| File name: | linksodi.exe |
| Full analysis: | https://app.any.run/tasks/e32a5406-29aa-44e2-af91-c02cba17e70a |
| Verdict: | Malicious activity |
| Threats: | Lumma is an information stealer, developed using the C programming language. It is offered for sale as a malware-as-a-service, with several plans available. It usually targets cryptocurrency wallets, login credentials, and other sensitive information on a compromised system. The malicious software regularly gets updates that improve and expand its functionality, making it a serious stealer threat. |
| Analysis date: | December 13, 2024, 21:10:23 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (console) Intel 80386 Mono/.Net assembly, for MS Windows, 5 sections |
| MD5: | FCA2CD59230700A1CF756D3AA177A028 |
| SHA1: | 45BA65B17AA5F386A71197BB6D603C682E66465E |
| SHA256: | 222698E152FF132BBBCB0B0679217849332D4056EEE11AD96192A1A240A136AD |
| SSDEEP: | 24576:Xa69OF+tiLTGBCKQ57wdqyTWYRR7qsunGsOorXVm:Xa69OYtiLTGBCKQ57wdqy6YRR7funHOm |
MALICIOUS
LUMMA mutex has been found
- aspnet_regiis.exe (PID: 4716)
Actions looks like stealing of personal data
- aspnet_regiis.exe (PID: 4716)
Steals credentials from Web Browsers
- aspnet_regiis.exe (PID: 4716)
LUMMA has been detected (YARA)
- aspnet_regiis.exe (PID: 4716)
SUSPICIOUS
Executable content was dropped or overwritten
- linksodi.exe (PID: 1556)
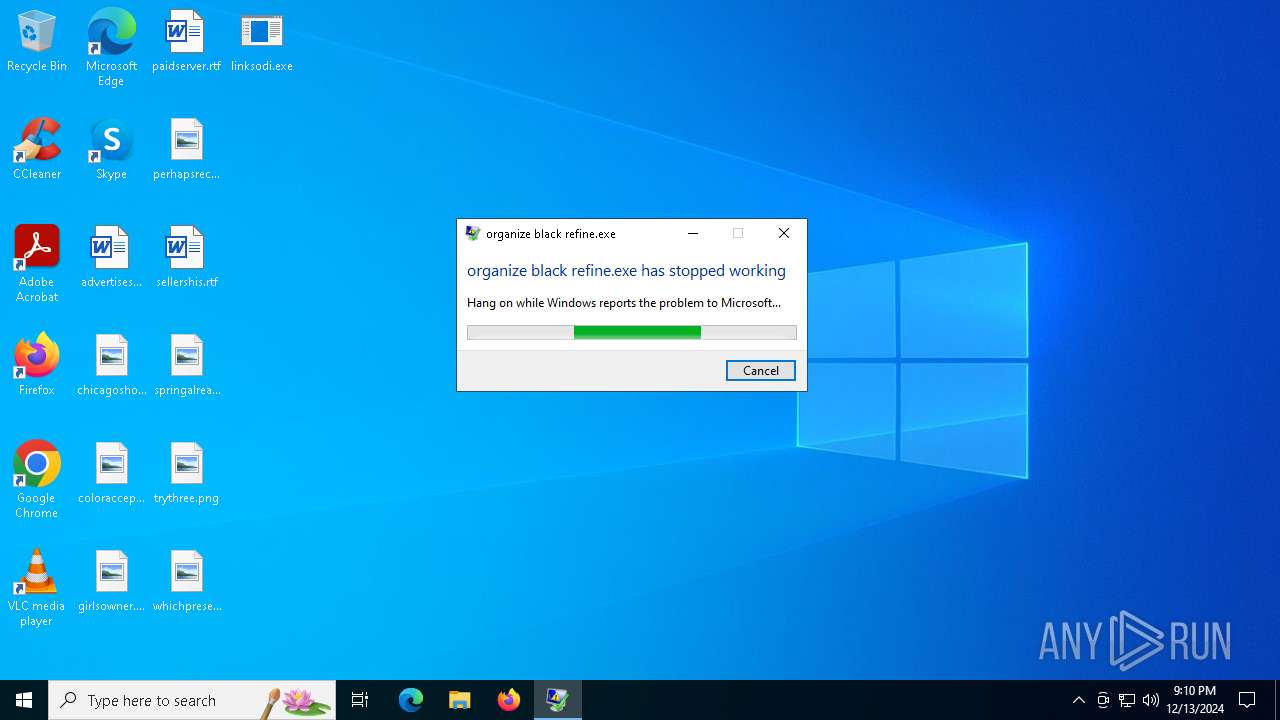
Executes application which crashes
- linksodi.exe (PID: 1556)
INFO
Reads the software policy settings
- aspnet_regiis.exe (PID: 4716)
Reads the computer name
- aspnet_regiis.exe (PID: 4716)
- linksodi.exe (PID: 1556)
Checks supported languages
- linksodi.exe (PID: 1556)
- aspnet_regiis.exe (PID: 4716)
Reads the machine GUID from the registry
- aspnet_regiis.exe (PID: 4716)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .dll | | | Win32 Dynamic Link Library (generic) (38.3) |
|---|---|---|
| .exe | | | Win32 Executable (generic) (26.2) |
| .exe | | | Win16/32 Executable Delphi generic (12) |
| .exe | | | Generic Win/DOS Executable (11.6) |
| .exe | | | DOS Executable Generic (11.6) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2024:12:13 13:42:48+00:00 |
| ImageFileCharacteristics: | Executable, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 48 |
| CodeSize: | 266240 |
| InitializedDataSize: | 473088 |
| UninitializedDataSize: | - |
| EntryPoint: | 0xbc00a |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 4 |
| Subsystem: | Windows command line |
| FileVersionNumber: | 7.9.5.5 |
| ProductVersionNumber: | 7.9.5.5 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
| Comments: | idea vision moon organize system slow expand generate galaxy us.exe |
| FileDescription: | organize black refine.exe |
| FileVersion: | 7.9.5.5 |
| InternalName: | PatrickQuinnBenjamin.exejsR |
| LegalCopyright: | annihilate conceive solution database absorb (c) 2023 |
| OriginalFileName: | PatrickQuinnBenjamin.exejsR |
| ProductVersion: | 7.9.5.5 |
| AssemblyVersion: | 7.9.5.5 |
Total processes
123
Monitored processes
4
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 536 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | linksodi.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1556 | "C:\Users\admin\Desktop\linksodi.exe" | C:\Users\admin\Desktop\linksodi.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Description: organize black refine.exe Version: 7.9.5.5 Modules
| |||||||||||||||
| 4716 | "C:\Windows\Microsoft.NET\Framework\v4.0.30319\aspnet_regiis.exe" | C:\Windows\Microsoft.NET\Framework\v4.0.30319\aspnet_regiis.exe | linksodi.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: aspnet_regiis.exe Exit code: 0 Version: 4.8.9037.0 built by: NET481REL1 Modules
| |||||||||||||||
| 6116 | C:\WINDOWS\SysWOW64\WerFault.exe -u -p 1556 -s 1144 | C:\Windows\SysWOW64\WerFault.exe | linksodi.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Problem Reporting Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
9 784
Read events
9 784
Write events
0
Delete events
0
Modification events
Executable files
1
Suspicious files
0
Text files
2
Unknown types
1
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6116 | WerFault.exe | C:\ProgramData\Microsoft\Windows\WER\ReportQueue\AppCrash_linksodi.exe_aae3aa14a44804f98b1dfb1bc135594095b467_86e6a22c_6f3e56d6-3193-43a3-9482-43f249c5afc0\Report.wer | — | |
MD5:— | SHA256:— | |||
| 6116 | WerFault.exe | C:\ProgramData\Microsoft\Windows\WER\Temp\WER6584.tmp.WERInternalMetadata.xml | xml | |
MD5:E9D4289BE9096773FA2CD32E0DC18A1B | SHA256:A81580EE4B058571FA26D271B3BA5997CFFAC2F38B08CD490D9962FFA32756A4 | |||
| 1556 | linksodi.exe | C:\Users\admin\AppData\Roaming\gdi32.dll | executable | |
MD5:807D7460C40398B132FF47DE769BD0FA | SHA256:6C04D2F7906791E2768ACB07FDC5F4476DB341BF546EEC8147BAC7839A502C30 | |||
| 6116 | WerFault.exe | C:\ProgramData\Microsoft\Windows\WER\Temp\WER65C4.tmp.xml | xml | |
MD5:855EE3C1F713E5C4EFD0C1D8071C32A6 | SHA256:2154819C0C7A7ADDCECFF9E72E9880C45BD1A0F3C45EB7992FE935B964EE7EF9 | |||
| 6116 | WerFault.exe | C:\ProgramData\Microsoft\Windows\WER\Temp\WER643B.tmp.dmp | dmp | |
MD5:0A4F8ACAA1F7DCAB6C641C518591D955 | SHA256:4D6E4DFCCDBBA2C752830E75CA9718E3908C2FF02F7CA5F6F9B2E93B604961F9 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
12
TCP/UDP connections
28
DNS requests
10
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1488 | svchost.exe | GET | 200 | 23.32.238.107:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 23.32.238.107:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 23.215.121.133:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | GET | 200 | 23.215.121.133:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | POST | 200 | 188.114.96.3:443 | https://spellshagey.biz/api | unknown | text | 17 b | malicious |
— | — | POST | 200 | 188.114.97.3:443 | https://spellshagey.biz/api | unknown | text | 16.7 Kb | malicious |
— | — | POST | 200 | 188.114.96.3:443 | https://spellshagey.biz/api | unknown | text | 2 b | malicious |
— | — | POST | 200 | 188.114.96.3:443 | https://spellshagey.biz/api | unknown | text | 17 b | malicious |
— | — | POST | 200 | 188.114.97.3:443 | https://spellshagey.biz/api | unknown | text | 17 b | malicious |
— | — | POST | 200 | 188.114.96.3:443 | https://spellshagey.biz/api | unknown | text | 17 b | malicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 192.168.100.255:137 | — | — | — | whitelisted |
1488 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4712 | MoUsoCoreWorker.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 2.19.80.75:443 | www.bing.com | Akamai International B.V. | DE | whitelisted |
— | — | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4716 | aspnet_regiis.exe | 188.114.97.3:443 | spellshagey.biz | CLOUDFLARENET | NL | malicious |
6116 | WerFault.exe | 20.189.173.21:443 | watson.events.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
1488 | svchost.exe | 23.32.238.107:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
1488 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
www.bing.com |
| whitelisted |
google.com |
| whitelisted |
spellshagey.biz |
| malicious |
watson.events.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
self.events.data.microsoft.com |
| whitelisted |