| File name: | 20389c7d417ec512e18bb246a693ce37e041390b6cf1cdd5dca0728b709f910d.exe |
| Full analysis: | https://app.any.run/tasks/a7f7d18d-3a9a-44f1-8147-e2bd91461069 |
| Verdict: | Malicious activity |
| Threats: | Crypto mining malware is a resource-intensive threat that infiltrates computers with the purpose of mining cryptocurrencies. This type of threat can be deployed either on an infected machine or a compromised website. In both cases the miner will utilize the computing power of the device and its network bandwidth. |
| Analysis date: | July 08, 2025, 08:21:02 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, Nullsoft Installer self-extracting archive, 5 sections |
| MD5: | 32F21AB8CF9B96E8BA86395A0EDC2E4F |
| SHA1: | 2A5B3C07E32B3B2B0C1EF33A10685027703440EC |
| SHA256: | 20389C7D417EC512E18BB246A693CE37E041390B6CF1CDD5DCA0728B709F910D |
| SSDEEP: | 98304:8cef4lNcsqzlrrVUU2FIgW/Ctt/1VIymxMEDefdZlfpizKYtubio+6MlfsGHIZhe:PXuO05 |
MALICIOUS
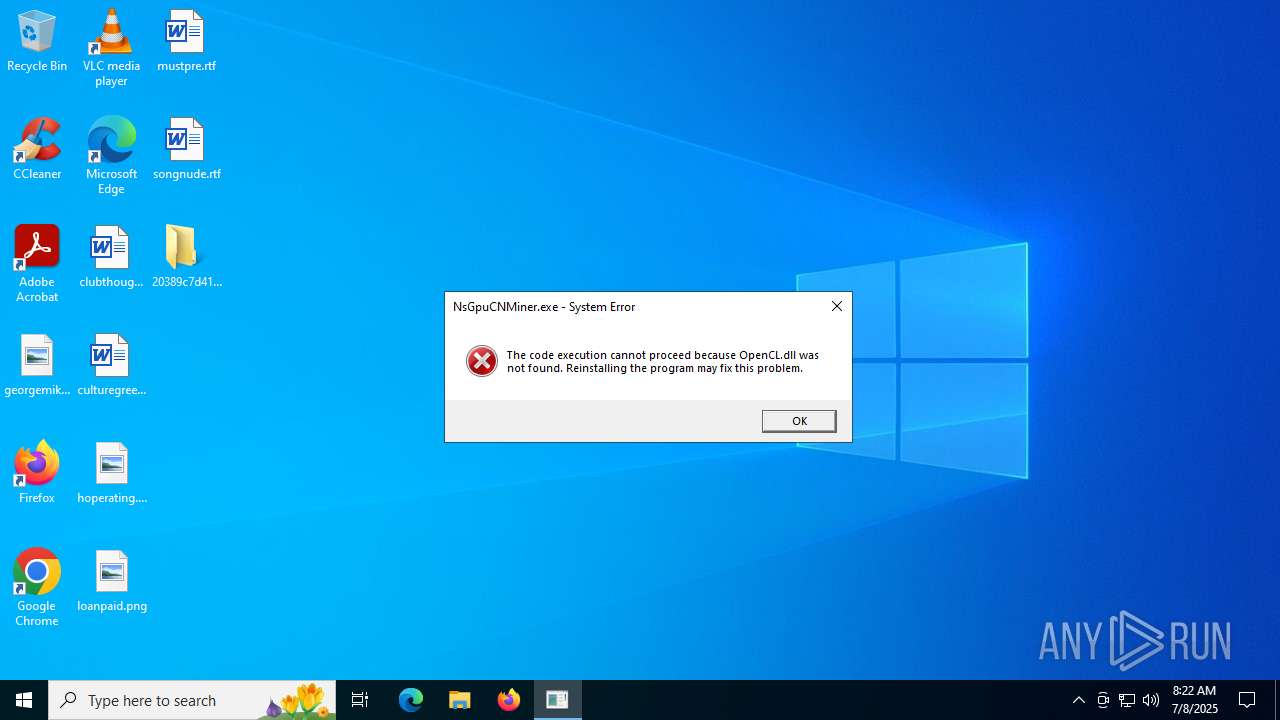
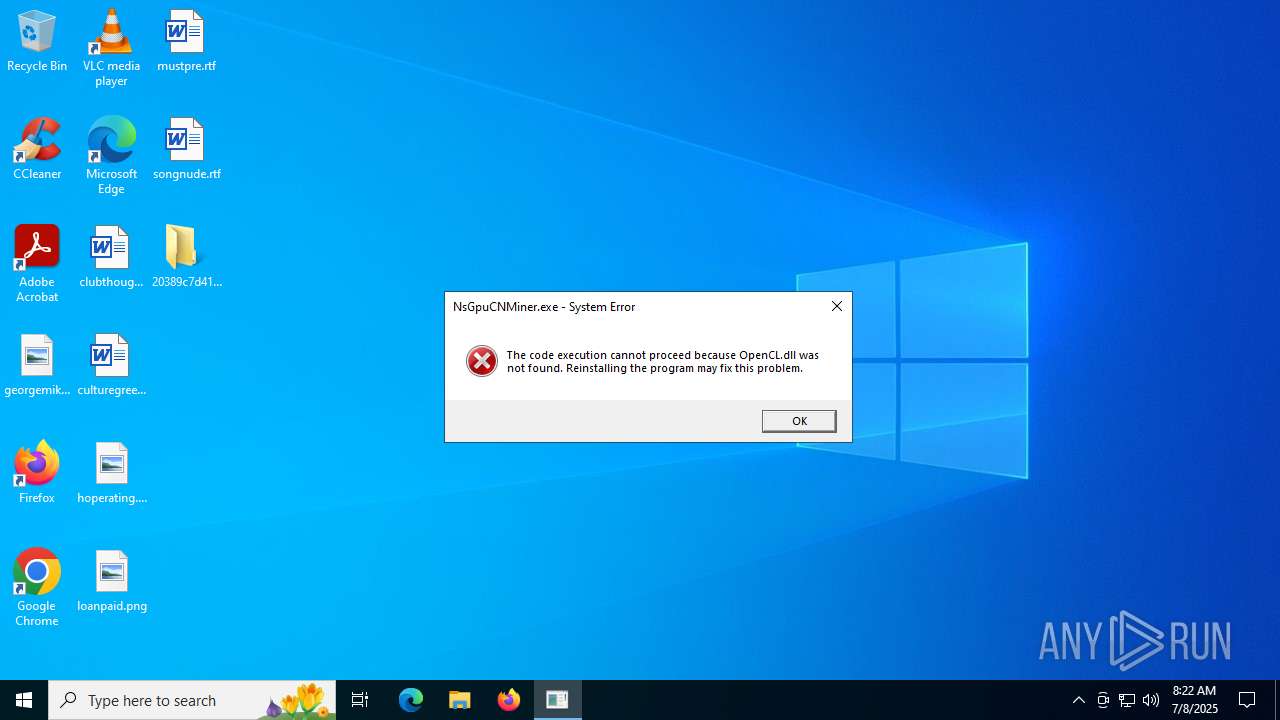
Looks like the application has launched a miner
- image.exe (PID: 2368)
- image.exe (PID: 5924)
Changes the autorun value in the registry
- image.exe (PID: 2368)
- image.exe (PID: 5924)
Create files in the Startup directory
- image.exe (PID: 2368)
SUSPICIOUS
Executable content was dropped or overwritten
- 20389c7d417ec512e18bb246a693ce37e041390b6cf1cdd5dca0728b709f910d.exe (PID: 2972)
- image.exe (PID: 2368)
- load.exe (PID: 1328)
- image.exe (PID: 5924)
- load.exe (PID: 5432)
Reads security settings of Internet Explorer
- 20389c7d417ec512e18bb246a693ce37e041390b6cf1cdd5dca0728b709f910d.exe (PID: 2972)
- image.exe (PID: 2368)
- image.exe (PID: 5924)
- load.exe (PID: 1328)
- load.exe (PID: 5432)
Starts itself from another location
- 20389c7d417ec512e18bb246a693ce37e041390b6cf1cdd5dca0728b709f910d.exe (PID: 2972)
There is functionality for taking screenshot (YARA)
- image.exe (PID: 2368)
- image.exe (PID: 5924)
The process creates files with name similar to system file names
- image.exe (PID: 2368)
- image.exe (PID: 5924)
Malware-specific behavior (creating "System.dll" in Temp)
- image.exe (PID: 2368)
- image.exe (PID: 5924)
Creates file in the systems drive root
- image.exe (PID: 2368)
- image.exe (PID: 5924)
Connects to unusual port
- NsCpuCNMiner64.exe (PID: 5720)
- NsCpuCNMiner64.exe (PID: 6140)
INFO
Checks supported languages
- 20389c7d417ec512e18bb246a693ce37e041390b6cf1cdd5dca0728b709f910d.exe (PID: 2972)
- image.exe (PID: 2368)
- NsCpuCNMiner64.exe (PID: 5720)
- load.exe (PID: 1328)
- image.exe (PID: 5924)
- NsCpuCNMiner64.exe (PID: 6140)
- load.exe (PID: 5432)
Reads the computer name
- 20389c7d417ec512e18bb246a693ce37e041390b6cf1cdd5dca0728b709f910d.exe (PID: 2972)
- image.exe (PID: 2368)
- load.exe (PID: 1328)
- image.exe (PID: 5924)
- NsCpuCNMiner64.exe (PID: 5720)
- load.exe (PID: 5432)
- NsCpuCNMiner64.exe (PID: 6140)
Create files in a temporary directory
- 20389c7d417ec512e18bb246a693ce37e041390b6cf1cdd5dca0728b709f910d.exe (PID: 2972)
- image.exe (PID: 2368)
- load.exe (PID: 1328)
- image.exe (PID: 5924)
- load.exe (PID: 5432)
The sample compiled with english language support
- 20389c7d417ec512e18bb246a693ce37e041390b6cf1cdd5dca0728b709f910d.exe (PID: 2972)
- image.exe (PID: 2368)
- load.exe (PID: 1328)
- image.exe (PID: 5924)
- load.exe (PID: 5432)
Checks proxy server information
- 20389c7d417ec512e18bb246a693ce37e041390b6cf1cdd5dca0728b709f910d.exe (PID: 2972)
- image.exe (PID: 2368)
- image.exe (PID: 5924)
- load.exe (PID: 1328)
- load.exe (PID: 5432)
- slui.exe (PID: 3876)
Creates files or folders in the user directory
- 20389c7d417ec512e18bb246a693ce37e041390b6cf1cdd5dca0728b709f910d.exe (PID: 2972)
- image.exe (PID: 2368)
- image.exe (PID: 5924)
- load.exe (PID: 1328)
- load.exe (PID: 5432)
Reads the machine GUID from the registry
- 20389c7d417ec512e18bb246a693ce37e041390b6cf1cdd5dca0728b709f910d.exe (PID: 2972)
- image.exe (PID: 2368)
- load.exe (PID: 1328)
- load.exe (PID: 5432)
- image.exe (PID: 5924)
Reads the software policy settings
- 20389c7d417ec512e18bb246a693ce37e041390b6cf1cdd5dca0728b709f910d.exe (PID: 2972)
- image.exe (PID: 2368)
- load.exe (PID: 1328)
- load.exe (PID: 5432)
- image.exe (PID: 5924)
- slui.exe (PID: 3876)
Process checks computer location settings
- 20389c7d417ec512e18bb246a693ce37e041390b6cf1cdd5dca0728b709f910d.exe (PID: 2972)
- image.exe (PID: 2368)
- image.exe (PID: 5924)
Launching a file from a Registry key
- image.exe (PID: 2368)
- image.exe (PID: 5924)
Launching a file from the Startup directory
- image.exe (PID: 2368)
Manual execution by a user
- image.exe (PID: 5924)
VMProtect protector has been detected
- NsCpuCNMiner64.exe (PID: 5720)
- NsCpuCNMiner64.exe (PID: 6140)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | NSIS - Nullsoft Scriptable Install System (94.8) |
|---|---|---|
| .exe | | | Win32 Executable MS Visual C++ (generic) (3.4) |
| .dll | | | Win32 Dynamic Link Library (generic) (0.7) |
| .exe | | | Win32 Executable (generic) (0.5) |
| .exe | | | Generic Win/DOS Executable (0.2) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2009:12:05 22:50:52+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 6 |
| CodeSize: | 24064 |
| InitializedDataSize: | 164864 |
| UninitializedDataSize: | 1024 |
| EntryPoint: | 0x30fa |
| OSVersion: | 4 |
| ImageVersion: | 6 |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 2.0.0.4 |
| ProductVersionNumber: | 2.0.0.4 |
| FileFlagsMask: | 0x0000 |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Windows, Latin1 |
| Comments: | FOLDER |
| CompanyName: | |
| FileDescription: | Folder |
| FileVersion: | 0.4 |
| LegalCopyright: | Copyright © 2014 |
| LegalTrademarks: | |
| ProductName: | Images folder (x86-x64) |
| ProductVersion: | 0.2 |
Total processes
148
Monitored processes
14
Malicious processes
3
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1164 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | NsCpuCNMiner64.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1328 | "C:\Users\admin\AppData\Roaming\Images\load.exe" | C:\Users\admin\AppData\Roaming\Images\load.exe | image.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 2 Modules
| |||||||||||||||
| 1944 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | NsCpuCNMiner64.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2368 | "C:\Users\admin\AppData\Roaming\Images\image.exe" SW_HIDE | C:\Users\admin\AppData\Roaming\Images\image.exe | 20389c7d417ec512e18bb246a693ce37e041390b6cf1cdd5dca0728b709f910d.exe | ||||||||||||
User: admin Company: Integrity Level: MEDIUM Description: Folder Version: 0.4 Modules
| |||||||||||||||
| 2972 | "C:\Users\admin\Desktop\20389c7d417ec512e18bb246a693ce37e041390b6cf1cdd5dca0728b709f910d.exe" | C:\Users\admin\Desktop\20389c7d417ec512e18bb246a693ce37e041390b6cf1cdd5dca0728b709f910d.exe | explorer.exe | ||||||||||||
User: admin Company: Integrity Level: MEDIUM Description: Folder Exit code: 2 Version: 0.4 Modules
| |||||||||||||||
| 3876 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4932 | "C:\Users\admin\AppData\Roaming\Images\NsGpuCNMiner.exe" -dbg -1 -o stratum+tcp://mine.moneropool.com:3333 -u 42sZmFqcpPyXH24VeFrJwpMeC2HLZw8ppjQ8SoWqsiidKhnBe8x3PxDA5mgETzD7dy9GXQ8qYw4BYH1yi4bJRrLcG9PJHuG -p x | C:\Users\admin\AppData\Roaming\Images\NsGpuCNMiner.exe | — | image.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221225781 Modules
| |||||||||||||||
| 5244 | "C:\Users\admin\AppData\Roaming\Images\NsGpuCNMiner.exe" -dbg -1 -o stratum+tcp://mine.moneropool.com:3333 -u 42sZmFqcpPyXH24VeFrJwpMeC2HLZw8ppjQ8SoWqsiidKhnBe8x3PxDA5mgETzD7dy9GXQ8qYw4BYH1yi4bJRrLcG9PJHuG -p x | C:\Users\admin\AppData\Roaming\Images\NsGpuCNMiner.exe | — | image.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221225781 Modules
| |||||||||||||||
| 5432 | "C:\Users\admin\AppData\Roaming\Images\load.exe" | C:\Users\admin\AppData\Roaming\Images\load.exe | image.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 2 Modules
| |||||||||||||||
| 5720 | "C:\Users\admin\AppData\Roaming\Images\NsCpuCNMiner64.exe" -dbg -1 -o stratum+tcp://mine.moneropool.com:3333 -u 42sZmFqcpPyXH24VeFrJwpMeC2HLZw8ppjQ8SoWqsiidKhnBe8x3PxDA5mgETzD7dy9GXQ8qYw4BYH1yi4bJRrLcG9PJHuG -p x | C:\Users\admin\AppData\Roaming\Images\NsCpuCNMiner64.exe | image.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Modules
| |||||||||||||||
Total events
22 807
Read events
22 790
Write events
17
Delete events
0
Modification events
| (PID) Process: | (2972) 20389c7d417ec512e18bb246a693ce37e041390b6cf1cdd5dca0728b709f910d.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (2972) 20389c7d417ec512e18bb246a693ce37e041390b6cf1cdd5dca0728b709f910d.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (2972) 20389c7d417ec512e18bb246a693ce37e041390b6cf1cdd5dca0728b709f910d.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (2368) image.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (2368) image.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (2368) image.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (2368) image.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Run |
| Operation: | write | Name: | Coin |
Value: C:\Users\admin\AppData\Roaming\Images\image.exe | |||
| (PID) Process: | (1328) load.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (1328) load.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (1328) load.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
Executable files
12
Suspicious files
1
Text files
9
Unknown types
1
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2972 | 20389c7d417ec512e18bb246a693ce37e041390b6cf1cdd5dca0728b709f910d.exe | C:\Users\admin\AppData\Local\Temp\nsa68CD.tmp\inetc.dll | executable | |
MD5:D7A3FA6A6C738B4A3C40D5602AF20B08 | SHA256:67EFF17C53A78C8EC9A28F392B9BB93DF3E74F96F6ECD87A333A482C36546B3E | |||
| 2368 | image.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\image.lnk | lnk | |
MD5:9221E56BBECD29F07EFDD5EEAB0386A7 | SHA256:B12FAC9DB6F2740FA28FED307D77412330B2D1DADDA3FEAD6F39BBAD9CDB5355 | |||
| 2368 | image.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\IE\KCV3KQBA\test5[1].htm | html | |
MD5:4F8E702CC244EC5D4DE32740C0ECBD97 | SHA256:9E17CB15DD75BBBD5DBB984EDA674863C3B10AB72613CF8A39A00C3E11A8492A | |||
| 2368 | image.exe | C:\Users\admin\AppData\Roaming\Images\NsGpuCNMiner.exe | executable | |
MD5:35D2C42B6EE0ACBCE9DFE8CC418FE5D8 | SHA256:7A2A860BB344526E8546ACD172522B4D276A4647F43DD4720281D40E390B283E | |||
| 2368 | image.exe | C:\Users\admin\AppData\Roaming\Images\pools.txt | text | |
MD5:7DC8FD6041F1FD72D9CA2140D0973E5F | SHA256:B209B7AF96AB8DA92860BDA8856A4B5632E142011489DE12CAC9487FC22C652D | |||
| 2368 | image.exe | C:\Users\admin\AppData\Roaming\Images\Data.bin | binary | |
MD5:54EF305626A0EA8B3EB8B28B331E73E2 | SHA256:932055827D87637BA7E11565F22DDA3F09CC9457769788D94413E96CF346A6E4 | |||
| 1328 | load.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\IE\RR3E01RZ\test6[1].htm | html | |
MD5:4F8E702CC244EC5D4DE32740C0ECBD97 | SHA256:9E17CB15DD75BBBD5DBB984EDA674863C3B10AB72613CF8A39A00C3E11A8492A | |||
| 2972 | 20389c7d417ec512e18bb246a693ce37e041390b6cf1cdd5dca0728b709f910d.exe | C:\Users\admin\AppData\Roaming\Images\image.exe | executable | |
MD5:32F21AB8CF9B96E8BA86395A0EDC2E4F | SHA256:20389C7D417EC512E18BB246A693CE37E041390B6CF1CDD5DCA0728B709F910D | |||
| 2368 | image.exe | C:\Users\admin\AppData\Roaming\Images\NsCpuCNMiner64.exe | executable | |
MD5:EEDB9D86AE8ABC65FA7AC7C6323D4E8F | SHA256:D0326F0DDCE4C00F93682E3A6F55A3125F6387E959E9ED6C5E5584E78E737078 | |||
| 2368 | image.exe | C:\Users\admin\AppData\Roaming\Images\NsCpuCNMiner32.exe | executable | |
MD5:3AFEB8E9AF02A33FF71BF2F6751CAE3A | SHA256:A0EBA3FDA0D7B22A5D694105EC700DF7C7012DDC4AE611C3071EF858E2C69F08 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
47
TCP/UDP connections
70
DNS requests
23
Threats
17
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | POST | 400 | 20.190.160.66:443 | https://login.live.com/ppsecure/deviceaddcredential.srf | unknown | text | 203 b | whitelisted |
5560 | RUXIMICS.exe | GET | 200 | 23.216.77.21:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | POST | 400 | 20.190.160.66:443 | https://login.live.com/ppsecure/deviceaddcredential.srf | unknown | text | 203 b | whitelisted |
5944 | MoUsoCoreWorker.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
2972 | 20389c7d417ec512e18bb246a693ce37e041390b6cf1cdd5dca0728b709f910d.exe | GET | 301 | 81.28.12.12:80 | http://testswork.ru/test5.txt | unknown | — | — | unknown |
5944 | MoUsoCoreWorker.exe | GET | 200 | 23.216.77.21:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | POST | 200 | 20.190.160.64:443 | https://login.live.com/RST2.srf | unknown | xml | 1.24 Kb | whitelisted |
— | — | GET | 404 | 81.28.12.12:443 | https://testswork.ru/test5.txt | unknown | html | 196 b | unknown |
— | — | POST | 400 | 40.126.32.134:443 | https://login.live.com/ppsecure/deviceaddcredential.srf | unknown | text | 203 b | whitelisted |
5560 | RUXIMICS.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
5560 | RUXIMICS.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5944 | MoUsoCoreWorker.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2972 | 20389c7d417ec512e18bb246a693ce37e041390b6cf1cdd5dca0728b709f910d.exe | 81.28.12.12:80 | testswork.ru | G-Core Labs S.A. | LU | unknown |
1268 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
2972 | 20389c7d417ec512e18bb246a693ce37e041390b6cf1cdd5dca0728b709f910d.exe | 81.28.12.12:443 | testswork.ru | G-Core Labs S.A. | LU | unknown |
4156 | svchost.exe | 40.126.32.68:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
5944 | MoUsoCoreWorker.exe | 23.216.77.21:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
testswork.ru |
| unknown |
login.live.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
nexusrules.officeapps.live.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
activation-v2.sls.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2972 | 20389c7d417ec512e18bb246a693ce37e041390b6cf1cdd5dca0728b709f910d.exe | Potentially Bad Traffic | ET USER_AGENTS Observed Suspicious UA (NSIS_Inetc (Mozilla)) |
— | — | Potentially Bad Traffic | ET USER_AGENTS Observed Suspicious UA (NSIS_Inetc (Mozilla)) |
2368 | image.exe | Potentially Bad Traffic | ET USER_AGENTS Observed Suspicious UA (NSIS_Inetc (Mozilla)) |
— | — | Unknown Traffic | ET USER_AGENTS Microsoft Dr Watson User-Agent (MSDW) |
2368 | image.exe | Potentially Bad Traffic | ET USER_AGENTS Observed Suspicious UA (NSIS_Inetc (Mozilla)) |
— | — | Potentially Bad Traffic | ET USER_AGENTS Observed Suspicious UA (NSIS_Inetc (Mozilla)) |
1328 | load.exe | Potentially Bad Traffic | ET USER_AGENTS Observed Suspicious UA (NSIS_Inetc (Mozilla)) |
1328 | load.exe | Potentially Bad Traffic | ET USER_AGENTS Observed Suspicious UA (NSIS_Inetc (Mozilla)) |
— | — | Potentially Bad Traffic | ET USER_AGENTS Observed Suspicious UA (NSIS_Inetc (Mozilla)) |
2368 | image.exe | Potentially Bad Traffic | ET USER_AGENTS Observed Suspicious UA (NSIS_Inetc (Mozilla)) |