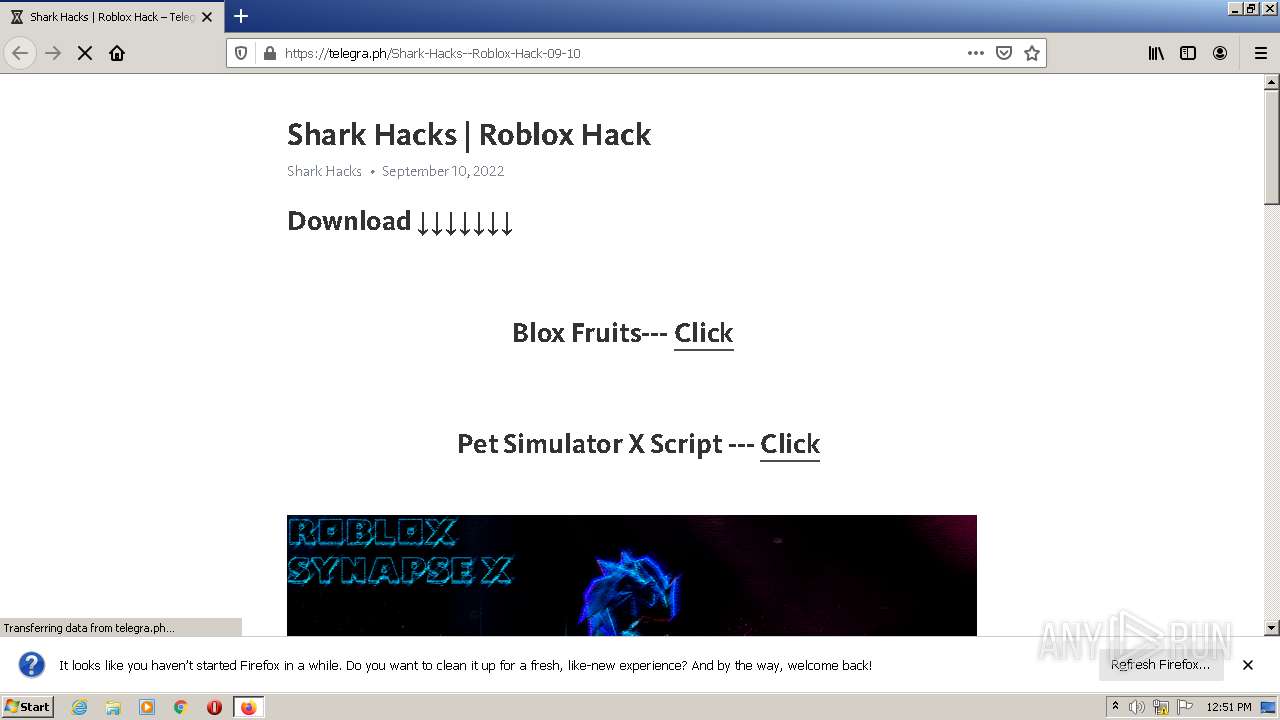
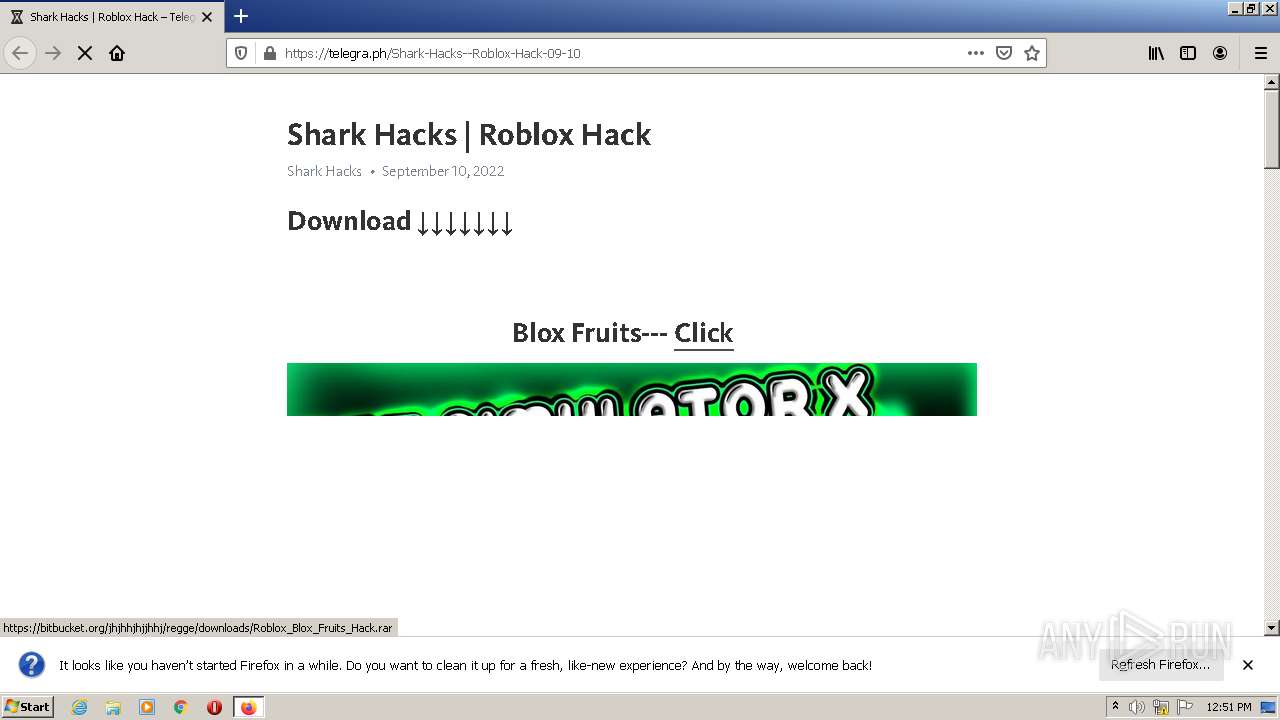
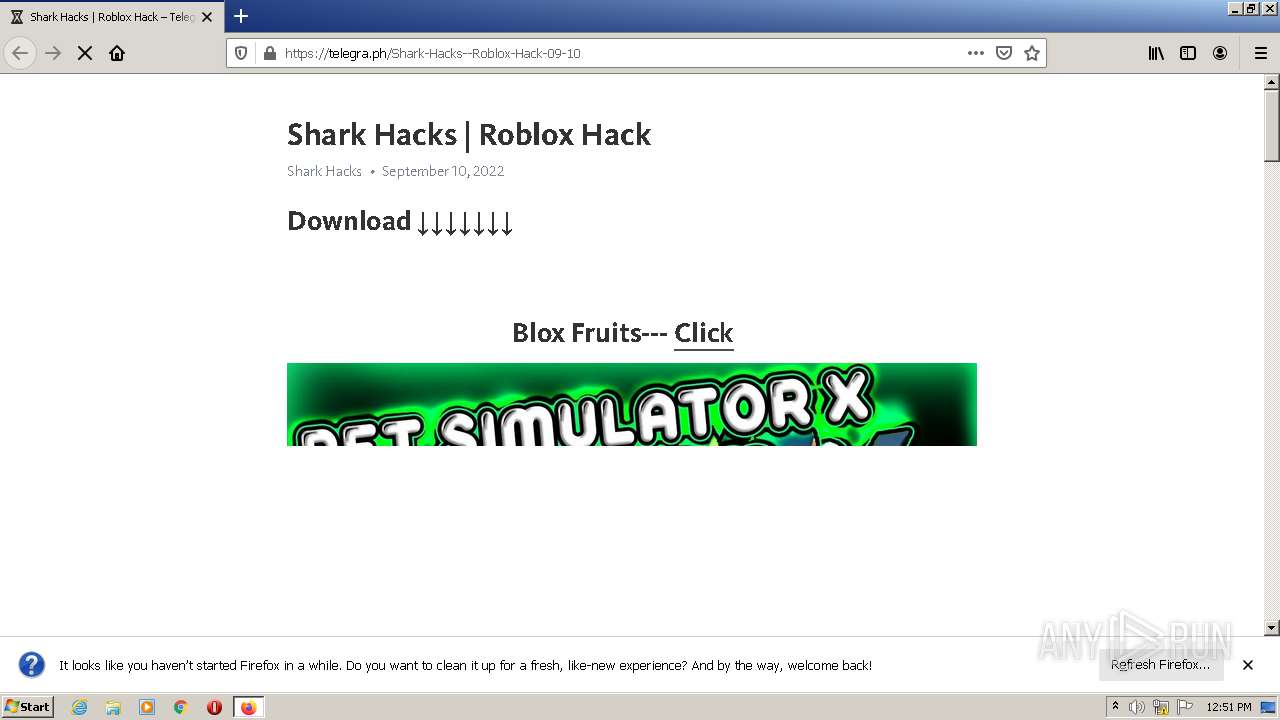
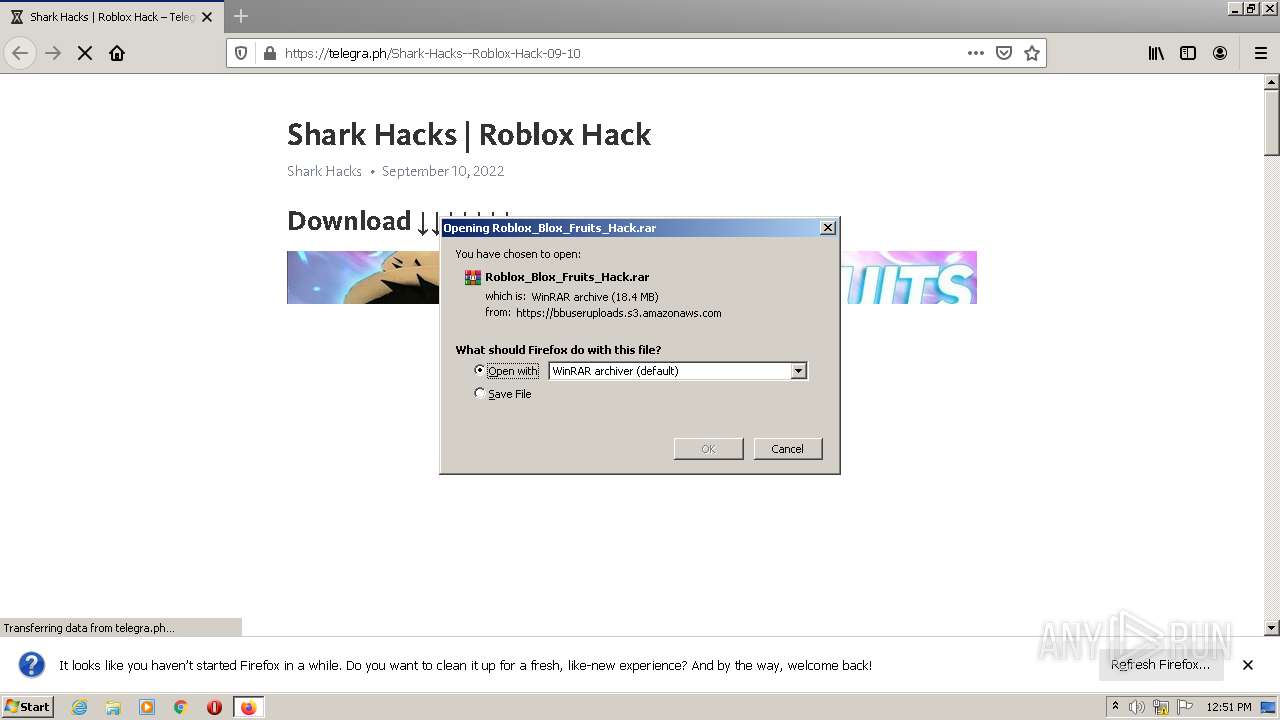
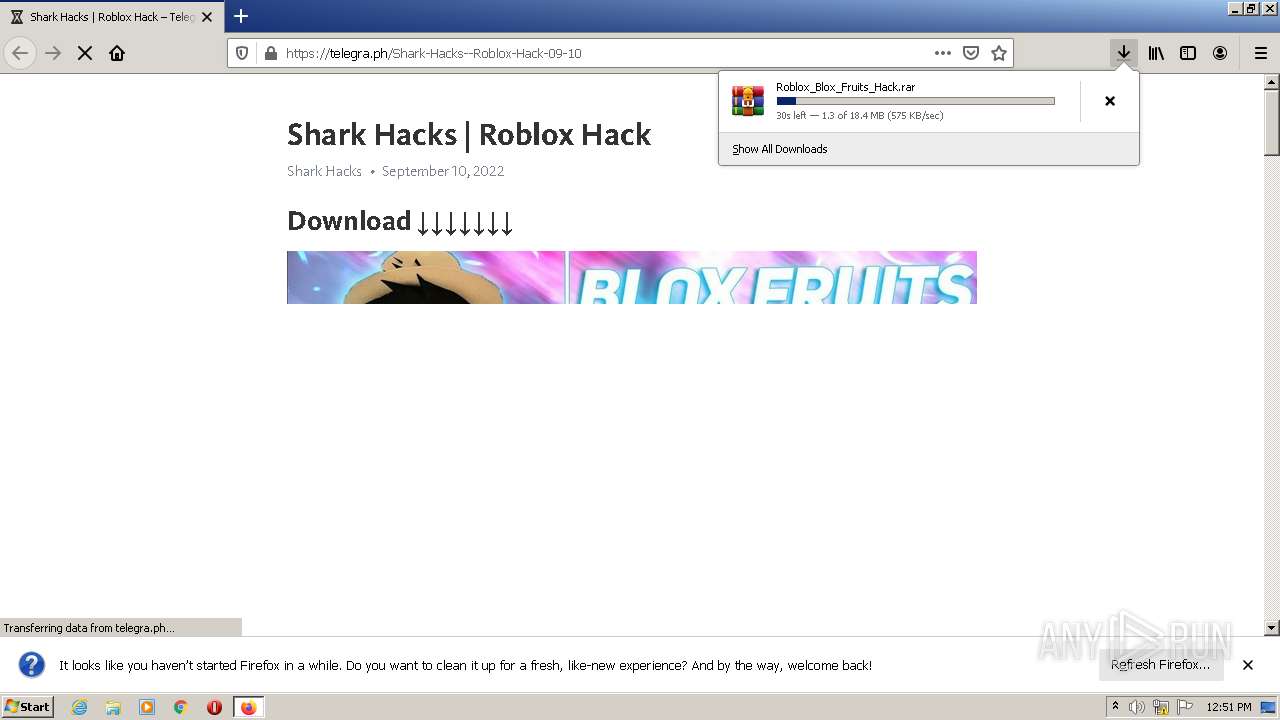
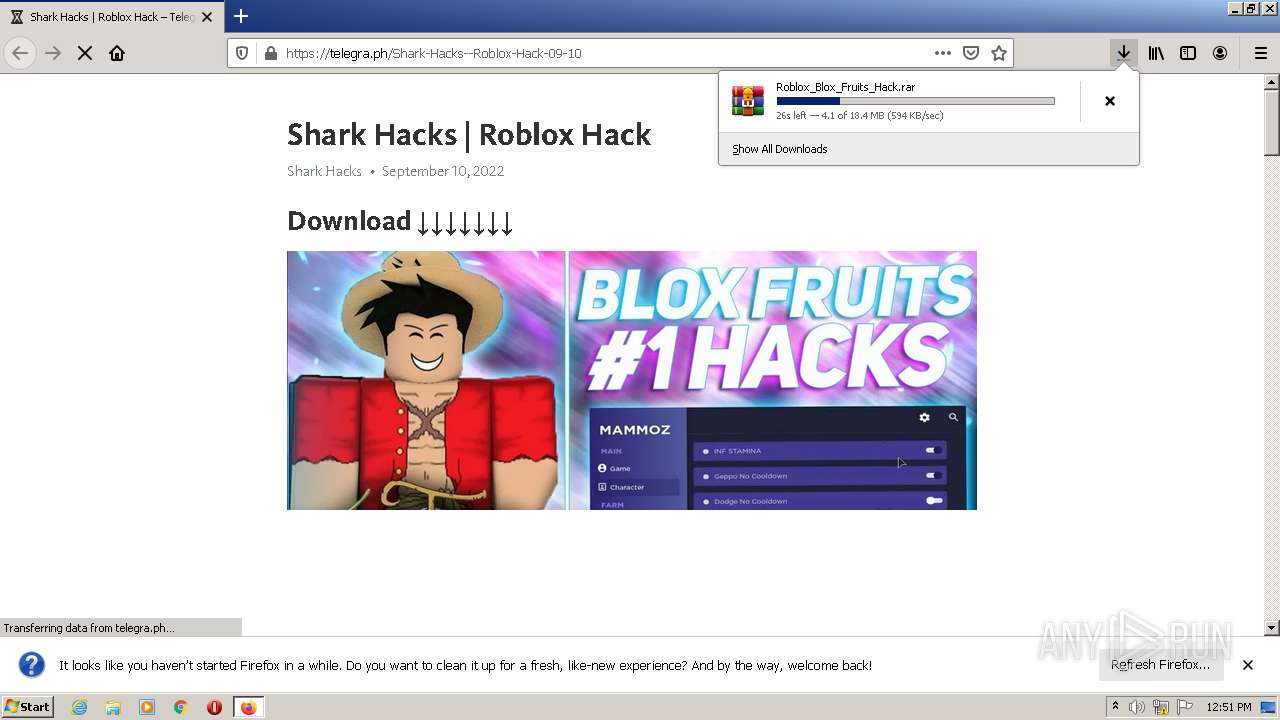
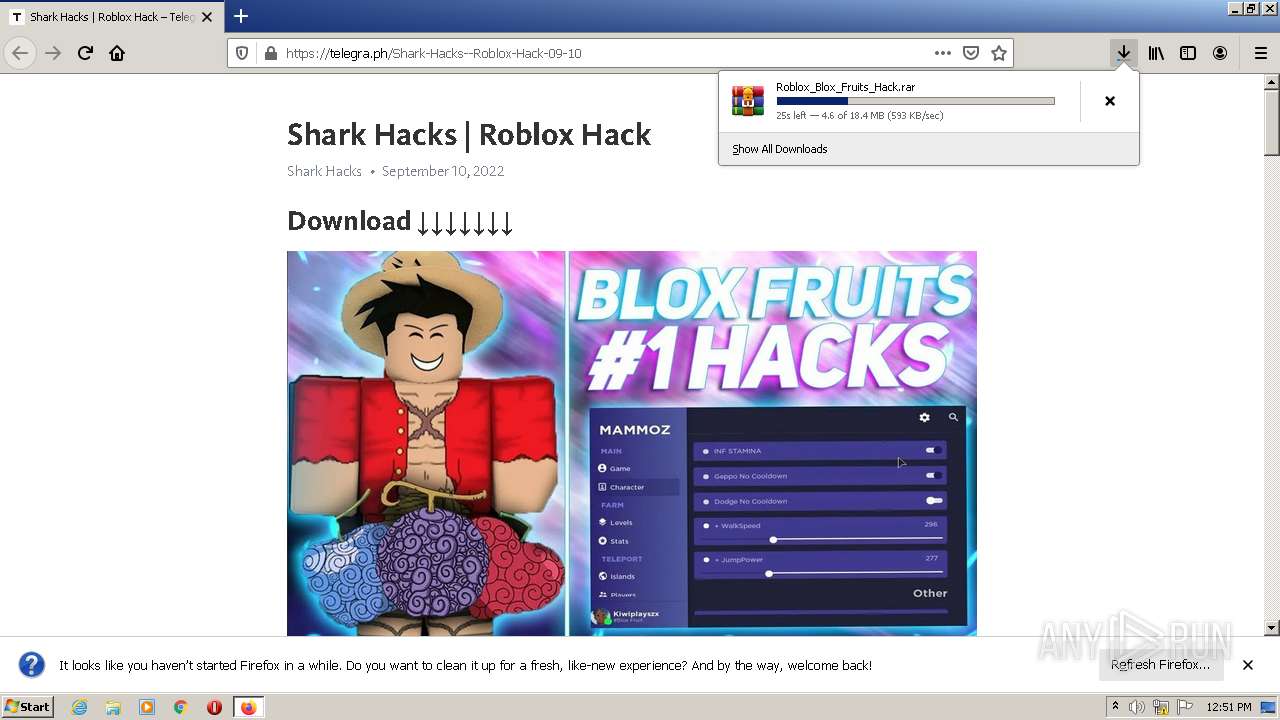
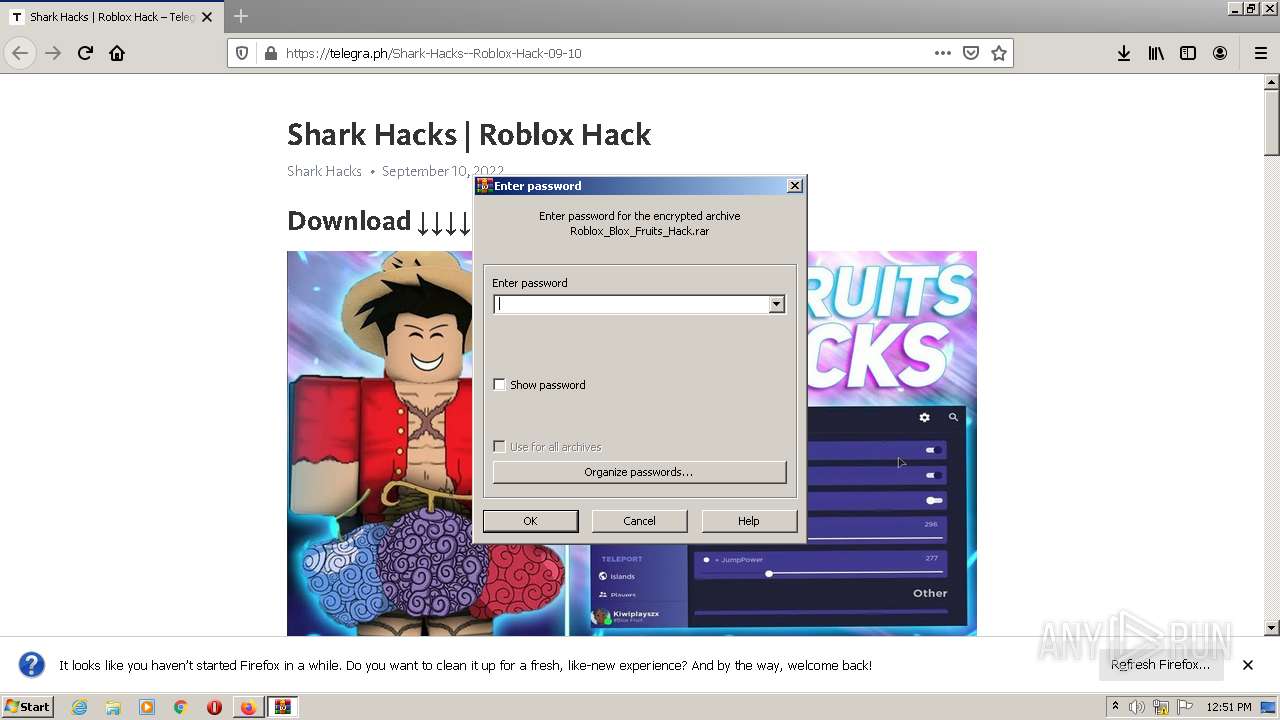
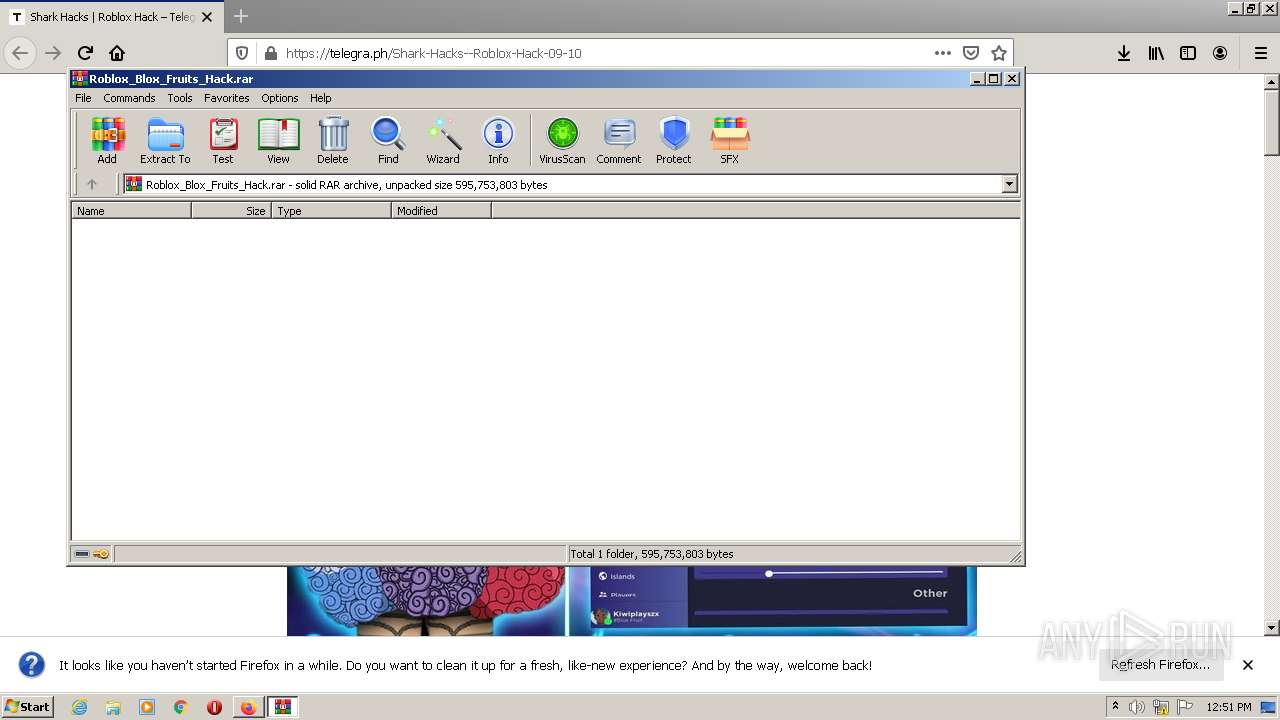
| URL: | https://telegra.ph/Shark-Hacks--Roblox-Hack-09-10 |
| Full analysis: | https://app.any.run/tasks/5cd79dc1-ba20-4214-a869-9577647e2d78 |
| Verdict: | Malicious activity |
| Threats: | Remote access trojans (RATs) are a type of malware that enables attackers to establish complete to partial control over infected computers. Such malicious programs often have a modular design, offering a wide range of functionalities for conducting illicit activities on compromised systems. Some of the most common features of RATs include access to the users’ data, webcam, and keystrokes. This malware is often distributed through phishing emails and links. |
| Analysis date: | April 01, 2023, 11:51:07 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MD5: | 1C41D9A9B1BFAE9A0306CBAB2692C39F |
| SHA1: | D424F2C3304B4353008CE8AF6C29685B1763F777 |
| SHA256: | 2434858D770166B2A9E324398DD6C4698297F06DA24566ECBC8E423FA1C66485 |
| SSDEEP: | 3:N8IrmoIfFEGOIU:2IqVf+D |
MALICIOUS
REDLINE was detected
- AddInProcess32.exe (PID: 3392)
Connects to the CnC server
- AddInProcess32.exe (PID: 3392)
Steals credentials from Web Browsers
- AddInProcess32.exe (PID: 3392)
Actions looks like stealing of personal data
- AddInProcess32.exe (PID: 3392)
SUSPICIOUS
Process communicates with Telegram (possibly using it as an attacker's C2 server)
- firefox.exe (PID: 948)
Connects to unusual port
- AddInProcess32.exe (PID: 3392)
Searches for installed software
- AddInProcess32.exe (PID: 3392)
Reads browser cookies
- AddInProcess32.exe (PID: 3392)
INFO
Application launched itself
- firefox.exe (PID: 2368)
- firefox.exe (PID: 948)
The process uses the downloaded file
- WinRAR.exe (PID: 3344)
- firefox.exe (PID: 948)
Reads the computer name
- Rоblох Вlох Fruits Hасk.exe (PID: 2696)
- AddInProcess32.exe (PID: 3392)
Reads product name
- AddInProcess32.exe (PID: 3392)
The process checks LSA protection
- AddInProcess32.exe (PID: 3392)
Reads the machine GUID from the registry
- AddInProcess32.exe (PID: 3392)
Reads Environment values
- AddInProcess32.exe (PID: 3392)
Create files in a temporary directory
- firefox.exe (PID: 948)
Manual execution by a user
- WinRAR.exe (PID: 3344)
Checks supported languages
- Rоblох Вlох Fruits Hасk.exe (PID: 2696)
- AddInProcess32.exe (PID: 3392)
Executable content was dropped or overwritten
- firefox.exe (PID: 948)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
48
Monitored processes
12
Malicious processes
3
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 948 | "C:\Program Files\Mozilla Firefox\firefox.exe" https://telegra.ph/Shark-Hacks--Roblox-Hack-09-10 | C:\Program Files\Mozilla Firefox\firefox.exe | firefox.exe | ||||||||||||
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Exit code: 0 Version: 83.0 Modules
| |||||||||||||||
| 1592 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel="948.27.594013106\1616928926" -childID 4 -isForBrowser -prefsHandle 3868 -prefMapHandle 3864 -prefsLen 7799 -prefMapSize 238726 -parentBuildID 20201112153044 -appdir "C:\Program Files\Mozilla Firefox\browser" - 948 "\\.\pipe\gecko-crash-server-pipe.948" 3880 tab | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: LOW Description: Firefox Exit code: 0 Version: 83.0 Modules
| |||||||||||||||
| 2340 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel="948.20.1986813359\1964570254" -childID 3 -isForBrowser -prefsHandle 3696 -prefMapHandle 3692 -prefsLen 7470 -prefMapSize 238726 -parentBuildID 20201112153044 -appdir "C:\Program Files\Mozilla Firefox\browser" - 948 "\\.\pipe\gecko-crash-server-pipe.948" 3708 tab | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: LOW Description: Firefox Exit code: 0 Version: 83.0 Modules
| |||||||||||||||
| 2368 | "C:\Program Files\Mozilla Firefox\firefox.exe" "https://telegra.ph/Shark-Hacks--Roblox-Hack-09-10" | C:\Program Files\Mozilla Firefox\firefox.exe | — | explorer.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Exit code: 0 Version: 83.0 Modules
| |||||||||||||||
| 2404 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel="948.35.457944307\82822158" -childID 6 -isForBrowser -prefsHandle 4276 -prefMapHandle 4272 -prefsLen 7973 -prefMapSize 238726 -parentBuildID 20201112153044 -appdir "C:\Program Files\Mozilla Firefox\browser" - 948 "\\.\pipe\gecko-crash-server-pipe.948" 4256 tab | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: LOW Description: Firefox Exit code: 0 Version: 83.0 Modules
| |||||||||||||||
| 2696 | "C:\Users\admin\AppData\Local\Temp\Rar$EXb3344.38851\Rоblох Вlох Fruits Hасk\Rоblох Вlох Fruits Hасk.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXb3344.38851\Rоblох Вlох Fruits Hасk\Rоblох Вlох Fruits Hасk.exe | — | WinRAR.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: explorer Exit code: 0 Version: 6.2.19041.1081 Modules
| |||||||||||||||
| 2952 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel="948.34.996073768\859993331" -childID 5 -isForBrowser -prefsHandle 4260 -prefMapHandle 4236 -prefsLen 7973 -prefMapSize 238726 -parentBuildID 20201112153044 -appdir "C:\Program Files\Mozilla Firefox\browser" - 948 "\\.\pipe\gecko-crash-server-pipe.948" 4288 tab | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: LOW Description: Firefox Exit code: 0 Version: 83.0 Modules
| |||||||||||||||
| 3048 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel="948.6.1178416727\2013227272" -childID 1 -isForBrowser -prefsHandle 3116 -prefMapHandle 3112 -prefsLen 181 -prefMapSize 238726 -parentBuildID 20201112153044 -appdir "C:\Program Files\Mozilla Firefox\browser" - 948 "\\.\pipe\gecko-crash-server-pipe.948" 3128 tab | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: LOW Description: Firefox Exit code: 0 Version: 83.0 Modules
| |||||||||||||||
| 3344 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\Rоblох_Вlох_Fruits_Hасk.rar" | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 3392 | "C:\Windows\Microsoft.NET\Framework\v4.0.30319\AddInProcess32.exe" | C:\Windows\Microsoft.NET\Framework\v4.0.30319\AddInProcess32.exe | Rоblох Вlох Fruits Hасk.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: AddInProcess.exe Exit code: 0 Version: 4.0.30319.34209 built by: FX452RTMGDR Modules
| |||||||||||||||
Total events
26 482
Read events
26 386
Write events
96
Delete events
0
Modification events
| (PID) Process: | (2368) firefox.exe | Key: | HKEY_CURRENT_USER\Software\Mozilla\Firefox\Launcher |
| Operation: | write | Name: | C:\Program Files\Mozilla Firefox\firefox.exe|Launcher |
Value: 09611C1E1E000000 | |||
| (PID) Process: | (948) firefox.exe | Key: | HKEY_CURRENT_USER\Software\Mozilla\Firefox\Launcher |
| Operation: | write | Name: | C:\Program Files\Mozilla Firefox\firefox.exe|Browser |
Value: AD681C1E1E000000 | |||
| (PID) Process: | (948) firefox.exe | Key: | HKEY_CURRENT_USER\Software\Mozilla\Firefox\Launcher |
| Operation: | write | Name: | C:\Program Files\Mozilla Firefox\firefox.exe|Telemetry |
Value: 0 | |||
| (PID) Process: | (948) firefox.exe | Key: | HKEY_CURRENT_USER\Software\Mozilla\Firefox\DllPrefetchExperiment |
| Operation: | write | Name: | C:\Program Files\Mozilla Firefox\firefox.exe |
Value: 0 | |||
| (PID) Process: | (948) firefox.exe | Key: | HKEY_CURRENT_USER\Software\Mozilla\Firefox\Default Browser Agent |
| Operation: | write | Name: | C:\Program Files\Mozilla Firefox|DisableTelemetry |
Value: 1 | |||
| (PID) Process: | (948) firefox.exe | Key: | HKEY_CURRENT_USER\Software\Mozilla\Firefox\Default Browser Agent |
| Operation: | write | Name: | C:\Program Files\Mozilla Firefox|DisableDefaultBrowserAgent |
Value: 0 | |||
| (PID) Process: | (948) firefox.exe | Key: | HKEY_CURRENT_USER\Software\Mozilla\Firefox\Default Browser Agent |
| Operation: | write | Name: | C:\Program Files\Mozilla Firefox|ServicesSettingsServer |
Value: https://firefox.settings.services.mozilla.com/v1 | |||
| (PID) Process: | (948) firefox.exe | Key: | HKEY_CURRENT_USER\Software\Mozilla\Firefox\Default Browser Agent |
| Operation: | write | Name: | C:\Program Files\Mozilla Firefox|SecurityContentSignatureRootHash |
Value: 97:E8:BA:9C:F1:2F:B3:DE:53:CC:42:A4:E6:57:7E:D6:4D:F4:93:C2:47:B4:14:FE:A0:36:81:8D:38:23:56:0E | |||
| (PID) Process: | (948) firefox.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | write | Name: | ProxyEnable |
Value: 0 | |||
| (PID) Process: | (948) firefox.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Connections |
| Operation: | write | Name: | SavedLegacySettings |
Value: 460000003D010000090000000000000000000000000000000400000000000000C0E333BBEAB1D3010000000000000000000000000100000002000000C0A80164000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
Executable files
8
Suspicious files
220
Text files
132
Unknown types
48
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 948 | firefox.exe | C:\Users\admin\AppData\Local\Mozilla\Firefox\Profiles\qldyz51w.default\startupCache\scriptCache-current.bin | — | |
MD5:— | SHA256:— | |||
| 948 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\qldyz51w.default\storage\permanent\chrome\idb\3870112724rsegmnoittet-es.sqlite | — | |
MD5:— | SHA256:— | |||
| 948 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\qldyz51w.default\places.sqlite-wal | sqlite-wal | |
MD5:— | SHA256:— | |||
| 948 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\qldyz51w.default\storage\permanent\chrome\idb\3870112724rsegmnoittet-es.sqlite-wal | binary | |
MD5:— | SHA256:— | |||
| 948 | firefox.exe | C:\Users\admin\AppData\Local\Mozilla\Firefox\Profiles\qldyz51w.default\startupCache\urlCache-current.bin | binary | |
MD5:994A33896BB41A278A315D0D796422B6 | SHA256:54EC50A20FFF8CC016710E49437CF6A11D3FE5EE7B28C185E4A9AAFEE2908B63 | |||
| 948 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\qldyz51w.default\cookies.sqlite-shm | binary | |
MD5:B7C14EC6110FA820CA6B65F5AEC85911 | SHA256:FD4C9FDA9CD3F9AE7C962B0DDF37232294D55580E1AA165AA06129B8549389EB | |||
| 948 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\qldyz51w.default\search.json.mozlz4.tmp | jsonlz4 | |
MD5:B17F8D93B0C43D6B72DC03752C20A2D9 | SHA256:ADA0F70D374223FB63C2F19471FAB45D986A681E2485692E63F00F5071F19D76 | |||
| 948 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\qldyz51w.default\storage\permanent\chrome\idb\2918063365piupsah.sqlite-shm | binary | |
MD5:B7C14EC6110FA820CA6B65F5AEC85911 | SHA256:FD4C9FDA9CD3F9AE7C962B0DDF37232294D55580E1AA165AA06129B8549389EB | |||
| 948 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\qldyz51w.default\prefs.js | text | |
MD5:299A2B747C11E4BDA194E563FEA4A699 | SHA256:94EE461F62E8B4A0A65471A41E10C8C56722B73C0A019D76ACA7F5BAF109813E | |||
| 948 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\qldyz51w.default\storage\permanent\chrome\idb\2823318777ntouromlalnodry--naod.sqlite-shm | binary | |
MD5:B7C14EC6110FA820CA6B65F5AEC85911 | SHA256:FD4C9FDA9CD3F9AE7C962B0DDF37232294D55580E1AA165AA06129B8549389EB | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
19
TCP/UDP connections
34
DNS requests
101
Threats
2
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
948 | firefox.exe | POST | 200 | 142.250.185.163:80 | http://ocsp.pki.goog/gts1c3 | US | der | 471 b | whitelisted |
948 | firefox.exe | POST | 200 | 184.24.77.46:80 | http://r3.o.lencr.org/ | US | der | 503 b | shared |
948 | firefox.exe | POST | 200 | 184.24.77.45:80 | http://r3.o.lencr.org/ | US | der | 503 b | shared |
948 | firefox.exe | POST | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/ | US | der | 471 b | whitelisted |
948 | firefox.exe | POST | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/ | US | der | 471 b | whitelisted |
948 | firefox.exe | GET | 200 | 34.107.221.82:80 | http://detectportal.firefox.com/success.txt?ipv4 | US | text | 8 b | whitelisted |
948 | firefox.exe | GET | 200 | 34.107.221.82:80 | http://detectportal.firefox.com/success.txt?ipv4 | US | text | 8 b | whitelisted |
948 | firefox.exe | POST | 200 | 18.66.121.98:80 | http://ocsp.sca1b.amazontrust.com/ | US | der | 471 b | whitelisted |
948 | firefox.exe | GET | 200 | 34.107.221.82:80 | http://detectportal.firefox.com/success.txt | US | text | 8 b | whitelisted |
948 | firefox.exe | POST | — | 192.124.249.41:80 | http://ocsp.godaddy.com/ | US | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
948 | firefox.exe | 34.107.221.82:80 | detectportal.firefox.com | GOOGLE | US | whitelisted |
948 | firefox.exe | 184.24.77.45:80 | r3.o.lencr.org | Akamai International B.V. | DE | unknown |
948 | firefox.exe | 35.241.9.150:443 | firefox.settings.services.mozilla.com | GOOGLE | US | suspicious |
948 | firefox.exe | 149.154.164.13:443 | telegra.ph | Telegram Messenger Inc | GB | suspicious |
948 | firefox.exe | 192.124.249.41:80 | ocsp.godaddy.com | SUCURI-SEC | US | suspicious |
948 | firefox.exe | 52.38.245.94:443 | location.services.mozilla.com | AMAZON-02 | US | unknown |
948 | firefox.exe | 142.250.186.170:443 | safebrowsing.googleapis.com | GOOGLE | US | whitelisted |
948 | firefox.exe | 34.160.144.191:443 | content-signature-2.cdn.mozilla.net | GOOGLE | US | suspicious |
948 | firefox.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
948 | firefox.exe | 34.111.73.144:443 | firefox-settings-attachments.cdn.mozilla.net | GOOGLE | US | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
detectportal.firefox.com |
| whitelisted |
prod.detectportal.prod.cloudops.mozgcp.net |
| whitelisted |
telegra.ph |
| malicious |
firefox.settings.services.mozilla.com |
| whitelisted |
example.org |
| whitelisted |
ipv4only.arpa |
| whitelisted |
ocsp.godaddy.com |
| whitelisted |
r3.o.lencr.org |
| shared |
a1887.dscq.akamai.net |
| whitelisted |
ocsp.godaddy.com.akadns.net |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
948 | firefox.exe | Misc activity | ET INFO Observed Telegram Domain (t .me in TLS SNI) |
3392 | AddInProcess32.exe | A Network Trojan was detected | ET MALWARE RedLine Stealer TCP CnC net.tcp Init |