| File name: | purchase order.doc |
| Full analysis: | https://app.any.run/tasks/7ea52ae3-0de7-4f25-bc3f-ccdfec22baa6 |
| Verdict: | Malicious activity |
| Threats: | Agent Tesla is spyware that collects information about the actions of its victims by recording keystrokes and user interactions. It is falsely marketed as a legitimate software on the dedicated website where this malware is sold. |
| Analysis date: | June 19, 2019, 03:16:48 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | text/rtf |
| File info: | Rich Text Format data, version 1, unknown character set |
| MD5: | B819877F4D1F3639902A3716C48E5994 |
| SHA1: | 82410483EAE34FC15F10CF1185E7B42787750518 |
| SHA256: | 24A6293BA60DBF92BC3391E24F9DBC78A8E2A1B8751C4A6333A19033E9522FAB |
| SSDEEP: | 24576:pd6qlMEjK5+nmJdGMBHLCpVMkTYe/U0mn1pDkAE7EG2elVPGjOjrGv05SoFU:+ |
MALICIOUS
Unusual execution from Microsoft Office
- WINWORD.EXE (PID: 3932)
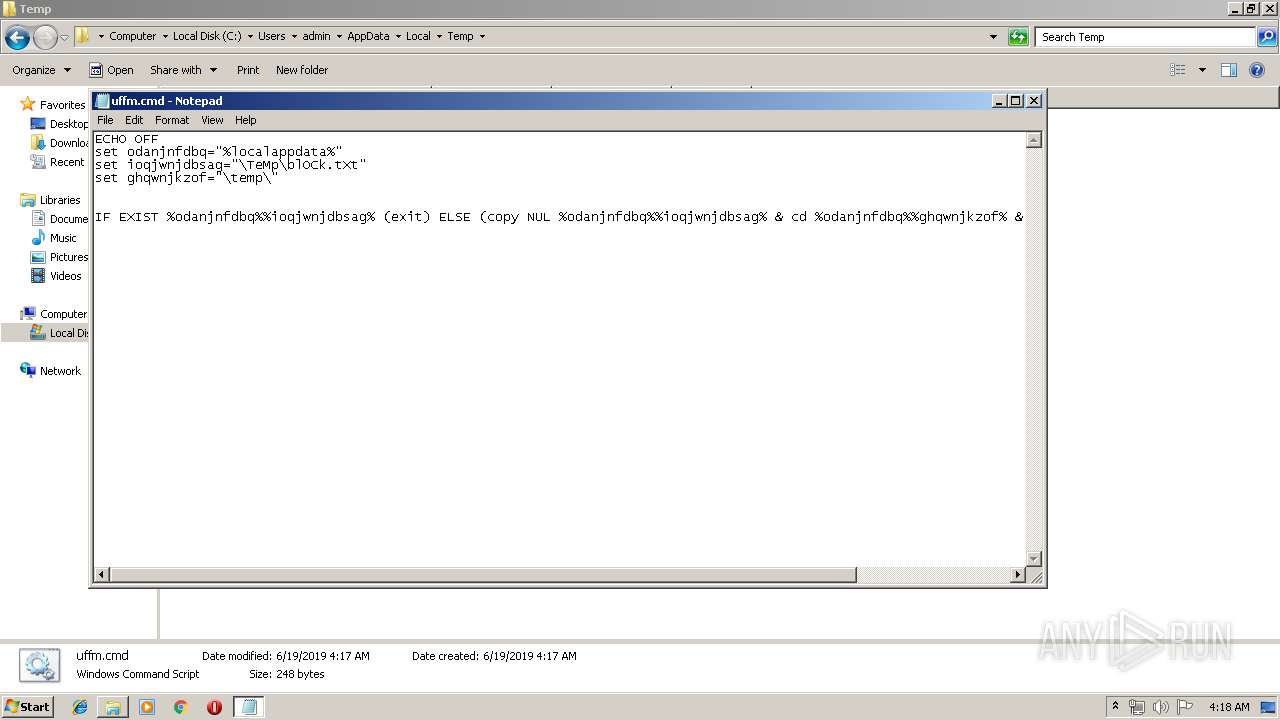
Starts CMD.EXE for commands execution
- WINWORD.EXE (PID: 3932)
Runs app for hidden code execution
- cmd.exe (PID: 1040)
- cmd.exe (PID: 1572)
Application was dropped or rewritten from another process
- saver.scr (PID: 3900)
- saver.scr (PID: 3308)
Actions looks like stealing of personal data
- saver.scr (PID: 3308)
Changes settings of System certificates
- saver.scr (PID: 3308)
AGENTTESLA was detected
- saver.scr (PID: 3308)
SUSPICIOUS
Starts CMD.EXE for commands execution
- cmd.exe (PID: 1572)
- cmd.exe (PID: 1040)
- cmd.exe (PID: 2324)
- cmd.exe (PID: 2328)
Uses REG.EXE to modify Windows registry
- cmd.exe (PID: 3120)
- cmd.exe (PID: 1040)
- cmd.exe (PID: 3100)
- cmd.exe (PID: 2600)
- cmd.exe (PID: 2328)
- cmd.exe (PID: 3656)
- cmd.exe (PID: 3920)
Executable content was dropped or overwritten
- cscript.exe (PID: 2172)
Executes scripts
- cmd.exe (PID: 2328)
Starts application with an unusual extension
- cmd.exe (PID: 2328)
- saver.scr (PID: 3900)
Application launched itself
- saver.scr (PID: 3900)
- cmd.exe (PID: 2328)
Adds / modifies Windows certificates
- saver.scr (PID: 3308)
Creates files in the user directory
- notepad++.exe (PID: 944)
Checks for external IP
- saver.scr (PID: 3308)
Uses TASKKILL.EXE to kill Office Apps
- cmd.exe (PID: 2328)
INFO
Creates files in the user directory
- WINWORD.EXE (PID: 3932)
Reads Microsoft Office registry keys
- WINWORD.EXE (PID: 3932)
Manual execution by user
- explorer.exe (PID: 2484)
- NOTEPAD.EXE (PID: 3148)
- notepad++.exe (PID: 944)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .rtf | | | Rich Text Format (100) |
|---|
Total processes
80
Monitored processes
42
Malicious processes
6
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 712 | REG QUERY "HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\15.0\Word\File MRU" /v "Item 1" | C:\Windows\system32\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Registry Console Tool Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 944 | "C:\Program Files\Notepad++\notepad++.exe" "C:\Users\admin\AppData\Local\Temp\saver.scr" | C:\Program Files\Notepad++\notepad++.exe | explorer.exe | ||||||||||||
User: admin Company: Don HO don.h@free.fr Integrity Level: MEDIUM Description: Notepad++ : a free (GNU) source code editor Exit code: 0 Version: 7.51 Modules
| |||||||||||||||
| 1012 | reg delete HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\14.0\Word\Resiliency /f | C:\Windows\system32\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Registry Console Tool Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1040 | "C:\Windows\System32\cmd.exe" /C CmD < "C:\Users\admin\AppData\Local\Temp\ufFm.cMD" | C:\Windows\System32\cmd.exe | — | WINWORD.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 1040 | C:\Windows\system32\cmd.exe /c REG QUERY "HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\13.0\Word\File MRU" /v "Item 1" | C:\Windows\system32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 1 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 1352 | REG QUERY "HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\12.0\Word\File MRU" /v "Item 1" | C:\Windows\system32\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Registry Console Tool Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1456 | REG QUERY "HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Word\File MRU" /v "Item 1" | C:\Windows\system32\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Registry Console Tool Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1484 | TIMEOUT /T 1 | C:\Windows\system32\timeout.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: timeout - pauses command processing Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1548 | TIMEOUT /T 1 | C:\Windows\system32\timeout.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: timeout - pauses command processing Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1572 | "C:\Windows\System32\cmd.exe" /C CmD < "C:\Users\admin\AppData\Local\Temp\ufFm.cMD" | C:\Windows\System32\cmd.exe | — | WINWORD.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
Total events
1 288
Read events
1 205
Write events
77
Delete events
6
Modification events
| (PID) Process: | (3932) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Word\Resiliency\StartupItems |
| Operation: | write | Name: | '3< |
Value: 27333C005C0F0000010000000000000000000000 | |||
| (PID) Process: | (3932) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: Off | |||
| (PID) Process: | (3932) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: On | |||
| (PID) Process: | (3932) WINWORD.EXE | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\UserData\S-1-5-18\Products\00004109D30000000000000000F01FEC\Usage |
| Operation: | write | Name: | WORDFiles |
Value: 1322450974 | |||
| (PID) Process: | (3932) WINWORD.EXE | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\UserData\S-1-5-18\Products\00004109D30000000000000000F01FEC\Usage |
| Operation: | write | Name: | ProductFiles |
Value: 1322451088 | |||
| (PID) Process: | (3932) WINWORD.EXE | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\UserData\S-1-5-18\Products\00004109D30000000000000000F01FEC\Usage |
| Operation: | write | Name: | ProductFiles |
Value: 1322451089 | |||
| (PID) Process: | (3932) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Word |
| Operation: | write | Name: | MTTT |
Value: 5C0F0000F4426F784D26D50100000000 | |||
| (PID) Process: | (3932) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Word\Resiliency\StartupItems |
| Operation: | write | Name: | 04< |
Value: 30343C005C0F000004000000000000008C00000001000000840000003E0043003A005C00550073006500720073005C00610064006D0069006E005C0041007000700044006100740061005C0052006F0061006D0069006E0067005C004D006900630072006F0073006F00660074005C00540065006D0070006C0061007400650073005C004E006F0072006D0061006C002E0064006F0074006D00000000000000 | |||
| (PID) Process: | (3932) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Word\Resiliency\StartupItems |
| Operation: | delete value | Name: | 04< |
Value: 30343C005C0F000004000000000000008C00000001000000840000003E0043003A005C00550073006500720073005C00610064006D0069006E005C0041007000700044006100740061005C0052006F0061006D0069006E0067005C004D006900630072006F0073006F00660074005C00540065006D0070006C0061007400650073005C004E006F0072006D0061006C002E0064006F0074006D00000000000000 | |||
| (PID) Process: | (3932) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
Executable files
1
Suspicious files
3
Text files
15
Unknown types
4
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3932 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\CVR42F8.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 3932 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Templates\~$Normal.dotm | pgc | |
MD5:— | SHA256:— | |||
| 3932 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\~$rchase order.doc | pgc | |
MD5:— | SHA256:— | |||
| 3932 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\mt6nzqofd.cmd | text | |
MD5:— | SHA256:— | |||
| 2172 | cscript.exe | C:\Users\admin\AppData\Local\Temp\gondi.doc | text | |
MD5:— | SHA256:— | |||
| 3932 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\kulebiaka.ZiP | compressed | |
MD5:— | SHA256:— | |||
| 2328 | cmd.exe | C:\Users\admin\AppData\Local\Temp\_.vbs | text | |
MD5:— | SHA256:— | |||
| 2172 | cscript.exe | C:\Users\admin\AppData\Local\Temp\saver.scr | executable | |
MD5:— | SHA256:— | |||
| 3932 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.Word\~WRS{FC32EBD7-5383-46A6-B5C4-8234080746C7}.tmp | binary | |
MD5:— | SHA256:— | |||
| 3932 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.Word\~WRF{62D90A86-B78C-4F7A-BDE1-31C04A785FB9}.tmp | binary | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
2
TCP/UDP connections
4
DNS requests
4
Threats
4
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 2.16.186.35:80 | http://isrg.trustid.ocsp.identrust.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBRv9GhNQxLSSGKBnMArPUcsHYovpgQUxKexpHsscfrb4UuQdf%2FEFWCFiRACEAoBQUIAAAFThXNqC4Xspwg%3D | unknown | der | 1.37 Kb | whitelisted |
3308 | saver.scr | GET | 200 | 34.233.102.38:80 | http://checkip.amazonaws.com/ | US | text | 15 b | malicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2776 | gup.exe | 37.59.28.236:443 | notepad-plus-plus.org | OVH SAS | FR | whitelisted |
3308 | saver.scr | 82.221.130.149:587 | smtp.vivaldi.net | Thor Data Center ehf | IS | unknown |
3308 | saver.scr | 34.233.102.38:80 | checkip.amazonaws.com | Amazon.com, Inc. | US | shared |
— | — | 2.16.186.35:80 | isrg.trustid.ocsp.identrust.com | Akamai International B.V. | — | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
smtp.vivaldi.net |
| malicious |
notepad-plus-plus.org |
| whitelisted |
isrg.trustid.ocsp.identrust.com |
| whitelisted |
checkip.amazonaws.com |
| malicious |
Threats
PID | Process | Class | Message |
|---|---|---|---|
3308 | saver.scr | Generic Protocol Command Decode | SURICATA Applayer Detect protocol only one direction |
3308 | saver.scr | A Network Trojan was detected | MALWARE [PTsecurity] AgentTesla IP Check |
2 ETPRO signatures available at the full report
Process | Message |
|---|---|
notepad++.exe | VerifyLibrary: C:\Program Files\Notepad++\SciLexer.dll
|
notepad++.exe | VerifyLibrary: certificate revocation checking is disabled
|
notepad++.exe | 42C4C5846BB675C74E2B2C90C69AB44366401093
|