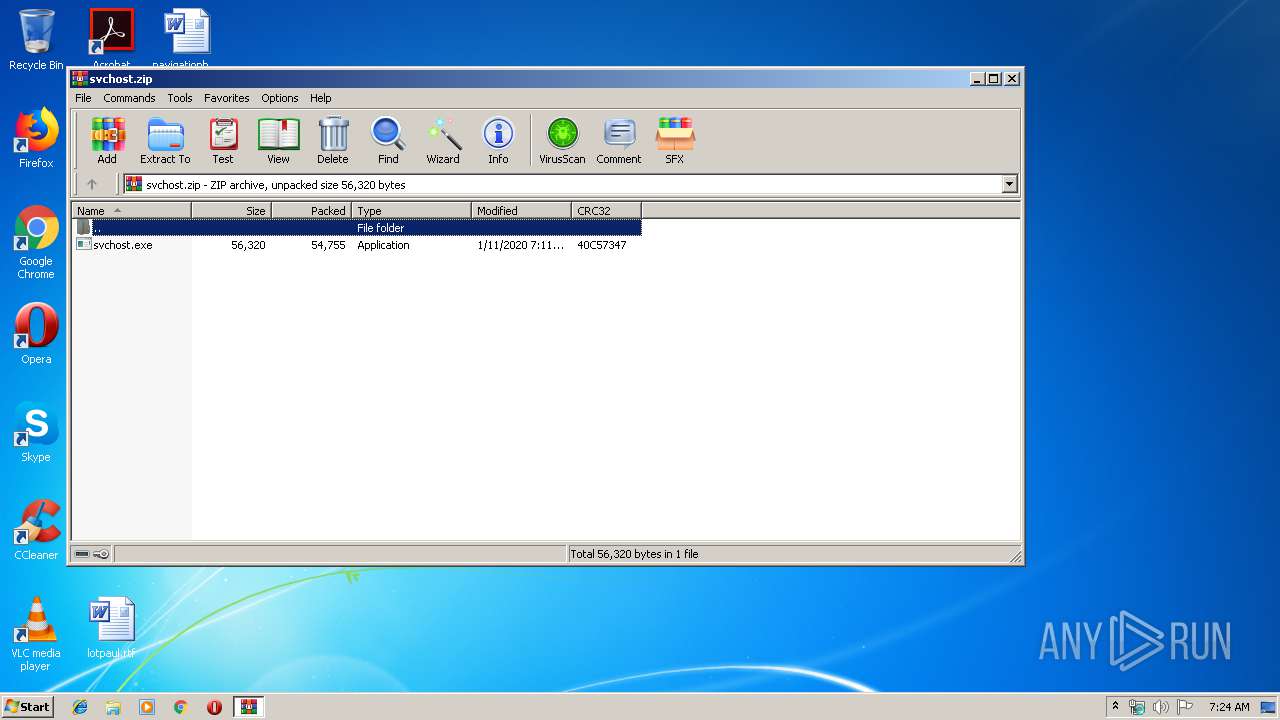
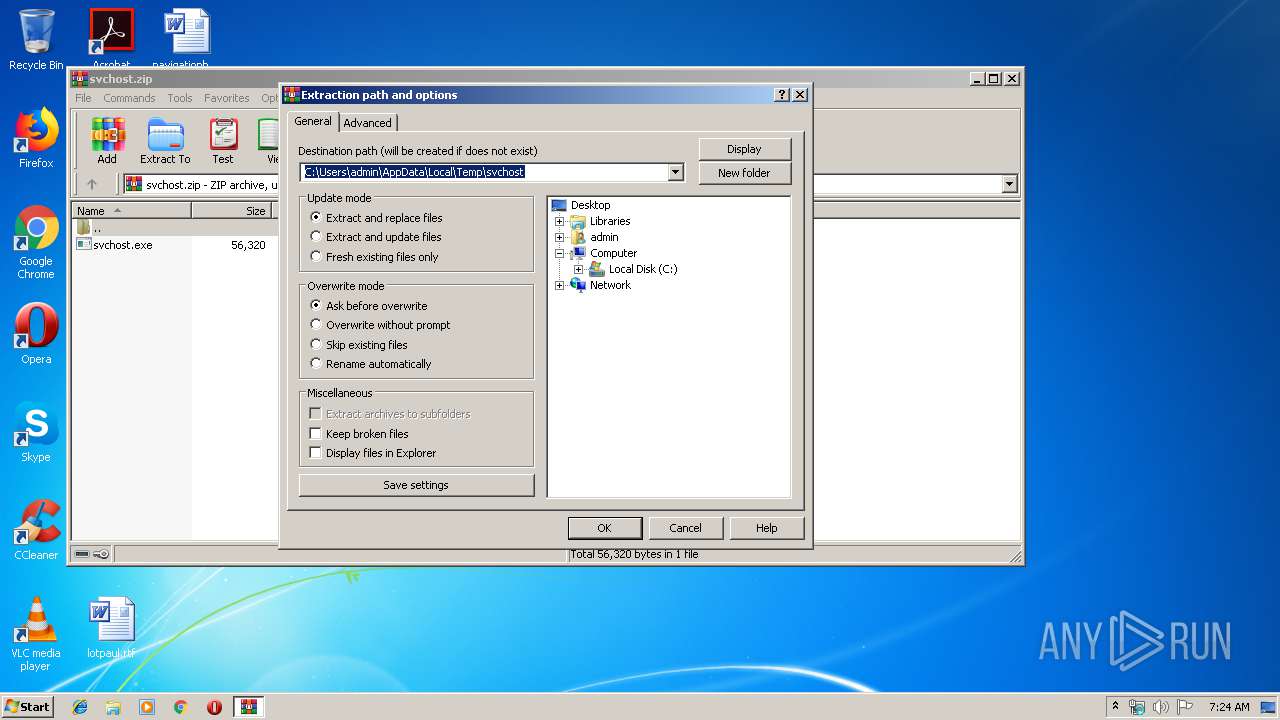
| File name: | svchost.zip |
| Full analysis: | https://app.any.run/tasks/761d2b1a-5144-4c49-b5a3-7a23c3533d86 |
| Verdict: | Malicious activity |
| Threats: | Ramnit is a highly modular banking trojan and worm that evolved from a file-infecting virus into a powerful cybercrime tool. It specializes in financial fraud, credential theft, remote access, and malware delivery, being a serious threat to businesses and individuals. First spotted in 2010, Ramnit became popular after the 2014 takedown of the GameOver Zeus botnet, as cybercriminals sought alternatives for banking fraud. |
| Analysis date: | January 11, 2020, 07:24:18 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract |
| MD5: | EF1E4C04BF60CACA1DFE0386A4F11D97 |
| SHA1: | C6C044EAFC184F275BF1A55DBDD85355C188D9E3 |
| SHA256: | 1FF04ED2CADB8BDA5A42EA75052F5346348CC75F14B4B22A841915D881BA1F7A |
| SSDEEP: | 1536:muaDO+nKjYRotV3nsPFG+5ODTb7MX6DgDTj:PwEYutj+5O7oH |
MALICIOUS
RAMNIT was detected
- iexplore.exe (PID: 1908)
Changes the login/logoff helper path in the registry
- iexplore.exe (PID: 1908)
Application was dropped or rewritten from another process
- svchost.exe (PID: 2572)
- DesktopLayer.exe (PID: 3388)
Connects to CnC server
- iexplore.exe (PID: 1908)
SUSPICIOUS
Executable content was dropped or overwritten
- WinRAR.exe (PID: 2456)
- svchost.exe (PID: 2572)
Creates executable files which already exist in Windows
- WinRAR.exe (PID: 2456)
Starts Internet Explorer
- DesktopLayer.exe (PID: 3388)
Creates files in the program directory
- iexplore.exe (PID: 1908)
- svchost.exe (PID: 2572)
INFO
Manual execution by user
- svchost.exe (PID: 2572)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2020:01:11 15:11:07 |
| ZipCRC: | 0x40c57347 |
| ZipCompressedSize: | 54755 |
| ZipUncompressedSize: | 56320 |
| ZipFileName: | svchost.exe |
Total processes
42
Monitored processes
4
Malicious processes
3
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1908 | "C:\Program Files\Internet Explorer\iexplore.exe" | C:\Program Files\Internet Explorer\iexplore.exe | DesktopLayer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Internet Explorer Exit code: 0 Version: 8.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2456 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\svchost.zip" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
| 2572 | "C:\Users\admin\Desktop\svchost.exe" | C:\Users\admin\Desktop\svchost.exe | explorer.exe | ||||||||||||
User: admin Company: SOFTWIN S.R.L. Integrity Level: HIGH Description: BitDefender Management Console Exit code: 0 Version: 106.42.73.61 Modules
| |||||||||||||||
| 3388 | "C:\Program Files\Microsoft\DesktopLayer.exe" | C:\Program Files\Microsoft\DesktopLayer.exe | — | svchost.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
Total events
534
Read events
523
Write events
11
Delete events
0
Modification events
| (PID) Process: | (2456) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (2456) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (2456) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\12B\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2456) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\svchost.zip | |||
| (PID) Process: | (2456) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (2456) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (2456) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (2456) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (2456) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\DialogEditHistory\ExtrPath |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop | |||
| (PID) Process: | (1908) iexplore.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Winlogon |
| Operation: | write | Name: | Userinit |
Value: c:\windows\system32\userinit.exe,,c:\program files\microsoft\desktoplayer.exe | |||
Executable files
2
Suspicious files
2
Text files
39
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1908 | iexplore.exe | C:\Program Files\Adobe\Acrobat Reader DC\Leame.htm | html | |
MD5:— | SHA256:— | |||
| 1908 | iexplore.exe | C:\Program Files\Adobe\Acrobat Reader DC\LueMinut.htm | html | |
MD5:— | SHA256:— | |||
| 1908 | iexplore.exe | C:\Program Files\Adobe\Acrobat Reader DC\LeesMij.htm | html | |
MD5:— | SHA256:— | |||
| 1908 | iexplore.exe | C:\Program Files\Internet Explorer\dmlconf.dat | binary | |
MD5:— | SHA256:— | |||
| 1908 | iexplore.exe | C:\Program Files\Adobe\Acrobat Reader DC\Reader\Legal\DEU\license.html | xml | |
MD5:— | SHA256:— | |||
| 1908 | iexplore.exe | C:\Program Files\Adobe\Acrobat Reader DC\Leggimi.htm | html | |
MD5:— | SHA256:— | |||
| 1908 | iexplore.exe | C:\Program Files\Adobe\Acrobat Reader DC\LeiaMe.htm | html | |
MD5:— | SHA256:— | |||
| 1908 | iexplore.exe | C:\Program Files\Adobe\Acrobat Reader DC\Liesmich.htm | html | |
MD5:— | SHA256:— | |||
| 1908 | iexplore.exe | C:\Program Files\Adobe\Acrobat Reader DC\Benioku.htm | html | |
MD5:— | SHA256:— | |||
| 1908 | iexplore.exe | C:\Program Files\Adobe\Acrobat Reader DC\Llegiu-me.htm | html | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
4
DNS requests
2
Threats
5
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
1908 | iexplore.exe | 72.26.218.70:443 | fget-career.com | Voxel Dot Net, Inc. | NL | malicious |
1908 | iexplore.exe | 172.217.16.78:80 | google.com | Google Inc. | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| malicious |
fget-career.com |
| malicious |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1908 | iexplore.exe | A Network Trojan was detected | ET TROJAN Win32/Ramnit Checkin |
1908 | iexplore.exe | A Network Trojan was detected | MALWARE [PTsecurity] Win32/Ramnit Checkin |
1908 | iexplore.exe | A Network Trojan was detected | ET TROJAN Win32/Ramnit Checkin |
1908 | iexplore.exe | A Network Trojan was detected | MALWARE [PTsecurity] Win32/Ramnit Checkin |
1 ETPRO signatures available at the full report