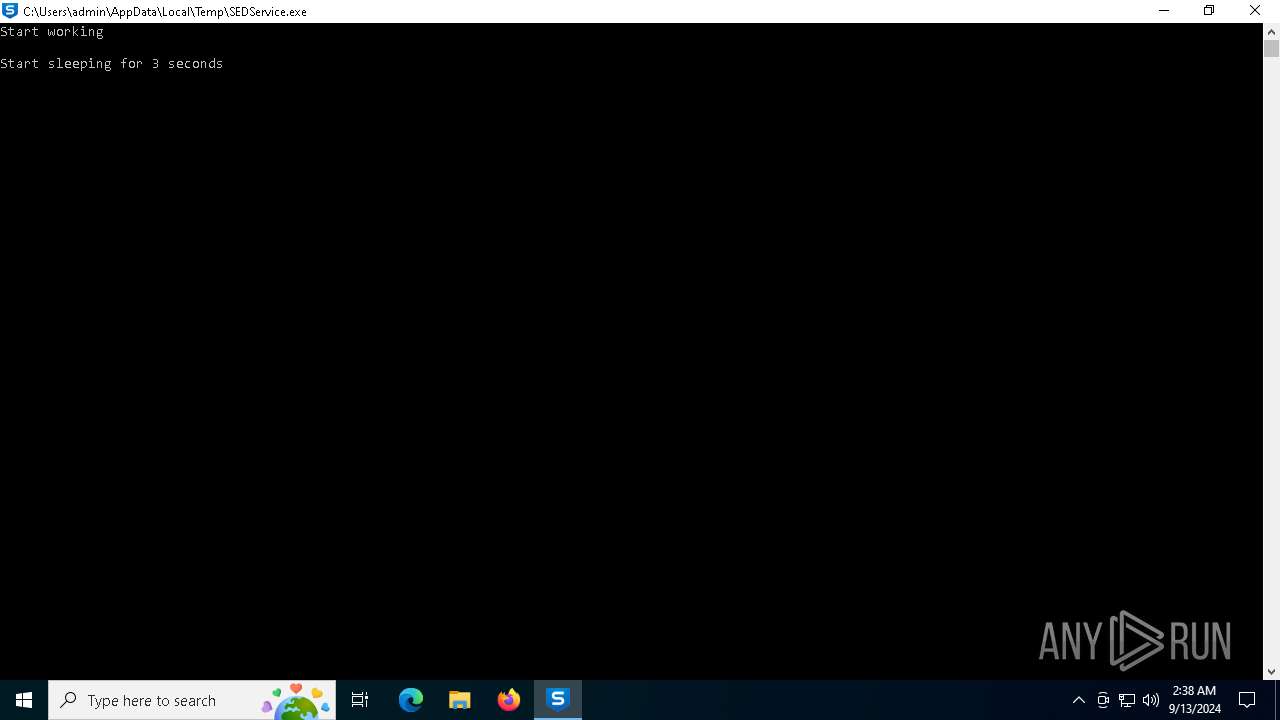
| File name: | SEDService.exe |
| Full analysis: | https://app.any.run/tasks/afbad5d5-ee6a-4e4f-8888-d526b99d9030 |
| Verdict: | Malicious activity |
| Threats: | Interlock is a relatively recent entrant into the ransomware landscape. First identified in 2023, it's a multi-functional malware strain used in ransomware-as-a-service (RaaS) operations. |
| Analysis date: | September 13, 2024, 02:38:48 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32+ executable (console) x86-64, for MS Windows |
| MD5: | 9AC4F6522C9F727EEA1192B7FE48419E |
| SHA1: | 37E17FE7D1B2B1B84318E64EB31D33BD3127512C |
| SHA256: | 252BF03C4C4127999C5C7ED98784125F6182CEEC25FD82B2CC9BE75774BB8B1E |
| SSDEEP: | 98304:xMYPAbLkne0dcXzzYQAwv7Du8DC8O2aEiwQeyPNueUxMN8vOLRsaKk1QQh+cjWBb:7V8zPaRThxHWF6 |
MALICIOUS
Actions looks like stealing of personal data
- SEDService.exe (PID: 3316)
SUSPICIOUS
No suspicious indicators.INFO
Creates files or folders in the user directory
- SEDService.exe (PID: 3316)
Reads the software policy settings
- slui.exe (PID: 6204)
Reads the computer name
- SEDService.exe (PID: 3316)
Create files in a temporary directory
- SEDService.exe (PID: 3316)
Checks supported languages
- SEDService.exe (PID: 3316)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win64 Executable (generic) (82.1) |
|---|---|---|
| .exe | | | Clipper DOS Executable (5.9) |
| .exe | | | Generic Win/DOS Executable (5.9) |
| .exe | | | DOS Executable Generic (5.9) |
EXIF
EXE
| MachineType: | AMD AMD64 |
|---|---|
| TimeStamp: | 2023:11:01 18:58:49+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, Large address aware |
| PEType: | PE32+ |
| LinkerVersion: | 14.29 |
| CodeSize: | 2726912 |
| InitializedDataSize: | 5689344 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x1af7a0 |
| OSVersion: | 6 |
| ImageVersion: | - |
| SubsystemVersion: | 6 |
| Subsystem: | Windows command line |
| FileVersionNumber: | 3.2.0.1560 |
| ProductVersionNumber: | 3.2.0.1560 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Windows NT 32-bit |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Unicode |
| Comments: | Sophos Endpoint Defense Service |
| CompanyName: | Sophos Limited |
| FileDescription: | Sophos Endpoint Defense Software |
| FileVersion: | 3.2.0.1560 |
| InternalName: | Sophos Endpoint Defense Service |
| LegalCopyright: | Copyright 1989-2023 Sophos Limited. All rights reserved. |
| LegalTrademarks: | Sophos Endpoint Defense, the Sophos name and Sophos logo are trademarks or registered trademarks of "Sophos Limited |
| OriginalFileName: | SEDService.exe |
| ProductName: | Sophos Endpoint Defense |
| ProductVersion: | 3.2.0.1560 |
Total processes
129
Monitored processes
5
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1164 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | SEDService.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3292 | C:\WINDOWS\system32\SppExtComObj.exe -Embedding | C:\Windows\System32\SppExtComObj.Exe | — | svchost.exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: KMS Connection Broker Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3316 | "C:\Users\admin\AppData\Local\Temp\SEDService.exe" | C:\Users\admin\AppData\Local\Temp\SEDService.exe | explorer.exe | ||||||||||||
User: admin Company: Sophos Limited Integrity Level: MEDIUM Description: Sophos Endpoint Defense Software Exit code: 0 Version: 3.2.0.1560 Modules
| |||||||||||||||
| 4060 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6204 | "C:\WINDOWS\System32\SLUI.exe" RuleId=3482d82e-ca2c-4e1f-8864-da0267b484b2;Action=AutoActivate;AppId=55c92734-d682-4d71-983e-d6ec3f16059f;SkuId=4de7cb65-cdf1-4de9-8ae8-e3cce27b9f2c;NotificationInterval=1440;Trigger=TimerEvent | C:\Windows\System32\slui.exe | SppExtComObj.Exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Activation Client Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
750
Read events
750
Write events
0
Delete events
0
Modification events
Executable files
0
Suspicious files
5
Text files
1
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3316 | SEDService.exe | C:\Users\admin\AppData\Local\Temp\Local State | binary | |
MD5:6EF6D4132727E4F700645C341C4BEEE2 | SHA256:5164FDFC5C55D1BE643CF646E2E89C32191344D969632C8AED72922AE31D06C2 | |||
| 3316 | SEDService.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\places.sqlite-shm | binary | |
MD5:B7C14EC6110FA820CA6B65F5AEC85911 | SHA256:FD4C9FDA9CD3F9AE7C962B0DDF37232294D55580E1AA165AA06129B8549389EB | |||
| 3316 | SEDService.exe | C:\Users\admin\AppData\Local\Temp\Login Data | binary | |
MD5:A45465CDCDC6CB30C8906F3DA4EC114C | SHA256:4412319EF944EBCCA9581CBACB1D4E1DC614C348D1DFC5D2FAAAAD863D300209 | |||
| 3316 | SEDService.exe | C:\Users\admin\AppData\Local\Temp\chrgetpdsi.txt | text | |
MD5:F19510FBA06BBCE4C7C893BD851C6C64 | SHA256:989BF1A546859C96CCEEE44D6AD2EADE47D1EF055AF36386BA0D37D933C36087 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
4
TCP/UDP connections
29
DNS requests
16
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
6776 | svchost.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
6112 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
— | — | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
568 | RUXIMICS.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
2120 | MoUsoCoreWorker.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6776 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6776 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6776 | svchost.exe | 95.101.149.131:80 | www.microsoft.com | Akamai International B.V. | NL | whitelisted |
2120 | MoUsoCoreWorker.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
3260 | svchost.exe | 40.113.110.67:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6112 | svchost.exe | 20.190.159.0:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6112 | svchost.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
activation-v2.sls.microsoft.com |
| whitelisted |