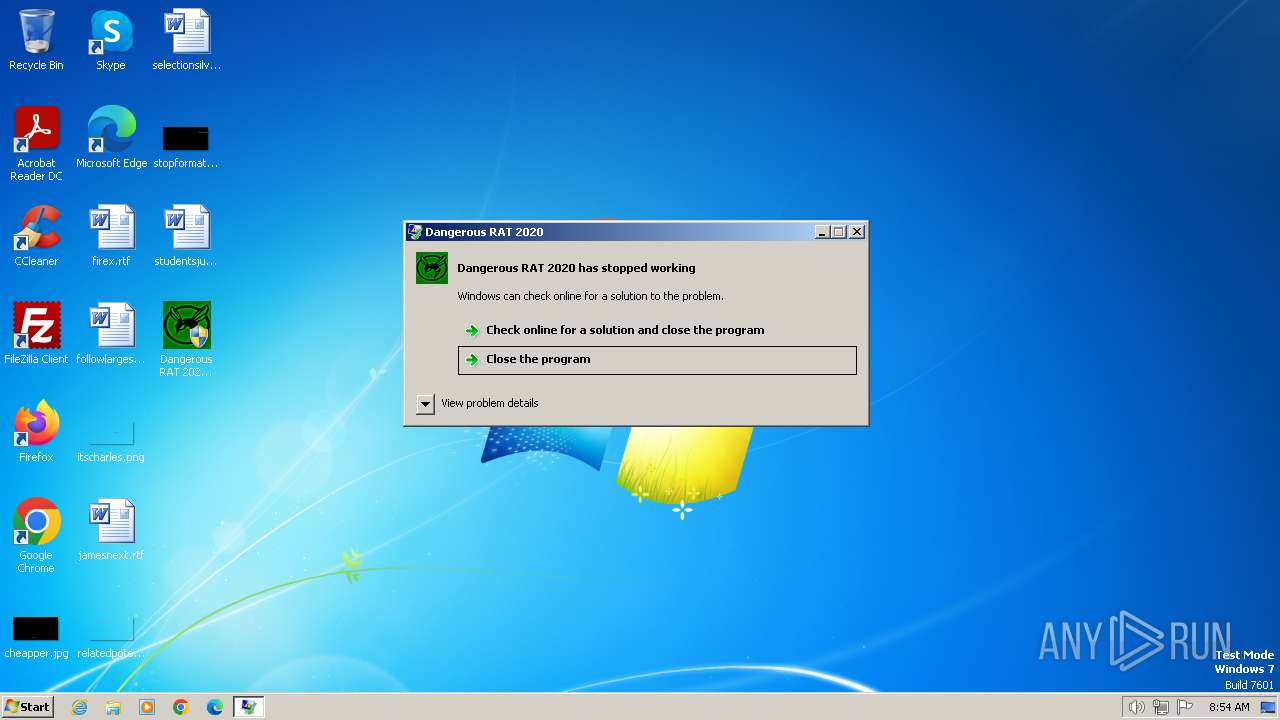
| File name: | Dangerous RAT 2020 Cracked by Unknown Venom.exe |
| Full analysis: | https://app.any.run/tasks/20eb47ad-05ce-47c4-94f2-27b917eaca2a |
| Verdict: | Malicious activity |
| Threats: | Crypto mining malware is a resource-intensive threat that infiltrates computers with the purpose of mining cryptocurrencies. This type of threat can be deployed either on an infected machine or a compromised website. In both cases the miner will utilize the computing power of the device and its network bandwidth. |
| Analysis date: | February 07, 2024, 08:54:25 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, Nullsoft Installer self-extracting archive |
| MD5: | 85A3BEE5F0A4D07474804479A2510C69 |
| SHA1: | C8C904A8B2B3FB2CAD156162A26F43461444AF77 |
| SHA256: | 2204AD2477B47B58702C87E8E0AC7BB08B0D2094D6A92B771AE2422EFB6C583F |
| SSDEEP: | 196608:4bugwpWPL7J3mHJxqJzw8mGFDAoLSk3/YLG9GYOfCZ/88x9Nl:Oug2g7J3c7qxhmGa+Sw/OGQjC2ODl |
MALICIOUS
Checks for elevated access (SCRIPT)
- wscript.exe (PID: 2556)
- wscript.exe (PID: 3040)
- wscript.exe (PID: 3548)
Drops the executable file immediately after the start
- Runtime Broker.exe (PID: 1028)
- Dangerous RAT 2020 Cracked by Unknown Venom.exe (PID: 1408)
- COM Surrogate.exe (PID: 2508)
- svchost.com (PID: 3572)
- Helper.exe (PID: 3656)
- Helper.exe (PID: 3668)
- Helper.exe (PID: 2832)
- CL_Debug_Log.txt (PID: 2536)
Creates internet connection object (SCRIPT)
- wscript.exe (PID: 2556)
- wscript.exe (PID: 3040)
- wscript.exe (PID: 3548)
Gets path to any of the special folders (SCRIPT)
- wscript.exe (PID: 2556)
- wscript.exe (PID: 3040)
- wscript.exe (PID: 3548)
Gets startup folder path (SCRIPT)
- wscript.exe (PID: 2556)
- wscript.exe (PID: 3040)
- wscript.exe (PID: 3548)
Checks whether a specified folder exists (SCRIPT)
- wscript.exe (PID: 2556)
- wscript.exe (PID: 3040)
- wscript.exe (PID: 3548)
Reads the value of a key from the registry (SCRIPT)
- wscript.exe (PID: 2556)
- wscript.exe (PID: 3040)
- wscript.exe (PID: 3548)
Accesses environment variables (SCRIPT)
- wscript.exe (PID: 2556)
- wscript.exe (PID: 3040)
- wscript.exe (PID: 3548)
Gets %appdata% folder path (SCRIPT)
- wscript.exe (PID: 2556)
- wscript.exe (PID: 3040)
- wscript.exe (PID: 3548)
Modifies registry startup key (SCRIPT)
- wscript.exe (PID: 3040)
- wscript.exe (PID: 3548)
Creates a new registry key or changes the value of an existing one (SCRIPT)
- wscript.exe (PID: 3040)
- wscript.exe (PID: 3548)
Copies file to a new location (SCRIPT)
- wscript.exe (PID: 3040)
- wscript.exe (PID: 3548)
Create files in the Startup directory
- wscript.exe (PID: 3040)
Gets a file object corresponding to the file in a specified path (SCRIPT)
- wscript.exe (PID: 3040)
- wscript.exe (PID: 3548)
Opens a text file (SCRIPT)
- wscript.exe (PID: 3548)
Opens an HTTP connection (SCRIPT)
- wscript.exe (PID: 3548)
Gets username (SCRIPT)
- wscript.exe (PID: 3548)
Sends HTTP request (SCRIPT)
- wscript.exe (PID: 3548)
Accesses information about the status of the installed antivirus(Win32_AntivirusProduct) via WMI (SCRIPT)
- wscript.exe (PID: 3548)
Actions looks like stealing of personal data
- svchost.com (PID: 3572)
- Runtime Broker.exe (PID: 1028)
Uses sleep, probably for evasion detection (SCRIPT)
- wscript.exe (PID: 3548)
Unusual connection from system programs
- wscript.exe (PID: 3548)
Looks like the application has launched a miner
- Helper.exe (PID: 3668)
MINER has been detected (SURICATA)
- attrib.exe (PID: 2248)
Connects to the CnC server
- attrib.exe (PID: 2248)
SUSPICIOUS
Reads the Internet Settings
- Dangerous RAT 2020 Cracked by Unknown Venom.exe (PID: 1408)
- Runtime Broker.exe (PID: 1028)
- wscript.exe (PID: 3040)
- wscript.exe (PID: 3548)
- Helper.exe (PID: 3668)
- Camera.exe (PID: 2796)
The process executes JS scripts
- Dangerous RAT 2020 Cracked by Unknown Venom.exe (PID: 1408)
- svchost.com (PID: 3572)
Creates FileSystem object to access computer's file system (SCRIPT)
- wscript.exe (PID: 2556)
- wscript.exe (PID: 3040)
- wscript.exe (PID: 3548)
Accesses commandline named arguments (SCRIPT)
- wscript.exe (PID: 2556)
- wscript.exe (PID: 3040)
- wscript.exe (PID: 3548)
Accesses command line arguments (SCRIPT)
- wscript.exe (PID: 2556)
- wscript.exe (PID: 3040)
- wscript.exe (PID: 3548)
Gets name of the script (SCRIPT)
- wscript.exe (PID: 2556)
- wscript.exe (PID: 3040)
- wscript.exe (PID: 3548)
Executable content was dropped or overwritten
- Runtime Broker.exe (PID: 1028)
- Dangerous RAT 2020 Cracked by Unknown Venom.exe (PID: 1408)
- svchost.com (PID: 3572)
- COM Surrogate.exe (PID: 2508)
- CL_Debug_Log.txt (PID: 2536)
- Helper.exe (PID: 3656)
- Helper.exe (PID: 3668)
- Helper.exe (PID: 2832)
Reads the BIOS version
- COM Surrogate.exe (PID: 2508)
Gets full path of the running script (SCRIPT)
- wscript.exe (PID: 3040)
- wscript.exe (PID: 3548)
Starts application with an unusual extension
- wscript.exe (PID: 3040)
- COM Surrogate.exe (PID: 2508)
- Helper.exe (PID: 3668)
- Camera.exe (PID: 2796)
Runs shell command (SCRIPT)
- wscript.exe (PID: 3040)
Checks whether the drive is ready (SCRIPT)
- wscript.exe (PID: 3548)
Gets a collection of all available drive names (SCRIPT)
- wscript.exe (PID: 3548)
Gets disk free space (SCRIPT)
- wscript.exe (PID: 3548)
Executes WMI query (SCRIPT)
- wscript.exe (PID: 3548)
Gets the drive type (SCRIPT)
- wscript.exe (PID: 3548)
Accesses current user name via WMI (SCRIPT)
- wscript.exe (PID: 3548)
Accesses WMI object, sets custom ImpersonationLevel (SCRIPT)
- wscript.exe (PID: 3548)
Accesses computer name via WMI (SCRIPT)
- wscript.exe (PID: 3548)
Accesses local storage devices (Win32_LogicalDisk) via WMI (SCRIPT)
- wscript.exe (PID: 3548)
Accesses OperatingSystem(Win32_OperatingSystem) via WMI (SCRIPT)
- wscript.exe (PID: 3548)
Accesses operating system name via WMI (SCRIPT)
- wscript.exe (PID: 3548)
Gets computer name (SCRIPT)
- wscript.exe (PID: 3548)
Accesses WMI object caption (SCRIPT)
- wscript.exe (PID: 3548)
Adds, changes, or deletes HTTP request header (SCRIPT)
- wscript.exe (PID: 3548)
Creates a Stream, which may work with files, input/output devices, pipes, or TCP/IP sockets (SCRIPT)
- wscript.exe (PID: 3548)
Reads data from a binary Stream object (SCRIPT)
- wscript.exe (PID: 3548)
Changes charset (SCRIPT)
- wscript.exe (PID: 3548)
Writes binary data to a Stream object (SCRIPT)
- wscript.exe (PID: 3548)
Drops 7-zip archiver for unpacking
- COM Surrogate.exe (PID: 2508)
Uses TIMEOUT.EXE to delay execution
- cmd.exe (PID: 3448)
The process executes via Task Scheduler
- Helper.exe (PID: 3864)
- Helper.exe (PID: 3668)
- Helper.exe (PID: 3516)
- Helper.exe (PID: 848)
- Helper.exe (PID: 2568)
- Helper.exe (PID: 2560)
Starts CMD.EXE for commands execution
- COM Surrogate.exe (PID: 2508)
Application launched itself
- Helper.exe (PID: 3668)
Starts POWERSHELL.EXE for commands execution
- Camera.exe (PID: 2796)
Connects to unusual port
- wscript.exe (PID: 3548)
- tor.exe (PID: 3304)
- attrib.exe (PID: 2248)
Checks for external IP
- wscript.exe (PID: 3548)
Drops a system driver (possible attempt to evade defenses)
- Helper.exe (PID: 2832)
Uses ATTRIB.EXE to modify file attributes
- Helper.exe (PID: 3668)
INFO
Checks supported languages
- Dangerous RAT 2020 Cracked by Unknown Venom.exe (PID: 1408)
- Runtime Broker.exe (PID: 1028)
- Camera.exe (PID: 2796)
- Dangerous RAT 2020 Cracked by Unknown Venom.exe (PID: 3016)
- COM Surrogate.exe (PID: 2508)
- svchost.com (PID: 3572)
- CL_Debug_Log.txt (PID: 2536)
- Helper.exe (PID: 3668)
- Helper.exe (PID: 3864)
- Helper.exe (PID: 3656)
- tor.exe (PID: 3304)
- svchost.com (PID: 3932)
- vlc.exe (PID: 3964)
- Helper.exe (PID: 3516)
- Helper.exe (PID: 848)
- Helper.exe (PID: 2832)
- Helper.exe (PID: 2568)
- Helper.exe (PID: 2560)
- wmpnscfg.exe (PID: 1832)
- svchost.com (PID: 4008)
Create files in a temporary directory
- Runtime Broker.exe (PID: 1028)
- Dangerous RAT 2020 Cracked by Unknown Venom.exe (PID: 1408)
- COM Surrogate.exe (PID: 2508)
- CL_Debug_Log.txt (PID: 2536)
- svchost.com (PID: 3572)
Reads the computer name
- Dangerous RAT 2020 Cracked by Unknown Venom.exe (PID: 3016)
- Runtime Broker.exe (PID: 1028)
- Camera.exe (PID: 2796)
- Dangerous RAT 2020 Cracked by Unknown Venom.exe (PID: 1408)
- COM Surrogate.exe (PID: 2508)
- CL_Debug_Log.txt (PID: 2536)
- Helper.exe (PID: 3668)
- Helper.exe (PID: 3656)
- tor.exe (PID: 3304)
- vlc.exe (PID: 3964)
- Helper.exe (PID: 2832)
- wmpnscfg.exe (PID: 1832)
Self-termination (SCRIPT)
- wscript.exe (PID: 2556)
- wscript.exe (PID: 3040)
Reads mouse settings
- COM Surrogate.exe (PID: 2508)
- Helper.exe (PID: 3516)
- Helper.exe (PID: 848)
- Helper.exe (PID: 2560)
- Helper.exe (PID: 2568)
- Helper.exe (PID: 3668)
- Helper.exe (PID: 3864)
Checks proxy server information
- wscript.exe (PID: 3548)
Creates files or folders in the user directory
- COM Surrogate.exe (PID: 2508)
- Helper.exe (PID: 3668)
- Helper.exe (PID: 3656)
- tor.exe (PID: 3304)
- Helper.exe (PID: 2832)
- Camera.exe (PID: 2796)
Reads the machine GUID from the registry
- Camera.exe (PID: 2796)
- tor.exe (PID: 3304)
- vlc.exe (PID: 3964)
The dropped object may contain a URL to Tor Browser
- Helper.exe (PID: 3656)
- Helper.exe (PID: 3668)
Dropped object may contain TOR URL's
- Helper.exe (PID: 3668)
- Helper.exe (PID: 3656)
Manual execution by a user
- wmpnscfg.exe (PID: 1832)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable MS Visual C++ (generic) (67.4) |
|---|---|---|
| .dll | | | Win32 Dynamic Link Library (generic) (14.2) |
| .exe | | | Win32 Executable (generic) (9.7) |
| .exe | | | Generic Win/DOS Executable (4.3) |
| .exe | | | DOS Executable Generic (4.3) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2015:12:27 06:38:52+01:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 6 |
| CodeSize: | 24064 |
| InitializedDataSize: | 120320 |
| UninitializedDataSize: | 1024 |
| EntryPoint: | 0x324f |
| OSVersion: | 4 |
| ImageVersion: | 6 |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
Total processes
81
Monitored processes
30
Malicious processes
10
Suspicious processes
4
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 848 | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Helper.exe -SystemCheck | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Helper.exe | — | taskeng.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 1028 | "C:\Users\admin\AppData\Local\Temp\Runtime Broker.exe" | C:\Users\admin\AppData\Local\Temp\Runtime Broker.exe | Dangerous RAT 2020 Cracked by Unknown Venom.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 1408 | "C:\Users\admin\Desktop\Dangerous RAT 2020 Cracked by Unknown Venom.exe" | C:\Users\admin\Desktop\Dangerous RAT 2020 Cracked by Unknown Venom.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 1832 | "C:\Program Files\Windows Media Player\wmpnscfg.exe" | C:\Program Files\Windows Media Player\wmpnscfg.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Media Player Network Sharing Service Configuration Application Exit code: 0 Version: 12.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2248 | -a RandomX -o stratum+tcp://xmrpool.eu:3333 -u 42LWroKkaot7k6VU59vZyz7kxmhQGgWJhfdrEhV5GBkQ1Q6DqNRmoDALTM4PoM5n2JcS4t4wYDXTfWR8oyM8XfQhQxXhvdU -p x -t 2 | C:\Windows\System32\attrib.exe | Helper.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Attribute Utility Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2508 | "C:\Users\admin\AppData\Local\Temp\COM Surrogate.exe" | C:\Users\admin\AppData\Local\Temp\COM Surrogate.exe | Dangerous RAT 2020 Cracked by Unknown Venom.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 2536 | C:\Users\admin\AppData\Local\Temp\CL_Debug_Log.txt e -p"JDQJndnqwdnqw2139dn21n3b312idDQDB" "C:\Users\admin\AppData\Local\Temp\CR_Debug_Log.txt" -o"C:\Users\admin\AppData\Local\Temp\" | C:\Users\admin\AppData\Local\Temp\CL_Debug_Log.txt | COM Surrogate.exe | ||||||||||||
User: admin Company: Igor Pavlov Integrity Level: HIGH Description: 7-Zip Standalone Console Exit code: 0 Version: 19.00 Modules
| |||||||||||||||
| 2556 | "C:\Windows\System32\WScript.exe" "C:\Users\admin\AppData\Local\Temp\Sound.js" | C:\Windows\System32\wscript.exe | — | Dangerous RAT 2020 Cracked by Unknown Venom.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft ® Windows Based Script Host Exit code: 0 Version: 5.8.7600.16385 Modules
| |||||||||||||||
| 2560 | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Helper.exe -SystemCheck | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Helper.exe | — | taskeng.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 2568 | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Helper.exe -SystemCheck | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Helper.exe | — | taskeng.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
Total events
5 989
Read events
5 900
Write events
89
Delete events
0
Modification events
| (PID) Process: | (1408) Dangerous RAT 2020 Cracked by Unknown Venom.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (1408) Dangerous RAT 2020 Cracked by Unknown Venom.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (1408) Dangerous RAT 2020 Cracked by Unknown Venom.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (1408) Dangerous RAT 2020 Cracked by Unknown Venom.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (1028) Runtime Broker.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (1028) Runtime Broker.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (1028) Runtime Broker.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (1028) Runtime Broker.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (3040) wscript.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (3040) wscript.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
Executable files
67
Suspicious files
8
Text files
25
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1408 | Dangerous RAT 2020 Cracked by Unknown Venom.exe | C:\Users\admin\AppData\Local\Temp\nsk5EBF.tmp | — | |
MD5:— | SHA256:— | |||
| 1028 | Runtime Broker.exe | C:\Windows\svchost.com | executable | |
MD5:36FD5E09C417C767A952B4609D73A54B | SHA256:980BAC6C9AFE8EFC9C6FE459A5F77213B0D8524EB00DE82437288EB96138B9A2 | |||
| 1408 | Dangerous RAT 2020 Cracked by Unknown Venom.exe | C:\Users\admin\AppData\Local\Temp\COM Surrogate.exe | executable | |
MD5:5839FB085C72CFC7015D2EE9C8908DE4 | SHA256:FF78908DFF76001CCBE16D0C52D486BA699621A0299A0AD3DB8655DC31B5C145 | |||
| 1408 | Dangerous RAT 2020 Cracked by Unknown Venom.exe | C:\Users\admin\AppData\Local\Temp\Sound.js | text | |
MD5:0BFD65241852C649635C90DD2344867F | SHA256:4B44A962C5F45E87884342C7E7C0DB1B168E3696894FE46D14048E803FEE8C3E | |||
| 3572 | svchost.com | C:\MSOCache\All Users\{90140000-006E-0410-0000-0000000FF1CE}-C\DW20.EXE | executable | |
MD5:02EE6A3424782531461FB2F10713D3C1 | SHA256:EAD58C483CB20BCD57464F8A4929079539D634F469B213054BF737D227C026DC | |||
| 1408 | Dangerous RAT 2020 Cracked by Unknown Venom.exe | C:\Users\admin\AppData\Local\Temp\Camera.exe | executable | |
MD5:A44F1B06D351B36E43AB10FB43922ED4 | SHA256:622FAAF7A1652F3F988312DD024FABCB51DDE490EE2B9A18113EB399C472E61B | |||
| 3040 | wscript.exe | C:\Users\admin\AppData\Roaming\VideoUI.js | text | |
MD5:99D3FCB737ED9BB3071A240B995F5C41 | SHA256:8276599D057E7892F4C0C6D70E0FF754469DDD82F71900202CEFF485BB128058 | |||
| 1028 | Runtime Broker.exe | C:\MSOCache\All Users\{90140000-003D-0000-0000-0000000FF1CE}-C\setup.exe | executable | |
MD5:566ED4F62FDC96F175AFEDD811FA0370 | SHA256:E17CD94C08FC0E001A49F43A0801CEA4625FB9AEE211B6DFEBEBEC446C21F460 | |||
| 3040 | wscript.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\VideoUI.js | text | |
MD5:99D3FCB737ED9BB3071A240B995F5C41 | SHA256:8276599D057E7892F4C0C6D70E0FF754469DDD82F71900202CEFF485BB128058 | |||
| 3572 | svchost.com | C:\MSOCache\All Users\{90140000-006E-0407-0000-0000000FF1CE}-C\dwtrig20.exe | executable | |
MD5:CF6C595D3E5E9667667AF096762FD9C4 | SHA256:593E60CC30AE0789448547195AF77F550387F6648D45847EA244DD0DD7ABF03D | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
1
TCP/UDP connections
22
DNS requests
4
Threats
13
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3548 | wscript.exe | GET | 200 | 208.95.112.1:80 | http://ip-api.com/json/ | unknown | binary | 293 b | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
3548 | wscript.exe | 208.95.112.1:80 | ip-api.com | TUT-AS | US | unknown |
3548 | wscript.exe | 194.132.123.111:8000 | redlan.linkpc.net | PVDataNet AB | IN | unknown |
3304 | tor.exe | 172.98.193.43:443 | — | DACEN-2 | US | unknown |
3304 | tor.exe | 185.220.101.32:20032 | — | Zwiebelfreunde e.V. | DE | unknown |
3304 | tor.exe | 37.120.174.249:443 | — | netcup GmbH | DE | unknown |
3304 | tor.exe | 85.214.212.219:9010 | — | Strato AG | DE | unknown |
3304 | tor.exe | 179.43.182.16:9001 | — | Private Layer INC | CH | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
ip-api.com |
| shared |
redlan.linkpc.net |
| unknown |
xmrpool.eu |
| unknown |
fee.ssl.xexi.xyz |
| unknown |
Threats
PID | Process | Class | Message |
|---|---|---|---|
3548 | wscript.exe | Potential Corporate Privacy Violation | AV POLICY Internal Host Retrieving External IP Address (ip-api. com) |
3548 | wscript.exe | Device Retrieving External IP Address Detected | ET POLICY External IP Lookup ip-api.com |
1080 | svchost.exe | Potentially Bad Traffic | ET INFO Observed DNS Query to DynDNS Domain (linkpc .net) |
3304 | tor.exe | Misc Attack | ET TOR Known Tor Exit Node Traffic group 43 |
3304 | tor.exe | Misc Attack | ET TOR Known Tor Relay/Router (Not Exit) Node Traffic group 43 |
3304 | tor.exe | Misc Attack | ET TOR Known Tor Relay/Router (Not Exit) Node Traffic group 638 |
3304 | tor.exe | Misc Attack | ET TOR Known Tor Relay/Router (Not Exit) Node Traffic group 794 |
3304 | tor.exe | Misc Attack | ET TOR Known Tor Relay/Router (Not Exit) Node Traffic group 257 |
3304 | tor.exe | Misc activity | ET POLICY TLS possible TOR SSL traffic |
3304 | tor.exe | Misc activity | ET POLICY TLS possible TOR SSL traffic |