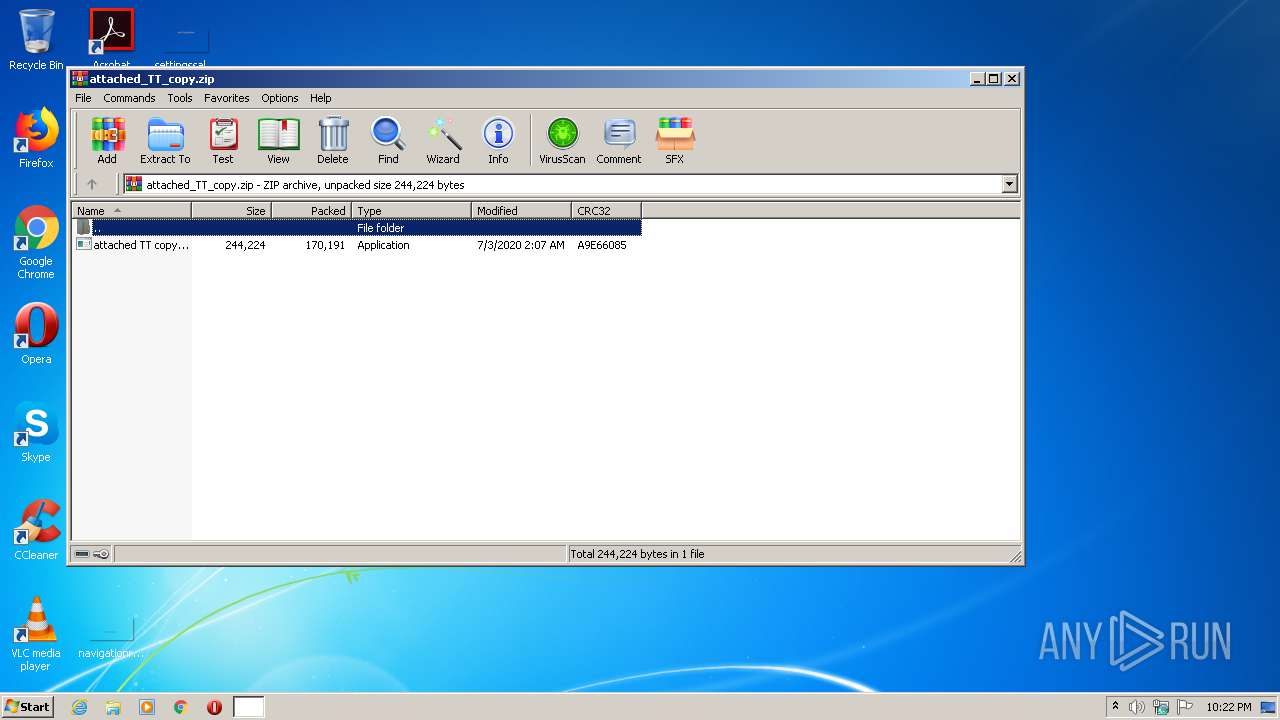
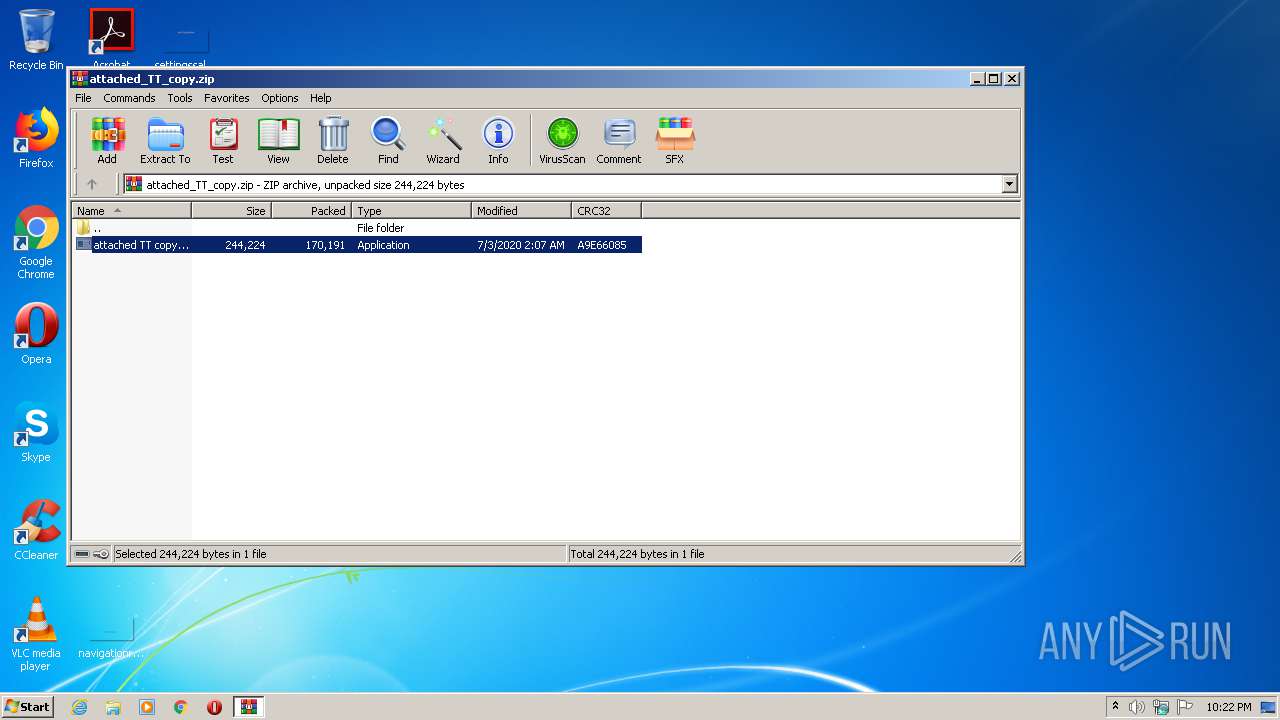
| File name: | attached_TT_copy.zip |
| Full analysis: | https://app.any.run/tasks/fe8daac3-674c-44dc-9802-5745829593e1 |
| Verdict: | Malicious activity |
| Threats: | LokiBot was developed in 2015 to steal information from a variety of applications. Despite the age, this malware is still rather popular among cybercriminals. |
| Analysis date: | July 12, 2020, 21:22:28 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract |
| MD5: | 4D0E01A7A16A732D6C461C313F126BCB |
| SHA1: | 64CE4C2A36DAF9D725BAAA9CC10EBDB42D0CC081 |
| SHA256: | 213FC1CC70DFBBCDA91291DCEF4C2A8F80E3EB25E9BC5059596BD551955651BD |
| SSDEEP: | 3072:cufdsYFxJUgHD02oWcQMLy+yo5DxCf3aLvB0aRkY019+qzZswEmS:cu1fFxJxj01RLGoePaLqaRkd3zZsr |
MALICIOUS
Application was dropped or rewritten from another process
- attached TT copy.pdf.exe (PID: 2344)
- attached TT copy.pdf.exe (PID: 2208)
- attached TT copy.pdf.exe (PID: 2516)
- attached TT copy.pdf.exe (PID: 3036)
LOKIBOT was detected
- attached TT copy.pdf.exe (PID: 2516)
Actions looks like stealing of personal data
- attached TT copy.pdf.exe (PID: 2516)
SUSPICIOUS
Executable content was dropped or overwritten
- WinRAR.exe (PID: 572)
- attached TT copy.pdf.exe (PID: 2516)
Application launched itself
- attached TT copy.pdf.exe (PID: 2344)
- attached TT copy.pdf.exe (PID: 2208)
Loads DLL from Mozilla Firefox
- attached TT copy.pdf.exe (PID: 2516)
Creates files in the user directory
- attached TT copy.pdf.exe (PID: 2516)
INFO
No info indicators.
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2020:07:03 03:07:00 |
| ZipCRC: | 0xa9e66085 |
| ZipCompressedSize: | 170191 |
| ZipUncompressedSize: | 244224 |
| ZipFileName: | attached TT copy.pdf.exe |
Total processes
37
Monitored processes
5
Malicious processes
3
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 572 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\attached_TT_copy.zip" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
| 2208 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa572.31602\attached TT copy.pdf.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa572.31602\attached TT copy.pdf.exe | — | WinRAR.exe | |||||||||||
User: admin Company: Aevitas Enterprises Integrity Level: MEDIUM Description: BlackMetal Exit code: 0 Version: 1.3.0.0 Modules
| |||||||||||||||
| 2344 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa572.30734\attached TT copy.pdf.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa572.30734\attached TT copy.pdf.exe | — | WinRAR.exe | |||||||||||
User: admin Company: Aevitas Enterprises Integrity Level: MEDIUM Description: BlackMetal Exit code: 0 Version: 1.3.0.0 Modules
| |||||||||||||||
| 2516 | "{path}" | C:\Users\admin\AppData\Local\Temp\Rar$EXa572.30734\attached TT copy.pdf.exe | attached TT copy.pdf.exe | ||||||||||||
User: admin Company: Aevitas Enterprises Integrity Level: MEDIUM Description: BlackMetal Exit code: 0 Version: 1.3.0.0 Modules
| |||||||||||||||
| 3036 | "{path}" | C:\Users\admin\AppData\Local\Temp\Rar$EXa572.31602\attached TT copy.pdf.exe | — | attached TT copy.pdf.exe | |||||||||||
User: admin Company: Aevitas Enterprises Integrity Level: MEDIUM Description: BlackMetal Exit code: 0 Version: 1.3.0.0 Modules
| |||||||||||||||
Total events
471
Read events
454
Write events
17
Delete events
0
Modification events
| (PID) Process: | (572) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (572) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (572) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\12F\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (572) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\12F\52C64B7E |
| Operation: | write | Name: | @C:\Windows\system32\NetworkExplorer.dll,-1 |
Value: Network | |||
| (PID) Process: | (572) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\attached_TT_copy.zip | |||
| (PID) Process: | (572) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (572) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (572) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (572) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (572) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
Executable files
3
Suspicious files
0
Text files
0
Unknown types
25
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2516 | attached TT copy.pdf.exe | C:\Users\admin\AppData\Roaming\Microsoft\Crypto\RSA\S-1-5-21-1302019708-1500728564-335382590-1000\0f5007522459c86e95ffcc62f32308f1_90059c37-1320-41a4-b58d-2b75a9850d2f | — | |
MD5:— | SHA256:— | |||
| 2516 | attached TT copy.pdf.exe | C:\Users\admin\AppData\Roaming\F63AAA\A71D80.lck | — | |
MD5:— | SHA256:— | |||
| 2516 | attached TT copy.pdf.exe | C:\Users\admin\AppData\Roaming\F63AAA\A71D80.exe | executable | |
MD5:— | SHA256:— | |||
| 572 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa572.30734\attached TT copy.pdf.exe | executable | |
MD5:— | SHA256:— | |||
| 572 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa572.31602\attached TT copy.pdf.exe | executable | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
0
DNS requests
1
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
DNS requests
Domain | IP | Reputation |
|---|---|---|
sportsgroup-hk.com |
| malicious |