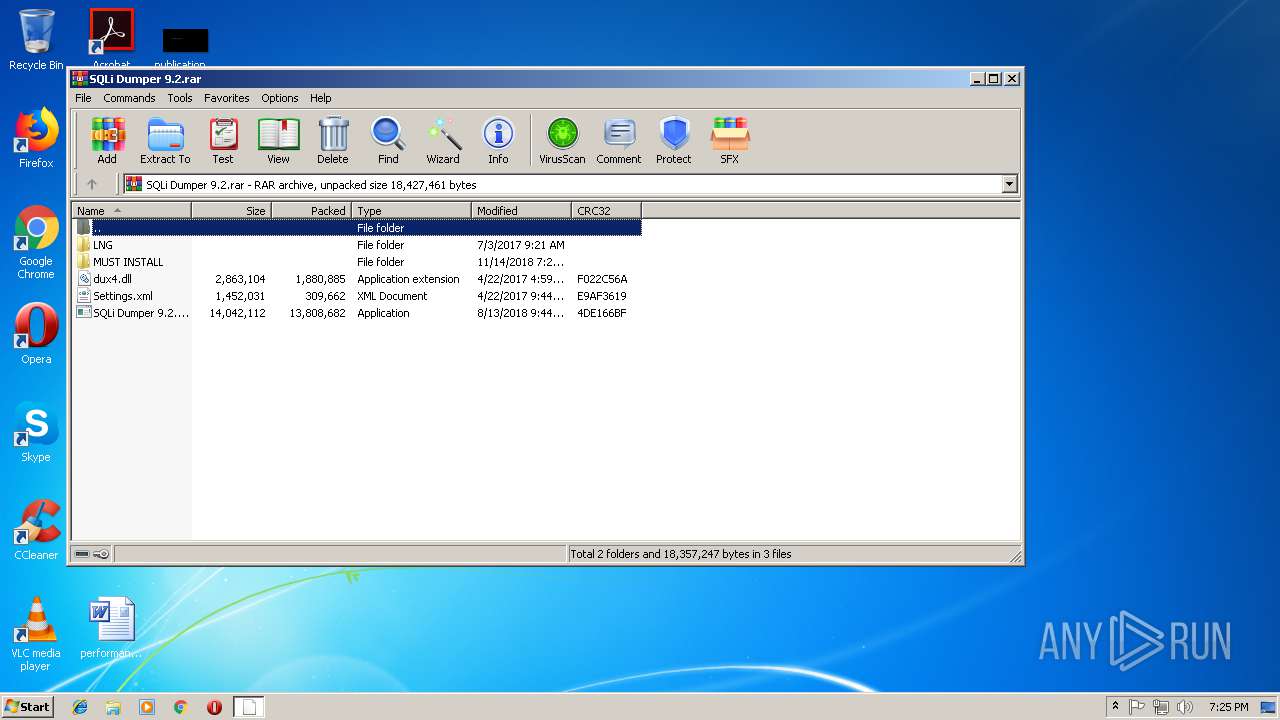
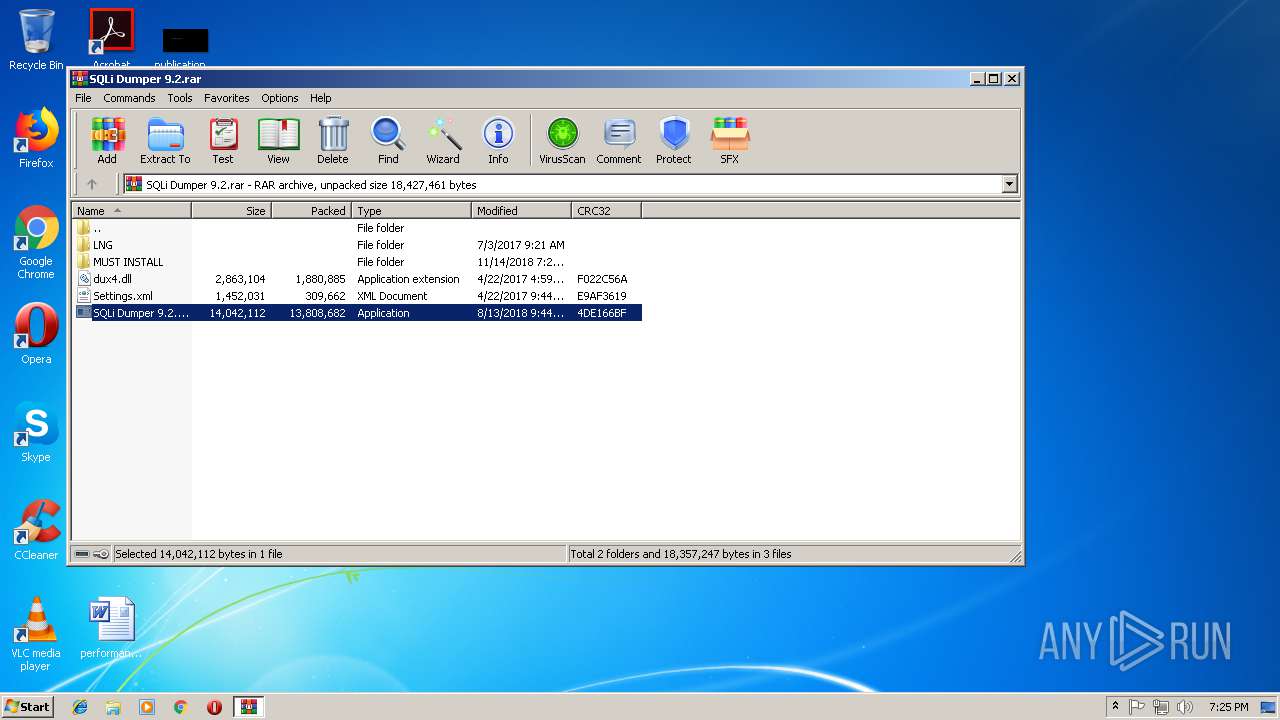
| File name: | SQLi Dumper 9.2.rar |
| Full analysis: | https://app.any.run/tasks/15de9f4d-5fc9-4cca-94b0-eecc89e9fe04 |
| Verdict: | Malicious activity |
| Threats: | Orcus is a modular Remote Access Trojan with some unusual functions. This RAT enables attackers to create plugins using a custom development library and offers a robust core feature set that makes it one of the most dangerous malicious programs in its class. |
| Analysis date: | November 14, 2018, 19:25:14 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-rar |
| File info: | RAR archive data, v5 |
| MD5: | A0157E775BFEB483C8D556BF8291F1D7 |
| SHA1: | 728CF33A07861E6B4FD0B5F089EF44FF7D4EC636 |
| SHA256: | 240894BB28D0D5C25A9219F3D427E76EAA41AA1CAC1F8F9214EE1117B2CFEA6B |
| SSDEEP: | 393216:tzl6hc0syAeBueaXJiQFeV0FPvI9A+cKrwG6:tz0zAeBue5H0dIuvh |
MALICIOUS
Application was dropped or rewritten from another process
- PBPJGFE4WUAQOFPWDCV8FBFPEF4FSWLN..EXE (PID: 2668)
- SQLi Dumper 9.2.1.exe (PID: 2124)
- SQLi Dumper 9.2.1..exe (PID: 3724)
- PBPJGFE4WUAQOFPWDCV8FBFPEF4FSWLN..EXE (PID: 3824)
- SQLi Dumper 9.2.1..exe (PID: 800)
- WindowsInput.exe (PID: 2900)
- SQLi Dumper 9.2.1...exe (PID: 1872)
- WindowsInput.exe (PID: 2920)
- c.exe (PID: 3248)
- v.exe (PID: 920)
- c.exe (PID: 3584)
- v.exe (PID: 3936)
QUASAR was detected
- SQLi Dumper 9.2.1...exe (PID: 1872)
Changes the autorun value in the registry
- v.exe (PID: 3936)
Orcus RAT was detected
- c.exe (PID: 3584)
Loads the Task Scheduler COM API
- v.exe (PID: 3936)
SUSPICIOUS
Executable content was dropped or overwritten
- WinRAR.exe (PID: 1184)
- SQLi Dumper 9.2.1.exe (PID: 2124)
- PBPJGFE4WUAQOFPWDCV8FBFPEF4FSWLN..EXE (PID: 3824)
- SQLi Dumper 9.2.1..exe (PID: 800)
- v.exe (PID: 3936)
Application launched itself
- SQLi Dumper 9.2.1..exe (PID: 3724)
- c.exe (PID: 3584)
Creates files in the user directory
- PBPJGFE4WUAQOFPWDCV8FBFPEF4FSWLN..EXE (PID: 3824)
- v.exe (PID: 3936)
Checks for external IP
- SQLi Dumper 9.2.1...exe (PID: 1872)
Creates files in the Windows directory
- SQLi Dumper 9.2.1..exe (PID: 800)
- WindowsInput.exe (PID: 2900)
Creates or modifies windows services
- WindowsInput.exe (PID: 2900)
Starts itself from another location
- SQLi Dumper 9.2.1..exe (PID: 800)
Creates files in the program directory
- SQLi Dumper 9.2.1..exe (PID: 800)
Connects to unusual port
- v.exe (PID: 3936)
INFO
No info indicators.
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .rar | | | RAR compressed archive (v5.0) (61.5) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (38.4) |
Total processes
48
Monitored processes
13
Malicious processes
9
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 800 | "C:\Users\admin\AppData\Roaming\SQLi Dumper 9.2.1..exe" /wait | C:\Users\admin\AppData\Roaming\SQLi Dumper 9.2.1..exe | SQLi Dumper 9.2.1..exe | ||||||||||||
User: admin Company: fLaSh Integrity Level: HIGH Description: SQLi Dumper Exit code: 0 Version: 9.2.1.0 Modules
| |||||||||||||||
| 920 | "C:\Program Files\v\v.exe" | C:\Program Files\v\v.exe | — | taskeng.exe | |||||||||||
User: admin Company: fLaSh Integrity Level: HIGH Description: SQLi Dumper Exit code: 0 Version: 9.2.1.0 Modules
| |||||||||||||||
| 1184 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\SQLi Dumper 9.2.rar" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
| 1872 | "C:\Users\admin\AppData\Roaming\SQLi Dumper 9.2.1...exe" | C:\Users\admin\AppData\Roaming\SQLi Dumper 9.2.1...exe | PBPJGFE4WUAQOFPWDCV8FBFPEF4FSWLN..EXE | ||||||||||||
User: admin Company: fLaSh Integrity Level: MEDIUM Description: SQLi Dumper Exit code: 0 Version: 9.2.1.0 Modules
| |||||||||||||||
| 2124 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa1184.5754\SQLi Dumper 9.2.1.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa1184.5754\SQLi Dumper 9.2.1.exe | WinRAR.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 2668 | "C:\Users\admin\AppData\Local\Temp\PBPJGFE4WUAQOFPWDCV8FBFPEF4FSWLN..EXE" | C:\Users\admin\AppData\Local\Temp\PBPJGFE4WUAQOFPWDCV8FBFPEF4FSWLN..EXE | — | SQLi Dumper 9.2.1.exe | |||||||||||
User: admin Company: fLaSh Integrity Level: MEDIUM Description: SQLi Dumper.exe Exit code: 0 Version: 9.2.1.0 Modules
| |||||||||||||||
| 2900 | "C:\Windows\system32\WindowsInput.exe" --install | C:\Windows\system32\WindowsInput.exe | — | SQLi Dumper 9.2.1..exe | |||||||||||
User: admin Company: Microsoft Integrity Level: HIGH Description: Windows Input Exit code: 0 Version: 0.1.0 Modules
| |||||||||||||||
| 2920 | "C:\Windows\system32\WindowsInput.exe" | C:\Windows\system32\WindowsInput.exe | — | services.exe | |||||||||||
User: SYSTEM Company: Microsoft Integrity Level: SYSTEM Description: Windows Input Exit code: 0 Version: 0.1.0 Modules
| |||||||||||||||
| 3248 | "C:\Users\admin\AppData\Roaming\c.exe" /watchProcess "C:\Program Files\v\v.exe" 3936 "/protectFile" | C:\Users\admin\AppData\Roaming\c.exe | — | c.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
| 3584 | "C:\Users\admin\AppData\Roaming\c.exe" /launchSelfAndExit "C:\Program Files\v\v.exe" 3936 /protectFile | C:\Users\admin\AppData\Roaming\c.exe | v.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 3248 Version: 1.0.0.0 Modules
| |||||||||||||||
Total events
2 352
Read events
2 292
Write events
60
Delete events
0
Modification events
| (PID) Process: | (1184) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (1184) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (1184) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\5F\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (1184) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\SQLi Dumper 9.2.rar | |||
| (PID) Process: | (1184) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (1184) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (1184) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (1184) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (1184) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
| (PID) Process: | (1184) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 1 | |||
Executable files
9
Suspicious files
0
Text files
7
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3824 | PBPJGFE4WUAQOFPWDCV8FBFPEF4FSWLN..EXE | C:\Users\admin\AppData\Roaming\SQLi Dumper 9.2.1...exe | executable | |
MD5:— | SHA256:— | |||
| 2124 | SQLi Dumper 9.2.1.exe | C:\Users\admin\AppData\Local\Temp\3HEUHBOWRGVP57YIVYDOLVPF2C9A1EXC..EXE | executable | |
MD5:— | SHA256:— | |||
| 1184 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa1184.5754\LNG\English.xml | xml | |
MD5:1EAEB87C91A30DD4133B8D3814F58171 | SHA256:7964A940F21E700F1D03ECB08D3E29CC06EF84841E11437FF3FCDF178E57E37B | |||
| 800 | SQLi Dumper 9.2.1..exe | C:\Program Files\v\v.exe | executable | |
MD5:— | SHA256:— | |||
| 3936 | v.exe | C:\Users\admin\AppData\Roaming\c.exe | executable | |
MD5:913967B216326E36A08010FB70F9DBA3 | SHA256:8D880758549220154D2FF4EE578F2B49527C5FB76A07D55237B61E30BCC09E3A | |||
| 2900 | WindowsInput.exe | C:\Windows\system32\WindowsInput.InstallState | xml | |
MD5:FFB29BD88BD23C639985F1D369DBD1CA | SHA256:1ADB4F9D1D152E018246A0A2762B473D910906340207F57D3F8CE1097E1DE09F | |||
| 800 | SQLi Dumper 9.2.1..exe | C:\Windows\system32\WindowsInput.exe.config | xml | |
MD5:A2B76CEA3A59FA9AF5EA21FF68139C98 | SHA256:F99EF5BF79A7C43701877F0BB0B890591885BB0A3D605762647CC8FFBF10C839 | |||
| 800 | SQLi Dumper 9.2.1..exe | C:\Windows\system32\WindowsInput.exe | executable | |
MD5:E6FCF516D8ED8D0D4427F86E08D0D435 | SHA256:8DBE814359391ED6B0B5B182039008CF1D00964DA9FBC4747F46242A95C24337 | |||
| 1184 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa1184.5754\Settings.xml | xml | |
MD5:4252974148A730AFF4918DF85CAA5F47 | SHA256:F2D3D47C0779D55339EF034B1FDDBA468934F131CD176AB77A1FB115E43B935F | |||
| 800 | SQLi Dumper 9.2.1..exe | C:\Program Files\v\v.exe.config | xml | |
MD5:A2B76CEA3A59FA9AF5EA21FF68139C98 | SHA256:F99EF5BF79A7C43701877F0BB0B890591885BB0A3D605762647CC8FFBF10C839 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
1
TCP/UDP connections
2
DNS requests
2
Threats
3
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1872 | SQLi Dumper 9.2.1...exe | GET | 200 | 185.194.141.58:80 | http://ip-api.com/json/ | DE | text | 260 b | malicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3936 | v.exe | 182.237.185.73:1090 | port1.gleeze.com | Fivenetwork Solution India Pvt Ltd Internet | IN | unknown |
1872 | SQLi Dumper 9.2.1...exe | 185.194.141.58:80 | ip-api.com | netcup GmbH | DE | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
ip-api.com |
| malicious |
port1.gleeze.com |
| malicious |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1872 | SQLi Dumper 9.2.1...exe | Potential Corporate Privacy Violation | ET POLICY External IP Lookup ip-api.com |
1872 | SQLi Dumper 9.2.1...exe | A Network Trojan was detected | MALWARE [PTsecurity] Quasar 1.3 RAT IP Lookup ip-api.com (HTTP headeer) |
1 ETPRO signatures available at the full report