PID) Process: | (6560) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\EdgeUpdate\ClientState\{56EB18F8-B008-4CBD-B6D2-8C97FE7E9062} |
| Operation: | write | Name: | dr |
Value: 1 | |||
| (PID) Process: | (6560) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\StabilityMetrics |
| Operation: | write | Name: | user_experience_metrics.stability.exited_cleanly |
Value: 0 | |||
| (PID) Process: | (6560) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge |
| Operation: | write | Name: | UsageStatsInSample |
Value: 1 | |||
| (PID) Process: | (6560) msedge.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\EdgeUpdate\ClientStateMedium\{56EB18F8-B008-4CBD-B6D2-8C97FE7E9062} |
| Operation: | write | Name: | usagestats |
Value: 0 | |||
| (PID) Process: | (6560) msedge.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\EdgeUpdate\ClientStateMedium\{56EB18F8-B008-4CBD-B6D2-8C97FE7E9062} |
| Operation: | write | Name: | urlstats |
Value: 0 | |||
Executable files
89
Suspicious files
601
Text files
2 366
Unknown types
75
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6560 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\parcel_tracking_db\LOG.old~RF11db59.TMP | — | |
MD5:— | SHA256:— | |||
| 6560 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\parcel_tracking_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 6560 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\discounts_db\LOG.old~RF11db59.TMP | — | |
MD5:— | SHA256:— | |||
| 6560 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\PersistentOriginTrials\LOG.old~RF11db59.TMP | — | |
MD5:— | SHA256:— | |||
| 6560 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\PersistentOriginTrials\LOG.old | — | |
MD5:— | SHA256:— | |||
| 6560 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\discounts_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 6560 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\commerce_subscription_db\LOG.old~RF11db78.TMP | — | |
MD5:— | SHA256:— | |||
| 6560 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\commerce_subscription_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 6560 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\EdgePushStorageWithConnectTokenAndKey\LOG.old~RF11db88.TMP | — | |
MD5:— | SHA256:— | |||
| 6560 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\EdgePushStorageWithConnectTokenAndKey\LOG.old | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
42
TCP/UDP connections
86
DNS requests
77
Threats
1
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
8152 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
2628 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
1080 | svchost.exe | HEAD | 200 | 2.19.126.155:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/062b65bc-b6a4-4f5a-8413-7218292237fe?P1=1724898807&P2=404&P3=2&P4=MS%2fKXR7x6itw0iYCtDwrta2q%2bX2FHXA8hm%2bO6GJhpdsdqARsGkPVhhedjsP1P%2biRcsr4pboNTvAHUV3KVbBAFQ%3d%3d | unknown | — | — | whitelisted |
1080 | svchost.exe | GET | 206 | 2.19.126.155:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/062b65bc-b6a4-4f5a-8413-7218292237fe?P1=1724898807&P2=404&P3=2&P4=MS%2fKXR7x6itw0iYCtDwrta2q%2bX2FHXA8hm%2bO6GJhpdsdqARsGkPVhhedjsP1P%2biRcsr4pboNTvAHUV3KVbBAFQ%3d%3d | unknown | — | — | whitelisted |
6412 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
1080 | svchost.exe | GET | 206 | 2.19.126.155:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/062b65bc-b6a4-4f5a-8413-7218292237fe?P1=1724898807&P2=404&P3=2&P4=MS%2fKXR7x6itw0iYCtDwrta2q%2bX2FHXA8hm%2bO6GJhpdsdqARsGkPVhhedjsP1P%2biRcsr4pboNTvAHUV3KVbBAFQ%3d%3d | unknown | — | — | whitelisted |
1080 | svchost.exe | GET | 206 | 2.19.126.155:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/062b65bc-b6a4-4f5a-8413-7218292237fe?P1=1724898807&P2=404&P3=2&P4=MS%2fKXR7x6itw0iYCtDwrta2q%2bX2FHXA8hm%2bO6GJhpdsdqARsGkPVhhedjsP1P%2biRcsr4pboNTvAHUV3KVbBAFQ%3d%3d | unknown | — | — | whitelisted |
1080 | svchost.exe | GET | 206 | 2.19.126.155:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/062b65bc-b6a4-4f5a-8413-7218292237fe?P1=1724898807&P2=404&P3=2&P4=MS%2fKXR7x6itw0iYCtDwrta2q%2bX2FHXA8hm%2bO6GJhpdsdqARsGkPVhhedjsP1P%2biRcsr4pboNTvAHUV3KVbBAFQ%3d%3d | unknown | — | — | whitelisted |
1080 | svchost.exe | GET | 206 | 2.19.126.155:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/062b65bc-b6a4-4f5a-8413-7218292237fe?P1=1724898807&P2=404&P3=2&P4=MS%2fKXR7x6itw0iYCtDwrta2q%2bX2FHXA8hm%2bO6GJhpdsdqARsGkPVhhedjsP1P%2biRcsr4pboNTvAHUV3KVbBAFQ%3d%3d | unknown | — | — | whitelisted |
1080 | svchost.exe | GET | 206 | 2.19.126.155:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/062b65bc-b6a4-4f5a-8413-7218292237fe?P1=1724898807&P2=404&P3=2&P4=MS%2fKXR7x6itw0iYCtDwrta2q%2bX2FHXA8hm%2bO6GJhpdsdqARsGkPVhhedjsP1P%2biRcsr4pboNTvAHUV3KVbBAFQ%3d%3d | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4200 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1356 | RUXIMICS.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
2120 | MoUsoCoreWorker.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
6892 | msedge.exe | 13.107.42.16:443 | config.edge.skype.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
6560 | msedge.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
6892 | msedge.exe | 89.208.103.60:80 | evotoaisystem.com | AEZA GROUP Ltd | DE | unknown |
6892 | msedge.exe | 204.79.197.239:443 | edge.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | unknown |
6892 | msedge.exe | 13.107.6.158:443 | business.bing.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
6892 | msedge.exe | 89.208.103.60:443 | evotoaisystem.com | AEZA GROUP Ltd | DE | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
config.edge.skype.com |
| whitelisted |
evotoaisystem.com |
| unknown |
edge.microsoft.com |
| whitelisted |
business.bing.com |
| whitelisted |
edge-mobile-static.azureedge.net |
| whitelisted |
bzib.nelreports.net |
| whitelisted |
www.bing.com |
| whitelisted |
xpaywalletcdn.azureedge.net |
| whitelisted |
Threats
1 ETPRO signatures available at the full report
Process | Message |
|---|---|
ITSMService.exe | QCoreApplication::applicationDirPath: Please instantiate the QApplication object first
|
ITSMService.exe | Try to find oem.strings in "C:/Program Files (x86)/COMODO/Endpoint Manager/oem.strings"
|
ITSMService.exe | OEM strings file does not exists! "C:/Program Files (x86)/COMODO/Endpoint Manager/oem.strings"
|
ITSMService.exe | Log dir is 'C:/ProgramData/COMODO/Endpoint Manager'
|
ITSMAgent.exe | Try to find oem.strings in "C:/Program Files (x86)/COMODO/Endpoint Manager/oem.strings"
|
ITSMAgent.exe | OEM strings file does not exists! "C:/Program Files (x86)/COMODO/Endpoint Manager/oem.strings"
|
ITSMAgent.exe | Log dir is 'C:/ProgramData/COMODO/Endpoint Manager'
|
ITSMAgent.exe | Try to find oem.strings in "C:/Program Files (x86)/COMODO/Endpoint Manager/oem.strings"
|
ITSMAgent.exe | OEM strings file does not exists! "C:/Program Files (x86)/COMODO/Endpoint Manager/oem.strings"
|
ITSMAgent.exe | Try to find oem.strings in "C:/Program Files (x86)/COMODO/Endpoint Manager/oem.strings"
|