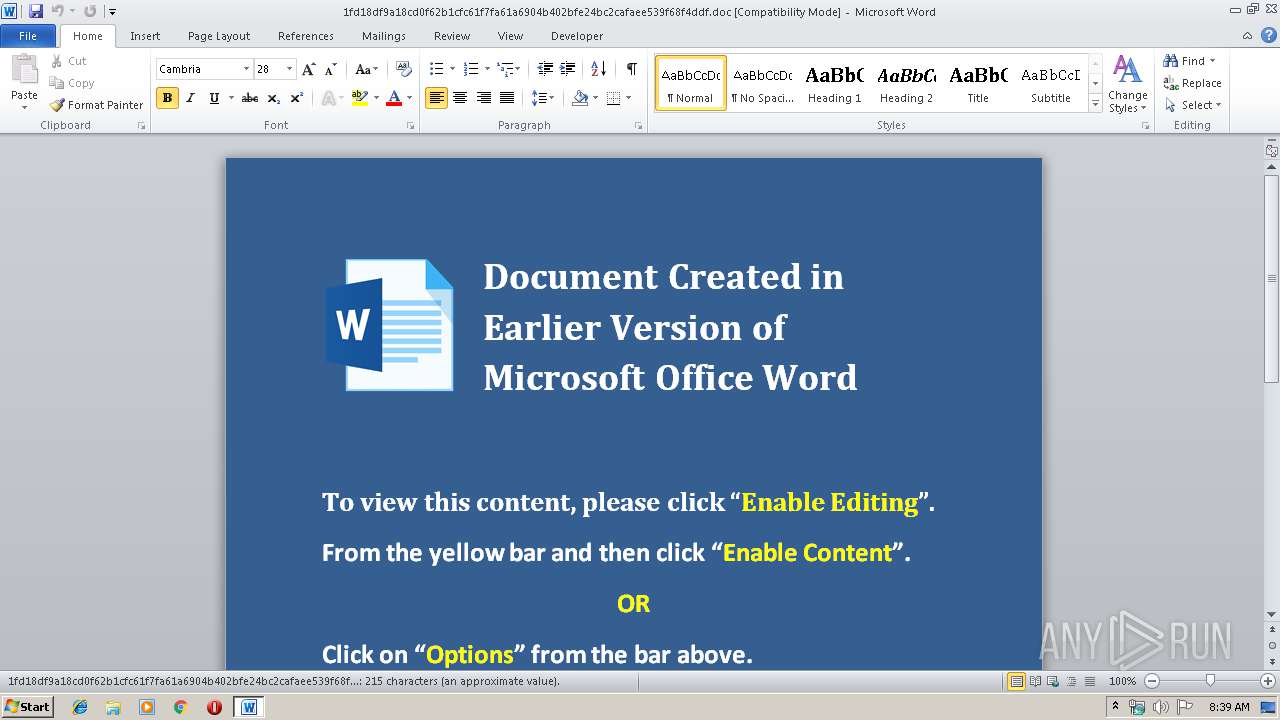
| File name: | 1fd18df9a18cd0f62b1cfc61f7fa61a6904b402bfe24bc2cafaee539f68f4ddf.doc |
| Full analysis: | https://app.any.run/tasks/68d9dad7-6ad4-4e82-8998-6d60398840ff |
| Verdict: | Malicious activity |
| Threats: | WarZone RAT is a remote access trojan, which is written in C++ and offered as a malware-as-a-service. It packs a wide range of capabilities, from stealing victims’ files and passwords to capturing desktop activities. WarZone RAT is primarily distributed via phishing emails and receives regular updates from its C2. |
| Analysis date: | September 02, 2019, 07:38:56 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/msword |
| File info: | Composite Document File V2 Document, Little Endian, Os: Windows, Version 6.2, Code page: 1252, Author: Xyz, Template: Normal.dotm, Last Saved By: Xyz, Revision Number: 2, Name of Creating Application: Microsoft Office Word, Total Editing Time: 01:00, Create Time/Date: Mon Aug 26 18:57:00 2019, Last Saved Time/Date: Mon Aug 26 18:58:00 2019, Number of Pages: 1, Number of Words: 38, Number of Characters: 223, Security: 0 |
| MD5: | DA9876099D168B9A8028D0D2DB854D28 |
| SHA1: | D8AB80E07E0A433A57A4145568DF05AA29F5811D |
| SHA256: | 1FD18DF9A18CD0F62B1CFC61F7FA61A6904B402BFE24BC2CAFAEE539F68F4DDF |
| SSDEEP: | 12288:fhOrf+uHxdWPqTF7Y+YTlunGaNj2CE1DhhtvLTFnTyY:5OrRHxdWPqTF7Y+YTlunGaNj29DhgY |
MALICIOUS
Unusual execution from Microsoft Office
- WINWORD.EXE (PID: 3368)
Application was dropped or rewritten from another process
- pyfwygm.exe (PID: 3780)
- tmpAF8E.exe (PID: 2340)
- tmpAF8E.exe (PID: 1456)
- tmpAF8E.exe (PID: 3864)
- tmpAF8E.exe (PID: 3348)
Executable content was dropped or overwritten
- WINWORD.EXE (PID: 3368)
Uses Task Scheduler to run other applications
- tmpAF8E.exe (PID: 2340)
Loads the Task Scheduler COM API
- schtasks.exe (PID: 2400)
Runs app for hidden code execution
- tmpAF8E.exe (PID: 1456)
AVEMARIA was detected
- tmpAF8E.exe (PID: 1456)
Runs injected code in another process
- tmpAF8E.exe (PID: 1456)
Changes the autorun value in the registry
- tmpAF8E.exe (PID: 1456)
Application was injected by another process
- explorer.exe (PID: 276)
Connects to CnC server
- tmpAF8E.exe (PID: 1456)
Loads dropped or rewritten executable
- dism.exe (PID: 2668)
SUSPICIOUS
Creates files in the user directory
- tmpAF8E.exe (PID: 2340)
Executable content was dropped or overwritten
- pyfwygm.exe (PID: 3780)
- tmpAF8E.exe (PID: 2340)
- DllHost.exe (PID: 2132)
- cmd.exe (PID: 2260)
Starts CMD.EXE for commands execution
- tmpAF8E.exe (PID: 1456)
Application launched itself
- tmpAF8E.exe (PID: 2340)
Executed via COM
- DllHost.exe (PID: 2132)
Reads the machine GUID from the registry
- tmpAF8E.exe (PID: 1456)
INFO
Starts Microsoft Office Application
- explorer.exe (PID: 276)
Creates files in the user directory
- WINWORD.EXE (PID: 3368)
Reads Microsoft Office registry keys
- WINWORD.EXE (PID: 3368)
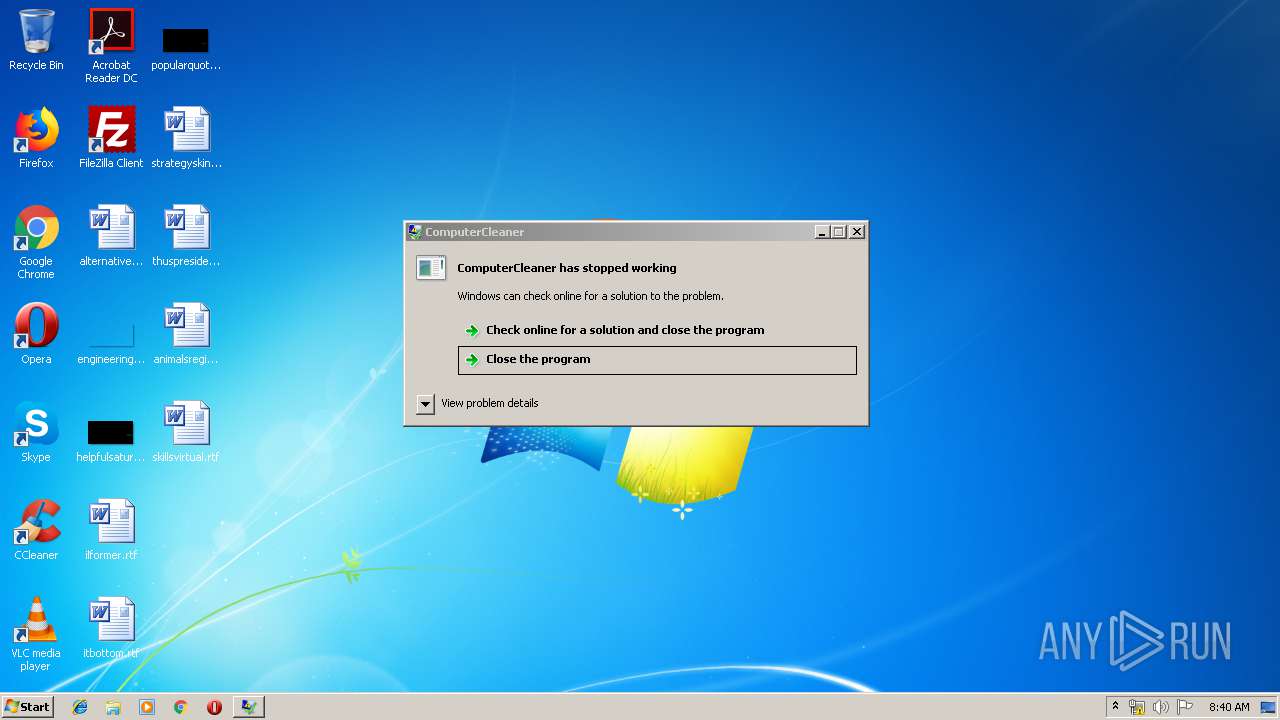
Application was crashed
- tmpAF8E.exe (PID: 1456)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .doc | | | Microsoft Word document (54.2) |
|---|---|---|
| .doc | | | Microsoft Word document (old ver.) (32.2) |
EXIF
FlashPix
| Title: | - |
|---|---|
| Subject: | - |
| Author: | Xyz |
| Keywords: | - |
| Comments: | - |
| Template: | Normal.dotm |
| LastModifiedBy: | Xyz |
| RevisionNumber: | 2 |
| Software: | Microsoft Office Word |
| TotalEditTime: | 1.0 minutes |
| CreateDate: | 2019:08:26 17:57:00 |
| ModifyDate: | 2019:08:26 17:58:00 |
| Pages: | 1 |
| Words: | 38 |
| Characters: | 223 |
| Security: | None |
| CodePage: | Windows Latin 1 (Western European) |
| Company: | - |
| Lines: | 1 |
| Paragraphs: | 1 |
| CharCountWithSpaces: | 260 |
| AppVersion: | 14 |
| ScaleCrop: | No |
| LinksUpToDate: | No |
| SharedDoc: | No |
| HyperlinksChanged: | No |
| TitleOfParts: | - |
| HeadingPairs: |
|
| CompObjUserTypeLen: | 32 |
| CompObjUserType: | Microsoft Word 97-2003 Document |
Total processes
53
Monitored processes
13
Malicious processes
5
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 276 | C:\Windows\Explorer.EXE | C:\Windows\explorer.exe | — | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1456 | "C:\Users\admin\AppData\Local\Temp\tmpAF8E.exe" | C:\Users\admin\AppData\Local\Temp\tmpAF8E.exe | tmpAF8E.exe | ||||||||||||
User: admin Company: Iobit Assemblies Integrity Level: MEDIUM Description: ComputerCleaner Exit code: 0 Version: 2.9.9.2 Modules
| |||||||||||||||
| 2132 | C:\Windows\system32\DllHost.exe /Processid:{3AD05575-8857-4850-9277-11B85BDB8E09} | C:\Windows\system32\DllHost.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: COM Surrogate Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2260 | "C:\Windows\System32\cmd.exe" | C:\Windows\System32\cmd.exe | tmpAF8E.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 2340 | "C:\Users\admin\AppData\Local\Temp\tmpAF8E.exe" | C:\Users\admin\AppData\Local\Temp\tmpAF8E.exe | pyfwygm.exe | ||||||||||||
User: admin Company: Iobit Assemblies Integrity Level: MEDIUM Description: ComputerCleaner Exit code: 0 Version: 2.9.9.2 Modules
| |||||||||||||||
| 2400 | "C:\Windows\System32\schtasks.exe" /Create /TN "Updates\SEOQwqLS" /XML "C:\Users\admin\AppData\Local\Temp\tmp8C32.tmp" | C:\Windows\System32\schtasks.exe | — | tmpAF8E.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Manages scheduled tasks Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2668 | "C:\Windows\system32\dism.exe" /online /norestart /apply-unattend:"C:\Users\admin\AppData\Local\Temp\ellocnak.xml" | C:\Windows\system32\dism.exe | — | pkgmgr.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Dism Image Servicing Utility Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2932 | "C:\Windows\system32\pkgmgr.exe" /n:%temp%\ellocnak.xml | C:\Windows\system32\pkgmgr.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Package Manager Exit code: 3221226540 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 3348 | "C:\Users\admin\AppData\Local\Temp\tmpAF8E.exe" | C:\Users\admin\AppData\Local\Temp\tmpAF8E.exe | — | explorer.exe | |||||||||||
User: admin Company: Iobit Assemblies Integrity Level: MEDIUM Description: ComputerCleaner Exit code: 0 Version: 2.9.9.2 Modules
| |||||||||||||||
| 3368 | "C:\Program Files\Microsoft Office\Office14\WINWORD.EXE" /n "C:\Users\admin\AppData\Local\Temp\1fd18df9a18cd0f62b1cfc61f7fa61a6904b402bfe24bc2cafaee539f68f4ddf.doc" | C:\Program Files\Microsoft Office\Office14\WINWORD.EXE | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Word Exit code: 0 Version: 14.0.6024.1000 Modules
| |||||||||||||||
Total events
1 589
Read events
1 500
Write events
80
Delete events
9
Modification events
| (PID) Process: | (3368) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Word\Resiliency\StartupItems |
| Operation: | write | Name: | ;d# |
Value: 3B642300280D0000010000000000000000000000 | |||
| (PID) Process: | (3368) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: Off | |||
| (PID) Process: | (3368) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: On | |||
| (PID) Process: | (3368) WINWORD.EXE | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\UserData\S-1-5-18\Products\00004109D30000000000000000F01FEC\Usage |
| Operation: | write | Name: | WORDFiles |
Value: 1327628318 | |||
| (PID) Process: | (3368) WINWORD.EXE | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\UserData\S-1-5-18\Products\00004109D30000000000000000F01FEC\Usage |
| Operation: | write | Name: | ProductFiles |
Value: 1327628432 | |||
| (PID) Process: | (3368) WINWORD.EXE | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\UserData\S-1-5-18\Products\00004109D30000000000000000F01FEC\Usage |
| Operation: | write | Name: | ProductFiles |
Value: 1327628433 | |||
| (PID) Process: | (3368) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Word |
| Operation: | write | Name: | MTTT |
Value: 280D000052A968846161D50100000000 | |||
| (PID) Process: | (3368) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Word\Resiliency\StartupItems |
| Operation: | write | Name: | de# |
Value: 64652300280D000004000000000000008C00000001000000840000003E0043003A005C00550073006500720073005C00610064006D0069006E005C0041007000700044006100740061005C0052006F0061006D0069006E0067005C004D006900630072006F0073006F00660074005C00540065006D0070006C0061007400650073005C004E006F0072006D0061006C002E0064006F0074006D00000000000000 | |||
| (PID) Process: | (3368) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Word\Resiliency\StartupItems |
| Operation: | delete value | Name: | de# |
Value: 64652300280D000004000000000000008C00000001000000840000003E0043003A005C00550073006500720073005C00610064006D0069006E005C0041007000700044006100740061005C0052006F0061006D0069006E0067005C004D006900630072006F0073006F00660074005C00540065006D0070006C0061007400650073005C004E006F0072006D0061006C002E0064006F0074006D00000000000000 | |||
| (PID) Process: | (3368) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
Executable files
5
Suspicious files
0
Text files
2
Unknown types
2
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3368 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\CVR988B.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 3368 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\~DF91B8216DB9E89A3D.TMP | — | |
MD5:— | SHA256:— | |||
| 3368 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.Word\~WRS{FEAFD573-A489-4DC6-8AAD-62001ED858F0}.tmp | — | |
MD5:— | SHA256:— | |||
| 3368 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.Word\~WRF{06AA1C27-F1B7-4649-9231-140DFF7868CF}.tmp | — | |
MD5:— | SHA256:— | |||
| 2340 | tmpAF8E.exe | C:\Users\admin\AppData\Local\Temp\tmp8C32.tmp | — | |
MD5:— | SHA256:— | |||
| 3368 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\pyfwygm.exe | executable | |
MD5:— | SHA256:— | |||
| 3780 | pyfwygm.exe | C:\Users\admin\AppData\Local\Temp\tmpAF8E.exe | executable | |
MD5:— | SHA256:— | |||
| 2340 | tmpAF8E.exe | C:\Users\admin\AppData\Roaming\SEOQwqLS.exe | executable | |
MD5:— | SHA256:— | |||
| 3852 | pkgmgr.exe | C:\Windows\Logs\CBS\CBS.log | text | |
MD5:— | SHA256:— | |||
| 3368 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Templates\~$Normal.dotm | pgc | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
2
DNS requests
1
Threats
2
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3780 | pyfwygm.exe | 173.212.193.7:443 | www.bpgc-golf.com | Contabo GmbH | DE | unknown |
1456 | tmpAF8E.exe | 64.188.25.152:4965 | — | QuadraNet, Inc | US | malicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.bpgc-golf.com |
| unknown |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1456 | tmpAF8E.exe | A Network Trojan was detected | AV TROJAN Ave Maria RAT CnC Response |
1456 | tmpAF8E.exe | A Network Trojan was detected | MALWARE [PTsecurity] AveMaria.RAT Encrypted Checkin |