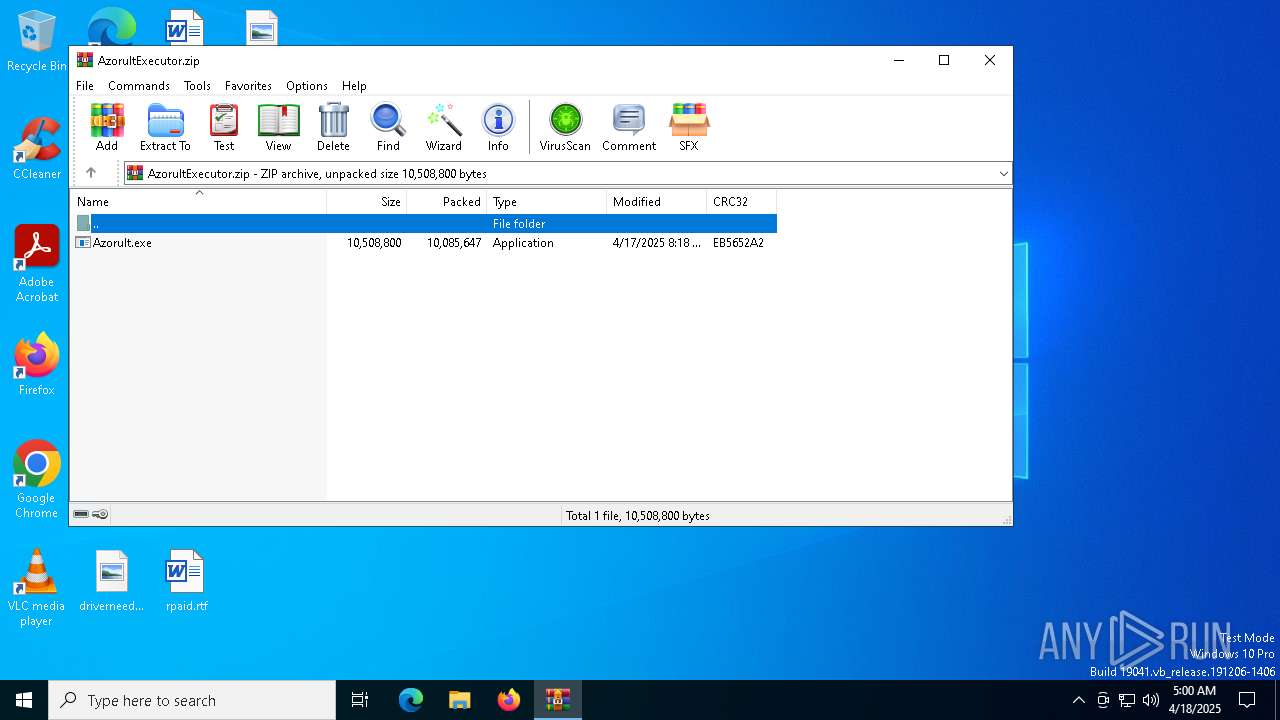
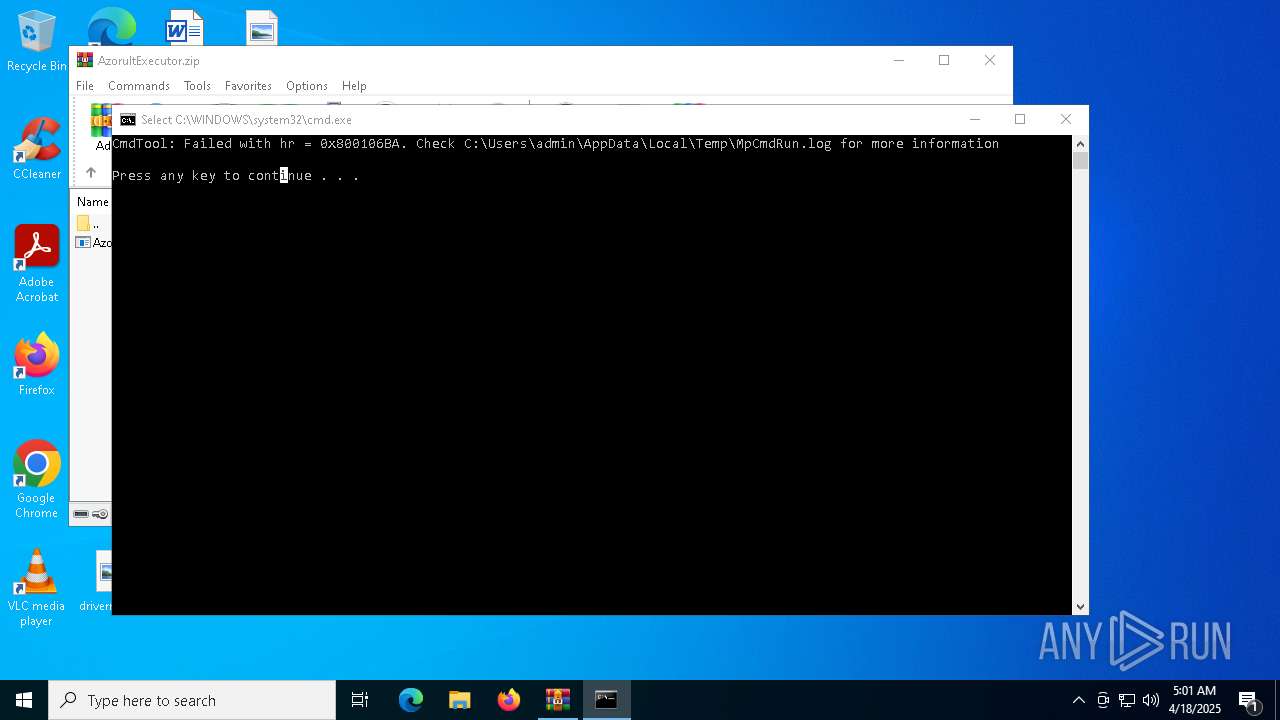
| File name: | AzorultExecutor.zip |
| Full analysis: | https://app.any.run/tasks/13557be3-2921-4dd1-9283-184a2b6960be |
| Verdict: | Malicious activity |
| Threats: | Remote access trojans (RATs) are a type of malware that enables attackers to establish complete to partial control over infected computers. Such malicious programs often have a modular design, offering a wide range of functionalities for conducting illicit activities on compromised systems. Some of the most common features of RATs include access to the users’ data, webcam, and keystrokes. This malware is often distributed through phishing emails and links. |
| Analysis date: | April 18, 2025, 05:00:04 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=deflate |
| MD5: | 8AD92677FF9A9A1B5AC4365DA66ED562 |
| SHA1: | DC910382181C1E323FE8E9F41793711051782706 |
| SHA256: | 258BBC42A9AFB92E2C79C4C7435EC971942687AC29561376F57245AF3DA3824E |
| SSDEEP: | 98304:qzAdSrqUyyZhDyUeckJUI58MLfM4gpoJ28YOskSMRMqwlNk4mpxiyGlkZh+d3ur3:qsdSD8Dtt7aKb3I5q1g3bIx |
MALICIOUS
UAC/LUA settings modification
- Azorult.exe (PID: 5376)
- regedit.exe (PID: 1452)
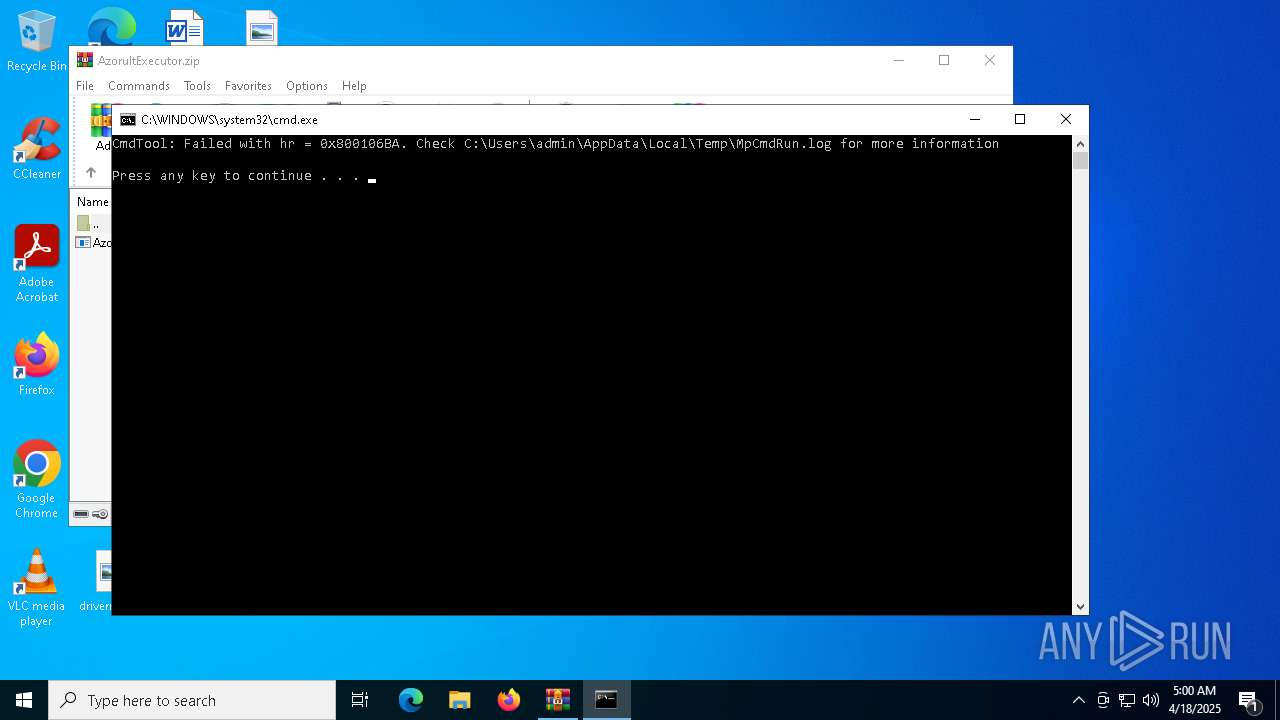
Disables Windows Defender
- Azorult.exe (PID: 5376)
RMS is detected
- regedit.exe (PID: 1452)
- regedit.exe (PID: 5164)
- rutserv.exe (PID: 5380)
Uses Task Scheduler to run other applications
- taskhost.exe (PID: 1280)
- Azorult.exe (PID: 5376)
Starts NET.EXE to view/add/change user profiles
- net.exe (PID: 7528)
- cmd.exe (PID: 3156)
Changes the autorun value in the registry
- taskhostw.exe (PID: 4424)
Starts NET.EXE to view/change users localgroup
- net.exe (PID: 7496)
- net.exe (PID: 8072)
- cmd.exe (PID: 3156)
- net.exe (PID: 8104)
- net.exe (PID: 7352)
- net.exe (PID: 7748)
- net.exe (PID: 208)
- net.exe (PID: 3024)
- net.exe (PID: 4988)
- net.exe (PID: 7612)
Uses Task Scheduler to autorun other applications
- taskhost.exe (PID: 1280)
- Azorult.exe (PID: 5376)
Changes the Windows auto-update feature
- powershell.exe (PID: 8040)
RDPWRAP has been detected
- RDPWInst.exe (PID: 7384)
Creates or modifies Windows services
- RDPWInst.exe (PID: 7384)
Starts NET.EXE to view/change login properties
- net.exe (PID: 9164)
- cmd.exe (PID: 3156)
RMS has been detected (YARA)
- rutserv.exe (PID: 5380)
- rfusclient.exe (PID: 6080)
- rfusclient.exe (PID: 1096)
SUSPICIOUS
Executable content was dropped or overwritten
- Azorult.exe (PID: 5376)
- wini.exe (PID: 6592)
- P.exe (PID: 5868)
- cheat.exe (PID: 968)
- R8.exe (PID: 8164)
- winlog.exe (PID: 7608)
- Rar.exe (PID: 7224)
- taskhost.exe (PID: 1280)
- taskhostw.exe (PID: 4424)
- RDPWInst.exe (PID: 7384)
The process executes VB scripts
- wini.exe (PID: 6592)
- R8.exe (PID: 8164)
- cmd.exe (PID: 7248)
Reads security settings of Internet Explorer
- ShellExperienceHost.exe (PID: 5984)
- wini.exe (PID: 6592)
- cheat.exe (PID: 968)
- ink.exe (PID: 4424)
- WinRAR.exe (PID: 1660)
- winit.exe (PID: 616)
- R8.exe (PID: 8164)
- winlog.exe (PID: 7608)
- winlogon.exe (PID: 6564)
- taskhost.exe (PID: 1280)
- RDPWInst.exe (PID: 7384)
- Azorult.exe (PID: 5376)
- taskhostw.exe (PID: 4424)
- RDPWInst.exe (PID: 8516)
Executing commands from a ".bat" file
- wscript.exe (PID: 4220)
- WinRAR.exe (PID: 1660)
- winit.exe (PID: 616)
- wscript.exe (PID: 2064)
- winlogon.exe (PID: 6564)
- wscript.exe (PID: 4428)
- taskhost.exe (PID: 1280)
Uses TIMEOUT.EXE to delay execution
- cmd.exe (PID: 5512)
- cmd.exe (PID: 8088)
- cmd.exe (PID: 7248)
- cmd.exe (PID: 6876)
Uses REG/REGEDIT.EXE to modify registry
- cmd.exe (PID: 5512)
- cmd.exe (PID: 3156)
Starts CMD.EXE for commands execution
- wscript.exe (PID: 4220)
- Azorult.exe (PID: 5376)
- WinRAR.exe (PID: 1660)
- winit.exe (PID: 616)
- wscript.exe (PID: 2064)
- winlogon.exe (PID: 6564)
- wscript.exe (PID: 4428)
- taskhost.exe (PID: 1280)
- winlogon.exe (PID: 7988)
- taskhostw.exe (PID: 4424)
Runs shell command (SCRIPT)
- wscript.exe (PID: 4220)
- wscript.exe (PID: 2064)
- wscript.exe (PID: 4428)
Executes as Windows Service
- rutserv.exe (PID: 5380)
Uses ATTRIB.EXE to modify file attributes
- cmd.exe (PID: 5512)
- cmd.exe (PID: 3156)
- cmd.exe (PID: 6876)
Windows service management via SC.EXE
- sc.exe (PID: 2100)
- sc.exe (PID: 5084)
- sc.exe (PID: 2108)
- sc.exe (PID: 4108)
- sc.exe (PID: 7580)
- sc.exe (PID: 7924)
- sc.exe (PID: 8008)
- sc.exe (PID: 1452)
- sc.exe (PID: 8092)
- sc.exe (PID: 7836)
- sc.exe (PID: 7364)
- sc.exe (PID: 7536)
- sc.exe (PID: 7912)
- sc.exe (PID: 7704)
Restarts service on failure
- sc.exe (PID: 4464)
Potential Corporate Privacy Violation
- rutserv.exe (PID: 5380)
- winit.exe (PID: 616)
- svchost.exe (PID: 2196)
- Azorult.exe (PID: 5376)
- taskhost.exe (PID: 1280)
- taskhostw.exe (PID: 4424)
The process creates files with name similar to system file names
- cheat.exe (PID: 968)
- Azorult.exe (PID: 5376)
Connects to unusual port
- rutserv.exe (PID: 5380)
Sets the service to start on system boot
- sc.exe (PID: 7408)
- sc.exe (PID: 7496)
Stops a currently running service
- sc.exe (PID: 7748)
- sc.exe (PID: 7664)
- sc.exe (PID: 8176)
- sc.exe (PID: 6044)
- sc.exe (PID: 7448)
- sc.exe (PID: 7620)
- sc.exe (PID: 3768)
Application launched itself
- rfusclient.exe (PID: 6080)
There is functionality for taking screenshot (YARA)
- Azorult.exe (PID: 5376)
Uses NETSH.EXE to change the status of the firewall
- cmd.exe (PID: 7852)
Uses NETSH.EXE to add a firewall rule or allowed programs
- cmd.exe (PID: 7824)
- cmd.exe (PID: 8012)
- cmd.exe (PID: 8104)
- cmd.exe (PID: 2852)
- cmd.exe (PID: 4000)
- cmd.exe (PID: 4464)
- cmd.exe (PID: 7560)
- cmd.exe (PID: 7384)
- cmd.exe (PID: 7764)
- cmd.exe (PID: 7768)
- cmd.exe (PID: 8076)
- cmd.exe (PID: 7968)
- cmd.exe (PID: 8024)
- cmd.exe (PID: 8064)
- cmd.exe (PID: 7252)
- cmd.exe (PID: 7360)
- cmd.exe (PID: 7336)
- cmd.exe (PID: 8028)
- cmd.exe (PID: 7396)
- cmd.exe (PID: 7668)
- cmd.exe (PID: 3156)
- RDPWInst.exe (PID: 7384)
The process verifies whether the antivirus software is installed
- winit.exe (PID: 616)
- icacls.exe (PID: 7616)
- icacls.exe (PID: 7720)
- icacls.exe (PID: 7372)
- icacls.exe (PID: 7396)
- icacls.exe (PID: 7684)
- icacls.exe (PID: 924)
- Azorult.exe (PID: 5376)
- icacls.exe (PID: 3304)
- icacls.exe (PID: 5124)
- icacls.exe (PID: 8024)
- icacls.exe (PID: 7688)
- icacls.exe (PID: 5508)
- icacls.exe (PID: 872)
- icacls.exe (PID: 7844)
- icacls.exe (PID: 7924)
Uses ICACLS.EXE to modify access control lists
- cmd.exe (PID: 7800)
- cmd.exe (PID: 7708)
- cmd.exe (PID: 8056)
- cmd.exe (PID: 6564)
- cmd.exe (PID: 8060)
- cmd.exe (PID: 8076)
- cmd.exe (PID: 8032)
- cmd.exe (PID: 2100)
- cmd.exe (PID: 4464)
- cmd.exe (PID: 7328)
- cmd.exe (PID: 7492)
- cmd.exe (PID: 7540)
- cmd.exe (PID: 7712)
- cmd.exe (PID: 7568)
- cmd.exe (PID: 7864)
- cmd.exe (PID: 8160)
- cmd.exe (PID: 7372)
- cmd.exe (PID: 7776)
- cmd.exe (PID: 5164)
- cmd.exe (PID: 7920)
- cmd.exe (PID: 8116)
- cmd.exe (PID: 2664)
- cmd.exe (PID: 1600)
- cmd.exe (PID: 7344)
- cmd.exe (PID: 7516)
- cmd.exe (PID: 7720)
- cmd.exe (PID: 7524)
- cmd.exe (PID: 6828)
- cmd.exe (PID: 7800)
- cmd.exe (PID: 7732)
- cmd.exe (PID: 7684)
- cmd.exe (PID: 7556)
- cmd.exe (PID: 8056)
- cmd.exe (PID: 7672)
- cmd.exe (PID: 732)
- cmd.exe (PID: 7476)
- cmd.exe (PID: 1272)
- cmd.exe (PID: 7904)
- cmd.exe (PID: 5936)
- cmd.exe (PID: 7692)
- cmd.exe (PID: 7900)
- cmd.exe (PID: 7628)
- cmd.exe (PID: 7580)
- cmd.exe (PID: 7936)
- cmd.exe (PID: 7896)
- cmd.exe (PID: 8032)
- cmd.exe (PID: 6392)
- cmd.exe (PID: 7324)
- cmd.exe (PID: 7592)
- cmd.exe (PID: 7744)
- cmd.exe (PID: 7236)
- cmd.exe (PID: 5744)
- cmd.exe (PID: 8028)
- cmd.exe (PID: 6300)
- cmd.exe (PID: 4696)
- cmd.exe (PID: 7436)
- cmd.exe (PID: 7760)
- cmd.exe (PID: 7408)
- cmd.exe (PID: 4696)
- cmd.exe (PID: 7696)
- cmd.exe (PID: 1748)
- cmd.exe (PID: 6208)
Checks for external IP
- svchost.exe (PID: 2196)
- winit.exe (PID: 616)
- Azorult.exe (PID: 5376)
Uses TASKKILL.EXE to kill process
- cmd.exe (PID: 7248)
- cmd.exe (PID: 6876)
Starts POWERSHELL.EXE for commands execution
- cmd.exe (PID: 7308)
Starts application with an unusual extension
- cmd.exe (PID: 7248)
- cmd.exe (PID: 3156)
Detected use of alternative data streams (AltDS)
- taskhostw.exe (PID: 4424)
Lists all scheduled tasks in specific format
- schtasks.exe (PID: 7404)
Modifies hosts file to alter network resolution
- cmd.exe (PID: 4172)
Process drops legitimate windows executable
- RDPWInst.exe (PID: 7384)
Deletes scheduled task without confirmation
- schtasks.exe (PID: 8276)
- schtasks.exe (PID: 8340)
- schtasks.exe (PID: 8332)
- schtasks.exe (PID: 8576)
- schtasks.exe (PID: 8560)
- schtasks.exe (PID: 8584)
- schtasks.exe (PID: 8592)
- schtasks.exe (PID: 8628)
- schtasks.exe (PID: 8612)
- schtasks.exe (PID: 8348)
- schtasks.exe (PID: 8404)
- schtasks.exe (PID: 8412)
- schtasks.exe (PID: 8436)
- schtasks.exe (PID: 8552)
- schtasks.exe (PID: 8604)
Process uses IPCONFIG to clear DNS cache
- cmd.exe (PID: 5172)
The process executes via Task Scheduler
- taskhostw.exe (PID: 8676)
INFO
Checks supported languages
- Azorult.exe (PID: 5376)
- wini.exe (PID: 6592)
- ShellExperienceHost.exe (PID: 5984)
- rutserv.exe (PID: 7036)
- winit.exe (PID: 616)
- rutserv.exe (PID: 5936)
- rutserv.exe (PID: 4428)
- rfusclient.exe (PID: 6080)
- rutserv.exe (PID: 5380)
- rfusclient.exe (PID: 1096)
- cheat.exe (PID: 968)
- P.exe (PID: 5868)
- taskhost.exe (PID: 1280)
- ink.exe (PID: 4424)
- MpCmdRun.exe (PID: 7324)
- rfusclient.exe (PID: 5384)
- R8.exe (PID: 8164)
- winlog.exe (PID: 7608)
- chcp.com (PID: 5968)
- Rar.exe (PID: 7224)
- winlogon.exe (PID: 6564)
- taskhostw.exe (PID: 4424)
- chcp.com (PID: 5588)
- RDPWInst.exe (PID: 7384)
- winlogon.exe (PID: 7988)
- taskhostw.exe (PID: 7596)
- RDPWInst.exe (PID: 8516)
- taskhostw.exe (PID: 8676)
Manual execution by a user
- Azorult.exe (PID: 3304)
- Azorult.exe (PID: 5376)
- taskhostw.exe (PID: 7596)
- winlogon.exe (PID: 7768)
Reads the computer name
- Azorult.exe (PID: 5376)
- ShellExperienceHost.exe (PID: 5984)
- wini.exe (PID: 6592)
- rutserv.exe (PID: 7036)
- rutserv.exe (PID: 5936)
- rutserv.exe (PID: 4428)
- rutserv.exe (PID: 5380)
- rfusclient.exe (PID: 1096)
- rfusclient.exe (PID: 6080)
- cheat.exe (PID: 968)
- P.exe (PID: 5868)
- ink.exe (PID: 4424)
- MpCmdRun.exe (PID: 7324)
- rfusclient.exe (PID: 5384)
- winit.exe (PID: 616)
- R8.exe (PID: 8164)
- winlog.exe (PID: 7608)
- winlogon.exe (PID: 6564)
- taskhost.exe (PID: 1280)
- taskhostw.exe (PID: 4424)
- RDPWInst.exe (PID: 7384)
- taskhostw.exe (PID: 7596)
- RDPWInst.exe (PID: 8516)
- taskhostw.exe (PID: 8676)
The sample compiled with english language support
- WinRAR.exe (PID: 1660)
- wini.exe (PID: 6592)
- P.exe (PID: 5868)
- cheat.exe (PID: 968)
- R8.exe (PID: 8164)
- Rar.exe (PID: 7224)
- taskhost.exe (PID: 1280)
- taskhostw.exe (PID: 4424)
- RDPWInst.exe (PID: 7384)
Creates files in the program directory
- Azorult.exe (PID: 5376)
- wini.exe (PID: 6592)
- cheat.exe (PID: 968)
- P.exe (PID: 5868)
- winit.exe (PID: 616)
- winlog.exe (PID: 7608)
- taskhost.exe (PID: 1280)
- RDPWInst.exe (PID: 7384)
- taskhostw.exe (PID: 4424)
Reads mouse settings
- Azorult.exe (PID: 5376)
- winit.exe (PID: 616)
- taskhost.exe (PID: 1280)
- taskhostw.exe (PID: 4424)
- winlogon.exe (PID: 7988)
- taskhostw.exe (PID: 7596)
- taskhostw.exe (PID: 8676)
Create files in a temporary directory
- Azorult.exe (PID: 5376)
- MpCmdRun.exe (PID: 7324)
- winit.exe (PID: 616)
- winlogon.exe (PID: 6564)
- taskhost.exe (PID: 1280)
- taskhostw.exe (PID: 4424)
Process checks computer location settings
- wini.exe (PID: 6592)
- cheat.exe (PID: 968)
- R8.exe (PID: 8164)
- winlog.exe (PID: 7608)
- winlogon.exe (PID: 6564)
- taskhost.exe (PID: 1280)
- Azorult.exe (PID: 5376)
Reads the machine GUID from the registry
- ink.exe (PID: 4424)
- winit.exe (PID: 616)
- RDPWInst.exe (PID: 7384)
- Azorult.exe (PID: 5376)
- RDPWInst.exe (PID: 8516)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 1660)
Checks proxy server information
- ink.exe (PID: 4424)
- winit.exe (PID: 616)
- RDPWInst.exe (PID: 7384)
- Azorult.exe (PID: 5376)
- taskhost.exe (PID: 1280)
- RDPWInst.exe (PID: 8516)
- taskhostw.exe (PID: 4424)
- slui.exe (PID: 5640)
The process uses AutoIt
- Azorult.exe (PID: 5376)
Reads CPU info
- winit.exe (PID: 616)
Creates files or folders in the user directory
- winit.exe (PID: 616)
- RDPWInst.exe (PID: 7384)
- RDPWInst.exe (PID: 8516)
Reads the software policy settings
- winit.exe (PID: 616)
- RDPWInst.exe (PID: 7384)
- Azorult.exe (PID: 5376)
- RDPWInst.exe (PID: 8516)
- slui.exe (PID: 5640)
Changes the display of characters in the console
- cmd.exe (PID: 7248)
- cmd.exe (PID: 3156)
Auto-launch of the file from Registry key
- taskhostw.exe (PID: 4424)
RDPWRAP has been detected
- RDPWInst.exe (PID: 7384)
- RDPWInst.exe (PID: 8516)
- attrib.exe (PID: 9212)
Aspack has been detected
- rutserv.exe (PID: 5380)
- rfusclient.exe (PID: 6080)
- rfusclient.exe (PID: 1096)
Compiled with Borland Delphi (YARA)
- rutserv.exe (PID: 5380)
- rfusclient.exe (PID: 6080)
- rfusclient.exe (PID: 1096)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2025:04:17 20:18:02 |
| ZipCRC: | 0xeb5652a2 |
| ZipCompressedSize: | 10085647 |
| ZipUncompressedSize: | 10508800 |
| ZipFileName: | Azorult.exe |
Total processes
618
Monitored processes
477
Malicious processes
34
Suspicious processes
16
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 208 | net localgroup "Пользователи удаленного рабочего стола" John /add | C:\Windows\SysWOW64\net.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Net Command Exit code: 2 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 616 | "C:\ProgramData\Windows\winit.exe" | C:\ProgramData\Windows\winit.exe | wini.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 664 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 672 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 732 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 732 | C:\WINDOWS\system32\cmd.exe /c icacls "C:\Program Files\AVAST Software" /deny %username%:(OI)(CI)(F) | C:\Windows\SysWOW64\cmd.exe | — | Azorult.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 732 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 744 | C:\WINDOWS\system32\net1 localgroup "Remote Desktop Users" John /add | C:\Windows\SysWOW64\net1.exe | — | net.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Net Command Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 744 | C:\WINDOWS\system32\cmd.exe /C schtasks /Delete /TN "Mozilla\Firefox Default Browser Agent 308046B0AF4A39CB" /F | C:\Windows\SysWOW64\cmd.exe | — | winlogon.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 872 | icacls "C:\Program Files\ESET" /deny admin:(OI)(CI)(F) | C:\Windows\SysWOW64\icacls.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
45 086
Read events
44 821
Write events
186
Delete events
79
Modification events
| (PID) Process: | (1660) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (1660) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (1660) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (1660) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\AzorultExecutor.zip | |||
| (PID) Process: | (1660) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (1660) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (1660) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (1660) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (5376) Azorult.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows NT\CurrentVersion\Winlogon\SpecialAccounts\UserList |
| Operation: | write | Name: | John |
Value: 0 | |||
| (PID) Process: | (5376) Azorult.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Winlogon\SpecialAccounts\UserList |
| Operation: | write | Name: | John |
Value: 0 | |||
Executable files
24
Suspicious files
12
Text files
22
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 5376 | Azorult.exe | C:\ProgramData\Microsoft\Check\Check.txt | — | |
MD5:— | SHA256:— | |||
| 5376 | Azorult.exe | C:\ProgramData\Microsoft\temp\Temp.bat | text | |
MD5:9380F21201174AC1267AA944E1096955 | SHA256:CCF47D036CCFE0C8D0FE2854D14CA21D99BE5FA11D0FBB16EDCC1D6C10DE3512 | |||
| 5376 | Azorult.exe | C:\ProgramData\Microsoft\temp\Clean.bat | text | |
MD5:041E144A6429A6926771B0469B901630 | SHA256:1134B862F4D0CE10466742BEB334C06C2386E85ACAD72725DDB1CECB1871B312 | |||
| 5376 | Azorult.exe | C:\Users\admin\AppData\Local\Temp\aut29DC.tmp | binary | |
MD5:7B5818F70DA8C573F74BE380A6658570 | SHA256:7985A07B0E5795C7DFAC7489B91A9B15CE9C0534DA1FFC2AE385F9FCAEFE92AB | |||
| 6592 | wini.exe | C:\ProgramData\Windows\rfusclient.exe | executable | |
MD5:B8667A1E84567FCF7821BCEFB6A444AF | SHA256:DC9D875E659421A51ADDD8E8A362C926369E84320AB0C5D8BBB1E4D12D372FC9 | |||
| 5376 | Azorult.exe | C:\ProgramData\Microsoft\temp\H.bat | text | |
MD5:76303BB3BB0FAA707000DF998D8C9F3D | SHA256:A33AF2B70AD8FEA8900B6BD31AC7B0AAB8A2B8B79E3E27ADAFBD34BDFCB67549 | |||
| 5376 | Azorult.exe | C:\Users\admin\AppData\Local\Temp\aut29FE.tmp | binary | |
MD5:A71F2FF7DE001638ABA284E64351AA97 | SHA256:8E750661ACD11C039FC9F97F5ACB89C0814A0DEB13F53299BE4FD15B4AE22859 | |||
| 6592 | wini.exe | C:\ProgramData\Windows\reg1.reg | text | |
MD5:806734F8BFF06B21E470515E314CFA0D | SHA256:7AE7E4C0155F559F3C31BE25D9E129672A88B445AF5847746FE0A9AAB3E79544 | |||
| 6592 | wini.exe | C:\ProgramData\Windows\rutserv.exe | executable | |
MD5:37A8802017A212BB7F5255ABC7857969 | SHA256:1699B9B4FC1724F9B0918B57CA58C453829A3935EFD89BD4E9FA66B5E9F2B8A6 | |||
| 6592 | wini.exe | C:\ProgramData\Windows\reg2.reg | text | |
MD5:6A5D2192B8AD9E96A2736C8B0BDBD06E | SHA256:4AE04A85412EC3DAA0FB33F21ED4EB3C4864C3668B95712BE9EC36EF7658422A | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
40
TCP/UDP connections
63
DNS requests
28
Threats
19
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 304 | 172.202.163.200:443 | https://slscr.update.microsoft.com/SLS/%7B522D76A4-93E1-47F8-B8CE-07C937AD1A1E%7D/x64/10.0.19045.4046/0?CH=686&L=en-US&P=&PT=0x30&WUA=10.0.19041.3996&MK=DELL&MD=DELL | unknown | — | — | unknown |
2148 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Signing%20CA%202.1.crl | unknown | — | — | whitelisted |
2148 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20Update%20Signing%20CA%202.2.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 172.202.163.200:443 | https://slscr.update.microsoft.com/sls/ping | unknown | — | — | unknown |
— | — | GET | — | 172.202.163.200:443 | https://slscr.update.microsoft.com/SLS/%7B522D76A4-93E1-47F8-B8CE-07C937AD1A1E%7D/x64/10.0.19045.4046/0?CH=686&L=en-US&P=&PT=0x30&WUA=10.0.19041.3996&MK=DELL&MD=DELL | unknown | — | — | unknown |
2148 | SIHClient.exe | GET | 200 | 23.216.77.6:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
2148 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20Update%20Signing%20CA%202.1.crl | unknown | — | — | whitelisted |
2148 | SIHClient.exe | GET | 200 | 23.216.77.6:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut_2010-06-23.crl | unknown | — | — | whitelisted |
— | — | GET | 304 | 172.202.163.200:443 | https://slscr.update.microsoft.com/SLS/%7BE7A50285-D08D-499D-9FF8-180FDC2332BC%7D/x64/10.0.19045.4046/0?CH=686&L=en-US&P=&PT=0x30&WUA=10.0.19041.3996&MK=DELL&MD=DELL | unknown | — | — | unknown |
616 | winit.exe | GET | 200 | 208.95.112.1:80 | http://ip-api.com/json | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
3216 | svchost.exe | 172.211.123.249:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
2148 | SIHClient.exe | 172.202.163.200:443 | slscr.update.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | GB | whitelisted |
2148 | SIHClient.exe | 23.216.77.6:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
2148 | SIHClient.exe | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
2148 | SIHClient.exe | 40.69.42.241:443 | fe3cr.delivery.mp.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5380 | rutserv.exe | 77.223.119.187:5655 | rms-server.tektonit.ru | OOO Network of data-centers Selectel | RU | suspicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
rms-server.tektonit.ru |
| unknown |
boglogov.site |
| unknown |
ip-api.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
5380 | rutserv.exe | Potential Corporate Privacy Violation | REMOTE [ANY.RUN] Remote Access Tool Has been detected |
2196 | svchost.exe | Device Retrieving External IP Address Detected | INFO [ANY.RUN] External IP Check (ip-api .com) |
616 | winit.exe | Device Retrieving External IP Address Detected | ET INFO External IP Lookup ip-api.com |
616 | winit.exe | Potential Corporate Privacy Violation | ET INFO Autoit Windows Automation tool User-Agent in HTTP Request - Possibly Hostile |
2196 | svchost.exe | Device Retrieving External IP Address Detected | ET INFO External IP Lookup Domain in DNS Lookup (ip-api .com) |
2196 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Attempting to access raw user content on GitHub |
2196 | svchost.exe | Potential Corporate Privacy Violation | ET INFO IP Check Domain (iplogger .org in DNS Lookup) |
5376 | Azorult.exe | Potential Corporate Privacy Violation | ET INFO IP Check Domain (iplogger .org in TLS SNI) |
— | — | Potentially Bad Traffic | ET INFO RDP Wrapper Download (ini) |
— | — | Potential Corporate Privacy Violation | ET INFO Autoit Windows Automation tool User-Agent in HTTP Request - Possibly Hostile |
Process | Message |
|---|---|
rutserv.exe | TMainService.Start |
rutserv.exe | GUID_CONSOLE_DISPLAY_STATE |
rutserv.exe | 18-04-2025_05:01:20:370#T:Msg Size: 104 |
rutserv.exe | 18-04-2025_05:01:20:370#T:MSG_KEEP_ALIVE |
rutserv.exe | 18-04-2025_05:01:20:370#T:Msg code: 3 |
rutserv.exe | MSG_KEEP_ALIVE |
rutserv.exe | MSG_KEEP_ALIVE |
rutserv.exe | 18-04-2025_05:01:47:761#T:Msg code: 3 |
rutserv.exe | 18-04-2025_05:01:47:761#T:Msg Size: 104 |
rutserv.exe | 18-04-2025_05:01:47:761#T:MSG_KEEP_ALIVE |