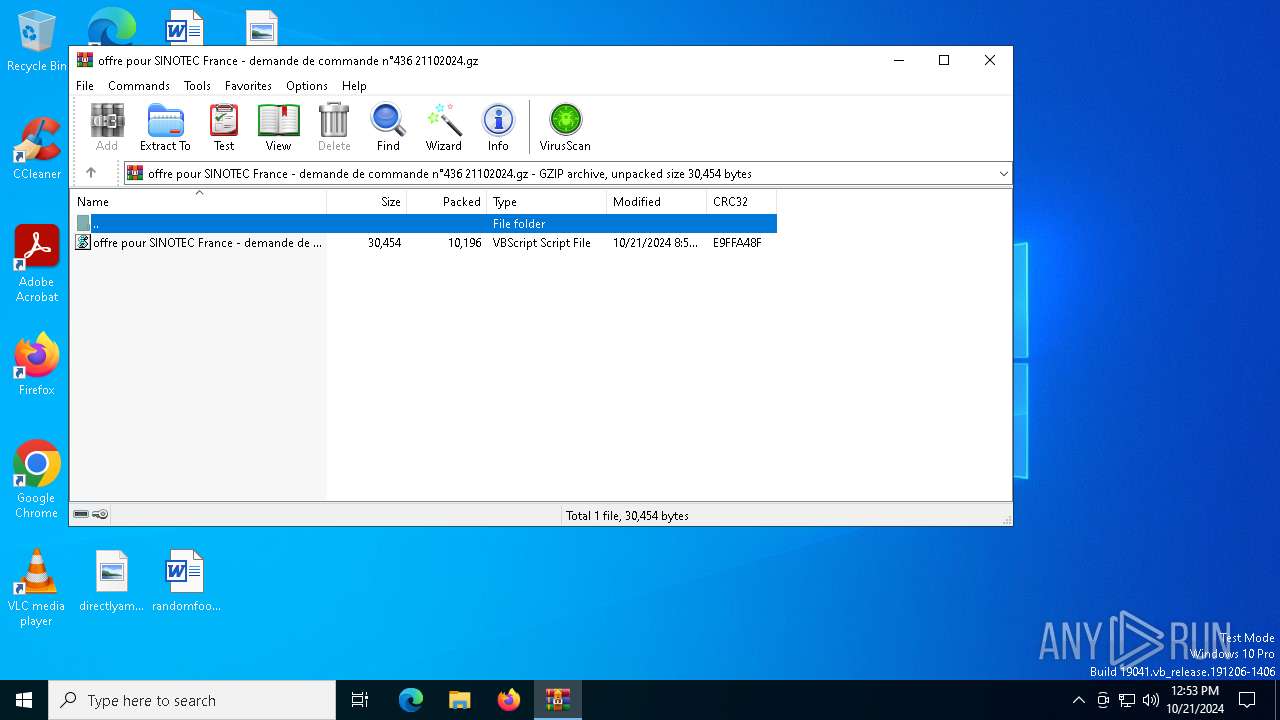
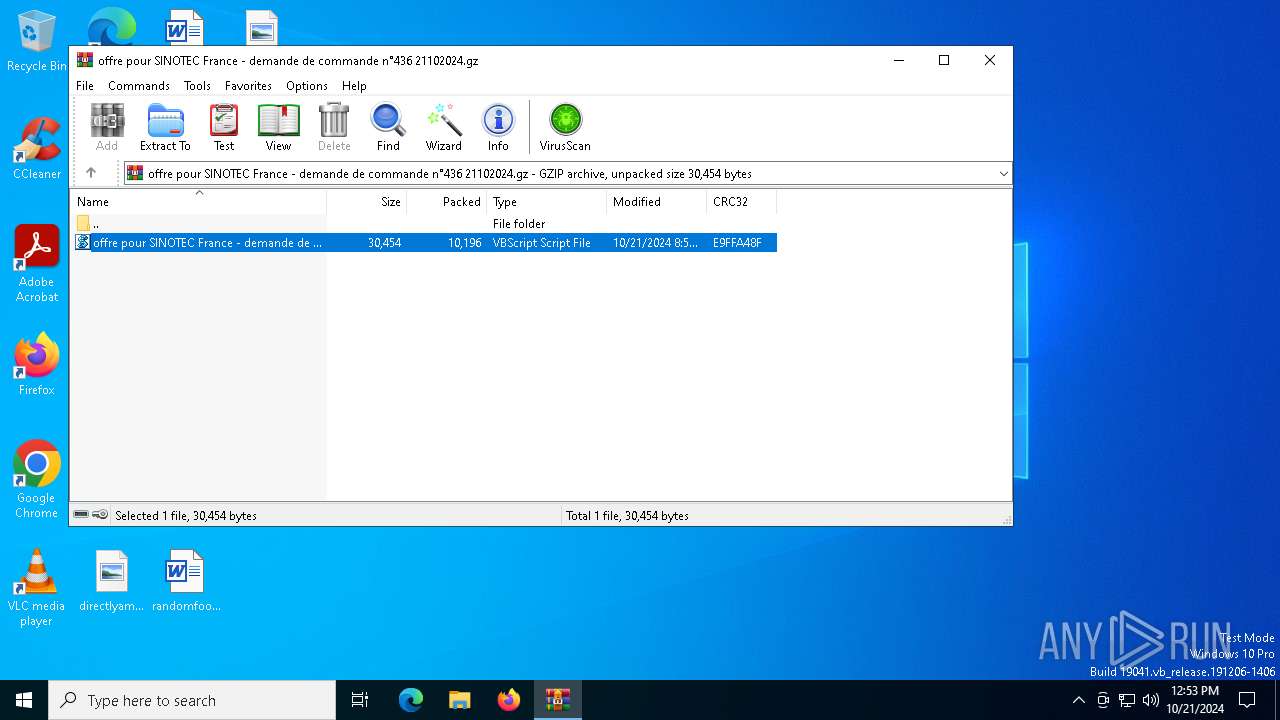
| File name: | offre pour SINOTEC France - demande de commande n°436 21102024.gz |
| Full analysis: | https://app.any.run/tasks/2be4c24b-1592-461f-927f-d622f2d2c36d |
| Verdict: | Malicious activity |
| Threats: | GuLoader is an advanced downloader written in shellcode. It’s used by criminals to distribute other malware, notably trojans, on a large scale. It’s infamous for using anti-detection and anti-analysis capabilities. |
| Analysis date: | October 21, 2024, 12:53:27 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/gzip |
| File info: | gzip compressed data, was "offre pour SINOTEC France - demande de commande n\260436 21102024.vbs", last modified: Mon Oct 21 08:57:16 2024, from FAT filesystem (MS-DOS, OS/2, NT), original size modulo 2^32 30454 |
| MD5: | 1B8F7D7B32DD1937D890621026C1F8DB |
| SHA1: | 05F2F86944C4E5936544EDF1A5A5EEAA506340A8 |
| SHA256: | 23F15807F53F8E4A9B327407CB83CBD8F47B1495D3480A166CDB201952F2BD23 |
| SSDEEP: | 192:JgGCY4IUmNknOogsoTLngcwBSfs++3Oz4KMwmbIC98lxqhy1t2aWCqtSrGgDq63l:JgvqEuLwBb3cybUqcD2vCe/g3/GP8 |
MALICIOUS
Generic archive extractor
- WinRAR.exe (PID: 2692)
GULOADER has been detected
- wscript.exe (PID: 616)
SUSPICIOUS
The process executes VB scripts
- WinRAR.exe (PID: 2692)
Executes application which crashes
- wscript.exe (PID: 616)
INFO
No info indicators.
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .z/gz/gzip | | | GZipped data (100) |
|---|
EXIF
ZIP
| Compression: | Deflated |
|---|---|
| Flags: | FileName |
| ModifyDate: | 2024:10:21 08:57:16+00:00 |
| ExtraFlags: | (none) |
| OperatingSystem: | FAT filesystem (MS-DOS, OS/2, NT/Win32) |
| ArchivedFileName: | offre pour SINOTEC France - demande de commande n?436 21102024.vbs |
Total processes
135
Monitored processes
5
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 616 | "C:\WINDOWS\System32\WScript.exe" "C:\Users\admin\AppData\Local\Temp\Rar$DIa2692.3343\offre pour SINOTEC France - demande de commande n°436 21102024.vbs" | C:\Windows\System32\wscript.exe | WinRAR.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft ® Windows Based Script Host Exit code: 3221225477 Version: 5.812.10240.16384 Modules
| |||||||||||||||
| 2692 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\offre pour SINOTEC France - demande de commande n°436 21102024.gz" | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.91.0 Modules
| |||||||||||||||
| 4448 | C:\WINDOWS\system32\WerFault.exe -u -p 616 -s 1496 | C:\Windows\System32\WerFault.exe | wscript.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Problem Reporting Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5976 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | PING.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6472 | ping gormezl_6777.6777.6777.677e | C:\Windows\System32\PING.EXE | — | wscript.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: TCP/IP Ping Command Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
8 756
Read events
8 749
Write events
7
Delete events
0
Modification events
| (PID) Process: | (2692) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\GoogleChromeEnterpriseBundle64.zip | |||
| (PID) Process: | (2692) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\offre pour SINOTEC France - demande de commande n°436 21102024.gz | |||
| (PID) Process: | (2692) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (2692) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (2692) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (2692) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (2692) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\FileExts\.vbs\OpenWithProgids |
| Operation: | write | Name: | VBSFile |
Value: | |||
Executable files
0
Suspicious files
3
Text files
3
Unknown types
3
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 4448 | WerFault.exe | C:\ProgramData\Microsoft\Windows\WER\ReportArchive\AppCrash_WScript.exe_5a352ea634ecd755e446f56f753aa6483fc84ee_debcac4a_bcf3d0b5-dd24-4b39-a69b-cae1fc83364c\Report.wer | — | |
MD5:— | SHA256:— | |||
| 4448 | WerFault.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\37C951188967C8EB88D99893D9D191FE | binary | |
MD5:4BD083851C443C1C0B8ABED000EBBB36 | SHA256:979BE359629F51DA88C3AA0FB9A6F1B282C6A256334FDD8DB12D95B263E175F2 | |||
| 4448 | WerFault.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\37C951188967C8EB88D99893D9D191FE | der | |
MD5:F0CF5B1794ECA7CD73F9C020DAAB8EF2 | SHA256:2AF00EDCE7EF3266897E52DC81E8DE3B7A079028C0F1F96EAFF9E38AD342F617 | |||
| 4448 | WerFault.exe | C:\ProgramData\Microsoft\Windows\WER\Temp\WERFF19.tmp.dmp | dmp | |
MD5:F25C02BD444DDDA63D32A67425CD6419 | SHA256:2C8161656F1F8FA09C9C1F2D246F442C7CC8120F4DAC353FFEC0E86A97122C68 | |||
| 4448 | WerFault.exe | C:\ProgramData\Microsoft\Windows\WER\Temp\WER12F.tmp.xml | xml | |
MD5:20F4C3105BFB948F05D4ACEF6C419C94 | SHA256:106E790BB266F8EDEF5F93800C03FAACB67579C73702C1E5E908E489F493C3D8 | |||
| 4448 | WerFault.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\21253908F3CB05D51B1C2DA8B681A785 | binary | |
MD5:E28C7C469FA00BF4521ECFDCA161409D | SHA256:5839A0016E02814F005DD8C0E00077D3E81CECA05B7F077C7B05ECBB4DC29D8B | |||
| 4448 | WerFault.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\21253908F3CB05D51B1C2DA8B681A785 | der | |
MD5:1B7FD5177461034E4086724C5845E927 | SHA256:065AF18C229898A1C2A8D989911ADCD9B1E2AB14B1953EBF8EAF34AE37EA1627 | |||
| 4448 | WerFault.exe | C:\Users\admin\AppData\Local\CrashDumps\wscript.exe.616.dmp | binary | |
MD5:C95C1B135954C922B1B8CD82B7E68B6B | SHA256:AF7B6A1B1ECCF18767814BA82D67F480AE3B23783C5E5B876E13C443EA2EE777 | |||
| 2692 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DIa2692.3343\offre pour SINOTEC France - demande de commande n°436 21102024.vbs | text | |
MD5:34BDEF2CCEE6D2E4C44BDDE97100EE72 | SHA256:B3CBE99653473F02E9059A76D009E0E0E88763C8CB2A8E4DDF21B189761BD6F5 | |||
| 4448 | WerFault.exe | C:\ProgramData\Microsoft\Windows\WER\Temp\WER82.tmp.WERInternalMetadata.xml | xml | |
MD5:553C8DC5F0FF9A3362E162FA58746A6D | SHA256:BE48F16BB15AFDF52AB38CA0F19387941634E4ECD447D8BF4FB487BFD7817769 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
11
TCP/UDP connections
54
DNS requests
20
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5488 | MoUsoCoreWorker.exe | GET | 200 | 23.53.40.178:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 23.53.40.178:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5488 | MoUsoCoreWorker.exe | GET | 200 | 23.218.209.163:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
5736 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
— | — | GET | 200 | 23.218.209.163:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
4448 | WerFault.exe | GET | 200 | 23.53.40.178:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
6584 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
4448 | WerFault.exe | GET | 200 | 69.192.161.161:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
4360 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
7224 | SIHClient.exe | GET | 200 | 69.192.161.161:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 104.126.37.128:443 | — | Akamai International B.V. | DE | unknown |
— | — | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
5488 | MoUsoCoreWorker.exe | 23.53.40.178:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
— | — | 23.53.40.178:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
5488 | MoUsoCoreWorker.exe | 23.218.209.163:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
— | — | 23.218.209.163:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
4020 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
5736 | svchost.exe | 20.190.160.14:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
gormezl_6777.6777.6777.677e |
| unknown |
watson.events.data.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |