| File name: | random.exe |
| Full analysis: | https://app.any.run/tasks/38cf2e84-2480-4c7e-8dd6-01022382a5fe |
| Verdict: | Malicious activity |
| Threats: | Amadey is a formidable Windows infostealer threat, characterized by its persistence mechanisms, modular design, and ability to execute various malicious tasks. |
| Analysis date: | April 18, 2025, 07:20:16 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, 7 sections |
| MD5: | 9103DEDCE3145E133CC78BC88E6B09B7 |
| SHA1: | 84F1BDBB6FF787809E5CA80F17915FD8C517D531 |
| SHA256: | 24C60271CDE0B25F2DE2B469A70528918FEE280E5F3F67D695B2F21C85CB6287 |
| SSDEEP: | 98304:i52LcStgXS9Z6077kYBOzZd50WQzqkXohcouRw77aAqXCvvUeGLaGuZh5JsbSQ3u:r2 |
MALICIOUS
Connects to the CnC server
- svchost.exe (PID: 2196)
- namez.exe (PID: 8140)
LUMMA has been detected (YARA)
- random.exe (PID: 7336)
- MSBuild.exe (PID: 4220)
LUMMA has been detected (SURICATA)
- svchost.exe (PID: 2196)
- random.exe (PID: 7336)
- 19539e5132.exe (PID: 7904)
- 19539e5132.exe (PID: 2552)
- core.exe (PID: 7704)
- MSBuild.exe (PID: 7184)
- MSBuild.exe (PID: 3800)
- aZOpr5t.exe (PID: 7676)
- Hmcm0Oj.exe (PID: 8344)
AMADEY has been detected (SURICATA)
- namez.exe (PID: 8140)
Steals credentials from Web Browsers
- random.exe (PID: 7336)
- MSBuild.exe (PID: 4220)
- 19539e5132.exe (PID: 7904)
- 19539e5132.exe (PID: 2552)
- core.exe (PID: 7704)
- aZOpr5t.exe (PID: 7676)
- MSBuild.exe (PID: 7184)
- MSBuild.exe (PID: 3800)
GENERIC has been found (auto)
- 3f0783acc1.exe (PID: 6640)
- cd58f59688.tmp (PID: 7300)
- svchost015.exe (PID: 4988)
- svchost015.exe (PID: 672)
- svchost.exe (PID: 7388)
GCLEANER has been detected (SURICATA)
- svchost015.exe (PID: 4988)
- svchost015.exe (PID: 672)
GCLEANER has been detected (YARA)
- svchost015.exe (PID: 4988)
- svchost015.exe (PID: 672)
AMADEY has been detected (YARA)
- namez.exe (PID: 8140)
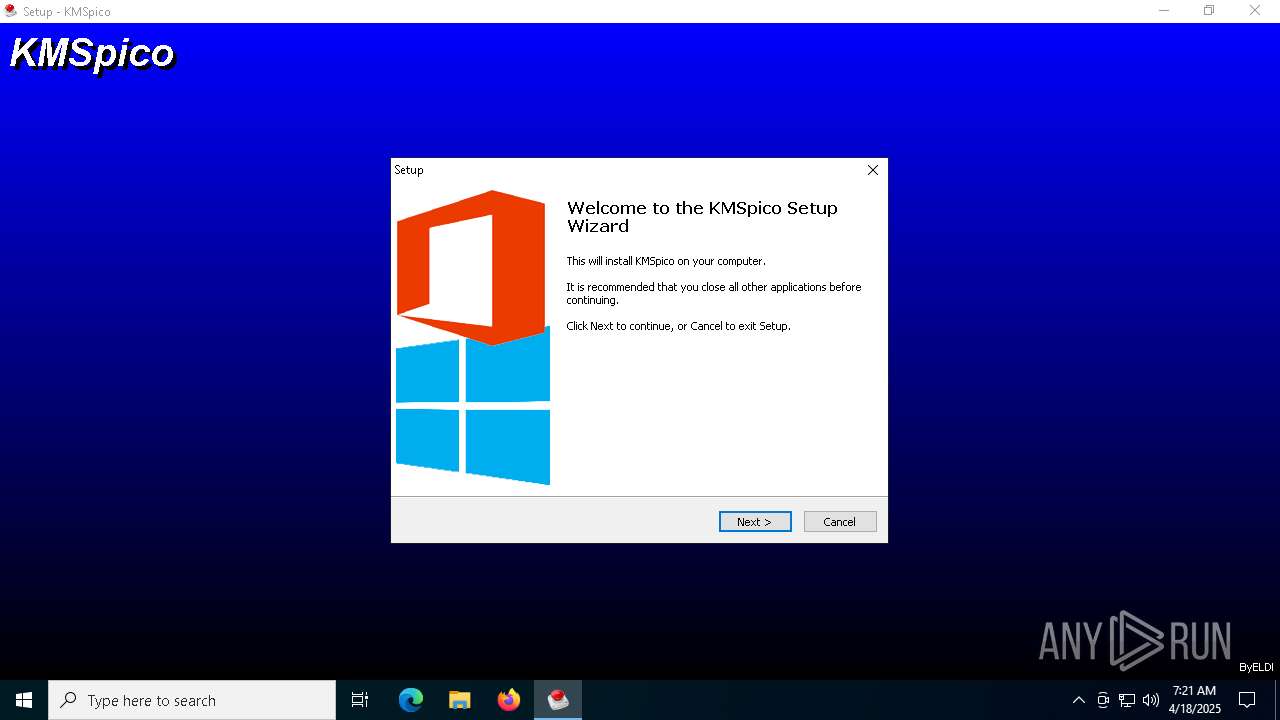
Executing a file with an untrusted certificate
- KMSpico.exe (PID: 7864)
- KMSpico.exe (PID: 7760)
- core.exe (PID: 7704)
- XOvCYdj.exe (PID: 7468)
- i5Kz53x.exe (PID: 2392)
- XOvCYdj.exe (PID: 8372)
PHISHING has been detected (SURICATA)
- svchost.exe (PID: 2196)
Changes the autorun value in the registry
- namez.exe (PID: 8140)
- svchost.exe (PID: 7388)
Disables Windows Defender
- 7838cb9b87.exe (PID: 7344)
Possible tool for stealing has been detected
- 9525873fc1.exe (PID: 2644)
- firefox.exe (PID: 5728)
- 9525873fc1.exe (PID: 5216)
- firefox.exe (PID: 1348)
Bypass execution policy to execute commands
- powershell.exe (PID: 4200)
Changes powershell execution policy (Bypass)
- core.exe (PID: 7704)
Changes the Windows auto-update feature
- 7838cb9b87.exe (PID: 7344)
Known privilege escalation attack
- dllhost.exe (PID: 7900)
Changes Windows Defender settings
- mmc.exe (PID: 6824)
Adds path to the Windows Defender exclusion list
- mmc.exe (PID: 6824)
Run PowerShell with an invisible window
- powershell.exe (PID: 7816)
- powershell.exe (PID: 6576)
MINER has been detected (SURICATA)
- svchost.exe (PID: 2196)
SUSPICIOUS
Contacting a server suspected of hosting an CnC
- svchost.exe (PID: 2196)
- namez.exe (PID: 8140)
- random.exe (PID: 7336)
- 19539e5132.exe (PID: 7904)
- 19539e5132.exe (PID: 2552)
- core.exe (PID: 7704)
- aZOpr5t.exe (PID: 7676)
- MSBuild.exe (PID: 7184)
- MSBuild.exe (PID: 3800)
- Hmcm0Oj.exe (PID: 8344)
Executable content was dropped or overwritten
- RJWWSKS6F7UONUQCOF.exe (PID: 8068)
- random.exe (PID: 7336)
- namez.exe (PID: 8140)
- 3f0783acc1.exe (PID: 6640)
- cd58f59688.exe (PID: 7324)
- cd58f59688.tmp (PID: 7300)
- KMSpico.exe (PID: 7864)
- KMSpico.tmp (PID: 7780)
- KMSpico.exe (PID: 7760)
- 19539e5132.exe (PID: 7904)
- 19539e5132.exe (PID: 2552)
- svchost015.exe (PID: 4988)
- svchost015.exe (PID: 672)
- svchost.exe (PID: 7388)
- mmc.exe (PID: 6824)
- aro5Tjw.exe (PID: 5556)
- XOvCYdj.exe (PID: 7468)
Potential Corporate Privacy Violation
- random.exe (PID: 7336)
- namez.exe (PID: 8140)
- 19539e5132.exe (PID: 7904)
- 19539e5132.exe (PID: 2552)
- svchost015.exe (PID: 4988)
- svchost015.exe (PID: 672)
- svchost.exe (PID: 7388)
Reads security settings of Internet Explorer
- RJWWSKS6F7UONUQCOF.exe (PID: 8068)
- namez.exe (PID: 8140)
- svchost015.exe (PID: 4988)
- svchost015.exe (PID: 672)
- cd58f59688.tmp (PID: 7300)
- KMSpico.tmp (PID: 7856)
- aro5Tjw.exe (PID: 5556)
- XOvCYdj.exe (PID: 7468)
Searches for installed software
- random.exe (PID: 7336)
- MSBuild.exe (PID: 4220)
- 19539e5132.exe (PID: 7904)
- 19539e5132.exe (PID: 2552)
- core.exe (PID: 7704)
- aZOpr5t.exe (PID: 7676)
- MSBuild.exe (PID: 3800)
- MSBuild.exe (PID: 7184)
Starts itself from another location
- RJWWSKS6F7UONUQCOF.exe (PID: 8068)
Process requests binary or script from the Internet
- random.exe (PID: 7336)
- namez.exe (PID: 8140)
- 19539e5132.exe (PID: 7904)
- 19539e5132.exe (PID: 2552)
Connects to the server without a host name
- random.exe (PID: 7336)
- namez.exe (PID: 8140)
- svchost015.exe (PID: 4988)
- svchost015.exe (PID: 672)
- 19539e5132.exe (PID: 7904)
- 19539e5132.exe (PID: 2552)
- svchost.exe (PID: 7388)
- mmc.exe (PID: 6824)
Process drops legitimate windows executable
- namez.exe (PID: 8140)
- KMSpico.tmp (PID: 7780)
- aro5Tjw.exe (PID: 5556)
Reads the BIOS version
- random.exe (PID: 7336)
- 3f0783acc1.exe (PID: 6640)
- 694c3b4028.exe (PID: 6872)
- 19539e5132.exe (PID: 7904)
- 19539e5132.exe (PID: 2552)
- 7838cb9b87.exe (PID: 7344)
- aZOpr5t.exe (PID: 7676)
- c6c12343d6.exe (PID: 920)
- c6c12343d6.exe (PID: 7344)
There is functionality for enable RDP (YARA)
- namez.exe (PID: 8140)
Starts a Microsoft application from unusual location
- 0dcce0575f.exe (PID: 6668)
- 235T1TS.exe (PID: 7020)
- i5Kz53x.exe (PID: 2392)
- crypted.exe (PID: 6244)
- sysdrv.exe (PID: 8252)
There is functionality for taking screenshot (YARA)
- namez.exe (PID: 8140)
- MSBuild.exe (PID: 4220)
Process communicates with Telegram (possibly using it as an attacker's C2 server)
- MSBuild.exe (PID: 4220)
Reads the Windows owner or organization settings
- cd58f59688.tmp (PID: 7300)
- KMSpico.tmp (PID: 7780)
- msiexec.exe (PID: 812)
The process executes via Task Scheduler
- namez.exe (PID: 7828)
- namez.exe (PID: 6112)
Uses TASKKILL.EXE to kill Browsers
- 9525873fc1.exe (PID: 2644)
- 9525873fc1.exe (PID: 5216)
Uses TASKKILL.EXE to kill process
- 9525873fc1.exe (PID: 2644)
- 9525873fc1.exe (PID: 5216)
Starts POWERSHELL.EXE for commands execution
- core.exe (PID: 7704)
- mmc.exe (PID: 6824)
- cmd.exe (PID: 232)
Drops 7-zip archiver for unpacking
- namez.exe (PID: 8140)
- msiexec.exe (PID: 812)
Executing commands from a ".bat" file
- svchost.exe (PID: 7388)
- aro5Tjw.exe (PID: 5556)
Starts CMD.EXE for commands execution
- svchost.exe (PID: 7388)
- aro5Tjw.exe (PID: 5556)
Script adds exclusion path to Windows Defender
- mmc.exe (PID: 6824)
Drops a system driver (possible attempt to evade defenses)
- mmc.exe (PID: 6824)
Creates or modifies Windows services
- mmc.exe (PID: 6824)
Reads the date of Windows installation
- aro5Tjw.exe (PID: 5556)
- XOvCYdj.exe (PID: 7468)
The executable file from the user directory is run by the CMD process
- crypted.exe (PID: 6244)
Connects to unusual port
- MSBuild.exe (PID: 7860)
Crypto Currency Mining Activity Detected
- svchost.exe (PID: 2196)
Application launched itself
- XOvCYdj.exe (PID: 7468)
INFO
Reads the computer name
- random.exe (PID: 7336)
- RJWWSKS6F7UONUQCOF.exe (PID: 8068)
- namez.exe (PID: 8140)
- MSBuild.exe (PID: 4220)
- 3f0783acc1.exe (PID: 6640)
- 694c3b4028.exe (PID: 6872)
- svchost015.exe (PID: 4988)
- cd58f59688.tmp (PID: 7300)
- svchost015.exe (PID: 672)
- KMSpico.tmp (PID: 7856)
- info.exe (PID: 1912)
- KMSpico.tmp (PID: 7780)
- 19539e5132.exe (PID: 7904)
- core.exe (PID: 7704)
- 7838cb9b87.exe (PID: 7344)
- 9525873fc1.exe (PID: 2644)
- msiexec.exe (PID: 812)
- 9525873fc1.exe (PID: 5216)
- aZOpr5t.exe (PID: 7676)
- 19539e5132.exe (PID: 2552)
- XOvCYdj.exe (PID: 7468)
- c6c12343d6.exe (PID: 920)
- 235T1TS.exe (PID: 7020)
- tzutil.exe (PID: 864)
- w32tm.exe (PID: 6592)
- MSBuild.exe (PID: 7184)
- MSBuild.exe (PID: 3800)
- aro5Tjw.exe (PID: 5556)
- MSBuild.exe (PID: 7860)
- sysdrv.exe (PID: 8252)
- XOvCYdj.exe (PID: 8372)
- Hmcm0Oj.exe (PID: 8344)
Themida protector has been detected
- random.exe (PID: 7336)
Create files in a temporary directory
- random.exe (PID: 7336)
- RJWWSKS6F7UONUQCOF.exe (PID: 8068)
- namez.exe (PID: 8140)
- 3f0783acc1.exe (PID: 6640)
- cd58f59688.exe (PID: 7324)
- cd58f59688.tmp (PID: 7300)
- KMSpico.exe (PID: 7864)
- KMSpico.tmp (PID: 7780)
- KMSpico.exe (PID: 7760)
- 19539e5132.exe (PID: 7904)
- 19539e5132.exe (PID: 2552)
- msiexec.exe (PID: 5228)
- powershell.exe (PID: 4200)
- svchost015.exe (PID: 4988)
- svchost015.exe (PID: 672)
- svchost.exe (PID: 7388)
- w32tm.exe (PID: 6592)
- aro5Tjw.exe (PID: 5556)
Checks supported languages
- RJWWSKS6F7UONUQCOF.exe (PID: 8068)
- namez.exe (PID: 8140)
- random.exe (PID: 7336)
- 0dcce0575f.exe (PID: 6668)
- 3f0783acc1.exe (PID: 6640)
- MSBuild.exe (PID: 4220)
- svchost015.exe (PID: 4988)
- 694c3b4028.exe (PID: 6872)
- svchost015.exe (PID: 672)
- cd58f59688.tmp (PID: 7300)
- cd58f59688.exe (PID: 7324)
- namez.exe (PID: 7828)
- KMSpico.exe (PID: 7864)
- KMSpico.tmp (PID: 7780)
- KMSpico.exe (PID: 7760)
- KMSpico.tmp (PID: 7856)
- info.exe (PID: 1912)
- 19539e5132.exe (PID: 7904)
- core.exe (PID: 7704)
- 19539e5132.exe (PID: 2552)
- 7838cb9b87.exe (PID: 7344)
- T7I1VMGCTT7IXT9N8GXWIB.exe (PID: 4696)
- 9525873fc1.exe (PID: 2644)
- R7FXOGJAHKWRLZMIFG8AGE63HHGT06.exe (PID: 6436)
- msiexec.exe (PID: 812)
- 9525873fc1.exe (PID: 5216)
- aZOpr5t.exe (PID: 7676)
- XOvCYdj.exe (PID: 7468)
- c6c12343d6.exe (PID: 920)
- c6c12343d6.exe (PID: 7344)
- LAc2heq.exe (PID: 5732)
- 235T1TS.exe (PID: 7020)
- w32tm.exe (PID: 6592)
- tzutil.exe (PID: 864)
- i5Kz53x.exe (PID: 2392)
- MSBuild.exe (PID: 7184)
- MSBuild.exe (PID: 3800)
- namez.exe (PID: 6112)
- crypted.exe (PID: 6244)
- aro5Tjw.exe (PID: 5556)
- rXEnFII.exe (PID: 5452)
- MSBuild.exe (PID: 7860)
- sysdrv.exe (PID: 8252)
- XOvCYdj.exe (PID: 8372)
- Hmcm0Oj.exe (PID: 8344)
Process checks computer location settings
- RJWWSKS6F7UONUQCOF.exe (PID: 8068)
- namez.exe (PID: 8140)
- cd58f59688.tmp (PID: 7300)
- KMSpico.tmp (PID: 7856)
- aro5Tjw.exe (PID: 5556)
- XOvCYdj.exe (PID: 7468)
Checks proxy server information
- namez.exe (PID: 8140)
- svchost015.exe (PID: 4988)
- svchost015.exe (PID: 672)
Creates files or folders in the user directory
- namez.exe (PID: 8140)
- svchost015.exe (PID: 4988)
- svchost015.exe (PID: 672)
- cd58f59688.tmp (PID: 7300)
Reads the software policy settings
- random.exe (PID: 7336)
- MSBuild.exe (PID: 4220)
- 19539e5132.exe (PID: 7904)
- 19539e5132.exe (PID: 2552)
- core.exe (PID: 7704)
- powershell.exe (PID: 4200)
- aZOpr5t.exe (PID: 7676)
- slui.exe (PID: 7516)
- MSBuild.exe (PID: 7184)
- MSBuild.exe (PID: 3800)
Attempting to use instant messaging service
- MSBuild.exe (PID: 4220)
The sample compiled with english language support
- 3f0783acc1.exe (PID: 6640)
- namez.exe (PID: 8140)
- KMSpico.tmp (PID: 7780)
- msiexec.exe (PID: 812)
- svchost.exe (PID: 7388)
- aro5Tjw.exe (PID: 5556)
- XOvCYdj.exe (PID: 7468)
Creates a software uninstall entry
- cd58f59688.tmp (PID: 7300)
Reads the machine GUID from the registry
- svchost015.exe (PID: 4988)
- svchost015.exe (PID: 672)
- c6c12343d6.exe (PID: 920)
- w32tm.exe (PID: 6592)
- MSBuild.exe (PID: 7860)
Auto-launch of the file from Registry key
- namez.exe (PID: 8140)
- svchost.exe (PID: 7388)
Manual execution by a user
- 19539e5132.exe (PID: 2552)
- 7838cb9b87.exe (PID: 5072)
- 9525873fc1.exe (PID: 5216)
Detects InnoSetup installer (YARA)
- KMSpico.exe (PID: 7864)
Reads mouse settings
- 9525873fc1.exe (PID: 2644)
- 9525873fc1.exe (PID: 5216)
Application launched itself
- firefox.exe (PID: 5728)
- firefox.exe (PID: 6540)
- firefox.exe (PID: 1348)
- firefox.exe (PID: 5392)
Executable content was dropped or overwritten
- msiexec.exe (PID: 812)
Reads security settings of Internet Explorer
- powershell.exe (PID: 4200)
- dllhost.exe (PID: 7900)
- svchost.exe (PID: 7388)
Script raised an exception (POWERSHELL)
- powershell.exe (PID: 4200)
- powershell.exe (PID: 5404)
- powershell.exe (PID: 7816)
Creates files in the program directory
- 235T1TS.exe (PID: 7020)
- svchost.exe (PID: 7388)
- XOvCYdj.exe (PID: 7468)
Checks if a key exists in the options dictionary (POWERSHELL)
- powershell.exe (PID: 5404)
- powershell.exe (PID: 7816)
The executable file from the user directory is run by the Powershell process
- sysdrv.exe (PID: 8252)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Lumma
(PID) Process(7336) random.exe
C2 (9)changeaie.top/geps
quilltayle.live/gksi
zestmodp.top/zeda
clarmodq.top/qoxo
nighetwhisper.top/lekd
liftally.top/xasj
piratetwrath.run/ytus
starofliught.top/wozd
salaccgfa.top/gsooz
(PID) Process(4220) MSBuild.exe
C2 (10)changeaie.top/geps
jawdedmirror.run/ewqd
owlflright.digital/qopy
https://t.me/cobasck
zestmodp.top/zeda
lonfgshadow.live/xawi
overlapseq.digital/yqoi
nighetwhisper.top/lekd
liftally.top/xasj
salaccgfa.top/gsooz
Amadey
(PID) Process(8140) namez.exe
C2185.215.113.59
URLhttp://185.215.113.59/Dy5h4kus/index.php
Version5.34
Options
Drop directoryf1e82329e5
Drop namenamez.exe
Strings (125)os:
Norton
st=s
vs:
2022
clip.dll
sd:
Programs
/Dy5h4kus/index.php
av:
ComputerName
Panda Security
abcdefghijklmnopqrstuvwxyz0123456789-_
:::
dll
SOFTWARE\Microsoft\Windows NT\CurrentVersion
ar:
0123456789
Bitdefender
un:
shell32.dll
SYSTEM\CurrentControlSet\Control\ComputerName\ComputerName
rundll32.exe
------
id:
pc:
Keyboard Layout\Preload
dm:
wb
og:
rb
SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\User Shell Folders
00000423
\0000
AVG
\
Rem
rundll32
#
=
GetNativeSystemInfo
random
zip
.jpg
00000419
ESET
lv:
Main
"
SYSTEM\CurrentControlSet\Control\UnitedVideo\CONTROL\VIDEO\
SOFTWARE\Microsoft\Windows\CurrentVersion\RunOnce
S-%lu-
SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\Shell Folders
Content-Type: multipart/form-data; boundary=----
ps1
360TotalSecurity
+++
r=
POST
/quiet
Powershell.exe
shutdown -s -t 0
185.215.113.59
SOFTWARE\Microsoft\Windows\CurrentVersion\Run
DefaultSettings.YResolution
d1
cred.dll|clip.dll|
2019
cmd /C RMDIR /s/q
5.34
2016
Content-Disposition: form-data; name="data"; filename="
-executionpolicy remotesigned -File "
"taskkill /f /im "
Kaspersky Lab
&&
------
e1
SYSTEM\ControlSet001\Services\BasicDisplay\Video
%-lu
<c>
namez.exe
ProgramData\
f1e82329e5
/k
exe
CurrentBuild
e2
&unit=
msi
VideoID
Sophos
"
Content-Type: application/octet-stream
Content-Type: application/x-www-form-urlencoded
-%lu
|
https://
\App
--
-unicode-
cmd
ProductName
kernel32.dll
e3
<d>
cred.dll
" && ren
Avira
0000043f
%USERPROFILE%
AVAST Software
/Plugins/
?scr=1
http://
&& Exit"
00000422
Comodo
" && timeout 1 && del
bi:
GET
WinDefender
DefaultSettings.XResolution
Startup
Doctor Web
2025
TRiD
| .exe | | | Generic Win/DOS Executable (50) |
|---|---|---|
| .exe | | | DOS Executable Generic (49.9) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2025:04:15 21:13:48+00:00 |
| ImageFileCharacteristics: | Executable, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 14 |
| CodeSize: | 317952 |
| InitializedDataSize: | 39936 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x4b2000 |
| OSVersion: | 6 |
| ImageVersion: | - |
| SubsystemVersion: | 6 |
| Subsystem: | Windows GUI |
Total processes
250
Monitored processes
115
Malicious processes
35
Suspicious processes
7
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 132 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 232 | C:\WINDOWS\system32\cmd.exe /c ""C:\Users\admin\AppData\Local\Temp\SystemService\start.bat" " | C:\Windows\System32\cmd.exe | — | aro5Tjw.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 496 | taskkill /F /IM chrome.exe /T | C:\Windows\SysWOW64\taskkill.exe | — | 9525873fc1.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Terminates Processes Exit code: 128 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 664 | taskkill /F /IM firefox.exe /T | C:\Windows\SysWOW64\taskkill.exe | — | 9525873fc1.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Terminates Processes Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 672 | "C:\Users\admin\AppData\Local\Temp\10043380101\694c3b4028.exe" | C:\Users\admin\AppData\Local\Temp\svchost015.exe | 694c3b4028.exe | ||||||||||||
User: admin Company: X-Ways Software Technology AG Integrity Level: MEDIUM Description: WinHex Exit code: 0 Version: 21.1 Modules
| |||||||||||||||
| 684 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | taskkill.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 684 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel=2016 -parentBuildID 20240213221259 -prefsHandle 2008 -prefMapHandle 2004 -prefsLen 32427 -prefMapSize 244583 -win32kLockedDown -appDir "C:\Program Files\Mozilla Firefox\browser" - {1f7fb0d8-37ae-40a2-a1a8-c357027f2d7e} 5392 "\\.\pipe\gecko-crash-server-pipe.5392" 1b8f8f84110 socket | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Version: 123.0 Modules
| |||||||||||||||
| 812 | C:\WINDOWS\system32\msiexec.exe /V | C:\Windows\System32\msiexec.exe | services.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows® installer Version: 5.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 864 | "C:\ProgramData\{425F784E-921A-4CC0-AE87-06A3B0393A0E}\tzutil.exe" "" | C:\ProgramData\{425F784E-921A-4CC0-AE87-06A3B0393A0E}\tzutil.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Resource and Performance Monitor Exit code: 0 Version: 10.00 Modules
| |||||||||||||||
| 920 | "C:\Users\admin\AppData\Local\Temp\10043460101\c6c12343d6.exe" | C:\Users\admin\AppData\Local\Temp\10043460101\c6c12343d6.exe | — | namez.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
Total events
69 402
Read events
69 323
Write events
70
Delete events
9
Modification events
| (PID) Process: | (8140) namez.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (8140) namez.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (8140) namez.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (4988) svchost015.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (4988) svchost015.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (4988) svchost015.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (672) svchost015.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (672) svchost015.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (672) svchost015.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (7300) cd58f59688.tmp | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\MyApp_is1 |
| Operation: | write | Name: | Inno Setup: Setup Version |
Value: 6.4.0 | |||
Executable files
69
Suspicious files
205
Text files
41
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 8068 | RJWWSKS6F7UONUQCOF.exe | C:\Users\admin\AppData\Local\Temp\f1e82329e5\namez.exe | executable | |
MD5:3EC886E81B3A5649FF9DAC6D88BABA96 | SHA256:ECC4CDE448FA9B09BFFC77555B878E1656AC4E5C6C4218B08078EE85B1B8F8D5 | |||
| 7300 | cd58f59688.tmp | C:\Users\admin\AppData\Roaming\MyApp\is-IKVCK.tmp | — | |
MD5:— | SHA256:— | |||
| 7300 | cd58f59688.tmp | C:\Users\admin\AppData\Roaming\MyApp\core.exe | — | |
MD5:— | SHA256:— | |||
| 8140 | namez.exe | C:\Users\admin\AppData\Local\Temp\10043370101\3f0783acc1.exe | executable | |
MD5:5D314B0CCE9388B469A0478306F88D48 | SHA256:6913E064AB05ADB891C9A64B1A1B3C361F08DB2073603C88A4CEE616B69C0C11 | |||
| 8140 | namez.exe | C:\Users\admin\AppData\Local\Temp\10043360101\0dcce0575f.exe | executable | |
MD5:AF5AB75EAA7716A26F543D06CA4BC1FC | SHA256:4D34C2C4890D33B17BCEEE71D1ADBD186A8E4414365E371E1DE85D3B359B9AA1 | |||
| 4988 | svchost015.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\IE\RR3E01RZ\success[1].htm | binary | |
MD5:CFCD208495D565EF66E7DFF9F98764DA | SHA256:5FECEB66FFC86F38D952786C6D696C79C2DBC239DD4E91B46729D73A27FB57E9 | |||
| 7324 | cd58f59688.exe | C:\Users\admin\AppData\Local\Temp\is-KN2OD.tmp\cd58f59688.tmp | executable | |
MD5:E4C43138CCB8240276872FD1AEC369BE | SHA256:46BE5E3F28A5E4ED63D66B901D927C25944B4DA36EFFEA9C97FB05994360EDF5 | |||
| 8068 | RJWWSKS6F7UONUQCOF.exe | C:\Windows\Tasks\namez.job | binary | |
MD5:FD356E07EB9DCAD38FA3A6B7478F938B | SHA256:E665CB6801B99E42C18E7337DF755AE43BFB27513DF770D102BAC2169E1D5CA9 | |||
| 7300 | cd58f59688.tmp | C:\Users\admin\AppData\Local\Temp\is-UVFCE.tmp\_isetup\_setup64.tmp | executable | |
MD5:E4211D6D009757C078A9FAC7FF4F03D4 | SHA256:388A796580234EFC95F3B1C70AD4CB44BFDDC7BA0F9203BF4902B9929B136F95 | |||
| 8140 | namez.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\IE\E4DJRUXW\random[1].exe | executable | |
MD5:56F12BB2BD6BCB7206A50AB15133FA1E | SHA256:B9B0C91EBB43B4610B5E9BC01D3EDE61F76E0664DDB5F6F5B8FAC27D88401246 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
186
TCP/UDP connections
248
DNS requests
169
Threats
176
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
7336 | random.exe | GET | 200 | 185.39.17.162:80 | http://185.39.17.162/mine/random.exe | unknown | — | — | unknown |
— | — | GET | 200 | 23.216.77.42:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | GET | 200 | 23.216.77.42:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
8140 | namez.exe | POST | 200 | 185.215.113.59:80 | http://185.215.113.59/Dy5h4kus/index.php | unknown | — | — | malicious |
8140 | namez.exe | GET | 200 | 185.39.17.162:80 | http://185.39.17.162/files/fate/random.exe | unknown | — | — | unknown |
8140 | namez.exe | POST | 200 | 185.215.113.59:80 | http://185.215.113.59/Dy5h4kus/index.php | unknown | — | — | malicious |
8140 | namez.exe | GET | 200 | 185.39.17.162:80 | http://185.39.17.162/files/unique2/random.exe | unknown | — | — | unknown |
6544 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
8140 | namez.exe | POST | 200 | 185.215.113.59:80 | http://185.215.113.59/Dy5h4kus/index.php | unknown | — | — | malicious |
8140 | namez.exe | GET | 200 | 185.39.17.162:80 | http://185.39.17.162/files/martin2/random.exe | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 20.73.194.208:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 23.216.77.42:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
5496 | MoUsoCoreWorker.exe | 23.216.77.42:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
2104 | svchost.exe | 20.73.194.208:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
7336 | random.exe | 172.67.205.184:443 | clarmodq.top | CLOUDFLARENET | US | malicious |
2112 | svchost.exe | 20.73.194.208:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
3216 | svchost.exe | 172.211.123.250:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
6544 | svchost.exe | 40.126.32.140:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
crl.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
clarmodq.top |
| malicious |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
t.me |
| whitelisted |
overlapseq.digital |
| malicious |
slscr.update.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2196 | svchost.exe | Potentially Bad Traffic | ET DNS Query to a *.top domain - Likely Hostile |
7336 | random.exe | Domain Observed Used for C2 Detected | ET MALWARE Observed Win32/Lumma Stealer Related Domain (clarmodq .top in TLS SNI) |
2196 | svchost.exe | A Network Trojan was detected | MALWARE [ANY.RUN] Suspected Domain Associated with Malware Distribution (clarmodq .top) |
2196 | svchost.exe | Domain Observed Used for C2 Detected | ET MALWARE Win32/Lumma Stealer Related CnC Domain in DNS Lookup (clarmodq .top) |
7336 | random.exe | Domain Observed Used for C2 Detected | ET MALWARE Observed Win32/Lumma Stealer Related Domain (clarmodq .top in TLS SNI) |
7336 | random.exe | Domain Observed Used for C2 Detected | ET MALWARE Observed Win32/Lumma Stealer Related Domain (clarmodq .top in TLS SNI) |
7336 | random.exe | Domain Observed Used for C2 Detected | ET MALWARE Observed Win32/Lumma Stealer Related Domain (clarmodq .top in TLS SNI) |
7336 | random.exe | Domain Observed Used for C2 Detected | ET MALWARE Observed Win32/Lumma Stealer Related Domain (clarmodq .top in TLS SNI) |
7336 | random.exe | Domain Observed Used for C2 Detected | ET MALWARE Observed Win32/Lumma Stealer Related Domain (clarmodq .top in TLS SNI) |
7336 | random.exe | Potentially Bad Traffic | ET INFO Executable Download from dotted-quad Host |