| File name: | mna10.exe |
| Full analysis: | https://app.any.run/tasks/be76999e-8ad4-49be-b07d-596ea9a0871e |
| Verdict: | Malicious activity |
| Threats: | Remote access trojans (RATs) are a type of malware that enables attackers to establish complete to partial control over infected computers. Such malicious programs often have a modular design, offering a wide range of functionalities for conducting illicit activities on compromised systems. Some of the most common features of RATs include access to the users’ data, webcam, and keystrokes. This malware is often distributed through phishing emails and links. |
| Analysis date: | July 18, 2019, 14:53:19 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, RAR self-extracting archive |
| MD5: | 48B9B0332812C13EFA9182DE830A1212 |
| SHA1: | AC814127F349AACA7D8A7C4B710BADC5D5747CA7 |
| SHA256: | 24947EEDFE537A616EABA709BF61BC2A7BE8D21270348E91EBE2807915E394A4 |
| SSDEEP: | 49152:+wZgtEQCNSJwKbtrfnyKIIfDcEDm0B4J/kQvwMEFQTFDoLR7NvMAsSo/pPrMmlyS:+ZEzPKbFaRqe0B2inQ5QR7NUAsSeVmX4 |
MALICIOUS
Application was dropped or rewritten from another process
- task-service.exe (PID: 2696)
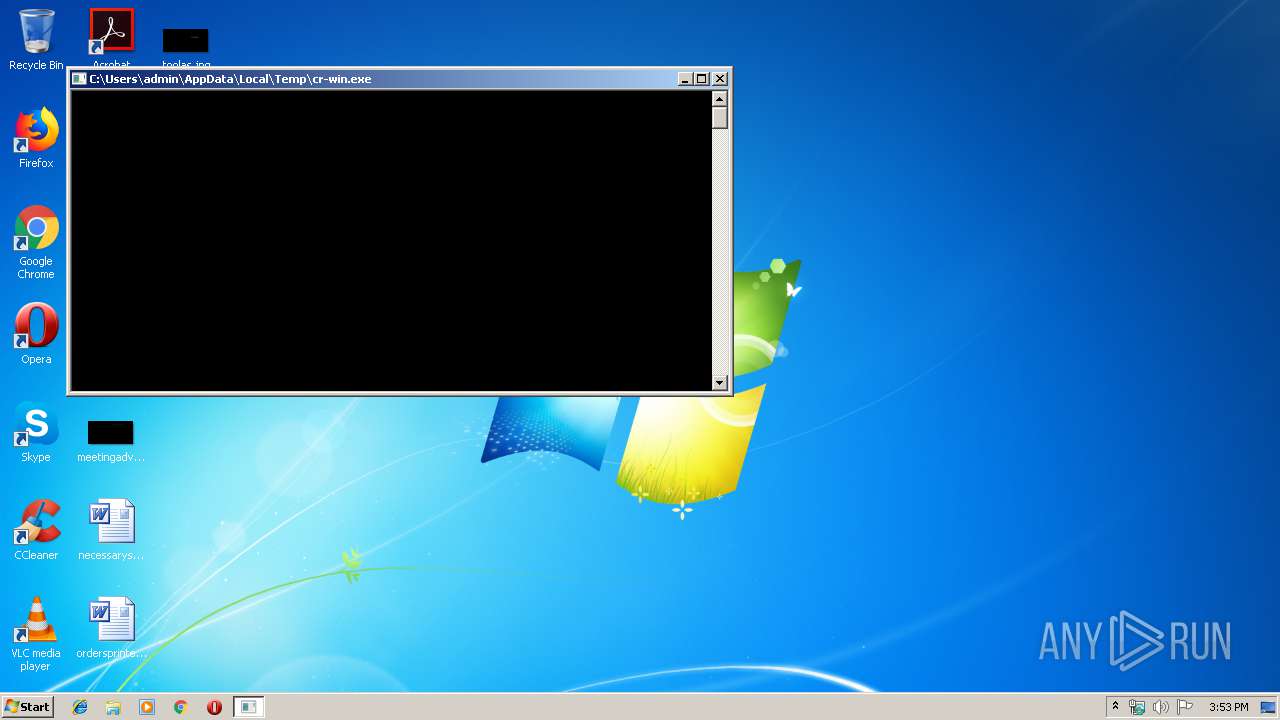
- cr-win.exe (PID: 3152)
- cr-win.exe (PID: 3792)
- winserv.exe (PID: 3928)
Loads dropped or rewritten executable
- cmd.exe (PID: 2436)
Changes the autorun value in the registry
- reg.exe (PID: 3484)
RMS was detected
- winserv.exe (PID: 3928)
SUSPICIOUS
Executable content was dropped or overwritten
- cmd.exe (PID: 2436)
- mna10.exe (PID: 3708)
- task-service.exe (PID: 2696)
Starts CMD.EXE for commands execution
- cr-win.exe (PID: 3152)
- cr-win.exe (PID: 3792)
Creates files in the program directory
- task-service.exe (PID: 2696)
Uses REG.EXE to modify Windows registry
- cmd.exe (PID: 2116)
Reads Environment values
- winserv.exe (PID: 3928)
Reads Windows Product ID
- winserv.exe (PID: 3928)
Reads the machine GUID from the registry
- winserv.exe (PID: 3928)
Creates files in the user directory
- winserv.exe (PID: 3928)
Uses TASKKILL.EXE to kill process
- cmd.exe (PID: 2116)
INFO
No info indicators.
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable MS Visual C++ (generic) (42.2) |
|---|---|---|
| .exe | | | Win64 Executable (generic) (37.3) |
| .dll | | | Win32 Dynamic Link Library (generic) (8.8) |
| .exe | | | Win32 Executable (generic) (6) |
| .exe | | | Generic Win/DOS Executable (2.7) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2012:01:09 14:44:06+01:00 |
| PEType: | PE32 |
| LinkerVersion: | 9 |
| CodeSize: | 72704 |
| InitializedDataSize: | 108032 |
| UninitializedDataSize: | - |
| EntryPoint: | 0xb3c1 |
| OSVersion: | 5 |
| ImageVersion: | - |
| SubsystemVersion: | 5 |
| Subsystem: | Windows GUI |
Summary
| Architecture: | IMAGE_FILE_MACHINE_I386 |
|---|---|
| Subsystem: | IMAGE_SUBSYSTEM_WINDOWS_GUI |
| Compilation Date: | 09-Jan-2012 13:44:06 |
| Detected languages: |
|
| Debug artifacts: |
|
DOS Header
| Magic number: | MZ |
|---|---|
| Bytes on last page of file: | 0x0090 |
| Pages in file: | 0x0003 |
| Relocations: | 0x0000 |
| Size of header: | 0x0004 |
| Min extra paragraphs: | 0x0000 |
| Max extra paragraphs: | 0xFFFF |
| Initial SS value: | 0x0000 |
| Initial SP value: | 0x00B8 |
| Checksum: | 0x0000 |
| Initial IP value: | 0x0000 |
| Initial CS value: | 0x0000 |
| Overlay number: | 0x0000 |
| OEM identifier: | 0x0000 |
| OEM information: | 0x0000 |
| Address of NE header: | 0x000000E0 |
PE Headers
| Signature: | PE |
|---|---|
| Machine: | IMAGE_FILE_MACHINE_I386 |
| Number of sections: | 5 |
| Time date stamp: | 09-Jan-2012 13:44:06 |
| Pointer to Symbol Table: | 0x00000000 |
| Number of symbols: | 0 |
| Size of Optional Header: | 0x00E0 |
| Characteristics: |
|
Sections
Name | Virtual Address | Virtual Size | Raw Size | Charateristics | Entropy |
|---|---|---|---|---|---|
.text | 0x00001000 | 0x00011A70 | 0x00011C00 | IMAGE_SCN_CNT_CODE, IMAGE_SCN_MEM_EXECUTE, IMAGE_SCN_MEM_READ | 6.55432 |
.rdata | 0x00013000 | 0x00001C05 | 0x00001E00 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 4.8666 |
.data | 0x00015000 | 0x000156FC | 0x00000200 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 3.57792 |
.CRT | 0x0002B000 | 0x00000010 | 0x00000200 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 0.213101 |
.rsrc | 0x0002C000 | 0x00002D74 | 0x00002E00 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 4.44708 |
Resources
Title | Entropy | Size | Codepage | Language | Type |
|---|---|---|---|---|---|
1 | 5.20816 | 1464 | UNKNOWN | English - United States | RT_MANIFEST |
7 | 3.24143 | 556 | UNKNOWN | English - United States | RT_STRING |
8 | 3.26996 | 974 | UNKNOWN | English - United States | RT_STRING |
9 | 3.04375 | 530 | UNKNOWN | English - United States | RT_STRING |
10 | 3.16254 | 776 | UNKNOWN | English - United States | RT_STRING |
11 | 3.06352 | 380 | UNKNOWN | English - United States | RT_STRING |
12 | 2.33959 | 102 | UNKNOWN | English - United States | RT_STRING |
101 | 4.19099 | 2998 | UNKNOWN | English - United States | RT_BITMAP |
ASKNEXTVOL | 3.42597 | 646 | UNKNOWN | English - United States | RT_DIALOG |
GETPASSWORD1 | 3.33944 | 314 | UNKNOWN | English - United States | RT_DIALOG |
Imports
ADVAPI32.dll |
COMCTL32.dll |
COMDLG32.dll |
GDI32.dll |
KERNEL32.dll |
OLEAUT32.dll |
SHELL32.dll |
SHLWAPI.dll |
USER32.dll |
ole32.dll |
Total processes
615
Monitored processes
579
Malicious processes
7
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 316 | taskkill /f /im "rundll32.exe" | C:\Windows\system32\taskkill.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Terminates Processes Exit code: 128 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 324 | taskkill /f /im "rundll32.exe" | C:\Windows\system32\taskkill.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Terminates Processes Exit code: 128 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 328 | taskkill /f /im "rundll32.exe" | C:\Windows\system32\taskkill.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Terminates Processes Exit code: 128 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 328 | taskkill /f /im "rundll32.exe" | C:\Windows\system32\taskkill.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Terminates Processes Exit code: 128 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 356 | taskkill /f /im "rundll32.exe" | C:\Windows\system32\taskkill.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Terminates Processes Exit code: 128 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 356 | taskkill /f /im "rundll32.exe" | C:\Windows\system32\taskkill.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Terminates Processes Exit code: 128 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 412 | taskkill /f /im "rundll32.exe" | C:\Windows\system32\taskkill.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Terminates Processes Exit code: 128 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 476 | taskkill /f /im "rundll32.exe" | C:\Windows\system32\taskkill.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Terminates Processes Exit code: 128 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 476 | taskkill /f /im "rundll32.exe" | C:\Windows\system32\taskkill.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Terminates Processes Exit code: 128 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 576 | taskkill /f /im "rundll32.exe" | C:\Windows\system32\taskkill.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Terminates Processes Exit code: 128 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
2 420
Read events
2 397
Write events
23
Delete events
0
Modification events
| (PID) Process: | (3708) mna10.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
| (PID) Process: | (3708) mna10.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 1 | |||
| (PID) Process: | (2696) task-service.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
| (PID) Process: | (2696) task-service.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 1 | |||
| (PID) Process: | (3484) reg.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run |
| Operation: | write | Name: | Windows Tasks Service |
Value: C:\ProgramData\Windows Tasks Service\winserv.exe | |||
| (PID) Process: | (3928) winserv.exe | Key: | HKEY_CURRENT_USER\Software\tektonit\Remote MANIPULATOR System\Host\Parameters |
| Operation: | write | Name: | Options |
Value: 545046301154524F4D5365727665724F7074696F6E7300095573654E5441757468080D53656375726974794C6576656C020304506F727403121614456E61626C654F7665726C617943617074757265080C53686F775472617949636F6E0915486964655472617949636F6E506F7075704D656E75080642696E644950060D416E7920696E746572666163651343616C6C6261636B4175746F436F6E6E656374081743616C6C6261636B436F6E6E656374496E74657276616C023C084869646553746F70080C497046696C746572547970650202105573654C656761637943617074757265081750726F7465637443616C6C6261636B53657474696E6773081550726F74656374496E6574496453657474696E6773080F446F4E6F7443617074757265524450080755736549507636091141736B557365725065726D697373696F6E0816557365725065726D697373696F6E496E74657276616C031027134175746F416C6C6F775065726D697373696F6E08134E656564417574686F72697479536572766572081F41736B5065726D697373696F6E4F6E6C794966557365724C6F676765644F6E0811557365496E6574436F6E6E656374696F6E0813557365437573746F6D496E6574536572766572080A496E65744964506F727402000D557365496E6574496449507636081444697361626C6552656D6F7465436F6E74726F6C081344697361626C6552656D6F746553637265656E081344697361626C6546696C655472616E73666572080F44697361626C655265646972656374080D44697361626C6554656C6E6574081444697361626C6552656D6F746545786563757465081244697361626C655461736B4D616E61676572080E44697361626C654F7665726C6179080F44697361626C6553687574646F776E081444697361626C6552656D6F746555706772616465081544697361626C655072657669657743617074757265081444697361626C654465766963654D616E61676572080B44697361626C6543686174081344697361626C6553637265656E5265636F7264081044697361626C65415643617074757265081244697361626C6553656E644D657373616765080F44697361626C655265676973747279080D44697361626C65415643686174081544697361626C6552656D6F746553657474696E6773081544697361626C6552656D6F74655072696E74696E67080A44697361626C65526470080F4E6F7469667953686F7750616E656C08144E6F746966794368616E67655472617949636F6E08104E6F7469667942616C6C6F6E48696E74080F4E6F74696679506C6179536F756E64080C4E6F7469667950616E656C5802FF0C4E6F7469667950616E656C5902FF064C6F67557365080E50726F787953657474696E6773320C880100003737752F5044393462577767646D567963326C76626A30694D5334774969426C626D4E765A476C755A7A3069565652474C546769507A344E436A7877636D39346556397A5A5852306157356E637942325A584A7A61573975505349324E7A41774D69492B5048567A5A563977636D39346554356D5957787A5A54777664584E6C5833427962336835506A7877636D3934655639306558426C506A41384C33427962336835583352356347552B504768766333512B5043396F62334E30506A787762334A30506A67774F4441384C334276636E512B5047356C5A575266595856306144356D5957787A5A547776626D566C5A4639686458526F506A787564473173583246316447672B5A6D4673633255384C32353062577866595856306144343864584E6C636D35686257552B5043393163325679626D46745A5434386347467A63336476636D512B5043397759584E7A643239795A4434385A47397459576C75506A77765A47397459576C75506A777663484A7665486C666332563064476C755A334D2B44516F3D0A4164646974696F6E616C0604353535351144697361626C65496E7465726E65744964080B536166654D6F6465536574080F53796E6341757468456E61626C6564081253686F7749644E6F74696669636174696F6E081953686F7749644E6F74696669636174696F6E52657175657374081A496E746567726174654669726577616C6C417453747572747570080000 | |||
| (PID) Process: | (3928) winserv.exe | Key: | HKEY_CURRENT_USER\Software\tektonit\Remote MANIPULATOR System\Host\Parameters |
| Operation: | write | Name: | Password |
Value: 38003900440043004100460043003500460042003900450044004200380041003800370030003400350033003600390033003300350037003700340030003800440031003700410036003500390036003400390033003800460033004100340035003400380036003200370030003100310037004600420036003300390041003700350043004300310039004400360046003400380030003000460030003700320037003900370036004200370030004300420041003800340037003700390034003900300034003600450033003400360034003600350030004300430045004100410045003800390046004100430030003500390037004600390032003400 | |||
| (PID) Process: | (3928) winserv.exe | Key: | HKEY_CURRENT_USER\Software\tektonit\Remote MANIPULATOR System\Host\Parameters |
| Operation: | write | Name: | notification |
Value: EFBBBF3C3F786D6C2076657273696F6E3D22312E302220656E636F64696E673D225554462D38223F3E0D0A3C726D735F696E65745F69645F6E6F74696669636174696F6E2076657273696F6E3D223637303032223E3C73657474696E67735F6170706C6965643E66616C73653C2F73657474696E67735F6170706C6965643E3C7573655F69645F73657474696E67733E747275653C2F7573655F69645F73657474696E67733E3C67656E65726174655F6E65775F69643E747275653C2F67656E65726174655F6E65775F69643E3C73656E645F746F5F656D61696C3E66616C73653C2F73656E645F746F5F656D61696C3E3C656D61696C3E3C2F656D61696C3E3C69643E7B43424432383033442D424143462D343839422D383438462D4436454130453331343038467D3C2F69643E3C67656E65726174655F6E65775F70617373776F72643E66616C73653C2F67656E65726174655F6E65775F70617373776F72643E3C61736B5F6964656E74696669636174696F6E3E66616C73653C2F61736B5F6964656E74696669636174696F6E3E3C73656E743E66616C73653C2F73656E743E3C76657273696F6E3E303C2F76657273696F6E3E3C7075626C69635F6B65795F6D3E3C2F7075626C69635F6B65795F6D3E3C7075626C69635F6B65795F653E3C2F7075626C69635F6B65795F653E3C70617373776F72643E3C2F70617373776F72643E3C696E7465726E65745F69643E3C2F696E7465726E65745F69643E3C646973636C61696D65723E3C2F646973636C61696D65723E3C6164646974696F6E616C5F746578743E3C2F6164646974696F6E616C5F746578743E3C6F76657277726974655F69645F636F64653E66616C73653C2F6F76657277726974655F69645F636F64653E3C6F76657277726974655F69645F73657474696E67733E66616C73653C2F6F76657277726974655F69645F73657474696E67733E3C69645F637573746F6D5F7365727665725F7573653E747275653C2F69645F637573746F6D5F7365727665725F7573653E3C69645F637573746F6D5F7365727665725F616464726573733E3136302E32302E3134372E35323C2F69645F637573746F6D5F7365727665725F616464726573733E3C69645F637573746F6D5F7365727665725F706F72743E353635353C2F69645F637573746F6D5F7365727665725F706F72743E3C69645F637573746F6D5F7365727665725F697076363E66616C73653C2F69645F637573746F6D5F7365727665725F697076363E3C636F6D70757465725F6E616D653E3C2F636F6D70757465725F6E616D653E3C73656C665F6964656E74696669636174696F6E3E3C2F73656C665F6964656E74696669636174696F6E3E3C2F726D735F696E65745F69645F6E6F74696669636174696F6E3E0D | |||
| (PID) Process: | (3928) winserv.exe | Key: | HKEY_CURRENT_USER\Software\tektonit\Remote MANIPULATOR System\Host\Parameters |
| Operation: | write | Name: | 믯㲿砿汭瘠牥楳湯∽⸱∰攠据摯湩㵧唢䙔㠭㼢ാ㰊浲彳湩瑥楟彤潮楴楦慣楴湯瘠牥楳湯∽㜶〰∲㰾敳瑴湩獧慟灰楬摥显污敳⼼敳瑴湩獧慟灰楬摥㰾獵彥摩獟瑥楴杮㹳牴敵⼼獵彥摩獟瑥楴杮㹳朼湥牥瑡彥敮彷摩琾畲㱥术湥牥瑡彥敮彷摩㰾敳摮瑟彯浥楡㹬慦獬㱥猯湥彤潴敟慭汩㰾浥楡㹬⼼浥楡㹬椼㹤䍻䑂㠲㌰ⵄ䅂䙃㐭㤸ⵂ㐸䘸䐭䔶ぁ㍅㐱㠰絆⼼摩㰾敧敮慲整湟睥灟獡睳牯㹤慦獬㱥术湥牥瑡彥敮彷慰獳潷摲㰾獡彫摩湥楴楦慣楴湯显污敳⼼獡彫摩湥楴楦慣楴湯㰾敳瑮显污敳⼼敳瑮㰾敶獲潩㹮㰰瘯牥楳湯㰾異汢捩歟祥浟㰾瀯扵楬彣敫役㹭瀼扵楬彣敫役㹥⼼異汢捩歟祥敟㰾慰獳潷摲㰾瀯獡睳牯㹤椼瑮牥敮彴摩㰾椯瑮牥敮彴摩㰾楤捳慬浩牥㰾搯獩汣楡敭㹲愼摤瑩潩慮彬整瑸㰾愯摤瑩潩慮彬整瑸㰾癯牥牷瑩彥摩损摯㹥慦獬㱥漯敶睲楲整楟彤潣敤㰾癯牥牷瑩彥摩獟瑥楴杮㹳慦獬㱥漯敶睲楲整楟彤敳瑴湩獧㰾摩损獵潴彭敳癲牥畟敳琾畲㱥椯彤畣瑳浯獟牥敶彲獵㹥椼彤畣瑳浯獟牥敶彲摡牤獥㹳㘱 |
Value: EFBBBF3C3F786D6C2076657273696F6E3D22312E302220656E636F64696E673D225554462D38223F3E0D0A3C726D735F696E65745F69645F6E6F74696669636174696F6E2076657273696F6E3D223637303032223E3C73657474696E67735F6170706C6965643E66616C73653C2F73657474696E67735F6170706C6965643E3C7573655F69645F73657474696E67733E747275653C2F7573655F69645F73657474696E67733E3C67656E65726174655F6E65775F69643E747275653C2F67656E65726174655F6E65775F69643E3C73656E645F746F5F656D61696C3E66616C73653C2F73656E645F746F5F656D61696C3E3C656D61696C3E3C2F656D61696C3E3C69643E7B43424432383033442D424143462D343839422D383438462D4436454130453331343038467D3C2F69643E3C67656E65726174655F6E65775F70617373776F72643E66616C73653C2F67656E65726174655F6E65775F70617373776F72643E3C61736B5F6964656E74696669636174696F6E3E66616C73653C2F61736B5F6964656E74696669636174696F6E3E3C73656E743E66616C73653C2F73656E743E3C76657273696F6E3E303C2F76657273696F6E3E3C7075626C69635F6B65795F6D3E3C2F7075626C69635F6B65795F6D3E3C7075626C69635F6B65795F653E3C2F7075626C69635F6B65795F653E3C70617373776F72643E3C2F70617373776F72643E3C696E7465726E65745F69643E3C2F696E7465726E65745F69643E3C646973636C61696D65723E3C2F646973636C61696D65723E3C6164646974696F6E616C5F746578743E3C2F6164646974696F6E616C5F746578743E3C6F76657277726974655F69645F636F64653E66616C73653C2F6F76657277726974655F69645F636F64653E3C6F76657277726974655F69645F73657474696E67733E66616C73653C2F6F76657277726974655F69645F73657474696E67733E3C69645F637573746F6D5F7365727665725F7573653E747275653C2F69645F637573746F6D5F7365727665725F7573653E3C69645F637573746F6D5F7365727665725F616464726573733E3136 | |||
| (PID) Process: | (3928) winserv.exe | Key: | HKEY_CURRENT_USER\Software\tektonit\Remote MANIPULATOR System\Host\Parameters |
| Operation: | write | Name: | FUSClientPath |
Value: C:\ProgramData\Windows Tasks Service\rfusclient.exe | |||
Executable files
5
Suspicious files
1
Text files
4
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3708 | mna10.exe | C:\Users\admin\AppData\Local\Temp\winme.dll | executable | |
MD5:— | SHA256:— | |||
| 2696 | task-service.exe | C:\ProgramData\Windows Tasks Service\settings.dat | binary | |
MD5:— | SHA256:— | |||
| 3928 | winserv.exe | C:\Users\admin\AppData\Roaming\RMS_settings\Logs\rms_log_2019-07.html | html | |
MD5:— | SHA256:— | |||
| 3708 | mna10.exe | C:\Users\admin\AppData\Local\Temp\cr-win.exe | executable | |
MD5:8F7BF24692621CD1C267DDE87EA3B619 | SHA256:BCFA2A972392656EF20C9B2AC946E10BE0C4A5A60AB9A37CCD9B63A40F5D4C11 | |||
| 2696 | task-service.exe | C:\ProgramData\Windows Tasks Service\cr-win.exe | executable | |
MD5:8F7BF24692621CD1C267DDE87EA3B619 | SHA256:BCFA2A972392656EF20C9B2AC946E10BE0C4A5A60AB9A37CCD9B63A40F5D4C11 | |||
| 3708 | mna10.exe | C:\Users\admin\AppData\Local\Temp\install.cmd | text | |
MD5:— | SHA256:— | |||
| 2436 | cmd.exe | C:\Users\admin\AppData\Local\Temp\task-service.exe | executable | |
MD5:— | SHA256:— | |||
| 2696 | task-service.exe | C:\ProgramData\Windows Tasks Service\install.cmd | text | |
MD5:— | SHA256:— | |||
| 2696 | task-service.exe | C:\ProgramData\Windows Tasks Service\winserv.exe | executable | |
MD5:3F4F5A6CB95047FEA6102BD7D2226AA9 | SHA256:99FD9E75E6241EFF30E01C5B59DF9E901FB24D12BEE89C069CC6158F78B3CC98 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
1
DNS requests
1
Threats
1
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3928 | winserv.exe | 160.20.147.52:5655 | — | — | — | suspicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.cloudflare.com |
| whitelisted |
Threats
1 ETPRO signatures available at the full report
Process | Message |
|---|---|
winserv.exe | Error WTSQueryUserToken #1314 |
winserv.exe | 18-07-2019_15:53:44:613#T:Error #20 @2 |
winserv.exe | 18-07-2019_15:54:12:441#T:Msg Size: 104 |
winserv.exe | 18-07-2019_15:54:12:441#T:Msg code: 3 |
winserv.exe | 18-07-2019_15:54:12:441#T:MSG_KEEP_ALIVE |
winserv.exe | MSG_KEEP_ALIVE |
winserv.exe | 18-07-2019_15:54:41:300#T:Msg Size: 104 |
winserv.exe | 18-07-2019_15:54:41:300#T:Msg code: 3 |
winserv.exe | 18-07-2019_15:54:41:300#T:MSG_KEEP_ALIVE |
winserv.exe | MSG_KEEP_ALIVE |