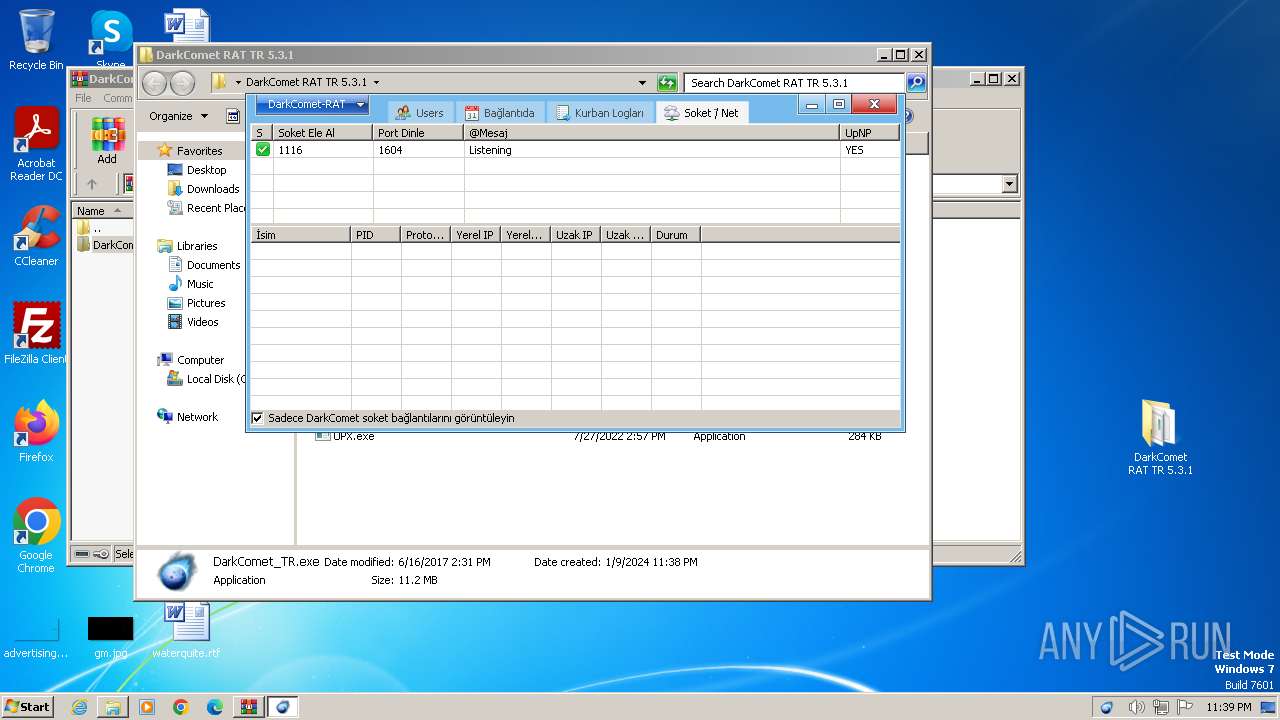
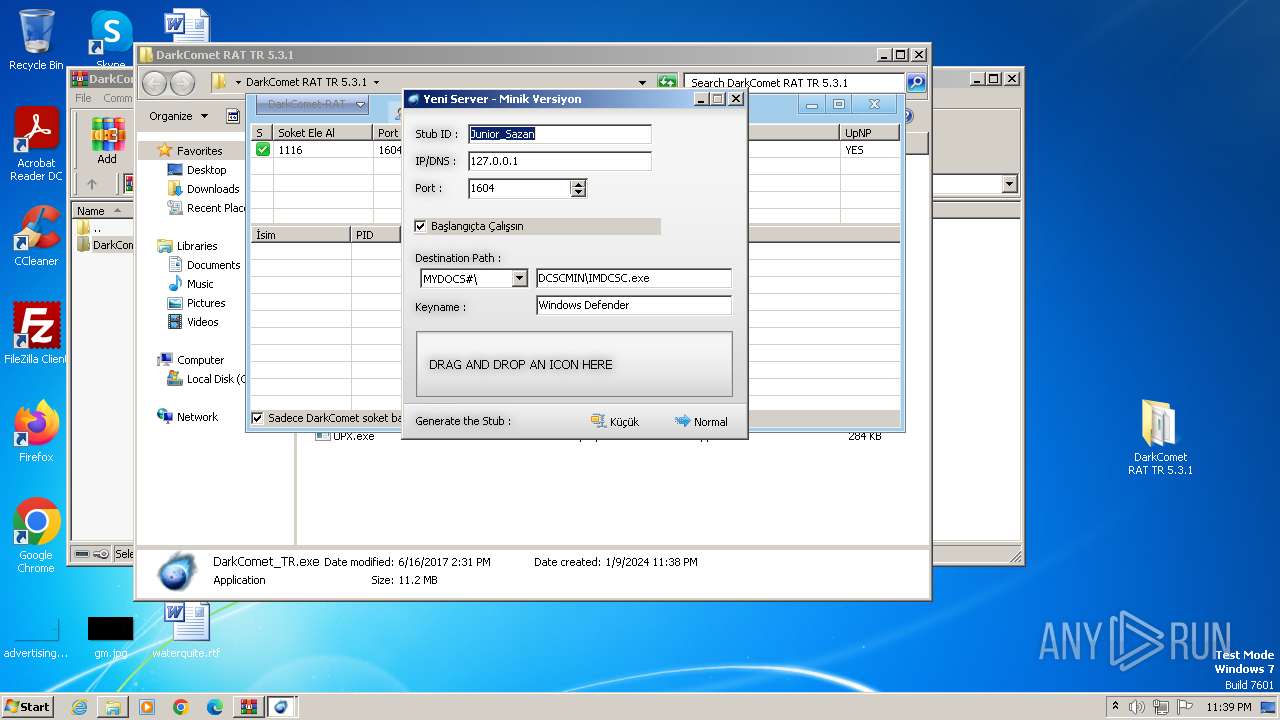
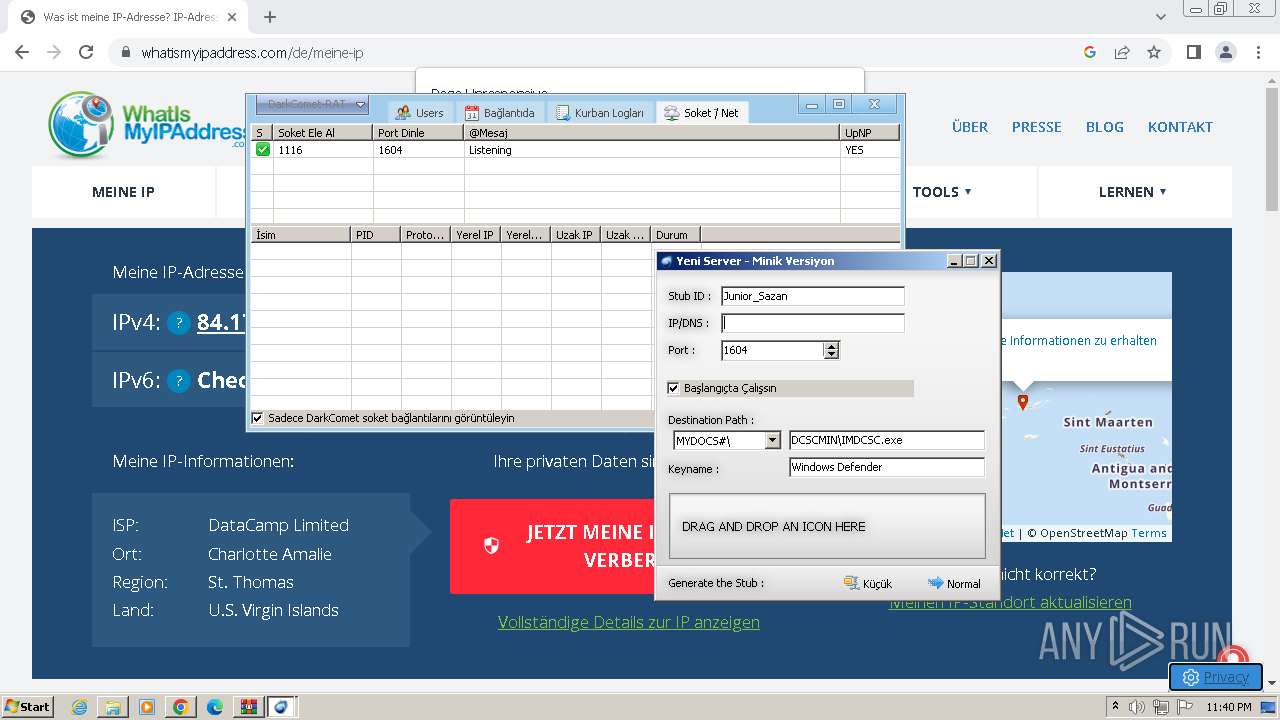
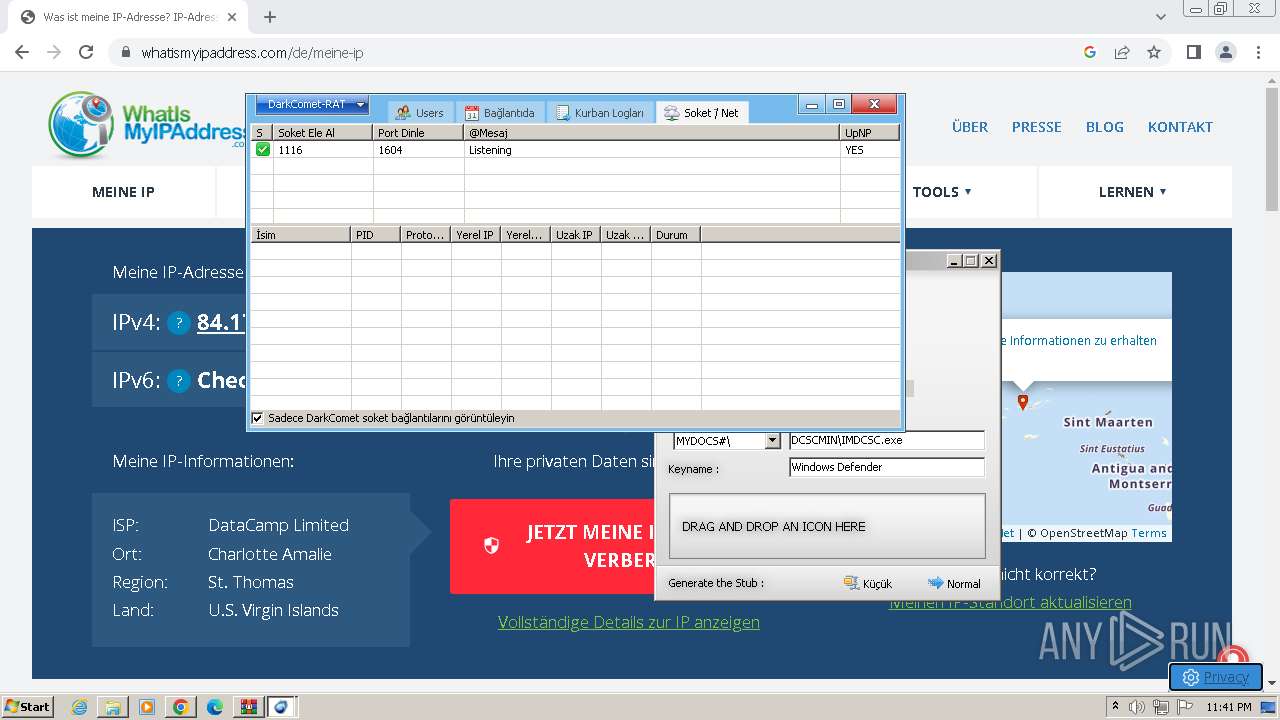
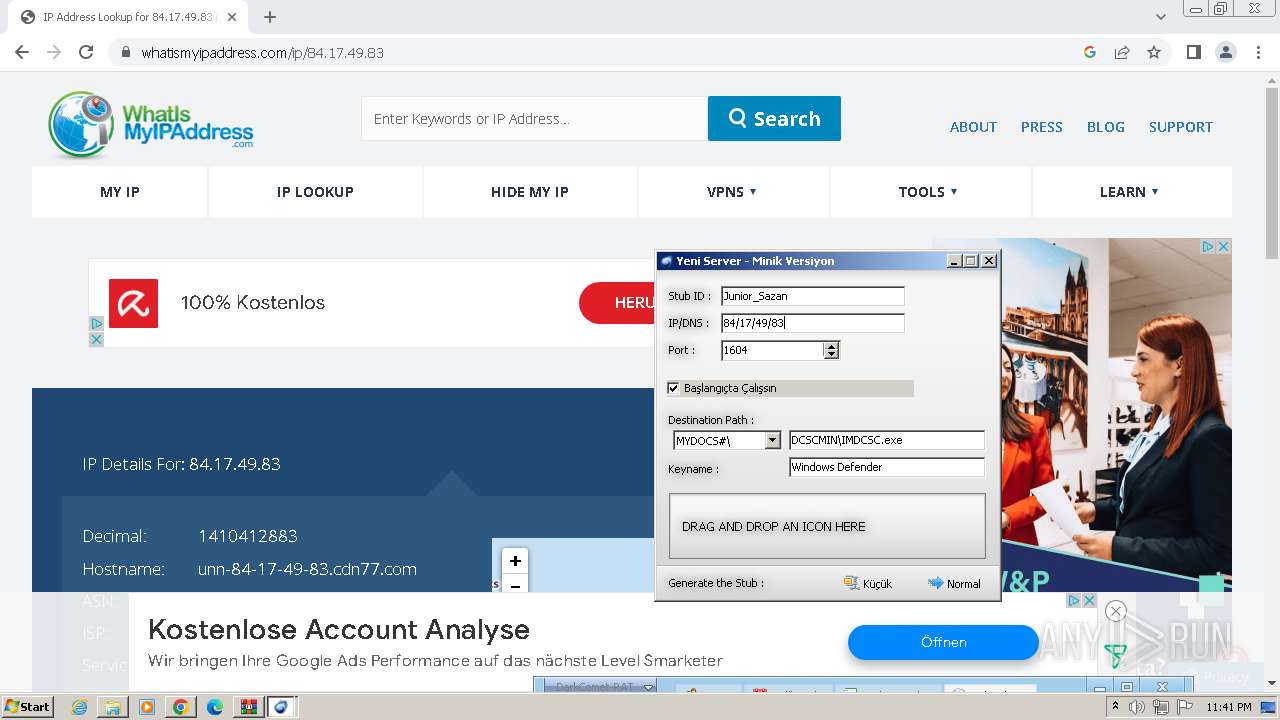
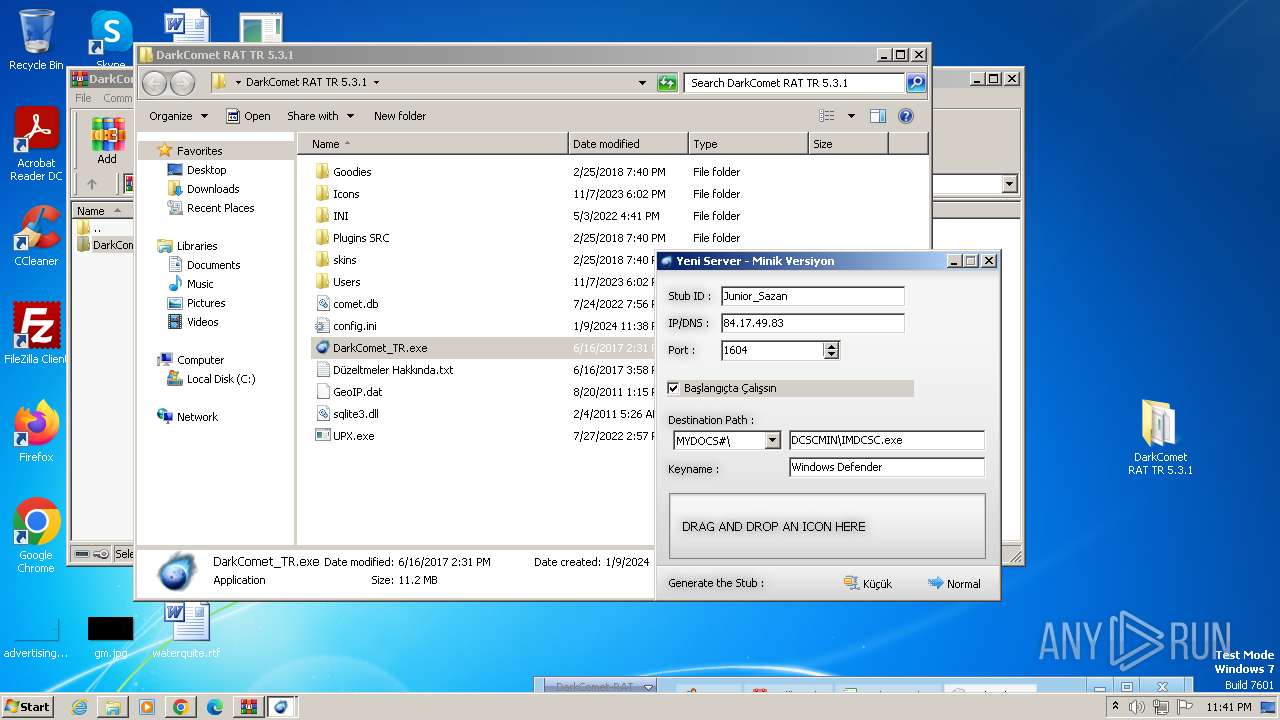
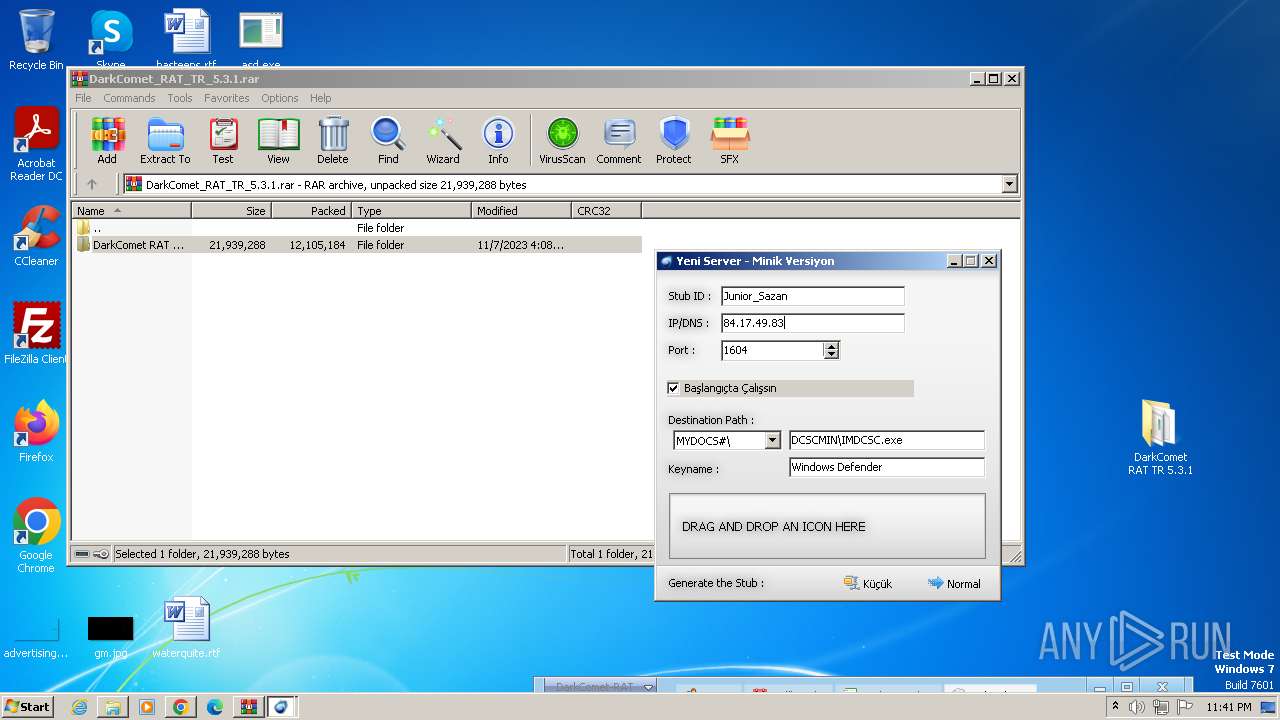
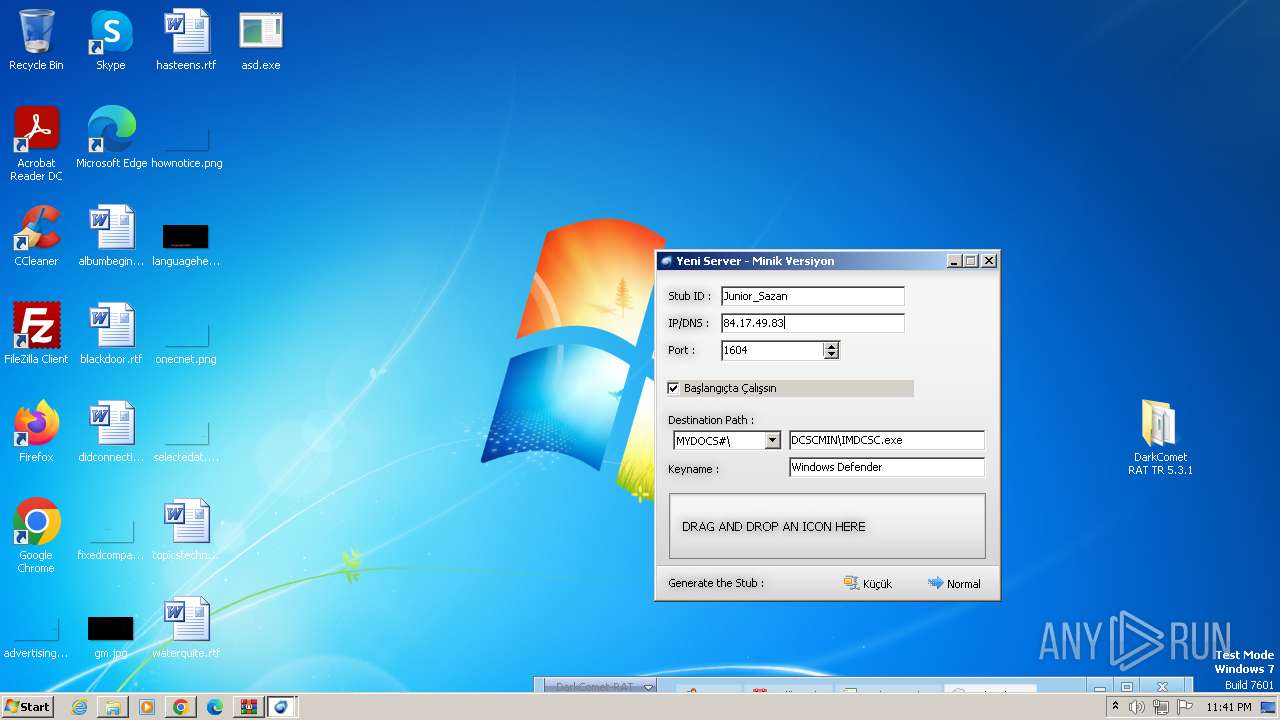
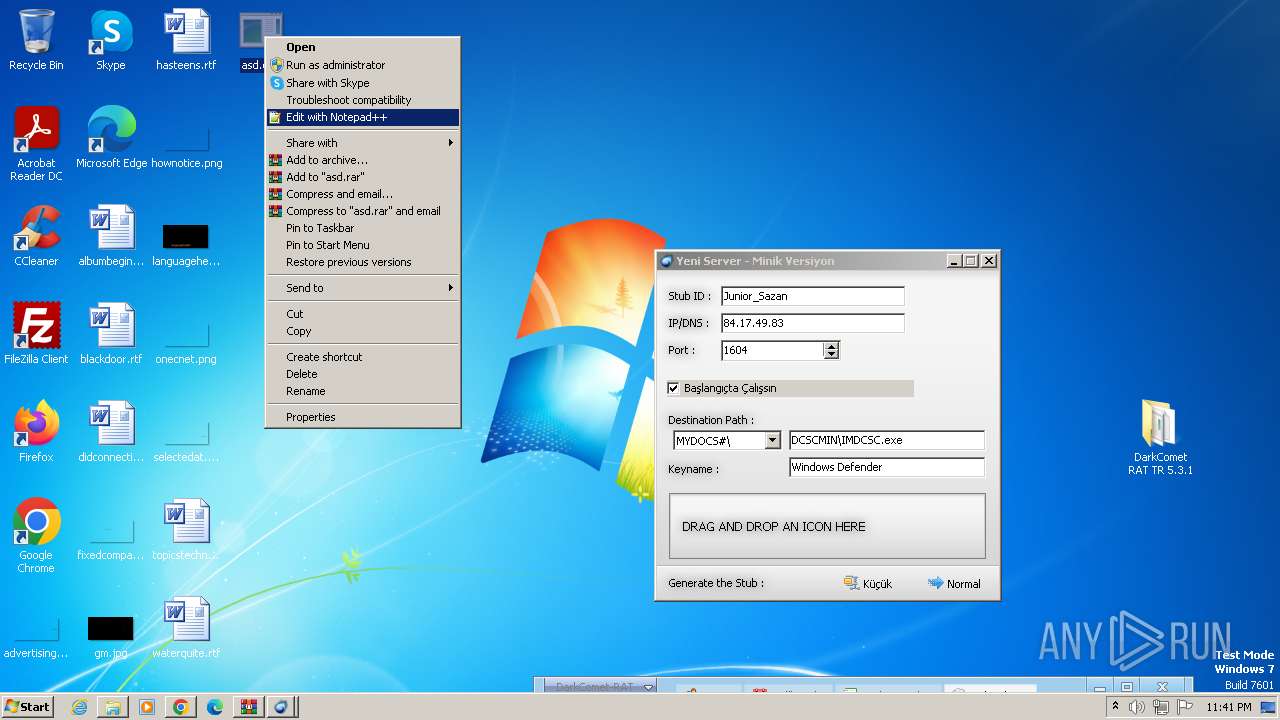
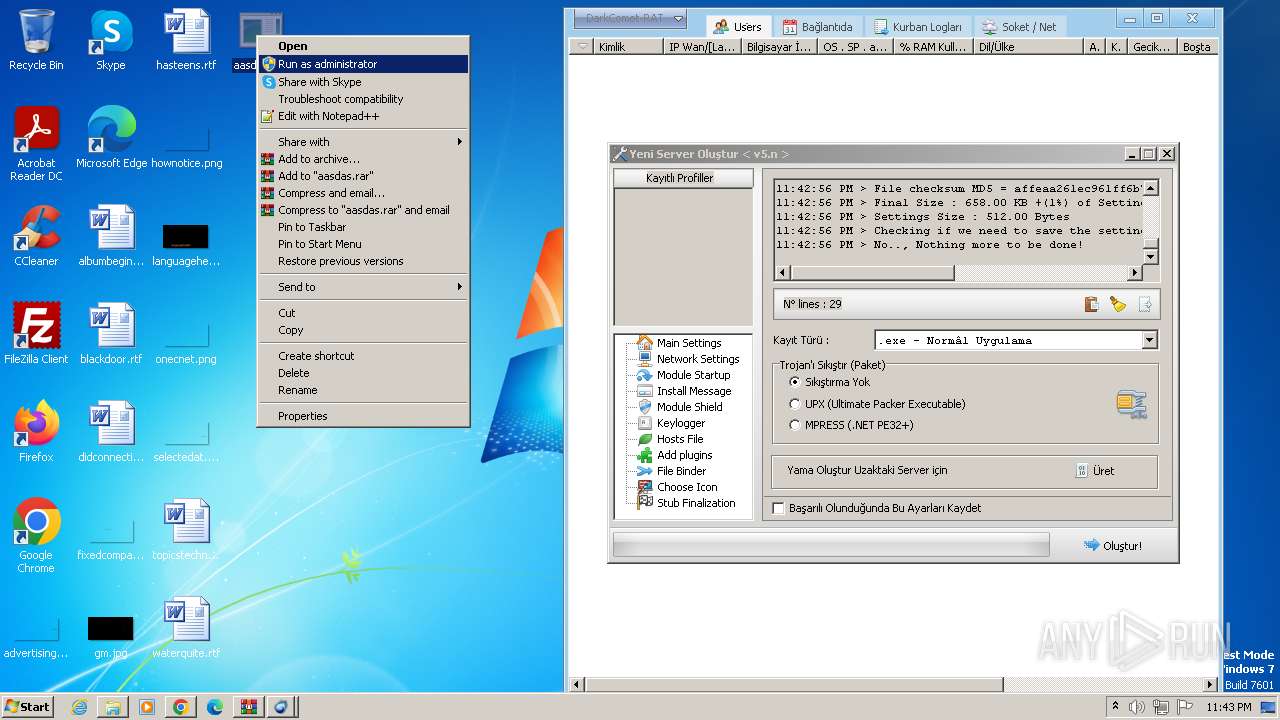
| File name: | DarkComet_RAT_TR_5.3.1.rar |
| Full analysis: | https://app.any.run/tasks/3a03c09f-e221-4dd3-8a32-98b8291e4142 |
| Verdict: | Malicious activity |
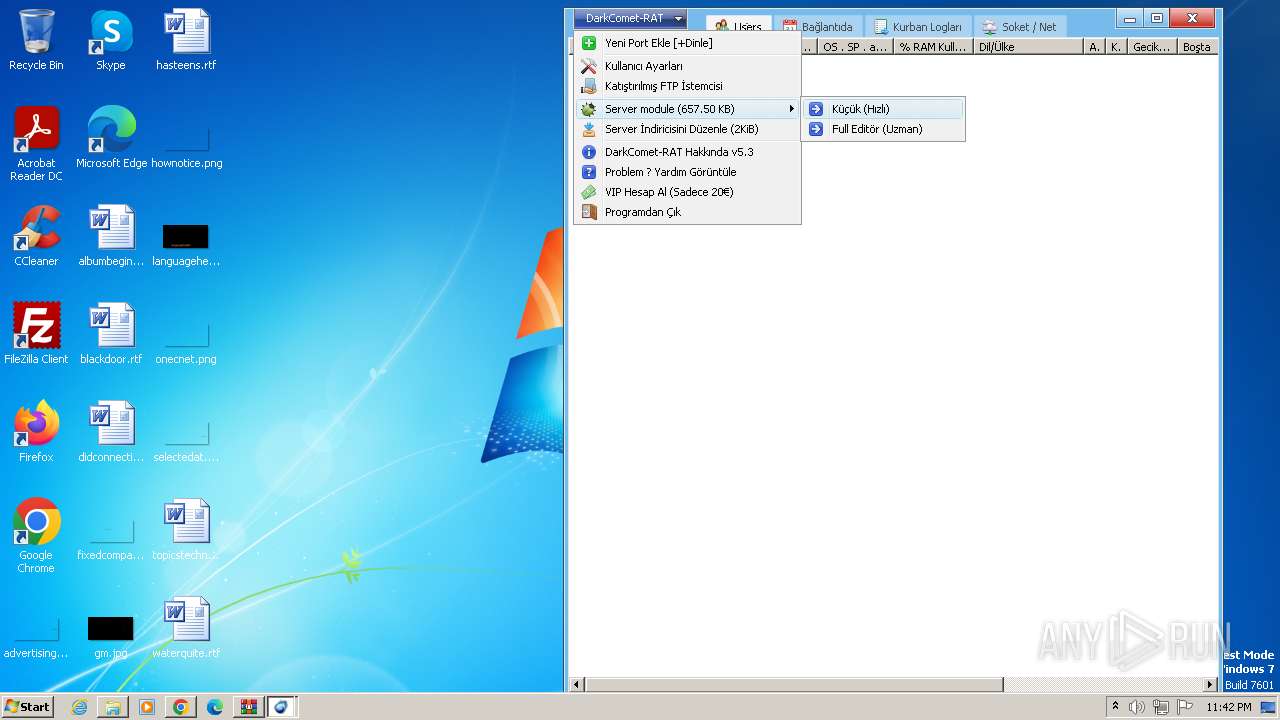
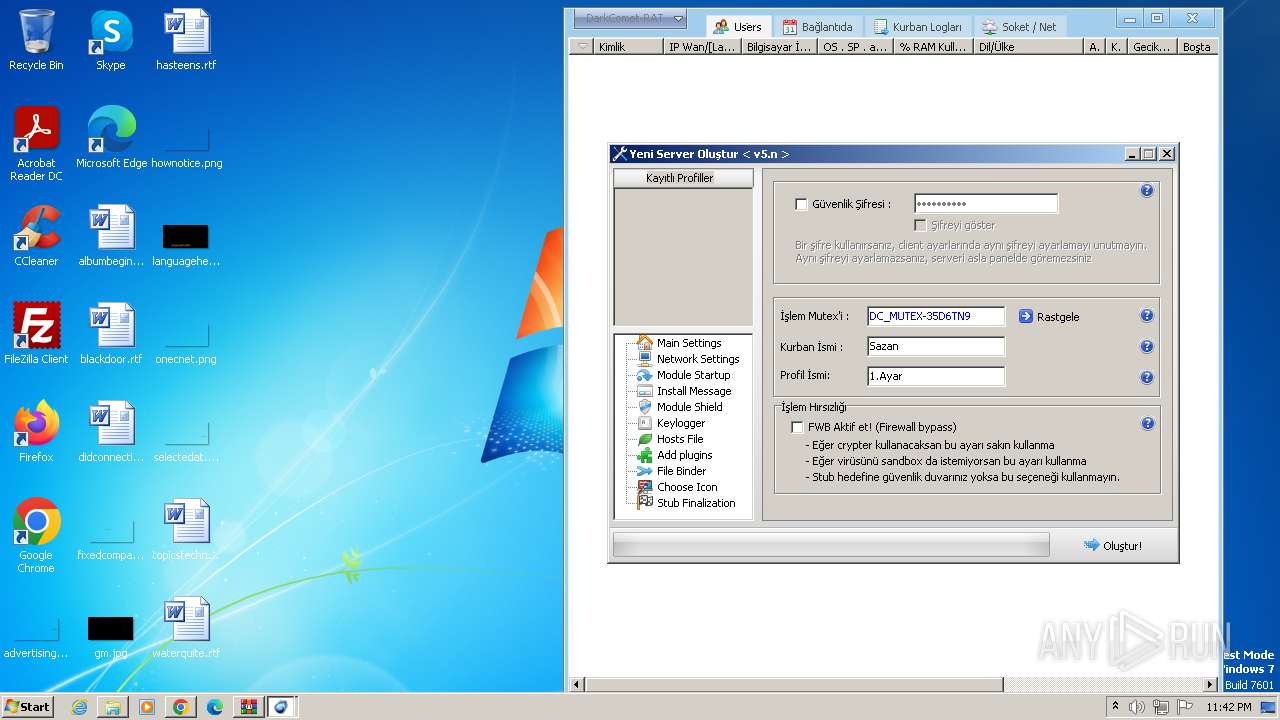
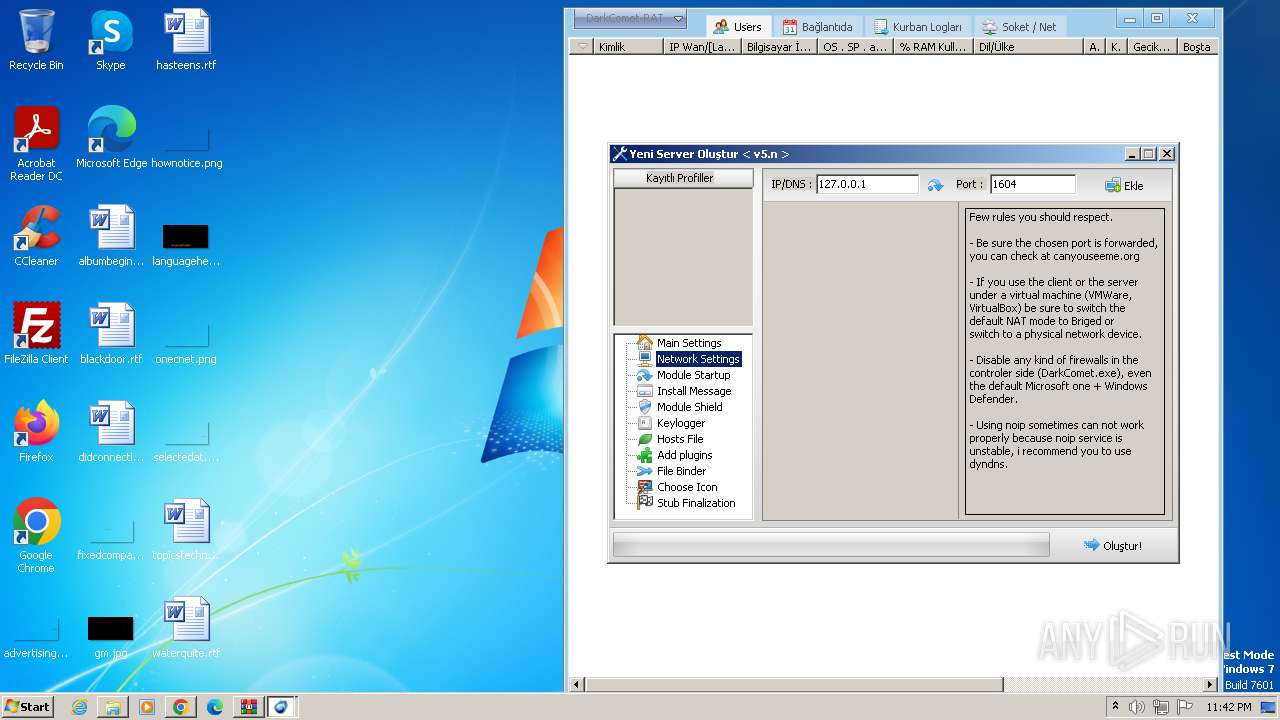
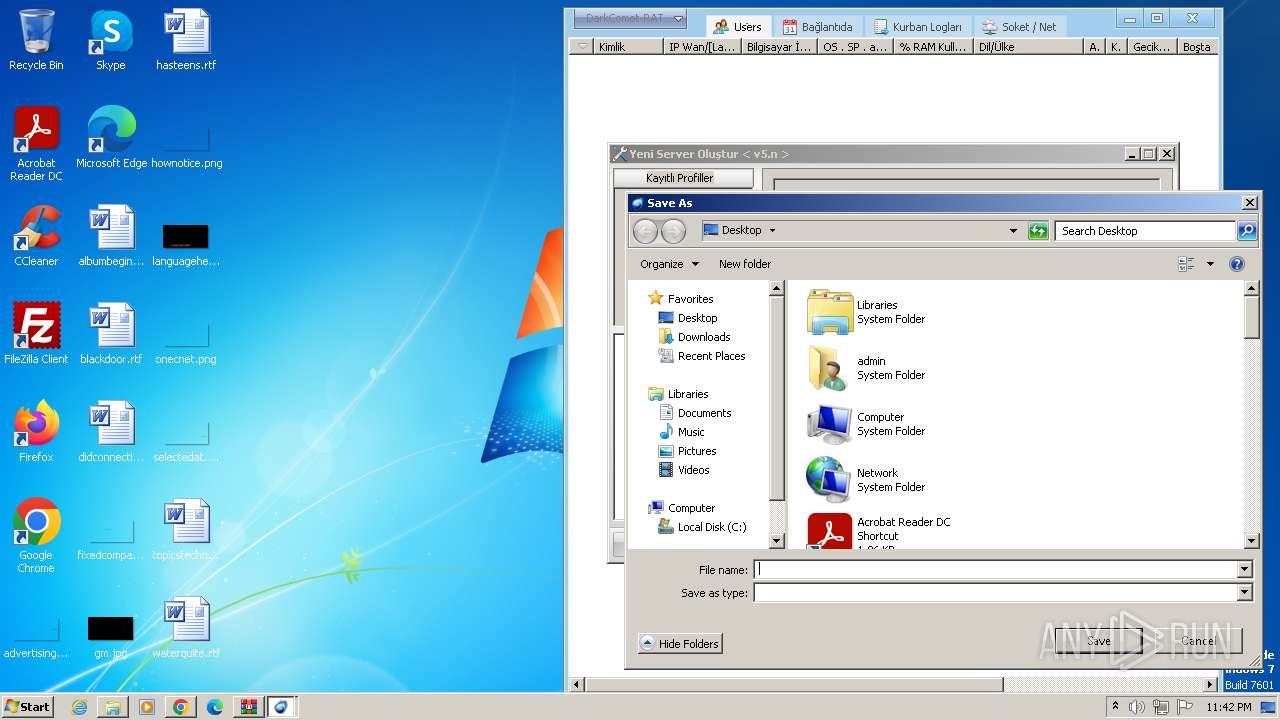
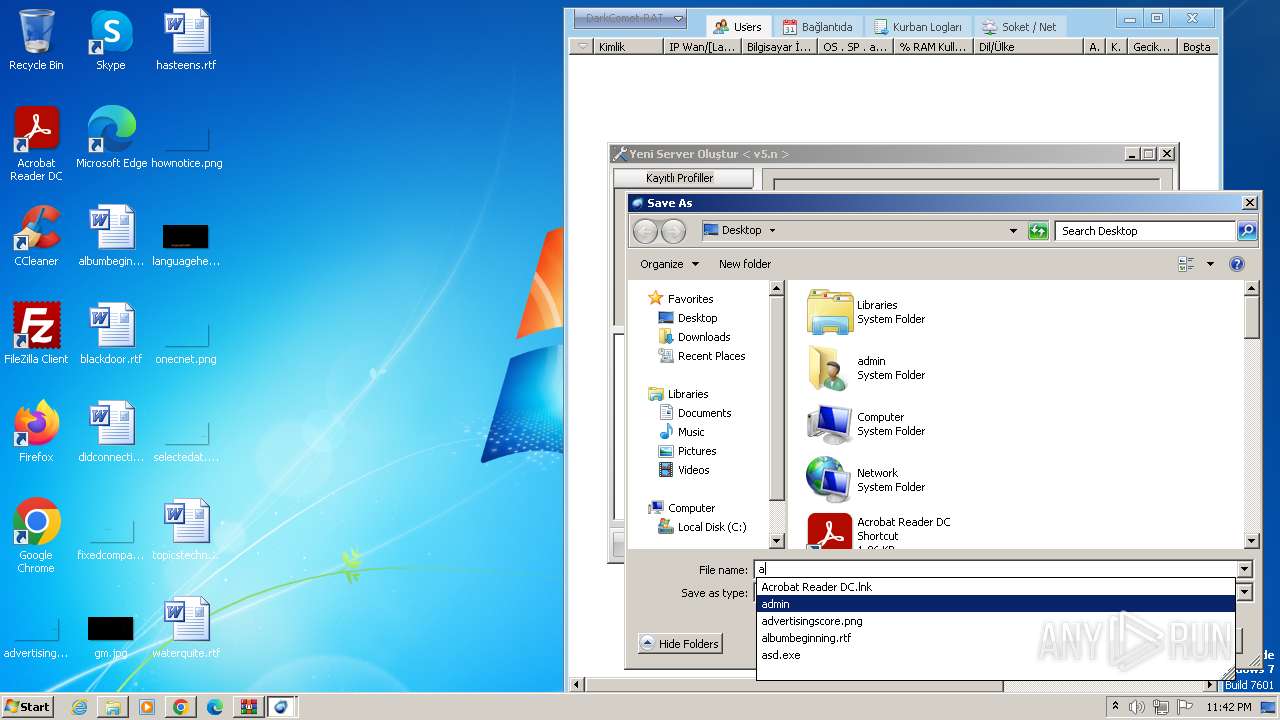
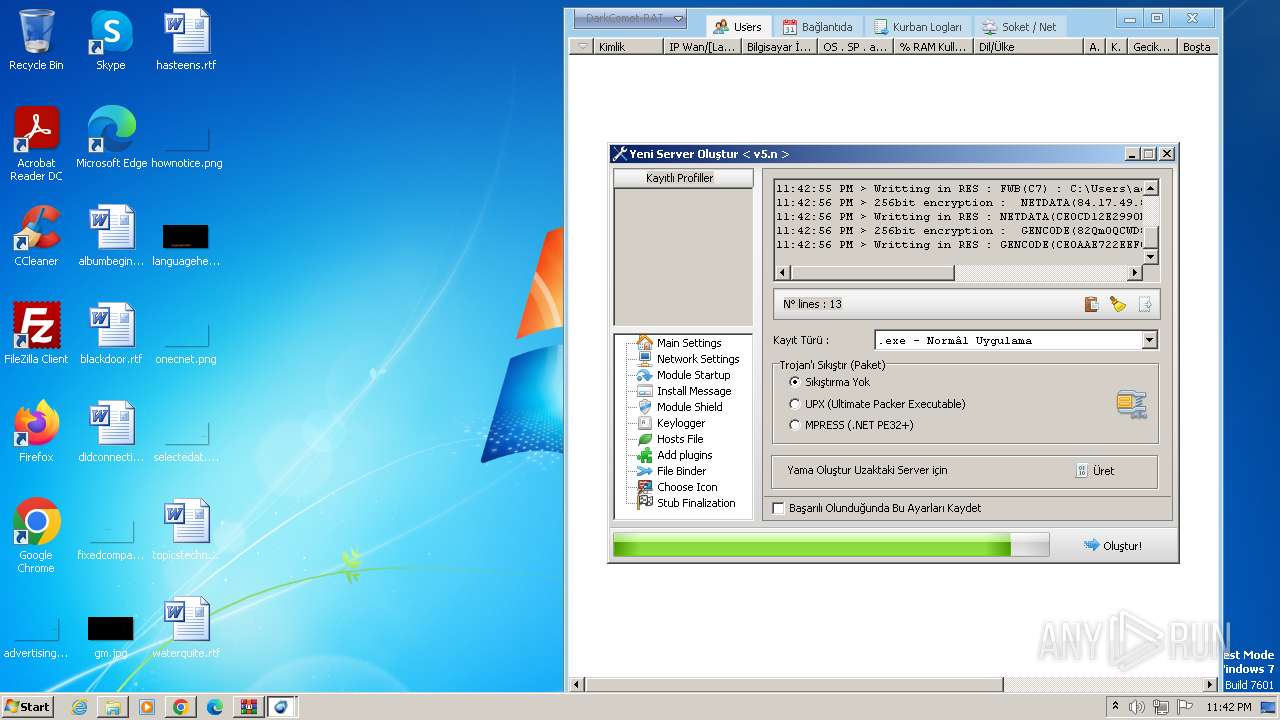
| Threats: | DarkComet RAT is a malicious program designed to remotely control or administer a victim's computer, steal private data and spy on the victim. |
| Analysis date: | January 09, 2024, 23:38:26 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-rar |
| File info: | RAR archive data, v5 |
| MD5: | B53044A16AAD31D7226227F65039129E |
| SHA1: | ECB8C4458E142A27191D8FEDD2124D6B59076712 |
| SHA256: | 2247BF993FECC3E5994AA54D15BF6B8D5AA08168A475C277AB794AE517617783 |
| SSDEEP: | 98304:DPx2B/QTBb921S9SrekzX/sPOrS3FnjwxhkdQXo9cUWWRyIXTBF8GIdzkTXL/JU+:Gh4MrzF06m2aLjkxSaeEMixrxS |
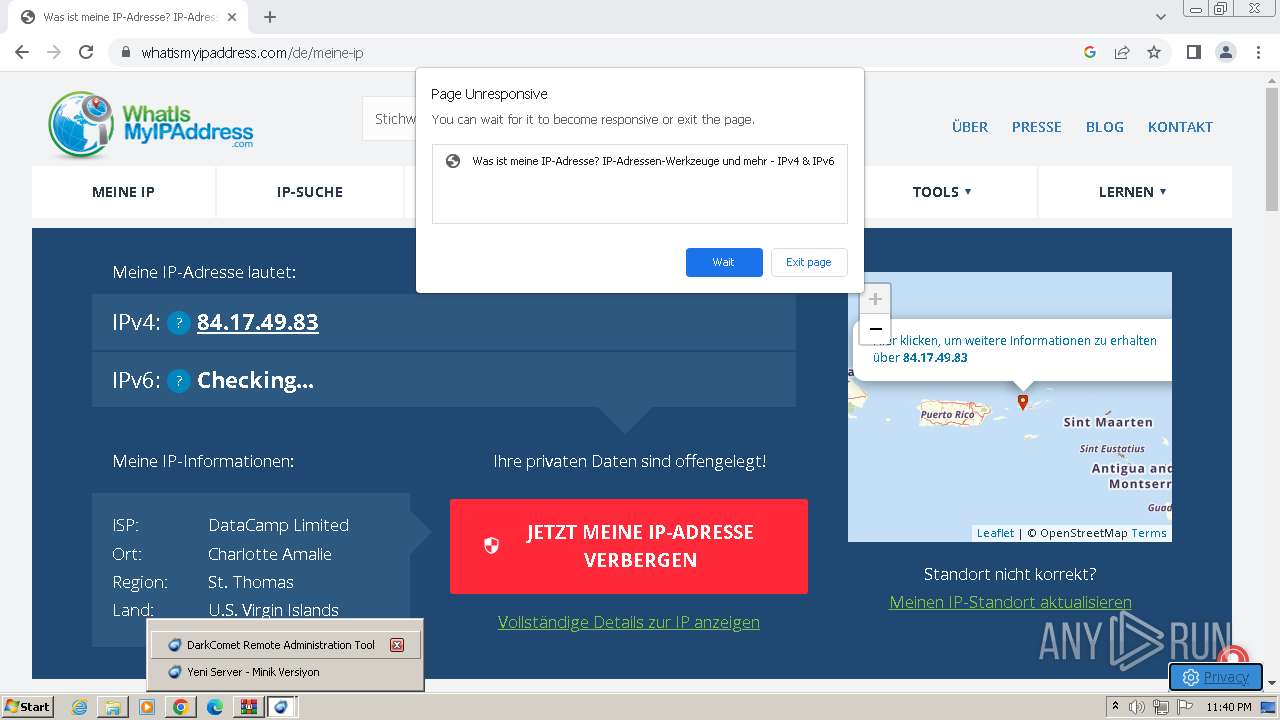
MALICIOUS
DARKCOMET has been detected (YARA)
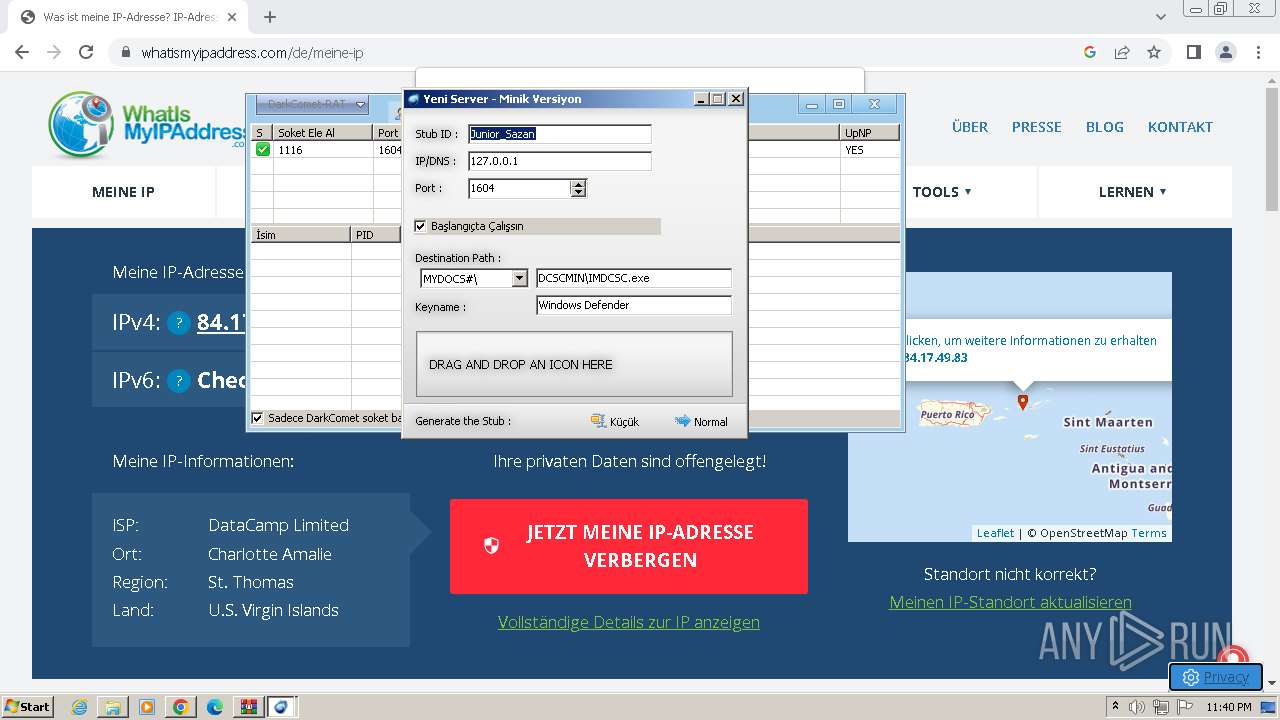
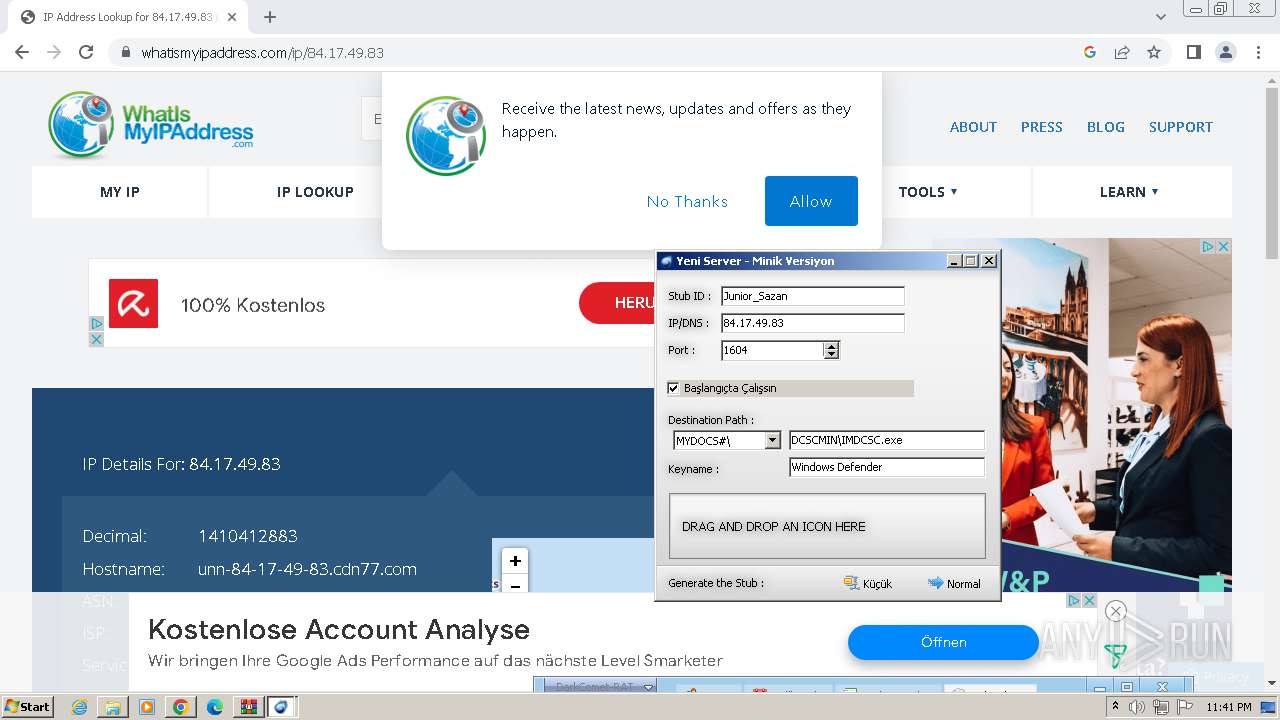
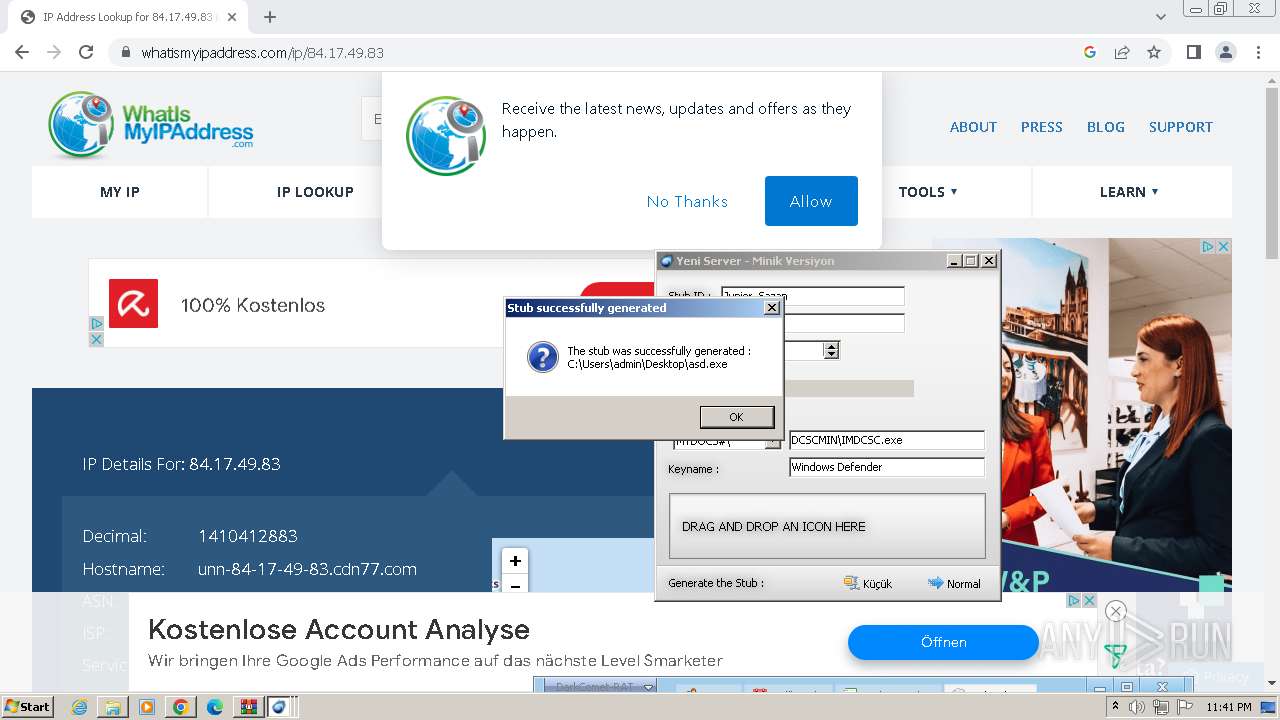
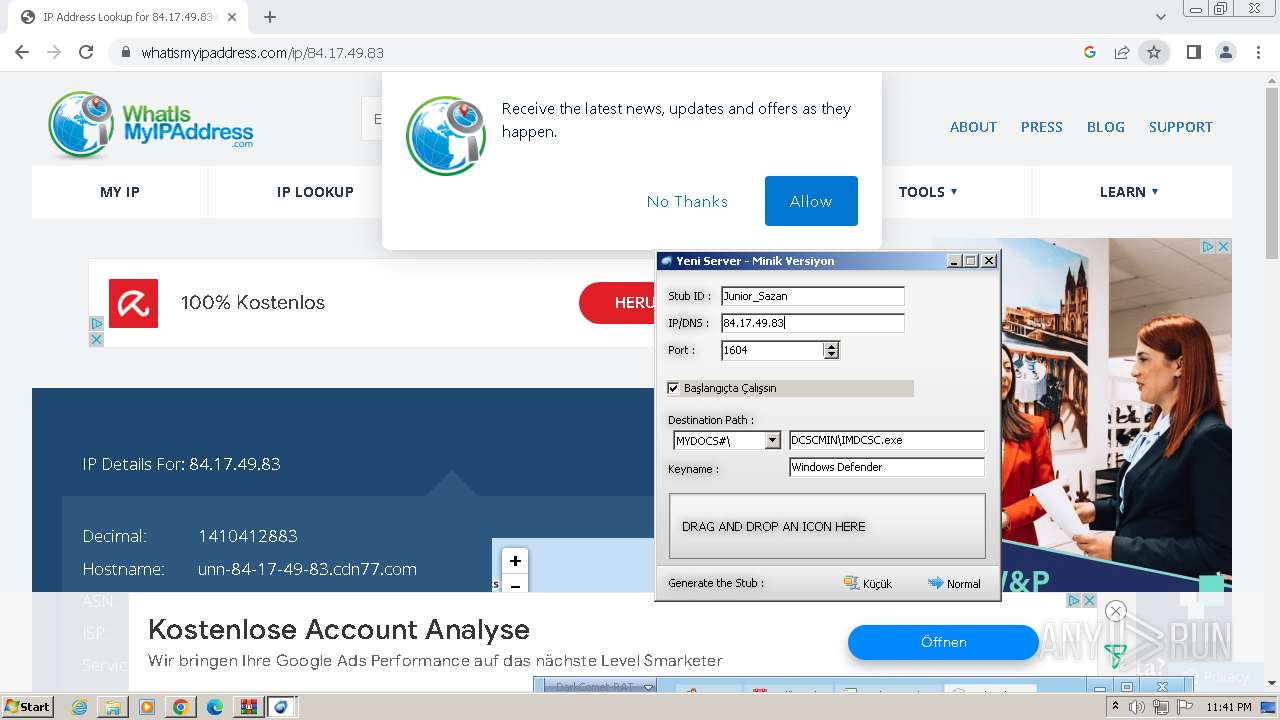
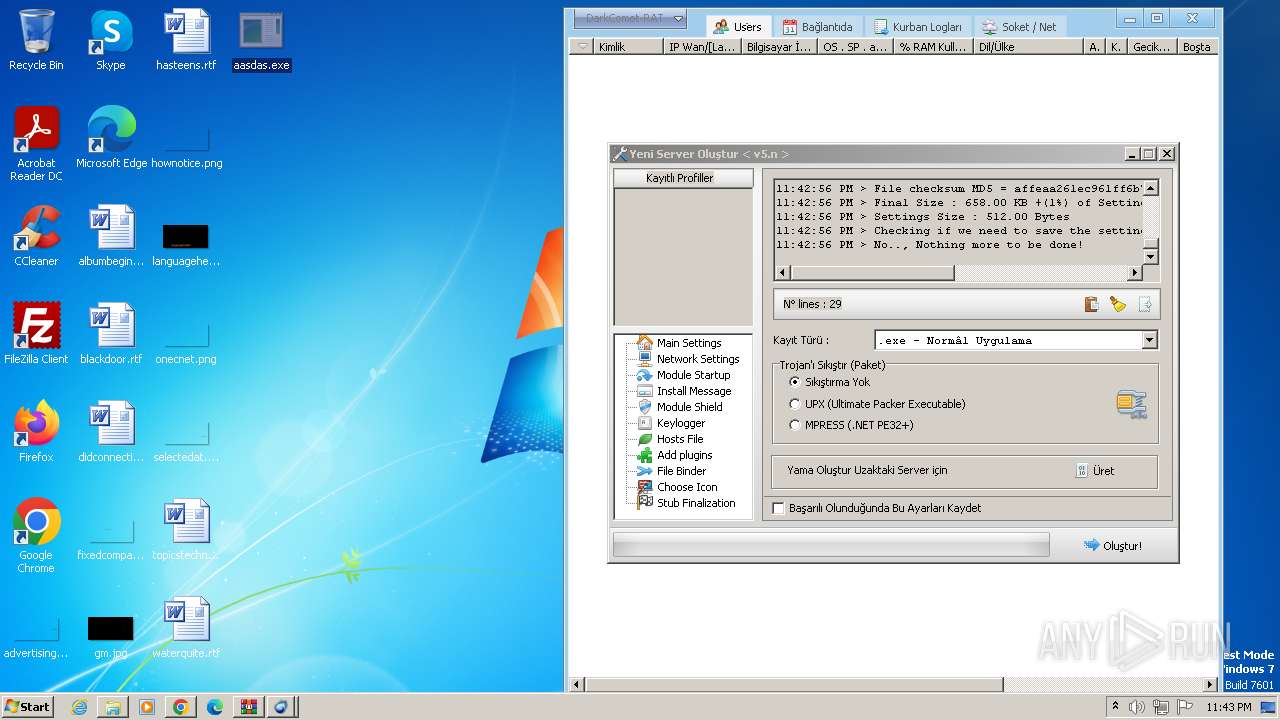
- DarkComet_TR.exe (PID: 532)
- IMDCSC.exe (PID: 3504)
Changes the login/logoff helper path in the registry
- asd.exe (PID: 3004)
SUSPICIOUS
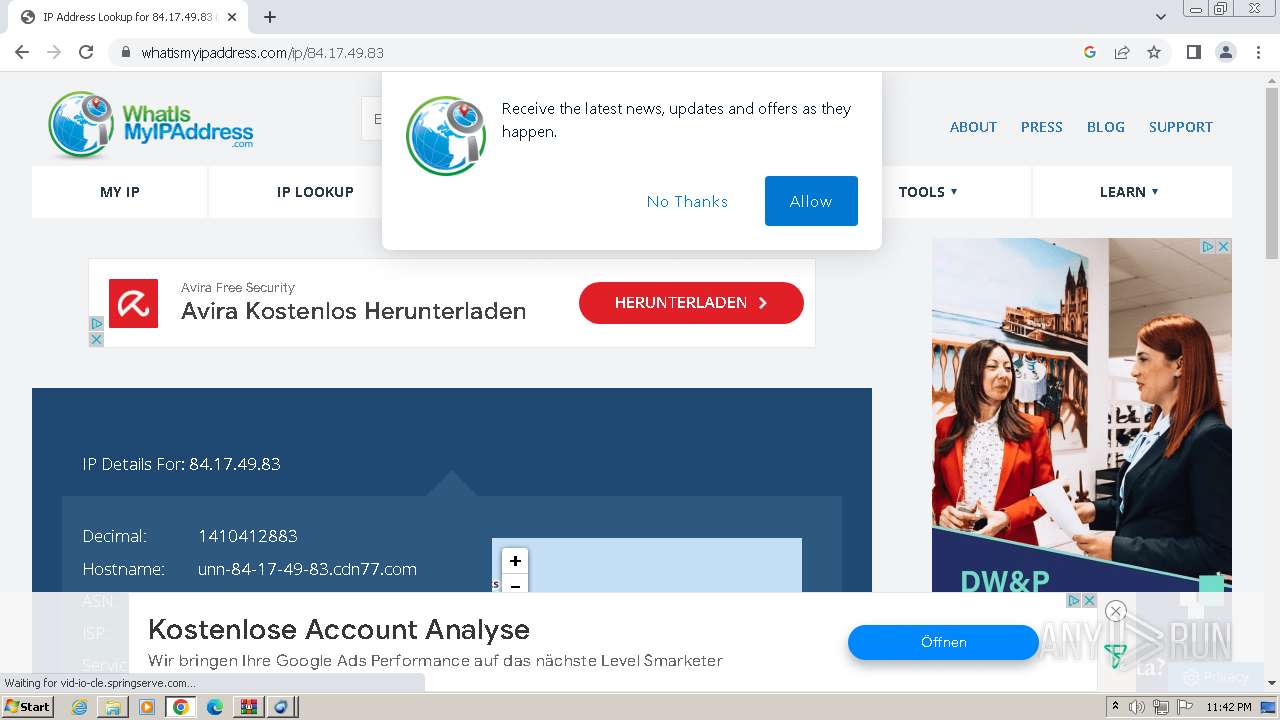
Reads the Internet Settings
- DarkComet_TR.exe (PID: 532)
- asd.exe (PID: 3004)
INFO
Manual execution by a user
- DarkComet_TR.exe (PID: 532)
- wmpnscfg.exe (PID: 2168)
- asd.exe (PID: 3004)
- chrome.exe (PID: 2308)
- asd.exe (PID: 3640)
- asd.exe (PID: 1496)
- aasdas.exe (PID: 3988)
- aasdas.exe (PID: 3972)
- aasdas.exe (PID: 3880)
Drops the executable file immediately after the start
- WinRAR.exe (PID: 124)
- DarkComet_TR.exe (PID: 532)
- asd.exe (PID: 3004)
- chrome.exe (PID: 1848)
Drops a (possible) Coronavirus decoy
- WinRAR.exe (PID: 124)
Reads the computer name
- DarkComet_TR.exe (PID: 532)
- upnp.exe (PID: 1112)
- wmpnscfg.exe (PID: 2168)
- asd.exe (PID: 3004)
- aasdas.exe (PID: 3988)
- asd.exe (PID: 1496)
- IMDCSC.exe (PID: 3504)
- asd.exe (PID: 3640)
- aasdas.exe (PID: 3972)
- aasdas.exe (PID: 3880)
Checks supported languages
- DarkComet_TR.exe (PID: 532)
- upnp.exe (PID: 1112)
- wmpnscfg.exe (PID: 2168)
- asd.exe (PID: 3004)
- asd.exe (PID: 3640)
- IMDCSC.exe (PID: 3504)
- aasdas.exe (PID: 3988)
- asd.exe (PID: 1496)
- aasdas.exe (PID: 3972)
- aasdas.exe (PID: 3880)
Create files in a temporary directory
- DarkComet_TR.exe (PID: 532)
Reads the machine GUID from the registry
- DarkComet_TR.exe (PID: 532)
Application launched itself
- chrome.exe (PID: 2308)
Starts itself from another location
- asd.exe (PID: 3004)
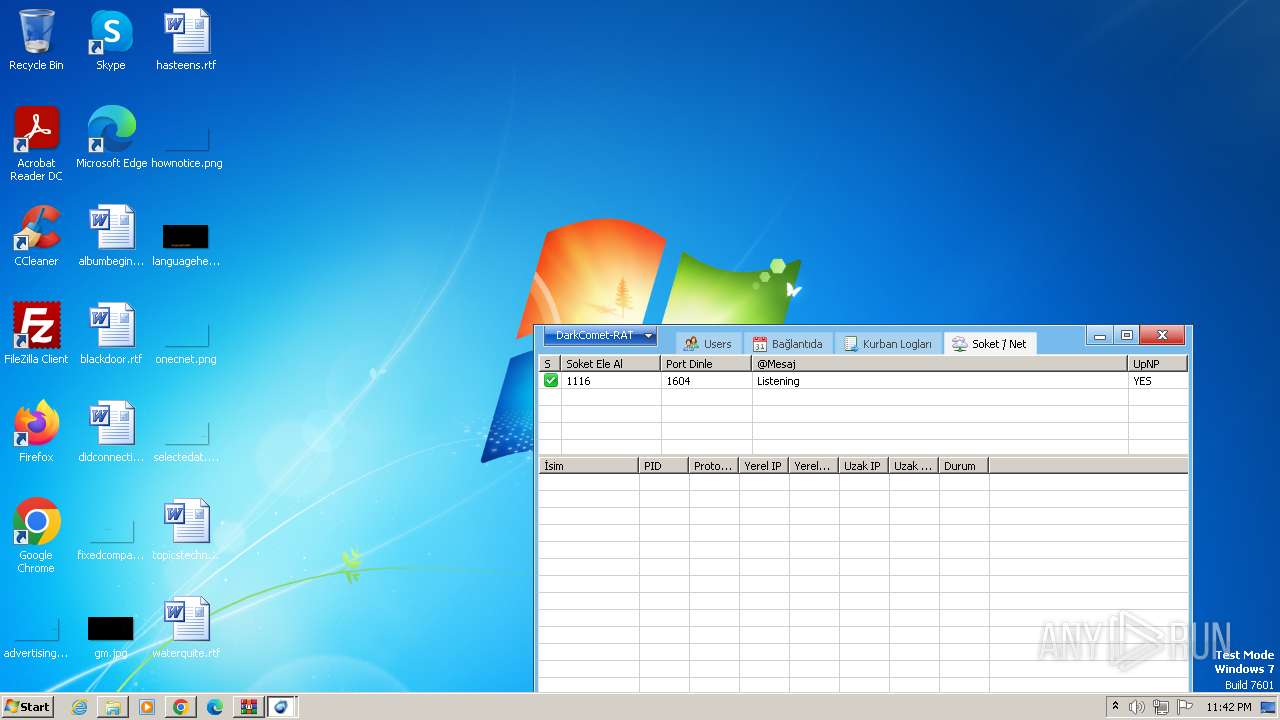
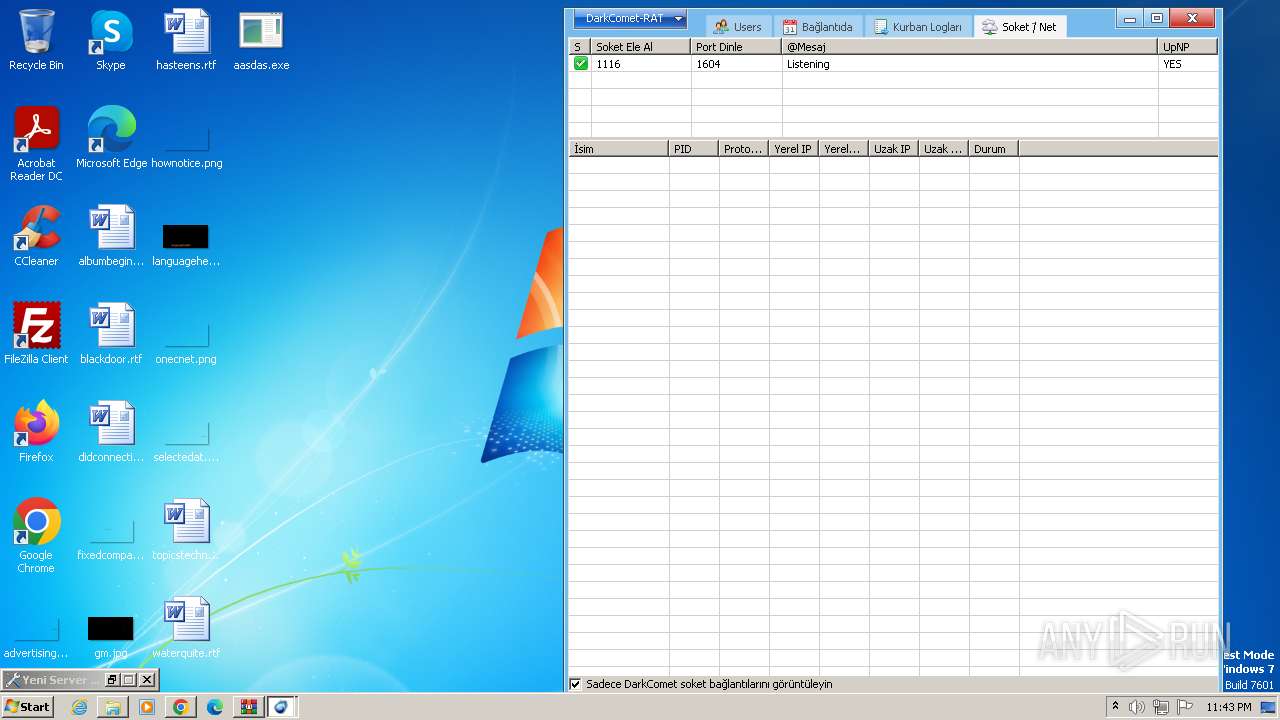
Connects to unusual port
- IMDCSC.exe (PID: 3504)
- iexplore.exe (PID: 908)
Creates files or folders in the user directory
- IMDCSC.exe (PID: 3504)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .rar | | | RAR compressed archive (v5.0) (61.5) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (38.4) |
Total processes
106
Monitored processes
62
Malicious processes
3
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 116 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --disable-gpu-compositing --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=21 --mojo-platform-channel-handle=1688 --field-trial-handle=1128,i,8636192914619069930,3958311286003204342,131072 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 124 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\DarkComet_RAT_TR_5.3.1.rar" | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
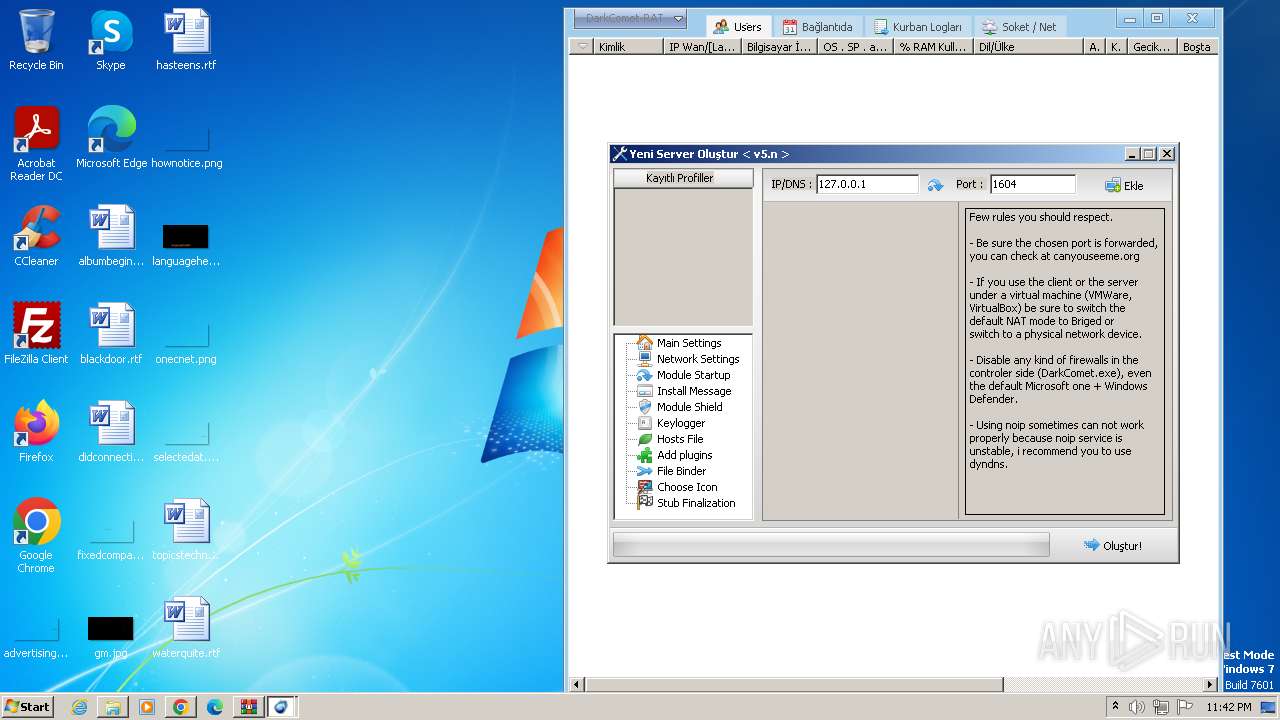
| 532 | "C:\Users\admin\Desktop\DarkComet RAT TR 5.3.1\DarkComet_TR.exe" | C:\Users\admin\Desktop\DarkComet RAT TR 5.3.1\DarkComet_TR.exe | explorer.exe | ||||||||||||
User: admin Company: Unremote.org Integrity Level: MEDIUM Description: DarkComet RAT TÜRKÇE V3 Exit code: 0 Version: 4.2.0.28 Modules
| |||||||||||||||
| 548 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --disable-gpu-compositing --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=42 --mojo-platform-channel-handle=5900 --field-trial-handle=1128,i,8636192914619069930,3958311286003204342,131072 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 552 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --first-renderer-process --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=6 --mojo-platform-channel-handle=2132 --field-trial-handle=1128,i,8636192914619069930,3958311286003204342,131072 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 568 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --lang=en-US --service-sandbox-type=service --disable-quic --mojo-platform-channel-handle=4260 --field-trial-handle=1128,i,8636192914619069930,3958311286003204342,131072 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 764 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --disable-gpu-compositing --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=22 --mojo-platform-channel-handle=3856 --field-trial-handle=1128,i,8636192914619069930,3958311286003204342,131072 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 884 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --disable-quic --mojo-platform-channel-handle=3620 --field-trial-handle=1128,i,8636192914619069930,3958311286003204342,131072 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 900 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --disable-quic --mojo-platform-channel-handle=1292 --field-trial-handle=1128,i,8636192914619069930,3958311286003204342,131072 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 908 | "C:\Program Files\Internet Explorer\iexplore.exe" | C:\Program Files\Internet Explorer\iexplore.exe | aasdas.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
Total events
8 904
Read events
8 696
Write events
201
Delete events
7
Modification events
| (PID) Process: | (124) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (124) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\virtio_ivshmem_master_build.zip | |||
| (PID) Process: | (124) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\phacker.zip | |||
| (PID) Process: | (124) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (124) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\curl-8.5.0_1-win32-mingw.zip | |||
| (PID) Process: | (124) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (124) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (124) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (124) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (532) DarkComet_TR.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
Executable files
19
Suspicious files
457
Text files
90
Unknown types
1
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 124 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa124.301\DarkComet RAT TR 5.3.1\GeoIP.dat | binary | |
MD5:B64EA0C3E9617CCD2F22D8568676A325 | SHA256:432E12E688449C2CF1B184C94E2E964F9E09398C194888A7FE1A5B1F8CF3059B | |||
| 124 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa124.301\DarkComet RAT TR 5.3.1\Icons\cubic.ico | image | |
MD5:F273CF2C932B6D768BB2D1D62E9D2A4A | SHA256:713CC5EDE2B35AE4933AD31B02B7C4BDA1255C9709B219A13162B72F228DF652 | |||
| 124 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa124.301\DarkComet RAT TR 5.3.1\Goodies\wallpaper_1.jpg | image | |
MD5:5B0F627CA05BE451F9A7AD52241DF3E3 | SHA256:8977220BC72B4588DF3873044E6DD9BFAF166E48DA57386B4C152B72C8424185 | |||
| 124 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa124.301\DarkComet RAT TR 5.3.1\Icons\chrome.ico | image | |
MD5:16A9E9B49F6E08635EBE55F5ECD5F346 | SHA256:FCD5923F3401B523C3AD27CE999398328612A86EEC253CC7C09030A0035B0F99 | |||
| 124 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa124.301\DarkComet RAT TR 5.3.1\Icons\heart.ico | image | |
MD5:AD26DD83AE2EC2DDF0CC07021825D063 | SHA256:11D3EAC0551CAE9686BC6EBE6166E6EEAB70C3B5F5BFC56DB45FF9DAFC8188D7 | |||
| 124 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa124.301\DarkComet RAT TR 5.3.1\Icons\facebook.ico | image | |
MD5:C6120E467C833D5F277C2B939251918E | SHA256:62A4FBD69E3E534E2CE8FE2F664EA8A803EB29F2EFF3BC7503DBA641AB33E589 | |||
| 124 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa124.301\DarkComet RAT TR 5.3.1\Icons\archive.ico | image | |
MD5:5AF592DF403C50B14B47F9185CFB417F | SHA256:99B5CEE64EF8164A68CAE08D883AEF65C4C96D3B57A8B075D330C537AAB183C5 | |||
| 124 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa124.301\DarkComet RAT TR 5.3.1\DarkComet_TR.exe | executable | |
MD5:9A7155E3DFE956A9658B1293906478CB | SHA256:32892D9BC32B165F528F64EFC5A71166FCA91CBD45CAC2885ECCA22FC78E1E78 | |||
| 124 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa124.301\DarkComet RAT TR 5.3.1\Icons\againzip.ico | image | |
MD5:B87DBD32F31532EA8F7AF9D28EE7800C | SHA256:C3C3B009CB602535C18ED168C0BC448441A62B63C69FF27E3F9C2D8973411250 | |||
| 124 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa124.301\DarkComet RAT TR 5.3.1\Icons\bittorrent.ico | image | |
MD5:73D8DECAB435ACB32DF1DCE812ED3ACD | SHA256:8E44BC15B2A99D99D4670112B6E3C494EA46ADB49A35899EC0192F12DCC30F5F | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
33
TCP/UDP connections
355
DNS requests
412
Threats
3
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
856 | svchost.exe | HEAD | 200 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/adasgb6qzo3kp62542i5hyaakdua_30.2/imefjhfbkmcmebodilednhmaccmincoa_30.2_win_kwiu22sehztwd3bii7gzgq4vri.crx3 | unknown | — | — | unknown |
856 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/adasgb6qzo3kp62542i5hyaakdua_30.2/imefjhfbkmcmebodilednhmaccmincoa_30.2_win_kwiu22sehztwd3bii7gzgq4vri.crx3 | unknown | binary | 6.55 Kb | unknown |
856 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/adasgb6qzo3kp62542i5hyaakdua_30.2/imefjhfbkmcmebodilednhmaccmincoa_30.2_win_kwiu22sehztwd3bii7gzgq4vri.crx3 | unknown | binary | 7.58 Kb | unknown |
856 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/adasgb6qzo3kp62542i5hyaakdua_30.2/imefjhfbkmcmebodilednhmaccmincoa_30.2_win_kwiu22sehztwd3bii7gzgq4vri.crx3 | unknown | binary | 8.77 Kb | unknown |
856 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/adasgb6qzo3kp62542i5hyaakdua_30.2/imefjhfbkmcmebodilednhmaccmincoa_30.2_win_kwiu22sehztwd3bii7gzgq4vri.crx3 | unknown | binary | 20.1 Kb | unknown |
856 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/adasgb6qzo3kp62542i5hyaakdua_30.2/imefjhfbkmcmebodilednhmaccmincoa_30.2_win_kwiu22sehztwd3bii7gzgq4vri.crx3 | unknown | binary | 25.4 Kb | unknown |
856 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/adasgb6qzo3kp62542i5hyaakdua_30.2/imefjhfbkmcmebodilednhmaccmincoa_30.2_win_kwiu22sehztwd3bii7gzgq4vri.crx3 | unknown | binary | 39.9 Kb | unknown |
856 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/adasgb6qzo3kp62542i5hyaakdua_30.2/imefjhfbkmcmebodilednhmaccmincoa_30.2_win_kwiu22sehztwd3bii7gzgq4vri.crx3 | unknown | binary | 9.05 Kb | unknown |
856 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/adasgb6qzo3kp62542i5hyaakdua_30.2/imefjhfbkmcmebodilednhmaccmincoa_30.2_win_kwiu22sehztwd3bii7gzgq4vri.crx3 | unknown | binary | 172 Kb | unknown |
856 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/adasgb6qzo3kp62542i5hyaakdua_30.2/imefjhfbkmcmebodilednhmaccmincoa_30.2_win_kwiu22sehztwd3bii7gzgq4vri.crx3 | unknown | binary | 679 Kb | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
1112 | upnp.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
2308 | chrome.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
2712 | chrome.exe | 142.250.186.99:443 | clientservices.googleapis.com | GOOGLE | US | whitelisted |
2712 | chrome.exe | 74.125.71.84:443 | accounts.google.com | GOOGLE | US | unknown |
2712 | chrome.exe | 142.250.186.164:443 | www.google.com | GOOGLE | US | whitelisted |
2712 | chrome.exe | 142.250.185.195:443 | www.gstatic.com | GOOGLE | US | whitelisted |
2712 | chrome.exe | 142.250.184.206:443 | apis.google.com | GOOGLE | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
clientservices.googleapis.com |
| whitelisted |
accounts.google.com |
| shared |
www.google.com |
| whitelisted |
www.gstatic.com |
| whitelisted |
apis.google.com |
| whitelisted |
encrypted-tbn0.gstatic.com |
| whitelisted |
update.googleapis.com |
| whitelisted |
fonts.gstatic.com |
| whitelisted |
consent.google.com |
| shared |
safebrowsing.googleapis.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2712 | chrome.exe | Device Retrieving External IP Address Detected | ET POLICY Known External IP Lookup Service Domain in SNI |
2712 | chrome.exe | Not Suspicious Traffic | INFO [ANY.RUN] A free CDN for open source projects (jsdelivr .net) |
2712 | chrome.exe | Not Suspicious Traffic | INFO [ANY.RUN] Cloudflare Network Error Logging (NEL) |