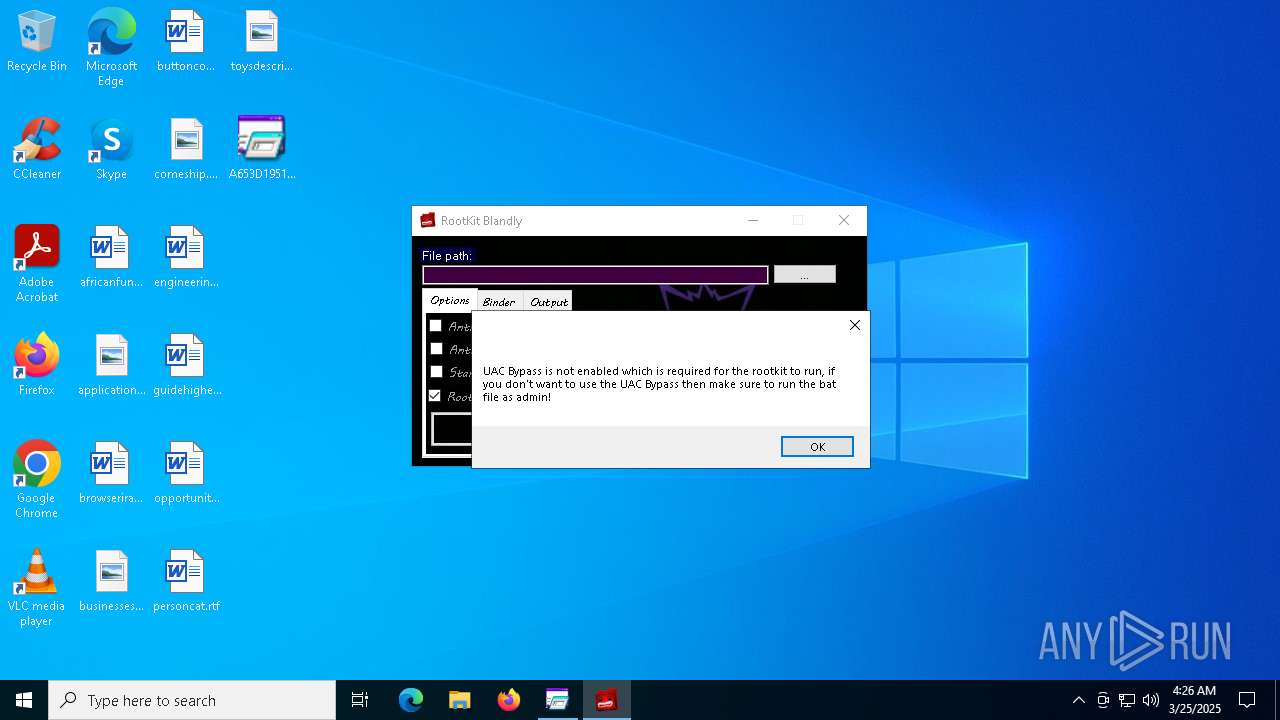
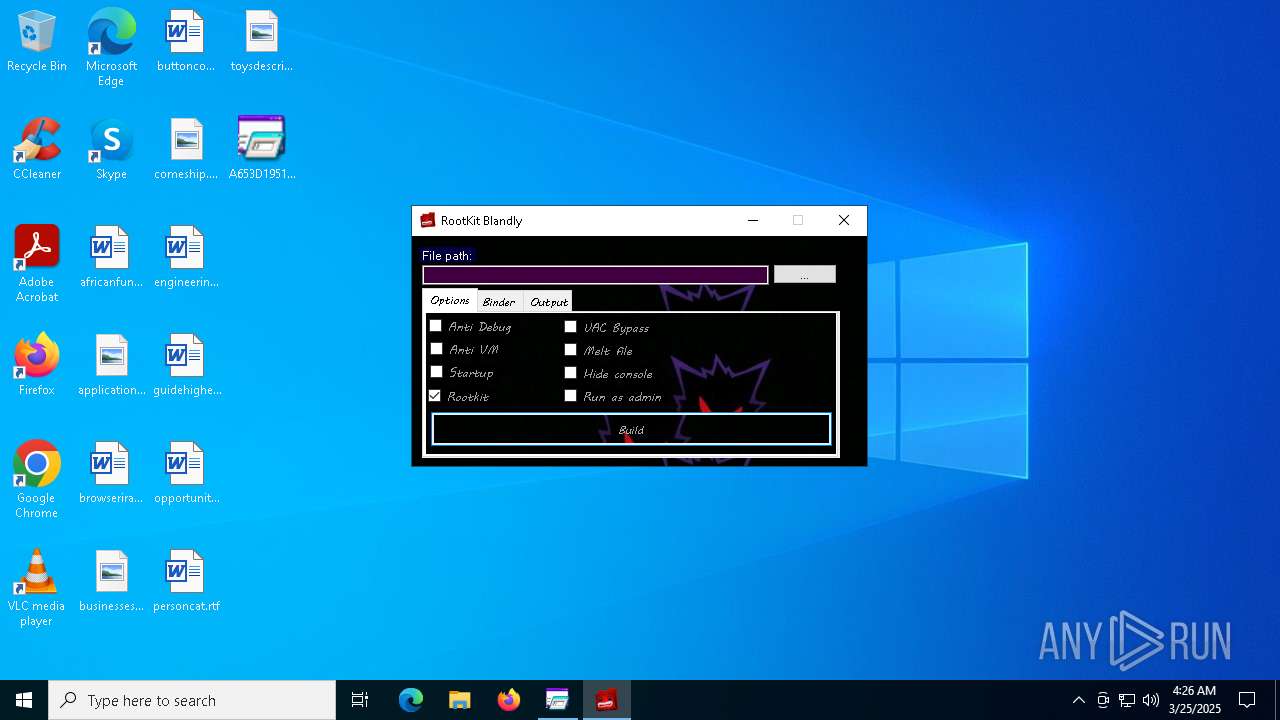
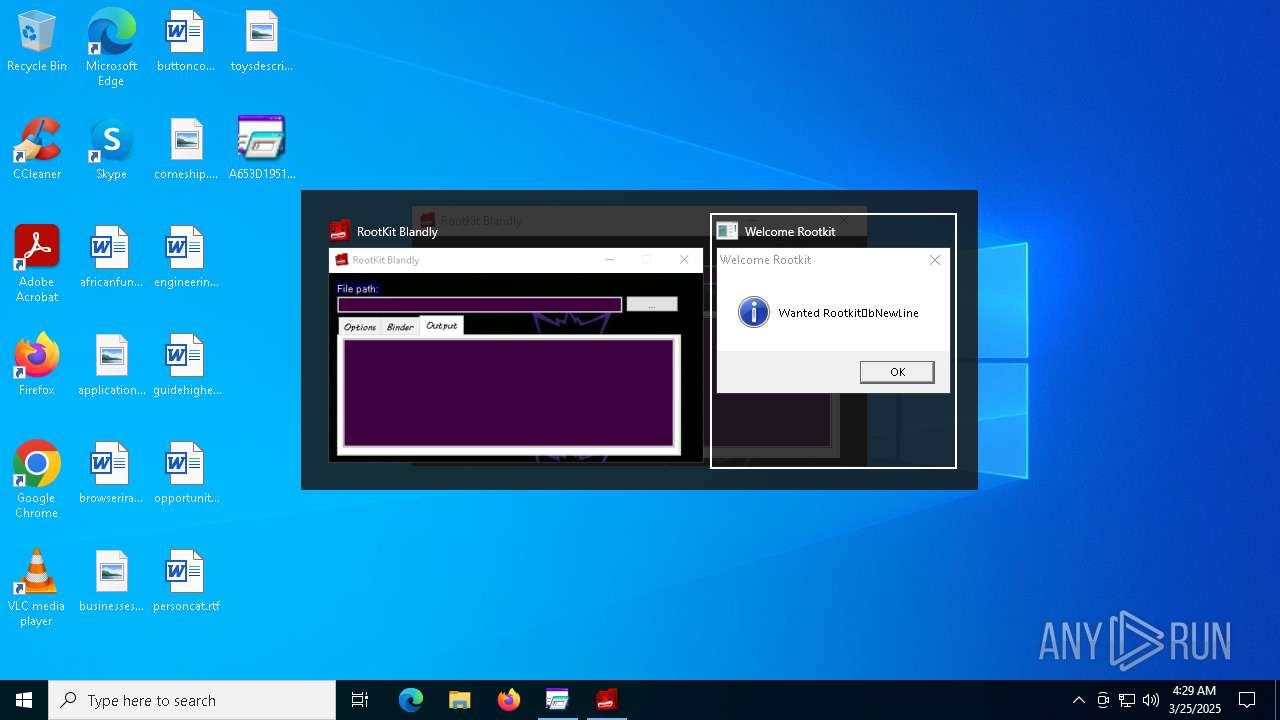
| File name: | A653D1951B3DE7E0EDE77758187763B0.exe |
| Full analysis: | https://app.any.run/tasks/81b18adf-6e20-4ea2-901f-745879845d5e |
| Verdict: | Malicious activity |
| Threats: | NanoCore is a Remote Access Trojan or RAT. This malware is highly customizable with plugins which allow attackers to tailor its functionality to their needs. Nanocore is created with the .NET framework and it’s available for purchase for just $25 from its “official” website. |
| Analysis date: | March 25, 2025, 04:25:48 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386 Mono/.Net assembly, for MS Windows, 3 sections |
| MD5: | A653D1951B3DE7E0EDE77758187763B0 |
| SHA1: | 06DF3427AA544488543152111F5C5CFC52D41463 |
| SHA256: | 21F3851DF5C3487B850C88275818072EB000857423F72608B0708B53BB3BBF64 |
| SSDEEP: | 98304:I6bXDBsQZa9fvSrpBZuYAtmN+KQ9QiD5AeT8WJz+jyaKaFE5FUgNWz+0LEmc3UOC:L0IY |
MALICIOUS
NANOCORE has been detected (YARA)
- 3377.exe (PID: 7248)
- ksmj.ddns.net.exe (PID: 7256)
NANOCORE has been detected (SURICATA)
- 3377.exe (PID: 7248)
Connects to the CnC server
- 3377.exe (PID: 7248)
SUSPICIOUS
Reads security settings of Internet Explorer
- A653D1951B3DE7E0EDE77758187763B0.exe (PID: 5216)
- A653D1951B3DE7E0EDE77758187763B0.exe (PID: 728)
- R00tkit Blandly.exe (PID: 7280)
- A653D1951B3DE7E0EDE77758187763B0.exe (PID: 7452)
Reads the date of Windows installation
- A653D1951B3DE7E0EDE77758187763B0.exe (PID: 5216)
- A653D1951B3DE7E0EDE77758187763B0.exe (PID: 728)
- R00tkit Blandly.exe (PID: 7280)
- A653D1951B3DE7E0EDE77758187763B0.exe (PID: 7452)
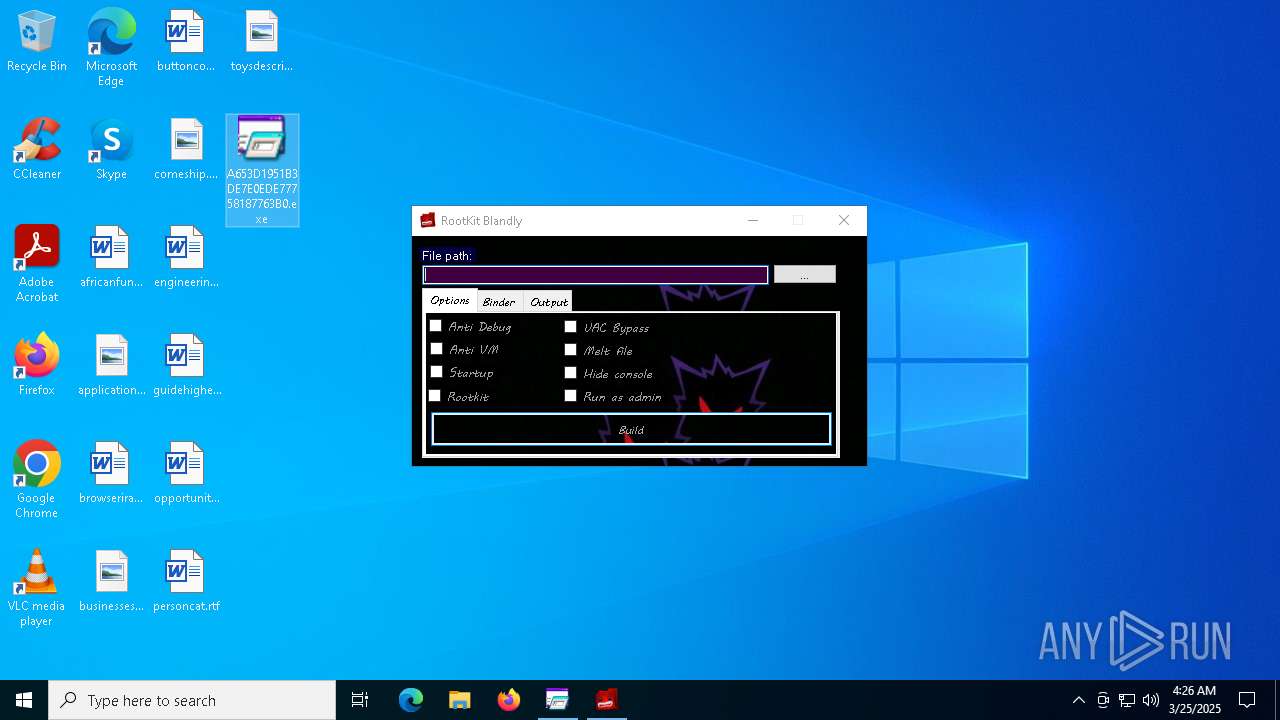
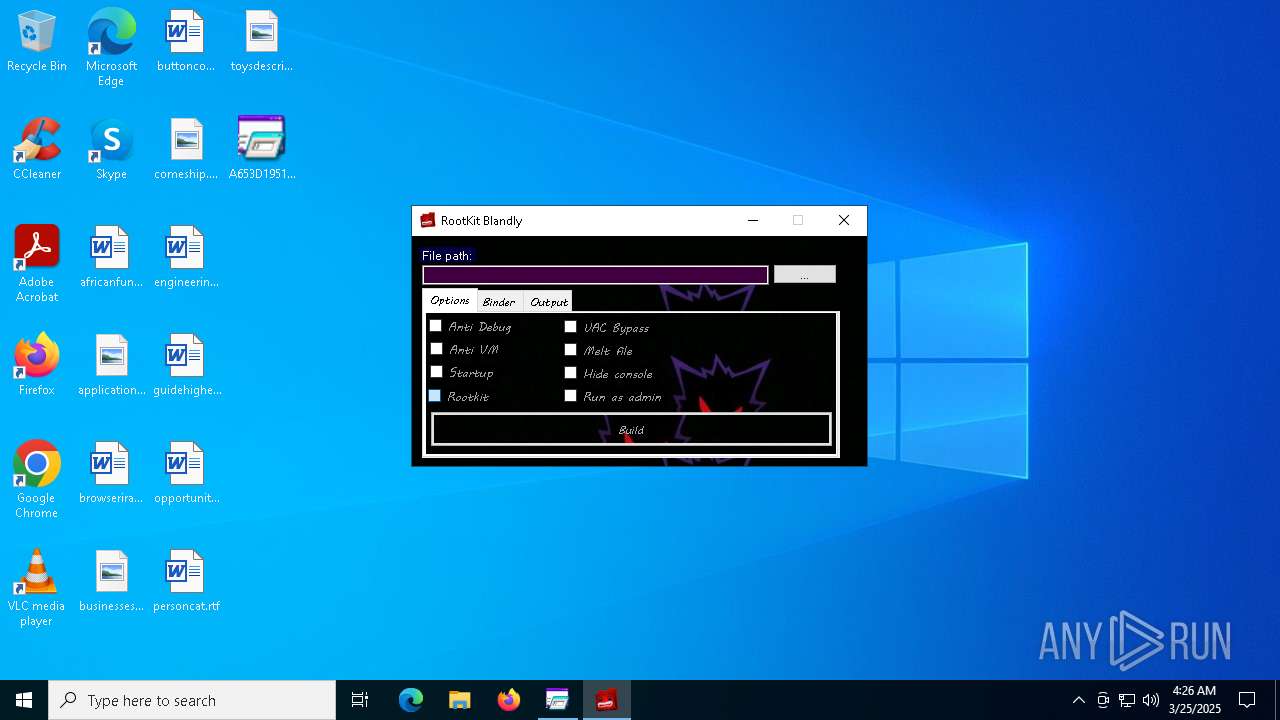
Executable content was dropped or overwritten
- A653D1951B3DE7E0EDE77758187763B0.exe (PID: 5216)
- R00tkit Blandly.exe (PID: 7280)
Connects to unusual port
- 3377.exe (PID: 7248)
- ksmj.ddns.net.exe (PID: 7256)
Contacting a server suspected of hosting an CnC
- 3377.exe (PID: 7248)
INFO
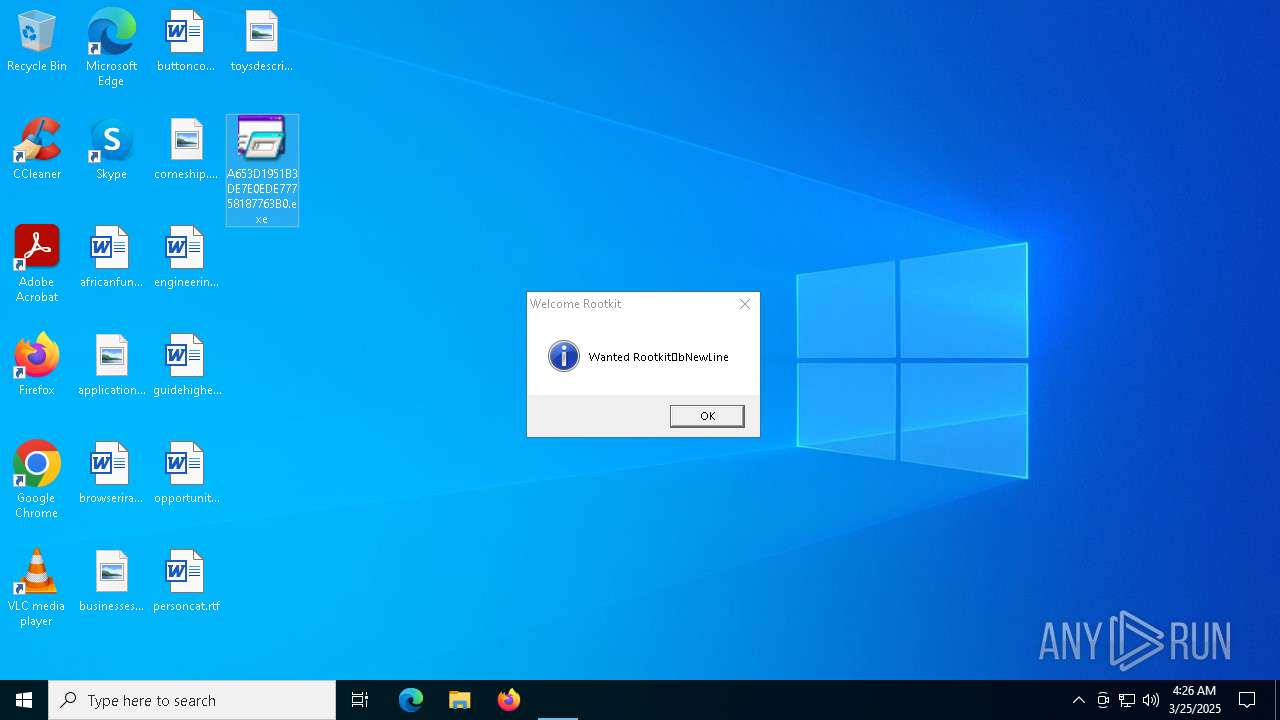
Manual execution by a user
- A653D1951B3DE7E0EDE77758187763B0.exe (PID: 728)
- A653D1951B3DE7E0EDE77758187763B0.exe (PID: 7452)
Checks supported languages
- A653D1951B3DE7E0EDE77758187763B0.exe (PID: 5216)
- ksmj.ddns.net.exe (PID: 7256)
- 3377.exe (PID: 7248)
- A653D1951B3DE7E0EDE77758187763B0.exe (PID: 7452)
- 3377.exe (PID: 7532)
- ksmj.ddns.net.exe (PID: 7552)
- A653D1951B3DE7E0EDE77758187763B0.exe (PID: 728)
- R00tkit Blandly.exe (PID: 7584)
- Blandly Rootkit.exe (PID: 7744)
- R00tkit Blandly.exe (PID: 7280)
- R00tkit Blandly.exe (PID: 6700)
- 3377.exe (PID: 7288)
- ksmj.ddns.net.exe (PID: 3896)
Create files in a temporary directory
- A653D1951B3DE7E0EDE77758187763B0.exe (PID: 5216)
- R00tkit Blandly.exe (PID: 7280)
- Blandly Rootkit.exe (PID: 7744)
Reads the computer name
- A653D1951B3DE7E0EDE77758187763B0.exe (PID: 5216)
- A653D1951B3DE7E0EDE77758187763B0.exe (PID: 728)
- R00tkit Blandly.exe (PID: 7280)
- 3377.exe (PID: 7248)
- ksmj.ddns.net.exe (PID: 7256)
- A653D1951B3DE7E0EDE77758187763B0.exe (PID: 7452)
- R00tkit Blandly.exe (PID: 7584)
- Blandly Rootkit.exe (PID: 7744)
- R00tkit Blandly.exe (PID: 6700)
- 3377.exe (PID: 7532)
- ksmj.ddns.net.exe (PID: 7552)
- 3377.exe (PID: 7288)
- ksmj.ddns.net.exe (PID: 3896)
Reads the machine GUID from the registry
- A653D1951B3DE7E0EDE77758187763B0.exe (PID: 5216)
- 3377.exe (PID: 7248)
- ksmj.ddns.net.exe (PID: 7256)
- A653D1951B3DE7E0EDE77758187763B0.exe (PID: 728)
- 3377.exe (PID: 7532)
- ksmj.ddns.net.exe (PID: 7552)
- R00tkit Blandly.exe (PID: 7280)
- Blandly Rootkit.exe (PID: 7744)
- A653D1951B3DE7E0EDE77758187763B0.exe (PID: 7452)
- 3377.exe (PID: 7288)
- ksmj.ddns.net.exe (PID: 3896)
Process checks computer location settings
- A653D1951B3DE7E0EDE77758187763B0.exe (PID: 5216)
- A653D1951B3DE7E0EDE77758187763B0.exe (PID: 728)
- R00tkit Blandly.exe (PID: 7280)
- A653D1951B3DE7E0EDE77758187763B0.exe (PID: 7452)
Process checks whether UAC notifications are on
- 3377.exe (PID: 7248)
- ksmj.ddns.net.exe (PID: 7256)
Creates files or folders in the user directory
- ksmj.ddns.net.exe (PID: 7256)
Reads Environment values
- Blandly Rootkit.exe (PID: 7744)
Disables trace logs
- Blandly Rootkit.exe (PID: 7744)
Checks proxy server information
- Blandly Rootkit.exe (PID: 7744)
- slui.exe (PID: 8128)
Reads the software policy settings
- Blandly Rootkit.exe (PID: 7744)
- slui.exe (PID: 7664)
- slui.exe (PID: 8128)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Nanocore
(PID) Process(7248) 3377.exe
BuildTime2025-03-11 20:35:10.091792
Version1.2.2.0
Mutexf761c1a4-b3fc-47bd-8557-06047cdf0973
DefaultGroupDefault
PrimaryConnectionHost
BackupConnectionHostksmj.ddns.net
ConnectionPort5552
RunOnStartupFalse
RequestElevationFalse
BypassUserAccountControlFalse
ClearZoneIdentifierTrue
ClearAccessControlFalse
SetCriticalProcessFalse
PreventSystemSleepTrue
ActivateAwayModeFalse
EnableDebugModeFalse
RunDelay0
ConnectDelay4000
RestartDelay5000
TimeoutInterval5000
KeepAliveTimeout30000
MutexTimeout5000
LanTimeout2500
WanTimeout8000
BufferSize65535
MaxPacketSize10485760
GCThreshold10485760
UseCustomDnsServerTrue
PrimaryDnsServer8.8.8.8
BackupDnsServer8.8.4.4
(PID) Process(7256) ksmj.ddns.net.exe
BuildTime2025-03-11 19:29:43.766992
Version1.2.2.0
Mutexb73dccc0-ae28-411e-8f12-dcb30e5628a2
DefaultGroupDefault
PrimaryConnectionHostksmj.ddns.net
BackupConnectionHostksmj.ddns.net
ConnectionPort1337
RunOnStartupFalse
RequestElevationFalse
BypassUserAccountControlFalse
ClearZoneIdentifierTrue
ClearAccessControlFalse
SetCriticalProcessFalse
PreventSystemSleepTrue
ActivateAwayModeFalse
EnableDebugModeFalse
RunDelay0
ConnectDelay4000
RestartDelay5000
TimeoutInterval5000
KeepAliveTimeout30000
MutexTimeout5000
LanTimeout2500
WanTimeout8000
BufferSize65535
MaxPacketSize10485760
GCThreshold10485760
UseCustomDnsServerTrue
PrimaryDnsServer8.8.8.8
BackupDnsServer8.8.4.4
TRiD
| .exe | | | Generic CIL Executable (.NET, Mono, etc.) (63.1) |
|---|---|---|
| .exe | | | Win64 Executable (generic) (23.8) |
| .dll | | | Win32 Dynamic Link Library (generic) (5.6) |
| .exe | | | Win32 Executable (generic) (3.8) |
| .exe | | | Generic Win/DOS Executable (1.7) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2025:03:11 20:37:02+00:00 |
| ImageFileCharacteristics: | Executable, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 11 |
| CodeSize: | 3130368 |
| InitializedDataSize: | 7680 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x2fe23e |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 1.0.0.0 |
| ProductVersionNumber: | 1.0.0.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
| FileDescription: | |
| FileVersion: | 1.0.0.0 |
| InternalName: | R00tkit.exe |
| LegalCopyright: | |
| OriginalFileName: | R00tkit.exe |
| ProductVersion: | 1.0.0.0 |
| AssemblyVersion: | 1.0.0.0 |
Total processes
155
Monitored processes
16
Malicious processes
3
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 728 | "C:\Users\admin\Desktop\A653D1951B3DE7E0EDE77758187763B0.exe" | C:\Users\admin\Desktop\A653D1951B3DE7E0EDE77758187763B0.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
| 3896 | "C:\Users\admin\AppData\Local\Temp\ksmj.ddns.net.exe" | C:\Users\admin\AppData\Local\Temp\ksmj.ddns.net.exe | — | A653D1951B3DE7E0EDE77758187763B0.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 5216 | "C:\Users\admin\Desktop\A653D1951B3DE7E0EDE77758187763B0.exe" | C:\Users\admin\Desktop\A653D1951B3DE7E0EDE77758187763B0.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Description: Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
| 6700 | "C:\Users\admin\AppData\Local\Temp\R00tkit Blandly.exe" | C:\Users\admin\AppData\Local\Temp\R00tkit Blandly.exe | — | A653D1951B3DE7E0EDE77758187763B0.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
| 7248 | "C:\Users\admin\AppData\Local\Temp\3377.exe" | C:\Users\admin\AppData\Local\Temp\3377.exe | A653D1951B3DE7E0EDE77758187763B0.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Modules
Nanocore(PID) Process(7248) 3377.exe BuildTime2025-03-11 20:35:10.091792 Version1.2.2.0 Mutexf761c1a4-b3fc-47bd-8557-06047cdf0973 DefaultGroupDefault PrimaryConnectionHost BackupConnectionHostksmj.ddns.net ConnectionPort5552 RunOnStartupFalse RequestElevationFalse BypassUserAccountControlFalse ClearZoneIdentifierTrue ClearAccessControlFalse SetCriticalProcessFalse PreventSystemSleepTrue ActivateAwayModeFalse EnableDebugModeFalse RunDelay0 ConnectDelay4000 RestartDelay5000 TimeoutInterval5000 KeepAliveTimeout30000 MutexTimeout5000 LanTimeout2500 WanTimeout8000 BufferSize65535 MaxPacketSize10485760 GCThreshold10485760 UseCustomDnsServerTrue PrimaryDnsServer8.8.8.8 BackupDnsServer8.8.4.4 | |||||||||||||||
| 7256 | "C:\Users\admin\AppData\Local\Temp\ksmj.ddns.net.exe" | C:\Users\admin\AppData\Local\Temp\ksmj.ddns.net.exe | A653D1951B3DE7E0EDE77758187763B0.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Modules
Nanocore(PID) Process(7256) ksmj.ddns.net.exe BuildTime2025-03-11 19:29:43.766992 Version1.2.2.0 Mutexb73dccc0-ae28-411e-8f12-dcb30e5628a2 DefaultGroupDefault PrimaryConnectionHostksmj.ddns.net BackupConnectionHostksmj.ddns.net ConnectionPort1337 RunOnStartupFalse RequestElevationFalse BypassUserAccountControlFalse ClearZoneIdentifierTrue ClearAccessControlFalse SetCriticalProcessFalse PreventSystemSleepTrue ActivateAwayModeFalse EnableDebugModeFalse RunDelay0 ConnectDelay4000 RestartDelay5000 TimeoutInterval5000 KeepAliveTimeout30000 MutexTimeout5000 LanTimeout2500 WanTimeout8000 BufferSize65535 MaxPacketSize10485760 GCThreshold10485760 UseCustomDnsServerTrue PrimaryDnsServer8.8.8.8 BackupDnsServer8.8.4.4 | |||||||||||||||
| 7280 | "C:\Users\admin\AppData\Local\Temp\R00tkit Blandly.exe" | C:\Users\admin\AppData\Local\Temp\R00tkit Blandly.exe | A653D1951B3DE7E0EDE77758187763B0.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Description: Version: 1.0.0.0 Modules
| |||||||||||||||
| 7288 | "C:\Users\admin\AppData\Local\Temp\3377.exe" | C:\Users\admin\AppData\Local\Temp\3377.exe | — | A653D1951B3DE7E0EDE77758187763B0.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 7452 | "C:\Users\admin\Desktop\A653D1951B3DE7E0EDE77758187763B0.exe" | C:\Users\admin\Desktop\A653D1951B3DE7E0EDE77758187763B0.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
| 7532 | "C:\Users\admin\AppData\Local\Temp\3377.exe" | C:\Users\admin\AppData\Local\Temp\3377.exe | — | A653D1951B3DE7E0EDE77758187763B0.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
Total events
5 703
Read events
5 689
Write events
14
Delete events
0
Modification events
| (PID) Process: | (7744) Blandly Rootkit.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\Blandly Rootkit_RASAPI32 |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
| (PID) Process: | (7744) Blandly Rootkit.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\Blandly Rootkit_RASAPI32 |
| Operation: | write | Name: | EnableAutoFileTracing |
Value: 0 | |||
| (PID) Process: | (7744) Blandly Rootkit.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\Blandly Rootkit_RASAPI32 |
| Operation: | write | Name: | EnableConsoleTracing |
Value: 0 | |||
| (PID) Process: | (7744) Blandly Rootkit.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\Blandly Rootkit_RASAPI32 |
| Operation: | write | Name: | FileTracingMask |
Value: | |||
| (PID) Process: | (7744) Blandly Rootkit.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\Blandly Rootkit_RASAPI32 |
| Operation: | write | Name: | ConsoleTracingMask |
Value: | |||
| (PID) Process: | (7744) Blandly Rootkit.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\Blandly Rootkit_RASAPI32 |
| Operation: | write | Name: | MaxFileSize |
Value: 1048576 | |||
| (PID) Process: | (7744) Blandly Rootkit.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\Blandly Rootkit_RASAPI32 |
| Operation: | write | Name: | FileDirectory |
Value: %windir%\tracing | |||
| (PID) Process: | (7744) Blandly Rootkit.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\Blandly Rootkit_RASMANCS |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
| (PID) Process: | (7744) Blandly Rootkit.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\Blandly Rootkit_RASMANCS |
| Operation: | write | Name: | EnableAutoFileTracing |
Value: 0 | |||
| (PID) Process: | (7744) Blandly Rootkit.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\Blandly Rootkit_RASMANCS |
| Operation: | write | Name: | EnableConsoleTracing |
Value: 0 | |||
Executable files
4
Suspicious files
0
Text files
2
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 5216 | A653D1951B3DE7E0EDE77758187763B0.exe | C:\Users\admin\AppData\Local\Temp\3377.exe | executable | |
MD5:0E013A4DB9F8352623A4EAA401D1911D | SHA256:0AFBFA4A8F94EF9204F6E19B8E65BB68A74795745F2D8C996AFFFAA44F4A2908 | |||
| 5216 | A653D1951B3DE7E0EDE77758187763B0.exe | C:\Users\admin\AppData\Local\Temp\ksmj.ddns.net.exe | executable | |
MD5:E2557F03A5D4DE545313BA77DE25139E | SHA256:CFD8EE211B76DB67B79ED33DDCE0BC60EC697E8E1E1162A02543188587760B56 | |||
| 7280 | R00tkit Blandly.exe | C:\Users\admin\AppData\Local\Temp\Blandly Rootkit.exe | executable | |
MD5:302E8CD3926E071313C59CB2AD1D1D79 | SHA256:984360F867C1891F7EA6293AC2F72907321D1BCC4E68184327DAD522744C97A5 | |||
| 5216 | A653D1951B3DE7E0EDE77758187763B0.exe | C:\Users\admin\AppData\Local\Temp\R00tkit Blandly.exe | executable | |
MD5:B66E88BA098DA4D287B2DD99F69D14EF | SHA256:105FEE6FB5D6119C586844D5B7CEAA27B86C8ACE1B8C2C30EAEA51EB55C7B115 | |||
| 7256 | ksmj.ddns.net.exe | C:\Users\admin\AppData\Roaming\BB926E54-E3CA-40FD-AE90-2764341E7792\run.dat | text | |
MD5:10E365641CCC26C1366F43332644D311 | SHA256:3324DA80DB33AF5DFD57998C2A6C88A9D41E219420D5C16F93A972A48A8C640E | |||
| 7744 | Blandly Rootkit.exe | C:\Users\admin\AppData\Local\Temp\bin\latestversion | text | |
MD5:F619991470DF8B3A8AD907BE8BC5FBD4 | SHA256:7F98E71C92F0055050A542C8A53E348320C6812CBFE33C12C53C1B153080A2B8 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
6
TCP/UDP connections
265
DNS requests
98
Threats
120
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5496 | MoUsoCoreWorker.exe | GET | 200 | 23.53.40.178:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
2104 | svchost.exe | GET | 200 | 23.53.40.178:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
7172 | backgroundTaskHost.exe | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
7528 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
7528 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5496 | MoUsoCoreWorker.exe | 23.53.40.178:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
2104 | svchost.exe | 23.53.40.178:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
5496 | MoUsoCoreWorker.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
3216 | svchost.exe | 40.113.103.199:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6544 | svchost.exe | 40.126.32.138:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6544 | svchost.exe | 184.30.131.245:80 | ocsp.digicert.com | AKAMAI-AS | US | whitelisted |
5404 | RUXIMICS.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
7256 | ksmj.ddns.net.exe | 169.150.202.83:1337 | ksmj.ddns.net | Datacamp Limited | IL | malicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
ksmj.ddns.net |
| malicious |
raw.githubusercontent.com |
| whitelisted |
arc.msn.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
7248 | 3377.exe | Potentially Bad Traffic | ET DYN_DNS DNS Query to DynDNS Domain *.ddns .net |
7256 | ksmj.ddns.net.exe | Potentially Bad Traffic | ET DYN_DNS DNS Query to DynDNS Domain *.ddns .net |
7248 | 3377.exe | Malware Command and Control Activity Detected | ET MALWARE NanoCore RAT CnC 7 |
2196 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Attempting to access raw user content on GitHub |
7256 | ksmj.ddns.net.exe | Potentially Bad Traffic | ET DYN_DNS DNS Query to DynDNS Domain *.ddns .net |
7248 | 3377.exe | Potentially Bad Traffic | ET DYN_DNS DNS Query to DynDNS Domain *.ddns .net |
7248 | 3377.exe | Malware Command and Control Activity Detected | ET MALWARE NanoCore RAT CnC 7 |
7256 | ksmj.ddns.net.exe | Potentially Bad Traffic | ET DYN_DNS DNS Query to DynDNS Domain *.ddns .net |
7248 | 3377.exe | Potentially Bad Traffic | ET DYN_DNS DNS Query to DynDNS Domain *.ddns .net |
7248 | 3377.exe | Malware Command and Control Activity Detected | ET MALWARE NanoCore RAT CnC 7 |