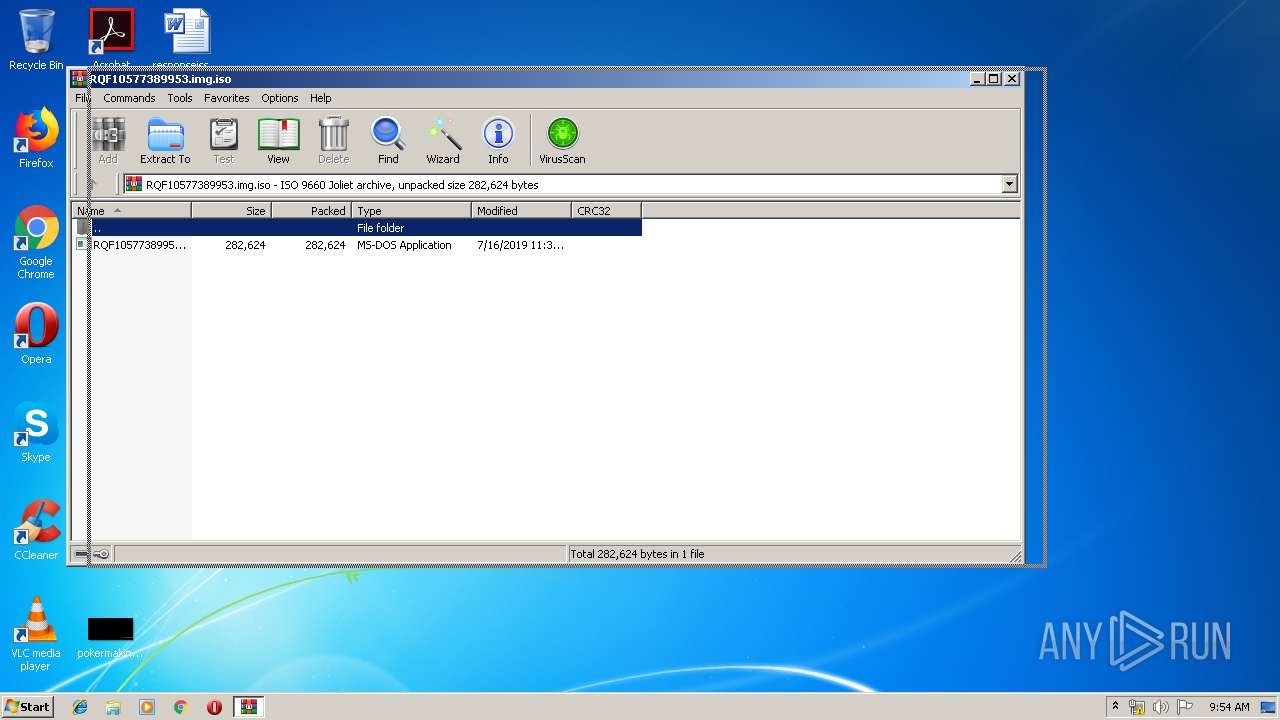
| File name: | RQF10577389953.img |
| Full analysis: | https://app.any.run/tasks/9a0de60b-cbd4-4a3b-8afe-99973590c344 |
| Verdict: | Malicious activity |
| Threats: | LokiBot was developed in 2015 to steal information from a variety of applications. Despite the age, this malware is still rather popular among cybercriminals. |
| Analysis date: | July 17, 2019, 08:53:24 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-iso9660-image |
| File info: | ISO 9660 CD-ROM filesystem data 'RQF10577389953' |
| MD5: | FF89AEA4E9CFF2240FEC7BFB678C9C96 |
| SHA1: | A52DCE07CF7B153CD65196D6B685741FEC08FAC7 |
| SHA256: | 24E92E0903DB616DC4CB369F2F258CB01AAC11B09FCD75BF6767A54698A57825 |
| SSDEEP: | 3072:9wbcpOOslorzL9tC6rTILRhIdn3LzgscS39OLWHeSORe3pWEyZuKvx8Ao:+bcC+v9tRqR63gDS3gLRReZWEydx |
MALICIOUS
Application was dropped or rewritten from another process
- RQF10577389953.com (PID: 2276)
- RQF10577389953.com (PID: 1252)
- RQF10577389953.com (PID: 3728)
- RQF10577389953.com (PID: 2152)
- RQF10577389953.com (PID: 312)
- RQF10577389953.com (PID: 4036)
LOKIBOT was detected
- RQF10577389953.com (PID: 312)
LokiBot was detected
- RQF10577389953.com (PID: 312)
Connects to CnC server
- RQF10577389953.com (PID: 312)
Actions looks like stealing of personal data
- RQF10577389953.com (PID: 312)
SUSPICIOUS
Application launched itself
- RQF10577389953.com (PID: 2276)
- RQF10577389953.com (PID: 1252)
- RQF10577389953.com (PID: 3728)
- RQF10577389953.com (PID: 2152)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 3700)
- RQF10577389953.com (PID: 312)
Starts application with an unusual extension
- WinRAR.exe (PID: 3700)
- RQF10577389953.com (PID: 2276)
- RQF10577389953.com (PID: 1252)
- RQF10577389953.com (PID: 3728)
- RQF10577389953.com (PID: 2152)
Loads DLL from Mozilla Firefox
- RQF10577389953.com (PID: 312)
Creates files in the user directory
- RQF10577389953.com (PID: 312)
INFO
No info indicators.
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .iso | | | ISO 9660 CD image (27.6) |
|---|---|---|
| .atn | | | Photoshop Action (27.1) |
| .gmc | | | Game Music Creator Music (6.1) |
EXIF
ISO
| System: | Win32 |
|---|---|
| VolumeName: | RQF10577389953 |
| VolumeBlockCount: | 168 |
| VolumeBlockSize: | 2048 |
| RootDirectoryCreateDate: | 2019:07:16 13:52:36+01:00 |
| Software: | PowerISO |
| VolumeCreateDate: | 2019:07:16 13:52:36.00+01:00 |
| VolumeModifyDate: | 2019:07:16 13:52:36.00+01:00 |
Composite
| VolumeSize: | 336 kB |
|---|
Total processes
43
Monitored processes
8
Malicious processes
6
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 312 | "C:\Users\admin\AppData\Local\Temp\Rar$DIa3700.17950\RQF10577389953.com" | C:\Users\admin\AppData\Local\Temp\Rar$DIa3700.17950\RQF10577389953.com | RQF10577389953.com | ||||||||||||
User: admin Company: amazon.cOM Integrity Level: MEDIUM Description: Fame3 Exit code: 0 Version: 4.05.0006 Modules
| |||||||||||||||
| 1252 | "C:\Users\admin\AppData\Local\Temp\Rar$DIa3700.17986\RQF10577389953.com" | C:\Users\admin\AppData\Local\Temp\Rar$DIa3700.17986\RQF10577389953.com | — | WinRAR.exe | |||||||||||
User: admin Company: amazon.cOM Integrity Level: MEDIUM Description: Fame3 Exit code: 0 Version: 4.05.0006 Modules
| |||||||||||||||
| 2152 | "C:\Users\admin\AppData\Local\Temp\Rar$DIa3700.17986\RQF10577389953.com" | C:\Users\admin\AppData\Local\Temp\Rar$DIa3700.17986\RQF10577389953.com | — | RQF10577389953.com | |||||||||||
User: admin Company: amazon.cOM Integrity Level: MEDIUM Description: Fame3 Exit code: 0 Version: 4.05.0006 Modules
| |||||||||||||||
| 2276 | "C:\Users\admin\AppData\Local\Temp\Rar$DIa3700.17950\RQF10577389953.com" | C:\Users\admin\AppData\Local\Temp\Rar$DIa3700.17950\RQF10577389953.com | — | WinRAR.exe | |||||||||||
User: admin Company: amazon.cOM Integrity Level: MEDIUM Description: Fame3 Exit code: 0 Version: 4.05.0006 Modules
| |||||||||||||||
| 3700 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\RQF10577389953.img.iso" | C:\Program Files\WinRAR\WinRAR.exe | rundll32.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
| 3728 | "C:\Users\admin\AppData\Local\Temp\Rar$DIa3700.17950\RQF10577389953.com" | C:\Users\admin\AppData\Local\Temp\Rar$DIa3700.17950\RQF10577389953.com | — | RQF10577389953.com | |||||||||||
User: admin Company: amazon.cOM Integrity Level: MEDIUM Description: Fame3 Exit code: 0 Version: 4.05.0006 Modules
| |||||||||||||||
| 3856 | "C:\Windows\system32\rundll32.exe" C:\Windows\system32\shell32.dll,OpenAs_RunDLL C:\Users\admin\AppData\Local\Temp\RQF10577389953.img.iso | C:\Windows\system32\rundll32.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 4036 | "C:\Users\admin\AppData\Local\Temp\Rar$DIa3700.17986\RQF10577389953.com" | C:\Users\admin\AppData\Local\Temp\Rar$DIa3700.17986\RQF10577389953.com | — | RQF10577389953.com | |||||||||||
User: admin Company: amazon.cOM Integrity Level: MEDIUM Description: Fame3 Exit code: 0 Version: 4.05.0006 Modules
| |||||||||||||||
Total events
920
Read events
842
Write events
78
Delete events
0
Modification events
| (PID) Process: | (3856) rundll32.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\70\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3856) rundll32.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\70\52C64B7E |
| Operation: | write | Name: | @C:\Windows\System32\isoburn.exe,-350 |
Value: Disc Image File | |||
| (PID) Process: | (3856) rundll32.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\FileExts\.iso\OpenWithProgids |
| Operation: | write | Name: | Windows.IsoFile |
Value: | |||
| (PID) Process: | (3856) rundll32.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\MuiCache |
| Operation: | write | Name: | C:\Windows\system32\NOTEPAD.EXE |
Value: Notepad | |||
| (PID) Process: | (3856) rundll32.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\MuiCache |
| Operation: | write | Name: | C:\PROGRA~1\MICROS~1\Office14\OIS.EXE |
Value: Microsoft Office 2010 | |||
| (PID) Process: | (3856) rundll32.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\MuiCache |
| Operation: | write | Name: | C:\Program Files\Microsoft Office\Office14\WINWORD.EXE |
Value: Microsoft Word | |||
| (PID) Process: | (3856) rundll32.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\FileExts\.iso\UserChoice |
| Operation: | write | Name: | Progid |
Value: WinRAR | |||
| (PID) Process: | (3700) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (3700) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (3700) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\70\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
Executable files
4
Suspicious files
0
Text files
6
Unknown types
2
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 312 | RQF10577389953.com | C:\Users\admin\AppData\Roaming\F63AAA\A71D80.lck | — | |
MD5:— | SHA256:— | |||
| 3700 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DIa3700.17950\RQF10577389953.com | executable | |
MD5:— | SHA256:— | |||
| 3700 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\RQF10577389953.img\RQF10577389953.com | executable | |
MD5:— | SHA256:— | |||
| 312 | RQF10577389953.com | C:\Users\admin\AppData\Roaming\F63AAA\A71D80.hdb | text | |
MD5:— | SHA256:— | |||
| 312 | RQF10577389953.com | C:\Users\admin\AppData\Roaming\F63AAA\A71D80.exe | executable | |
MD5:— | SHA256:— | |||
| 1252 | RQF10577389953.com | C:\Users\admin\AppData\Local\VirtualStore\Windows\win.ini | text | |
MD5:D2A2412BDDBA16D60EC63BD9550D933F | SHA256:79FF2254E38192BE1626D05BEC6C82E10C85E1CF91DF7440C4C443380A1E877A | |||
| 3700 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DIa3700.17986\RQF10577389953.com | executable | |
MD5:— | SHA256:— | |||
| 312 | RQF10577389953.com | C:\Users\admin\AppData\Roaming\Microsoft\Crypto\RSA\S-1-5-21-1302019708-1500728564-335382590-1000\0f5007522459c86e95ffcc62f32308f1_90059c37-1320-41a4-b58d-2b75a9850d2f | dbf | |
MD5:18B8CFC0185C50383AAC0A4F30A9DAC8 | SHA256:913E8CED6A447FE791954D382ABA52D490513C5D2F689B391866C7E561F89A03 | |||
| 2152 | RQF10577389953.com | C:\Users\admin\AppData\Local\VirtualStore\Windows\win.ini | text | |
MD5:D2A2412BDDBA16D60EC63BD9550D933F | SHA256:79FF2254E38192BE1626D05BEC6C82E10C85E1CF91DF7440C4C443380A1E877A | |||
| 3728 | RQF10577389953.com | C:\Users\admin\AppData\Local\VirtualStore\Windows\win.ini | text | |
MD5:D2A2412BDDBA16D60EC63BD9550D933F | SHA256:79FF2254E38192BE1626D05BEC6C82E10C85E1CF91DF7440C4C443380A1E877A | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
4
TCP/UDP connections
4
DNS requests
1
Threats
22
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
312 | RQF10577389953.com | POST | — | 104.18.40.63:80 | http://meghanchantilew.gq/sabali/freeme.php | US | — | — | malicious |
312 | RQF10577389953.com | POST | — | 104.18.40.63:80 | http://meghanchantilew.gq/sabali/freeme.php | US | — | — | malicious |
312 | RQF10577389953.com | POST | — | 104.18.40.63:80 | http://meghanchantilew.gq/sabali/freeme.php | US | — | — | malicious |
312 | RQF10577389953.com | POST | — | 104.18.40.63:80 | http://meghanchantilew.gq/sabali/freeme.php | US | — | — | malicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
312 | RQF10577389953.com | 104.18.40.63:80 | meghanchantilew.gq | Cloudflare Inc | US | shared |
DNS requests
Domain | IP | Reputation |
|---|---|---|
meghanchantilew.gq |
| malicious |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1052 | svchost.exe | Potentially Bad Traffic | ET INFO DNS Query for Suspicious .gq Domain |
312 | RQF10577389953.com | A Network Trojan was detected | ET TROJAN LokiBot User-Agent (Charon/Inferno) |
312 | RQF10577389953.com | A Network Trojan was detected | ET TROJAN LokiBot Checkin |
312 | RQF10577389953.com | Potentially Bad Traffic | ET INFO HTTP POST Request to Suspicious *.gq domain |
312 | RQF10577389953.com | A Network Trojan was detected | ET TROJAN LokiBot Application/Credential Data Exfiltration Detected M1 |
312 | RQF10577389953.com | A Network Trojan was detected | MALWARE [PTsecurity] Loki Bot Check-in M2 |
312 | RQF10577389953.com | A Network Trojan was detected | ET TROJAN LokiBot User-Agent (Charon/Inferno) |
312 | RQF10577389953.com | A Network Trojan was detected | ET TROJAN LokiBot Checkin |
312 | RQF10577389953.com | Potentially Bad Traffic | ET INFO HTTP POST Request to Suspicious *.gq domain |
312 | RQF10577389953.com | A Network Trojan was detected | ET TROJAN LokiBot Application/Credential Data Exfiltration Detected M1 |